Network Security and Protocols: DNS/DHCP, IPSec/TLS, UTM/SIEM Report
VerifiedAdded on 2021/08/10
|26
|4317
|64
Report
AI Summary
This report provides a comprehensive overview of network security protocols, covering DNS/DHCP, IPSec/TLS, and UTM/SIEM. It begins with an introduction to DHCP and DNS, explaining their functions and differences, followed by an in-depth analysis of DNS and DHCP vulnerabilities, including volumetric attacks, exploits, stealth DoS attacks, protocol abuse, DHCP starvation, and rogue server attacks. The report then explores mitigation techniques for both DNS and DHCP. It further delves into IPSec and SSL/TLS, comparing their advantages and disadvantages, and outlining various deployment scenarios. Finally, the report contrasts UTM and SIEM, detailing their features, technologies, and goals, and highlighting their respective roles in network security. The report is a valuable resource for understanding and addressing network security challenges.
Amey U. Parulkar, UWL
MSc Cyber Security
Network security and Protocols
Exploring DNS/DHCP, IPSec/TLS and UTM/SIEM
MSc Cyber Security
Network security and Protocols
Exploring DNS/DHCP, IPSec/TLS and UTM/SIEM
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
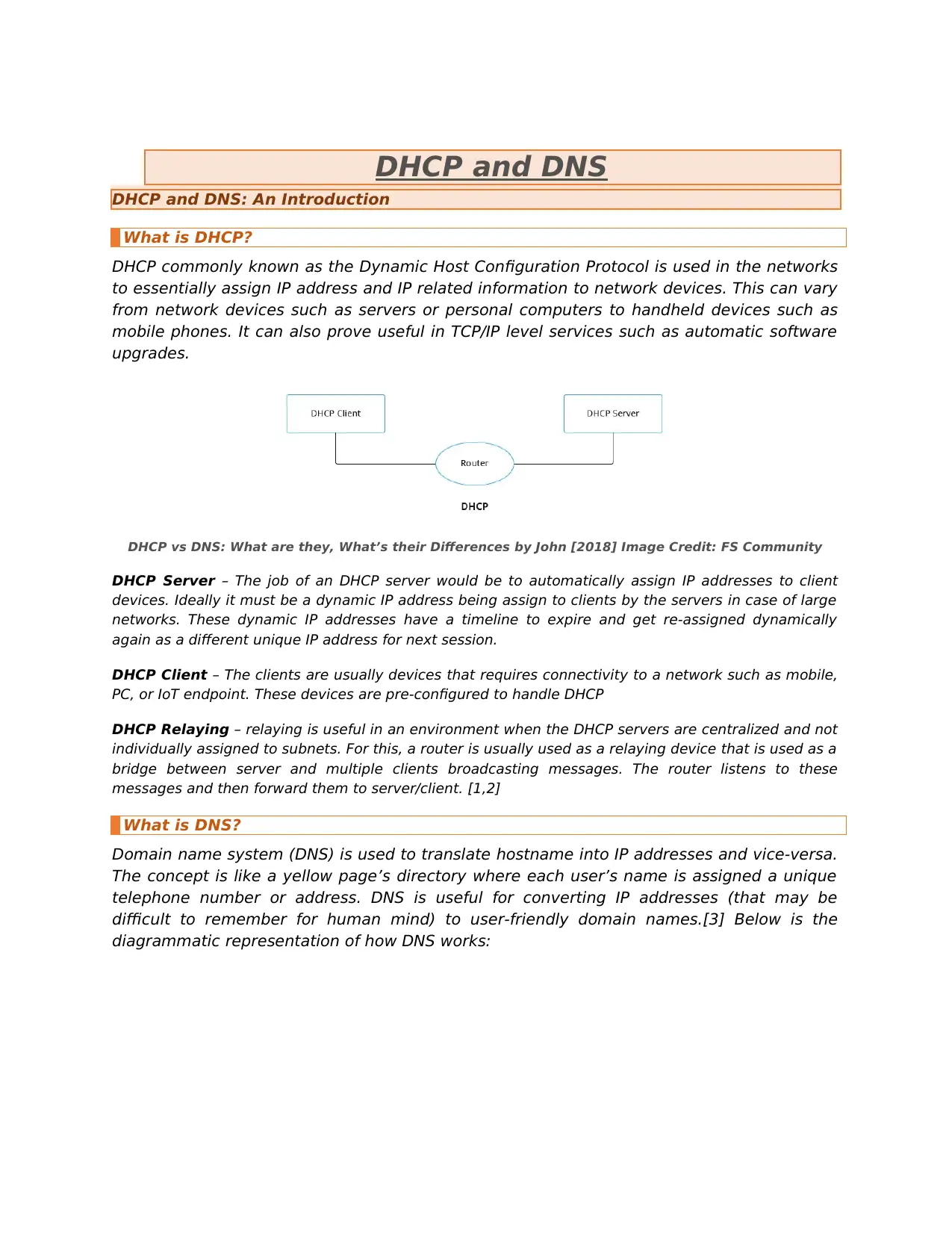
DHCP and DNS
DHCP and DNS: An Introduction
What is DHCP?
DHCP commonly known as the Dynamic Host Configuration Protocol is used in the networks
to essentially assign IP address and IP related information to network devices. This can vary
from network devices such as servers or personal computers to handheld devices such as
mobile phones. It can also prove useful in TCP/IP level services such as automatic software
upgrades.
DHCP vs DNS: What are they, What’s their Differences by John [2018] Image Credit: FS Community
DHCP Server – The job of an DHCP server would be to automatically assign IP addresses to client
devices. Ideally it must be a dynamic IP address being assign to clients by the servers in case of large
networks. These dynamic IP addresses have a timeline to expire and get re-assigned dynamically
again as a different unique IP address for next session.
DHCP Client – The clients are usually devices that requires connectivity to a network such as mobile,
PC, or IoT endpoint. These devices are pre-configured to handle DHCP
DHCP Relaying – relaying is useful in an environment when the DHCP servers are centralized and not
individually assigned to subnets. For this, a router is usually used as a relaying device that is used as a
bridge between server and multiple clients broadcasting messages. The router listens to these
messages and then forward them to server/client. [1,2]
What is DNS?
Domain name system (DNS) is used to translate hostname into IP addresses and vice-versa.
The concept is like a yellow page’s directory where each user’s name is assigned a unique
telephone number or address. DNS is useful for converting IP addresses (that may be
difficult to remember for human mind) to user-friendly domain names.[3] Below is the
diagrammatic representation of how DNS works:
DHCP and DNS: An Introduction
What is DHCP?
DHCP commonly known as the Dynamic Host Configuration Protocol is used in the networks
to essentially assign IP address and IP related information to network devices. This can vary
from network devices such as servers or personal computers to handheld devices such as
mobile phones. It can also prove useful in TCP/IP level services such as automatic software
upgrades.
DHCP vs DNS: What are they, What’s their Differences by John [2018] Image Credit: FS Community
DHCP Server – The job of an DHCP server would be to automatically assign IP addresses to client
devices. Ideally it must be a dynamic IP address being assign to clients by the servers in case of large
networks. These dynamic IP addresses have a timeline to expire and get re-assigned dynamically
again as a different unique IP address for next session.
DHCP Client – The clients are usually devices that requires connectivity to a network such as mobile,
PC, or IoT endpoint. These devices are pre-configured to handle DHCP
DHCP Relaying – relaying is useful in an environment when the DHCP servers are centralized and not
individually assigned to subnets. For this, a router is usually used as a relaying device that is used as a
bridge between server and multiple clients broadcasting messages. The router listens to these
messages and then forward them to server/client. [1,2]
What is DNS?
Domain name system (DNS) is used to translate hostname into IP addresses and vice-versa.
The concept is like a yellow page’s directory where each user’s name is assigned a unique
telephone number or address. DNS is useful for converting IP addresses (that may be
difficult to remember for human mind) to user-friendly domain names.[3] Below is the
diagrammatic representation of how DNS works:

The history of DNS Vulnerabilities and the cloud by Prizmant, Daniel [2020] Image Credit: FS
Community
Vulnerabilities & Consequences: DNS and DHCP
DNS Vulnerabilities
DNS is vulnerable to a multitude of attack types. Most commonly they target a specific DNS
function such as cache, recursive or authoritative). The main objective is to derail
businesses, perform data corruption, and steal data or ALL! Hackers or attackers mostly
prey on these vulnerabilities in the form of DNS attacks which is broadly categorized in 4
main types: [5]
Community
Vulnerabilities & Consequences: DNS and DHCP
DNS Vulnerabilities
DNS is vulnerable to a multitude of attack types. Most commonly they target a specific DNS
function such as cache, recursive or authoritative). The main objective is to derail
businesses, perform data corruption, and steal data or ALL! Hackers or attackers mostly
prey on these vulnerabilities in the form of DNS attacks which is broadly categorized in 4
main types: [5]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Fig:1 DNS Vulnerability Categories
The above categories can be further extrapolated into various types of attacks that makes
DNS more vulnerable as a protocol. Below section would highlight each of the above four
categories and the types of attacks that it encompasses making DNS vulnerable to each one
of them.
Volumetric Attacks
Volumetric attacks are a result of flooding DNS servers with direct requests resulting into
exhaustion of resources such as cache, recursion or authoritative functions using a spoofed
IP address. [7]
Volumetric DoS attacks:
When a DNS server is
overwhelmed by a sudden
surge of DNS requests
from either one or multiple
sources which results in a
service unavailability or
degradation
Exploits:
Exploiting flaws or bugs in
existing DNS protocol or on
an operating system
running DNS services
Stealth/Slow Drip DoS
attacks:
Using slow response to a
particular DNS query
thereby causing a
capacity exhaustion which
leads to a service
degradation eventually.
Protocol Abuse:
DNS can be exploited in a
way that was not
oroginally intended which
results in phishing and
exfiltration
The above categories can be further extrapolated into various types of attacks that makes
DNS more vulnerable as a protocol. Below section would highlight each of the above four
categories and the types of attacks that it encompasses making DNS vulnerable to each one
of them.
Volumetric Attacks
Volumetric attacks are a result of flooding DNS servers with direct requests resulting into
exhaustion of resources such as cache, recursion or authoritative functions using a spoofed
IP address. [7]
Volumetric DoS attacks:
When a DNS server is
overwhelmed by a sudden
surge of DNS requests
from either one or multiple
sources which results in a
service unavailability or
degradation
Exploits:
Exploiting flaws or bugs in
existing DNS protocol or on
an operating system
running DNS services
Stealth/Slow Drip DoS
attacks:
Using slow response to a
particular DNS query
thereby causing a
capacity exhaustion which
leads to a service
degradation eventually.
Protocol Abuse:
DNS can be exploited in a
way that was not
oroginally intended which
results in phishing and
exfiltration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
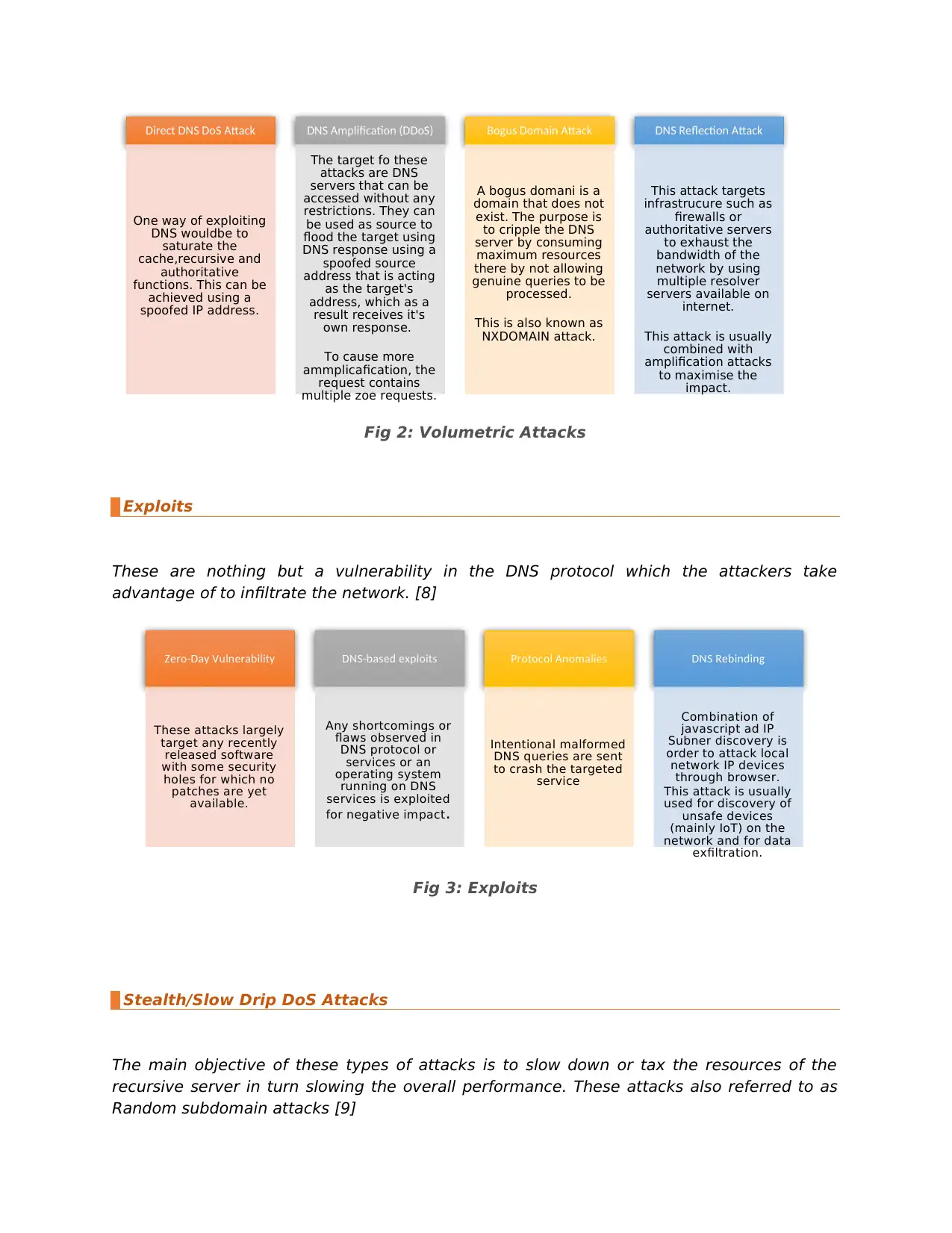
Fig 2: Volumetric Attacks
Exploits
These are nothing but a vulnerability in the DNS protocol which the attackers take
advantage of to infiltrate the network. [8]
Fig 3: Exploits
Stealth/Slow Drip DoS Attacks
The main objective of these types of attacks is to slow down or tax the resources of the
recursive server in turn slowing the overall performance. These attacks also referred to as
Random subdomain attacks [9]
Direct DNS DoS Attack
One way of exploiting
DNS wouldbe to
saturate the
cache,recursive and
authoritative
functions. This can be
achieved using a
spoofed IP address.
DNS Amplification (DDoS)
The target fo these
attacks are DNS
servers that can be
accessed without any
restrictions. They can
be used as source to
flood the target using
DNS response using a
spoofed source
address that is acting
as the target's
address, which as a
result receives it's
own response.
To cause more
ammplicafication, the
request contains
multiple zoe requests.
Bogus Domain Attack
A bogus domani is a
domain that does not
exist. The purpose is
to cripple the DNS
server by consuming
maximum resources
there by not allowing
genuine queries to be
processed.
This is also known as
NXDOMAIN attack.
DNS Reflection Attack
This attack targets
infrastrucure such as
firewalls or
authoritative servers
to exhaust the
bandwidth of the
network by using
multiple resolver
servers available on
internet.
This attack is usually
combined with
amplification attacks
to maximise the
impact.
Zero-Day Vulnerability
These attacks largely
target any recently
released software
with some security
holes for which no
patches are yet
available.
DNS-based exploits
Any shortcomings or
flaws observed in
DNS protocol or
services or an
operating system
running on DNS
services is exploited
for negative impact.
Protocol Anomalies
Intentional malformed
DNS queries are sent
to crash the targeted
service
DNS Rebinding
Combination of
javascript ad IP
Subner discovery is
order to attack local
network IP devices
through browser.
This attack is usually
used for discovery of
unsafe devices
(mainly IoT) on the
network and for data
exfiltration.
Exploits
These are nothing but a vulnerability in the DNS protocol which the attackers take
advantage of to infiltrate the network. [8]
Fig 3: Exploits
Stealth/Slow Drip DoS Attacks
The main objective of these types of attacks is to slow down or tax the resources of the
recursive server in turn slowing the overall performance. These attacks also referred to as
Random subdomain attacks [9]
Direct DNS DoS Attack
One way of exploiting
DNS wouldbe to
saturate the
cache,recursive and
authoritative
functions. This can be
achieved using a
spoofed IP address.
DNS Amplification (DDoS)
The target fo these
attacks are DNS
servers that can be
accessed without any
restrictions. They can
be used as source to
flood the target using
DNS response using a
spoofed source
address that is acting
as the target's
address, which as a
result receives it's
own response.
To cause more
ammplicafication, the
request contains
multiple zoe requests.
Bogus Domain Attack
A bogus domani is a
domain that does not
exist. The purpose is
to cripple the DNS
server by consuming
maximum resources
there by not allowing
genuine queries to be
processed.
This is also known as
NXDOMAIN attack.
DNS Reflection Attack
This attack targets
infrastrucure such as
firewalls or
authoritative servers
to exhaust the
bandwidth of the
network by using
multiple resolver
servers available on
internet.
This attack is usually
combined with
amplification attacks
to maximise the
impact.
Zero-Day Vulnerability
These attacks largely
target any recently
released software
with some security
holes for which no
patches are yet
available.
DNS-based exploits
Any shortcomings or
flaws observed in
DNS protocol or
services or an
operating system
running on DNS
services is exploited
for negative impact.
Protocol Anomalies
Intentional malformed
DNS queries are sent
to crash the targeted
service
DNS Rebinding
Combination of
javascript ad IP
Subner discovery is
order to attack local
network IP devices
through browser.
This attack is usually
used for discovery of
unsafe devices
(mainly IoT) on the
network and for data
exfiltration.
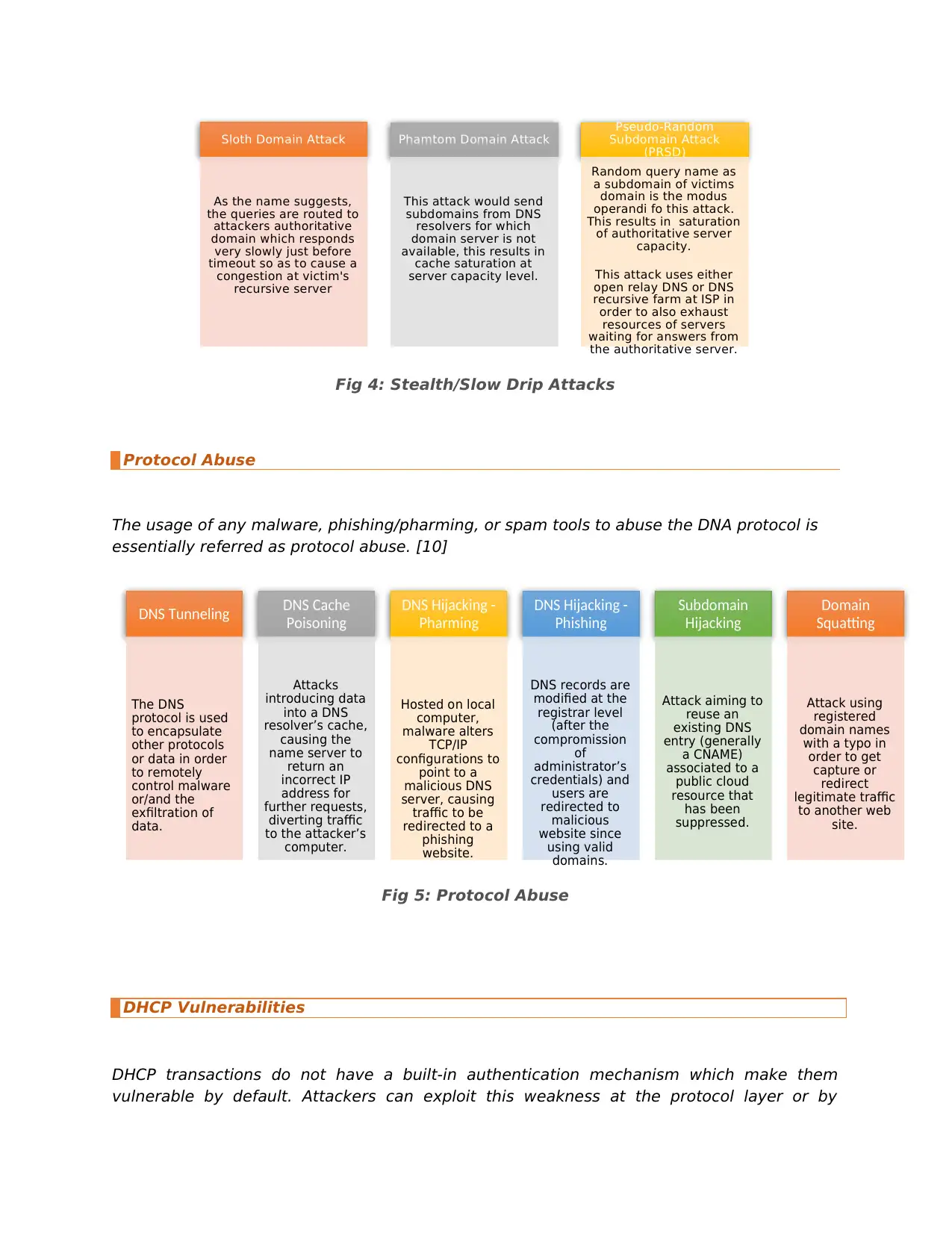
Fig 4: Stealth/Slow Drip Attacks
Protocol Abuse
The usage of any malware, phishing/pharming, or spam tools to abuse the DNA protocol is
essentially referred as protocol abuse. [10]
Fig 5: Protocol Abuse
DHCP Vulnerabilities
DHCP transactions do not have a built-in authentication mechanism which make them
vulnerable by default. Attackers can exploit this weakness at the protocol layer or by
Sloth Domain Attack
As the name suggests,
the queries are routed to
attackers authoritative
domain which responds
very slowly just before
timeout so as to cause a
congestion at victim's
recursive server
Phamtom Domain Attack
This attack would send
subdomains from DNS
resolvers for which
domain server is not
available, this results in
cache saturation at
server capacity level.
Pseudo-Random
Subdomain Attack
(PRSD)
Random query name as
a subdomain of victims
domain is the modus
operandi fo this attack.
This results in saturation
of authoritative server
capacity.
This attack uses either
open relay DNS or DNS
recursive farm at ISP in
order to also exhaust
resources of servers
waiting for answers from
the authoritative server.
DNS Tunneling
The DNS
protocol is used
to encapsulate
other protocols
or data in order
to remotely
control malware
or/and the
exfiltration of
data.
DNS Cache
Poisoning
Attacks
introducing data
into a DNS
resolver’s cache,
causing the
name server to
return an
incorrect IP
address for
further requests,
diverting traffic
to the attacker’s
computer.
DNS Hijacking -
Pharming
Hosted on local
computer,
malware alters
TCP/IP
configurations to
point to a
malicious DNS
server, causing
traffic to be
redirected to a
phishing
website.
DNS Hijacking -
Phishing
DNS records are
modified at the
registrar level
(after the
compromission
of
administrator’s
credentials) and
users are
redirected to
malicious
website since
using valid
domains.
Subdomain
Hijacking
Attack aiming to
reuse an
existing DNS
entry (generally
a CNAME)
associated to a
public cloud
resource that
has been
suppressed.
Domain
Squatting
Attack using
registered
domain names
with a typo in
order to get
capture or
redirect
legitimate traffic
to another web
site.
Protocol Abuse
The usage of any malware, phishing/pharming, or spam tools to abuse the DNA protocol is
essentially referred as protocol abuse. [10]
Fig 5: Protocol Abuse
DHCP Vulnerabilities
DHCP transactions do not have a built-in authentication mechanism which make them
vulnerable by default. Attackers can exploit this weakness at the protocol layer or by
Sloth Domain Attack
As the name suggests,
the queries are routed to
attackers authoritative
domain which responds
very slowly just before
timeout so as to cause a
congestion at victim's
recursive server
Phamtom Domain Attack
This attack would send
subdomains from DNS
resolvers for which
domain server is not
available, this results in
cache saturation at
server capacity level.
Pseudo-Random
Subdomain Attack
(PRSD)
Random query name as
a subdomain of victims
domain is the modus
operandi fo this attack.
This results in saturation
of authoritative server
capacity.
This attack uses either
open relay DNS or DNS
recursive farm at ISP in
order to also exhaust
resources of servers
waiting for answers from
the authoritative server.
DNS Tunneling
The DNS
protocol is used
to encapsulate
other protocols
or data in order
to remotely
control malware
or/and the
exfiltration of
data.
DNS Cache
Poisoning
Attacks
introducing data
into a DNS
resolver’s cache,
causing the
name server to
return an
incorrect IP
address for
further requests,
diverting traffic
to the attacker’s
computer.
DNS Hijacking -
Pharming
Hosted on local
computer,
malware alters
TCP/IP
configurations to
point to a
malicious DNS
server, causing
traffic to be
redirected to a
phishing
website.
DNS Hijacking -
Phishing
DNS records are
modified at the
registrar level
(after the
compromission
of
administrator’s
credentials) and
users are
redirected to
malicious
website since
using valid
domains.
Subdomain
Hijacking
Attack aiming to
reuse an
existing DNS
entry (generally
a CNAME)
associated to a
public cloud
resource that
has been
suppressed.
Domain
Squatting
Attack using
registered
domain names
with a typo in
order to get
capture or
redirect
legitimate traffic
to another web
site.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
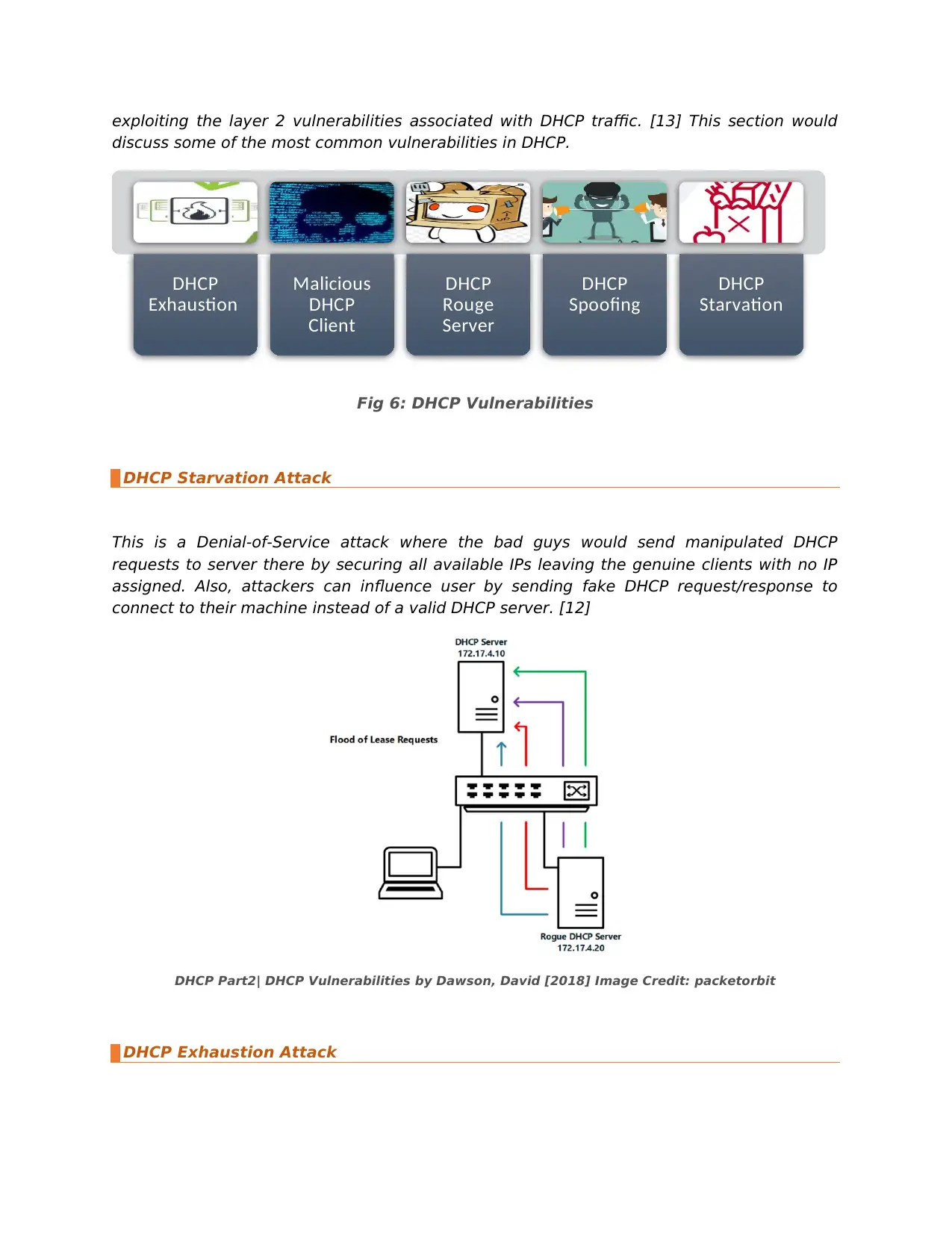
exploiting the layer 2 vulnerabilities associated with DHCP traffic. [13] This section would
discuss some of the most common vulnerabilities in DHCP.
Fig 6: DHCP Vulnerabilities
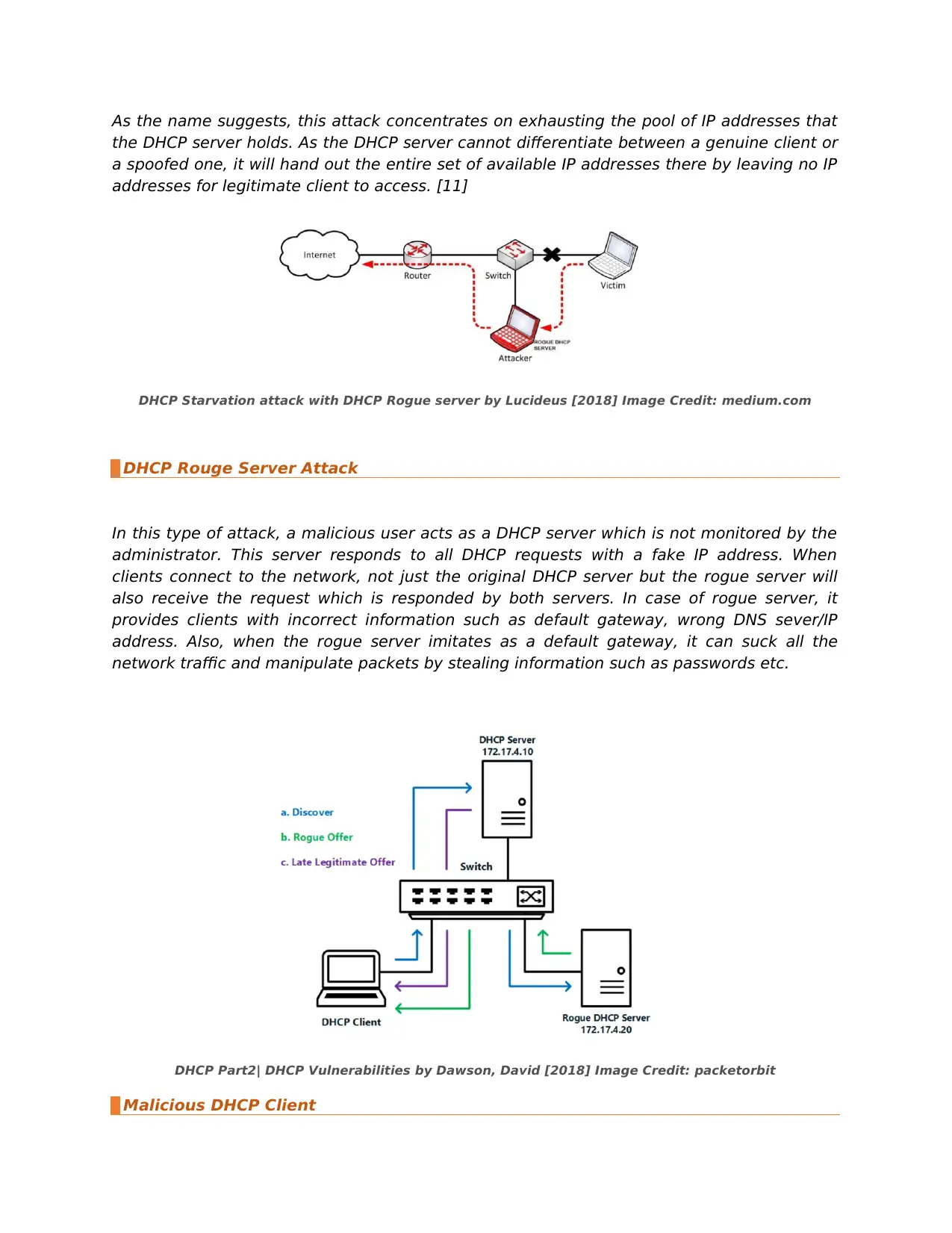
DHCP Starvation Attack
This is a Denial-of-Service attack where the bad guys would send manipulated DHCP
requests to server there by securing all available IPs leaving the genuine clients with no IP
assigned. Also, attackers can influence user by sending fake DHCP request/response to
connect to their machine instead of a valid DHCP server. [12]
DHCP Part2| DHCP Vulnerabilities by Dawson, David [2018] Image Credit: packetorbit
DHCP Exhaustion Attack
DHCP
Exhaustion
Malicious
DHCP
Client
DHCP
Rouge
Server
DHCP
Spoofing
DHCP
Starvation
discuss some of the most common vulnerabilities in DHCP.
Fig 6: DHCP Vulnerabilities
DHCP Starvation Attack
This is a Denial-of-Service attack where the bad guys would send manipulated DHCP
requests to server there by securing all available IPs leaving the genuine clients with no IP
assigned. Also, attackers can influence user by sending fake DHCP request/response to
connect to their machine instead of a valid DHCP server. [12]
DHCP Part2| DHCP Vulnerabilities by Dawson, David [2018] Image Credit: packetorbit
DHCP Exhaustion Attack
DHCP
Exhaustion
Malicious
DHCP
Client
DHCP
Rouge
Server
DHCP
Spoofing
DHCP
Starvation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
As the name suggests, this attack concentrates on exhausting the pool of IP addresses that
the DHCP server holds. As the DHCP server cannot differentiate between a genuine client or
a spoofed one, it will hand out the entire set of available IP addresses there by leaving no IP
addresses for legitimate client to access. [11]
DHCP Starvation attack with DHCP Rogue server by Lucideus [2018] Image Credit: medium.com
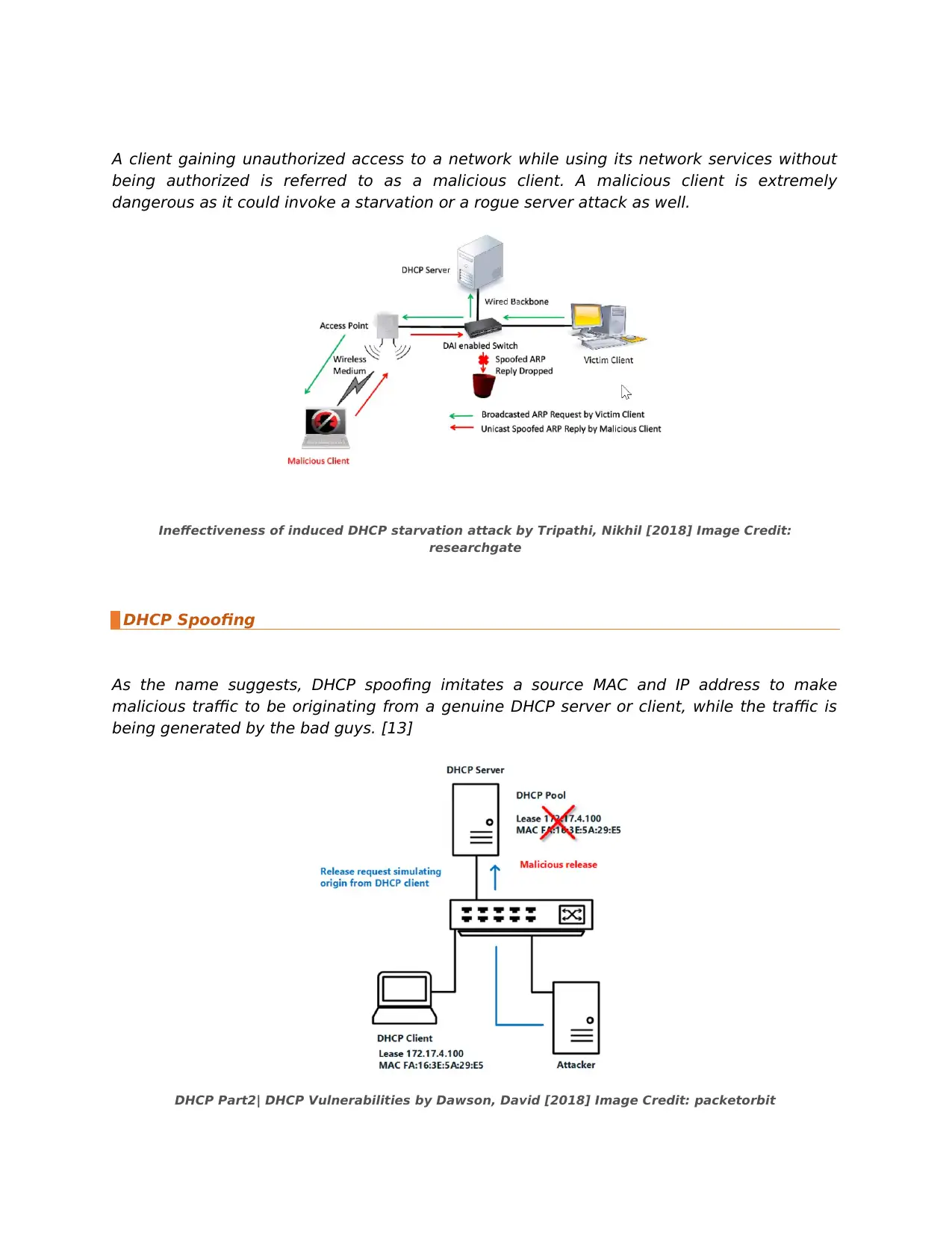
DHCP Rouge Server Attack
In this type of attack, a malicious user acts as a DHCP server which is not monitored by the
administrator. This server responds to all DHCP requests with a fake IP address. When
clients connect to the network, not just the original DHCP server but the rogue server will
also receive the request which is responded by both servers. In case of rogue server, it
provides clients with incorrect information such as default gateway, wrong DNS sever/IP
address. Also, when the rogue server imitates as a default gateway, it can suck all the
network traffic and manipulate packets by stealing information such as passwords etc.
DHCP Part2| DHCP Vulnerabilities by Dawson, David [2018] Image Credit: packetorbit
Malicious DHCP Client
the DHCP server holds. As the DHCP server cannot differentiate between a genuine client or
a spoofed one, it will hand out the entire set of available IP addresses there by leaving no IP
addresses for legitimate client to access. [11]
DHCP Starvation attack with DHCP Rogue server by Lucideus [2018] Image Credit: medium.com
DHCP Rouge Server Attack
In this type of attack, a malicious user acts as a DHCP server which is not monitored by the
administrator. This server responds to all DHCP requests with a fake IP address. When
clients connect to the network, not just the original DHCP server but the rogue server will
also receive the request which is responded by both servers. In case of rogue server, it
provides clients with incorrect information such as default gateway, wrong DNS sever/IP
address. Also, when the rogue server imitates as a default gateway, it can suck all the
network traffic and manipulate packets by stealing information such as passwords etc.
DHCP Part2| DHCP Vulnerabilities by Dawson, David [2018] Image Credit: packetorbit
Malicious DHCP Client
A client gaining unauthorized access to a network while using its network services without
being authorized is referred to as a malicious client. A malicious client is extremely
dangerous as it could invoke a starvation or a rogue server attack as well.
Ineffectiveness of induced DHCP starvation attack by Tripathi, Nikhil [2018] Image Credit:
researchgate
DHCP Spoofing
As the name suggests, DHCP spoofing imitates a source MAC and IP address to make
malicious traffic to be originating from a genuine DHCP server or client, while the traffic is
being generated by the bad guys. [13]
DHCP Part2| DHCP Vulnerabilities by Dawson, David [2018] Image Credit: packetorbit
being authorized is referred to as a malicious client. A malicious client is extremely
dangerous as it could invoke a starvation or a rogue server attack as well.
Ineffectiveness of induced DHCP starvation attack by Tripathi, Nikhil [2018] Image Credit:
researchgate
DHCP Spoofing
As the name suggests, DHCP spoofing imitates a source MAC and IP address to make
malicious traffic to be originating from a genuine DHCP server or client, while the traffic is
being generated by the bad guys. [13]
DHCP Part2| DHCP Vulnerabilities by Dawson, David [2018] Image Credit: packetorbit
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Mitigation Techniques: DNS and DHCP
The above-mentioned vulnerabilities regarding DHCP, and DNS are extremely dangerous
and can bring down any network device or devices or whole network in a matter of minutes.
However, there are mitigation techniques, if followed, can help reduce the risk of the
network device or overall networks being vulnerable to such attacks.
DNS Mitigation Techniques
Can be detected via payload or traffic analysis
Payload analysis will observe the DNS requests/responses by
looking at the size of request versus response.
Traffic analysis will delve into the volume aspect such as number
of requests, geographic location , domain history etc.
Tools such as "Zscaler", "TunnelGuard" and "Splunk"can be useful
for detection.
Setting strong rules on firewall for inbound and outbound traffic
based on detection can mitigate further DNS tunneling
DNS Tunneling - Mitigation
Use DNS security extensions (DNSSEC) to address threats against
DNS.
Look for any anamoly observed in teh DNS traffic by active
monitoring using tools.
Due to its vulnerable nature, keep DNS pacthed to the latest level
Implement strong password policies on network devices
Make use of HTTPS indicators to prove the legitimacy of the site
being accessed.
DNS Cache Poisoning -
Mitigation
Avoid links and attachments from unknown senders
Only access secured links that begins with HTTPS
Do not access the sites taht looks suspicious
If it is too good to be true, then it is a scam. stay away from such
deals.
Choose the correct ISP and change default settings of home
raouter.
DNS Hijacking - Pharming -
Mitigation
Educate employees via training and mock phishing scenarios.
Install SPAM filter to detect virus etc.
Deploy web filter to block malicious websites.
Encrypt all sensitive information.
Disable HTML email messages.
DNS Hijacking - Phishing
Review access to domain name registrars
Review DNS roles and responsibilities
Update all registration information
Use roles for domain registration information
Don't use personal email addresses
Credential Updates - Change the passwords
Subdomain Hijacking
Register your brand name with TMCH -trademark clearinghouse.
Use ICANN - trademark registry exchange service to ensure
unauthorized registrations are blocked.
Install SSL certificates to depict your site as real site.
Include sender policy framework to use secure email gateways
and software to detect the mismatched headers and envelope
sender addresses.
Domain Squatting
The above-mentioned vulnerabilities regarding DHCP, and DNS are extremely dangerous
and can bring down any network device or devices or whole network in a matter of minutes.
However, there are mitigation techniques, if followed, can help reduce the risk of the
network device or overall networks being vulnerable to such attacks.
DNS Mitigation Techniques
Can be detected via payload or traffic analysis
Payload analysis will observe the DNS requests/responses by
looking at the size of request versus response.
Traffic analysis will delve into the volume aspect such as number
of requests, geographic location , domain history etc.
Tools such as "Zscaler", "TunnelGuard" and "Splunk"can be useful
for detection.
Setting strong rules on firewall for inbound and outbound traffic
based on detection can mitigate further DNS tunneling
DNS Tunneling - Mitigation
Use DNS security extensions (DNSSEC) to address threats against
DNS.
Look for any anamoly observed in teh DNS traffic by active
monitoring using tools.
Due to its vulnerable nature, keep DNS pacthed to the latest level
Implement strong password policies on network devices
Make use of HTTPS indicators to prove the legitimacy of the site
being accessed.
DNS Cache Poisoning -
Mitigation
Avoid links and attachments from unknown senders
Only access secured links that begins with HTTPS
Do not access the sites taht looks suspicious
If it is too good to be true, then it is a scam. stay away from such
deals.
Choose the correct ISP and change default settings of home
raouter.
DNS Hijacking - Pharming -
Mitigation
Educate employees via training and mock phishing scenarios.
Install SPAM filter to detect virus etc.
Deploy web filter to block malicious websites.
Encrypt all sensitive information.
Disable HTML email messages.
DNS Hijacking - Phishing
Review access to domain name registrars
Review DNS roles and responsibilities
Update all registration information
Use roles for domain registration information
Don't use personal email addresses
Credential Updates - Change the passwords
Subdomain Hijacking
Register your brand name with TMCH -trademark clearinghouse.
Use ICANN - trademark registry exchange service to ensure
unauthorized registrations are blocked.
Install SSL certificates to depict your site as real site.
Include sender policy framework to use secure email gateways
and software to detect the mismatched headers and envelope
sender addresses.
Domain Squatting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
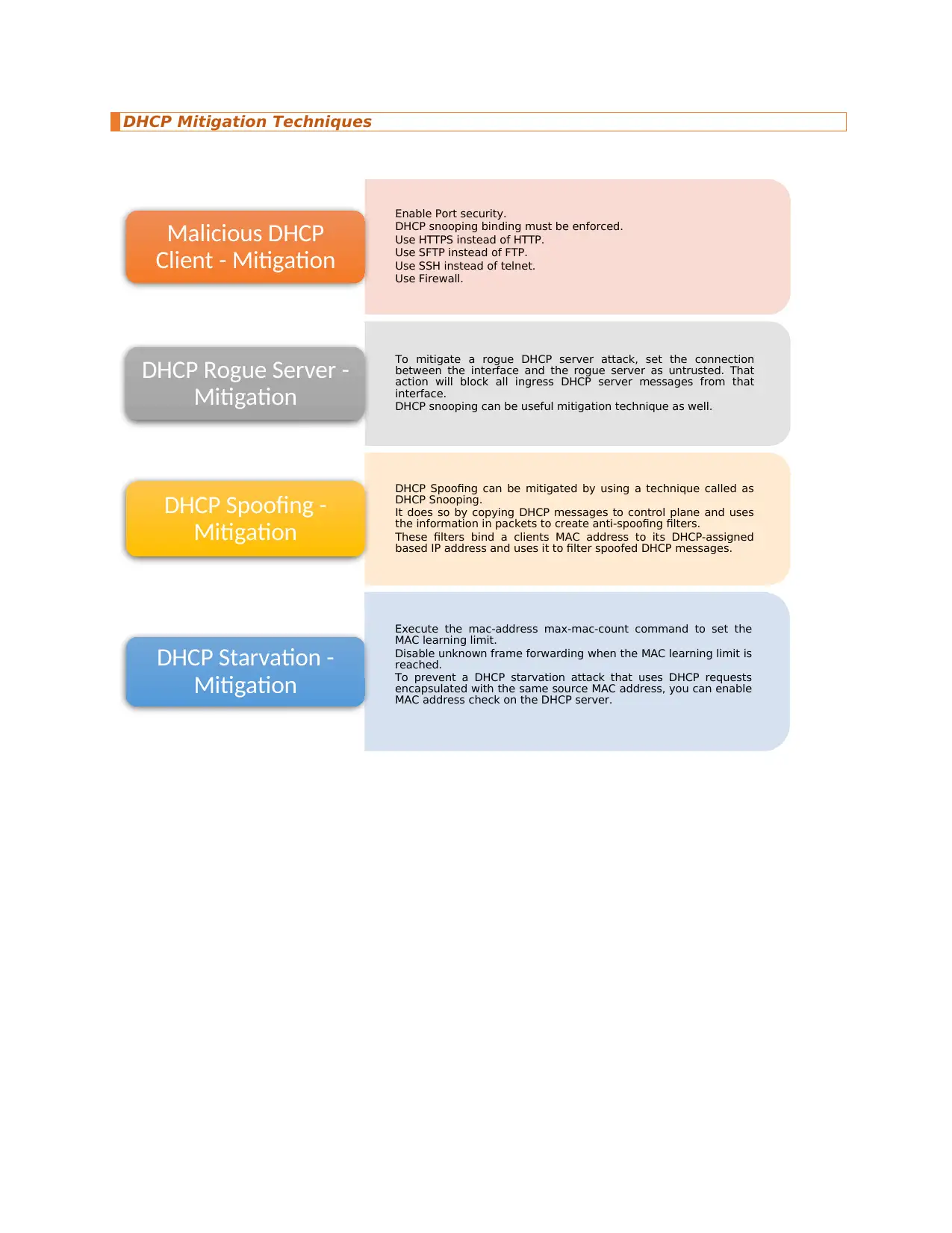
DHCP Mitigation Techniques
Enable Port security.
DHCP snooping binding must be enforced.
Use HTTPS instead of HTTP.
Use SFTP instead of FTP.
Use SSH instead of telnet.
Use Firewall.
Malicious DHCP
Client - Mitigation
To mitigate a rogue DHCP server attack, set the connection
between the interface and the rogue server as untrusted. That
action will block all ingress DHCP server messages from that
interface.
DHCP snooping can be useful mitigation technique as well.
DHCP Rogue Server -
Mitigation
DHCP Spoofing can be mitigated by using a technique called as
DHCP Snooping.
It does so by copying DHCP messages to control plane and uses
the information in packets to create anti-spoofing filters.
These filters bind a clients MAC address to its DHCP-assigned
based IP address and uses it to filter spoofed DHCP messages.
DHCP Spoofing -
Mitigation
Execute the mac-address max-mac-count command to set the
MAC learning limit.
Disable unknown frame forwarding when the MAC learning limit is
reached.
To prevent a DHCP starvation attack that uses DHCP requests
encapsulated with the same source MAC address, you can enable
MAC address check on the DHCP server.
DHCP Starvation -
Mitigation
Enable Port security.
DHCP snooping binding must be enforced.
Use HTTPS instead of HTTP.
Use SFTP instead of FTP.
Use SSH instead of telnet.
Use Firewall.
Malicious DHCP
Client - Mitigation
To mitigate a rogue DHCP server attack, set the connection
between the interface and the rogue server as untrusted. That
action will block all ingress DHCP server messages from that
interface.
DHCP snooping can be useful mitigation technique as well.
DHCP Rogue Server -
Mitigation
DHCP Spoofing can be mitigated by using a technique called as
DHCP Snooping.
It does so by copying DHCP messages to control plane and uses
the information in packets to create anti-spoofing filters.
These filters bind a clients MAC address to its DHCP-assigned
based IP address and uses it to filter spoofed DHCP messages.
DHCP Spoofing -
Mitigation
Execute the mac-address max-mac-count command to set the
MAC learning limit.
Disable unknown frame forwarding when the MAC learning limit is
reached.
To prevent a DHCP starvation attack that uses DHCP requests
encapsulated with the same source MAC address, you can enable
MAC address check on the DHCP server.
DHCP Starvation -
Mitigation

IPSec and SSL/TLS
Advantages of IPSec and SSL/TLS – A Comparison
IPSec
It is a protocol essentially used to communicate between two network devices or
communication endpoints. Encryption of data including authentication, integrity and
protection is supported by IPSec. For example, we can use this protocol between two routers
or between a router and a host or between a firewall and a host etc.
IPSec Advantages
Network Layer
Security
IPSec is transparent to
applications.
End user need not bother
about its configuration.
No impact on layers
above network layer as
IPSec at Network layer.
IPSec allows monitoring
of all network traffic.
It is recommended to
have IPSec based VPN for
network protection.
Confidentiality
An advantage of IPSec is
it offers confidentiality.
IPSec uses public key to
ensure safe data
transfer.
Keys help to verify that
data has come from
correct host.
Due to this, it is
impossible forge data
packets.
Zero
dependability
on Application
IPSec is implemented at
network layer and hence
independent of the
applications used.
IPSec requires
modification at OS level
and hence IPSec-based
VPNs have no issues for
ype of applications.
Network Support
IPSec can be
implemented to any
network irrespective of
it's size.
A network rangin from
local LAN toWAN such as
internet can use IPSec for
security.
Authentication
IPSec does
authentication by placing
digital signatures on
each dta packets.
Any 3rd party
interference can be
protected here.
Contents inside packets
cannot be modified
without detection, which
makes IPSec more
secured.
Advantages of IPSec and SSL/TLS – A Comparison
IPSec
It is a protocol essentially used to communicate between two network devices or
communication endpoints. Encryption of data including authentication, integrity and
protection is supported by IPSec. For example, we can use this protocol between two routers
or between a router and a host or between a firewall and a host etc.
IPSec Advantages
Network Layer
Security
IPSec is transparent to
applications.
End user need not bother
about its configuration.
No impact on layers
above network layer as
IPSec at Network layer.
IPSec allows monitoring
of all network traffic.
It is recommended to
have IPSec based VPN for
network protection.
Confidentiality
An advantage of IPSec is
it offers confidentiality.
IPSec uses public key to
ensure safe data
transfer.
Keys help to verify that
data has come from
correct host.
Due to this, it is
impossible forge data
packets.
Zero
dependability
on Application
IPSec is implemented at
network layer and hence
independent of the
applications used.
IPSec requires
modification at OS level
and hence IPSec-based
VPNs have no issues for
ype of applications.
Network Support
IPSec can be
implemented to any
network irrespective of
it's size.
A network rangin from
local LAN toWAN such as
internet can use IPSec for
security.
Authentication
IPSec does
authentication by placing
digital signatures on
each dta packets.
Any 3rd party
interference can be
protected here.
Contents inside packets
cannot be modified
without detection, which
makes IPSec more
secured.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



