Comprehensive Network Management and Security Report for STP Limited
VerifiedAdded on 2020/05/11
|15
|3942
|175
Report
AI Summary
This report provides a comprehensive analysis of network management and security for STP Limited, a kitchen cabinet maker with multiple factories. It addresses project background, scope, and strategic alignment, focusing on the implementation of a new information system. The report explores network security measures, including securing data through people, products, and policies, as well as addressing ISP security and mobile device security concerns like WLAN attacks and BYOD risks. It also details a plan for hardware purchases, including acquisition strategies and the use of an asset register. Furthermore, the report covers business continuity planning with data backup, physical security, and stock control, alongside risk management strategies such as security policies and training. Recommendations are provided to enhance STP Limited's network infrastructure and ensure business continuity and data protection. The report is designed to provide insights on how to improve business operations and protect the organization's data.

Running head: NETWORK MANAGEMENT AND SECURITY
Network Management and Security
Name of the Student
Name of the University
Author’s note
Network Management and Security
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK MANAGEMENT AND SECURITY
Table of Contents
1.0. Project Background.............................................................................................................2
1.1. Network Project Background..........................................................................................2
1.2. Project enhancing the future growth of STP...................................................................3
1.2.1. Project scope............................................................................................................3
1.2.2. Project goal...............................................................................................................3
1.2.3. Strategic alignment of project..................................................................................4
2.0. Network Security................................................................................................................5
2.1. Securing data...................................................................................................................5
2.1.1. People, products, policies and procedures...............................................................5
2.1.2. ISP security and privacy considerations..................................................................5
2.2. Mobile device security....................................................................................................5
2.2.1. Wireless Local Area Network (WLAN) attacks......................................................5
2.2.2. BYOD risks..............................................................................................................6
3. Plan for hardware purchases..................................................................................................6
3.1. Acquisition of new hardware..........................................................................................6
3.2. End-user feedback and reviews.......................................................................................6
3.3. Purchasing strategies.......................................................................................................7
3.4. Asset register...................................................................................................................7
4.0. Business continuity.............................................................................................................8
4.1. Data Backup....................................................................................................................8
4.2. Physical Security.............................................................................................................9
4.3. Successful planning.........................................................................................................9
4.4. Stock Control system......................................................................................................9
5.0. Risk management..............................................................................................................10
5.1. Security Policy..............................................................................................................10
5.2. Training and awareness.................................................................................................10
5.3. Integration technology..................................................................................................10
6.0. Conclusions.......................................................................................................................11
7.0. Recommendations.............................................................................................................11
8.0. Bibliography......................................................................................................................12
Table of Contents
1.0. Project Background.............................................................................................................2
1.1. Network Project Background..........................................................................................2
1.2. Project enhancing the future growth of STP...................................................................3
1.2.1. Project scope............................................................................................................3
1.2.2. Project goal...............................................................................................................3
1.2.3. Strategic alignment of project..................................................................................4
2.0. Network Security................................................................................................................5
2.1. Securing data...................................................................................................................5
2.1.1. People, products, policies and procedures...............................................................5
2.1.2. ISP security and privacy considerations..................................................................5
2.2. Mobile device security....................................................................................................5
2.2.1. Wireless Local Area Network (WLAN) attacks......................................................5
2.2.2. BYOD risks..............................................................................................................6
3. Plan for hardware purchases..................................................................................................6
3.1. Acquisition of new hardware..........................................................................................6
3.2. End-user feedback and reviews.......................................................................................6
3.3. Purchasing strategies.......................................................................................................7
3.4. Asset register...................................................................................................................7
4.0. Business continuity.............................................................................................................8
4.1. Data Backup....................................................................................................................8
4.2. Physical Security.............................................................................................................9
4.3. Successful planning.........................................................................................................9
4.4. Stock Control system......................................................................................................9
5.0. Risk management..............................................................................................................10
5.1. Security Policy..............................................................................................................10
5.2. Training and awareness.................................................................................................10
5.3. Integration technology..................................................................................................10
6.0. Conclusions.......................................................................................................................11
7.0. Recommendations.............................................................................................................11
8.0. Bibliography......................................................................................................................12

2NETWORK MANAGEMENT AND SECURITY
1.0. Project Background
1.1. Network Project Background
STP Limited, the kitchen cabinet makers have four factories at Wollongong, Sydney,
Bathurst and Lithgow and they sell cupboards and drawer fronts to the customers. STP
limited has planned to update the existing information system in their premises and they have
planned to conduct the business activities with the aid of stock control system, with the aid of
accounting system. They have also planned to revolutionize the information system with the
customer management system and the website management system. The report has been
made focusing on the adaptation of the information system and the associated with the
privacy and security of the system. The investigation has been made and the various aspects
of the project like the scope of the project, the project requirements, the expectations related
to the project. Certain issues have been raised like unskilled workforce, inaccuracy related to
stock control, the inefficient product manufacturing and lacking workforce and productivity
as a whole. The organizations also have the very little learned workforce and very little
technical staff to serve the business requirements. STP Limited requires the more technical
staffs and they should be educated with the technical details so that they can contribute to the
business needs and can enrich the business activities.
1.2. Project enhancing the future growth of STP
1.2.1. Project scope
The project scope involves the installation and configuration of database system at the
locations Wollongong, Sydney, Bathurst and Lithgow. The Internet connectivity through
ADSL (Asymmetric Digital Subscriber Line) was connected with the aid of modem and with
the aid of switch and it involves the wireless technology concepts, this helps the staff to gets
connected to via BYOD (Bring Your Own Device). The aforesaid project has been developed
1.0. Project Background
1.1. Network Project Background
STP Limited, the kitchen cabinet makers have four factories at Wollongong, Sydney,
Bathurst and Lithgow and they sell cupboards and drawer fronts to the customers. STP
limited has planned to update the existing information system in their premises and they have
planned to conduct the business activities with the aid of stock control system, with the aid of
accounting system. They have also planned to revolutionize the information system with the
customer management system and the website management system. The report has been
made focusing on the adaptation of the information system and the associated with the
privacy and security of the system. The investigation has been made and the various aspects
of the project like the scope of the project, the project requirements, the expectations related
to the project. Certain issues have been raised like unskilled workforce, inaccuracy related to
stock control, the inefficient product manufacturing and lacking workforce and productivity
as a whole. The organizations also have the very little learned workforce and very little
technical staff to serve the business requirements. STP Limited requires the more technical
staffs and they should be educated with the technical details so that they can contribute to the
business needs and can enrich the business activities.
1.2. Project enhancing the future growth of STP
1.2.1. Project scope
The project scope involves the installation and configuration of database system at the
locations Wollongong, Sydney, Bathurst and Lithgow. The Internet connectivity through
ADSL (Asymmetric Digital Subscriber Line) was connected with the aid of modem and with
the aid of switch and it involves the wireless technology concepts, this helps the staff to gets
connected to via BYOD (Bring Your Own Device). The aforesaid project has been developed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK MANAGEMENT AND SECURITY
keeping in mind so that the project can go well with the mentioned four locations. The project
also focuses on the plans so that the employees of the enterprise can have the requisite
knowledge to enhance their business operations. Currently, they have one technical staff. The
part-time technology has been given to handle the website and all the associated web
services.
1.2.2. Project goal
The project goal involves catering the tools to the management team and the internal
staff of STP Limited to embellish the business activities and makes work relatively easy for
the customer and the clients’ base of the enterprise. The goal of the project is to provide the
enterprise with the skilled technical so that they can help. The project is also focused on the
required network equipment that can increase the productivity of the customer and clients
focused applications. The project’s goal is to enhance the relationship of the enterprise with
the customers and the clients with the implementation of a CRM system along with
development and improvement of the website to support the enterprise’s products.
1.2.3. Strategic alignment of project
There are certain risks as well as benefits while adopting a new technology in the
enterprise. That is why the management team must analyse the strength, weakness,
challenges and the threats. Now, as I am the information systems manager of STP it is my
duty to make the SWOT analysis of the company’s business process and will address the
benefits that the information system has to offer the STP. The strength of the information
system to STP Limited is it has a large customer base, the cloud computing can serve them
well, moreover, they have the dedicated employees who are willing to learn. The weakness is
that the employees are not technically skills and there are vulnerabilities related to insider
threats. There are multiple opportunities for STP Limited and they are communicating with
customers with the aid of advanced cloud-based information system, the integration of
keeping in mind so that the project can go well with the mentioned four locations. The project
also focuses on the plans so that the employees of the enterprise can have the requisite
knowledge to enhance their business operations. Currently, they have one technical staff. The
part-time technology has been given to handle the website and all the associated web
services.
1.2.2. Project goal
The project goal involves catering the tools to the management team and the internal
staff of STP Limited to embellish the business activities and makes work relatively easy for
the customer and the clients’ base of the enterprise. The goal of the project is to provide the
enterprise with the skilled technical so that they can help. The project is also focused on the
required network equipment that can increase the productivity of the customer and clients
focused applications. The project’s goal is to enhance the relationship of the enterprise with
the customers and the clients with the implementation of a CRM system along with
development and improvement of the website to support the enterprise’s products.
1.2.3. Strategic alignment of project
There are certain risks as well as benefits while adopting a new technology in the
enterprise. That is why the management team must analyse the strength, weakness,
challenges and the threats. Now, as I am the information systems manager of STP it is my
duty to make the SWOT analysis of the company’s business process and will address the
benefits that the information system has to offer the STP. The strength of the information
system to STP Limited is it has a large customer base, the cloud computing can serve them
well, moreover, they have the dedicated employees who are willing to learn. The weakness is
that the employees are not technically skills and there are vulnerabilities related to insider
threats. There are multiple opportunities for STP Limited and they are communicating with
customers with the aid of advanced cloud-based information system, the integration of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK MANAGEMENT AND SECURITY
information system and the empowerment of workforce. The threats that are related are
sensitive information leaks as their security framework is relatively weak now.
Table 2.4 SWOT analysis of STP Limited network project
Internal
POSITIVE NEGATIVE
Strengths Weaknesses
Large customer base
Enhanced sales targets
The cloud-based applications
Dedicated employees
Insider Threat
Employees are not technically skilled
No specific rules and procedure
External Opportunities Threats
Communication with the customers
via information system
The integration of information system
The workforce empowerment
Sensitive personal data leaks
2.0. Network Security
2.1. Securing data
STP Limited has implied the information system in their premises and they have got
some benefits till now. The information security must be managed to by applying various
strategies and the strategies can be internal as well as external (Ciampa 2015). The internal
layer must be implied in the layers which involve the establishment of regulations and the
policies, people and the products they made in their premises.
2.1.1. People, products, policies and procedures
The information system at STP Limited highly relies upon the Internet so marinating
certain strategies, policies and procedures will help them to conduct the business operations
(Ciampa 2015). The rules regarding the security policy aspects help to provide security and
that can help to carry out the business operations securely and safely (Queensland
Government 2016). The policies can help to store, access data and store data.
information system and the empowerment of workforce. The threats that are related are
sensitive information leaks as their security framework is relatively weak now.
Table 2.4 SWOT analysis of STP Limited network project
Internal
POSITIVE NEGATIVE
Strengths Weaknesses
Large customer base
Enhanced sales targets
The cloud-based applications
Dedicated employees
Insider Threat
Employees are not technically skilled
No specific rules and procedure
External Opportunities Threats
Communication with the customers
via information system
The integration of information system
The workforce empowerment
Sensitive personal data leaks
2.0. Network Security
2.1. Securing data
STP Limited has implied the information system in their premises and they have got
some benefits till now. The information security must be managed to by applying various
strategies and the strategies can be internal as well as external (Ciampa 2015). The internal
layer must be implied in the layers which involve the establishment of regulations and the
policies, people and the products they made in their premises.
2.1.1. People, products, policies and procedures
The information system at STP Limited highly relies upon the Internet so marinating
certain strategies, policies and procedures will help them to conduct the business operations
(Ciampa 2015). The rules regarding the security policy aspects help to provide security and
that can help to carry out the business operations securely and safely (Queensland
Government 2016). The policies can help to store, access data and store data.

5NETWORK MANAGEMENT AND SECURITY
2.1.2. ISP security and privacy considerations
STP Limited is dependent on the Internet to carry out the business activities and he
secure WAN can be able to provide them with the secured service from the vulnerable threats
like malware and virus. The BigPond Network has the capability to cater the secured network
by implementing the security feature that can diminish the side effects of security breaches
(Telstra 2016). The ISP has the capability so that the payment system can be conducted in the
most secure way.
2.2. Mobile device security
2.2.1. Wireless Local Area Network (WLAN) attacks
The wireless networking is comparatively risky; the employees of the organisations
connect to the devices like laptops via wireless mediums. The intruders can take the
advantage of the weak network connectivity can gain entry into the system and can steal the
vital information of the database (Gupta & Hammond 2005). The attacks related to WLAN
attacks can be rooted out by appropriate configuration of the employees and the training
programs related to employees.
2.2.2. BYOD risks
BYOD risks can enhance the financial risks, the devices are shared among the users
and this can disclose the sensitive information of the system. The other types of concerns that
are associated with are the malicious activities associated with the software and the with the
operating system (Ciampa 2015). BYOD should be implemented ineffective way to safeguard
the operations safely with any breaches.
2.1.2. ISP security and privacy considerations
STP Limited is dependent on the Internet to carry out the business activities and he
secure WAN can be able to provide them with the secured service from the vulnerable threats
like malware and virus. The BigPond Network has the capability to cater the secured network
by implementing the security feature that can diminish the side effects of security breaches
(Telstra 2016). The ISP has the capability so that the payment system can be conducted in the
most secure way.
2.2. Mobile device security
2.2.1. Wireless Local Area Network (WLAN) attacks
The wireless networking is comparatively risky; the employees of the organisations
connect to the devices like laptops via wireless mediums. The intruders can take the
advantage of the weak network connectivity can gain entry into the system and can steal the
vital information of the database (Gupta & Hammond 2005). The attacks related to WLAN
attacks can be rooted out by appropriate configuration of the employees and the training
programs related to employees.
2.2.2. BYOD risks
BYOD risks can enhance the financial risks, the devices are shared among the users
and this can disclose the sensitive information of the system. The other types of concerns that
are associated with are the malicious activities associated with the software and the with the
operating system (Ciampa 2015). BYOD should be implemented ineffective way to safeguard
the operations safely with any breaches.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK MANAGEMENT AND SECURITY
3. Plan for hardware purchases
3.1. Acquisition of new hardware
The new hardware has a lot to offer to STP Limited. The new hardware can be helpful
to manage the company assets; it can help to adopt the latest information technology
innovation and thus can help STP to prepare the strategies, procedures and the policies to
progress further (Batenburg et al 2015). The infrastructure will assist the staff to diminish the
disruption within, diminish the production issue.
3.2. End-user feedback and reviews
The software is advancing day by day and is getting revolutionized. It may happen
that the software applications may not comply with the outdated hardware existing within the
organization. The security breaches can occur even when the applications are downloaded
from the sites which are not verified and are not trustworthy. Those files run in the
background and are vulnerable (Crawford et al 2005). Thus antivirus software must be
installed and hardware must be brand new to get the best outcome. The end users have the
required scope to evaluate the risks and based on that the management team can take the best
decision that can assist in taking the best decision for the business (Haring ND).
3.3. Purchasing strategies
STP Limited needs forward planning and they must save money to purchase the latest
hardware for the business activity. The members of the enterprise must communicate with
each other and must communicate with each other and must make a better strategy to enhance
the business. They should recognize the suppliers and should understand the requisites of the
business via the asset register, they should choose the hardware for the enterprise’s
betterment.
3. Plan for hardware purchases
3.1. Acquisition of new hardware
The new hardware has a lot to offer to STP Limited. The new hardware can be helpful
to manage the company assets; it can help to adopt the latest information technology
innovation and thus can help STP to prepare the strategies, procedures and the policies to
progress further (Batenburg et al 2015). The infrastructure will assist the staff to diminish the
disruption within, diminish the production issue.
3.2. End-user feedback and reviews
The software is advancing day by day and is getting revolutionized. It may happen
that the software applications may not comply with the outdated hardware existing within the
organization. The security breaches can occur even when the applications are downloaded
from the sites which are not verified and are not trustworthy. Those files run in the
background and are vulnerable (Crawford et al 2005). Thus antivirus software must be
installed and hardware must be brand new to get the best outcome. The end users have the
required scope to evaluate the risks and based on that the management team can take the best
decision that can assist in taking the best decision for the business (Haring ND).
3.3. Purchasing strategies
STP Limited needs forward planning and they must save money to purchase the latest
hardware for the business activity. The members of the enterprise must communicate with
each other and must communicate with each other and must make a better strategy to enhance
the business. They should recognize the suppliers and should understand the requisites of the
business via the asset register, they should choose the hardware for the enterprise’s
betterment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
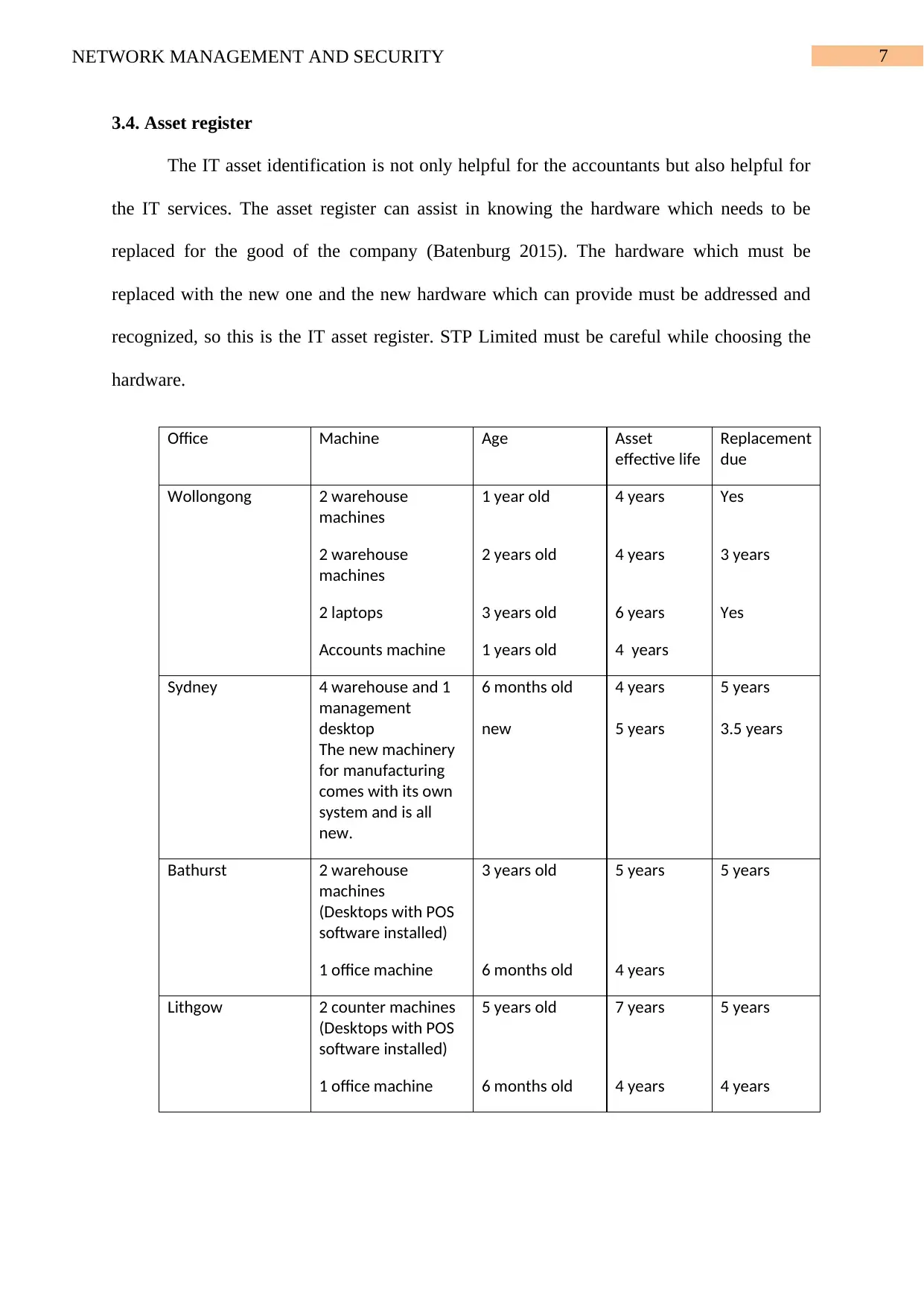
7NETWORK MANAGEMENT AND SECURITY
3.4. Asset register
The IT asset identification is not only helpful for the accountants but also helpful for
the IT services. The asset register can assist in knowing the hardware which needs to be
replaced for the good of the company (Batenburg 2015). The hardware which must be
replaced with the new one and the new hardware which can provide must be addressed and
recognized, so this is the IT asset register. STP Limited must be careful while choosing the
hardware.
Office Machine Age Asset
effective life
Replacement
due
Wollongong 2 warehouse
machines
1 year old 4 years Yes
2 warehouse
machines
2 years old 4 years 3 years
2 laptops 3 years old 6 years Yes
Accounts machine 1 years old 4 years
Sydney 4 warehouse and 1
management
desktop
The new machinery
for manufacturing
comes with its own
system and is all
new.
6 months old
new
4 years
5 years
5 years
3.5 years
Bathurst 2 warehouse
machines
(Desktops with POS
software installed)
3 years old 5 years 5 years
1 office machine 6 months old 4 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 7 years 5 years
1 office machine 6 months old 4 years 4 years
3.4. Asset register
The IT asset identification is not only helpful for the accountants but also helpful for
the IT services. The asset register can assist in knowing the hardware which needs to be
replaced for the good of the company (Batenburg 2015). The hardware which must be
replaced with the new one and the new hardware which can provide must be addressed and
recognized, so this is the IT asset register. STP Limited must be careful while choosing the
hardware.
Office Machine Age Asset
effective life
Replacement
due
Wollongong 2 warehouse
machines
1 year old 4 years Yes
2 warehouse
machines
2 years old 4 years 3 years
2 laptops 3 years old 6 years Yes
Accounts machine 1 years old 4 years
Sydney 4 warehouse and 1
management
desktop
The new machinery
for manufacturing
comes with its own
system and is all
new.
6 months old
new
4 years
5 years
5 years
3.5 years
Bathurst 2 warehouse
machines
(Desktops with POS
software installed)
3 years old 5 years 5 years
1 office machine 6 months old 4 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 7 years 5 years
1 office machine 6 months old 4 years 4 years

8NETWORK MANAGEMENT AND SECURITY
4.0. Business continuity
The information system via installation and configuration of the cloud-based apps
MYOB, TradeGecko and Salesforce can get the edge by which they can embellish their
business activities (Ciampa 2015). The data backup, succession planning are the three topics
that will be discussed in the later sections so these subsections will cater STP Limited the
better overview how the cloud applications can prosper their business growth.
4.1. Data Backup
STP Limited has planned to adopt the cloud technology, the cloud-based SaaS apps
that can help the enterprise to store the files of the enterprise as backups, thus STP Limited
can use the cloud backups whenever required, this can help to gain the competitive edge they
require. They can process the data stored in the cloud and can even store the modified files as
a backup (Ciampa 2015). This can reduce the cost of the cost of the enterprise as they do not
have to buy the server to store the files as a backup and there is also less chance of virus
attack because of the cloud vendor advanced technology.
4.2. Physical Security
The cloud-based applications can even help to overcome the challenges associated
with the physical security issues, the physical issues depicted here are network failures, road
blockages and flood and power outages. The cloud vendor will store the data for the
enterprise so they do not have to face heavy consequences, their devices can get damaged but
the data will remain will safe (Greitzer & Hohimer 2011). The cloud technology can protect
from the insider threats as well.
4.3. Successful planning
It may happen any employee of the company can get injured, can suffer from severe
illness., even the member can resign from the job or may get died, whatever may be the
4.0. Business continuity
The information system via installation and configuration of the cloud-based apps
MYOB, TradeGecko and Salesforce can get the edge by which they can embellish their
business activities (Ciampa 2015). The data backup, succession planning are the three topics
that will be discussed in the later sections so these subsections will cater STP Limited the
better overview how the cloud applications can prosper their business growth.
4.1. Data Backup
STP Limited has planned to adopt the cloud technology, the cloud-based SaaS apps
that can help the enterprise to store the files of the enterprise as backups, thus STP Limited
can use the cloud backups whenever required, this can help to gain the competitive edge they
require. They can process the data stored in the cloud and can even store the modified files as
a backup (Ciampa 2015). This can reduce the cost of the cost of the enterprise as they do not
have to buy the server to store the files as a backup and there is also less chance of virus
attack because of the cloud vendor advanced technology.
4.2. Physical Security
The cloud-based applications can even help to overcome the challenges associated
with the physical security issues, the physical issues depicted here are network failures, road
blockages and flood and power outages. The cloud vendor will store the data for the
enterprise so they do not have to face heavy consequences, their devices can get damaged but
the data will remain will safe (Greitzer & Hohimer 2011). The cloud technology can protect
from the insider threats as well.
4.3. Successful planning
It may happen any employee of the company can get injured, can suffer from severe
illness., even the member can resign from the job or may get died, whatever may be the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK MANAGEMENT AND SECURITY
reason the organization must be ready to face the consequences. They have to prepare a
suitable successor for the job role (Ciampa 2015). The successor must have the required
knowledge and the expertise to understand the business requirements and should be ready to
take necessary actions that can assist the team to take the correct decision.
4.4. Stock Control system
The website of STP Limited must be developed in such a way so that the customers
can view all the products available. The cupboard, the drawer fronts having different colours,
different textures, and different styles must be showcased and the data must be stored in the
cloud and along with that, the data must be modified whenever required. The stock
availability must be kept updated all the time (George 2013). Once any products get ordered
shipped they must update the cloud database so that the customers and the employees across
the four STP Limited factories can know the availability of stock.
5.0. Risk management
The technology adoption can give rise to various concerns from various kinds of
threats, risks and the privacy issues and thus STP Limited must be responsive and should
adopt the security model that can embellish the growth of the company (Gupta & Hammond
2005). All these security aspects can be well handled by the risk mitigation, risk avoidance
and the risk transference.
5.1. Security Policy
The security policies must be implemented to protect and secure the assets and can
cater a general outline that can embellish the business growth. The security policies can act as
a tool to develop a culture that can benefit the organization to securely conduct business
activities. The employees must have the sound knowledge of the security procedures so that
they can discover the security breaches and can take actions immediately (Ciampa 2015). The
reason the organization must be ready to face the consequences. They have to prepare a
suitable successor for the job role (Ciampa 2015). The successor must have the required
knowledge and the expertise to understand the business requirements and should be ready to
take necessary actions that can assist the team to take the correct decision.
4.4. Stock Control system
The website of STP Limited must be developed in such a way so that the customers
can view all the products available. The cupboard, the drawer fronts having different colours,
different textures, and different styles must be showcased and the data must be stored in the
cloud and along with that, the data must be modified whenever required. The stock
availability must be kept updated all the time (George 2013). Once any products get ordered
shipped they must update the cloud database so that the customers and the employees across
the four STP Limited factories can know the availability of stock.
5.0. Risk management
The technology adoption can give rise to various concerns from various kinds of
threats, risks and the privacy issues and thus STP Limited must be responsive and should
adopt the security model that can embellish the growth of the company (Gupta & Hammond
2005). All these security aspects can be well handled by the risk mitigation, risk avoidance
and the risk transference.
5.1. Security Policy
The security policies must be implemented to protect and secure the assets and can
cater a general outline that can embellish the business growth. The security policies can act as
a tool to develop a culture that can benefit the organization to securely conduct business
activities. The employees must have the sound knowledge of the security procedures so that
they can discover the security breaches and can take actions immediately (Ciampa 2015). The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK MANAGEMENT AND SECURITY
privilege, the incident management and the change management will assist and support the
security policies so that the security inside the organization can be ensured.
5.2. Training and awareness
The risk model must identify the three aspects that can prove to be effective to STP
Limited. The risk model addresses the possible risks that must be identified and detected,
again, the risks prevention techniques must be applied to mitigate the risks associated within
and lastly the corrective measures that can help to rectify the solution (Bandyopadhyay et al
2011). Lastly, the employees of STP must be learned and they should have the desired
knowledge to handle the threat scenario and data breaches efficiently.
5.3. Integration technology
The information integration technology can serve the purpose really well. Via the
SaaS model and the PaaS model, greater benefits can be gained. PaaS involves the
independent software vendors that have the capability to build and execute applications. In
this scenario, Slaesforce.com provides the SaaS functionality to STP Limited like the agile
effective advanced cloud solutions and the advanced security solutions (Chang, Dillon & Wu
2010). However, there still remains the risk of data breaches, the security issues, the
interoperability issues have been highlighted and the employees and the management team
must make a service level agreement to grant the required and the desired service.
6.0. Conclusions
It can be concluded from the above discourse that the security control measures can
aid the adoption of information system in STP Limited. The security breaches have been
highlighted throughout the report. The risks related to wireless LAN and the BYOD devices
have been showcased. The possible solutions to mitigate those risks have been discussed as
well in the report as well. The three aspects – policies, people and the products can
privilege, the incident management and the change management will assist and support the
security policies so that the security inside the organization can be ensured.
5.2. Training and awareness
The risk model must identify the three aspects that can prove to be effective to STP
Limited. The risk model addresses the possible risks that must be identified and detected,
again, the risks prevention techniques must be applied to mitigate the risks associated within
and lastly the corrective measures that can help to rectify the solution (Bandyopadhyay et al
2011). Lastly, the employees of STP must be learned and they should have the desired
knowledge to handle the threat scenario and data breaches efficiently.
5.3. Integration technology
The information integration technology can serve the purpose really well. Via the
SaaS model and the PaaS model, greater benefits can be gained. PaaS involves the
independent software vendors that have the capability to build and execute applications. In
this scenario, Slaesforce.com provides the SaaS functionality to STP Limited like the agile
effective advanced cloud solutions and the advanced security solutions (Chang, Dillon & Wu
2010). However, there still remains the risk of data breaches, the security issues, the
interoperability issues have been highlighted and the employees and the management team
must make a service level agreement to grant the required and the desired service.
6.0. Conclusions
It can be concluded from the above discourse that the security control measures can
aid the adoption of information system in STP Limited. The security breaches have been
highlighted throughout the report. The risks related to wireless LAN and the BYOD devices
have been showcased. The possible solutions to mitigate those risks have been discussed as
well in the report as well. The three aspects – policies, people and the products can

11NETWORK MANAGEMENT AND SECURITY
effectively root out the security breaches. Till now, any successful implementation has been
planned by which the company can move forward or move ahead, the report will help STP
Limited to know what measures should be taken to flourish the business operations.
7.0. Recommendations
i. STP Limited must implement policies and procedures properly in their premises to carry
out the business activities smoothly.
ii. They should conduct the business activities via secured network; they should wait until the
secured network concepts are applied like rogue discovery tools and the portal access points.
iii. The asset register must be well maintained. STP Limited should be careful about the risk
management procedures.
iv. They must keep back up of the necessary financial data file and the customers’ data files
safely and securely in their premises.
v. The employees must be trained so that they can deliver the best services and the training ca
also to recognize the threats beforehand.
vi. The stock control must be strengthened by the information technology assistance. The
website must be developed in such a way that the website will showcase all the cupboard and
drawer fronts products at a glance, once a customer order a product, they must proactively
update the website, in this way both the customers and STP Limited can know the availability
of products across the four locations.
effectively root out the security breaches. Till now, any successful implementation has been
planned by which the company can move forward or move ahead, the report will help STP
Limited to know what measures should be taken to flourish the business operations.
7.0. Recommendations
i. STP Limited must implement policies and procedures properly in their premises to carry
out the business activities smoothly.
ii. They should conduct the business activities via secured network; they should wait until the
secured network concepts are applied like rogue discovery tools and the portal access points.
iii. The asset register must be well maintained. STP Limited should be careful about the risk
management procedures.
iv. They must keep back up of the necessary financial data file and the customers’ data files
safely and securely in their premises.
v. The employees must be trained so that they can deliver the best services and the training ca
also to recognize the threats beforehand.
vi. The stock control must be strengthened by the information technology assistance. The
website must be developed in such a way that the website will showcase all the cupboard and
drawer fronts products at a glance, once a customer order a product, they must proactively
update the website, in this way both the customers and STP Limited can know the availability
of products across the four locations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





