Network Requirement Analysis
VerifiedAdded on 2021/01/02
|9
|1883
|297
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Network requirement
analysis
analysis
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Contents
INTRODUCTION...........................................................................................................................1
1.Scope of inter-networking........................................................................................................1
2. Functional and non-functional requirements (NFR) of inter-networking...............................1
3. Design of networking based on the human concepts...............................................................2
4. Requirements of internet protocols (IP) and its justification in a tabular form.......................2
5 Topology diagram of network..................................................................................................3
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5
INTRODUCTION...........................................................................................................................1
1.Scope of inter-networking........................................................................................................1
2. Functional and non-functional requirements (NFR) of inter-networking...............................1
3. Design of networking based on the human concepts...............................................................2
4. Requirements of internet protocols (IP) and its justification in a tabular form.......................2
5 Topology diagram of network..................................................................................................3
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5

INTRODUCTION
A network is a connection of computers in which different devices are connected that
allows computer to share and exchange data and information. Inter networking refers to
connection of devices where data is shared with some restrictions. In this the access is only given
to internal users. Moreover, inter networking can also be connected to several other devices to
expand the range of network. This report will show what are the functional and non functional
requirements in architecture of network. In addition to this, it will describe protocols and
topologies that are required in designing. Alongside this, study will also focus on various
configuration requirements that are used in implementing connections.
1.Scope of inter-networking
A network of computer is so powerful that allows in sharing and data and information. It
contains different types of hardware and software tools and equipment’s. these requirements are
used in designing network architecture [1]. Apart from this, network is connected from multiple
stations to increase its range. Inter networking can be done by using the cloud computing. It
helps in providing safe and protected sharing of data and information. Besides this, scope of
developing this network is it helps in creating a strong communication channel between various
business department and operations. With this it becomes easy in effective functioning of
activities in entire organisation. the scope can be described as follows :-
Providing an effective platform for communicating quickly and effectively with the help
of wireless technology.
The protocols and configuration provide a protected network to share confidential
information.
The applications and software used are frequently updated to enhance the technological
skills and development of employees.
2. Functional and non-functional requirements (NFR) of inter-networking
In order to create a network, it is necessary that requirements are identified. This helps in
effective design and implementation of network. Basically, there are two types of requirements
needed in inter networking that are functional and non functional. These are described below :-
For establishing wireless network, different technologies are available that create and
connect systems. They are LAN, WAN, etc. they are having their range in which connection is
1
A network is a connection of computers in which different devices are connected that
allows computer to share and exchange data and information. Inter networking refers to
connection of devices where data is shared with some restrictions. In this the access is only given
to internal users. Moreover, inter networking can also be connected to several other devices to
expand the range of network. This report will show what are the functional and non functional
requirements in architecture of network. In addition to this, it will describe protocols and
topologies that are required in designing. Alongside this, study will also focus on various
configuration requirements that are used in implementing connections.
1.Scope of inter-networking
A network of computer is so powerful that allows in sharing and data and information. It
contains different types of hardware and software tools and equipment’s. these requirements are
used in designing network architecture [1]. Apart from this, network is connected from multiple
stations to increase its range. Inter networking can be done by using the cloud computing. It
helps in providing safe and protected sharing of data and information. Besides this, scope of
developing this network is it helps in creating a strong communication channel between various
business department and operations. With this it becomes easy in effective functioning of
activities in entire organisation. the scope can be described as follows :-
Providing an effective platform for communicating quickly and effectively with the help
of wireless technology.
The protocols and configuration provide a protected network to share confidential
information.
The applications and software used are frequently updated to enhance the technological
skills and development of employees.
2. Functional and non-functional requirements (NFR) of inter-networking
In order to create a network, it is necessary that requirements are identified. This helps in
effective design and implementation of network. Basically, there are two types of requirements
needed in inter networking that are functional and non functional. These are described below :-
For establishing wireless network, different technologies are available that create and
connect systems. They are LAN, WAN, etc. they are having their range in which connection is
1

established. Mostly, WAN are used as it has very high range which varies from 500km. while
implementing wireless technologies certain protocols of networking are followed.
The functional requirement in NFR refers to those components that performs specific
functions [2]. These components create a link between output and input devices. they act as an
interface in network. There are several resources that can be used in this that are NIC, hub,
switches, routers, etc. besides this, it also enables in working as application based interface
(API). These components can also store data for user authentication.
On the other hand non functional requirements are related to configuration of network.
They are related to security, reliability, scalability, etc. These help in maintaining the security of
data and information as well as systems.
3. Design of networking based on the human concepts
Generally, network are designed on the basis of structure of organization. The network
architecture must be properly designed so that there is smooth flow of data and information.
There are two types of approaches which are usually followed in designing of network. They are
based on human concepts which is defined as below :-
Top-down approach- Here, network is designed from top to bottom. This means firstly
applications are identified and then connection is developed between them. It is most commonly
followed by experts. also, in this approach the flow of communication is from top to bottom. The
layer in which user will interact at last is developed at end.
Bottom-up design- In this approach, physical layer is designed first and then all other layers.
Here, flow is from bottom to up [3]. OSI model is used in designing of network through this.
Also, many other resources are installed that are firewall, bandwidth, etc.
The present network architecture will be designed on the basis of top down approach.
The subnets will be connected with various departments.
4. Requirements of internet protocols (IP) and its justification in a tabular form
A network includes certain protocols that helps in communication and sharing of data and
information. These protocols are known as IP. They send and receive data from one source to
another. Each system have its own unique IP address which is used by server to track the device
from which request is sent. There is a process through which IP are divided into subnets that is of
different size which is known as VLSM. The process is described below :-
2
implementing wireless technologies certain protocols of networking are followed.
The functional requirement in NFR refers to those components that performs specific
functions [2]. These components create a link between output and input devices. they act as an
interface in network. There are several resources that can be used in this that are NIC, hub,
switches, routers, etc. besides this, it also enables in working as application based interface
(API). These components can also store data for user authentication.
On the other hand non functional requirements are related to configuration of network.
They are related to security, reliability, scalability, etc. These help in maintaining the security of
data and information as well as systems.
3. Design of networking based on the human concepts
Generally, network are designed on the basis of structure of organization. The network
architecture must be properly designed so that there is smooth flow of data and information.
There are two types of approaches which are usually followed in designing of network. They are
based on human concepts which is defined as below :-
Top-down approach- Here, network is designed from top to bottom. This means firstly
applications are identified and then connection is developed between them. It is most commonly
followed by experts. also, in this approach the flow of communication is from top to bottom. The
layer in which user will interact at last is developed at end.
Bottom-up design- In this approach, physical layer is designed first and then all other layers.
Here, flow is from bottom to up [3]. OSI model is used in designing of network through this.
Also, many other resources are installed that are firewall, bandwidth, etc.
The present network architecture will be designed on the basis of top down approach.
The subnets will be connected with various departments.
4. Requirements of internet protocols (IP) and its justification in a tabular form
A network includes certain protocols that helps in communication and sharing of data and
information. These protocols are known as IP. They send and receive data from one source to
another. Each system have its own unique IP address which is used by server to track the device
from which request is sent. There is a process through which IP are divided into subnets that is of
different size which is known as VLSM. The process is described below :-
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
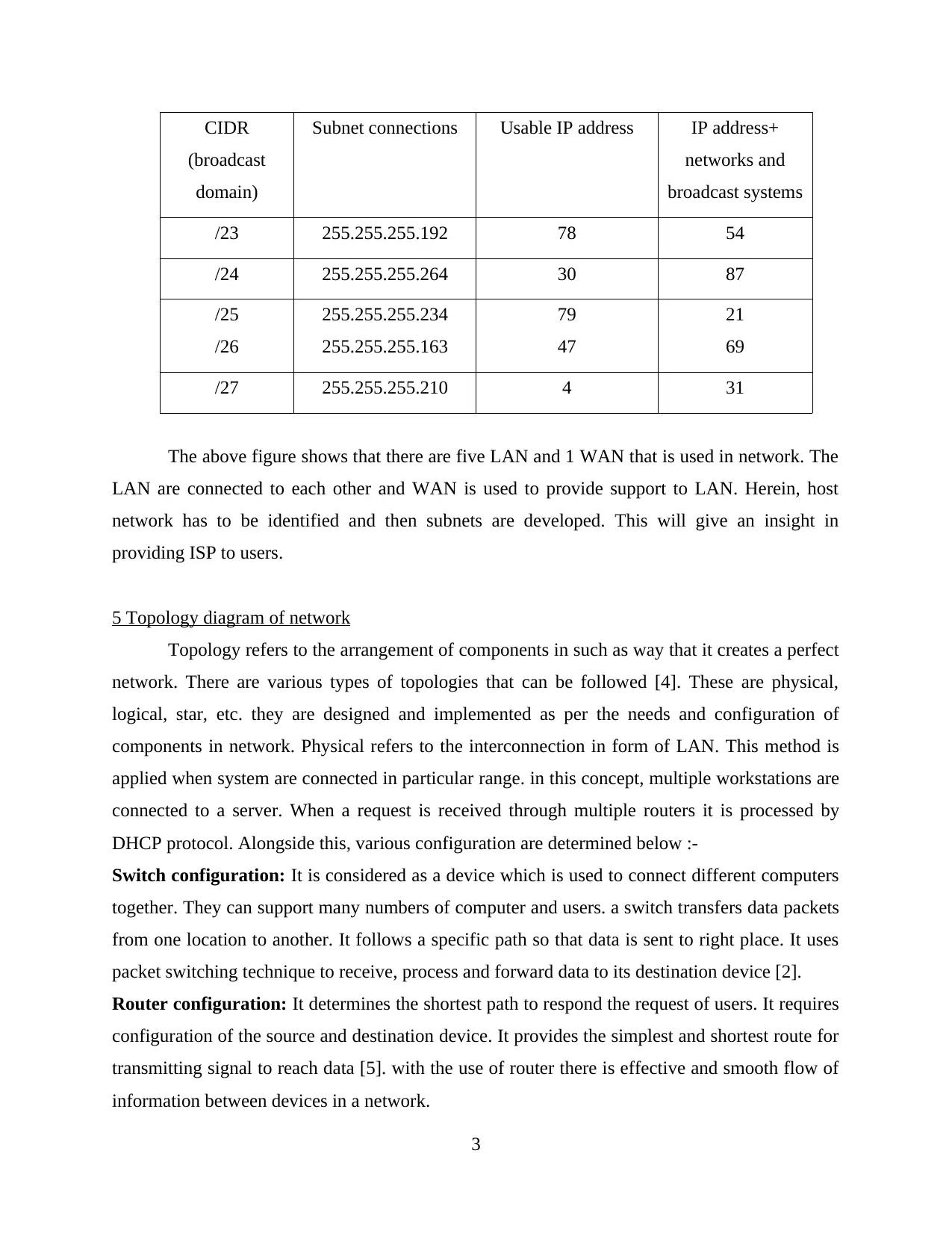
CIDR
(broadcast
domain)
Subnet connections Usable IP address IP address+
networks and
broadcast systems
/23 255.255.255.192 78 54
/24 255.255.255.264 30 87
/25
/26
255.255.255.234
255.255.255.163
79
47
21
69
/27 255.255.255.210 4 31
The above figure shows that there are five LAN and 1 WAN that is used in network. The
LAN are connected to each other and WAN is used to provide support to LAN. Herein, host
network has to be identified and then subnets are developed. This will give an insight in
providing ISP to users.
5 Topology diagram of network
Topology refers to the arrangement of components in such as way that it creates a perfect
network. There are various types of topologies that can be followed [4]. These are physical,
logical, star, etc. they are designed and implemented as per the needs and configuration of
components in network. Physical refers to the interconnection in form of LAN. This method is
applied when system are connected in particular range. in this concept, multiple workstations are
connected to a server. When a request is received through multiple routers it is processed by
DHCP protocol. Alongside this, various configuration are determined below :-
Switch configuration: It is considered as a device which is used to connect different computers
together. They can support many numbers of computer and users. a switch transfers data packets
from one location to another. It follows a specific path so that data is sent to right place. It uses
packet switching technique to receive, process and forward data to its destination device [2].
Router configuration: It determines the shortest path to respond the request of users. It requires
configuration of the source and destination device. It provides the simplest and shortest route for
transmitting signal to reach data [5]. with the use of router there is effective and smooth flow of
information between devices in a network.
3
(broadcast
domain)
Subnet connections Usable IP address IP address+
networks and
broadcast systems
/23 255.255.255.192 78 54
/24 255.255.255.264 30 87
/25
/26
255.255.255.234
255.255.255.163
79
47
21
69
/27 255.255.255.210 4 31
The above figure shows that there are five LAN and 1 WAN that is used in network. The
LAN are connected to each other and WAN is used to provide support to LAN. Herein, host
network has to be identified and then subnets are developed. This will give an insight in
providing ISP to users.
5 Topology diagram of network
Topology refers to the arrangement of components in such as way that it creates a perfect
network. There are various types of topologies that can be followed [4]. These are physical,
logical, star, etc. they are designed and implemented as per the needs and configuration of
components in network. Physical refers to the interconnection in form of LAN. This method is
applied when system are connected in particular range. in this concept, multiple workstations are
connected to a server. When a request is received through multiple routers it is processed by
DHCP protocol. Alongside this, various configuration are determined below :-
Switch configuration: It is considered as a device which is used to connect different computers
together. They can support many numbers of computer and users. a switch transfers data packets
from one location to another. It follows a specific path so that data is sent to right place. It uses
packet switching technique to receive, process and forward data to its destination device [2].
Router configuration: It determines the shortest path to respond the request of users. It requires
configuration of the source and destination device. It provides the simplest and shortest route for
transmitting signal to reach data [5]. with the use of router there is effective and smooth flow of
information between devices in a network.
3
DHCP configuration: DHCP is basically referred to a protocol that is used to manage a network
by dynamically assigning an IP address to either a device or a node on some sort of network to
enable them communicate with one other using that particularly assigned IP. DHCP is used to
systematise a centrally managed configuration. This in turn assist the network administrators in
avoiding manual handling of various IP addresses in their distinct set of network devices. A
successful implementation of DHCP is known to be done on both small local networks along
with the networking done in large entities. It is ultimately used as a router that connects IP
addresses and provides the link to establish a network connection.by using this it becomes easy
in following a specific route of processing data in a network.
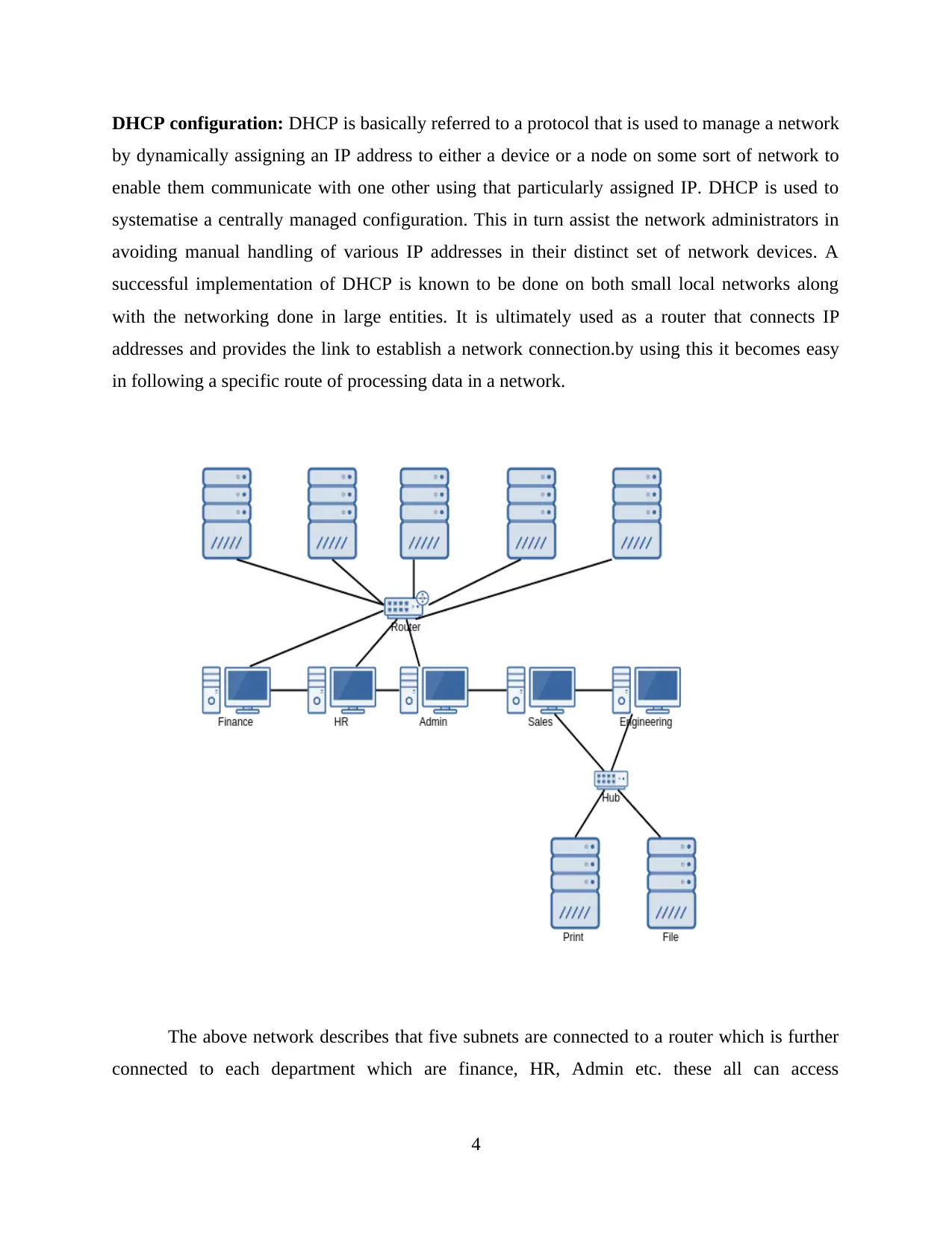
The above network describes that five subnets are connected to a router which is further
connected to each department which are finance, HR, Admin etc. these all can access
4
by dynamically assigning an IP address to either a device or a node on some sort of network to
enable them communicate with one other using that particularly assigned IP. DHCP is used to
systematise a centrally managed configuration. This in turn assist the network administrators in
avoiding manual handling of various IP addresses in their distinct set of network devices. A
successful implementation of DHCP is known to be done on both small local networks along
with the networking done in large entities. It is ultimately used as a router that connects IP
addresses and provides the link to establish a network connection.by using this it becomes easy
in following a specific route of processing data in a network.
The above network describes that five subnets are connected to a router which is further
connected to each department which are finance, HR, Admin etc. these all can access
4

information from router [6]. Apart from this, a hub is installed to provide access to print and file
server and connecting it with sales and engineering.
CONCLUSION
From this report it is concluded that network protocols are identified while designing a
network. This gives an insight about the configuration that will be required in network. The
functional and non functional requirements are NIC, hub and security, reliability, etc. moreover,
it is also concluded that network can be designed by applying common two approaches that are
top down and bottom up. With this an overview is gained that how information will flow in
network. A process of VLSM is applied in determining the IP address of subnets in systems. At
last various types of topologies like star, bus, etc. are discussed.
5
server and connecting it with sales and engineering.
CONCLUSION
From this report it is concluded that network protocols are identified while designing a
network. This gives an insight about the configuration that will be required in network. The
functional and non functional requirements are NIC, hub and security, reliability, etc. moreover,
it is also concluded that network can be designed by applying common two approaches that are
top down and bottom up. With this an overview is gained that how information will flow in
network. A process of VLSM is applied in determining the IP address of subnets in systems. At
last various types of topologies like star, bus, etc. are discussed.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
[1].Shabanpour R, Javanmardi M, Fasihozaman M, Miralinaghi M, Mohammadian A.
Investigating the applicability of ADAPTS activity-based model in air quality analysis.
Travel Behaviour and Society. 2018 Jul 1;12:130-40.
[2].Stefaniak J, Schiefer J, Miller EJ, Krenn CG, Baron DM, Faybik P. Macrophage
migration inhibitory factor as a potential predictor for requirement of renal replacement
therapy after orthotopic liver transplantation. Liver Transplantation. 2015
May;21(5):662-9.
[3].Xilouris G, Trouva E, Lobillo F, Soares JM, Carapinha J, McGrath MJ, Gardikis G,
Paglierani P, Pallis E, Zuccaro L, Rebahi Y. T-NOVA: A marketplace for virtualized
network functions. In2014 European Conference on Networks and Communications
(EuCNC) 2014 Jun 23 (pp. 1-5). IEEE.
[4].Gayvoronska G, Sakharova S. Researching the requirements from different user groups
to Telecommunications Network. InProblems of Infocommunications Science and
Technology (PIC S&T), 2016 Third International Scientific-Practical Conference 2016
Oct 4 (pp. 84-87). IEEE.
[5].Medhi D, Ramasamy K. Network routing: algorithms, protocols, and architectures.
Morgan Kaufmann; 2017 Sep 6.
[6].Yang JT. Safety risk analysis and countermeasures study on regular mass passenger flow
of China's urban subway. Procedia Engineering. 2016 Jan 1;135:175-9.
6
Books and journals
[1].Shabanpour R, Javanmardi M, Fasihozaman M, Miralinaghi M, Mohammadian A.
Investigating the applicability of ADAPTS activity-based model in air quality analysis.
Travel Behaviour and Society. 2018 Jul 1;12:130-40.
[2].Stefaniak J, Schiefer J, Miller EJ, Krenn CG, Baron DM, Faybik P. Macrophage
migration inhibitory factor as a potential predictor for requirement of renal replacement
therapy after orthotopic liver transplantation. Liver Transplantation. 2015
May;21(5):662-9.
[3].Xilouris G, Trouva E, Lobillo F, Soares JM, Carapinha J, McGrath MJ, Gardikis G,
Paglierani P, Pallis E, Zuccaro L, Rebahi Y. T-NOVA: A marketplace for virtualized
network functions. In2014 European Conference on Networks and Communications
(EuCNC) 2014 Jun 23 (pp. 1-5). IEEE.
[4].Gayvoronska G, Sakharova S. Researching the requirements from different user groups
to Telecommunications Network. InProblems of Infocommunications Science and
Technology (PIC S&T), 2016 Third International Scientific-Practical Conference 2016
Oct 4 (pp. 84-87). IEEE.
[5].Medhi D, Ramasamy K. Network routing: algorithms, protocols, and architectures.
Morgan Kaufmann; 2017 Sep 6.
[6].Yang JT. Safety risk analysis and countermeasures study on regular mass passenger flow
of China's urban subway. Procedia Engineering. 2016 Jan 1;135:175-9.
6

7
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





