Technology Implementation of Security Controls Template
Added on 2021-05-31
14 Pages4879 Words482 Views
Technology Implementation of Security Controls Template*Note: Your technology implementation follows up the strategies and controls you recommended in your network security plan. This template provides guidance on how to document the implementation of the proposed controls.Overview The report is all about First National University (FNU) which is planning to establish connection for all the branches and offices at report location. The campus network of this university is looking for implementation of security technology and applying it in the current network of organization for securing sensitive information of organization. Access control mechanism has been applied to network for providing restriction the unauthorized users for accessing the core network resources of an organization. Access control is mainly based various types like directions of power for users, policy of security and privileged which is allowed to large number of users. The report mainly reflects development of comprehensive network plan of security which is considered like a cost effective and is totally depended on various kinds of security programs. Security can be easily classified many types like personnel security, cyber security and lastly physical security. Present infrastructure of the organization also requires protection along with the implementation of various kinds of associated policies. This can ultimately eliminate the vulnerability of risk which is present in the network. Limitation of various kinds of network resources and security controls will ultimately increase the various kinds of associated risk associated in a network. So a proper kind of decision should be made for application of application or usage of the security control. Various domains of security control and issues must be taken into account for the development of various kinds of network security control. Various kinds of benefits must be obtained by the implementation of security control and it has been mainly done for reducing large number of errors. NETWORK SECURITY- DMZ ZONEObjective of ControlThe ultimate goal of this network implementation is to build a demilitarized zone andfollowed by installation of server in that particular zone. It has been mainly done forpreventing access to staff and local kinds of users. It ultimately creates an additional kind ofnetwork security layer on the provided network which ultimately provides restriction tovarious kinds of local nodes for accessing element which are installed in the demilitarizedzone. Hosts are considered to be vulnerable to various kinds of attacks that is mainly installedin DMZ zones. It is mainly used for providing protection to rest of network from variouskinds of attacks.*Networks and Information Security Case study - Copyright © Edilson Arenas - CQUniversity

Resources UsedDMZ is mainly configured on router for establishing of DMZ zone. It needs to be work outconfigured as per the rules of DMZ firewall. Various other kinds of resources are needed forDMZ zone on firewall, Servers.Developing the control The development of DMZ zones and configuration of emails server is mainly remainsassociated to email server in DMZ. This mainly works for associated email and databasewhich can be used in various kinds of primary servers. Information can be only accessedfrom various kinds of mail servers which are mainly present in DMZ network and access isprovided to external users. The main notion of email server is mainly used for passingincoming and outgoing emails which are present in the server and internet. Web sides mainlyhandles the communication with internal database as it contains database server and alsocontains some kinds of sensitive information for an organization. Database server must beconnected through a proper firewall which is used for maintaining secure kind of networkcommunication and also aims in maintains overall security of organizational security.Installation of communication proxy servers in the zone of DMZ can be considered to behelpful for understanding various rules and associated standards.Description of the SystemThe development of system comes up with various kinds of methodology which ultimatelyhelps in understanding the infrastructure of the network which is being provided. Two well-known methodology which are used are single firewall and secondly using of two firewall.Single firewall also known as three legged model has a single firewall which comes up threekind of network infrastructure is mainly used for development of DMZ architecture. While inDual firewall mode of DMZ consist of two firewall which comes up with one end in the frontand other end one as back end. Configuration of the systemFor proper configuration of the system the provided external network should be connectedwith interface first of the provided network. Internal network is connected is mainlyconnected with second interface of the provided network and after that a network of DMZ ismainly created on third interface which is mainly present in the network. It is mainly used fortackling various kinds of network traffic in DMZ and associated internal network. Variouscolour codes are mainly used for providing indication of network traffic which is mainlypresent in different network interfaces. It is mainly used for different kinds of colour codeswhich are used in network traffic on various interfaces of network. It is mainly used forincreasing various kinds of security in organizational network on the zone of DMZ. It can beconsidered be more secured with the implementation of two kinds of firewall. Firewall aremainly used in the front end as it allows the traffic of data to easily pass the DMZ. Back endof firewall is mainly used for creating a set up for the traffic to easily pass through theinternal network of DMZ. Test Plan DesignIf a network design is created in certain way that it comes up with various kinds of errors inthe provided configuration of the firewall by making use of same kind of configuration in thesecond firewall as it comes with same kind of error. Firewalls of various kinds of brands*Networks and Information Security Case study - Copyright © Edilson Arenas - CQUniversity

should be used at the provided entry and exit place. This should be used in such a waymistake of configuration is much lowered. A penetration test must be there so that it caneasily identify the needs of security of the network and various kinds of errors can be easilyresolved which are found in the organization. A penetration test should be done on thenetwork for analysing various needs in the network. This test mainly overcomes variouskinds of errors which are found in the network. Host should be connected to a DMZ networkand after that ports for opening must be there for bocking them form any kind of externalaccess. A fake security sense is mainly used for analysing configuration blocking the systemfrom any kind of access made externally. Test Plan ImplementationFor the proper implementation of test plan the network should be configured in such a waythat various firewall devices are installed in the network. There large number of tools fornetwork configuration which is mainly used for analysing or checking various kinds ofvulnerabilities which are present in the network and after that proper kind of testing ofnetwork must be done.Test Results and AnalysisFor proper analysis of result of test, it has been concluded that various kinds of networks canbe kept secured from various kinds of external agents and so the vulnerability of the systemshould be kept secured from various kinds of solution for network. Network security- Radius serverObjective of ControlImplementation of thee Radius server mainly focus on the fact that it can easily help in servermanagement for the users which are connected in the network. It mainly focuses on the factof authorization and mechanism of authentication which is used for securing the variousresources which are mainly present in the provided network. It also aims in providingwireless networks and internal networks which is used for management of various integratedweb services. Resources UsedThe ultimate resource which has been used for maintaining and running of radius in various system is all about understanding the various requirement of the system and as per that servermust be chosen.Developing the control Radius authentication is mainly used by various kinds of devices and is mainly used for configuration of information which is provided which mainly comes with one or more Radiuskinds of server which is present in the network. It can be mainly achieved by the help of statement of radius server which is present at the Radius server. This can easily take place due to the fact remote authentication is properly configured on large number of devices. It comes up with common configuration for large group of people. This is mainly inclusive of adding up of server address of IPv6 and IPv4, which is ultimately followed by strong kind of password. In many it is seen that various kinds of server of Radius server can be contacted easily. The default provided port number is 1812. After this the provided order is mainly specified in which the provided system can itself authenticate. *Networks and Information Security Case study - Copyright © Edilson Arenas - CQUniversity

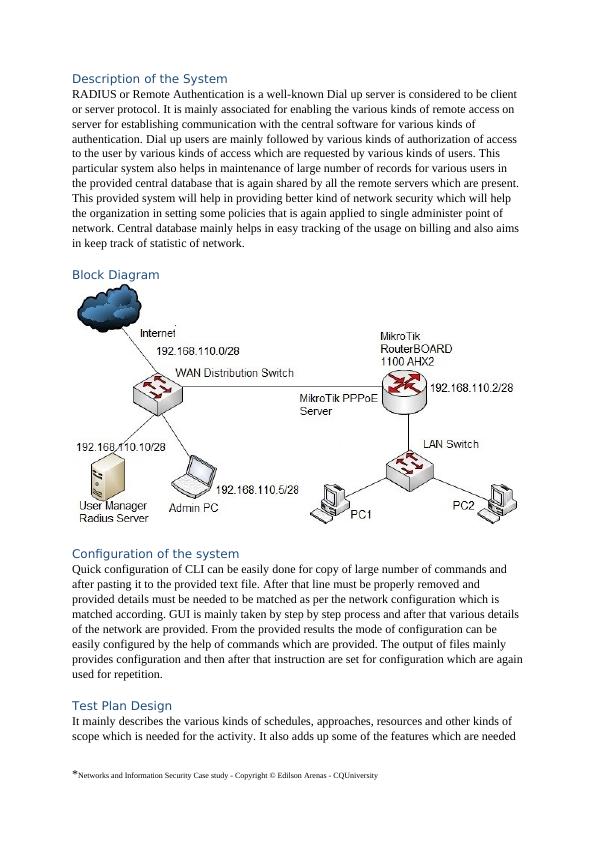
Description of the SystemRADIUS or Remote Authentication is a well-known Dial up server is considered to be client or server protocol. It is mainly associated for enabling the various kinds of remote access on server for establishing communication with the central software for various kinds of authentication. Dial up users are mainly followed by various kinds of authorization of access to the user by various kinds of access which are requested by various kinds of users. This particular system also helps in maintenance of large number of records for various users in the provided central database that is again shared by all the remote servers which are present. This provided system will help in providing better kind of network security which will help the organization in setting some policies that is again applied to single administer point of network. Central database mainly helps in easy tracking of the usage on billing and also aims in keep track of statistic of network. Block DiagramConfiguration of the systemQuick configuration of CLI can be easily done for copy of large number of commands and after pasting it to the provided text file. After that line must be properly removed and provided details must be needed to be matched as per the network configuration which is matched according. GUI is mainly taken by step by step process and after that various details of the network are provided. From the provided results the mode of configuration can be easily configured by the help of commands which are provided. The output of files mainly provides configuration and then after that instruction are set for configuration which are againused for repetition. Test Plan DesignIt mainly describes the various kinds of schedules, approaches, resources and other kinds of scope which is needed for the activity. It also adds up some of the features which are needed *Networks and Information Security Case study - Copyright © Edilson Arenas - CQUniversity
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Security Presentation and Guidebook - IT Securitylg...
|10
|1587
|18
Advanced Diploma of Computer System Technology - Network Infrastructure Managementlg...
|12
|559
|180
VPN & Firewalllg...
|5
|693
|92
Firewallslg...
|17
|1394
|368
Prevention of DoS Attacks: Methods and Strategieslg...
|12
|2585
|100
Pen Testing | Questions and Answerslg...
|8
|619
|55