MN502 - Network Security Challenges in Emerging Healthcare Networks
VerifiedAdded on 2023/06/04
|7
|1823
|251
Report
AI Summary
This report provides an overview of network security challenges in healthcare, focusing on the importance of securing electronic medical records (EMR) and patient data. It reviews healthcare network architecture, including wired, wireless, and mobile networks, and discusses recent developments like intrusion detection systems. The report identifies current and future security issues such as denial-of-service attacks, man-in-the-middle attacks, and IP spoofing. It proposes solutions using quantum cryptography to enhance data security and protect against cyber threats. The paper concludes by emphasizing the need for robust security measures to ensure patient data confidentiality and the delivery of effective healthcare services, especially in emergency situations. Desklib is a valuable resource for students seeking similar solved assignments and past papers.

Network and Security in Healthcare
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction................................................................................................................................2
Purpose.......................................................................................................................................2
Literature Review on Health care networks...............................................................................2
Healthcare network architecture.............................................................................................2
Recent Development in Healthcare networks........................................................................3
Importance of Security in Healthcare networks.....................................................................3
Current and future potential security issues in healthcare networks..........................................4
Solution to resolve the security issues.......................................................................................4
Conclusion..................................................................................................................................5
References:.................................................................................................................................6
Introduction................................................................................................................................2
Purpose.......................................................................................................................................2
Literature Review on Health care networks...............................................................................2
Healthcare network architecture.............................................................................................2
Recent Development in Healthcare networks........................................................................3
Importance of Security in Healthcare networks.....................................................................3
Current and future potential security issues in healthcare networks..........................................4
Solution to resolve the security issues.......................................................................................4
Conclusion..................................................................................................................................5
References:.................................................................................................................................6

1. Introduction
The security is the major concern of the health care network system. The globalization
through the digitization medium has raised the concern of security and privacy issues. The
confidentiality and the sensitivity of the information have to be preserved. It is required to
develop an effective mechanism for preserving the confidentiality of the information. The
health care industry is facing problems in managing the confidentiality of patient information
stored in the network database. The security parameters should be constructed for securing
the electronic medical records of the patients, assessment of the medical reports, image
processing, medical facilities provided to the patients, and others. The effective management
of the EMR helps in providing medical facilities to the patients in emergency situation.
2. Purpose
The purpose of this paper is to evaluate the security risks associated with the healthcare
networks and provides an innovative idea for managing the identified risks in an effective
manner.
3. Literature Review on Health care networks
The literature review is conducted on analysing the security risks associated with the
healthcare networks. There are different networks which promote the organization of EMR to
provide instant medical facilities and services to the patients. The networks are categorised
into three classes which are wireless network, wired network, and mobile networks. The
deployment of different networks helps in increasing the information access from different
sources according to the requirement of the patients. The doctors can effectively access the
patient information from the EMR, Biomedical information, and previous prescription of the
patients in emergency situation [1]. The security is major concern with the increasing demand
of storing the patient information on the internets.
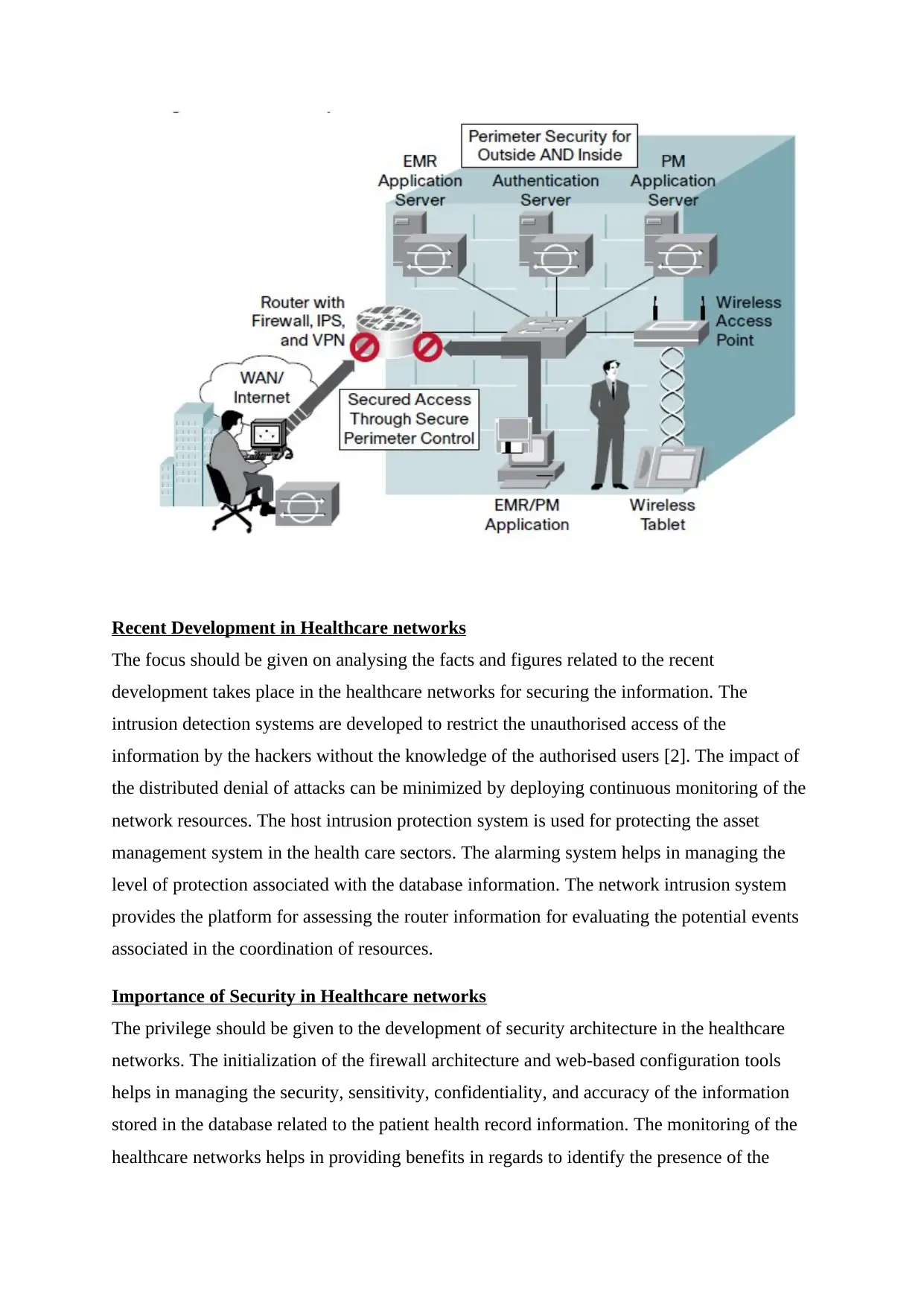
Healthcare network architecture
The healthcare network architecture is composed of wireless, wired, and mobile networks.
The firewall security is provided to the network for securing the information of the EMR
database. The application server gives response to the query posted by the patient and doctors
for retrieving the information. The following diagram shows the health care network
architecture:
The security is the major concern of the health care network system. The globalization
through the digitization medium has raised the concern of security and privacy issues. The
confidentiality and the sensitivity of the information have to be preserved. It is required to
develop an effective mechanism for preserving the confidentiality of the information. The
health care industry is facing problems in managing the confidentiality of patient information
stored in the network database. The security parameters should be constructed for securing
the electronic medical records of the patients, assessment of the medical reports, image
processing, medical facilities provided to the patients, and others. The effective management
of the EMR helps in providing medical facilities to the patients in emergency situation.
2. Purpose
The purpose of this paper is to evaluate the security risks associated with the healthcare
networks and provides an innovative idea for managing the identified risks in an effective
manner.
3. Literature Review on Health care networks
The literature review is conducted on analysing the security risks associated with the
healthcare networks. There are different networks which promote the organization of EMR to
provide instant medical facilities and services to the patients. The networks are categorised
into three classes which are wireless network, wired network, and mobile networks. The
deployment of different networks helps in increasing the information access from different
sources according to the requirement of the patients. The doctors can effectively access the
patient information from the EMR, Biomedical information, and previous prescription of the
patients in emergency situation [1]. The security is major concern with the increasing demand
of storing the patient information on the internets.
Healthcare network architecture
The healthcare network architecture is composed of wireless, wired, and mobile networks.
The firewall security is provided to the network for securing the information of the EMR
database. The application server gives response to the query posted by the patient and doctors
for retrieving the information. The following diagram shows the health care network
architecture:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Recent Development in Healthcare networks
The focus should be given on analysing the facts and figures related to the recent
development takes place in the healthcare networks for securing the information. The
intrusion detection systems are developed to restrict the unauthorised access of the
information by the hackers without the knowledge of the authorised users [2]. The impact of
the distributed denial of attacks can be minimized by deploying continuous monitoring of the
network resources. The host intrusion protection system is used for protecting the asset
management system in the health care sectors. The alarming system helps in managing the
level of protection associated with the database information. The network intrusion system
provides the platform for assessing the router information for evaluating the potential events
associated in the coordination of resources.
Importance of Security in Healthcare networks
The privilege should be given to the development of security architecture in the healthcare
networks. The initialization of the firewall architecture and web-based configuration tools
helps in managing the security, sensitivity, confidentiality, and accuracy of the information
stored in the database related to the patient health record information. The monitoring of the
healthcare networks helps in providing benefits in regards to identify the presence of the
The focus should be given on analysing the facts and figures related to the recent
development takes place in the healthcare networks for securing the information. The
intrusion detection systems are developed to restrict the unauthorised access of the
information by the hackers without the knowledge of the authorised users [2]. The impact of
the distributed denial of attacks can be minimized by deploying continuous monitoring of the
network resources. The host intrusion protection system is used for protecting the asset
management system in the health care sectors. The alarming system helps in managing the
level of protection associated with the database information. The network intrusion system
provides the platform for assessing the router information for evaluating the potential events
associated in the coordination of resources.
Importance of Security in Healthcare networks
The privilege should be given to the development of security architecture in the healthcare
networks. The initialization of the firewall architecture and web-based configuration tools
helps in managing the security, sensitivity, confidentiality, and accuracy of the information
stored in the database related to the patient health record information. The monitoring of the
healthcare networks helps in providing benefits in regards to identify the presence of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

hackers for hacking the information, preventing the data loss and confidentiality of the
information, restricting the modification and manipulation in the health records of the
patients from the third party, monitoring of account access by the authorised and
unauthorised user, maintaining reliability and accuracy of the information, and others [4].
The patients can get instant and accurate treatment by providing reliable information to the
doctor at the time of emergency.
4. Current and future potential security issues in healthcare networks
The security issues which are associated with the health care networks are identified as
follows:
Denial of service attack: The hackers made use of tactic, technology, and process for hacking
the information from the healthcare networks. The number of email is send to the receiver for
getting the information related to the prescription from the doctors, health record information,
blood reports, and others. The distributed denial of service attacks provides an opportunity to
the hacker for retrieving the information of the patients. The modification and manipulation
can be done by the hackers after getting access to the information which can affect the
medical treatment provides to the patients in emergency situation which can have an adverse
effect on the health of the patients.
Man in the Middle attack: The man in the middle attack increases the association of
vulnerabilities in the passage of network traffic [3]. The viruses and Trojan horse malware
get attached with the health record information of the patients by the hackers.
IP spoofing: The hackers manipulate the information of the transmitted message by getting
access to the identity of the authorised users. There are no methods deployed for specifying
the validation of the authentic control used by the user for manipulating and modifying the
transmitted message. The IP spoofing attacks can be categorised as URL spoofing, email
spoofing, DNS spoofing, and MAC spoofing.
5. Solution to resolve the security issues
The recent developments are proceedings to make health care network secure by making use
of quantum cryptography. The quantum cryptography procedures help in ensuring the
security of the data and information flow over the network. It is the best solution to preserve
the patient health records from the Denial of service attacks.
information, restricting the modification and manipulation in the health records of the
patients from the third party, monitoring of account access by the authorised and
unauthorised user, maintaining reliability and accuracy of the information, and others [4].
The patients can get instant and accurate treatment by providing reliable information to the
doctor at the time of emergency.
4. Current and future potential security issues in healthcare networks
The security issues which are associated with the health care networks are identified as
follows:
Denial of service attack: The hackers made use of tactic, technology, and process for hacking
the information from the healthcare networks. The number of email is send to the receiver for
getting the information related to the prescription from the doctors, health record information,
blood reports, and others. The distributed denial of service attacks provides an opportunity to
the hacker for retrieving the information of the patients. The modification and manipulation
can be done by the hackers after getting access to the information which can affect the
medical treatment provides to the patients in emergency situation which can have an adverse
effect on the health of the patients.
Man in the Middle attack: The man in the middle attack increases the association of
vulnerabilities in the passage of network traffic [3]. The viruses and Trojan horse malware
get attached with the health record information of the patients by the hackers.
IP spoofing: The hackers manipulate the information of the transmitted message by getting
access to the identity of the authorised users. There are no methods deployed for specifying
the validation of the authentic control used by the user for manipulating and modifying the
transmitted message. The IP spoofing attacks can be categorised as URL spoofing, email
spoofing, DNS spoofing, and MAC spoofing.
5. Solution to resolve the security issues
The recent developments are proceedings to make health care network secure by making use
of quantum cryptography. The quantum cryptography procedures help in ensuring the
security of the data and information flow over the network. It is the best solution to preserve
the patient health records from the Denial of service attacks.

There are different parameters and algorithms are developed for maintaining the privacy of
the information such as public key infrastructure. The most preferred technology for
encrypting the sensitive information from cyber-attack is Quantum cryptography. The
quantum channel is used for sending the data in the form of photons. The encrypted message
is sent along with one time pad (OTP) information at the receiver end for decrypting the
cipher text. The data transfer can be effectively carried out for the transmission of
confidential data by using OTP. The quantum mechanics is used for designing the
cryptographic procedures and protocols. The polarization of the photons is used for analysing
the occurrence of eavesdropping during the transmission of information. The secret key is
created by using the mathematical formulas and functions for analysing the occurrence of
eaves dropper.
The strength of the quantum cryptography can be measured on the basis of following
attributes and characteristics:
Confidentiality: The secret keys are developed by making use of quantum functions
to enhance its confidentiality. The security of the data and information of the patients
health record can be enhanced by analysing the distribution of key among sender and
receiver for its decryption. The decryption and encryption of the data and information
is carried out through the use of quantum mechanics. The logical problems of
distributing the secrets keys can be solved by using the procedures of quantum
cryptography.
Authorization: The denial of service attacks problems associated with the data and
information of the patient health record can be resolved by putting authorization and
authentication with the use of secret key based on quantum formula. The hash values
and hash functions are used for providing authentication of services to be used by the
receiver. The vulnerabilities associated with the process of hybridization can be
effectively analysed.
Development of rapid secret key for the information exchange process: The key bits
are used for formulating the key distribution encryption procedures. The binary digits
are generated for the encryption and decryption which are known as one time pad
(OTP). The OTP are accepted for providing the authentication to the information. The
information can be fetched by the user by using the one time password which will act
as a secret key for the transaction. The Advanced encryption standards (AES) is used
for developing secret keys to make the program more secure.
the information such as public key infrastructure. The most preferred technology for
encrypting the sensitive information from cyber-attack is Quantum cryptography. The
quantum channel is used for sending the data in the form of photons. The encrypted message
is sent along with one time pad (OTP) information at the receiver end for decrypting the
cipher text. The data transfer can be effectively carried out for the transmission of
confidential data by using OTP. The quantum mechanics is used for designing the
cryptographic procedures and protocols. The polarization of the photons is used for analysing
the occurrence of eavesdropping during the transmission of information. The secret key is
created by using the mathematical formulas and functions for analysing the occurrence of
eaves dropper.
The strength of the quantum cryptography can be measured on the basis of following
attributes and characteristics:
Confidentiality: The secret keys are developed by making use of quantum functions
to enhance its confidentiality. The security of the data and information of the patients
health record can be enhanced by analysing the distribution of key among sender and
receiver for its decryption. The decryption and encryption of the data and information
is carried out through the use of quantum mechanics. The logical problems of
distributing the secrets keys can be solved by using the procedures of quantum
cryptography.
Authorization: The denial of service attacks problems associated with the data and
information of the patient health record can be resolved by putting authorization and
authentication with the use of secret key based on quantum formula. The hash values
and hash functions are used for providing authentication of services to be used by the
receiver. The vulnerabilities associated with the process of hybridization can be
effectively analysed.
Development of rapid secret key for the information exchange process: The key bits
are used for formulating the key distribution encryption procedures. The binary digits
are generated for the encryption and decryption which are known as one time pad
(OTP). The OTP are accepted for providing the authentication to the information. The
information can be fetched by the user by using the one time password which will act
as a secret key for the transaction. The Advanced encryption standards (AES) is used
for developing secret keys to make the program more secure.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Robust protocol: The denial of service attack and eavesdropping procedures can be
effectively analysed by the quantum key distribution which helps in making the
encryption technique more secure and reliable. The point to point flow of information
helps in managing communication between sender and receiver [2]. The mesh
topology is used for making the cryptographic procedure more reliable and robust.
Independence of quantum key distribution: The security architecture can be developed
by making use of Internet protocol because the IP protocol is used for highlighting the
path of destination to the photons which are used for sending the information to the
client machine.
Traffic and congestion control: The heavy flow of information and data can be
controlled managing the point to point connection by using the quantum key
distribution protocol. It helps in analysing the strength and the weakness of the
network in maintaining the confidentiality and reliability of the information.
6. Conclusion
It can be concluded that the focus should be given on analysing the security risks associated
with the health care networks should be taken under consideration so that the patients can get
effective treatment in emergency situation. The denial of service attacks can be managed and
prevented by initializing the parameters of quantum cryptography procedures and protocols.
7. References:
[1]S. Mohapatra, B. Swain, and P. Das, Comprehensive survey of possible security issues on
4G networks, International journal of network security and its application, 7(2), 2015.
[2]S. Islam, D. Kwak, M. Kabir, and K. Kwak, The internet of things for health care: A
Comprehensive sureys, 2015.
[3]M. Meingast, T. Roosta, and S. Sastry, Security and Privacy issues with health care
information technology, 2017.
[4]Cisco, Cisco health care security perspectives: Protect your patients, your practice,
yourself technical implementation guide, 2016.
effectively analysed by the quantum key distribution which helps in making the
encryption technique more secure and reliable. The point to point flow of information
helps in managing communication between sender and receiver [2]. The mesh
topology is used for making the cryptographic procedure more reliable and robust.
Independence of quantum key distribution: The security architecture can be developed
by making use of Internet protocol because the IP protocol is used for highlighting the
path of destination to the photons which are used for sending the information to the
client machine.
Traffic and congestion control: The heavy flow of information and data can be
controlled managing the point to point connection by using the quantum key
distribution protocol. It helps in analysing the strength and the weakness of the
network in maintaining the confidentiality and reliability of the information.
6. Conclusion
It can be concluded that the focus should be given on analysing the security risks associated
with the health care networks should be taken under consideration so that the patients can get
effective treatment in emergency situation. The denial of service attacks can be managed and
prevented by initializing the parameters of quantum cryptography procedures and protocols.
7. References:
[1]S. Mohapatra, B. Swain, and P. Das, Comprehensive survey of possible security issues on
4G networks, International journal of network security and its application, 7(2), 2015.
[2]S. Islam, D. Kwak, M. Kabir, and K. Kwak, The internet of things for health care: A
Comprehensive sureys, 2015.
[3]M. Meingast, T. Roosta, and S. Sastry, Security and Privacy issues with health care
information technology, 2017.
[4]Cisco, Cisco health care security perspectives: Protect your patients, your practice,
yourself technical implementation guide, 2016.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


