Network Design and Troubleshooting Report - Semester 1, Year 2
VerifiedAdded on 2022/11/14
|16
|3783
|190
Report
AI Summary
This report details the network design and troubleshooting process for a client, alm.co.uk, outlining the functional and non-functional requirements for a network infrastructure. It includes an examination of network components, a justification for device selection, and an analysis of current network problems. The report evaluates various technologies and protocols, presents a network subnet plan and diagram, and discusses security precautions and configurations. It emphasizes the use of VLANs for department segmentation, redundant links for reliability, and the integration of wireless access points. The report addresses scalability, security, and the importance of physical security measures for servers. The report also provides a detailed technical design and implementation plan for the network, covering aspects like IP addressing, switch and router configurations, and wireless network setup.

Running head: NETWORK DESIGN AND TROUBLESHOOTING
Network Design and Troubleshooting
Name of the Student
Name of the University
Author’s Note
Network Design and Troubleshooting
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK DESIGN AND TROUBLESHOOTING
Table of Contents
Introduction......................................................................................................................................2
Functional and Non Functional Requirement..................................................................................2
Examination and Analysis of different network Components.........................................................3
Reason for selection of device and components..............................................................................4
Current problems in the network.....................................................................................................5
Evaluation of different technology and protocols...........................................................................5
Network Subnet Plan.......................................................................................................................7
Network Diagram............................................................................................................................9
Justification......................................................................................................................................9
Security precaution and Configuration..........................................................................................10
Testing of the network...................................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
NETWORK DESIGN AND TROUBLESHOOTING
Table of Contents
Introduction......................................................................................................................................2
Functional and Non Functional Requirement..................................................................................2
Examination and Analysis of different network Components.........................................................3
Reason for selection of device and components..............................................................................4
Current problems in the network.....................................................................................................5
Evaluation of different technology and protocols...........................................................................5
Network Subnet Plan.......................................................................................................................7
Network Diagram............................................................................................................................9
Justification......................................................................................................................................9
Security precaution and Configuration..........................................................................................10
Testing of the network...................................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13

2
NETWORK DESIGN AND TROUBLESHOOTING
Introduction
The process of evaluating, understanding and scoping the network which is to be
implemented is known as network designing. It is generally performed by the engineers who
represents the network design as the network diagram. The network design includes several other
things like the logical map of the desired network, the cabling structure, quantity, location and
the type of the network devices like the routers, servers and the switches (Govindan et al. 2016).
IP addressing structures are also among the prime requirements along with the architecture for
network as well as overall security. The purpose of the report is the development of a network
infrastructure for a client named alm.co.uk that have four departments. An analysis is made on
the number of users and their requirement for the development of the network. The network
model that can be implemented for development of the network is evaluated and discussed in the
report for improving the scalability and security of the network.
Functional and Non Functional Requirement
The functional requirement identified for developing the network solution for alm.co.uk.
are stated below:
To allow users to connect their wireless devices with the developed network
To restrict the access of the users for a department to connect with the other
department subnet
To use redundant link such that the data packet can flow between the different
host with minimum delay and packet loss
To reduce congestion in the network and allow users to connect with the network
from remote location
NETWORK DESIGN AND TROUBLESHOOTING
Introduction
The process of evaluating, understanding and scoping the network which is to be
implemented is known as network designing. It is generally performed by the engineers who
represents the network design as the network diagram. The network design includes several other
things like the logical map of the desired network, the cabling structure, quantity, location and
the type of the network devices like the routers, servers and the switches (Govindan et al. 2016).
IP addressing structures are also among the prime requirements along with the architecture for
network as well as overall security. The purpose of the report is the development of a network
infrastructure for a client named alm.co.uk that have four departments. An analysis is made on
the number of users and their requirement for the development of the network. The network
model that can be implemented for development of the network is evaluated and discussed in the
report for improving the scalability and security of the network.
Functional and Non Functional Requirement
The functional requirement identified for developing the network solution for alm.co.uk.
are stated below:
To allow users to connect their wireless devices with the developed network
To restrict the access of the users for a department to connect with the other
department subnet
To use redundant link such that the data packet can flow between the different
host with minimum delay and packet loss
To reduce congestion in the network and allow users to connect with the network
from remote location
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK DESIGN AND TROUBLESHOOTING
To host an internal website and configure a Web server and dns server
To configure an email server and allow the user to send and receive mail between
each of the department.
To restrict the unauthorized users to access the sensitive data and resources of the
organization
To use separate IP address for the wireless network and restrict the wireless users
to access the internal network
To use secure encryption algorithm to restrict the unknown users to access the
wireless network
The non-functional requirements includes scalability, reliability, availability, regulatory,
recoverability, capacity, maintainability, serviceability, security, regulatory, manageability,
environmental, data integrity, interoperability and usability (Xiaogang and Quan 2018). The
functional requirement includes every technical details, calculations, processing, data
manipulation and every other specification that a particular system is desired to achieve.
The desired network must be scalable as mentioned. A system is termed as scalable when
it can handle changes within itself, especially the growing ones. The system must be capable of
adding more resources to its existing framework.
Examination and Analysis of different network Components
An analysis is needed to be made on the data flow in the network by capturing the
network traffic from different network equipment’s. Different components of the wireless
networks are as follows: Switches, routers, network hubs, wireless access points, network
servers, network cables, and Network Interface Cards (NIC). Since the organization has a private
IP address for the LAN, one of the interface is needed to be subnetted for allocating different
NETWORK DESIGN AND TROUBLESHOOTING
To host an internal website and configure a Web server and dns server
To configure an email server and allow the user to send and receive mail between
each of the department.
To restrict the unauthorized users to access the sensitive data and resources of the
organization
To use separate IP address for the wireless network and restrict the wireless users
to access the internal network
To use secure encryption algorithm to restrict the unknown users to access the
wireless network
The non-functional requirements includes scalability, reliability, availability, regulatory,
recoverability, capacity, maintainability, serviceability, security, regulatory, manageability,
environmental, data integrity, interoperability and usability (Xiaogang and Quan 2018). The
functional requirement includes every technical details, calculations, processing, data
manipulation and every other specification that a particular system is desired to achieve.
The desired network must be scalable as mentioned. A system is termed as scalable when
it can handle changes within itself, especially the growing ones. The system must be capable of
adding more resources to its existing framework.
Examination and Analysis of different network Components
An analysis is needed to be made on the data flow in the network by capturing the
network traffic from different network equipment’s. Different components of the wireless
networks are as follows: Switches, routers, network hubs, wireless access points, network
servers, network cables, and Network Interface Cards (NIC). Since the organization has a private
IP address for the LAN, one of the interface is needed to be subnetted for allocating different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK DESIGN AND TROUBLESHOOTING
range of IP address for the four departments (Betzel et al. 2016). Another interface is needed for
the wireless network and connect the wireless access point for providing wireless service to the
users. Routers are responsible for transferring data from one device to the other. The data are
sent in the form of packets. The determination of the destination of the packet delivery is done by
the router, which reads the packets to route the information to a specific destination. The network
is also provided with switches which ensures the proper flow of information within the network.
Network hubs are present to connect numerous networks and make them act as a one (Gal et al.
2017). Network hub, like the switches and the routers, broadcasts information throughout the
connection instead of a particular device. Apart from these, there are wireless access points.
These points helps in routing data like routers with the help of wireless frequencies. IEEE 802.11
is the most frequently used protocol. This protocol braces the wireless networking applications.
Reason for selection of device and components
The main reason for the selection of the device and the components is to allow the user to
share files and information between the different user. The NIC card of the computer is used for
connecting the Ethernet cable and it has a unique hardware address for identifying the computer.
The speed of the interface card is needed to be 1000 Mbps such that it can meet the future needs
of the user. Router is used for connecting the internal network of the organization with the
internet service provider (Salmond 2019). Layer 3 switch are used for the management of the
distribution of the network and it is configured as VTP server such that the VLAN information
are automatically distributed with the VTP client. The wireless access point is of 300N such that
it has a wider coverage area and better performance.
NETWORK DESIGN AND TROUBLESHOOTING
range of IP address for the four departments (Betzel et al. 2016). Another interface is needed for
the wireless network and connect the wireless access point for providing wireless service to the
users. Routers are responsible for transferring data from one device to the other. The data are
sent in the form of packets. The determination of the destination of the packet delivery is done by
the router, which reads the packets to route the information to a specific destination. The network
is also provided with switches which ensures the proper flow of information within the network.
Network hubs are present to connect numerous networks and make them act as a one (Gal et al.
2017). Network hub, like the switches and the routers, broadcasts information throughout the
connection instead of a particular device. Apart from these, there are wireless access points.
These points helps in routing data like routers with the help of wireless frequencies. IEEE 802.11
is the most frequently used protocol. This protocol braces the wireless networking applications.
Reason for selection of device and components
The main reason for the selection of the device and the components is to allow the user to
share files and information between the different user. The NIC card of the computer is used for
connecting the Ethernet cable and it has a unique hardware address for identifying the computer.
The speed of the interface card is needed to be 1000 Mbps such that it can meet the future needs
of the user. Router is used for connecting the internal network of the organization with the
internet service provider (Salmond 2019). Layer 3 switch are used for the management of the
distribution of the network and it is configured as VTP server such that the VLAN information
are automatically distributed with the VTP client. The wireless access point is of 300N such that
it has a wider coverage area and better performance.

5
NETWORK DESIGN AND TROUBLESHOOTING
Current problems in the network
The existing wired network connection had few disadvantages. Firstly, the wired
connections has to be fixed. Relocating is very inconvenient as this include extension of the wire,
requirement of new ports, and many other stuffs. Thus designing of a wireless network will
result in easy relocation of the student. Installation process for a wired network system can be
complex as it needs several components to be set up first. The installation process of the network
can be lengthy depending upon the requirements of the infrastructure (Vriend et al. 2019.).
Maintenance of the network can be expensive. Smaller networks does not require any server. As
the network grows, it adds more system to it, and it needs a proper server to keep a track of the
activity. The maintenance is expensive as an IT professional may be needed for the controlling
the process. Moreover, the wires are the main disadvantage of the wired network. With the
increase in systems in a network, the connectivity has to be increased, with more LAN cables it
becomes very difficult to maintain them and they look clumsy (Margi, Alves and Sepulveda
2017). A wireless network can be a very helpful in this scenario, as the students may access the
network with every possible convenient way.
Evaluation of different technology and protocols
The most common internet protocol in use is the TCP/IP. It stands for Transmission
Control Protocol/ Internet Protocol. It is a stream protocol. The client and the server negotiated.
The data transfer occurs between these two end points, without a failure. The protocol is thus
known as the lossless protocol. It is also known as peer to peer protocol. The TCP/IP layer is
utilized for sending emails. The application layer firstly collects the email and built a connection
with the server (Morales et al. 2017). The hostname is resolved by the DNS and the packets from
NETWORK DESIGN AND TROUBLESHOOTING
Current problems in the network
The existing wired network connection had few disadvantages. Firstly, the wired
connections has to be fixed. Relocating is very inconvenient as this include extension of the wire,
requirement of new ports, and many other stuffs. Thus designing of a wireless network will
result in easy relocation of the student. Installation process for a wired network system can be
complex as it needs several components to be set up first. The installation process of the network
can be lengthy depending upon the requirements of the infrastructure (Vriend et al. 2019.).
Maintenance of the network can be expensive. Smaller networks does not require any server. As
the network grows, it adds more system to it, and it needs a proper server to keep a track of the
activity. The maintenance is expensive as an IT professional may be needed for the controlling
the process. Moreover, the wires are the main disadvantage of the wired network. With the
increase in systems in a network, the connectivity has to be increased, with more LAN cables it
becomes very difficult to maintain them and they look clumsy (Margi, Alves and Sepulveda
2017). A wireless network can be a very helpful in this scenario, as the students may access the
network with every possible convenient way.
Evaluation of different technology and protocols
The most common internet protocol in use is the TCP/IP. It stands for Transmission
Control Protocol/ Internet Protocol. It is a stream protocol. The client and the server negotiated.
The data transfer occurs between these two end points, without a failure. The protocol is thus
known as the lossless protocol. It is also known as peer to peer protocol. The TCP/IP layer is
utilized for sending emails. The application layer firstly collects the email and built a connection
with the server (Morales et al. 2017). The hostname is resolved by the DNS and the packets from
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK DESIGN AND TROUBLESHOOTING
the transport layer is forwarded by the network layer. The data link layer allows communication
to one another. The bits are moved back to the destination by the physical layer.
Presentation layer is used for the conversion of the incoming and the outgoing messages.
Conversion of encrypted text to clear text and vice versa takes place in this layer.
The session layer is used for the packaging of the data and the error checking before
packaging of data. For most of the application TCP and UDP is used (Vangulick et al. 2017).
The layer used for the packaging of data is the transport layer. Delivering the package for
checking the error is also done in this layer.
The layer responsible for handling the routing and addressing of the data to the correct
address is the network layer. Internet Protocol is used in the network layer.
The data link layer establishes the physical link and framing the packets properly inside a
network (Robson 2018).
The second most used protocol is the HTTP. This protocol is used for transmitting data
from the World Wide Web. The Hyper Text Transfer Protocol is the protocol to transmit HTML.
Thirdly, the File Transfer protocol is mostly used protocol. The computers that are
connected in the TCP/IP network can transmit files among them. The technologies used in the
network designing are wireless LAN, Wireless Access points, cloud based control and one
premise control. The wireless LAN makes use of the radio frequency technology (Nedić,
Olshevsky and Rabbat 2018). This is a technology which includes a frequency that is within the
electromagnetic spectrum. This electromagnetic spectrum is associated with the radio wave
propagation. The WLAN (Wireless LAN) allows the users to connect with the network under a
particular coverage area. The wireless access points are integrated into the routers. Ethernet
connection is used to connect a standalone wireless access point to the router so that it can get
NETWORK DESIGN AND TROUBLESHOOTING
the transport layer is forwarded by the network layer. The data link layer allows communication
to one another. The bits are moved back to the destination by the physical layer.
Presentation layer is used for the conversion of the incoming and the outgoing messages.
Conversion of encrypted text to clear text and vice versa takes place in this layer.
The session layer is used for the packaging of the data and the error checking before
packaging of data. For most of the application TCP and UDP is used (Vangulick et al. 2017).
The layer used for the packaging of data is the transport layer. Delivering the package for
checking the error is also done in this layer.
The layer responsible for handling the routing and addressing of the data to the correct
address is the network layer. Internet Protocol is used in the network layer.
The data link layer establishes the physical link and framing the packets properly inside a
network (Robson 2018).
The second most used protocol is the HTTP. This protocol is used for transmitting data
from the World Wide Web. The Hyper Text Transfer Protocol is the protocol to transmit HTML.
Thirdly, the File Transfer protocol is mostly used protocol. The computers that are
connected in the TCP/IP network can transmit files among them. The technologies used in the
network designing are wireless LAN, Wireless Access points, cloud based control and one
premise control. The wireless LAN makes use of the radio frequency technology (Nedić,
Olshevsky and Rabbat 2018). This is a technology which includes a frequency that is within the
electromagnetic spectrum. This electromagnetic spectrum is associated with the radio wave
propagation. The WLAN (Wireless LAN) allows the users to connect with the network under a
particular coverage area. The wireless access points are integrated into the routers. Ethernet
connection is used to connect a standalone wireless access point to the router so that it can get
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK DESIGN AND TROUBLESHOOTING
connected to the network system. The other devices are can access to this network with the help
of the radio frequency method itself (Quevedo et al. 2017). The cloud allows the users to
download and install files in the chosen device with the help of internet. The user can later access
them from any other device as and when required with the help of internet. The files can be
edited later on in the cloud.
Network Subnet Plan
Major Network: 192.168.168.0/24
Available IP addresses in major network: 254
Number of IP addresses needed: 140
Available IP addresses in allocated subnets: 170
About 70% of available major network address space is used
About 82% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Departm
ent 1
49 62 192.168.168
.64
/26 255.255.255
.192
192.168.168
.65 -
192.168.168
.126
192.168.168
.127
Departm
ent 2
19 30 192.168.168
.128
/27 255.255.255
.224
192.168.168
.129 -
192.168.168
192.168.168
.159
NETWORK DESIGN AND TROUBLESHOOTING
connected to the network system. The other devices are can access to this network with the help
of the radio frequency method itself (Quevedo et al. 2017). The cloud allows the users to
download and install files in the chosen device with the help of internet. The user can later access
them from any other device as and when required with the help of internet. The files can be
edited later on in the cloud.
Network Subnet Plan
Major Network: 192.168.168.0/24
Available IP addresses in major network: 254
Number of IP addresses needed: 140
Available IP addresses in allocated subnets: 170
About 70% of available major network address space is used
About 82% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Departm
ent 1
49 62 192.168.168
.64
/26 255.255.255
.192
192.168.168
.65 -
192.168.168
.126
192.168.168
.127
Departm
ent 2
19 30 192.168.168
.128
/27 255.255.255
.224
192.168.168
.129 -
192.168.168
192.168.168
.159
8
NETWORK DESIGN AND TROUBLESHOOTING
.158
Departm
ent 3
12 14 192.168.168
.160
/28 255.255.255
.240
192.168.168
.161 -
192.168.168
.174
192.168.168
.175
Departm
ent 4
59 62 192.168.168
.0
/26 255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Wireless 100 126 10.11.12.0 /25 255.255.255
.128
10.11.12.1 -
10.11.12.12
6
10.11.12.12
7
NETWORK DESIGN AND TROUBLESHOOTING
.158
Departm
ent 3
12 14 192.168.168
.160
/28 255.255.255
.240
192.168.168
.161 -
192.168.168
.174
192.168.168
.175
Departm
ent 4
59 62 192.168.168
.0
/26 255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Wireless 100 126 10.11.12.0 /25 255.255.255
.128
10.11.12.1 -
10.11.12.12
6
10.11.12.12
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
NETWORK DESIGN AND TROUBLESHOOTING
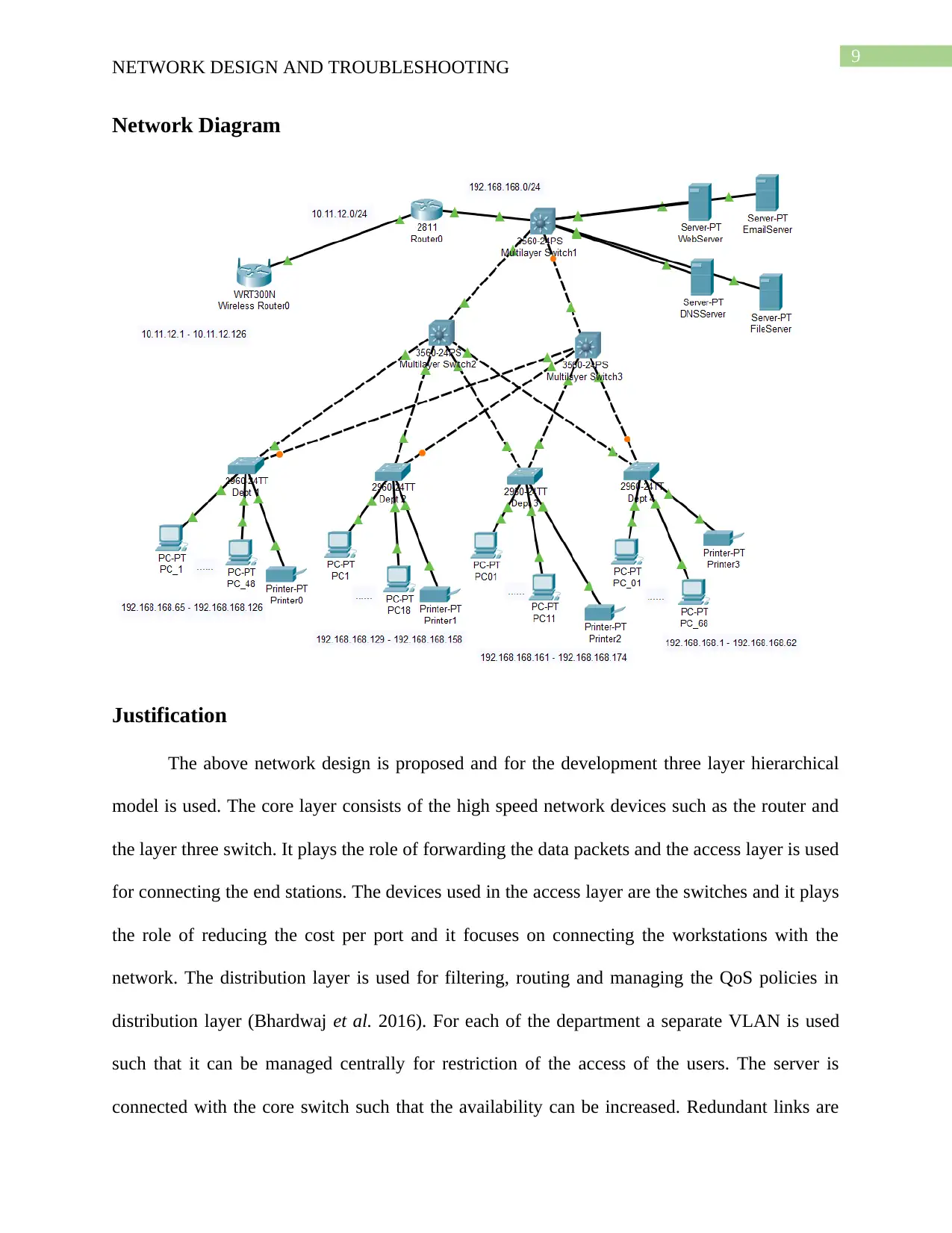
Network Diagram
Justification
The above network design is proposed and for the development three layer hierarchical
model is used. The core layer consists of the high speed network devices such as the router and
the layer three switch. It plays the role of forwarding the data packets and the access layer is used
for connecting the end stations. The devices used in the access layer are the switches and it plays
the role of reducing the cost per port and it focuses on connecting the workstations with the
network. The distribution layer is used for filtering, routing and managing the QoS policies in
distribution layer (Bhardwaj et al. 2016). For each of the department a separate VLAN is used
such that it can be managed centrally for restriction of the access of the users. The server is
connected with the core switch such that the availability can be increased. Redundant links are
NETWORK DESIGN AND TROUBLESHOOTING
Network Diagram
Justification
The above network design is proposed and for the development three layer hierarchical
model is used. The core layer consists of the high speed network devices such as the router and
the layer three switch. It plays the role of forwarding the data packets and the access layer is used
for connecting the end stations. The devices used in the access layer are the switches and it plays
the role of reducing the cost per port and it focuses on connecting the workstations with the
network. The distribution layer is used for filtering, routing and managing the QoS policies in
distribution layer (Bhardwaj et al. 2016). For each of the department a separate VLAN is used
such that it can be managed centrally for restriction of the access of the users. The server is
connected with the core switch such that the availability can be increased. Redundant links are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK DESIGN AND TROUBLESHOOTING
used for management of the access and eliminate congestion, packet loss and jitter in the
network.
Security precaution and Configuration
Before focusing on the technical part, taking physical precautions are essential. The
Server should be located in a safe place, where it can be locked securely. Generally, most
hardware firewalls are located in the broadband router and can prevent the invading threats such
as downloading any corrupt file from the internet (Han et al. 2015). But they are less productive
at preventing outgoing threats. Installed software should be updated, after installation, updates
for protecting against the computer viruses be it latest or usual is received periodically. Sharing
passwords should be avoided until it’s a need-to-know case, and changing them every two
months is an efficient way to prevent getting their way into the wrong hands (Stergiopoulos et
al. 2018). The settings of default log-in should be changed by making it disabled for default log-
in.
Wireless Network have greater convenience but also prone to risks. Here, risk means
easy access of hackers into the system network. Hence, for protecting the network, best
encryption system should be owned such as, WPA2 (Chin et al. 2015). A security professional
can inform about the latest unified threat management and can also spot the threats that might
have got overlooked hence, consulting a security professional is an effective option.
Basically, to fix or repair any sort of failed product the process of troubleshooting is used.
To make the process or the system fully functional or operational, troubleshooting is used as it is
a logical and systematic search process. It does elimination of potential causes of any problem.
In general, identifying and diagnosing of the problem is known as troubleshooting (Samdanis,
Costa-Perez and Sciancalepore 2016). It identifies the symptoms of malfunction and provide
NETWORK DESIGN AND TROUBLESHOOTING
used for management of the access and eliminate congestion, packet loss and jitter in the
network.
Security precaution and Configuration
Before focusing on the technical part, taking physical precautions are essential. The
Server should be located in a safe place, where it can be locked securely. Generally, most
hardware firewalls are located in the broadband router and can prevent the invading threats such
as downloading any corrupt file from the internet (Han et al. 2015). But they are less productive
at preventing outgoing threats. Installed software should be updated, after installation, updates
for protecting against the computer viruses be it latest or usual is received periodically. Sharing
passwords should be avoided until it’s a need-to-know case, and changing them every two
months is an efficient way to prevent getting their way into the wrong hands (Stergiopoulos et
al. 2018). The settings of default log-in should be changed by making it disabled for default log-
in.
Wireless Network have greater convenience but also prone to risks. Here, risk means
easy access of hackers into the system network. Hence, for protecting the network, best
encryption system should be owned such as, WPA2 (Chin et al. 2015). A security professional
can inform about the latest unified threat management and can also spot the threats that might
have got overlooked hence, consulting a security professional is an effective option.
Basically, to fix or repair any sort of failed product the process of troubleshooting is used.
To make the process or the system fully functional or operational, troubleshooting is used as it is
a logical and systematic search process. It does elimination of potential causes of any problem.
In general, identifying and diagnosing of the problem is known as troubleshooting (Samdanis,
Costa-Perez and Sciancalepore 2016). It identifies the symptoms of malfunction and provide

11
NETWORK DESIGN AND TROUBLESHOOTING
remedy to these symptoms. Troubleshooting primarily focuses on the changes that are very
recent to the system or the surrounding in which it is existing.
Testing of the network
The security configuration and the protocols are needed to be tested such that an
unknown user cannot have access of the network. Network monitoring tool can be used for
gathering data regarding the network and the network is needed to be pinged from different
location for getting the network response. The available bandwidth is also needed to be identified
a penetration testing can be made in the network for gathering data and vulnerability of the
network devices (Kwasinski and Kwasinski 2015). The parameters of QoS are needed to be used
for measuring the packet loss, latency and jitter. Network performance monitoring tool can be
used for automating the network testing and eliminate the issues with the current network.
Computerized troubleshooting cables can be used for efficient services to the users, there
are a few computerized troubleshooting services such as Mac’s server which was previously
known as prim FAQs, shows the top 10 solutions with the highest probability of fixing the
problem immediately. The additional questions can be answered by the qualified technicians to
advance through the troubleshooting procedure with each step narrowing the list of probable
solutions to fix the problem (Sousa et al. 2016). Network troubleshooting involves, determining
the problems for resolving, establishing the internet connection of a computer. Configuring a
router, its switch or any device for network management is important. Updating the firmware
devices or router switches after the installation of Wi-Fi devices then removing the viruses is
also involved. The entire work of Network troubleshooting can be automated or can be done
manually and for automated task network diagnostic software is needed for network
management.
NETWORK DESIGN AND TROUBLESHOOTING
remedy to these symptoms. Troubleshooting primarily focuses on the changes that are very
recent to the system or the surrounding in which it is existing.
Testing of the network
The security configuration and the protocols are needed to be tested such that an
unknown user cannot have access of the network. Network monitoring tool can be used for
gathering data regarding the network and the network is needed to be pinged from different
location for getting the network response. The available bandwidth is also needed to be identified
a penetration testing can be made in the network for gathering data and vulnerability of the
network devices (Kwasinski and Kwasinski 2015). The parameters of QoS are needed to be used
for measuring the packet loss, latency and jitter. Network performance monitoring tool can be
used for automating the network testing and eliminate the issues with the current network.
Computerized troubleshooting cables can be used for efficient services to the users, there
are a few computerized troubleshooting services such as Mac’s server which was previously
known as prim FAQs, shows the top 10 solutions with the highest probability of fixing the
problem immediately. The additional questions can be answered by the qualified technicians to
advance through the troubleshooting procedure with each step narrowing the list of probable
solutions to fix the problem (Sousa et al. 2016). Network troubleshooting involves, determining
the problems for resolving, establishing the internet connection of a computer. Configuring a
router, its switch or any device for network management is important. Updating the firmware
devices or router switches after the installation of Wi-Fi devices then removing the viruses is
also involved. The entire work of Network troubleshooting can be automated or can be done
manually and for automated task network diagnostic software is needed for network
management.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




