Network Implementation for a New Medium Size Client Project
VerifiedAdded on 2020/04/21
|14
|2505
|88
Project
AI Summary
This project presents a comprehensive network implementation plan for a new medium-sized client. It begins with network design, considering the client's business requirements and utilizing existing network devices to minimize development costs. The project outlines the directory structure, including sites, organizational units, and groups, with an emphasis on Active Directory management and security. It specifies server configurations, detailing the number and location of virtual and physical servers, along with their roles and an approval sign-off document. The project includes a server build task list, a detailed server test plan with objectives, tasks, and responsibilities, and a server maintenance plan covering backups, database integrity checks, and index maintenance. Router specifications are provided, including the implementation plan, cable types, protocols, and traffic monitoring processes. A robust security policy plan is detailed, encompassing perimeter design, remote access, site-to-site links, defense in depth, security auditing, threat identification, risk analysis, and response procedures. User documentation is also addressed. The project concludes with a project sign-off document and discusses ongoing maintenance support, including user training and feedback programs. The project references relevant literature on network implementation and cloud deployment.

Running head: NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
Network Implementation for a New Medium Size Client
Name of the Student
Name of the University
Author’s Note
Network Implementation for a New Medium Size Client
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
Table of Contents
a. Network Design and Supporting Documents..................................................................3
b. Directory Structure..........................................................................................................3
i. Sites..............................................................................................................................3
ii. Organizational Units....................................................................................................3
iii. Groups........................................................................................................................4
c. Server Specification.........................................................................................................5
i. Number and Location of Virtual and physical Servers................................................5
ii. Roles of servers...........................................................................................................5
iii. Approval Sign off document......................................................................................5
d. Server build task list........................................................................................................6
e. Server Test Plan...............................................................................................................6
f. Server Maintenance Plan..................................................................................................7
g. Router Specification........................................................................................................8
i. Plan for Implementation...............................................................................................8
ii. Cable types required....................................................................................................9
iii. Protocols used.............................................................................................................9
iv. Traffic monitoring process.........................................................................................9
h. Security policy plan.........................................................................................................9
i. Perimeter Design..........................................................................................................9
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
Table of Contents
a. Network Design and Supporting Documents..................................................................3
b. Directory Structure..........................................................................................................3
i. Sites..............................................................................................................................3
ii. Organizational Units....................................................................................................3
iii. Groups........................................................................................................................4
c. Server Specification.........................................................................................................5
i. Number and Location of Virtual and physical Servers................................................5
ii. Roles of servers...........................................................................................................5
iii. Approval Sign off document......................................................................................5
d. Server build task list........................................................................................................6
e. Server Test Plan...............................................................................................................6
f. Server Maintenance Plan..................................................................................................7
g. Router Specification........................................................................................................8
i. Plan for Implementation...............................................................................................8
ii. Cable types required....................................................................................................9
iii. Protocols used.............................................................................................................9
iv. Traffic monitoring process.........................................................................................9
h. Security policy plan.........................................................................................................9
i. Perimeter Design..........................................................................................................9

2
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
ii. Remote Access..........................................................................................................10
iii. Site to site links........................................................................................................10
iv. Defense in depth.......................................................................................................10
v. Security Auditing and Monitoring.............................................................................10
vi. Threat identification.................................................................................................11
vii. Risk Analysis...........................................................................................................11
viii. Response Procedure...............................................................................................11
i. User Documentation.......................................................................................................11
j. Project Signoff................................................................................................................12
k. Ongoing maintenance Support......................................................................................12
Bibliography......................................................................................................................13
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
ii. Remote Access..........................................................................................................10
iii. Site to site links........................................................................................................10
iv. Defense in depth.......................................................................................................10
v. Security Auditing and Monitoring.............................................................................10
vi. Threat identification.................................................................................................11
vii. Risk Analysis...........................................................................................................11
viii. Response Procedure...............................................................................................11
i. User Documentation.......................................................................................................11
j. Project Signoff................................................................................................................12
k. Ongoing maintenance Support......................................................................................12
Bibliography......................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
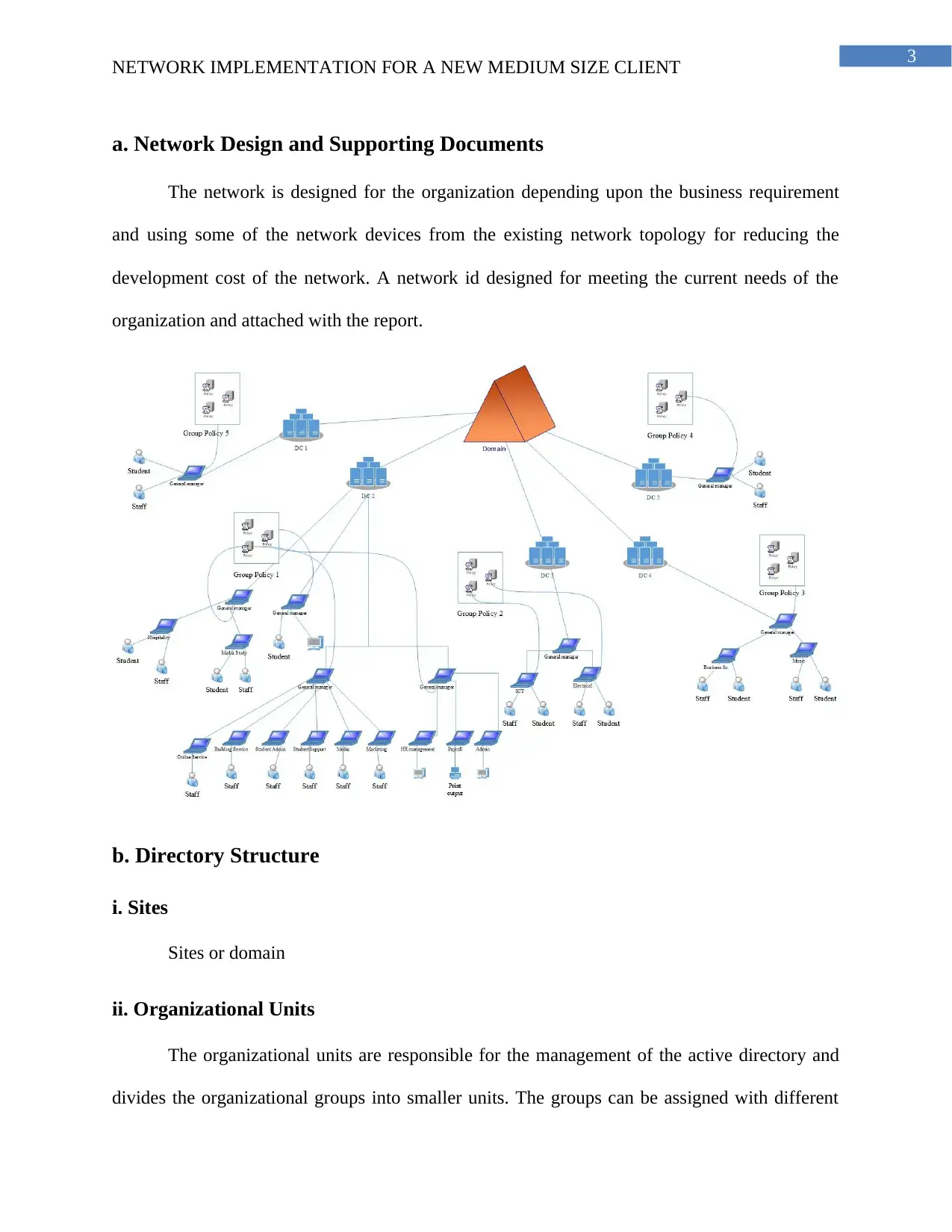
a. Network Design and Supporting Documents
The network is designed for the organization depending upon the business requirement
and using some of the network devices from the existing network topology for reducing the
development cost of the network. A network id designed for meeting the current needs of the
organization and attached with the report.
b. Directory Structure
i. Sites
Sites or domain
ii. Organizational Units
The organizational units are responsible for the management of the active directory and
divides the organizational groups into smaller units. The groups can be assigned with different
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
a. Network Design and Supporting Documents
The network is designed for the organization depending upon the business requirement
and using some of the network devices from the existing network topology for reducing the
development cost of the network. A network id designed for meeting the current needs of the
organization and attached with the report.
b. Directory Structure
i. Sites
Sites or domain
ii. Organizational Units
The organizational units are responsible for the management of the active directory and
divides the organizational groups into smaller units. The groups can be assigned with different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
permission for increasing the security of the system. The organizational units can also be used
for the deployment of application and enforce administrative controls on the objects of the active
directory.
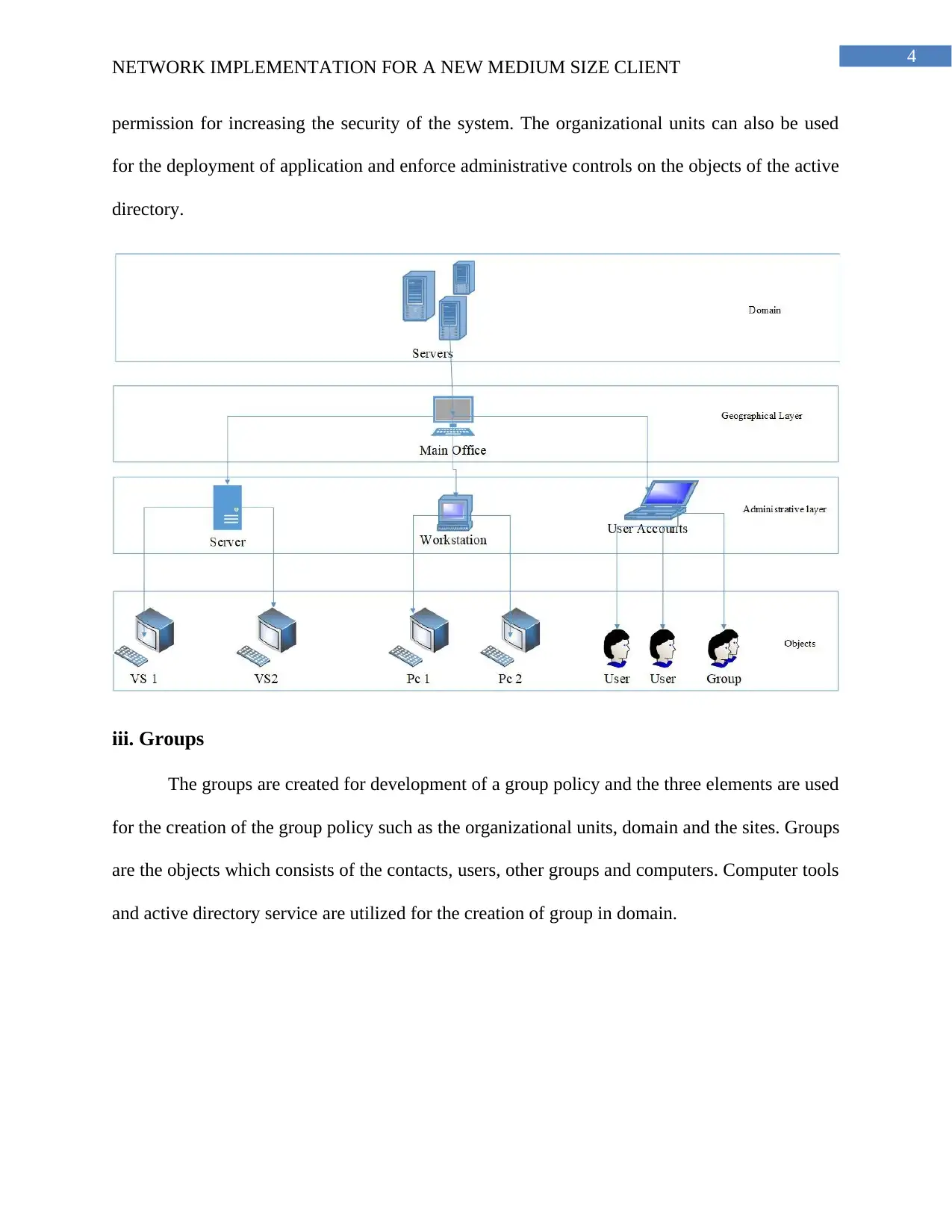
iii. Groups
The groups are created for development of a group policy and the three elements are used
for the creation of the group policy such as the organizational units, domain and the sites. Groups
are the objects which consists of the contacts, users, other groups and computers. Computer tools
and active directory service are utilized for the creation of group in domain.
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
permission for increasing the security of the system. The organizational units can also be used
for the deployment of application and enforce administrative controls on the objects of the active
directory.
iii. Groups
The groups are created for development of a group policy and the three elements are used
for the creation of the group policy such as the organizational units, domain and the sites. Groups
are the objects which consists of the contacts, users, other groups and computers. Computer tools
and active directory service are utilized for the creation of group in domain.
5
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
c. Server Specification
i. Number and Location of Virtual and physical Servers
Two high end physical server is installed in the network for handling the request of the
client and protecting the network resources from unauthorized users.
ii. Roles of servers
The main role of the server is to assign permission for the users accessing the internal
resources of the network. The resources are kept under the security group and permission are
assigned to the group of users for accessing the resources of the organization.
iii. Approval Sign off document
Prepared by Signature Date
Author’s Name
[Title]
[Organization] _________________________ _________________
Accepted by Signature Date
[Client Acceptor’s Name]
[Title]
[Organization] _________________________ _________________
Approved by Signature Date
[Client Approver’s Name]
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
c. Server Specification
i. Number and Location of Virtual and physical Servers
Two high end physical server is installed in the network for handling the request of the
client and protecting the network resources from unauthorized users.
ii. Roles of servers
The main role of the server is to assign permission for the users accessing the internal
resources of the network. The resources are kept under the security group and permission are
assigned to the group of users for accessing the resources of the organization.
iii. Approval Sign off document
Prepared by Signature Date
Author’s Name
[Title]
[Organization] _________________________ _________________
Accepted by Signature Date
[Client Acceptor’s Name]
[Title]
[Organization] _________________________ _________________
Approved by Signature Date
[Client Approver’s Name]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
[Title]
[Organization] _________________________ _________________
[Project Manager’s Name]
[Title]
[Organization] _________________________ _________________
d. Server build task list
Task 1: Configuration of the physical server
Task 2: Installation of the operating system
Task 3: Optimization of the operating system and performance tuning
e. Server Test Plan
Scope
The test plan is created for the testing the environment and scalability and flexibility to
meet the growing needs of the organization
Objectives
Testing the connectivity of the network
Testing the online connection
Testing the websites and for ensuring the accessibility
Testing the internal components for accessibility
Testing the external components
Testing the developer’s ability for accessing the development, production and
testing environment.
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
[Title]
[Organization] _________________________ _________________
[Project Manager’s Name]
[Title]
[Organization] _________________________ _________________
d. Server build task list
Task 1: Configuration of the physical server
Task 2: Installation of the operating system
Task 3: Optimization of the operating system and performance tuning
e. Server Test Plan
Scope
The test plan is created for the testing the environment and scalability and flexibility to
meet the growing needs of the organization
Objectives
Testing the connectivity of the network
Testing the online connection
Testing the websites and for ensuring the accessibility
Testing the internal components for accessibility
Testing the external components
Testing the developer’s ability for accessing the development, production and
testing environment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
Task and responsibility
Student_Name – test project manager
Harlan Vergara – System tester
General Approach
Different testing tools are used for testing the functionality and accessibility of the
servers and different testing tools are used such as FTP client browser, Dreamweaver, Homesites
4.5 and Workstations.
Different types of tests are executed for accessing the web sites and uploading files via
the ftp client. A mapping is done on the folders for the servers and a testing methodology is
selected for the selection of the testing procedures. The testing procedure is used accessing each
of the server using the ftp client and different files are uploaded into the server for testing the
connection and checking the group policy. The files are then transferred between different
workstation and using a virtual site created on each of the server. User accounts are created and
the users are divided into groups for the management of the accounts for each of the domain
created on the server.
System testing and case development strategy
The requirement are reviewed and each of the requirement are validated for testing the
system data and develop the network for the organization.
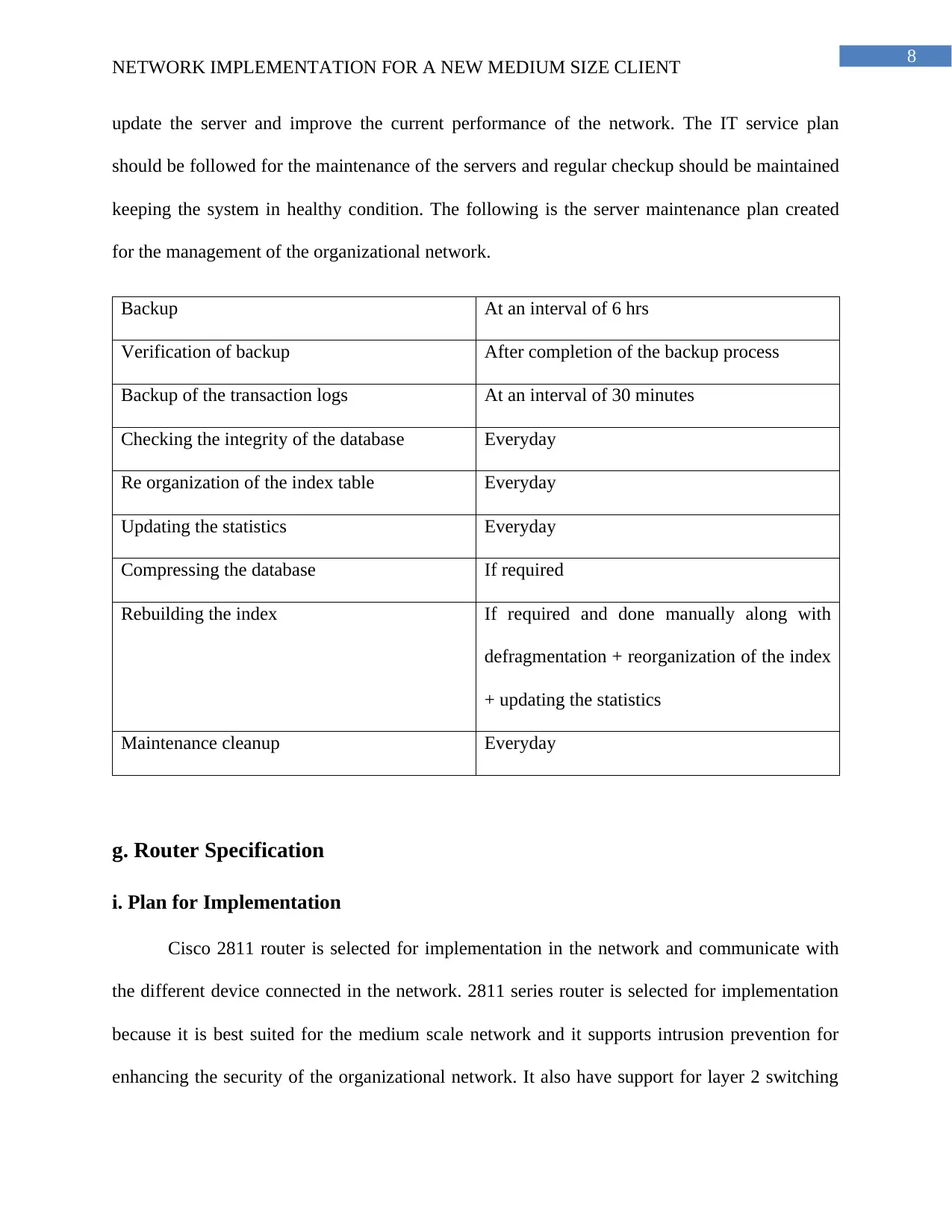
f. Server Maintenance Plan
It is important to create a server maintenance plan for ensuring that the network of the
organization are running smoothly and it is the responsibility of the network administrator to
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
Task and responsibility
Student_Name – test project manager
Harlan Vergara – System tester
General Approach
Different testing tools are used for testing the functionality and accessibility of the
servers and different testing tools are used such as FTP client browser, Dreamweaver, Homesites
4.5 and Workstations.
Different types of tests are executed for accessing the web sites and uploading files via
the ftp client. A mapping is done on the folders for the servers and a testing methodology is
selected for the selection of the testing procedures. The testing procedure is used accessing each
of the server using the ftp client and different files are uploaded into the server for testing the
connection and checking the group policy. The files are then transferred between different
workstation and using a virtual site created on each of the server. User accounts are created and
the users are divided into groups for the management of the accounts for each of the domain
created on the server.
System testing and case development strategy
The requirement are reviewed and each of the requirement are validated for testing the
system data and develop the network for the organization.
f. Server Maintenance Plan
It is important to create a server maintenance plan for ensuring that the network of the
organization are running smoothly and it is the responsibility of the network administrator to
8
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
update the server and improve the current performance of the network. The IT service plan
should be followed for the maintenance of the servers and regular checkup should be maintained
keeping the system in healthy condition. The following is the server maintenance plan created
for the management of the organizational network.
Backup At an interval of 6 hrs
Verification of backup After completion of the backup process
Backup of the transaction logs At an interval of 30 minutes
Checking the integrity of the database Everyday
Re organization of the index table Everyday
Updating the statistics Everyday
Compressing the database If required
Rebuilding the index If required and done manually along with
defragmentation + reorganization of the index
+ updating the statistics
Maintenance cleanup Everyday
g. Router Specification
i. Plan for Implementation
Cisco 2811 router is selected for implementation in the network and communicate with
the different device connected in the network. 2811 series router is selected for implementation
because it is best suited for the medium scale network and it supports intrusion prevention for
enhancing the security of the organizational network. It also have support for layer 2 switching
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
update the server and improve the current performance of the network. The IT service plan
should be followed for the maintenance of the servers and regular checkup should be maintained
keeping the system in healthy condition. The following is the server maintenance plan created
for the management of the organizational network.
Backup At an interval of 6 hrs
Verification of backup After completion of the backup process
Backup of the transaction logs At an interval of 30 minutes
Checking the integrity of the database Everyday
Re organization of the index table Everyday
Updating the statistics Everyday
Compressing the database If required
Rebuilding the index If required and done manually along with
defragmentation + reorganization of the index
+ updating the statistics
Maintenance cleanup Everyday
g. Router Specification
i. Plan for Implementation
Cisco 2811 router is selected for implementation in the network and communicate with
the different device connected in the network. 2811 series router is selected for implementation
because it is best suited for the medium scale network and it supports intrusion prevention for
enhancing the security of the organizational network. It also have support for layer 2 switching
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
and can be used for voip configuration in the network. The router is installed in the central
location and connected with a layer three switch for connecting the servers and the workstations
in different subnet and vlan.
ii. Cable types required
The bandwidth required for smooth operation of the device connected in the network
should be calculated for estimation of the cables to be used interconnecting the different
hardware device in the network. Cat 6a cable is selected for connecting the router with the switch
and the host and server with the switch.
iii. Protocols used
Distance vector routing protocol is used for the configuration of the router. The
configuration of the router with EIGRP protocol would automate the routing and the routers
would be able to share information with the neighbor router for sending and receiving data
packets in the network.
iv. Traffic monitoring process
Network protocol analyzer can be installed in a workstation for monitoring the data flow
in the network. Traffic can also be monitored from the router by entering the command monitor
traffic in the privilege EXEC mode of the router.
h. Security policy plan
i. Perimeter Design
It is required to be defined according to the security perimeters and assures that the
control and the security of changes made on the network device that can be utilized for securing
the network perimeter. The main purpose of the security perimeter design is confidentiality of
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
and can be used for voip configuration in the network. The router is installed in the central
location and connected with a layer three switch for connecting the servers and the workstations
in different subnet and vlan.
ii. Cable types required
The bandwidth required for smooth operation of the device connected in the network
should be calculated for estimation of the cables to be used interconnecting the different
hardware device in the network. Cat 6a cable is selected for connecting the router with the switch
and the host and server with the switch.
iii. Protocols used
Distance vector routing protocol is used for the configuration of the router. The
configuration of the router with EIGRP protocol would automate the routing and the routers
would be able to share information with the neighbor router for sending and receiving data
packets in the network.
iv. Traffic monitoring process
Network protocol analyzer can be installed in a workstation for monitoring the data flow
in the network. Traffic can also be monitored from the router by entering the command monitor
traffic in the privilege EXEC mode of the router.
h. Security policy plan
i. Perimeter Design
It is required to be defined according to the security perimeters and assures that the
control and the security of changes made on the network device that can be utilized for securing
the network perimeter. The main purpose of the security perimeter design is confidentiality of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
the organizational data. A DMZ zone is created for the installation of the servers and other
components in the network are separated using a firewall for securing the internet and the
network of the organization.
ii. Remote Access
Enabling remote access in the network helps the network administrator or other user to
connect with the organizational network. A vpn channel is used for allowing remote access in the
network and the server is configured with a username and password for enabling authentication
to access the resources of the network.
iii. Site to site links
A site to site link should be created between the servers installed in the network for
allowing the users to access the files and the traffic flow should be maintained. The traffic
between the dmz zones should be blocked and external connectivity in the network such as the
inbound or the out bound connection in the network should be created for securing the
communication link.
iv. Defense in depth
A firewall should be configured according to the business rules of the organization for
protecting the device from external agents. The architecture of the firewall should be compatible
with the protocols used for configuration of the network otherwise it can leave an open path for
the intruder to access the organizational resources.
v. Security Auditing and Monitoring
Security auditing is important for the configuration of the firewall policy and it should be
audited twice for adoption of the changes in the organizational network. The security policy
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
the organizational data. A DMZ zone is created for the installation of the servers and other
components in the network are separated using a firewall for securing the internet and the
network of the organization.
ii. Remote Access
Enabling remote access in the network helps the network administrator or other user to
connect with the organizational network. A vpn channel is used for allowing remote access in the
network and the server is configured with a username and password for enabling authentication
to access the resources of the network.
iii. Site to site links
A site to site link should be created between the servers installed in the network for
allowing the users to access the files and the traffic flow should be maintained. The traffic
between the dmz zones should be blocked and external connectivity in the network such as the
inbound or the out bound connection in the network should be created for securing the
communication link.
iv. Defense in depth
A firewall should be configured according to the business rules of the organization for
protecting the device from external agents. The architecture of the firewall should be compatible
with the protocols used for configuration of the network otherwise it can leave an open path for
the intruder to access the organizational resources.
v. Security Auditing and Monitoring
Security auditing is important for the configuration of the firewall policy and it should be
audited twice for adoption of the changes in the organizational network. The security policy

11
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
should be reviewed and necessary changes should be applied for completion of the security
auditing. Monitoring is done on the current flow of data and recognition of the patterns of attacks
on the network for securing changing the security policy of the network.
vi. Threat identification
A penetration testing should be done on the network for identification of the weak points
of the network. Patches and the encryption algorithm used for securing the network should be
evaluated for the identification of the threat in the network.
vii. Risk Analysis
A risk analysis is done on the network for identification of the threats and secure the
network from external agents. A security log should be maintained for protecting the network
and the daily activity should be reviewed for analyzing the risk arising in the network.
viii. Response Procedure
A risk management plan is created for responding to the risk arising in the deployment of
the network for the organization. The arising in the development of the organization should be
mitigated immediately in the development phase for the improvement of the quality of the
network. The security of the organization can be improved with the reduction of the risk.
i. User Documentation
The documentation is necessary for recording the network address plan and the
configuration of the device. The strategy followed for the development of the network solution
should be documented such that if any error occur in the network it can be resolved following the
procedure. The group of users should be segmented and different policy should be created for the
NETWORK IMPLEMENTATION FOR A NEW MEDIUM SIZE CLIENT
should be reviewed and necessary changes should be applied for completion of the security
auditing. Monitoring is done on the current flow of data and recognition of the patterns of attacks
on the network for securing changing the security policy of the network.
vi. Threat identification
A penetration testing should be done on the network for identification of the weak points
of the network. Patches and the encryption algorithm used for securing the network should be
evaluated for the identification of the threat in the network.
vii. Risk Analysis
A risk analysis is done on the network for identification of the threats and secure the
network from external agents. A security log should be maintained for protecting the network
and the daily activity should be reviewed for analyzing the risk arising in the network.
viii. Response Procedure
A risk management plan is created for responding to the risk arising in the deployment of
the network for the organization. The arising in the development of the organization should be
mitigated immediately in the development phase for the improvement of the quality of the
network. The security of the organization can be improved with the reduction of the risk.
i. User Documentation
The documentation is necessary for recording the network address plan and the
configuration of the device. The strategy followed for the development of the network solution
should be documented such that if any error occur in the network it can be resolved following the
procedure. The group of users should be segmented and different policy should be created for the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





