IT Networking Design and Implementation for Infocollege.edu
VerifiedAdded on 2020/05/08
|31
|7490
|73
Report
AI Summary
This report details the design and implementation of an IT network for Infocollege.edu, focusing on creating a robust LAN solution for the head office and its branches. The report begins with an examination of network principles, protocols, and the impact of network topology, including bandwidth requirements for various applications like email, web browsing, and video streaming. It then delves into the operating principles of networking devices, such as layer 3 switches and different server types, along with the interdependency of workstation hardware and network software. The core of the report covers the design of an efficient network system, including the selection of LAN technology, topology, and device justification. It provides a maintenance schedule and a test plan for the network. The report also addresses the implementation of the designed network, documentation, and analysis of test results, as well as the network's ability to scale and communicate with other devices. The report concludes with a comprehensive overview of the network design and implementation for Infocollege.edu.

Running head: IT NETWORKING DESIGNING
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT NETWORKING DESIGNING
Executive Summary
The report is set up for outlining and designing a system utilizing different system interface that
are associated with routers and switches. A layer three switch is utilized for planning the system
and the Pc connected in different department of the head office of Infocolllege.edu College. The
LAN solution is proposed according to the requirement of the organization and different servers
are installed in the network and allowed access from departments for increasing the productivity
of the network. The web server is designed with HTTP for serving the customer clients with the
pages and react to their demand. A firewall is arranged in the system and the router is configured
with access control list for blocking the different departments to communicate with each other
and increase the security of the network.
IT NETWORKING DESIGNING
Executive Summary
The report is set up for outlining and designing a system utilizing different system interface that
are associated with routers and switches. A layer three switch is utilized for planning the system
and the Pc connected in different department of the head office of Infocolllege.edu College. The
LAN solution is proposed according to the requirement of the organization and different servers
are installed in the network and allowed access from departments for increasing the productivity
of the network. The web server is designed with HTTP for serving the customer clients with the
pages and react to their demand. A firewall is arranged in the system and the router is configured
with access control list for blocking the different departments to communicate with each other
and increase the security of the network.

2
IT NETWORKING DESIGNING
Table of Contents
1. Examination of the different network principles and protocols......................................4
1.1. Introduction...............................................................................................................4
1.2. Benefits and constraints of different types of network and standards......................4
1.3. Impact of the network topology................................................................................5
1.4. Communication and bandwidth requirement............................................................6
2. Network Device and operation........................................................................................9
2.1. Operating principles of networking devices and types of servers............................9
2.2. Inter dependency of workstation hardware and relevant network software...........10
3. Designing efficient network systems.............................................................................11
3.1. Design of the network system.................................................................................11
3.1.1. Description of the LAN technology and topology used in the network..........11
3.2. Testing and evaluation of the design......................................................................12
3.2.1. Description and justification of the device used in the network......................12
3.2.2. Suggestion and maintenance schedule for supporting the network system.....13
3.2.3. Production of test plan.....................................................................................14
4. Implementation of the test and diagnosis of the networked system..............................16
4.1. Implementation of the designed network based on the network specification.......16
4.2. Documentation and analysis of the test result........................................................17
IT NETWORKING DESIGNING
Table of Contents
1. Examination of the different network principles and protocols......................................4
1.1. Introduction...............................................................................................................4
1.2. Benefits and constraints of different types of network and standards......................4
1.3. Impact of the network topology................................................................................5
1.4. Communication and bandwidth requirement............................................................6
2. Network Device and operation........................................................................................9
2.1. Operating principles of networking devices and types of servers............................9
2.2. Inter dependency of workstation hardware and relevant network software...........10
3. Designing efficient network systems.............................................................................11
3.1. Design of the network system.................................................................................11
3.1.1. Description of the LAN technology and topology used in the network..........11
3.2. Testing and evaluation of the design......................................................................12
3.2.1. Description and justification of the device used in the network......................12
3.2.2. Suggestion and maintenance schedule for supporting the network system.....13
3.2.3. Production of test plan.....................................................................................14
4. Implementation of the test and diagnosis of the networked system..............................16
4.1. Implementation of the designed network based on the network specification.......16
4.2. Documentation and analysis of the test result........................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT NETWORKING DESIGNING
4.3. Investigation of the ability of the network for growth and communicating with the
other devices..............................................................................................................................17
5. Conclusion.....................................................................................................................19
References..........................................................................................................................21
Appendices........................................................................................................................26
Configuration of the layer 3 switch installed in the network.........................................26
IT NETWORKING DESIGNING
4.3. Investigation of the ability of the network for growth and communicating with the
other devices..............................................................................................................................17
5. Conclusion.....................................................................................................................19
References..........................................................................................................................21
Appendices........................................................................................................................26
Configuration of the layer 3 switch installed in the network.........................................26
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT NETWORKING DESIGNING
1. Examination of the different network principles and protocols
1.1. Introduction
The report is prepared for infocollege.edu to design the network with a complete LAN
technology and connect the other branches of the college located in Birmingham, Liverpool,
Manchester and Glasgow. The network is designed for the central head office located in London
such that it can communicate with the other branches and manage the information of the college
from a central point. The LAN solution is prepared with the private IP address of 192.168.5.0/ 24
and it is made flexible to adopt the future requirement of the college to grow its network
according to the changes in the requirement of the college. The network solution is designed with
the application of new technologies and different subnets are used for the different departments
for reducing the wastage of the IP address and increasing the efficiency of the proposed network
solution (Witten et al. 2016). An IP addressing plan is created for the network solution and
attached with the report for future assistance and configure the network device according to the
addressing plan. Some extra bits of address are reserved for each of the department of the college
such that the network can accommodate the future growth of the college and the servers are
configured according to the requirement of the college to handle emails and file request from the
college.
1.2. Benefits and constraints of different types of network and standards
The selection of the network topology is important for connecting the different
department in the organization and the structure of the network is used for defining the
communication standards maintained in the proposed network solution. There are advantages
and disadvantages associated with the implementation of the different network topology and
IT NETWORKING DESIGNING
1. Examination of the different network principles and protocols
1.1. Introduction
The report is prepared for infocollege.edu to design the network with a complete LAN
technology and connect the other branches of the college located in Birmingham, Liverpool,
Manchester and Glasgow. The network is designed for the central head office located in London
such that it can communicate with the other branches and manage the information of the college
from a central point. The LAN solution is prepared with the private IP address of 192.168.5.0/ 24
and it is made flexible to adopt the future requirement of the college to grow its network
according to the changes in the requirement of the college. The network solution is designed with
the application of new technologies and different subnets are used for the different departments
for reducing the wastage of the IP address and increasing the efficiency of the proposed network
solution (Witten et al. 2016). An IP addressing plan is created for the network solution and
attached with the report for future assistance and configure the network device according to the
addressing plan. Some extra bits of address are reserved for each of the department of the college
such that the network can accommodate the future growth of the college and the servers are
configured according to the requirement of the college to handle emails and file request from the
college.
1.2. Benefits and constraints of different types of network and standards
The selection of the network topology is important for connecting the different
department in the organization and the structure of the network is used for defining the
communication standards maintained in the proposed network solution. There are advantages
and disadvantages associated with the implementation of the different network topology and

5
IT NETWORKING DESIGNING
each of the elements used in the designing of the network should be listed for making a physical
and logical framework of the network. There are different types of network such as LAN, WAN,
WLAN, MAN, SAN, CAN, PAN and the each have its application in differ5ent field of the
network.
The local area network is used for connecting the device in the network located at a short
distance and it may be home, school buildings, office. It is mainly applied in TCP//IP network
and not used as a single subnet for connecting the devices in the network. The wide area
network is used as a collection of LANs where the router maintains the records of the LANs used
in the network and the WAN spreads over a larger distance than the LAN and a router is used for
inter connecting the devices installed in the network (Sahhaf et al. 2015). In wide area network
the network can be segmented and different subnets and IP address can be used on different
interface of the devices. WAN uses different technology such as frame relay, ATM, etc. for
establishment of a secure connection between the nodes. Moreover there are other types of
network such as metropolitan area network and campus area network that are used for spanning
multiple LANs and connecting different data centers with high speed connection.
1.3. Impact of the network topology
The selection of the right network topology is important for increasing the efficiency of
communication between the nodes connected in the network. The network cabling plan is
important for accommodation of the growing needs of the organization and reducing the
congestion in the network traffic. The network used for head office in London should be fully
connected with the other branches and offices such that the resources of the private college is
available to the network administrator (Rezha and Shin 2014). The cost of the network,
scalability and availability is considered before selection of the network topology and
IT NETWORKING DESIGNING
each of the elements used in the designing of the network should be listed for making a physical
and logical framework of the network. There are different types of network such as LAN, WAN,
WLAN, MAN, SAN, CAN, PAN and the each have its application in differ5ent field of the
network.
The local area network is used for connecting the device in the network located at a short
distance and it may be home, school buildings, office. It is mainly applied in TCP//IP network
and not used as a single subnet for connecting the devices in the network. The wide area
network is used as a collection of LANs where the router maintains the records of the LANs used
in the network and the WAN spreads over a larger distance than the LAN and a router is used for
inter connecting the devices installed in the network (Sahhaf et al. 2015). In wide area network
the network can be segmented and different subnets and IP address can be used on different
interface of the devices. WAN uses different technology such as frame relay, ATM, etc. for
establishment of a secure connection between the nodes. Moreover there are other types of
network such as metropolitan area network and campus area network that are used for spanning
multiple LANs and connecting different data centers with high speed connection.
1.3. Impact of the network topology
The selection of the right network topology is important for increasing the efficiency of
communication between the nodes connected in the network. The network cabling plan is
important for accommodation of the growing needs of the organization and reducing the
congestion in the network traffic. The network used for head office in London should be fully
connected with the other branches and offices such that the resources of the private college is
available to the network administrator (Rezha and Shin 2014). The cost of the network,
scalability and availability is considered before selection of the network topology and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT NETWORKING DESIGNING
implementation in the head office LAN solution. For securing the different components in the
network privacy should be maintained and proactive routing is configured for communicating
with the other branches and offices of the college. The advantage that can be gained with the
configuration of the router with proactive routing is that the waiting time is less but there is a
disadvantage that with the increase in the traffic in the network the CPU load increases. Thus the
increase in the congestion can decrease the performance of the organization and impact the
growth of the organization (Sadique and Shah 2016). The transmission links used for
interconnecting the devices should be up and a core components of the network such as the
servers and the routers should be kept out of reach from the staffs for reducing the risk of
physical assault.
1.4. Communication and bandwidth requirement
The capacity of the network should be estimated for the estimation of the capacity of the
channel and the bandwidth requirement. The data transfer rate also depends on the bandwidth
requirement and the user using the network for transmission of the data packets. The latency of
the data should be noted for transmission of the queued traffic and the lags in the network should
be reduced for increasing the efficiency of the network (Pan 2016). The communication service
enabled in the network is listed along with the bandwidth required for running the service
efficiently.
Application Required Bandwidth Note
Email 10 – 100 Kbps The email are asynchronous
and it can tolerate the latency
in the network. The
bandwidth usage are
IT NETWORKING DESIGNING
implementation in the head office LAN solution. For securing the different components in the
network privacy should be maintained and proactive routing is configured for communicating
with the other branches and offices of the college. The advantage that can be gained with the
configuration of the router with proactive routing is that the waiting time is less but there is a
disadvantage that with the increase in the traffic in the network the CPU load increases. Thus the
increase in the congestion can decrease the performance of the organization and impact the
growth of the organization (Sadique and Shah 2016). The transmission links used for
interconnecting the devices should be up and a core components of the network such as the
servers and the routers should be kept out of reach from the staffs for reducing the risk of
physical assault.
1.4. Communication and bandwidth requirement
The capacity of the network should be estimated for the estimation of the capacity of the
channel and the bandwidth requirement. The data transfer rate also depends on the bandwidth
requirement and the user using the network for transmission of the data packets. The latency of
the data should be noted for transmission of the queued traffic and the lags in the network should
be reduced for increasing the efficiency of the network (Pan 2016). The communication service
enabled in the network is listed along with the bandwidth required for running the service
efficiently.
Application Required Bandwidth Note
Email 10 – 100 Kbps The email are asynchronous
and it can tolerate the latency
in the network. The
bandwidth usage are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT NETWORKING DESIGNING
significant for attachment of
the large doc files, spams,
viruses.
Messaging < 10 Kbps The messaging traffic are
infrequent and thus it can
tolerate high latency in the
network.
Web Browsing 64 – 100+ Kbps It is used for requesting of
data and asynchronous
communication is used and a
fair lag can be tolerated in the
network. The bandwidth
requirement increases with
the increase in the request
from the users for getting
more data, long downloads,
etc.
Audio Streaming 96 -160 Kbps The streaming service
requires a large bandwidth
and a large buffer can be
introduced for reducing the
latency of bandwidth. If
extended period of lag is
IT NETWORKING DESIGNING
significant for attachment of
the large doc files, spams,
viruses.
Messaging < 10 Kbps The messaging traffic are
infrequent and thus it can
tolerate high latency in the
network.
Web Browsing 64 – 100+ Kbps It is used for requesting of
data and asynchronous
communication is used and a
fair lag can be tolerated in the
network. The bandwidth
requirement increases with
the increase in the request
from the users for getting
more data, long downloads,
etc.
Audio Streaming 96 -160 Kbps The streaming service
requires a large bandwidth
and a large buffer can be
introduced for reducing the
latency of bandwidth. If
extended period of lag is
8
IT NETWORKING DESIGNING
faced in the network the
streaming can fail and it can
occur outrage of the session.
VOIP 24 – 100+ Kbps It requires constant
bandwidth and no lag in the
network can be tolerated
because it can cause call drop
and miscommunication may
happen.
Video Streaming 96 – 200+ Kbps It is similar with audio
streaming and the latency can
be avoided by using large
buffer size and high
throughput is required for the
working of the video
streaming properly.
File Sharing 0 – infinity Mbps For setting up a peer to peer
network the any amount of
latency can be tolerated and
the throughput can be used
for transmission of the data to
the clients connected in the
network.
IT NETWORKING DESIGNING
faced in the network the
streaming can fail and it can
occur outrage of the session.
VOIP 24 – 100+ Kbps It requires constant
bandwidth and no lag in the
network can be tolerated
because it can cause call drop
and miscommunication may
happen.
Video Streaming 96 – 200+ Kbps It is similar with audio
streaming and the latency can
be avoided by using large
buffer size and high
throughput is required for the
working of the video
streaming properly.
File Sharing 0 – infinity Mbps For setting up a peer to peer
network the any amount of
latency can be tolerated and
the throughput can be used
for transmission of the data to
the clients connected in the
network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT NETWORKING DESIGNING
Thus for the estimation of the bandwidth necessary for the communication the expected
number of users are multiplied by the application used by them and calculate the total bandwidth.
2. Network Device and operation
2.1. Operating principles of networking devices and types of servers
The different networking connected in the network operates on different principles and
different medium can be used for the establishment of the connection between the nodes installed
in the network. The devices uses the different layers of the OSI model and the devices are
categorized into five different categories for transmission of the data packets in the network. The
categories are gateway, routing or layer three switch, layer 2 switch or bridge, hub or repeater
and passive hubs (Quinn and Guichard 2014). The switch is used as the central point for
connecting the different devices and the switch are of different types such as the layer 3 and
layer 2 switch. Several number of network cables can be plugged from different device for
communicating with each other. The business policy of the organization is configured in the
network for restricting the departments to communicate with the other department (Lu et al.
2016). The repeater are used for long distance communication and regeneration of the signal for
reducing the loss of data in the network. Bridge or layer 2 switch is used for checking the
destination address and forwarding the data packets in the destination network. The traffic in the
network can be filtered by creation of different vlans for the different departments and blocking
the vlan to communicate with the departments (Lu, Yu and Yao 2014). The layer three switch is
configured with access control list according to the business policy for meeting the requirement
of the organization and maintaining a smooth transition in the network. Different types of servers
are usd in the network such as the email, web, dns and file server and the servers are connected
IT NETWORKING DESIGNING
Thus for the estimation of the bandwidth necessary for the communication the expected
number of users are multiplied by the application used by them and calculate the total bandwidth.
2. Network Device and operation
2.1. Operating principles of networking devices and types of servers
The different networking connected in the network operates on different principles and
different medium can be used for the establishment of the connection between the nodes installed
in the network. The devices uses the different layers of the OSI model and the devices are
categorized into five different categories for transmission of the data packets in the network. The
categories are gateway, routing or layer three switch, layer 2 switch or bridge, hub or repeater
and passive hubs (Quinn and Guichard 2014). The switch is used as the central point for
connecting the different devices and the switch are of different types such as the layer 3 and
layer 2 switch. Several number of network cables can be plugged from different device for
communicating with each other. The business policy of the organization is configured in the
network for restricting the departments to communicate with the other department (Lu et al.
2016). The repeater are used for long distance communication and regeneration of the signal for
reducing the loss of data in the network. Bridge or layer 2 switch is used for checking the
destination address and forwarding the data packets in the destination network. The traffic in the
network can be filtered by creation of different vlans for the different departments and blocking
the vlan to communicate with the departments (Lu, Yu and Yao 2014). The layer three switch is
configured with access control list according to the business policy for meeting the requirement
of the organization and maintaining a smooth transition in the network. Different types of servers
are usd in the network such as the email, web, dns and file server and the servers are connected
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT NETWORKING DESIGNING
in a different vlan and allowed access to all the departments for increasing the performance of
the network solution.
2.2. Inter dependency of workstation hardware and relevant network software
The hardware of the workstation used in the organization is interdependent with the
application and network software installed in the machines. Some of the network software are
designed for handling multiple processing and consumes large amount of memory and thus the
workstation hardware should be compatible to run different application software. The traditional
workstation uses PCI 32 bit version and it may be insufficient for handling huge number of
request and wider bus with high data transmission rate should be installed (Oinas-Kukkonen
2013). The network server used in the network are installed with a network operating system for
the management of the entire network and respond to the request coming from different clients in
the network (Larsson et al. 2014). If the load of the network increases and the hardware should
support virtualization for handling the request and reducing the load on the network. The
virtualization of the network server can increase the efficiency of the network and reduce the
waiting time of the user and thus improving the overall production of the organization
(Mehrpouyan et al. 2014). The interdependency should be identified during the design phase and
the security measures should be applied for the improvement of the organizational framework.
The security measures should be applied and the network should be tested for ensuring that the
unforeseen vulnerabilities in the network are identified (Oliviero and Woodward 2014). Training
should be given to the users such that the staffs does not installs unwanted applications in the
workstation because it may open path for the hackers to intrude into the organizational network
and hack the organizational data.
IT NETWORKING DESIGNING
in a different vlan and allowed access to all the departments for increasing the performance of
the network solution.
2.2. Inter dependency of workstation hardware and relevant network software
The hardware of the workstation used in the organization is interdependent with the
application and network software installed in the machines. Some of the network software are
designed for handling multiple processing and consumes large amount of memory and thus the
workstation hardware should be compatible to run different application software. The traditional
workstation uses PCI 32 bit version and it may be insufficient for handling huge number of
request and wider bus with high data transmission rate should be installed (Oinas-Kukkonen
2013). The network server used in the network are installed with a network operating system for
the management of the entire network and respond to the request coming from different clients in
the network (Larsson et al. 2014). If the load of the network increases and the hardware should
support virtualization for handling the request and reducing the load on the network. The
virtualization of the network server can increase the efficiency of the network and reduce the
waiting time of the user and thus improving the overall production of the organization
(Mehrpouyan et al. 2014). The interdependency should be identified during the design phase and
the security measures should be applied for the improvement of the organizational framework.
The security measures should be applied and the network should be tested for ensuring that the
unforeseen vulnerabilities in the network are identified (Oliviero and Woodward 2014). Training
should be given to the users such that the staffs does not installs unwanted applications in the
workstation because it may open path for the hackers to intrude into the organizational network
and hack the organizational data.
11
IT NETWORKING DESIGNING
3. Designing efficient network systems
3.1. Design of the network system
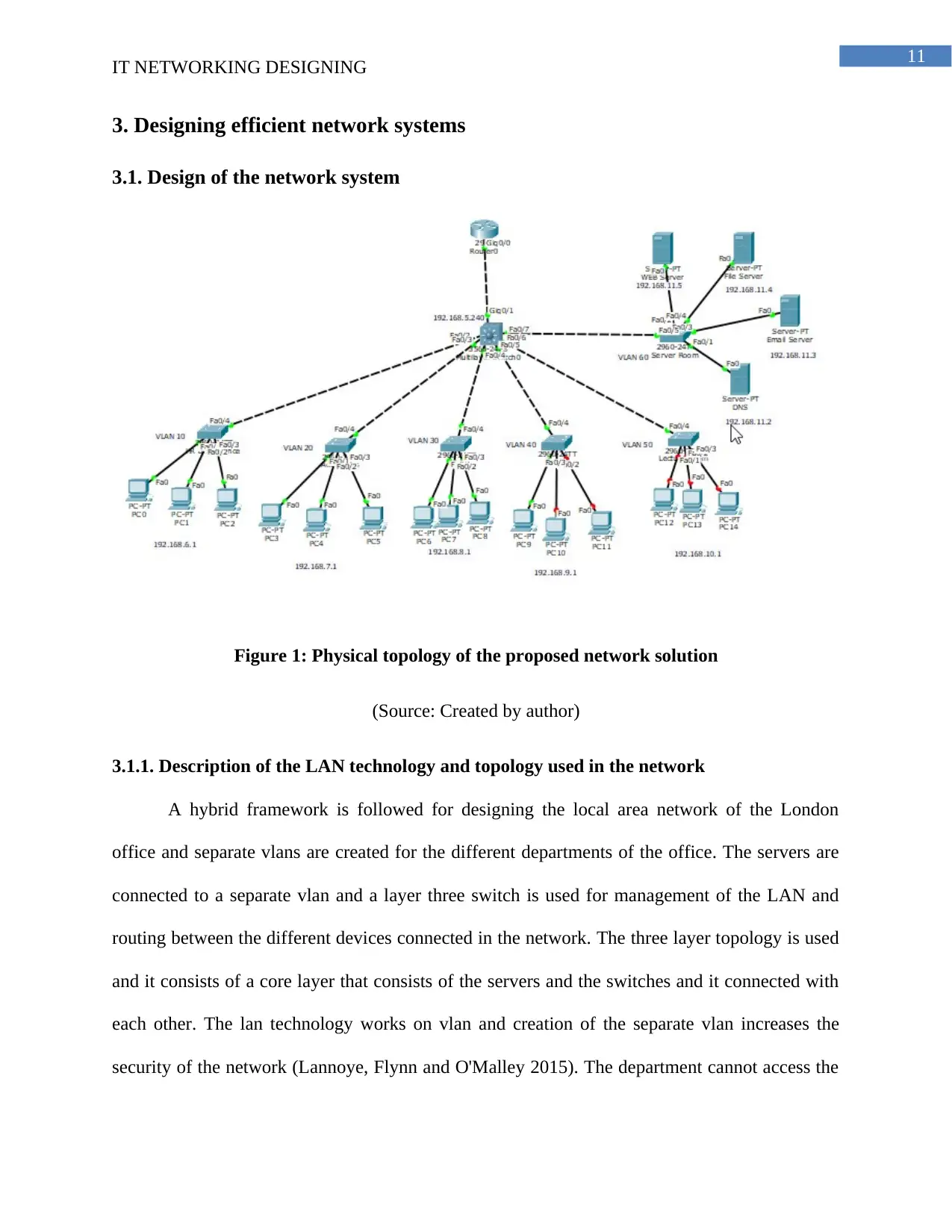
Figure 1: Physical topology of the proposed network solution
(Source: Created by author)
3.1.1. Description of the LAN technology and topology used in the network
A hybrid framework is followed for designing the local area network of the London
office and separate vlans are created for the different departments of the office. The servers are
connected to a separate vlan and a layer three switch is used for management of the LAN and
routing between the different devices connected in the network. The three layer topology is used
and it consists of a core layer that consists of the servers and the switches and it connected with
each other. The lan technology works on vlan and creation of the separate vlan increases the
security of the network (Lannoye, Flynn and O'Malley 2015). The department cannot access the
IT NETWORKING DESIGNING
3. Designing efficient network systems
3.1. Design of the network system
Figure 1: Physical topology of the proposed network solution
(Source: Created by author)
3.1.1. Description of the LAN technology and topology used in the network
A hybrid framework is followed for designing the local area network of the London
office and separate vlans are created for the different departments of the office. The servers are
connected to a separate vlan and a layer three switch is used for management of the LAN and
routing between the different devices connected in the network. The three layer topology is used
and it consists of a core layer that consists of the servers and the switches and it connected with
each other. The lan technology works on vlan and creation of the separate vlan increases the
security of the network (Lannoye, Flynn and O'Malley 2015). The department cannot access the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





