Network Security | Task Report
Added on 2022-09-12
11 Pages661 Words21 Views
End of preview
Want to access all the pages? Upload your documents or become a member.
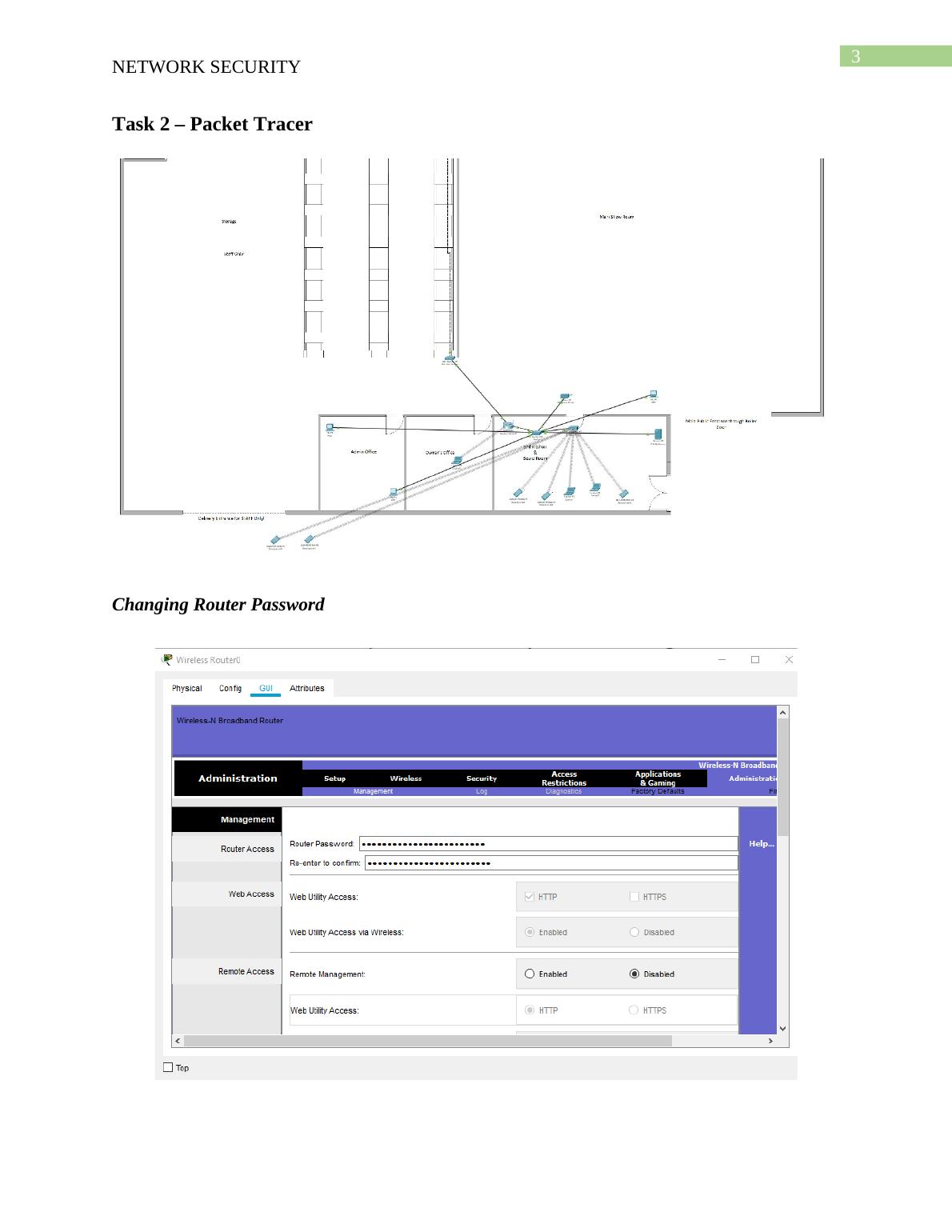
Network Design for Top Network Company
|11
|1135
|334
Advanced Network Design Name of the Student Name of the University Authors Note
|21
|3526
|196
IT Networking and Designing: Proposal for MonkeyNet
|11
|1524
|110
Technology Implementation of Security Controls Template
|14
|4879
|482
Network Design Report for ICT106 Data Communications and Networks
|10
|1566
|337
Network Security Implementation
|20
|3861
|478