Advanced Medicos Limited Network Expansion Report - CSC00240
VerifiedAdded on 2023/01/20
|14
|3277
|96
Report
AI Summary
This report provides a comprehensive analysis of the network expansion requirements for Advanced Medicos Limited (AML), a digital health company. The report begins by outlining AML's business and technical goals, including improved communication, scalability, and security. It then analyzes the current network setup, identifying limitations and areas for improvement. The core of the report proposes a redesigned network infrastructure to support AML's growth, including detailed network topologies, hardware specifications, and application requirements. The proposed network utilizes LAN and WAN technologies to connect three buildings, ensuring sufficient bandwidth, security, and scalability for over 400 employees. The report includes calculations of subnet sizes and IP address allocation, along with descriptions of the network's key components, such as routers, switches, and firewalls. The report concludes that the proposed network design effectively meets AML's current and future needs, addressing all identified concerns and providing a robust and secure infrastructure for the company's expansion.

Network Expansion of AML
Author
Date
Author
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
The objective of this report lies in summarizing network expansion requirements for the medical
institute AML (Advanced Medicos Limited) seeks open a new branch office. To facilitate the network
throughout the three different buildings including those of the headquarters as well as the newly
opened branch office, AML attempts to redesign their existing network infrastructure into a wider
network that can cater to the requirements of all the three buildings. The report begins by touching
on the different business goals, followed by the several technological goals, all of which AML wishes
to meet. Then after analysis of the respective requirements, this report tries explaining further on
reasoning and methods by which the network being proposed meets every future requirement of
the institute. This is again crosschecked by comparing various requirements with the functions of the
new network and how it is achieved. Thereafter the overall network layout gets thoroughly
discussed as also the roles of critical parts of the proposed network. From the observations drawn,
conclusions are made that the network design proposed in the report easily meets AML’s
requirements for the future while also addressing all concerns successfully.
The objective of this report lies in summarizing network expansion requirements for the medical
institute AML (Advanced Medicos Limited) seeks open a new branch office. To facilitate the network
throughout the three different buildings including those of the headquarters as well as the newly
opened branch office, AML attempts to redesign their existing network infrastructure into a wider
network that can cater to the requirements of all the three buildings. The report begins by touching
on the different business goals, followed by the several technological goals, all of which AML wishes
to meet. Then after analysis of the respective requirements, this report tries explaining further on
reasoning and methods by which the network being proposed meets every future requirement of
the institute. This is again crosschecked by comparing various requirements with the functions of the
new network and how it is achieved. Thereafter the overall network layout gets thoroughly
discussed as also the roles of critical parts of the proposed network. From the observations drawn,
conclusions are made that the network design proposed in the report easily meets AML’s
requirements for the future while also addressing all concerns successfully.

Table of Contents
Author...............................................................................................................................................1
Date...................................................................................................................................................1
1. Introduction.......................................................................................................................................4
2. Analysis of User Requirements......................................................................................................4
Requirement Summary and Analysis of Old network........................................................................4
Requirement Summary and Analysis of Proposed network..............................................................4
Network Requirements.................................................................................................................5
3. Description & Analysis of Current Setup with old setup....................................................................6
3.1 Data Transmission.......................................................................................................................7
3.2 Network Hardware......................................................................................................................7
3.3 Physical Network Topologies.......................................................................................................7
3.4 Description..................................................................................................................................7
3.5 Application Summary...............................................................................................................7
4. Conclusions........................................................................................................................................8
List of References..................................................................................................................................9
Appendix A..........................................................................................................................................10
Current System...........................................................................................................................10
Appendix B..........................................................................................................................................11
LAN Topology...............................................................................................................................11
WAN Topology.............................................................................................................................11
Old system...................................................................................................................................12
Author...............................................................................................................................................1
Date...................................................................................................................................................1
1. Introduction.......................................................................................................................................4
2. Analysis of User Requirements......................................................................................................4
Requirement Summary and Analysis of Old network........................................................................4
Requirement Summary and Analysis of Proposed network..............................................................4
Network Requirements.................................................................................................................5
3. Description & Analysis of Current Setup with old setup....................................................................6
3.1 Data Transmission.......................................................................................................................7
3.2 Network Hardware......................................................................................................................7
3.3 Physical Network Topologies.......................................................................................................7
3.4 Description..................................................................................................................................7
3.5 Application Summary...............................................................................................................7
4. Conclusions........................................................................................................................................8
List of References..................................................................................................................................9
Appendix A..........................................................................................................................................10
Current System...........................................................................................................................10
Appendix B..........................................................................................................................................11
LAN Topology...............................................................................................................................11
WAN Topology.............................................................................................................................11
Old system...................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
The report studies and analyses the specifications and requirements for network
infrastructure of the company AML (Advanced Medicos Limited) which looks to expand by opening a
new branch office and presents a requirements summary (Taleb, Bagaa and Ksentini 2015). For
facilitating the network among the headquarters and the newly created branch office, attempts to
redesign their existing network infrastructure into a wider network that can cater to the
requirements of all the three buildings. The report begins by touching on the different business
goals, followed by the several technological goals, all of which AML wishes to meet. Then after
analysis of the respective requirements, the study proceeds to explain further on why and by what
means can the proposed network meet all the future requirements of the company, AML by
comparing the various requirements with the functions of the new network and how it is achieved.
Thereafter the overall network layout gets thoroughly discussed as also the roles of critical parts of
the proposed network. Then the report ends with concluding notes with observations that suggest
the proposed network handily meeting AML’s future requirements.
2. Analysis of User Requirements
2.1 Business Goal
The communication channels have improved significantly through implementation of WLAN
network and enabling of videoconferencing and live meetings (Cao, Cheung and Yuk 2015). Every
expense allocated for restructuring of the network is crosschecked with requirements. Securing the
network is a key part of restructuring the network. The company AML requires to employ over 400
members in the near future and wishes to tap the advancement in technology for accomplishing the
expansion without having to invest fortunes.
2.2 Technical Goal
The rooms housing the computers, servers and network devise needs upgrading. The video
conferencing facility has to be enabled and made accessible in campuses for meeting needs of
employees (Sun et al. 2017). The network proposed, must be scalable as AML seeks to expand.
Wireless access points must be present helping employees in remote accessing of AML’s network
(Cao, Cheung and Yuk 2015). The resources must be accessible to members from office rooms and
campuses. Network should never be negatively affecting the performance of the organizational
members (Oostenbrink 2015). The network must not possess any loopholes and risk of failures
(Alatorre et al. 2019). Security of device and components of the network needs to be treated with
highest priority.
2.3 Requirement Summary and Analysis of Old network
Building/Location Department
Name
Number
of
Servers
Number of
Workstations
Number
of
Laptops
Number
of
Printers
Number
of Floors
The report studies and analyses the specifications and requirements for network
infrastructure of the company AML (Advanced Medicos Limited) which looks to expand by opening a
new branch office and presents a requirements summary (Taleb, Bagaa and Ksentini 2015). For
facilitating the network among the headquarters and the newly created branch office, attempts to
redesign their existing network infrastructure into a wider network that can cater to the
requirements of all the three buildings. The report begins by touching on the different business
goals, followed by the several technological goals, all of which AML wishes to meet. Then after
analysis of the respective requirements, the study proceeds to explain further on why and by what
means can the proposed network meet all the future requirements of the company, AML by
comparing the various requirements with the functions of the new network and how it is achieved.
Thereafter the overall network layout gets thoroughly discussed as also the roles of critical parts of
the proposed network. Then the report ends with concluding notes with observations that suggest
the proposed network handily meeting AML’s future requirements.
2. Analysis of User Requirements
2.1 Business Goal
The communication channels have improved significantly through implementation of WLAN
network and enabling of videoconferencing and live meetings (Cao, Cheung and Yuk 2015). Every
expense allocated for restructuring of the network is crosschecked with requirements. Securing the
network is a key part of restructuring the network. The company AML requires to employ over 400
members in the near future and wishes to tap the advancement in technology for accomplishing the
expansion without having to invest fortunes.
2.2 Technical Goal
The rooms housing the computers, servers and network devise needs upgrading. The video
conferencing facility has to be enabled and made accessible in campuses for meeting needs of
employees (Sun et al. 2017). The network proposed, must be scalable as AML seeks to expand.
Wireless access points must be present helping employees in remote accessing of AML’s network
(Cao, Cheung and Yuk 2015). The resources must be accessible to members from office rooms and
campuses. Network should never be negatively affecting the performance of the organizational
members (Oostenbrink 2015). The network must not possess any loopholes and risk of failures
(Alatorre et al. 2019). Security of device and components of the network needs to be treated with
highest priority.
2.3 Requirement Summary and Analysis of Old network
Building/Location Department
Name
Number
of
Servers
Number of
Workstations
Number
of
Laptops
Number
of
Printers
Number
of Floors
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
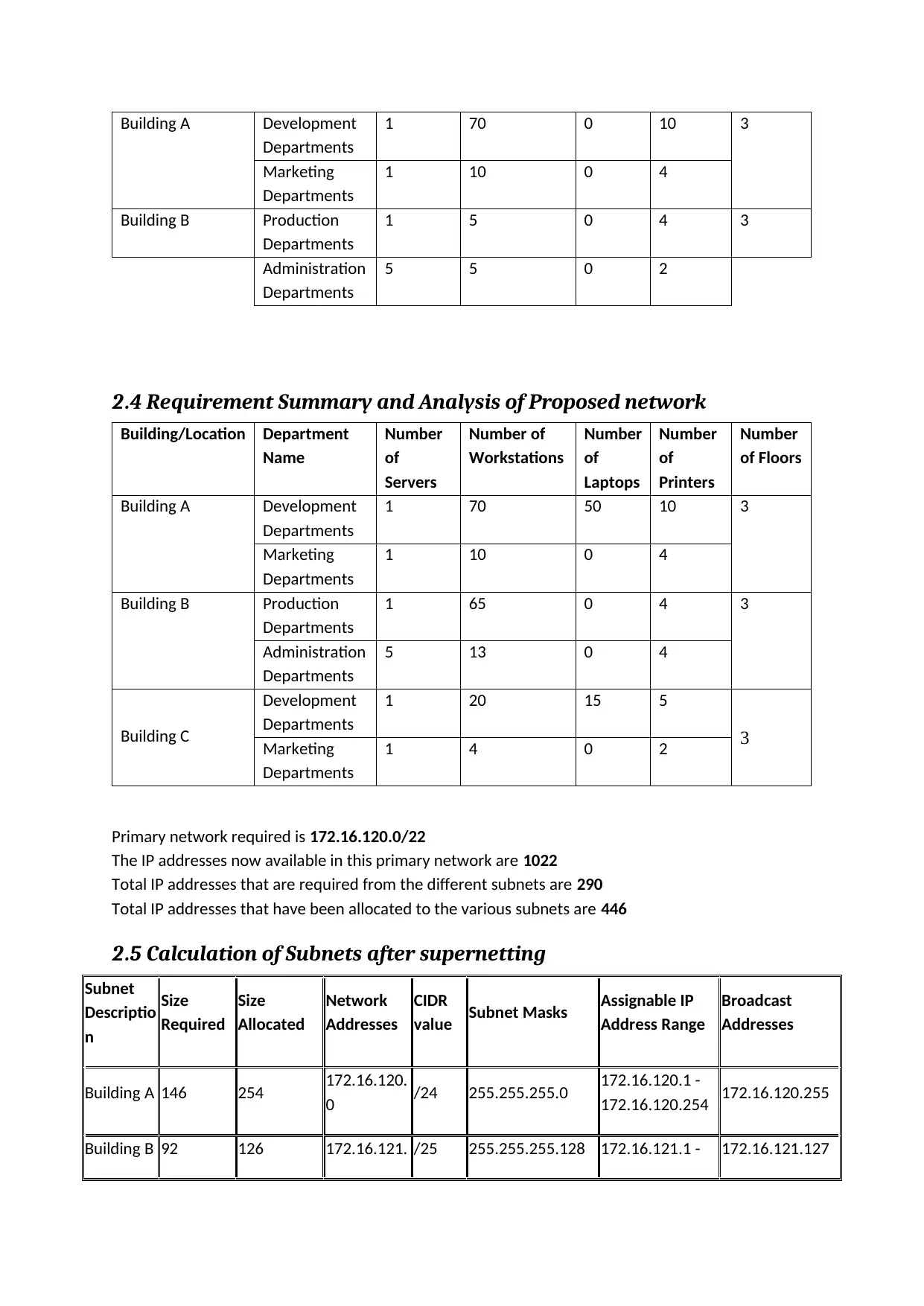
Building A Development
Departments
1 70 0 10 3
Marketing
Departments
1 10 0 4
Building B Production
Departments
1 5 0 4 3
Administration
Departments
5 5 0 2
2.4 Requirement Summary and Analysis of Proposed network
Building/Location Department
Name
Number
of
Servers
Number of
Workstations
Number
of
Laptops
Number
of
Printers
Number
of Floors
Building A Development
Departments
1 70 50 10 3
Marketing
Departments
1 10 0 4
Building B Production
Departments
1 65 0 4 3
Administration
Departments
5 13 0 4
Building C
Development
Departments
1 20 15 5
3
Marketing
Departments
1 4 0 2
Primary network required is 172.16.120.0/22
The IP addresses now available in this primary network are 1022
Total IP addresses that are required from the different subnets are 290
Total IP addresses that have been allocated to the various subnets are 446
2.5 Calculation of Subnets after supernetting
Subnet
Descriptio
n
Size
Required
Size
Allocated
Network
Addresses
CIDR
value Subnet Masks Assignable IP
Address Range
Broadcast
Addresses
Building A 146 254 172.16.120.
0 /24 255.255.255.0 172.16.120.1 -
172.16.120.254 172.16.120.255
Building B 92 126 172.16.121. /25 255.255.255.128 172.16.121.1 - 172.16.121.127
Departments
1 70 0 10 3
Marketing
Departments
1 10 0 4
Building B Production
Departments
1 5 0 4 3
Administration
Departments
5 5 0 2
2.4 Requirement Summary and Analysis of Proposed network
Building/Location Department
Name
Number
of
Servers
Number of
Workstations
Number
of
Laptops
Number
of
Printers
Number
of Floors
Building A Development
Departments
1 70 50 10 3
Marketing
Departments
1 10 0 4
Building B Production
Departments
1 65 0 4 3
Administration
Departments
5 13 0 4
Building C
Development
Departments
1 20 15 5
3
Marketing
Departments
1 4 0 2
Primary network required is 172.16.120.0/22
The IP addresses now available in this primary network are 1022
Total IP addresses that are required from the different subnets are 290
Total IP addresses that have been allocated to the various subnets are 446
2.5 Calculation of Subnets after supernetting
Subnet
Descriptio
n
Size
Required
Size
Allocated
Network
Addresses
CIDR
value Subnet Masks Assignable IP
Address Range
Broadcast
Addresses
Building A 146 254 172.16.120.
0 /24 255.255.255.0 172.16.120.1 -
172.16.120.254 172.16.120.255
Building B 92 126 172.16.121. /25 255.255.255.128 172.16.121.1 - 172.16.121.127
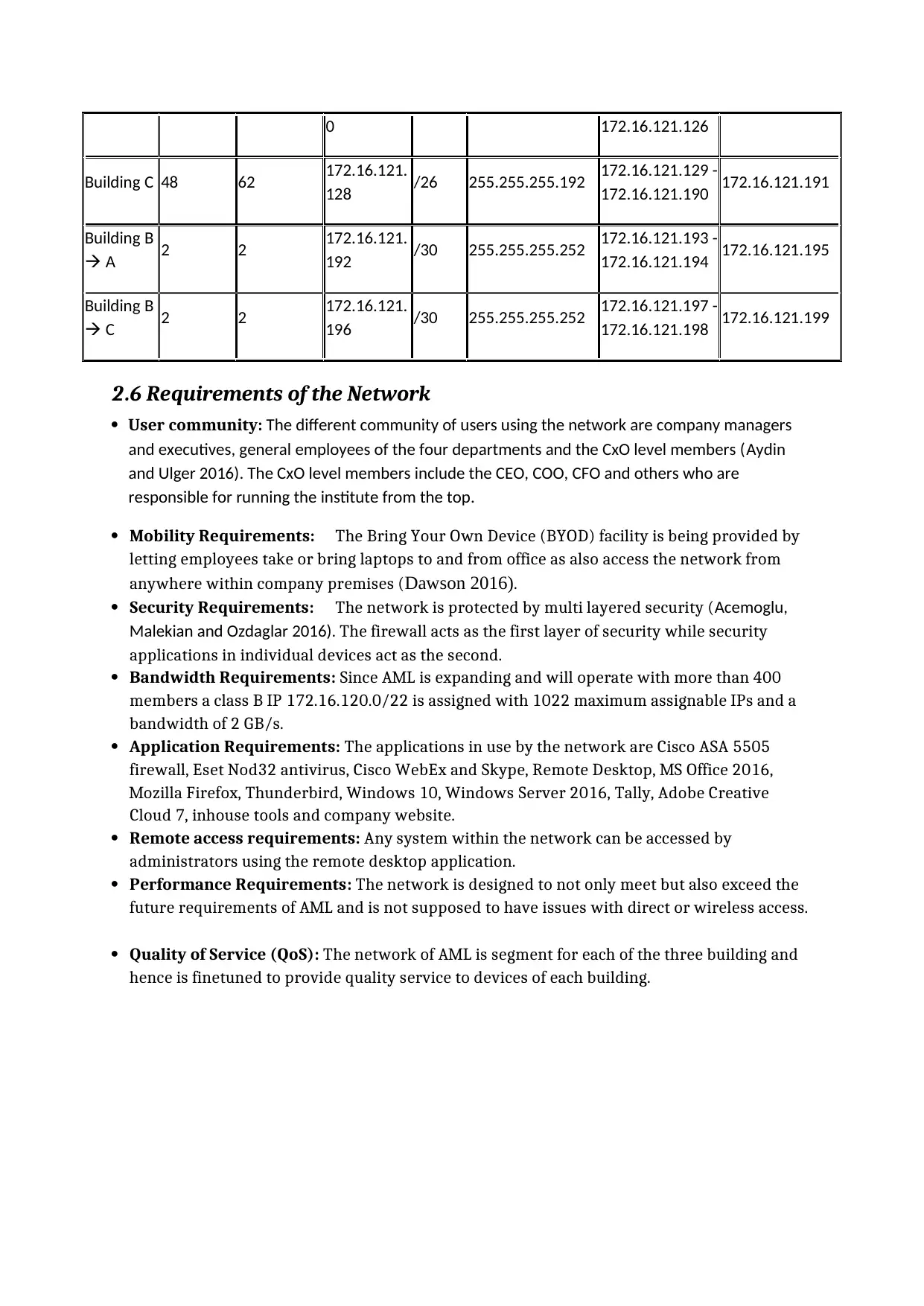
0 172.16.121.126
Building C 48 62 172.16.121.
128 /26 255.255.255.192 172.16.121.129 -
172.16.121.190 172.16.121.191
Building B
A 2 2 172.16.121.
192 /30 255.255.255.252 172.16.121.193 -
172.16.121.194 172.16.121.195
Building B
C 2 2 172.16.121.
196 /30 255.255.255.252 172.16.121.197 -
172.16.121.198 172.16.121.199
2.6 Requirements of the Network
User community: The different community of users using the network are company managers
and executives, general employees of the four departments and the CxO level members (Aydin
and Ulger 2016). The CxO level members include the CEO, COO, CFO and others who are
responsible for running the institute from the top.
Mobility Requirements: The Bring Your Own Device (BYOD) facility is being provided by
letting employees take or bring laptops to and from office as also access the network from
anywhere within company premises (Dawson 2016).
Security Requirements: The network is protected by multi layered security (Acemoglu,
Malekian and Ozdaglar 2016). The firewall acts as the first layer of security while security
applications in individual devices act as the second.
Bandwidth Requirements: Since AML is expanding and will operate with more than 400
members a class B IP 172.16.120.0/22 is assigned with 1022 maximum assignable IPs and a
bandwidth of 2 GB/s.
Application Requirements: The applications in use by the network are Cisco ASA 5505
firewall, Eset Nod32 antivirus, Cisco WebEx and Skype, Remote Desktop, MS Office 2016,
Mozilla Firefox, Thunderbird, Windows 10, Windows Server 2016, Tally, Adobe Creative
Cloud 7, inhouse tools and company website.
Remote access requirements: Any system within the network can be accessed by
administrators using the remote desktop application.
Performance Requirements: The network is designed to not only meet but also exceed the
future requirements of AML and is not supposed to have issues with direct or wireless access.
Quality of Service (QoS): The network of AML is segment for each of the three building and
hence is finetuned to provide quality service to devices of each building.
Building C 48 62 172.16.121.
128 /26 255.255.255.192 172.16.121.129 -
172.16.121.190 172.16.121.191
Building B
A 2 2 172.16.121.
192 /30 255.255.255.252 172.16.121.193 -
172.16.121.194 172.16.121.195
Building B
C 2 2 172.16.121.
196 /30 255.255.255.252 172.16.121.197 -
172.16.121.198 172.16.121.199
2.6 Requirements of the Network
User community: The different community of users using the network are company managers
and executives, general employees of the four departments and the CxO level members (Aydin
and Ulger 2016). The CxO level members include the CEO, COO, CFO and others who are
responsible for running the institute from the top.
Mobility Requirements: The Bring Your Own Device (BYOD) facility is being provided by
letting employees take or bring laptops to and from office as also access the network from
anywhere within company premises (Dawson 2016).
Security Requirements: The network is protected by multi layered security (Acemoglu,
Malekian and Ozdaglar 2016). The firewall acts as the first layer of security while security
applications in individual devices act as the second.
Bandwidth Requirements: Since AML is expanding and will operate with more than 400
members a class B IP 172.16.120.0/22 is assigned with 1022 maximum assignable IPs and a
bandwidth of 2 GB/s.
Application Requirements: The applications in use by the network are Cisco ASA 5505
firewall, Eset Nod32 antivirus, Cisco WebEx and Skype, Remote Desktop, MS Office 2016,
Mozilla Firefox, Thunderbird, Windows 10, Windows Server 2016, Tally, Adobe Creative
Cloud 7, inhouse tools and company website.
Remote access requirements: Any system within the network can be accessed by
administrators using the remote desktop application.
Performance Requirements: The network is designed to not only meet but also exceed the
future requirements of AML and is not supposed to have issues with direct or wireless access.
Quality of Service (QoS): The network of AML is segment for each of the three building and
hence is finetuned to provide quality service to devices of each building.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3. Description & Analysis of Current Setup with old setup
The previous network of AML composed of two buildings of the headquarters Building A and
Building B being connected through LAN and communications had to be made by accessing the
company web portal (refer to figure 4). In this network Building A operated 80 workstations and 14
printers of the software development department and marketing department combined.
The proposed network of AML comprises of three buildings (refer to figure 1). These are the
two buildings of the headquarters - Building A and Building B connected through a LAN network as
well as a third building – Building C or branch office which connects its devices through its own LAN
and communications which is connected to LAN of the headquarters to form a LAN to LAN wide area
network (WAN) (Leon, Parra and Bermudez 2018). In this network Building A operates 80
workstations, 50 laptops and 14 printers of the software development department and marketing
department combined. Building B operates 78 workstations, 0 laptops and 8 printers. Building C
operates 24 workstations 15 laptops and 7 printers.
Building B acts as the server farm where the web servers, email servers and file servers are
present (Sahinoglu 2018). Other servers in different floors of all buildings serve networking needs of
respective departments.
3.1 Data Transmission
The different cables used to establish the network are:
Fast-Ethernet: A Fast-Ethernet cable provides transmission of data rates around 100
megabytes/second (Dolezilek, Gordon and Anderson 2016). This cable is used to enable direct
connections from routers as also connection to wireless access points.
Gigabit-Ethernet: A Gigabit-Ethernet cable is used for providing technologies for transmission of
frames at the rate of 1 gigabyte/second (Swartz et al. 2017). This cable is generally used to distribute
the network from a switch to multiple devices present within the network.
3.2 Networking Hardware
The components that comprise this network can be 3 routers, 3 switches, 10 servers, 182
workstations and 35 printers (Wood et al. 2015). Each router facilitates network access to a specific
building or wing. The network is distributed by switches to the devices. Most servers are in Building
B, the server farm.
3.3 Physical Network Topologies
The various networking topologies used in the proposed network of AML
are:
Local Area Network (LAN) (refer to figure 2)
Wide Area Network (WAN) (refer to figure 3)
Wireless Local Area Network (WLAN)
The previous network of AML composed of two buildings of the headquarters Building A and
Building B being connected through LAN and communications had to be made by accessing the
company web portal (refer to figure 4). In this network Building A operated 80 workstations and 14
printers of the software development department and marketing department combined.
The proposed network of AML comprises of three buildings (refer to figure 1). These are the
two buildings of the headquarters - Building A and Building B connected through a LAN network as
well as a third building – Building C or branch office which connects its devices through its own LAN
and communications which is connected to LAN of the headquarters to form a LAN to LAN wide area
network (WAN) (Leon, Parra and Bermudez 2018). In this network Building A operates 80
workstations, 50 laptops and 14 printers of the software development department and marketing
department combined. Building B operates 78 workstations, 0 laptops and 8 printers. Building C
operates 24 workstations 15 laptops and 7 printers.
Building B acts as the server farm where the web servers, email servers and file servers are
present (Sahinoglu 2018). Other servers in different floors of all buildings serve networking needs of
respective departments.
3.1 Data Transmission
The different cables used to establish the network are:
Fast-Ethernet: A Fast-Ethernet cable provides transmission of data rates around 100
megabytes/second (Dolezilek, Gordon and Anderson 2016). This cable is used to enable direct
connections from routers as also connection to wireless access points.
Gigabit-Ethernet: A Gigabit-Ethernet cable is used for providing technologies for transmission of
frames at the rate of 1 gigabyte/second (Swartz et al. 2017). This cable is generally used to distribute
the network from a switch to multiple devices present within the network.
3.2 Networking Hardware
The components that comprise this network can be 3 routers, 3 switches, 10 servers, 182
workstations and 35 printers (Wood et al. 2015). Each router facilitates network access to a specific
building or wing. The network is distributed by switches to the devices. Most servers are in Building
B, the server farm.
3.3 Physical Network Topologies
The various networking topologies used in the proposed network of AML
are:
Local Area Network (LAN) (refer to figure 2)
Wide Area Network (WAN) (refer to figure 3)
Wireless Local Area Network (WLAN)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3.4 Description
3.5 Application Summary
Cisco ASA 5505 Firewall: To secure network components and function as firewall, the Cisco ASA
5505 is selected (Konikiewicz and Markowski 2017). This is a standalone device that provides
security for all parts of AML’s network.
Eset Nod32 Antivirus: This is an industry leading anti-virus solution installed on each system to
provide a second layer of security.
Cisco WebEx Meeting: A corporate communication application for video and meetings and is in use
among big, medium and small sized businesses. This application provides an interface tailor made to
support office work including greater details in user profiles.
Remote Desktop: RDC (Remote Desktop Connection) is Microsoft’s default connectivity tool for
remotely connecting other systems within the network.
Microsoft Office 2016: This suite of office applications is the latest offering from Microsoft and offers
maximum functionalities and compatibility.
Mozilla Firefox: This is a free and open source web browser that offers comprehensive set of
features offered by few other competing browsers.
Thunderbird: Thunderbird mail is another open source product from Mozilla offering multiplatform
support (Ghiglieri, Henhapl and Gerber 2018). The thunderbird mailing agent is both cost effective
and efficient in terms of performance with respect to competition.
Windows 10: Windows 10, the latest OS from Microsoft is popular its compatibility towards a broad
array of applications and secure framework with support for regular patches and updates. Based
upon the windows platform, it offers the most popular services tailor made for businesses and
educational institutes.
Windows Server 2016: This is the windows based operation specially built for serving server based
roles. Hence, this operating system is best suited for the various types of servers being used by AML
like web servers, mail servers, database servers and networking servers of building B.
Tally: The Tally Software refers to a leading accounting application used by businesses worldwide in
performing financial and accounting tasks as well as ERP related activities (Amin et al. 2016). It
handles almost all forms of accounting transactions in conjunction with GST calculation and billing,
compliance, banking and the like. For ERP, Tally.ERP 9 among leading and most widely used
software.
Adobe Creative Suite 6: This application package is used to perform creative work such as photo or
video editing, business card design and like (Oakes 2016). The Marketing department of AML makes
extensive use of the software for repeatedly producing creative content.
In house tools: These tools are the ones that are developed by the software development team for
automating task for own benefit and fast tracking of business processes. These automation tools are
3.5 Application Summary
Cisco ASA 5505 Firewall: To secure network components and function as firewall, the Cisco ASA
5505 is selected (Konikiewicz and Markowski 2017). This is a standalone device that provides
security for all parts of AML’s network.
Eset Nod32 Antivirus: This is an industry leading anti-virus solution installed on each system to
provide a second layer of security.
Cisco WebEx Meeting: A corporate communication application for video and meetings and is in use
among big, medium and small sized businesses. This application provides an interface tailor made to
support office work including greater details in user profiles.
Remote Desktop: RDC (Remote Desktop Connection) is Microsoft’s default connectivity tool for
remotely connecting other systems within the network.
Microsoft Office 2016: This suite of office applications is the latest offering from Microsoft and offers
maximum functionalities and compatibility.
Mozilla Firefox: This is a free and open source web browser that offers comprehensive set of
features offered by few other competing browsers.
Thunderbird: Thunderbird mail is another open source product from Mozilla offering multiplatform
support (Ghiglieri, Henhapl and Gerber 2018). The thunderbird mailing agent is both cost effective
and efficient in terms of performance with respect to competition.
Windows 10: Windows 10, the latest OS from Microsoft is popular its compatibility towards a broad
array of applications and secure framework with support for regular patches and updates. Based
upon the windows platform, it offers the most popular services tailor made for businesses and
educational institutes.
Windows Server 2016: This is the windows based operation specially built for serving server based
roles. Hence, this operating system is best suited for the various types of servers being used by AML
like web servers, mail servers, database servers and networking servers of building B.
Tally: The Tally Software refers to a leading accounting application used by businesses worldwide in
performing financial and accounting tasks as well as ERP related activities (Amin et al. 2016). It
handles almost all forms of accounting transactions in conjunction with GST calculation and billing,
compliance, banking and the like. For ERP, Tally.ERP 9 among leading and most widely used
software.
Adobe Creative Suite 6: This application package is used to perform creative work such as photo or
video editing, business card design and like (Oakes 2016). The Marketing department of AML makes
extensive use of the software for repeatedly producing creative content.
In house tools: These tools are the ones that are developed by the software development team for
automating task for own benefit and fast tracking of business processes. These automation tools are

typically based on MS Excel with the help of macros as well as several the visual studio dot net
framework.
Company web portal: The web portal of AML is built owned and hosted by the company themselves
and serves as an interface for communication within the network. In the older network this web
portal would facilitate communications between the two buildings by itself. In the proposed network
the web portal additionally enables communications with the branch office as well as the portable
devices like laptops from the campus premises of all three buildings.
4. Conclusions
To conclude the report successfully analyses the requirements and specifications of AML’s
network infrastructure which is undergoing expansion by opening a new branch office and presents
a requirements summary. To enable network access and communications between the two buildings
of the company headquarters as well as the new branch of AML, a restructuring and design of their
existing network infrastructure is conducted to form a wider network that can cater to the
requirements of all the three buildings. The report talks about the various business goals along with
the technological goals, all of which AML wishes to meet. Then after analysis of the respective
requirements, this report proceeds to describe further on why and by what means can the
redesigned network structure is able to meet all of company’s requirements in the future, by
comparing the various requirements with the functions of the new network and how it is achieved.
Thereafter the overall network layout gets thoroughly discussed as also the roles of critical parts of
the proposed network. From the study conducted, it is observed that this redesigned network
structure easily meets AML’s future requirements.
framework.
Company web portal: The web portal of AML is built owned and hosted by the company themselves
and serves as an interface for communication within the network. In the older network this web
portal would facilitate communications between the two buildings by itself. In the proposed network
the web portal additionally enables communications with the branch office as well as the portable
devices like laptops from the campus premises of all three buildings.
4. Conclusions
To conclude the report successfully analyses the requirements and specifications of AML’s
network infrastructure which is undergoing expansion by opening a new branch office and presents
a requirements summary. To enable network access and communications between the two buildings
of the company headquarters as well as the new branch of AML, a restructuring and design of their
existing network infrastructure is conducted to form a wider network that can cater to the
requirements of all the three buildings. The report talks about the various business goals along with
the technological goals, all of which AML wishes to meet. Then after analysis of the respective
requirements, this report proceeds to describe further on why and by what means can the
redesigned network structure is able to meet all of company’s requirements in the future, by
comparing the various requirements with the functions of the new network and how it is achieved.
Thereafter the overall network layout gets thoroughly discussed as also the roles of critical parts of
the proposed network. From the study conducted, it is observed that this redesigned network
structure easily meets AML’s future requirements.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

List of References
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and contagion. Journal of
Economic Theory, 166, pp.536-585.
Alatorre, D., Nasser, B., Rabani, A., Nagy-Sochacki, A., Dong, X., Axinte, D. and Kell, J., 2019.
Overcoming the Internet Latency Hurdle. IEEE ROBOTICS & AUTOMATION
MAGAZINE, 1070(9932/19).
Amin, M.K., Munira, S., Azhar, A., Amin, A. and Karim, M.T., 2016, December. Factors affecting
employees' behavioral intention to adopt accounting information system (AIS) in Bangladesh.
In 2016 19th International Conference on Computer and Information Technology (ICCIT) (pp. 501-
505). IEEE.
Aydin, M.N. and Ulger, C., 2016. Perception of IT Governance in an Emerging Market. Perception,
5(01).
Cao, Y.F., Cheung, S.W. and Yuk, T.I., 2015. A multiband slot antenna for GPS/WiMAX/WLAN
systems. IEEE Transactions on Antennas and Propagation, 63(3), pp.952-958.
Dawson, P., 2016. Five ways to hack and cheat with bring‐your‐own‐device electronic
examinations. British Journal of Educational Technology, 47(4), pp.592-600.
Dolezilek, D., Gordon, C. and Anderson, D., 2016, November. Fast Fault Detection Isolation and
Recovery in Ethernet Networks for Teleprotection and High-Speed Automation Applications. In
CIGRE Mexico International Colloquium, Mexico City.
Ghiglieri, M., Henhapl, B. and Gerber, N., 2018. Evaluation der Nutzbarkeit von PGP und S/MIME in
Thunderbird. Mensch und Computer 2018-Workshopband.
Konikiewicz, W. and Markowski, M., 2017. Analysis of Performance and Efficiency of Hardware and
Software Firewalls. Journal of Applied Computer Science Methods, 9(1), pp.49-63.
Leon, A.F.H., Parra, O.J.S. and Bermudez, G.M.T., 2018. LAN-WAN-LAN end-to-end Network
Simulation with NS2. International Journal of Applied Engineering Research, 13(17), pp.13136-13140.
Oakes, M.D., 2016. Testing the Viability of a 3D Workflow Using Only Adobe Creative Cloud.
Oostenbrink, J., 2015. Financial impact of downtime decrease and performance increase of IT
services (Bachelor's thesis, University of Twente).
Sahinoglu, M., 2018. CLOUD computing risk management for server farm repair rates, consumer‐
load cycle, server farm repair crew count, and additional servers.‐ Wiley Interdisciplinary Reviews:
Computational Statistics, 10(2), p.e1424.
Sun, M., Liu, Z., Qiu, J., Zhang, Z. and Sinclair, M., 2017
Swartz, M., Torres, D.J., Liberatore, S. and Millard, R., 2017. WHOI SDSL data-link project—ethernet
telemetry through sea cables. Journal of Atmospheric and Oceanic Technology, 34(2), pp.269-275.
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and contagion. Journal of
Economic Theory, 166, pp.536-585.
Alatorre, D., Nasser, B., Rabani, A., Nagy-Sochacki, A., Dong, X., Axinte, D. and Kell, J., 2019.
Overcoming the Internet Latency Hurdle. IEEE ROBOTICS & AUTOMATION
MAGAZINE, 1070(9932/19).
Amin, M.K., Munira, S., Azhar, A., Amin, A. and Karim, M.T., 2016, December. Factors affecting
employees' behavioral intention to adopt accounting information system (AIS) in Bangladesh.
In 2016 19th International Conference on Computer and Information Technology (ICCIT) (pp. 501-
505). IEEE.
Aydin, M.N. and Ulger, C., 2016. Perception of IT Governance in an Emerging Market. Perception,
5(01).
Cao, Y.F., Cheung, S.W. and Yuk, T.I., 2015. A multiband slot antenna for GPS/WiMAX/WLAN
systems. IEEE Transactions on Antennas and Propagation, 63(3), pp.952-958.
Dawson, P., 2016. Five ways to hack and cheat with bring‐your‐own‐device electronic
examinations. British Journal of Educational Technology, 47(4), pp.592-600.
Dolezilek, D., Gordon, C. and Anderson, D., 2016, November. Fast Fault Detection Isolation and
Recovery in Ethernet Networks for Teleprotection and High-Speed Automation Applications. In
CIGRE Mexico International Colloquium, Mexico City.
Ghiglieri, M., Henhapl, B. and Gerber, N., 2018. Evaluation der Nutzbarkeit von PGP und S/MIME in
Thunderbird. Mensch und Computer 2018-Workshopband.
Konikiewicz, W. and Markowski, M., 2017. Analysis of Performance and Efficiency of Hardware and
Software Firewalls. Journal of Applied Computer Science Methods, 9(1), pp.49-63.
Leon, A.F.H., Parra, O.J.S. and Bermudez, G.M.T., 2018. LAN-WAN-LAN end-to-end Network
Simulation with NS2. International Journal of Applied Engineering Research, 13(17), pp.13136-13140.
Oakes, M.D., 2016. Testing the Viability of a 3D Workflow Using Only Adobe Creative Cloud.
Oostenbrink, J., 2015. Financial impact of downtime decrease and performance increase of IT
services (Bachelor's thesis, University of Twente).
Sahinoglu, M., 2018. CLOUD computing risk management for server farm repair rates, consumer‐
load cycle, server farm repair crew count, and additional servers.‐ Wiley Interdisciplinary Reviews:
Computational Statistics, 10(2), p.e1424.
Sun, M., Liu, Z., Qiu, J., Zhang, Z. and Sinclair, M., 2017
Swartz, M., Torres, D.J., Liberatore, S. and Millard, R., 2017. WHOI SDSL data-link project—ethernet
telemetry through sea cables. Journal of Atmospheric and Oceanic Technology, 34(2), pp.269-275.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Taleb, T., Bagaa, M. and Ksentini, A., 2015, June. User mobility-aware virtual network function
placement for virtual 5G network infrastructure. In 2015 IEEE International Conference on
Communications (ICC) (pp. 3879-3884). IEEE.
Wood, T., Ramakrishnan, K.K., Hwang, J., Liu, G. and Zhang, W., 2015. Toward a software-based
network: integrating software defined networking and network function virtualization. IEEE Network,
29(3), pp.36-41.
placement for virtual 5G network infrastructure. In 2015 IEEE International Conference on
Communications (ICC) (pp. 3879-3884). IEEE.
Wood, T., Ramakrishnan, K.K., Hwang, J., Liu, G. and Zhang, W., 2015. Toward a software-based
network: integrating software defined networking and network function virtualization. IEEE Network,
29(3), pp.36-41.
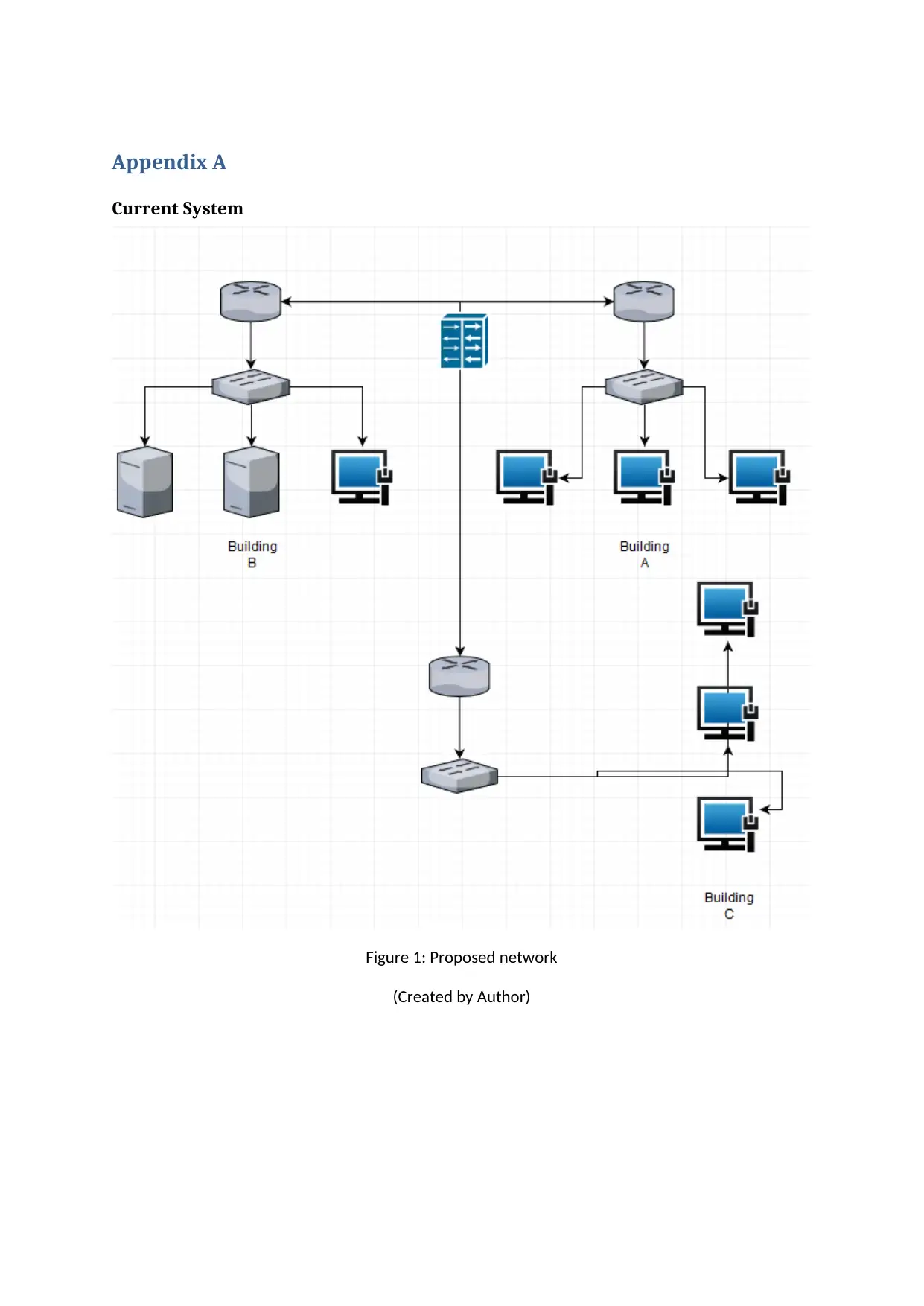
Appendix A
Current System
Figure 1: Proposed network
(Created by Author)
Current System
Figure 1: Proposed network
(Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



