7COM1029 Advanced Networking Concepts: Network Services Report 2019-20
VerifiedAdded on 2022/09/18
|17
|2436
|19
Report
AI Summary
This report provides a comprehensive overview of network services, delving into the intricacies of network design, implementation, and security. It begins with an abstract and introduction, followed by background information and a literature review, setting the stage for the core content. The report covers network diagrams, experimental analysis, and testing and evaluation of various network configurations, including DHCP and DNS server installations, QoS implementation, and SSH security. It also explores penetration testing to assess network vulnerabilities. The report concludes with a summary of findings and references, providing a complete guide to network services. The report covers the topology and architectural design of the company, proposed design for the improvement of the company, the layouts of the floor plans and their dimensions, the workstation’s interconnection and its enhancements, and specifications of the network equipment.

Running head: REPORT ON NETWORK network SERVICES
By
Academic Year: 2019-20
Module: Network network Services
By
Academic Year: 2019-20
Module: Network network Services
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
Table of content
Abstract .............................................................................................................2
Introduction........................................................................................................3
Background Information....................................................................................3
Literature Review..............................................................................................4
Scope and limitations.........................................................................................5
Network Diagram...............................................................................................6
Experimental Analysis.......................................................................................7
Testing and Evaluation......................................................................................14
Conclusion..........................................................................................................16
References...........................................................................................................17
Table of content
Abstract .............................................................................................................2
Introduction........................................................................................................3
Background Information....................................................................................3
Literature Review..............................................................................................4
Scope and limitations.........................................................................................5
Network Diagram...............................................................................................6
Experimental Analysis.......................................................................................7
Testing and Evaluation......................................................................................14
Conclusion..........................................................................................................16
References...........................................................................................................17

2
Abstract
Network structure and Implementation are critical for any business arrangement. An
inadequately structured condition can cause security and execution issues. Not exclusively
does making a network configuration help our professionals execute the business arrange, yet
it additionally makes future adaptability and specialized help a lot easier errand to perform.
Thusly giving simplicity of workstream for clients and stays with the network running better.
By considering all the business needs, viably full filling those requirements, and supporting
end clients in the midst of hardship.
Introduction
Creating a business IT network isn't as straightforward as simply interfacing your gadgets,
there are numerous different components to consider. An ineffectively structured network
may work today, yet may have deadly issues tomorrow, as a result of ill-conceived
versatility. To make a decent network configuration includes comprehension of explicit
gadgets, their development confinements, permitting, appropriate wiring just as the simplicity
of adaptability and highlights. A network can be structured depending on the present
information traffic, however, it is in every case great to anticipate an expansion in rush hour
gridlock and having the option to effectively scale up to suit it. Choices made basically
dependent on cost reserve funds and never the less making a greater emergency just as an
expanded cost overall. While making plans customers spending plans and potential
development are significant factors in the picking appropriate gadgets, programming
authorizing and what sort of network is required by the business. Acquainting ourselves with
Abstract
Network structure and Implementation are critical for any business arrangement. An
inadequately structured condition can cause security and execution issues. Not exclusively
does making a network configuration help our professionals execute the business arrange, yet
it additionally makes future adaptability and specialized help a lot easier errand to perform.
Thusly giving simplicity of workstream for clients and stays with the network running better.
By considering all the business needs, viably full filling those requirements, and supporting
end clients in the midst of hardship.
Introduction
Creating a business IT network isn't as straightforward as simply interfacing your gadgets,
there are numerous different components to consider. An ineffectively structured network
may work today, yet may have deadly issues tomorrow, as a result of ill-conceived
versatility. To make a decent network configuration includes comprehension of explicit
gadgets, their development confinements, permitting, appropriate wiring just as the simplicity
of adaptability and highlights. A network can be structured depending on the present
information traffic, however, it is in every case great to anticipate an expansion in rush hour
gridlock and having the option to effectively scale up to suit it. Choices made basically
dependent on cost reserve funds and never the less making a greater emergency just as an
expanded cost overall. While making plans customers spending plans and potential
development are significant factors in the picking appropriate gadgets, programming
authorizing and what sort of network is required by the business. Acquainting ourselves with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
the kind of business, business needs, and objectives is useful to comprehend what different
elements to consider. Extra gadgets that might be required, for example, Wireless switch or
remote passage for versatile availability. Actualizing another network or redesigning a
current one depends on the exact execution of the plan factors referenced previously. The
arranging stage looks to confine disturbances in the organization utilizing a staged
methodology. During the execution stage, the Technical Framework will assist you with
planning with representatives, office heads, and outside merchants. Clear correspondence in
regards to the extent of every usage stage will keep everybody educated and help staff to
restrain the effect of normal personal times.
Background information
To the discussion of the links, you can utilize the wound pair (otherwise called 10BaseT) or
the flimsy urge (otherwise called 10Base2) for your system link. The decision,
notwithstanding, will rely upon the kind of system you're setting. You can utilize both the
sorts together. Turned pair cabling is less expensive, adaptable, and perfect for cabling short
separations. You can utilize slight cajole for bigger systems. A system interface card (NIC)
associates the system PC to the system cabling. While some NICs are introduced inside the
PC others may require PCI openings(Breed, Automotive Technologies International Inc,
2020).
Literature review
PC systems speak to one of the significant drivers behind ongoing progressions in the
Information and Communication Technology (ICT) field. Accordingly, PC organizing
research facilities are a distinct advantage for those scholarly associations that expect to give
the kind of business, business needs, and objectives is useful to comprehend what different
elements to consider. Extra gadgets that might be required, for example, Wireless switch or
remote passage for versatile availability. Actualizing another network or redesigning a
current one depends on the exact execution of the plan factors referenced previously. The
arranging stage looks to confine disturbances in the organization utilizing a staged
methodology. During the execution stage, the Technical Framework will assist you with
planning with representatives, office heads, and outside merchants. Clear correspondence in
regards to the extent of every usage stage will keep everybody educated and help staff to
restrain the effect of normal personal times.
Background information
To the discussion of the links, you can utilize the wound pair (otherwise called 10BaseT) or
the flimsy urge (otherwise called 10Base2) for your system link. The decision,
notwithstanding, will rely upon the kind of system you're setting. You can utilize both the
sorts together. Turned pair cabling is less expensive, adaptable, and perfect for cabling short
separations. You can utilize slight cajole for bigger systems. A system interface card (NIC)
associates the system PC to the system cabling. While some NICs are introduced inside the
PC others may require PCI openings(Breed, Automotive Technologies International Inc,
2020).
Literature review
PC systems speak to one of the significant drivers behind ongoing progressions in the
Information and Communication Technology (ICT) field. Accordingly, PC organizing
research facilities are a distinct advantage for those scholarly associations that expect to give
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
their understudies the essential offices for testing just as learning fundamental and propelled
ideas in systems administration. In conventional processing research centers, standard clients
are not permitted to adjust the creation arrange framework or change the workstation
organize settings, as this may cause serious issues as far as administration accessibility and
conveyed asset the executives. Commonly, clients of a PC organizing lab are understudies
learning and exploring different avenues regarding the system itself. Along these lines, they
ought to be permitted to investigate genuine hardware, change the system topology, and
deliberately cause and take care of disappointments and other network issues so as to see how
things work, in actuality, situations. As a result, completely utilitarian systems administration
research center offices are hard to configuration, execute and oversee while consenting to
spend plan, scholastic and the executive's targets(Johansson et al., 2019). Thus, PC
organizing tests are regularly executed inside virtual or mimicked conditions, despite the fact
that this methodology may confine the understudy learning experience. This is the method of
reasoning behind the improvement of PC organizing research centers joining creative
administration frameworks. These frameworks permit the execution of all the necessary PC
and hardware upkeep errands in a proficient manner while as yet supporting genuine hands-
on (i.e., not reproduced) encounters for understudies just as giving proving ground
arrangements to examine exercises. The primary commitment of this paper is the depiction of
the inventive structure approach received by the creators, who have updated the PC
organizing research center offices for the Telecommunications and Networking Program at
the School of Information Sciences of the University of Pittsburgh. One of the key parts of
the received plan is the usage of a productive research facility the board structure and an
adaptable topology building technique that permits clients to completely abuse the physical
lab framework for a wide scope of system setups. Another significant element is the
circulated idea of the research facility framework, which permits various groups of
their understudies the essential offices for testing just as learning fundamental and propelled
ideas in systems administration. In conventional processing research centers, standard clients
are not permitted to adjust the creation arrange framework or change the workstation
organize settings, as this may cause serious issues as far as administration accessibility and
conveyed asset the executives. Commonly, clients of a PC organizing lab are understudies
learning and exploring different avenues regarding the system itself. Along these lines, they
ought to be permitted to investigate genuine hardware, change the system topology, and
deliberately cause and take care of disappointments and other network issues so as to see how
things work, in actuality, situations. As a result, completely utilitarian systems administration
research center offices are hard to configuration, execute and oversee while consenting to
spend plan, scholastic and the executive's targets(Johansson et al., 2019). Thus, PC
organizing tests are regularly executed inside virtual or mimicked conditions, despite the fact
that this methodology may confine the understudy learning experience. This is the method of
reasoning behind the improvement of PC organizing research centers joining creative
administration frameworks. These frameworks permit the execution of all the necessary PC
and hardware upkeep errands in a proficient manner while as yet supporting genuine hands-
on (i.e., not reproduced) encounters for understudies just as giving proving ground
arrangements to examine exercises. The primary commitment of this paper is the depiction of
the inventive structure approach received by the creators, who have updated the PC
organizing research center offices for the Telecommunications and Networking Program at
the School of Information Sciences of the University of Pittsburgh. One of the key parts of
the received plan is the usage of a productive research facility the board structure and an
adaptable topology building technique that permits clients to completely abuse the physical
lab framework for a wide scope of system setups. Another significant element is the
circulated idea of the research facility framework, which permits various groups of

5
understudies to work at the same time so as to encourage collaboration and give involvement
with filling in as a group.
Scope and limitations
The study covers the topology and architectural design of the company.
The proponents include the proposed design for the improvement of the company.
The layouts of the floor plans and their dimensions.
The workstation’s interconnection and its enhancements.
Specifications of the network equipment (Pope, Tauritz, and Rawlings, 2019, July).
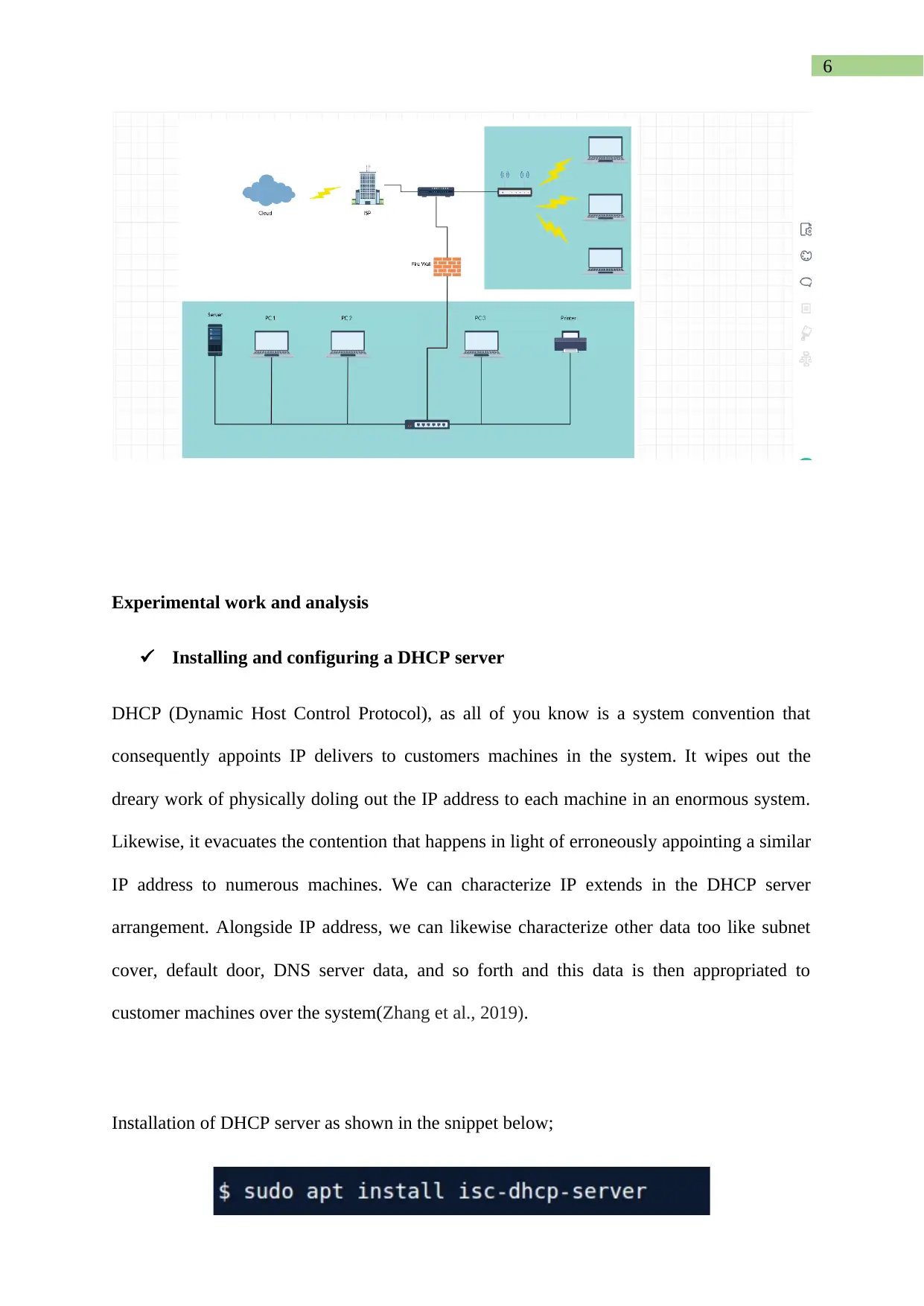
Network Diagram
understudies to work at the same time so as to encourage collaboration and give involvement
with filling in as a group.
Scope and limitations
The study covers the topology and architectural design of the company.
The proponents include the proposed design for the improvement of the company.
The layouts of the floor plans and their dimensions.
The workstation’s interconnection and its enhancements.
Specifications of the network equipment (Pope, Tauritz, and Rawlings, 2019, July).
Network Diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
Experimental work and analysis
Installing and configuring a DHCP server
DHCP (Dynamic Host Control Protocol), as all of you know is a system convention that
consequently appoints IP delivers to customers machines in the system. It wipes out the
dreary work of physically doling out the IP address to each machine in an enormous system.
Likewise, it evacuates the contention that happens in light of erroneously appointing a similar
IP address to numerous machines. We can characterize IP extends in the DHCP server
arrangement. Alongside IP address, we can likewise characterize other data too like subnet
cover, default door, DNS server data, and so forth and this data is then appropriated to
customer machines over the system(Zhang et al., 2019).
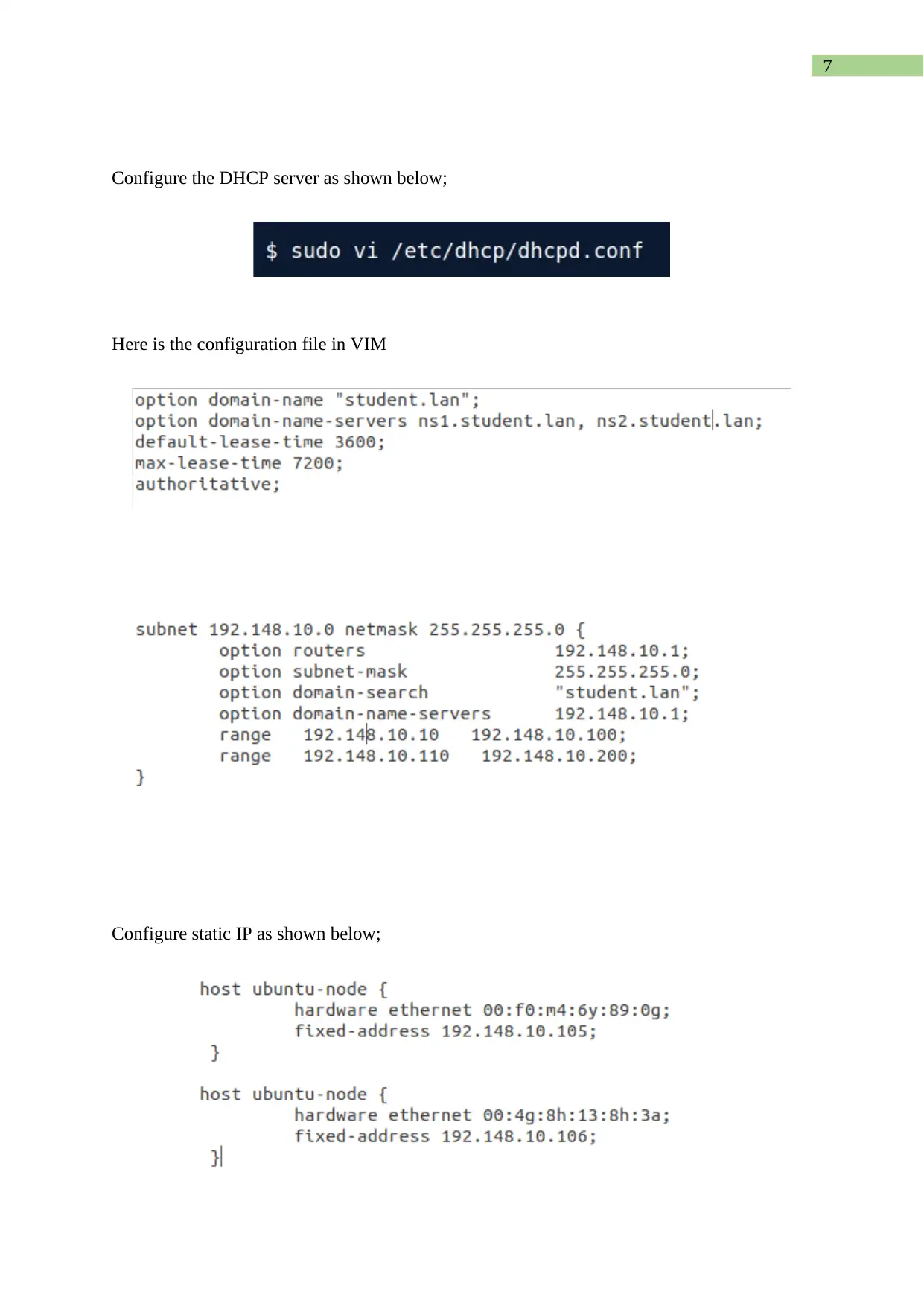
Installation of DHCP server as shown in the snippet below;
Experimental work and analysis
Installing and configuring a DHCP server
DHCP (Dynamic Host Control Protocol), as all of you know is a system convention that
consequently appoints IP delivers to customers machines in the system. It wipes out the
dreary work of physically doling out the IP address to each machine in an enormous system.
Likewise, it evacuates the contention that happens in light of erroneously appointing a similar
IP address to numerous machines. We can characterize IP extends in the DHCP server
arrangement. Alongside IP address, we can likewise characterize other data too like subnet
cover, default door, DNS server data, and so forth and this data is then appropriated to
customer machines over the system(Zhang et al., 2019).
Installation of DHCP server as shown in the snippet below;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
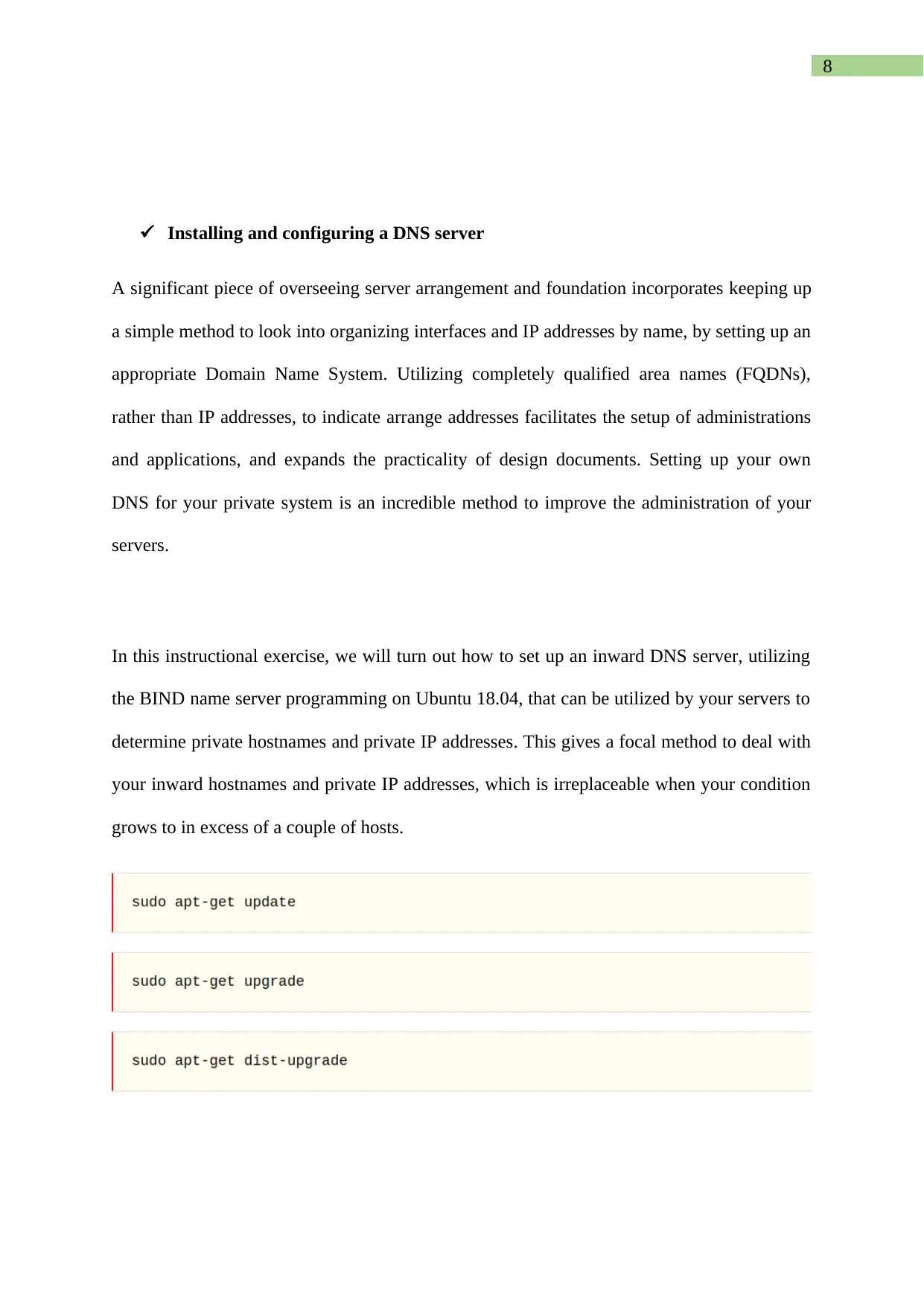
Configure the DHCP server as shown below;
Here is the configuration file in VIM
Configure static IP as shown below;
Configure the DHCP server as shown below;
Here is the configuration file in VIM
Configure static IP as shown below;
8
Installing and configuring a DNS server
A significant piece of overseeing server arrangement and foundation incorporates keeping up
a simple method to look into organizing interfaces and IP addresses by name, by setting up an
appropriate Domain Name System. Utilizing completely qualified area names (FQDNs),
rather than IP addresses, to indicate arrange addresses facilitates the setup of administrations
and applications, and expands the practicality of design documents. Setting up your own
DNS for your private system is an incredible method to improve the administration of your
servers.
In this instructional exercise, we will turn out how to set up an inward DNS server, utilizing
the BIND name server programming on Ubuntu 18.04, that can be utilized by your servers to
determine private hostnames and private IP addresses. This gives a focal method to deal with
your inward hostnames and private IP addresses, which is irreplaceable when your condition
grows to in excess of a couple of hosts.
Installing and configuring a DNS server
A significant piece of overseeing server arrangement and foundation incorporates keeping up
a simple method to look into organizing interfaces and IP addresses by name, by setting up an
appropriate Domain Name System. Utilizing completely qualified area names (FQDNs),
rather than IP addresses, to indicate arrange addresses facilitates the setup of administrations
and applications, and expands the practicality of design documents. Setting up your own
DNS for your private system is an incredible method to improve the administration of your
servers.
In this instructional exercise, we will turn out how to set up an inward DNS server, utilizing
the BIND name server programming on Ubuntu 18.04, that can be utilized by your servers to
determine private hostnames and private IP addresses. This gives a focal method to deal with
your inward hostnames and private IP addresses, which is irreplaceable when your condition
grows to in excess of a couple of hosts.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
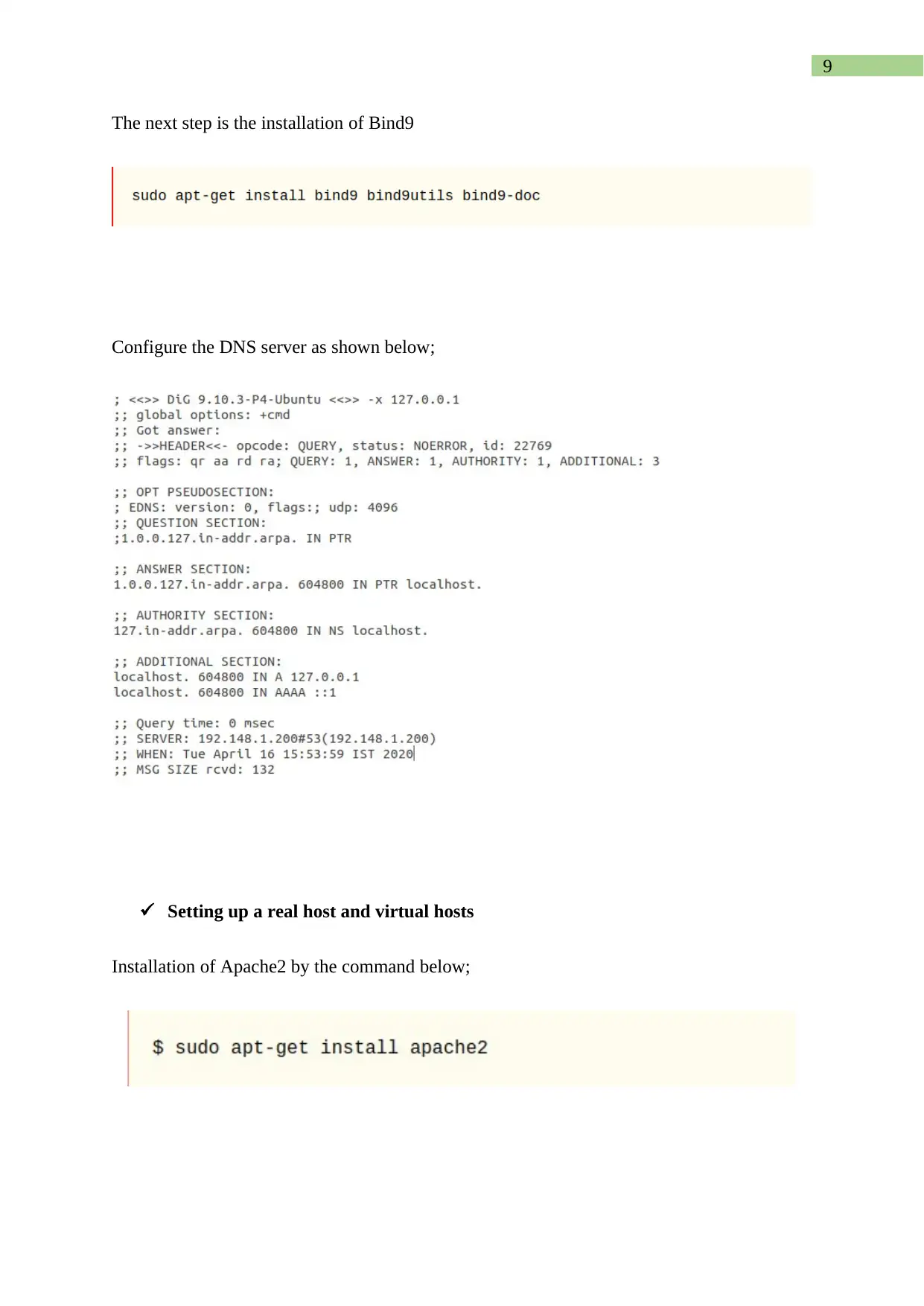
The next step is the installation of Bind9
Configure the DNS server as shown below;
Setting up a real host and virtual hosts
Installation of Apache2 by the command below;
The next step is the installation of Bind9
Configure the DNS server as shown below;
Setting up a real host and virtual hosts
Installation of Apache2 by the command below;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
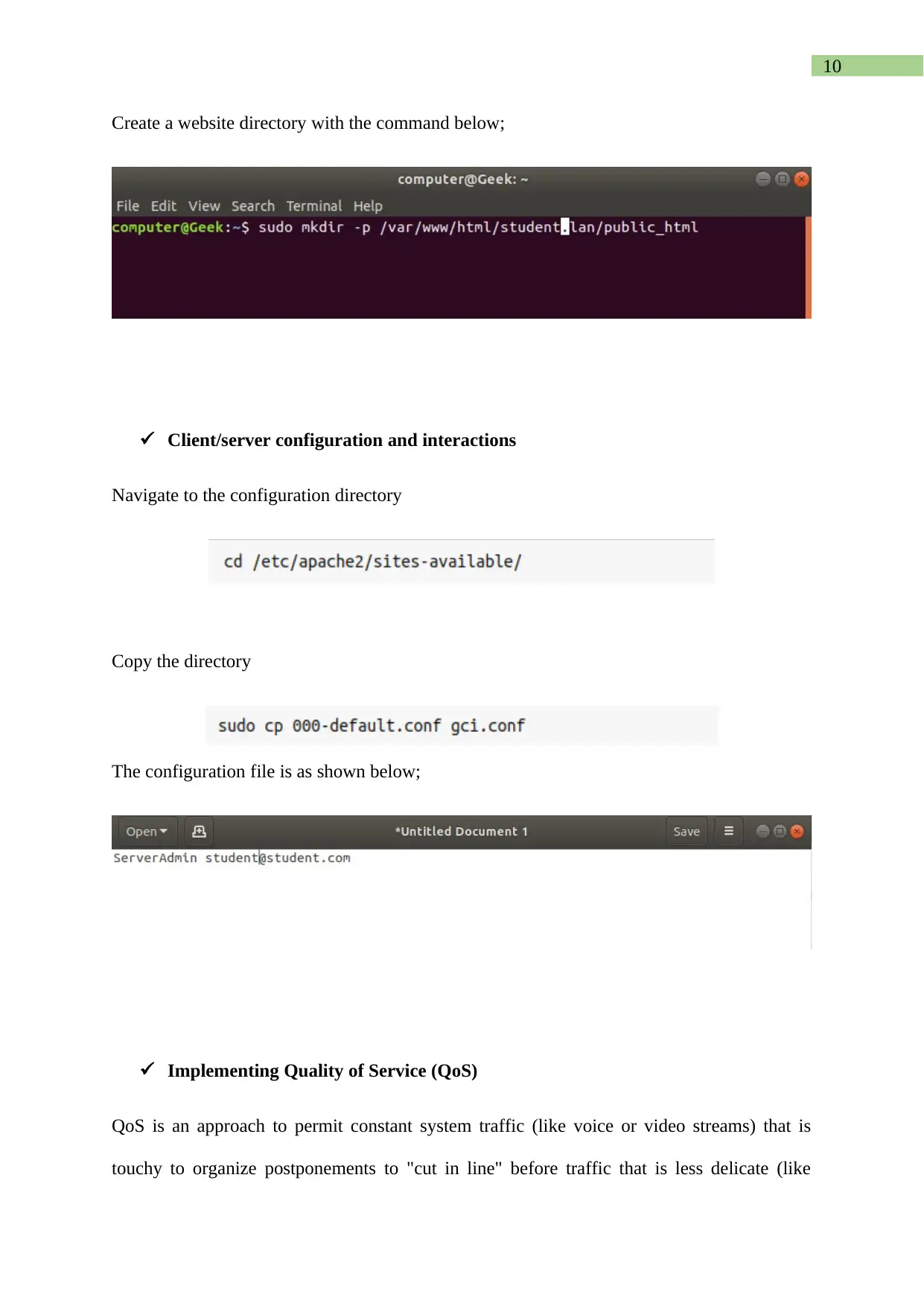
Create a website directory with the command below;
Client/server configuration and interactions
Navigate to the configuration directory
Copy the directory
The configuration file is as shown below;
Implementing Quality of Service (QoS)
QoS is an approach to permit constant system traffic (like voice or video streams) that is
touchy to organize postponements to "cut in line" before traffic that is less delicate (like
Create a website directory with the command below;
Client/server configuration and interactions
Navigate to the configuration directory
Copy the directory
The configuration file is as shown below;
Implementing Quality of Service (QoS)
QoS is an approach to permit constant system traffic (like voice or video streams) that is
touchy to organize postponements to "cut in line" before traffic that is less delicate (like

11
downloading another application, where an additional second to download is definitely not a
serious deal). QoS recognizes and denotes all bundles progressively streams (utilizing
Windows Group Policy Objects and a steering highlight called Port-based Access Control
Lists, increasingly about those is beneath) which at that point encourages your system to give
voice, video, and screen share streams a committed segment of system data transfer capacity.
Without some type of QoS, you may see the accompanying quality issues in voice and video:
Jitter – media bundles showing up at various rates, which can bring about missing
words or syllables in calls.
Bundle misfortune – parcels dropped, which can likewise bring about speak with
softer tone quality and difficult to get discourse.
Postponed full circle time (RTT) – media bundles setting aside a long effort to arrive
at their goals, which brings about observable deferrals between two gatherings in a
discussion, making individuals talk over one another.
The least perplexing approach to deliver these issues is to build the size of the information
associations, both inside and out to the web. Since that is regularly cost-restrictive, QoS gives
an approach to all the more successfully deal with the assets you have as opposed to
including new assets. To completely address quality issues you would utilize QoS over the
usage, at that point include network just where totally vital.
For QoS to be successful, you will have reliable QoS settings applied start to finish in your
association, on the grounds that any piece of the way that neglects to help your QoS needs
downloading another application, where an additional second to download is definitely not a
serious deal). QoS recognizes and denotes all bundles progressively streams (utilizing
Windows Group Policy Objects and a steering highlight called Port-based Access Control
Lists, increasingly about those is beneath) which at that point encourages your system to give
voice, video, and screen share streams a committed segment of system data transfer capacity.
Without some type of QoS, you may see the accompanying quality issues in voice and video:
Jitter – media bundles showing up at various rates, which can bring about missing
words or syllables in calls.
Bundle misfortune – parcels dropped, which can likewise bring about speak with
softer tone quality and difficult to get discourse.
Postponed full circle time (RTT) – media bundles setting aside a long effort to arrive
at their goals, which brings about observable deferrals between two gatherings in a
discussion, making individuals talk over one another.
The least perplexing approach to deliver these issues is to build the size of the information
associations, both inside and out to the web. Since that is regularly cost-restrictive, QoS gives
an approach to all the more successfully deal with the assets you have as opposed to
including new assets. To completely address quality issues you would utilize QoS over the
usage, at that point include network just where totally vital.
For QoS to be successful, you will have reliable QoS settings applied start to finish in your
association, on the grounds that any piece of the way that neglects to help your QoS needs
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




