Networking Concepts Assignment - Wireless Local Area Networks
Added on 2020-03-16
11 Pages2124 Words64 Views
Running head: NETWORKING CONCEPTSNetworking ConceptsName of the StudentName of the UniversityAuthor’s Note:

1NETWORKING CONCEPTSTable of ContentsQuestion 1........................................................................................................................................2Question 2.a.....................................................................................................................................3Question 2.b.....................................................................................................................................4Question 3........................................................................................................................................5Question 4........................................................................................................................................7References........................................................................................................................................9

2NETWORKING CONCEPTSQuestion 1Compare and contrast the inner workings of physical layers for 802.11b and 802.11astandards.SolutionThe Wireless Local Area Networks or WLANs with higher speed are extremely popularin all sectors of the world (Vinel, 2012). These sectors are the most important sectors for anysociety. The main standard for the WLANs is the IEEE 802.11. The specification of this 802.11standard is that it specifies the physical layer and the MAC or medium access control for theWLANs. For the physical layer of the WLANs, this particular standard has four typicalstandards. They are the 802.11a, 802.11b, 802.11g and 802.11n (Bayraktaroglu et al., 2013). Thecomparison and contrast between 802.11a and 802.11b are as follows:Key Aspects802.11a802.11b1. Range of FrequencyUp to 5 GHzUp to 2.4 GHz2. Speed or Rate in Mbps6, 9, 12, 18, 24, 36, 48, 541, 2, 5.5, 6, 9, 11, 12, 18, 22,24, 33, 36, 48, 543. ModulationBinary Phase Shift Keying,Quadrature Phase ShiftKeying, 16 QuadratureAmplitude Modulation 64Quadrature AmplitudeModulation (OrthogonalFrequency DivisionMultiplexing)Differential Phase ShiftKeying, DifferentiallyQuadrature Phase ShiftKeying, CCK (DirectSequence Spread Spectrum,FH and IR) 4. FEC Rate1/2, 2/3, 3/4NA5. Base RateUp to 6 MbpsUp to 1 or 2 Mbps6. FunctionsProviding eight PHY modesand transmitting data (Naraei,Amiri & Saberi, 2014).Serves as the interfacebetween physical layer andhost device and the robustnessfeatures are PackerFragmentation and CyclicRedundancy Check or CRC.
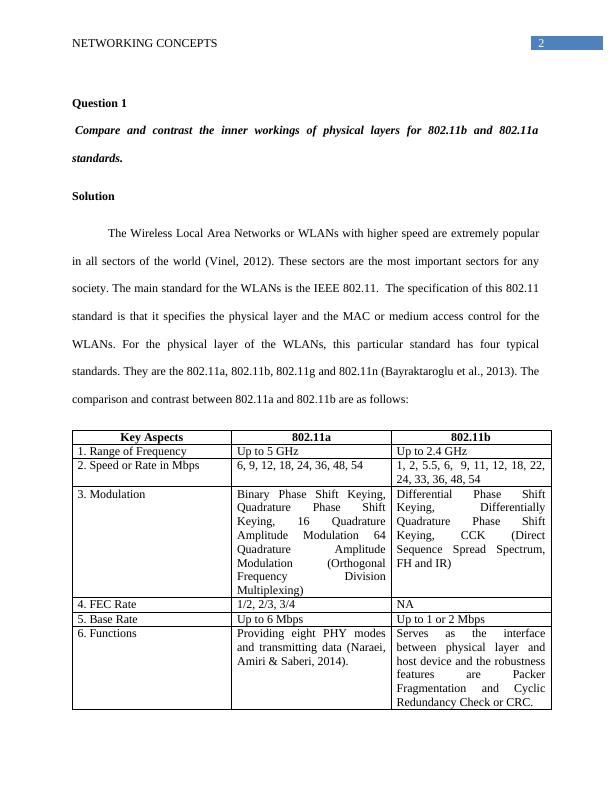
3NETWORKING CONCEPTSThe above table clearly defines about the comparisons and contrasts between the twotypical standards of 802.11, which are the 802.11a and 802.11b. Both of them work in thephysical layer. Question 2.aExplain how 802.11i allows for a client device to be authenticated against an authenticationserver.SolutionThe 802.11i standard enhances the 802.11 with various innovative mechanisms ofsecurity for ensuring the integrity and confidentiality of messages (Alasmary & Zhuang, 2012).Some of the new mechanisms are the additions, and others are the absolute replacements of theprocedures of 802.11. 802.11i also allows any other standard of IEEE which is the 802.1x portauthentication algorithm, for providing a specific framework to obtain a strong management ofkeys and mutual authentication (De Cristofaro et al., 2013). The authentication procedure thatstarts at first is normally carried out by following two distinct ways. One way is to utilize thePre-Shared Key or PSK and the second way is to follow the exchange of EAP via 802.1x. ThisEAP exchange is called as the EAPOL. The authentication server is needed or required to bepresent during the following of EAP exchange (Vinel, 2012). The procedure of EAP exchangemakes sure that client device or the client station is to be authenticated with the help of an accesspoint. Once the pre shared key or the authentication of 802.1x is completed, a new shred secretkey is created (Naraei, Amiri & Saberi, 2014). This is known as the PMK or pair wise master

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Wireless Local Area Networks vs. 802.11blg...
|11
|2332
|256
Outlines a Wireless Local Area Networklg...
|9
|2033
|187
Wireless Networks Assignmentlg...
|12
|2732
|95
Wireless Digital Communications Assignmentlg...
|9
|1877
|266
Wireless Connectivity- Assignmentlg...
|9
|2154
|31
Networking Assignment | Wireless Sensor Networklg...
|13
|2886
|64
