Comprehensive Network Design Report: Talon Textile Fasteners (TTF)
VerifiedAdded on 2020/01/21
|20
|5604
|583
Report
AI Summary
This report outlines a comprehensive network design for Talon Textile Fasteners (TTF), addressing key requirements such as security, speed, reliability, and scalability. The design proposes a Wide Area Network (WAN) with a star architecture connecting multiple offices to the headquarters, utilizing Gigabit Ethernet for its physical and data layers. The report details hardware configurations, including Layer 3 switches, Layer 2 switches, and media converters, along with a diagram illustrating the network layout. It further elaborates on the directory structure, server design (DNS, DHCP, Directory Services, Security and Network Management, Manufacturing application Servers), and security policies, including user documentation and ongoing maintenance support. The network design incorporates redundancy through NIC teaming and a VMware ESX server setup with shared storage, ensuring business continuity. The report also covers cabling, router specifications, and security measures to safeguard the network from unauthorized access. The proposed solution aims to provide a robust, scalable, and secure network infrastructure for TTF's operations.

NETWORK DESIGN 1
Network Design Assignment
Tatum Spencer
Network Design Assignment
Tatum Spencer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK DESIGN 2
Contents
Introduction.................................................................................................................................................3
Assumptions in the Design..........................................................................................................................3
Network Requirements...............................................................................................................................3
Network Design...........................................................................................................................................4
TTF WAN Architecture [1]............................................................................................................................4
Technology..............................................................................................................................................4
Cabling.....................................................................................................................................................4
Security....................................................................................................................................................4
Hardware Configuration [4][6]................................................................................................................4
Diagram...................................................................................................................................................5
Directory Structure [7].................................................................................................................................7
Server Design [4][6].....................................................................................................................................8
TTF HQ.........................................................................................................................................................9
Server Farm Access Layer............................................................................................................................9
Access layer.............................................................................................................................................9
NIC Teaming............................................................................................................................................9
Server Monitoring.....................................................................................................................................10
Router [3][5]..............................................................................................................................................10
Router Specification..............................................................................................................................10
Router Protocols....................................................................................................................................10
Security Policies and Plans [5]...............................................................................................................10
User Documentation.................................................................................................................................12
Ongoing Maintenance Support.................................................................................................................13
References.................................................................................................................................................15
Contents
Introduction.................................................................................................................................................3
Assumptions in the Design..........................................................................................................................3
Network Requirements...............................................................................................................................3
Network Design...........................................................................................................................................4
TTF WAN Architecture [1]............................................................................................................................4
Technology..............................................................................................................................................4
Cabling.....................................................................................................................................................4
Security....................................................................................................................................................4
Hardware Configuration [4][6]................................................................................................................4
Diagram...................................................................................................................................................5
Directory Structure [7].................................................................................................................................7
Server Design [4][6].....................................................................................................................................8
TTF HQ.........................................................................................................................................................9
Server Farm Access Layer............................................................................................................................9
Access layer.............................................................................................................................................9
NIC Teaming............................................................................................................................................9
Server Monitoring.....................................................................................................................................10
Router [3][5]..............................................................................................................................................10
Router Specification..............................................................................................................................10
Router Protocols....................................................................................................................................10
Security Policies and Plans [5]...............................................................................................................10
User Documentation.................................................................................................................................12
Ongoing Maintenance Support.................................................................................................................13
References.................................................................................................................................................15

NETWORK DESIGN 3
Network Objectives
Introduction
The network for Talon Textile Fasteners (TTF) is designed to satisfy the following requirements:
1) Security – the network should not allow unauthorized access, both physically and
logically.
2) Speed – the network has to have adequate bandwidth. It should meet demand during
peak usage.
3) Reliability – the network should overcome redundancy and make sure that failure of one
system doesn’t bring the entire network down.
4) Scalability – the network must support sustaining scalability without the requirement to
rebuild the system every time a change is implemented.
Assumptions in the Design
1) TTF has a weak and old network design. Thus, it would be wise to build a new network
from scratch.
2) TTF wants all the circuits to be built.
3) Each department of TTF is located within accessible means. There are a few global
offices too.
4) The physical security of the network has to be maintained.
5) TTF does not share its network with other businesses.
Network Requirements
TTF’s major network traffic includes file sharing including accounting details, brochures, reports,
personnel profiles and financial information. The network should take care of various databases
and web pages too. At this moment, TTF needs video teleconferencing and VoIP services.
Network Objectives
Introduction
The network for Talon Textile Fasteners (TTF) is designed to satisfy the following requirements:
1) Security – the network should not allow unauthorized access, both physically and
logically.
2) Speed – the network has to have adequate bandwidth. It should meet demand during
peak usage.
3) Reliability – the network should overcome redundancy and make sure that failure of one
system doesn’t bring the entire network down.
4) Scalability – the network must support sustaining scalability without the requirement to
rebuild the system every time a change is implemented.
Assumptions in the Design
1) TTF has a weak and old network design. Thus, it would be wise to build a new network
from scratch.
2) TTF wants all the circuits to be built.
3) Each department of TTF is located within accessible means. There are a few global
offices too.
4) The physical security of the network has to be maintained.
5) TTF does not share its network with other businesses.
Network Requirements
TTF’s major network traffic includes file sharing including accounting details, brochures, reports,
personnel profiles and financial information. The network should take care of various databases
and web pages too. At this moment, TTF needs video teleconferencing and VoIP services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK DESIGN 4
Network Design
TTF will have a wide area network connecting several offices to the main headquarters. The
wide-area-network is connected to the company’s backbone network. The backbone network
connects all local-area-networks in the branch offices to the wide-area-network. Every
employee at TTF will be connected to a department local-area-network, which supports
departments to share database information and files.
In the high level, TTF’s WAN follows a star architecture. However, ring architecture would be
easier to manage. Star architecture is faster because information does not travel around a ring
to reach headquarters. TTF does not require a mesh network because it is expensive.
TTF WAN Architecture [1]
Technology
Asynchronous Transfer Mode and Frame Relay are considered for the TTF WAN’s physical and
data layers. Ultimately, 1000Base-FX Gigabit Ethernet is chosen over fiber optic cabling [2].
Both Frame Relay and ATM have latency issues during protocol conversion. The entire network
makes use of the Gigabit Ethernet. This eliminates the need for complex protocols in the TTF
network. Also, the company can make incremental investments during expansion. In case, TTF
plans to open a new branch, they don’t have to worry about anything. Ethernet is shared using
hubs because it is cheaper than fitting the entire building with fiber optic cables.
Cabling
TTF WAN has connections between the branch offices and headquarters. Fiber optic cables can
be laid for this connection. It is recommended for TTF to use leased lines.
Security
Traffic into the network is managed by TTF HQ. There are points to limit the amount of
incoming data. Redundancy can be built in one of the systems to handle problematic situations.
In case the HQ network faces bottle necks, entry points can be redirected to other offices.
Because data has only one entry point, LANs don’t have any firewalls. Security is taken care of
by the anomaly detector and firewall in the TTF HQ machine.
Hardware Configuration [4][6]
The organisation relies on fiber cables. Media converters are used because departs in TTF have
LANs with 100 Mbps Ehternet over the normal Cat 5e cables. The core office can use a Layer 3
switch. This will let the company configure virtual LANS in the future. For instance, sales
managers can use the same circuit when they are within the company showcasing details to
customers. For a Layer 3 switch, Cisco’s 3750 X Catalyst 48P-S is preferred. In the distribution
Network Design
TTF will have a wide area network connecting several offices to the main headquarters. The
wide-area-network is connected to the company’s backbone network. The backbone network
connects all local-area-networks in the branch offices to the wide-area-network. Every
employee at TTF will be connected to a department local-area-network, which supports
departments to share database information and files.
In the high level, TTF’s WAN follows a star architecture. However, ring architecture would be
easier to manage. Star architecture is faster because information does not travel around a ring
to reach headquarters. TTF does not require a mesh network because it is expensive.
TTF WAN Architecture [1]
Technology
Asynchronous Transfer Mode and Frame Relay are considered for the TTF WAN’s physical and
data layers. Ultimately, 1000Base-FX Gigabit Ethernet is chosen over fiber optic cabling [2].
Both Frame Relay and ATM have latency issues during protocol conversion. The entire network
makes use of the Gigabit Ethernet. This eliminates the need for complex protocols in the TTF
network. Also, the company can make incremental investments during expansion. In case, TTF
plans to open a new branch, they don’t have to worry about anything. Ethernet is shared using
hubs because it is cheaper than fitting the entire building with fiber optic cables.
Cabling
TTF WAN has connections between the branch offices and headquarters. Fiber optic cables can
be laid for this connection. It is recommended for TTF to use leased lines.
Security
Traffic into the network is managed by TTF HQ. There are points to limit the amount of
incoming data. Redundancy can be built in one of the systems to handle problematic situations.
In case the HQ network faces bottle necks, entry points can be redirected to other offices.
Because data has only one entry point, LANs don’t have any firewalls. Security is taken care of
by the anomaly detector and firewall in the TTF HQ machine.
Hardware Configuration [4][6]
The organisation relies on fiber cables. Media converters are used because departs in TTF have
LANs with 100 Mbps Ehternet over the normal Cat 5e cables. The core office can use a Layer 3
switch. This will let the company configure virtual LANS in the future. For instance, sales
managers can use the same circuit when they are within the company showcasing details to
customers. For a Layer 3 switch, Cisco’s 3750 X Catalyst 48P-S is preferred. In the distribution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK DESIGN 5
layer, there can be four Layer 2 switches (one for LAN, and one for demilitarized zones). The
headquarters has 6 employees broken into three departments (management, sales, technical).
Thus, four switches will be required. Switches act as separate point-to-point connections. This
reduces the chances of collisions.
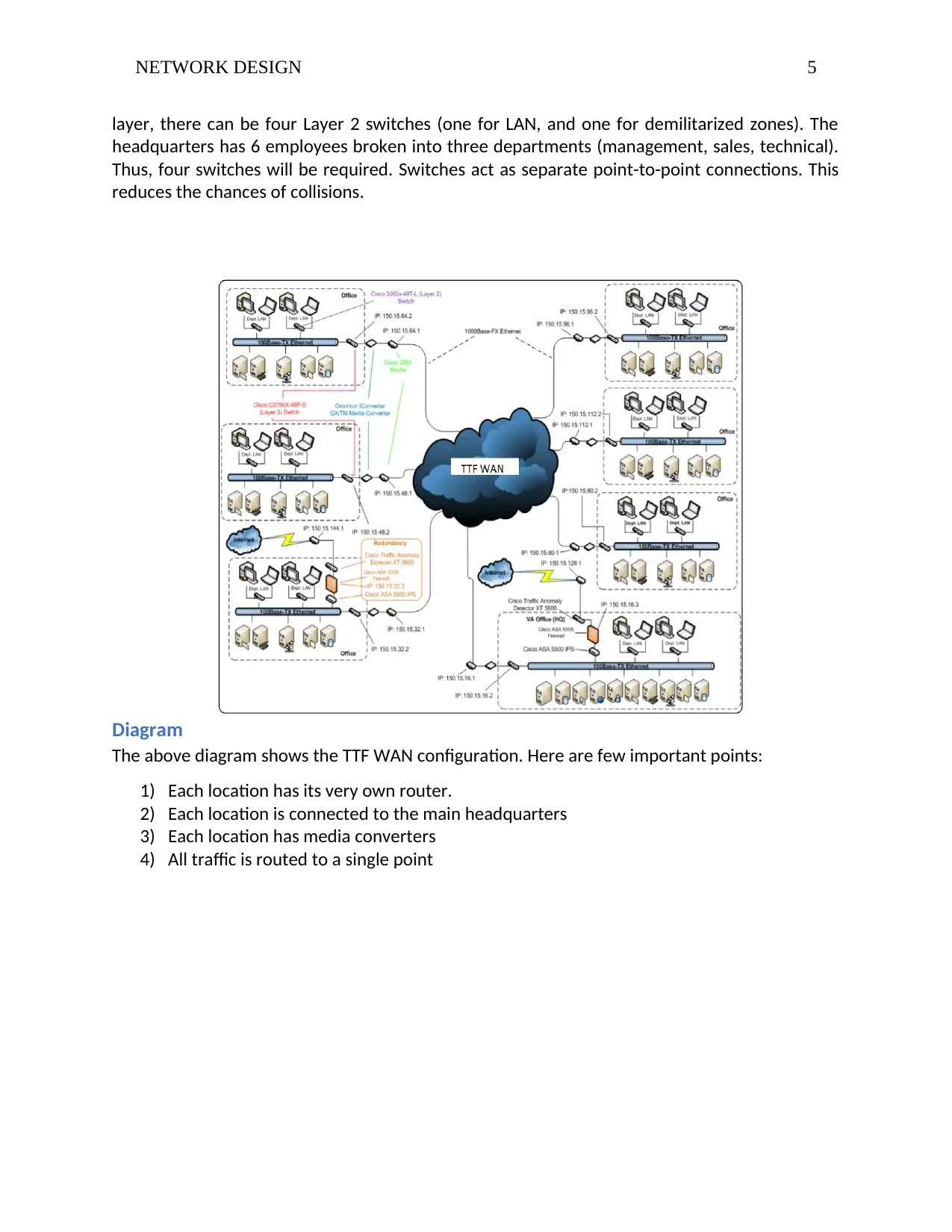
Diagram
The above diagram shows the TTF WAN configuration. Here are few important points:
1) Each location has its very own router.
2) Each location is connected to the main headquarters
3) Each location has media converters
4) All traffic is routed to a single point
layer, there can be four Layer 2 switches (one for LAN, and one for demilitarized zones). The
headquarters has 6 employees broken into three departments (management, sales, technical).
Thus, four switches will be required. Switches act as separate point-to-point connections. This
reduces the chances of collisions.
Diagram
The above diagram shows the TTF WAN configuration. Here are few important points:
1) Each location has its very own router.
2) Each location is connected to the main headquarters
3) Each location has media converters
4) All traffic is routed to a single point
NETWORK DESIGN 6
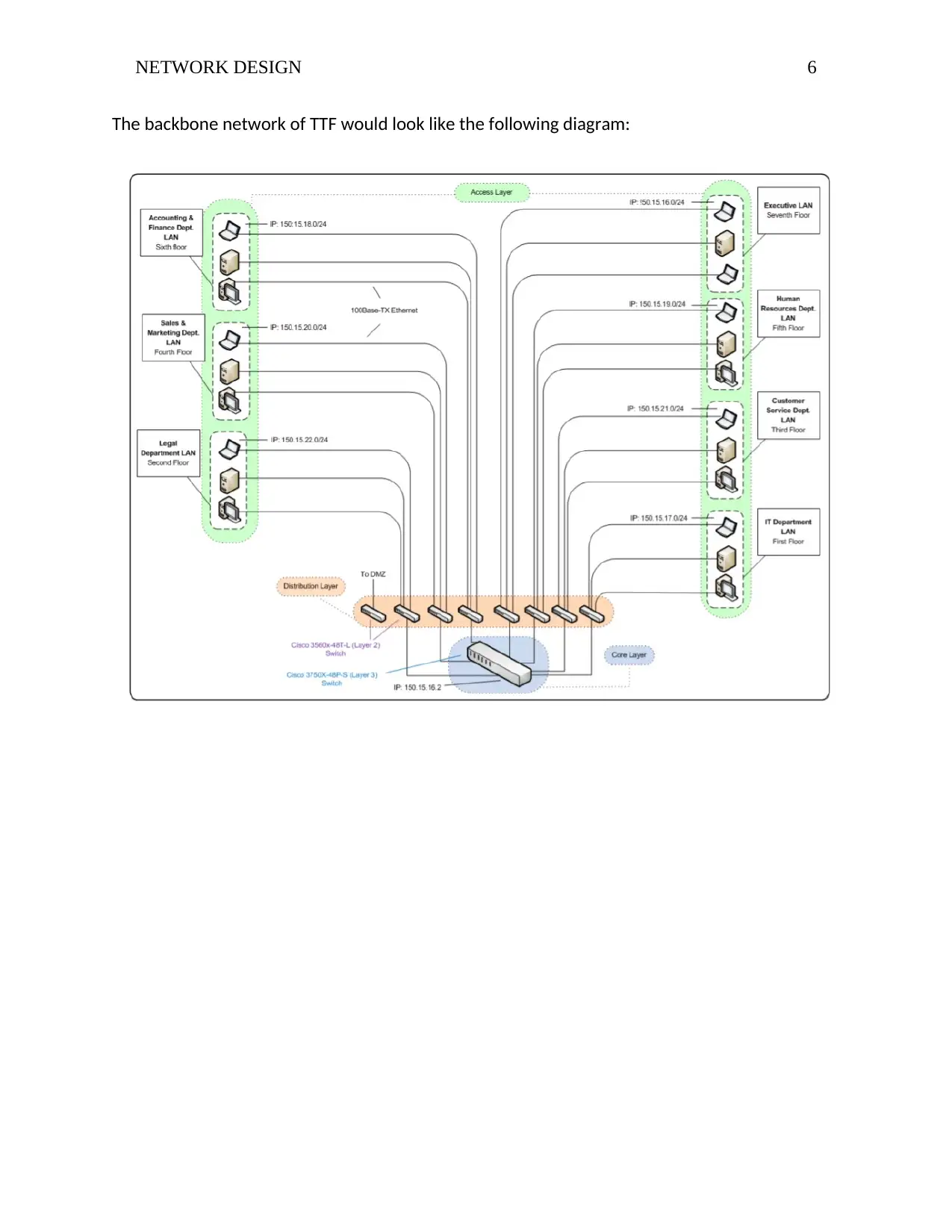
The backbone network of TTF would look like the following diagram:
The backbone network of TTF would look like the following diagram:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK DESIGN 7
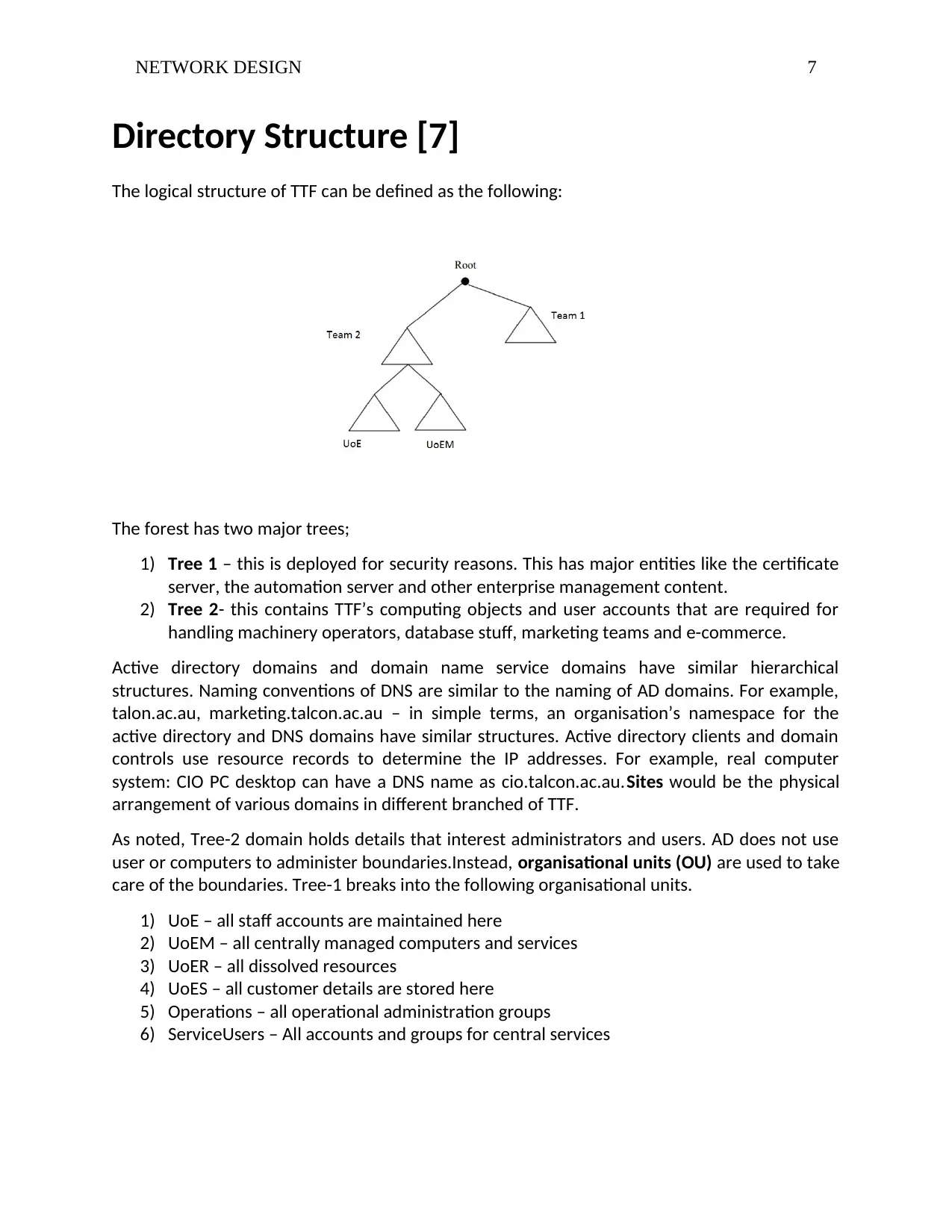
Directory Structure [7]
The logical structure of TTF can be defined as the following:
The forest has two major trees;
1) Tree 1 – this is deployed for security reasons. This has major entities like the certificate
server, the automation server and other enterprise management content.
2) Tree 2- this contains TTF’s computing objects and user accounts that are required for
handling machinery operators, database stuff, marketing teams and e-commerce.
Active directory domains and domain name service domains have similar hierarchical
structures. Naming conventions of DNS are similar to the naming of AD domains. For example,
talon.ac.au, marketing.talcon.ac.au – in simple terms, an organisation’s namespace for the
active directory and DNS domains have similar structures. Active directory clients and domain
controls use resource records to determine the IP addresses. For example, real computer
system: CIO PC desktop can have a DNS name as cio.talcon.ac.au.Sites would be the physical
arrangement of various domains in different branched of TTF.
As noted, Tree-2 domain holds details that interest administrators and users. AD does not use
user or computers to administer boundaries.Instead, organisational units (OU) are used to take
care of the boundaries. Tree-1 breaks into the following organisational units.
1) UoE – all staff accounts are maintained here
2) UoEM – all centrally managed computers and services
3) UoER – all dissolved resources
4) UoES – all customer details are stored here
5) Operations – all operational administration groups
6) ServiceUsers – All accounts and groups for central services
Directory Structure [7]
The logical structure of TTF can be defined as the following:
The forest has two major trees;
1) Tree 1 – this is deployed for security reasons. This has major entities like the certificate
server, the automation server and other enterprise management content.
2) Tree 2- this contains TTF’s computing objects and user accounts that are required for
handling machinery operators, database stuff, marketing teams and e-commerce.
Active directory domains and domain name service domains have similar hierarchical
structures. Naming conventions of DNS are similar to the naming of AD domains. For example,
talon.ac.au, marketing.talcon.ac.au – in simple terms, an organisation’s namespace for the
active directory and DNS domains have similar structures. Active directory clients and domain
controls use resource records to determine the IP addresses. For example, real computer
system: CIO PC desktop can have a DNS name as cio.talcon.ac.au.Sites would be the physical
arrangement of various domains in different branched of TTF.
As noted, Tree-2 domain holds details that interest administrators and users. AD does not use
user or computers to administer boundaries.Instead, organisational units (OU) are used to take
care of the boundaries. Tree-1 breaks into the following organisational units.
1) UoE – all staff accounts are maintained here
2) UoEM – all centrally managed computers and services
3) UoER – all dissolved resources
4) UoES – all customer details are stored here
5) Operations – all operational administration groups
6) ServiceUsers – All accounts and groups for central services
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK DESIGN 8
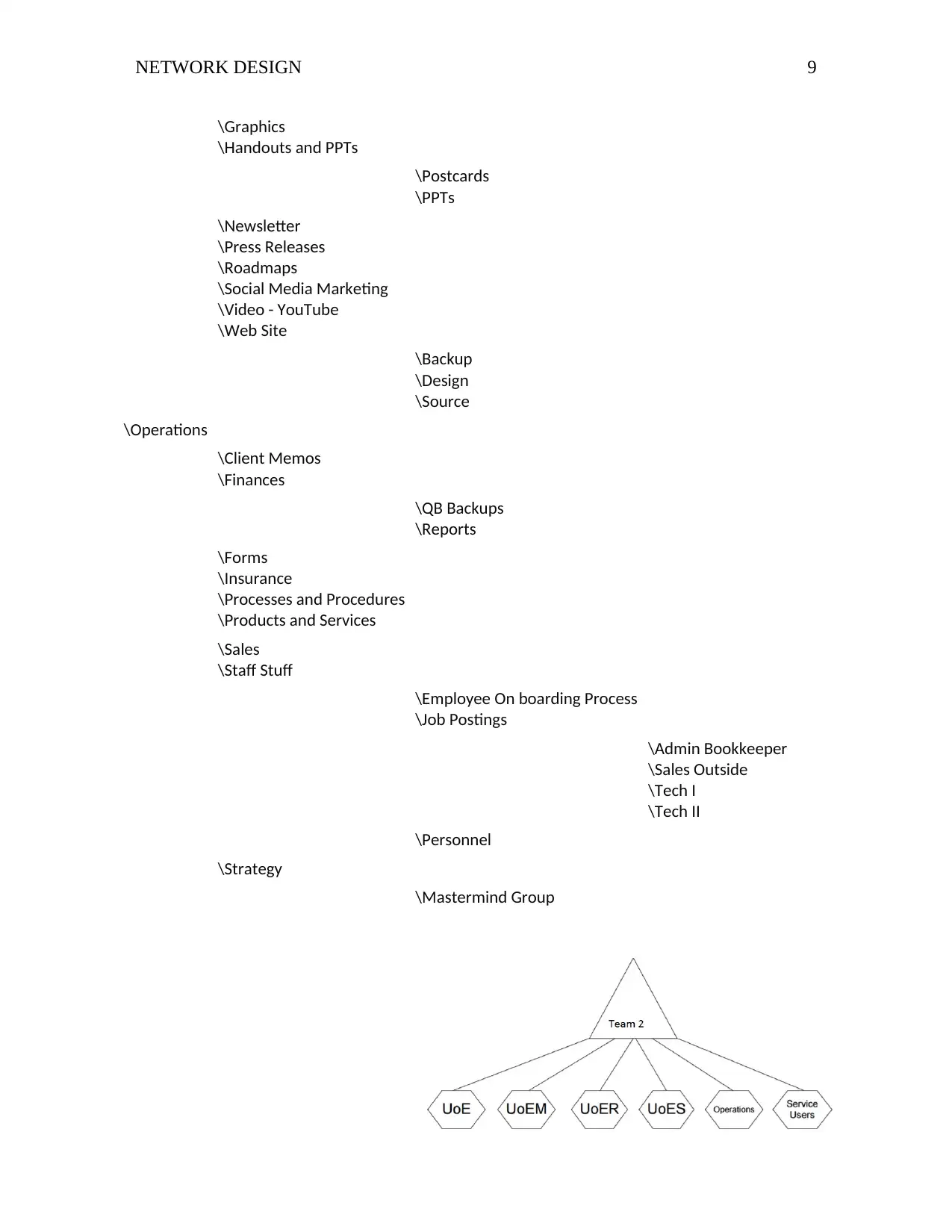
With respect to sites for the TTF network, there are three major categories. This includes
/clients (ServiceUsers, UoES,UoE), /marketing (UoE) and /operations (UoEM,UoER,operations)
The clients folder can take care of all current clients, previous clients and prospects. Previous
clients would be those who acquired services from TTF but left. Details of these customers
should be moved and handled by a separate department. Client folders can be accessed and
managed by the admin staff, sales staff and service manager. This is an open site; thus, it should
not have customer payment details. Payment details must be stored carefully in
/operations/finance. This is a secure site and secured folder in the system.
Marketing is an important part of TTF network. This is where organizational units that take care
of adwords, co-marketing, contacts, campaigns, social media marketing, road maps and website
management are held. Since TTF is venturing in e-commerce, this is a separate site. There are
organizational employees handling marketing information. These details cannot be accessed by
everyone in the company. However, they can be accessed by admin staff and marketing staff.
Operations site is secured for important operations and file management routines. This site is
handled by managers and owners of the company. It carries groups to take care of finances,
forms, client memos, insurance, products and services, sales, processes and procedures and
employee information. Information in this site is secured from most employees. The operations
folder can be accessed by a known and authorized group of administrative employees,
managers and owners. Most staff members are not allowed to enter into area.
Clients
\!Old
\!Prospects
\ABC Client
\DEF Client
\GHI Client
\JKL Client
\etc.
\Marketing
\Adwords
\Blog Fodder
\Posted
\Campaigns
\Fall Push
\HP - MS - Office
\Spring Microsoft
\Summer
\Co-Marketing
\Contacts - Mailing Lists
With respect to sites for the TTF network, there are three major categories. This includes
/clients (ServiceUsers, UoES,UoE), /marketing (UoE) and /operations (UoEM,UoER,operations)
The clients folder can take care of all current clients, previous clients and prospects. Previous
clients would be those who acquired services from TTF but left. Details of these customers
should be moved and handled by a separate department. Client folders can be accessed and
managed by the admin staff, sales staff and service manager. This is an open site; thus, it should
not have customer payment details. Payment details must be stored carefully in
/operations/finance. This is a secure site and secured folder in the system.
Marketing is an important part of TTF network. This is where organizational units that take care
of adwords, co-marketing, contacts, campaigns, social media marketing, road maps and website
management are held. Since TTF is venturing in e-commerce, this is a separate site. There are
organizational employees handling marketing information. These details cannot be accessed by
everyone in the company. However, they can be accessed by admin staff and marketing staff.
Operations site is secured for important operations and file management routines. This site is
handled by managers and owners of the company. It carries groups to take care of finances,
forms, client memos, insurance, products and services, sales, processes and procedures and
employee information. Information in this site is secured from most employees. The operations
folder can be accessed by a known and authorized group of administrative employees,
managers and owners. Most staff members are not allowed to enter into area.
Clients
\!Old
\!Prospects
\ABC Client
\DEF Client
\GHI Client
\JKL Client
\etc.
\Marketing
\Adwords
\Blog Fodder
\Posted
\Campaigns
\Fall Push
\HP - MS - Office
\Spring Microsoft
\Summer
\Co-Marketing
\Contacts - Mailing Lists
NETWORK DESIGN 9
\Graphics
\Handouts and PPTs
\Postcards
\PPTs
\Newsletter
\Press Releases
\Roadmaps
\Social Media Marketing
\Video - YouTube
\Web Site
\Backup
\Design
\Source
\Operations
\Client Memos
\Finances
\QB Backups
\Reports
\Forms
\Insurance
\Processes and Procedures
\Products and Services
\Sales
\Staff Stuff
\Employee On boarding Process
\Job Postings
\Admin Bookkeeper
\Sales Outside
\Tech I
\Tech II
\Personnel
\Strategy
\Mastermind Group
\Graphics
\Handouts and PPTs
\Postcards
\PPTs
\Newsletter
\Press Releases
\Roadmaps
\Social Media Marketing
\Video - YouTube
\Web Site
\Backup
\Design
\Source
\Operations
\Client Memos
\Finances
\QB Backups
\Reports
\Forms
\Insurance
\Processes and Procedures
\Products and Services
\Sales
\Staff Stuff
\Employee On boarding Process
\Job Postings
\Admin Bookkeeper
\Sales Outside
\Tech I
\Tech II
\Personnel
\Strategy
\Mastermind Group
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK DESIGN 10
Server Design [4][6]
The servers used in TTF can be classified into three major categories. Servers provide the
following network-based services:
1) DNS – this is used to resolve hostnames to corresponding IP addresses
2) DHCP – This is used by end devices to get IP addresses along with other parameters like
the IP Address of DNS servers, subnet mask and default gateway from the DHCP server.
This server makes sure the IP Addresses are unique. No two sites can have a similar IP
address. IP address poll management is done by the DHCP server.
3) Directory Services – all details of applications that structure data about the end user and
network resources is managed here.
4) Security and Network Management Server – TTF can rely on Cisco Security Monitoring,
response system and analysis. These servers reduce false positives between end-to-end
view of the network. Promote awareness of unexpected network behavior. MARS offers
recommendations for effective threat removal.
5) Manufacturing application Servers – this helps in handling the database, asset security,
supervisory computers and factory talk servers.
TTF HQ
At TTF HQ, all servers for the TTF networks will be housed. This includes the database,
department file and print servers. There are two domain controllers to handle the employees.
There is a single database server to have details of TTF. IP Addresses are assigned at LAN level
dynamically. HQ will also have a SQL server, application server, IM server and DNS Server.
Options for these servers would be HP Proliant Line or Dell PowerEdge line.
Server Farm Access Layer
Access layer
The access layer represents the physical connectivity to the actual server farm. Applications on
the servers that take care of the manufacturing zone are business-critical ones. Thus, they need
to be dual-homed. The layer has to be connected to the access layer switches. Layer 2 access
model is linked to the aggregation layer using the IEEE 802.1Q trunk. The aggregation switch
takes care of layer 3 processing. The layer model supports VLAN instances throughout the
access layer switches. This allows TTF to rack servers anywhere.
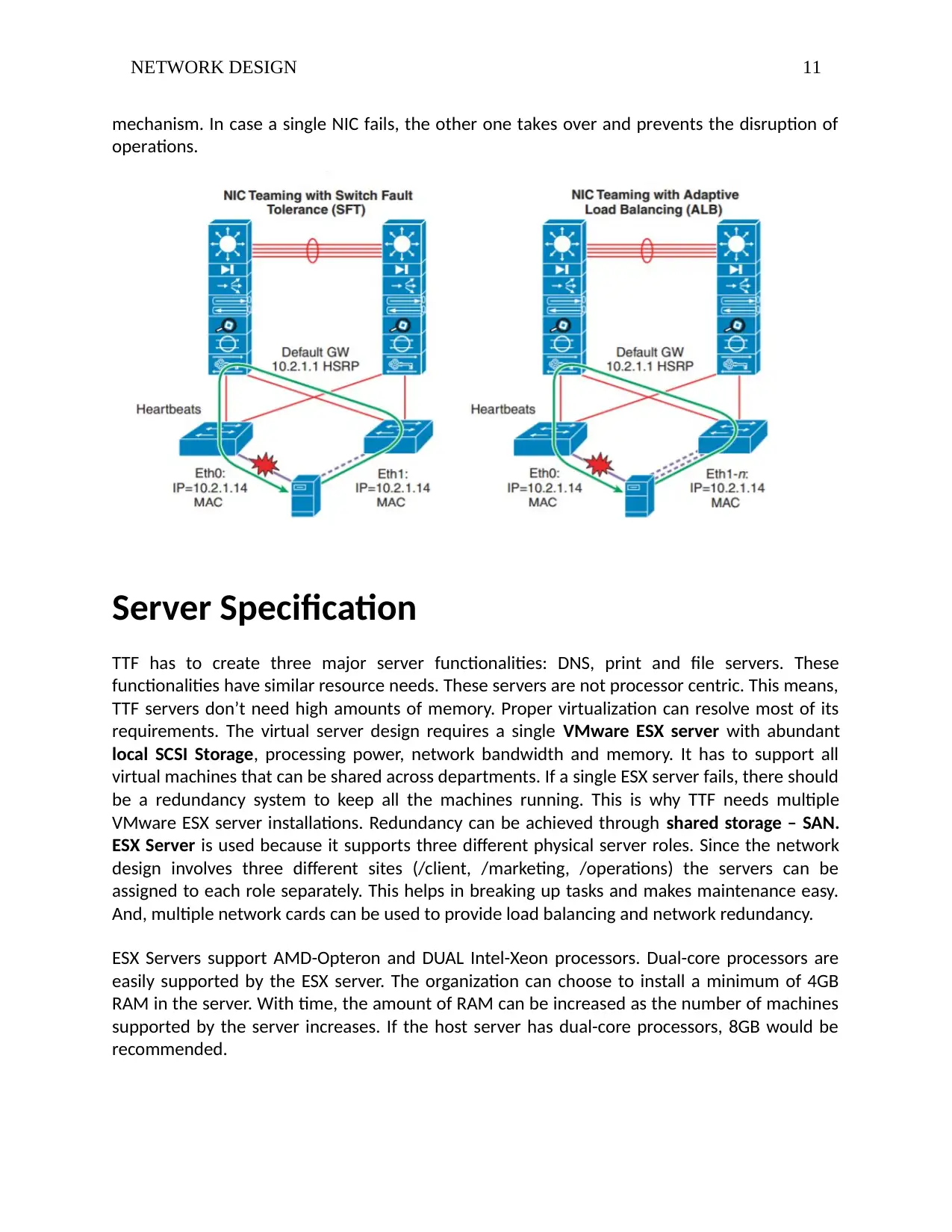
NIC Teaming
TTF needs a mission critical network that can tolerate downtime. To eliminate single server
failures, NIC Teaming is used. NIC Teaming provides software and drivers for failover
Server Design [4][6]
The servers used in TTF can be classified into three major categories. Servers provide the
following network-based services:
1) DNS – this is used to resolve hostnames to corresponding IP addresses
2) DHCP – This is used by end devices to get IP addresses along with other parameters like
the IP Address of DNS servers, subnet mask and default gateway from the DHCP server.
This server makes sure the IP Addresses are unique. No two sites can have a similar IP
address. IP address poll management is done by the DHCP server.
3) Directory Services – all details of applications that structure data about the end user and
network resources is managed here.
4) Security and Network Management Server – TTF can rely on Cisco Security Monitoring,
response system and analysis. These servers reduce false positives between end-to-end
view of the network. Promote awareness of unexpected network behavior. MARS offers
recommendations for effective threat removal.
5) Manufacturing application Servers – this helps in handling the database, asset security,
supervisory computers and factory talk servers.
TTF HQ
At TTF HQ, all servers for the TTF networks will be housed. This includes the database,
department file and print servers. There are two domain controllers to handle the employees.
There is a single database server to have details of TTF. IP Addresses are assigned at LAN level
dynamically. HQ will also have a SQL server, application server, IM server and DNS Server.
Options for these servers would be HP Proliant Line or Dell PowerEdge line.
Server Farm Access Layer
Access layer
The access layer represents the physical connectivity to the actual server farm. Applications on
the servers that take care of the manufacturing zone are business-critical ones. Thus, they need
to be dual-homed. The layer has to be connected to the access layer switches. Layer 2 access
model is linked to the aggregation layer using the IEEE 802.1Q trunk. The aggregation switch
takes care of layer 3 processing. The layer model supports VLAN instances throughout the
access layer switches. This allows TTF to rack servers anywhere.
NIC Teaming
TTF needs a mission critical network that can tolerate downtime. To eliminate single server
failures, NIC Teaming is used. NIC Teaming provides software and drivers for failover
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK DESIGN 11
mechanism. In case a single NIC fails, the other one takes over and prevents the disruption of
operations.
Server Specification
TTF has to create three major server functionalities: DNS, print and file servers. These
functionalities have similar resource needs. These servers are not processor centric. This means,
TTF servers don’t need high amounts of memory. Proper virtualization can resolve most of its
requirements. The virtual server design requires a single VMware ESX server with abundant
local SCSI Storage, processing power, network bandwidth and memory. It has to support all
virtual machines that can be shared across departments. If a single ESX server fails, there should
be a redundancy system to keep all the machines running. This is why TTF needs multiple
VMware ESX server installations. Redundancy can be achieved through shared storage – SAN.
ESX Server is used because it supports three different physical server roles. Since the network
design involves three different sites (/client, /marketing, /operations) the servers can be
assigned to each role separately. This helps in breaking up tasks and makes maintenance easy.
And, multiple network cards can be used to provide load balancing and network redundancy.
ESX Servers support AMD-Opteron and DUAL Intel-Xeon processors. Dual-core processors are
easily supported by the ESX server. The organization can choose to install a minimum of 4GB
RAM in the server. With time, the amount of RAM can be increased as the number of machines
supported by the server increases. If the host server has dual-core processors, 8GB would be
recommended.
mechanism. In case a single NIC fails, the other one takes over and prevents the disruption of
operations.
Server Specification
TTF has to create three major server functionalities: DNS, print and file servers. These
functionalities have similar resource needs. These servers are not processor centric. This means,
TTF servers don’t need high amounts of memory. Proper virtualization can resolve most of its
requirements. The virtual server design requires a single VMware ESX server with abundant
local SCSI Storage, processing power, network bandwidth and memory. It has to support all
virtual machines that can be shared across departments. If a single ESX server fails, there should
be a redundancy system to keep all the machines running. This is why TTF needs multiple
VMware ESX server installations. Redundancy can be achieved through shared storage – SAN.
ESX Server is used because it supports three different physical server roles. Since the network
design involves three different sites (/client, /marketing, /operations) the servers can be
assigned to each role separately. This helps in breaking up tasks and makes maintenance easy.
And, multiple network cards can be used to provide load balancing and network redundancy.
ESX Servers support AMD-Opteron and DUAL Intel-Xeon processors. Dual-core processors are
easily supported by the ESX server. The organization can choose to install a minimum of 4GB
RAM in the server. With time, the amount of RAM can be increased as the number of machines
supported by the server increases. If the host server has dual-core processors, 8GB would be
recommended.
NETWORK DESIGN 12
For TTF, RAID-1 or disk mirroring is sufficient to take backup of data. However, RAID-5 offers
quicker read access and are highly recommended for organizations. A hot spare drive can be
included to offer immediate failover if a hard drive fails. Additional redundancy can be
introduced through remote access interfaces (Dell DRAC, HP iLO) and redundant fan kits. To take
care of failovers, VMware Consolidated Backup can be used. This is a backup method for
centralized backup of files from the server. This is a standard backup agent with a single instance
in the proxy server. Backup traffic is overcome through the use of Fiber Channel tape devices.
When compared to print and file servers, DNS servers require higher hardware configuration.
The file and print servers are responsible for sending and receiving traffic from client
workstations. TCP connections can be used to handle these sessions. The benefit of using ESX
Servers would be its ability to schedule efficiently. Multiple processors can be hosted. The TTF
server requires only 512 MB RAM. This is because ESX Servers handle memory management
efficiently with transparent page sharing across several virtual machines. This will be a cost
effective method for TTF.
For Networking, virtual switches are used and the ESX Server’s NIC cards are useful. Since TTF
has staff moving across branches, multiple physical NIC adapters can be connected to a single
virtual switch. This takes care of load balancing.
Since a virtual Server is proposed for TTF, everything gets configured into a set of files. Virtual
disks of equal sizes and disk capacity of 8GB are suggested. Implementing shared storage
removes the dependency various machines have on the ESX Server. There are three types of
storage to choose from. This includes NAS, SAN and iSCSI SAN.
Server Test Plan
1. Test 1 – Maximum client capacity
a. To support the growing needs of TTF to handle various load conditions and to
characterize its peak capabilities
b. The maximum steady state DHCP transactions or requests handling capacity
should be gauged. The server performance should not drop with additional
packets or traffic seeping into the server
1. Test 2 – Maximum transaction rate
For TTF, RAID-1 or disk mirroring is sufficient to take backup of data. However, RAID-5 offers
quicker read access and are highly recommended for organizations. A hot spare drive can be
included to offer immediate failover if a hard drive fails. Additional redundancy can be
introduced through remote access interfaces (Dell DRAC, HP iLO) and redundant fan kits. To take
care of failovers, VMware Consolidated Backup can be used. This is a backup method for
centralized backup of files from the server. This is a standard backup agent with a single instance
in the proxy server. Backup traffic is overcome through the use of Fiber Channel tape devices.
When compared to print and file servers, DNS servers require higher hardware configuration.
The file and print servers are responsible for sending and receiving traffic from client
workstations. TCP connections can be used to handle these sessions. The benefit of using ESX
Servers would be its ability to schedule efficiently. Multiple processors can be hosted. The TTF
server requires only 512 MB RAM. This is because ESX Servers handle memory management
efficiently with transparent page sharing across several virtual machines. This will be a cost
effective method for TTF.
For Networking, virtual switches are used and the ESX Server’s NIC cards are useful. Since TTF
has staff moving across branches, multiple physical NIC adapters can be connected to a single
virtual switch. This takes care of load balancing.
Since a virtual Server is proposed for TTF, everything gets configured into a set of files. Virtual
disks of equal sizes and disk capacity of 8GB are suggested. Implementing shared storage
removes the dependency various machines have on the ESX Server. There are three types of
storage to choose from. This includes NAS, SAN and iSCSI SAN.
Server Test Plan
1. Test 1 – Maximum client capacity
a. To support the growing needs of TTF to handle various load conditions and to
characterize its peak capabilities
b. The maximum steady state DHCP transactions or requests handling capacity
should be gauged. The server performance should not drop with additional
packets or traffic seeping into the server
1. Test 2 – Maximum transaction rate
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





