Network Management Solution Report - Data Capture and Storage
VerifiedAdded on 2023/04/26
|12
|1605
|321
Report
AI Summary
This report presents a network management solution designed to capture and store data from a range of devices, including routers, printers, switches, web servers, and personal computers. The project focuses on the design and implementation of a system that utilizes IP addressing and SNMP for data retrieval and management. The report outlines the scenario, which involves device configuration, fault management, and performance monitoring. It details the different operations such as Get, Get Request, Set, Trap, Inform and Response. The report also explores IP addressing and managed objects (static and dynamic), as well as the specific data points to be collected from each device. The design includes the use of MIBs (Management Information Bases) and network strings for secure access. The report concludes by summarizing the project's aim, which is to design and implement an effective network management solution capable of capturing and storing data from various devices, including system descriptions, interface details, and CPU usage metrics. The report also covers the device’s system like System Name, System Location, System Contact and Interface Number, Interface Table. The report provides an overview of network management tools and the significance of data collection and organization for device behavior modification.

University
*** Semester
Network Management
Student Name:
Register Number:
Submission Date:
*** Semester
Network Management
Student Name:
Register Number:
Submission Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The spotlight of this project is on the network management solutions. This report ensures to
review and examine the data capturing and data storage from various devices and its relation
with network management. Network management has the various usages such as it can be used
in some tools, for supervising the devices, for the execution of data and setup. Subsequently, the
network management could be used in the network management tools that are simple, especially
the ones which can be used to collect and sort out the data of the devices on the IP address
network and to send the server necessary requests, then collect the data for changing the
behaviour of the device. The SNMP could be utilized by the manager for exchanging the requests
with the web server and the router. The investigation is on how the manager device could retrieve
the data and request the manager with the help of TCP and IP data by connecting with the port’s
IP address.
The spotlight of this project is on the network management solutions. This report ensures to
review and examine the data capturing and data storage from various devices and its relation
with network management. Network management has the various usages such as it can be used
in some tools, for supervising the devices, for the execution of data and setup. Subsequently, the
network management could be used in the network management tools that are simple, especially
the ones which can be used to collect and sort out the data of the devices on the IP address
network and to send the server necessary requests, then collect the data for changing the
behaviour of the device. The SNMP could be utilized by the manager for exchanging the requests
with the web server and the router. The investigation is on how the manager device could retrieve
the data and request the manager with the help of TCP and IP data by connecting with the port’s
IP address.

Table of Contents
1. Introduction of the Scenario.................................................................................................................................... 1
1.1 Aim..................................................................................................................................................................... 1
2. IP Addressing.......................................................................................................................................................... 2
2.1 Static and Dynamic Managed Objects.................................................................................................................2
2.2 Design................................................................................................................................................................. 4
2.3 Router................................................................................................................................................................. 4
2.4 Printer................................................................................................................................................................ 5
2.5 Switch................................................................................................................................................................. 5
2.6 Web Server......................................................................................................................................................... 5
2.7 Personal Computer............................................................................................................................................. 5
3. Conclusion............................................................................................................................................................... 5
1. Introduction of the Scenario.................................................................................................................................... 1
1.1 Aim..................................................................................................................................................................... 1
2. IP Addressing.......................................................................................................................................................... 2
2.1 Static and Dynamic Managed Objects.................................................................................................................2
2.2 Design................................................................................................................................................................. 4
2.3 Router................................................................................................................................................................. 4
2.4 Printer................................................................................................................................................................ 5
2.5 Switch................................................................................................................................................................. 5
2.6 Web Server......................................................................................................................................................... 5
2.7 Personal Computer............................................................................................................................................. 5
3. Conclusion............................................................................................................................................................... 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction of the Scenario
This project’s scenario can be specified on the network management device. It follows
the following stages such as Device Configuration management, Device Fault management,
Device accounting management, Device performance management and Device security
management. The devices namely, printers, routers, Personal computer, switch and web server
could be connected to the TCP and IP configuration, in a network management device.
The scenario follows the following procedure:
a) Get: The Get operation’s Manager device could be utilized for sending the
request to the manager’s manager device. It could even perform data retrieval for
sending the manager device to manager.
b) GET request: This request could be utilized to configure the IP address on the
web server’s manager devices and it can also be utilized for retrieving the data on
the MIB tree with the router connection. Further, it has been utilized post initial
get request for retrieving the next object’s instance from the table/ list.
c) SET: The chiefs utilize this activity for changing or allotting the estimation of the
Managed device. It can also be utilized for setting the MIB variable on an agent.
d) RAPS: In contrast with the above mentioned directions that began by the SNMP
Manager, the agents starts the TRAPS. In the event of an occasion, it acts as a flag
for the SNMP Manager by the Agent. It is used by the operator for transmitting
the alert spontaneously to the chief. A Trap data is sent in cases where the explicit
conditions occur. For instance, an adjustment in the condition of a gadget, a
gadget or segment disappointment, or an operator in statement or restart.
e) Advise: It is similar to TRAP which began by the Agent. INFORM contains
affirmation from the SNMP chief to get the request of the data.
f) Reaction: It refers to the order that is utilized for conveying back the data or flag
of activities that are coordinated by the SNMP Manager. The network
management’s switch could be utilized to directly connect it with the IP address’s
host.
1.1 Aim
To design and implement the network management solution, which has the capacity of
1
This project’s scenario can be specified on the network management device. It follows
the following stages such as Device Configuration management, Device Fault management,
Device accounting management, Device performance management and Device security
management. The devices namely, printers, routers, Personal computer, switch and web server
could be connected to the TCP and IP configuration, in a network management device.
The scenario follows the following procedure:
a) Get: The Get operation’s Manager device could be utilized for sending the
request to the manager’s manager device. It could even perform data retrieval for
sending the manager device to manager.
b) GET request: This request could be utilized to configure the IP address on the
web server’s manager devices and it can also be utilized for retrieving the data on
the MIB tree with the router connection. Further, it has been utilized post initial
get request for retrieving the next object’s instance from the table/ list.
c) SET: The chiefs utilize this activity for changing or allotting the estimation of the
Managed device. It can also be utilized for setting the MIB variable on an agent.
d) RAPS: In contrast with the above mentioned directions that began by the SNMP
Manager, the agents starts the TRAPS. In the event of an occasion, it acts as a flag
for the SNMP Manager by the Agent. It is used by the operator for transmitting
the alert spontaneously to the chief. A Trap data is sent in cases where the explicit
conditions occur. For instance, an adjustment in the condition of a gadget, a
gadget or segment disappointment, or an operator in statement or restart.
e) Advise: It is similar to TRAP which began by the Agent. INFORM contains
affirmation from the SNMP chief to get the request of the data.
f) Reaction: It refers to the order that is utilized for conveying back the data or flag
of activities that are coordinated by the SNMP Manager. The network
management’s switch could be utilized to directly connect it with the IP address’s
host.
1.1 Aim
To design and implement the network management solution, which has the capacity of
1

capturing and storing the data from a wide ranges of devices.
2. IP Addressing
System stream refers to the unidirectional game plan of packages between the source and
the endpoints of the aim. The system streams are especially granular, moreover the IP address as
well as the transport layer application port numbers identify the endpoints of the stream.
Similarly, the net flow identifies the streams with the help of TCP, IP tradition type and the data
interface identifier. For area and correspondence, in each system’s hub, the IP address acts as the
reference name distributed to every single system’s center point and is utilized by several other
centers. Additionally, the IP addresses are said to have twofold numbers, but anyway they are
secured in comprehensible configuration, each as the IPv4 address or the IPv6 address. The
segments with the IP address which makes a system could be isolated as several subsystems that
rely on the territory, device type, get to, etc. The devices in the equal subnet contain an ordinary
system prefix portrayed in its IP address.
2.1 Static and Dynamic Managed Objects
The static strategies that map every single overseen object class into the relating TCP
interface are contrasted, and the dynamic systems that rely on the runtime of data. The intension
of this report is that the TCP-based system’s board applications are becoming more appealing in
terms of effectiveness, surviving the impediments of early arrangements and application
estimation. The following steps are followed by the static and dynamic methods of object:
1) The following must be determined:
Scope, objectives, policies, expected outcome from the security program.
2) The following must be evaluated:
Objectives of the business, functionality requirements, user productivity and the
security risks.
3) The following must be defined:
Necessary steps for ensuring that the above mentioned steps are addressed
effectively.
2
2. IP Addressing
System stream refers to the unidirectional game plan of packages between the source and
the endpoints of the aim. The system streams are especially granular, moreover the IP address as
well as the transport layer application port numbers identify the endpoints of the stream.
Similarly, the net flow identifies the streams with the help of TCP, IP tradition type and the data
interface identifier. For area and correspondence, in each system’s hub, the IP address acts as the
reference name distributed to every single system’s center point and is utilized by several other
centers. Additionally, the IP addresses are said to have twofold numbers, but anyway they are
secured in comprehensible configuration, each as the IPv4 address or the IPv6 address. The
segments with the IP address which makes a system could be isolated as several subsystems that
rely on the territory, device type, get to, etc. The devices in the equal subnet contain an ordinary
system prefix portrayed in its IP address.
2.1 Static and Dynamic Managed Objects
The static strategies that map every single overseen object class into the relating TCP
interface are contrasted, and the dynamic systems that rely on the runtime of data. The intension
of this report is that the TCP-based system’s board applications are becoming more appealing in
terms of effectiveness, surviving the impediments of early arrangements and application
estimation. The following steps are followed by the static and dynamic methods of object:
1) The following must be determined:
Scope, objectives, policies, expected outcome from the security program.
2) The following must be evaluated:
Objectives of the business, functionality requirements, user productivity and the
security risks.
3) The following must be defined:
Necessary steps for ensuring that the above mentioned steps are addressed
effectively.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
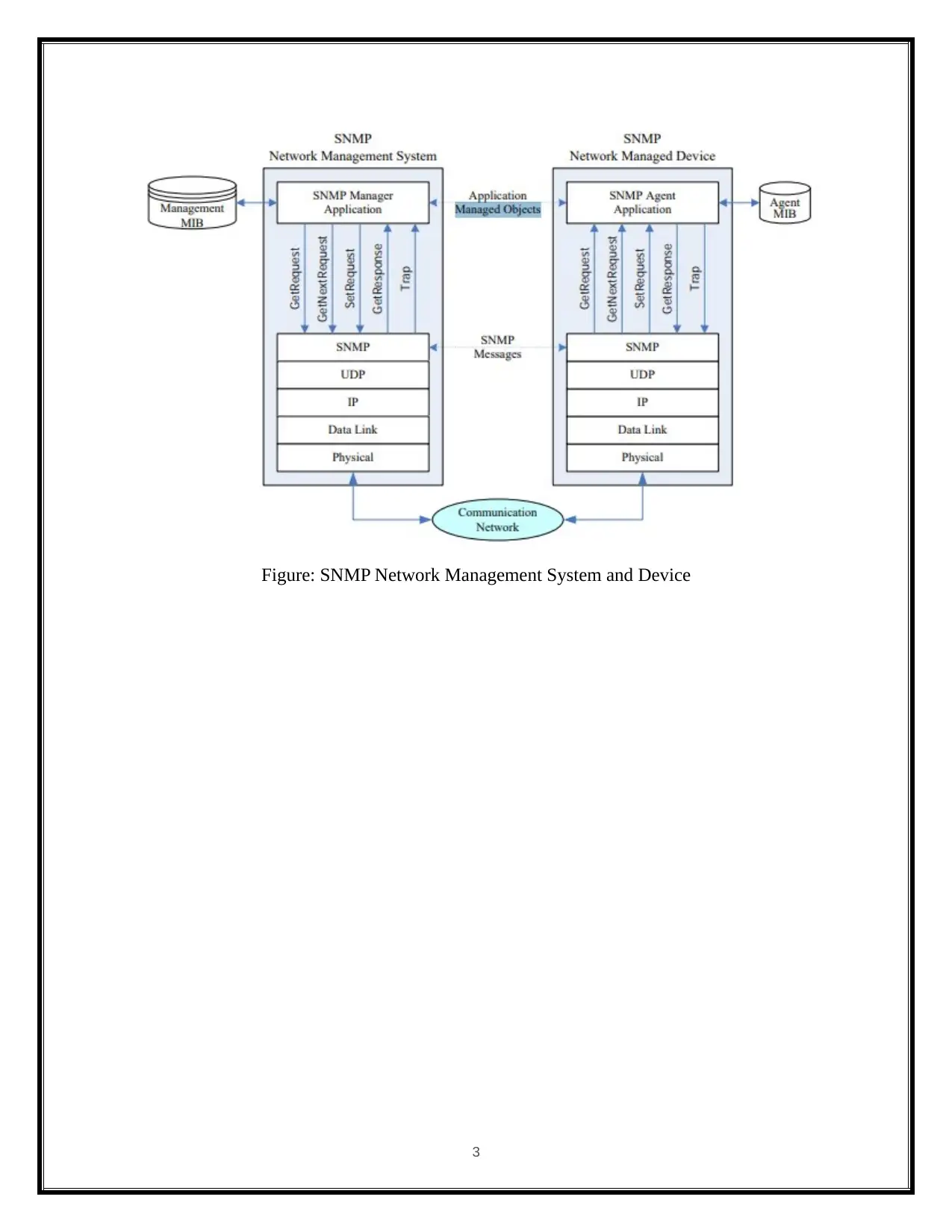
Figure: SNMP Network Management System and Device
3
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
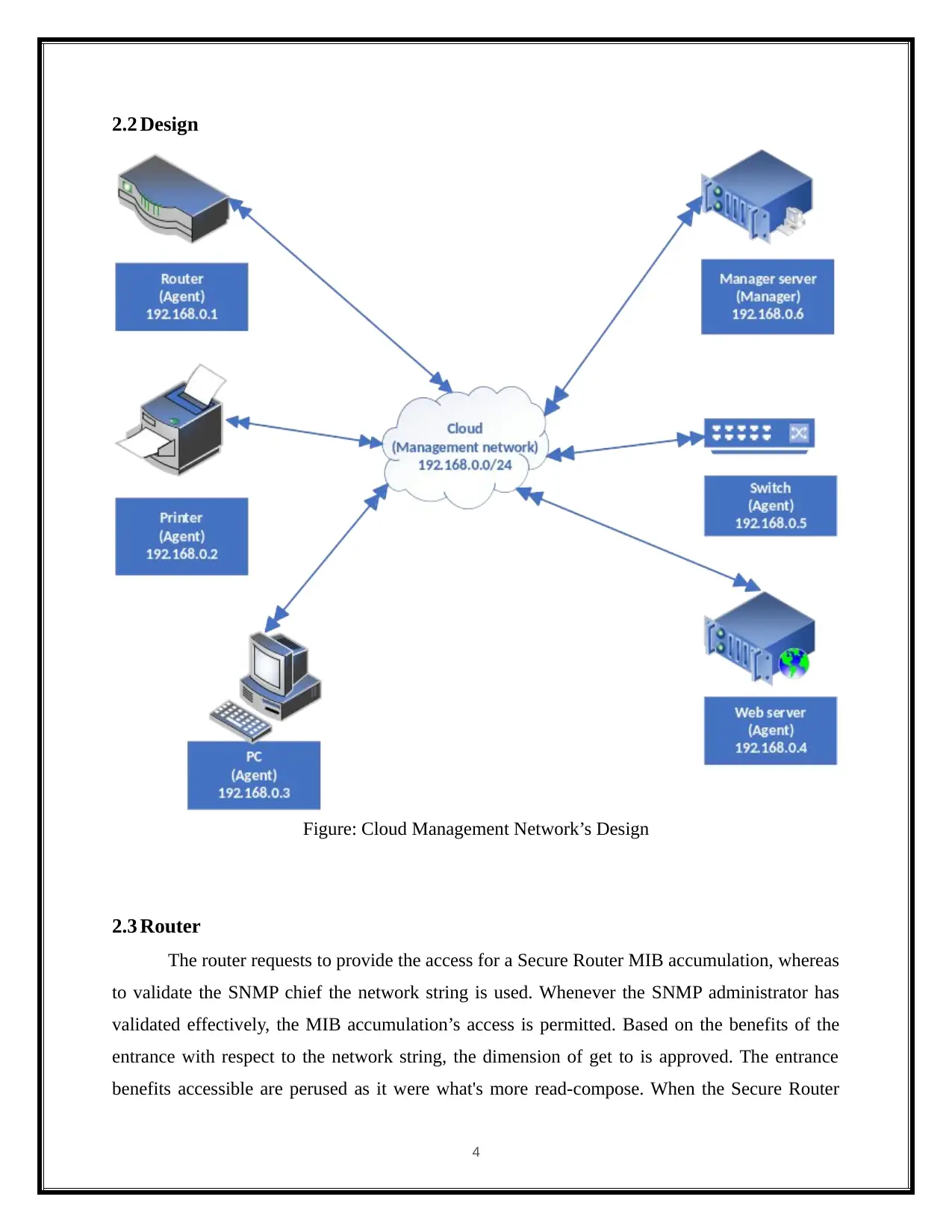
2.2 Design
Figure: Cloud Management Network’s Design
2.3 Router
The router requests to provide the access for a Secure Router MIB accumulation, whereas
to validate the SNMP chief the network string is used. Whenever the SNMP administrator has
validated effectively, the MIB accumulation’s access is permitted. Based on the benefits of the
entrance with respect to the network string, the dimension of get to is approved. The entrance
benefits accessible are perused as it were what's more read-compose. When the Secure Router
4
Figure: Cloud Management Network’s Design
2.3 Router
The router requests to provide the access for a Secure Router MIB accumulation, whereas
to validate the SNMP chief the network string is used. Whenever the SNMP administrator has
validated effectively, the MIB accumulation’s access is permitted. Based on the benefits of the
entrance with respect to the network string, the dimension of get to is approved. The entrance
benefits accessible are perused as it were what's more read-compose. When the Secure Router
4

fails to perceive the SNMP administrator as the substantial customer, there is a possibility that
the confirmation can fail. Based on the determination of snare target setup, the SNMP
verification disappointment traps are sent to SNMP focuses.
System
System Descri - 1.3.6.1.2.1.1.1
System Up Time - 1.3.6.1.2.1.1.3
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.1.1
Interface Table - 1.3.6.1.2.1.2.2
IP
IP Forwarding - 1.3.6.1.2.1.4.1
IP Route - 1.3.6.1.2.1.4.21.1.1
ICMP
Icmp in Errors - 1.3.6.1.2.1.5.2
UDP
UDP In Datagrams - 1.3.6.1.2.1.7.4
UDP Table - 1.3.6.1.2.1.7.4
5
the confirmation can fail. Based on the determination of snare target setup, the SNMP
verification disappointment traps are sent to SNMP focuses.
System
System Descri - 1.3.6.1.2.1.1.1
System Up Time - 1.3.6.1.2.1.1.3
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.1.1
Interface Table - 1.3.6.1.2.1.2.2
IP
IP Forwarding - 1.3.6.1.2.1.4.1
IP Route - 1.3.6.1.2.1.4.21.1.1
ICMP
Icmp in Errors - 1.3.6.1.2.1.5.2
UDP
UDP In Datagrams - 1.3.6.1.2.1.7.4
UDP Table - 1.3.6.1.2.1.7.4
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.4 Printer
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
Interface Table - 1.3.6.1.2.1.2.2
2.5 Switch
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
Interface Table - 1.3.6.1.2.1.2.2
2.6 Web Server
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
6
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
Interface Table - 1.3.6.1.2.1.2.2
2.5 Switch
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
Interface Table - 1.3.6.1.2.1.2.2
2.6 Web Server
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Interface Table - 1.3.6.1.2.1.2.2
TCP
TCP connection Table - 1.3.6.1.2.1.6.13
ICMP
Icmp in Errors - 1.3.6.1.2.1.5.2
UDP
UDP In Datagrams - 1.3.6.1.2.1.7.4
UDP Table - 1.3.6.1.2.1.7.4
2.7 Personal Computer
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
Interface Table - 1.3.6.1.2.1.2.2
CPU
cpmCPUTotal1min - 1.3.6.1.4.1.9.9
cpmCPUTotal5min - 1.3.6.1.4.1.9.9
3. Conclusion
This report’s aim is accomplished, where the network management solutions are designed
and implemented, which has the capacity of capturing and storing the data wide range of devices.
This report has examined data capturing and data storage from various devices and its
relation with network management. Network management is believed to have various usages
7
TCP
TCP connection Table - 1.3.6.1.2.1.6.13
ICMP
Icmp in Errors - 1.3.6.1.2.1.5.2
UDP
UDP In Datagrams - 1.3.6.1.2.1.7.4
UDP Table - 1.3.6.1.2.1.7.4
2.7 Personal Computer
System
System Name - 1.3.6.1.2.1.1.5
System Location - 1.3.6.1.2.1.1.6
System Contact - 1.3.6.1.2.1.1.4
interfaces
Interface Number - 1.3.6.1.2.1.2.1
Interface Table - 1.3.6.1.2.1.2.2
CPU
cpmCPUTotal1min - 1.3.6.1.4.1.9.9
cpmCPUTotal5min - 1.3.6.1.4.1.9.9
3. Conclusion
This report’s aim is accomplished, where the network management solutions are designed
and implemented, which has the capacity of capturing and storing the data wide range of devices.
This report has examined data capturing and data storage from various devices and its
relation with network management. Network management is believed to have various usages
7

such as, it can be used in some tools, for supervising the devices, for the execution of data and
setup. The network management could also be used in the network management tools that are
simple, particularly the ones which can be used to collect and sort out the data of the devices on
the IP address network and to send the server necessary requests, then collect the data for
changing the behaviour of the device. The SNMP could be utilized by the manager for
exchanging the requests with the web server and the router. The investigation on how the
manager device could retrieve the data and request the manager with the help of TCP and IP data
by connecting with the port’s IP address is completed. However, the SNMP devices could
support the moderns, link, workstations, switches, servers, printers, etc.
8
setup. The network management could also be used in the network management tools that are
simple, particularly the ones which can be used to collect and sort out the data of the devices on
the IP address network and to send the server necessary requests, then collect the data for
changing the behaviour of the device. The SNMP could be utilized by the manager for
exchanging the requests with the web server and the router. The investigation on how the
manager device could retrieve the data and request the manager with the help of TCP and IP data
by connecting with the port’s IP address is completed. However, the SNMP devices could
support the moderns, link, workstations, switches, servers, printers, etc.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





