Information Technology Networking 2022
VerifiedAdded on 2022/08/22
|6
|1887
|13
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

NETWORKING 1
Abstract
IoT is a part of information technology that helps to interconnect computers, networks, and machines easily and
provide data transmission facilities to the companies. It is capable to transfer data from one location to another and
monitor computing devices easily. Security is a problem associated with IoT networks due to which companies can
suffer from cyber-crimes and data breach concerns. This paper focusses on the security implications of IoT networks
and highlighted social, ethical and professional concerns linked to the IoT technology. It is found that misconfiguration
and unauthorized access both are major factors leading security threats in IoT networks and GDPR provides a way to
secure data of individuals in the workplace. So, it is suggested that companies should provide training to the members
and include firewall and encryption-based systems for securing data and managing cyber-crimes.
Keywords: IoT, security issues, firewall, encryption, and GDPR.
Introduction
IoT is a kind of system which is capable to interconnect computing networks, machines, devices and systems with each
other and able to transfer signals over computing networks without needing human-to-human communication. In this
modern generation, the uses of IoT networks are enhancing rapidly and many companies are moving towards IoT due
to their capability to enhance business performance and manage communication gaps (Frustaci, et al., 2017). Security
is a major concern linked with the IoT networks that negatively impact on the performance of computing devices and
personal data of the companies. The purpose of the investigation is to review the security implications of IoT networks
and highlight the effect of GDPR on data. This paper will include various points such as IoT protocols, the effect of
GDPR, ethical and social issues linked to IoT, appropriate security policies and many more.
Background
IoT is an effective technology that provides a way to perform data transmission over computing networks easily and
companies are adopting IoT based networks for performing business operations and managing communication-related
concerns. Khan and Salah, (2018) reported that IoT helps companies to enhance organizational performance but also
lead security threats as it includes wireless networks and systems which are less secured and can be hacked by
transferring malware signals.
(Source: Khan, and Salah, 2018)
Abstract
IoT is a part of information technology that helps to interconnect computers, networks, and machines easily and
provide data transmission facilities to the companies. It is capable to transfer data from one location to another and
monitor computing devices easily. Security is a problem associated with IoT networks due to which companies can
suffer from cyber-crimes and data breach concerns. This paper focusses on the security implications of IoT networks
and highlighted social, ethical and professional concerns linked to the IoT technology. It is found that misconfiguration
and unauthorized access both are major factors leading security threats in IoT networks and GDPR provides a way to
secure data of individuals in the workplace. So, it is suggested that companies should provide training to the members
and include firewall and encryption-based systems for securing data and managing cyber-crimes.
Keywords: IoT, security issues, firewall, encryption, and GDPR.
Introduction
IoT is a kind of system which is capable to interconnect computing networks, machines, devices and systems with each
other and able to transfer signals over computing networks without needing human-to-human communication. In this
modern generation, the uses of IoT networks are enhancing rapidly and many companies are moving towards IoT due
to their capability to enhance business performance and manage communication gaps (Frustaci, et al., 2017). Security
is a major concern linked with the IoT networks that negatively impact on the performance of computing devices and
personal data of the companies. The purpose of the investigation is to review the security implications of IoT networks
and highlight the effect of GDPR on data. This paper will include various points such as IoT protocols, the effect of
GDPR, ethical and social issues linked to IoT, appropriate security policies and many more.
Background
IoT is an effective technology that provides a way to perform data transmission over computing networks easily and
companies are adopting IoT based networks for performing business operations and managing communication-related
concerns. Khan and Salah, (2018) reported that IoT helps companies to enhance organizational performance but also
lead security threats as it includes wireless networks and systems which are less secured and can be hacked by
transferring malware signals.
(Source: Khan, and Salah, 2018)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

NETWORKING 2
Figure: IoT networks
So, the utilization of IoT networks may impact on the privacy and lead security threats and cyber-crimes in the
companies and users may lose their sensitive information. This paper will help to examine risk factors leading security
issues in IoT networks and review the role of GDPR in the security of personal information. From recent literature, it is
found that IoT includes computing networks and communication channels where hackers transfer traffic signals and
reduce the confidentiality of data that produces data breach issues in the companies ( Mahmoud, et al., 2015).
Therefore, it is reported that the utilization of IoT networks can lead security threats in the companies but using
effective mitigation techniques and security policies highlighted by GDPR such issues can be managed easily.
The security implications of IoT devices
IoT protocols
Oh, and Kim, (2017) determined that the main current transport layer protocols used in the IoT networks are UDP and
TCP that help to perform operations and communicate effectively over networks. TCP is criticized as an IoT protocol
due to its larger effectiveness and reliability towards wireless communication. There are major four layers involve in
the TCP/IP stack including physical, network, transport, and application layer. The physical layer is an effective
TCP/IP layer that helps IoT networks to establish the interconnection channels in the business. The network layer helps
IoT systems to evaluate each computing device is linked to a similar router and unique numbers. Riahi, et al., (2014)
highlighted that 6LoWPAN is an effective network used in the IoT that helps to connect two or more computing
devices easily. The transport layer plays a significant character in IoT where consumers can control and address
unwanted signals and reduce cyber-attacks effectively. However, the application layer provides communication among
the consumer and the developed sensor applications. In the case of IoT MQTT, AMQP or CoAP protocols are used at
the application layer for performing data communication.
Source: Xu, Wendt, and Potkonjak, (2014)
Figure: IoT networks
So, the utilization of IoT networks may impact on the privacy and lead security threats and cyber-crimes in the
companies and users may lose their sensitive information. This paper will help to examine risk factors leading security
issues in IoT networks and review the role of GDPR in the security of personal information. From recent literature, it is
found that IoT includes computing networks and communication channels where hackers transfer traffic signals and
reduce the confidentiality of data that produces data breach issues in the companies ( Mahmoud, et al., 2015).
Therefore, it is reported that the utilization of IoT networks can lead security threats in the companies but using
effective mitigation techniques and security policies highlighted by GDPR such issues can be managed easily.
The security implications of IoT devices
IoT protocols
Oh, and Kim, (2017) determined that the main current transport layer protocols used in the IoT networks are UDP and
TCP that help to perform operations and communicate effectively over networks. TCP is criticized as an IoT protocol
due to its larger effectiveness and reliability towards wireless communication. There are major four layers involve in
the TCP/IP stack including physical, network, transport, and application layer. The physical layer is an effective
TCP/IP layer that helps IoT networks to establish the interconnection channels in the business. The network layer helps
IoT systems to evaluate each computing device is linked to a similar router and unique numbers. Riahi, et al., (2014)
highlighted that 6LoWPAN is an effective network used in the IoT that helps to connect two or more computing
devices easily. The transport layer plays a significant character in IoT where consumers can control and address
unwanted signals and reduce cyber-attacks effectively. However, the application layer provides communication among
the consumer and the developed sensor applications. In the case of IoT MQTT, AMQP or CoAP protocols are used at
the application layer for performing data communication.
Source: Xu, Wendt, and Potkonjak, (2014)
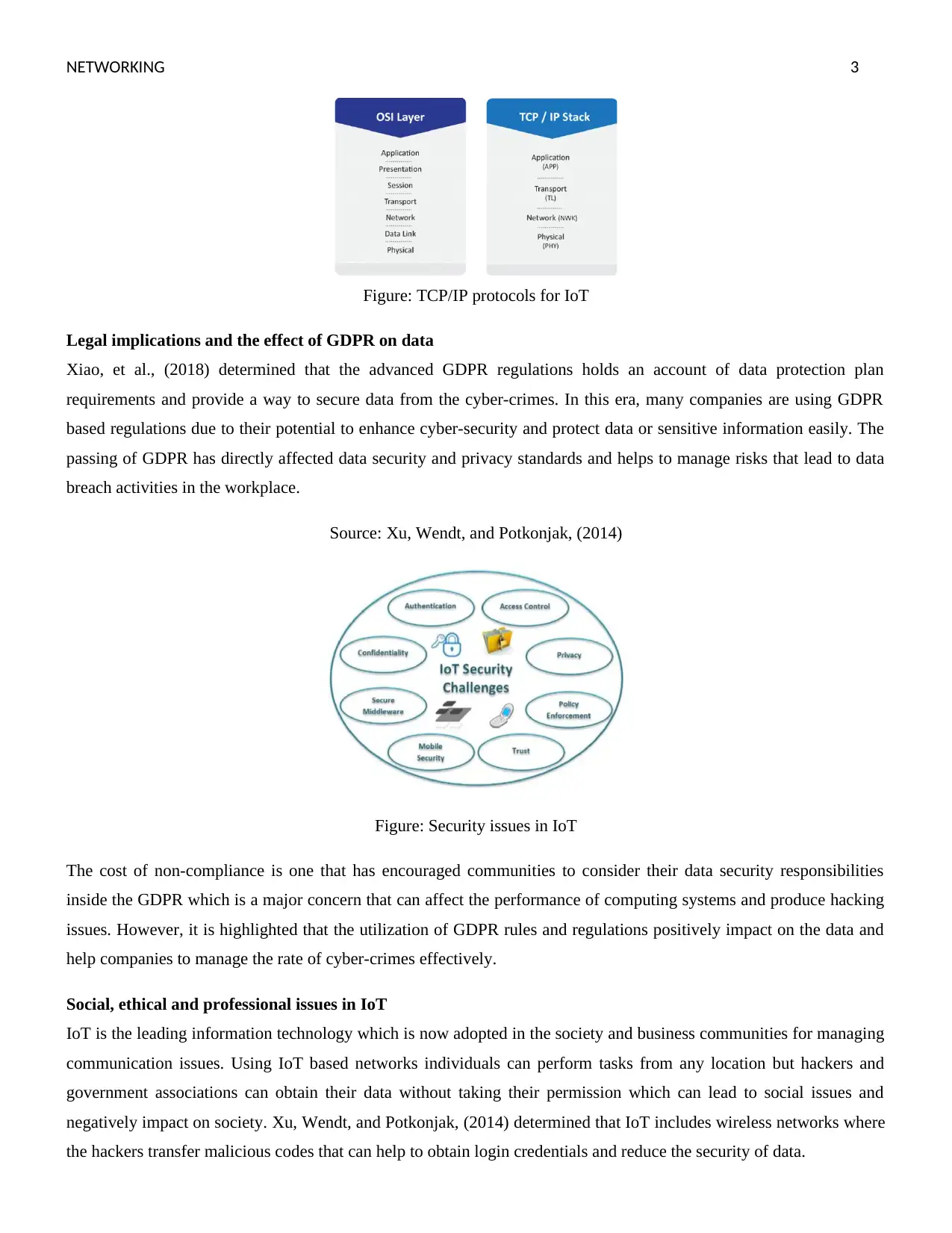
NETWORKING 3
Figure: TCP/IP protocols for IoT
Legal implications and the effect of GDPR on data
Xiao, et al., (2018) determined that the advanced GDPR regulations holds an account of data protection plan
requirements and provide a way to secure data from the cyber-crimes. In this era, many companies are using GDPR
based regulations due to their potential to enhance cyber-security and protect data or sensitive information easily. The
passing of GDPR has directly affected data security and privacy standards and helps to manage risks that lead to data
breach activities in the workplace.
Source: Xu, Wendt, and Potkonjak, (2014)
Figure: Security issues in IoT
The cost of non-compliance is one that has encouraged communities to consider their data security responsibilities
inside the GDPR which is a major concern that can affect the performance of computing systems and produce hacking
issues. However, it is highlighted that the utilization of GDPR rules and regulations positively impact on the data and
help companies to manage the rate of cyber-crimes effectively.
Social, ethical and professional issues in IoT
IoT is the leading information technology which is now adopted in the society and business communities for managing
communication issues. Using IoT based networks individuals can perform tasks from any location but hackers and
government associations can obtain their data without taking their permission which can lead to social issues and
negatively impact on society. Xu, Wendt, and Potkonjak, (2014) determined that IoT includes wireless networks where
the hackers transfer malicious codes that can help to obtain login credentials and reduce the security of data.
Figure: TCP/IP protocols for IoT
Legal implications and the effect of GDPR on data
Xiao, et al., (2018) determined that the advanced GDPR regulations holds an account of data protection plan
requirements and provide a way to secure data from the cyber-crimes. In this era, many companies are using GDPR
based regulations due to their potential to enhance cyber-security and protect data or sensitive information easily. The
passing of GDPR has directly affected data security and privacy standards and helps to manage risks that lead to data
breach activities in the workplace.
Source: Xu, Wendt, and Potkonjak, (2014)
Figure: Security issues in IoT
The cost of non-compliance is one that has encouraged communities to consider their data security responsibilities
inside the GDPR which is a major concern that can affect the performance of computing systems and produce hacking
issues. However, it is highlighted that the utilization of GDPR rules and regulations positively impact on the data and
help companies to manage the rate of cyber-crimes effectively.
Social, ethical and professional issues in IoT
IoT is the leading information technology which is now adopted in the society and business communities for managing
communication issues. Using IoT based networks individuals can perform tasks from any location but hackers and
government associations can obtain their data without taking their permission which can lead to social issues and
negatively impact on society. Xu, Wendt, and Potkonjak, (2014) determined that IoT includes wireless networks where
the hackers transfer malicious codes that can help to obtain login credentials and reduce the security of data.

NETWORKING 4
Source: Zhang, et al., (2014)
Figure: Security concerns in IoT networks
So, using IoT networks, data breach and cyber-crimes can occur in the workplace by which data of users can be lost
which can increase ethical issues in society. Moreover, It stores personal information of companies where hackers can
obtain such information and demand money to restore private information due to which financial issues can be
occurred and hackers can use gathered data for performing illegal activities that may enhance ethical issues. In
companies, managers use IoT based networks and perform business operations through IoT systems that obtain data of
employees and if any malware signal occurred in the system the data of employees can be lost that may lead to
professional issues. So, it is highlighted that the utilization of IoT networks can lead to ethical, social and professional
issues and impact on personal data.
Appropriate policy statements
Zhang, et al., (2014) found that three major risk factors leading security issues in IoT networks such as lack of
awareness, misconfiguration of networks and unauthorized access. For managing such issues, all employees in the
companies should be experienced and able to handle security threats and unwanted signals transmitted by hackers.
Companies should include IT members and provide training to the employees in regard to the uses of IoT networks.
Threat analysis and risk evaluation must be included by the managers while implementing IoT networks. Moreover, the
security process and guidance should be integrated with business processes and include effective security tools like
encryption, firewall and so on. All these are effective policy statements that should be included by the companies for
managing security issues from the IoT networks.
Conclusion
It may be summarized that IoT is an appropriate technology that can be adopted in the business communities but it is
significant to manage and focuses on the security concerns linked to the IoT. This paper identified and evaluated the
security implications of IoT networks and reviewed the effect of GDPR on data of the individuals. It is found that using
IoT networks companies can suffer from security threats and data can be lost easily due to which the managers can
suffer from financial issues and ethical issues. Therefore, it is suggested that organizations should integrate security
policies and plans with business activities and adopt firewall-based systems in the IoT networks for managing security
issues.
Source: Zhang, et al., (2014)
Figure: Security concerns in IoT networks
So, using IoT networks, data breach and cyber-crimes can occur in the workplace by which data of users can be lost
which can increase ethical issues in society. Moreover, It stores personal information of companies where hackers can
obtain such information and demand money to restore private information due to which financial issues can be
occurred and hackers can use gathered data for performing illegal activities that may enhance ethical issues. In
companies, managers use IoT based networks and perform business operations through IoT systems that obtain data of
employees and if any malware signal occurred in the system the data of employees can be lost that may lead to
professional issues. So, it is highlighted that the utilization of IoT networks can lead to ethical, social and professional
issues and impact on personal data.
Appropriate policy statements
Zhang, et al., (2014) found that three major risk factors leading security issues in IoT networks such as lack of
awareness, misconfiguration of networks and unauthorized access. For managing such issues, all employees in the
companies should be experienced and able to handle security threats and unwanted signals transmitted by hackers.
Companies should include IT members and provide training to the employees in regard to the uses of IoT networks.
Threat analysis and risk evaluation must be included by the managers while implementing IoT networks. Moreover, the
security process and guidance should be integrated with business processes and include effective security tools like
encryption, firewall and so on. All these are effective policy statements that should be included by the companies for
managing security issues from the IoT networks.
Conclusion
It may be summarized that IoT is an appropriate technology that can be adopted in the business communities but it is
significant to manage and focuses on the security concerns linked to the IoT. This paper identified and evaluated the
security implications of IoT networks and reviewed the effect of GDPR on data of the individuals. It is found that using
IoT networks companies can suffer from security threats and data can be lost easily due to which the managers can
suffer from financial issues and ethical issues. Therefore, it is suggested that organizations should integrate security
policies and plans with business activities and adopt firewall-based systems in the IoT networks for managing security
issues.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

NETWORKING 5

NETWORKING 6
References
Frustaci, M., Pace, P., Aloi, G. and Fortino, G., (2017) Evaluating critical security issues of the IoT world: Present and
future challenges. IEEE Internet of things journal, 5(4), pp.2483-2495.
Khan, M.A., and Salah, K., (2018) IoT security: Review, blockchain solutions, and open challenges. Future
Generation Computer Systems, 82(6), pp.395-411.
Mahmoud, R., Yousuf, T., Aloul, F. and Zualkernan, I., (2015) Internet of things (IoT) security: Current status,
challenges, and prospective measures. In 2015 10th International Conference for Internet Technology and Secured
Transactions (ICITST), 12(6), pp. 336-341.
Oh, S.R. and Kim, Y.G., (2017) Security requirements analysis for the IoT. In 2017 International Conference on
Platform Technology and Service (PlatCon), 12(6), pp. 1-6.
Riahi, A., Natalizio, E., Challal, Y., Mitton, N. and Iera, A., (2014) A systemic and cognitive approach for IoT
security. In 2014 international conferences on computing, networking, and communications (ICNC), 12(6), pp. 183-
188.
Xiao, L., Wan, X., Lu, X., Zhang, Y. and Wu, D., (2018) IoT security techniques based on machine learning: How do
IoT devices use AI to enhance security?. IEEE Signal Processing Magazine, 35(5), pp.41-49.
Xu, T., Wendt, J.B. and Potkonjak, M., (2014) Security of IoT systems: Design challenges and opportunities. In 2014
IEEE/ACM International Conference on Computer-Aided Design (ICCAD), 12(6). pp. 417-423.
Zhang, Z.K., Cho, M.C.Y., Wang, C.W., Hsu, C.W., Chen, C.K. and Shieh, S., (2014) IoT security: ongoing challenges
and research opportunities. In 2014 IEEE 7th international conference on service-oriented computing and applications,
8(4), pp. 230-234.
References
Frustaci, M., Pace, P., Aloi, G. and Fortino, G., (2017) Evaluating critical security issues of the IoT world: Present and
future challenges. IEEE Internet of things journal, 5(4), pp.2483-2495.
Khan, M.A., and Salah, K., (2018) IoT security: Review, blockchain solutions, and open challenges. Future
Generation Computer Systems, 82(6), pp.395-411.
Mahmoud, R., Yousuf, T., Aloul, F. and Zualkernan, I., (2015) Internet of things (IoT) security: Current status,
challenges, and prospective measures. In 2015 10th International Conference for Internet Technology and Secured
Transactions (ICITST), 12(6), pp. 336-341.
Oh, S.R. and Kim, Y.G., (2017) Security requirements analysis for the IoT. In 2017 International Conference on
Platform Technology and Service (PlatCon), 12(6), pp. 1-6.
Riahi, A., Natalizio, E., Challal, Y., Mitton, N. and Iera, A., (2014) A systemic and cognitive approach for IoT
security. In 2014 international conferences on computing, networking, and communications (ICNC), 12(6), pp. 183-
188.
Xiao, L., Wan, X., Lu, X., Zhang, Y. and Wu, D., (2018) IoT security techniques based on machine learning: How do
IoT devices use AI to enhance security?. IEEE Signal Processing Magazine, 35(5), pp.41-49.
Xu, T., Wendt, J.B. and Potkonjak, M., (2014) Security of IoT systems: Design challenges and opportunities. In 2014
IEEE/ACM International Conference on Computer-Aided Design (ICCAD), 12(6). pp. 417-423.
Zhang, Z.K., Cho, M.C.Y., Wang, C.W., Hsu, C.W., Chen, C.K. and Shieh, S., (2014) IoT security: ongoing challenges
and research opportunities. In 2014 IEEE 7th international conference on service-oriented computing and applications,
8(4), pp. 230-234.
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





