Network Security Design & Implementation Report - BIT243 Course
VerifiedAdded on 2023/03/31
|21
|2437
|494
Report
AI Summary
This report presents a network security solution designed for a small organization with 100 users facing an outdated and unsecured network infrastructure. The proposed solution includes a new network design developed and tested using Cisco Packet Tracer, featuring improved security measures, proper IP addressing, and secured network devices including a firewall. The report discusses the application of Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to enhance security. Network connections are verified through PING tests between devices. The design incorporates two routers, an ASA firewall, access points for wireless networking, and switches for wired connections. The report also touches on the use of DNS, DHCP, encryption, web services, and Active Directory services for centralized authentication, suggesting the introduction of Windows Server 2012 R2 for these roles.
NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
One small organization with 100 users got a out dated network infrastructure. New network
design with many security features are proposed. Cisco pocket tracer is used for designing and
testing the new network design. Proper IP design is done and applied. Secured network devices
are selected for the design. Firewall is used for better security. The application of IPS and IDS
are discussed. Network connections are verified using PING tests between network devices.
1
One small organization with 100 users got a out dated network infrastructure. New network
design with many security features are proposed. Cisco pocket tracer is used for designing and
testing the new network design. Proper IP design is done and applied. Secured network devices
are selected for the design. Firewall is used for better security. The application of IPS and IDS
are discussed. Network connections are verified using PING tests between network devices.
1

Contents
1. Introduction.......................................................................................................................................2
2. Requirements.....................................................................................................................................3
3. Solution Design..................................................................................................................................4
4. Analysis and Evaluation..................................................................................................................14
5. Conclusion........................................................................................................................................15
2
1. Introduction.......................................................................................................................................2
2. Requirements.....................................................................................................................................3
3. Solution Design..................................................................................................................................4
4. Analysis and Evaluation..................................................................................................................14
5. Conclusion........................................................................................................................................15
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
A typical service oriented company is selected for the analysis. The present network got
lot of disadvantages. The network is not secured. It doesn’t have any security measures to protect
data. The company with the 100+ users, 3 branches and supported with 2 routers and one
firewalls. A new well secured network design will be done. Network design is the important part
of technical activity. The network with the three layered viewpoint is excellent. The number of
department and other information are the same for the new design. The network design will be
done using Cisco packet tracer. The design is tested by Cisco packet tracer. IP address settings is
proceeded. The network design is will be verified.
In the requirement, it also explains the need of thinking wireless network. The
network design is explained in this process. In the implementation process, it explains about the
major role of the wireless network. The advantages of using this simulator will be investigated.
2. Requirements
The requirements are given below.
1. Network Design needs to be done.
2. Security needs to be improved in the network design.
3. Network design should be simulated using suitable simulation software.
4. Network design needs to be tested.
5. IDS and IPS needs to be discussed.
6. Firewall should be included in the design.
3
A typical service oriented company is selected for the analysis. The present network got
lot of disadvantages. The network is not secured. It doesn’t have any security measures to protect
data. The company with the 100+ users, 3 branches and supported with 2 routers and one
firewalls. A new well secured network design will be done. Network design is the important part
of technical activity. The network with the three layered viewpoint is excellent. The number of
department and other information are the same for the new design. The network design will be
done using Cisco packet tracer. The design is tested by Cisco packet tracer. IP address settings is
proceeded. The network design is will be verified.
In the requirement, it also explains the need of thinking wireless network. The
network design is explained in this process. In the implementation process, it explains about the
major role of the wireless network. The advantages of using this simulator will be investigated.
2. Requirements
The requirements are given below.
1. Network Design needs to be done.
2. Security needs to be improved in the network design.
3. Network design should be simulated using suitable simulation software.
4. Network design needs to be tested.
5. IDS and IPS needs to be discussed.
6. Firewall should be included in the design.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network design:
The network design is executed by the administrators, engineers, and other network staff.
The network design is used in technical works (Beasley., 2008). It is a key for the success of
business in computer network designing. 24 hours networking is provided for the people. The
speed of the network is considered as most important. (Hallberg, 2013).
The network is nothing but computers. It is used for sending data and information.
They are classified into 7 types.
LAN, WAN, PAN, WLAN, CAN, MAN and SAN
Metropolitan area networks (MANs).
Storage area networks (SANs).
Wide area networks (WANs).
Personal area networks (PANs).
Wireless local area networks (WLANs).
Local area networks (LANs).
Campus area networks (CANs).
Most of the people are using LANs. They are used in schools, offices, and homes.
Networking is good for sharing internet access and files and databases. As you may have been
read in books and movies they used for network designing. The firewalls can be used to filter
unwanted network traffic. Virtual private networks are used to connect remote controlled
security. The VPNs is used for strong data encryption to hide data moving the router.
Networking in very easy to learn which can be learned in a month. The network is a two
or more computer systems linked together. Most important that is often used are network design
and technical work. The good network is necessary for the network verification. The description
of the test plan website is said to be accepted. The plan will be created by the project. The
network designs are modified easily for business improvement. It recognizes goals for the
4
The network design is executed by the administrators, engineers, and other network staff.
The network design is used in technical works (Beasley., 2008). It is a key for the success of
business in computer network designing. 24 hours networking is provided for the people. The
speed of the network is considered as most important. (Hallberg, 2013).
The network is nothing but computers. It is used for sending data and information.
They are classified into 7 types.
LAN, WAN, PAN, WLAN, CAN, MAN and SAN
Metropolitan area networks (MANs).
Storage area networks (SANs).
Wide area networks (WANs).
Personal area networks (PANs).
Wireless local area networks (WLANs).
Local area networks (LANs).
Campus area networks (CANs).
Most of the people are using LANs. They are used in schools, offices, and homes.
Networking is good for sharing internet access and files and databases. As you may have been
read in books and movies they used for network designing. The firewalls can be used to filter
unwanted network traffic. Virtual private networks are used to connect remote controlled
security. The VPNs is used for strong data encryption to hide data moving the router.
Networking in very easy to learn which can be learned in a month. The network is a two
or more computer systems linked together. Most important that is often used are network design
and technical work. The good network is necessary for the network verification. The description
of the test plan website is said to be accepted. The plan will be created by the project. The
network designs are modified easily for business improvement. It recognizes goals for the
4

business and technical requirements. The web server of DNS is improved and it changes the
major applications. The network design will be improved and represents the routing process and
performs addressing in design.
The network design is important to use based on the router and switch, servers. Network
security is based on the overall process and IP addressing is seated. Traffic is controlled by using
the wireless connection. Switch, router and servers and a computer are wireless network.
Antenna, remote are considered as a wireless connection. It also uses the internet connectivity in
a wireless connection. Many connections to connect the same time in to connect the access point
without wire. The network uses people have used the cable connection .wireless connections are
used in radio waves to connect.
Wireless networks are not connected by cables. The use of a wireless network enables
to use of radio waves and make phone calls from many locations worldwide.
There are three major of wireless:
1. Wireless clients or wireless station.
2. Access points
3. Ad-Hoc node.
It is used to connect distant buildings or areas. The long-distance connection is said to be
point-to-point.
The wireless communication system has been a necessary part of various types of
wireless communication devices. The licenses of the user to communicate from telnet operated
areas. They are many devices is used for wireless network communication. It is also used for
cordless telephones, Zigbee wireless technology, Global Positioning System, Wi-Fi, satellite
television, and wireless computer parts. This current technology used for 3G and 4G networks,
Bluetooth and Wi-Fi technologies. Ethical implementation is enforced by the computer which is
used for computing devices The computer ethics plays a major role which used It also
approaches the other devices. Ethical implication is important in WLAN. Wireless area network
is used in educational institutions, business and etc.it is mostly used in corporate environment.
5
major applications. The network design will be improved and represents the routing process and
performs addressing in design.
The network design is important to use based on the router and switch, servers. Network
security is based on the overall process and IP addressing is seated. Traffic is controlled by using
the wireless connection. Switch, router and servers and a computer are wireless network.
Antenna, remote are considered as a wireless connection. It also uses the internet connectivity in
a wireless connection. Many connections to connect the same time in to connect the access point
without wire. The network uses people have used the cable connection .wireless connections are
used in radio waves to connect.
Wireless networks are not connected by cables. The use of a wireless network enables
to use of radio waves and make phone calls from many locations worldwide.
There are three major of wireless:
1. Wireless clients or wireless station.
2. Access points
3. Ad-Hoc node.
It is used to connect distant buildings or areas. The long-distance connection is said to be
point-to-point.
The wireless communication system has been a necessary part of various types of
wireless communication devices. The licenses of the user to communicate from telnet operated
areas. They are many devices is used for wireless network communication. It is also used for
cordless telephones, Zigbee wireless technology, Global Positioning System, Wi-Fi, satellite
television, and wireless computer parts. This current technology used for 3G and 4G networks,
Bluetooth and Wi-Fi technologies. Ethical implementation is enforced by the computer which is
used for computing devices The computer ethics plays a major role which used It also
approaches the other devices. Ethical implication is important in WLAN. Wireless area network
is used in educational institutions, business and etc.it is mostly used in corporate environment.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Wireless security does not control the communication medium. High scoring company’s mostly
use wireless network.
The wireless connection range is 80 to the 200.without wireless router can manage the
network. The additional computers can also connect the without wire connection. But the outside
attack is not safe in this wireless connection. Wired connection is very costly but the wireless
connection is not very much cost (Lammle, 2011).
Switch:
The switch is a hardware.it is the element of networking.it is used to connecting computer
and other devices. Other devices are connected by using Ethernet cables. Routers and adapter do
not communicate with each other devices without switches. The switch is sent to information
straightly for other devices. Switch configuration is very simple. Very easy to send the incoming
message with the help of a local area network.it is forwards the network for other devices.
Switch contains a multiport. Network performance is increased. The workload is decreased. The
switch connects the workstations directly (Lammle and Tedder, 2011). Ethernet switch link
Ethernet devices together. Ethernet is the main form of a network switch. The computer network
is a network switch. Open system interconnect model creates a data link layer separate collision
domain for each switch port.
Switch Advantages and Disadvantages:
Advantages of switch:
It is an electronic tool.it manually operated.
The switch utilizes the data link layer.
It accessible in a different configuration.
It data speed as 10/100 Gaps.
It working in full duplex mode.
It avoids the accident, the data transmission is to be port to port.
6
use wireless network.
The wireless connection range is 80 to the 200.without wireless router can manage the
network. The additional computers can also connect the without wire connection. But the outside
attack is not safe in this wireless connection. Wired connection is very costly but the wireless
connection is not very much cost (Lammle, 2011).
Switch:
The switch is a hardware.it is the element of networking.it is used to connecting computer
and other devices. Other devices are connected by using Ethernet cables. Routers and adapter do
not communicate with each other devices without switches. The switch is sent to information
straightly for other devices. Switch configuration is very simple. Very easy to send the incoming
message with the help of a local area network.it is forwards the network for other devices.
Switch contains a multiport. Network performance is increased. The workload is decreased. The
switch connects the workstations directly (Lammle and Tedder, 2011). Ethernet switch link
Ethernet devices together. Ethernet is the main form of a network switch. The computer network
is a network switch. Open system interconnect model creates a data link layer separate collision
domain for each switch port.
Switch Advantages and Disadvantages:
Advantages of switch:
It is an electronic tool.it manually operated.
The switch utilizes the data link layer.
It accessible in a different configuration.
It data speed as 10/100 Gaps.
It working in full duplex mode.
It avoids the accident, the data transmission is to be port to port.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disadvantages:
The switch is very expensive.
Transmit traffic concerning.
If switches are in fast mode the security will attacks.
Correct design and arrangements are needed in order to grasp multicast packets
Limiting transmit, not well to routers.
Router:
The router is a network device.it is hardware. Multiple networks are connected by using a
router. Main work of the router is given the information .it transfer the information from the one
computer to another computer (Lorenz and Dini, 2005). The router is secure.it well performed.
The router contains a more capability.it is used for network design. The wireless router gives Wi-
Fi. Wi-Fi is used for smartphones, laptop and etc. The router is another type of router. A virtual
router is another type of router. Many types of the router are used.it is used for virtual router
redundancy protocol. Router activates only about a thousand meters.
Two or more connections of different networks are connected with the router. Router
choose the shortest path between a computers. The pc sends the information to the router is
going to the default gateway to send the router. The default gateway is can send the information
from the computer to router. RAM, NVRAM, flash memory is two or more networks interfaces.
The core connects the large organization networks. LAN will is supported to the router. A
wireless router is another advanced. The router is two types.one is wired and another one is a
wireless router. Router main purpose is routing the device.it is also two types.one is static and
another one is dynamic. Static is a fixed way to given but dynamic way is the shortest path will
reach.
A router is most important in the network. The large distance computer can communicate
easily. Router is one only work with the routing protocol. The wireless router is very expensive
7
The switch is very expensive.
Transmit traffic concerning.
If switches are in fast mode the security will attacks.
Correct design and arrangements are needed in order to grasp multicast packets
Limiting transmit, not well to routers.
Router:
The router is a network device.it is hardware. Multiple networks are connected by using a
router. Main work of the router is given the information .it transfer the information from the one
computer to another computer (Lorenz and Dini, 2005). The router is secure.it well performed.
The router contains a more capability.it is used for network design. The wireless router gives Wi-
Fi. Wi-Fi is used for smartphones, laptop and etc. The router is another type of router. A virtual
router is another type of router. Many types of the router are used.it is used for virtual router
redundancy protocol. Router activates only about a thousand meters.
Two or more connections of different networks are connected with the router. Router
choose the shortest path between a computers. The pc sends the information to the router is
going to the default gateway to send the router. The default gateway is can send the information
from the computer to router. RAM, NVRAM, flash memory is two or more networks interfaces.
The core connects the large organization networks. LAN will is supported to the router. A
wireless router is another advanced. The router is two types.one is wired and another one is a
wireless router. Router main purpose is routing the device.it is also two types.one is static and
another one is dynamic. Static is a fixed way to given but dynamic way is the shortest path will
reach.
A router is most important in the network. The large distance computer can communicate
easily. Router is one only work with the routing protocol. The wireless router is very expensive
7

to compare wired router. A wireless router is also the slowest router is compared wired router
wireless connection is not secure.
Wireless technology is also used in the future network. Wi-Fi connection is also called
wireless connection. Cable can connect the computers is called a wired connection.
Cisco packet tracer:
The network designs will create the Cisco packet tracer. Routers and switches will be
configured to use this packet tracer. The network device is added and removes the packet tracer
is allowed. This is based on the education tool is certified the network associate. The download
will be free for these tools. Most of the uses of Linux and Microsoft Windows in packet tracer. It
is also represented by cable in physical connection. It is supported by the layer protocols. Multi-
user system to supports this protocol. It is a small number of features will be used in these
applications.
This is not suitable for a modeling production network. The knowledge will be improved
the packet tracer is used. The assignments will be finished the students to use these applications.
The packet tracer will teach the user that application in it. Real-time knowledge will be getting.
The assignments will finish their student. The most visual is very clear. Network configuration is
used to network devices. Available for all the network devices.
This is mainly related to routing, switching, and networking. It is used to drag the visual.
Lab training also included the Cisco packet tracer. The modes of the operating system are two
types. Simulation is the first mode. Another one is the real-time mode (Stewart, 2009).
3. Solution Design
Typical network design is shown below. Two routers with one ASA firewall is used. Access
points will give wireless networking. Switch will give wired networking. IDS and IPS are used
for network security.
8
wireless connection is not secure.
Wireless technology is also used in the future network. Wi-Fi connection is also called
wireless connection. Cable can connect the computers is called a wired connection.
Cisco packet tracer:
The network designs will create the Cisco packet tracer. Routers and switches will be
configured to use this packet tracer. The network device is added and removes the packet tracer
is allowed. This is based on the education tool is certified the network associate. The download
will be free for these tools. Most of the uses of Linux and Microsoft Windows in packet tracer. It
is also represented by cable in physical connection. It is supported by the layer protocols. Multi-
user system to supports this protocol. It is a small number of features will be used in these
applications.
This is not suitable for a modeling production network. The knowledge will be improved
the packet tracer is used. The assignments will be finished the students to use these applications.
The packet tracer will teach the user that application in it. Real-time knowledge will be getting.
The assignments will finish their student. The most visual is very clear. Network configuration is
used to network devices. Available for all the network devices.
This is mainly related to routing, switching, and networking. It is used to drag the visual.
Lab training also included the Cisco packet tracer. The modes of the operating system are two
types. Simulation is the first mode. Another one is the real-time mode (Stewart, 2009).
3. Solution Design
Typical network design is shown below. Two routers with one ASA firewall is used. Access
points will give wireless networking. Switch will give wired networking. IDS and IPS are used
for network security.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
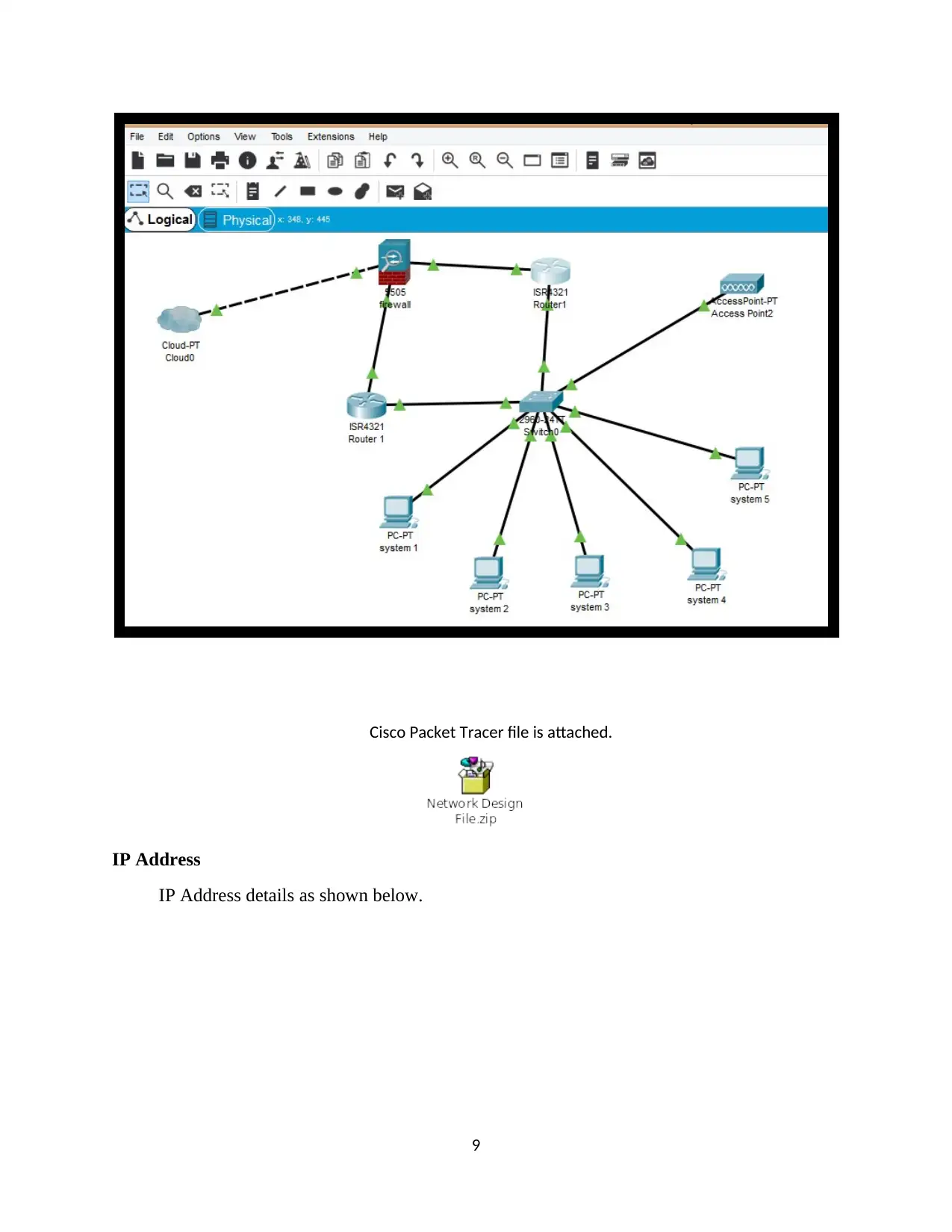
Cisco Packet Tracer file is attached.
IP Address
IP Address details as shown below.
9
IP Address
IP Address details as shown below.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
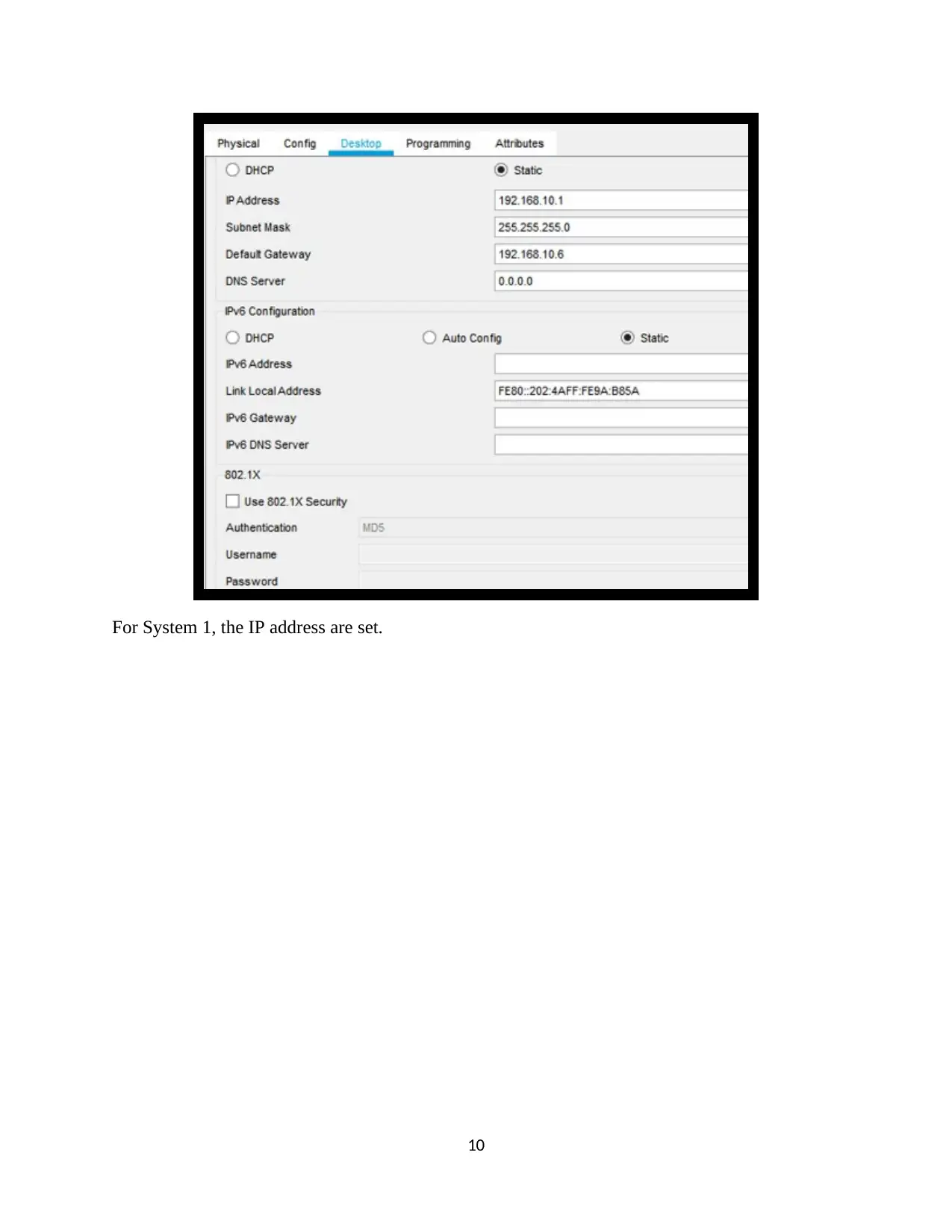
For System 1, the IP address are set.
10
10
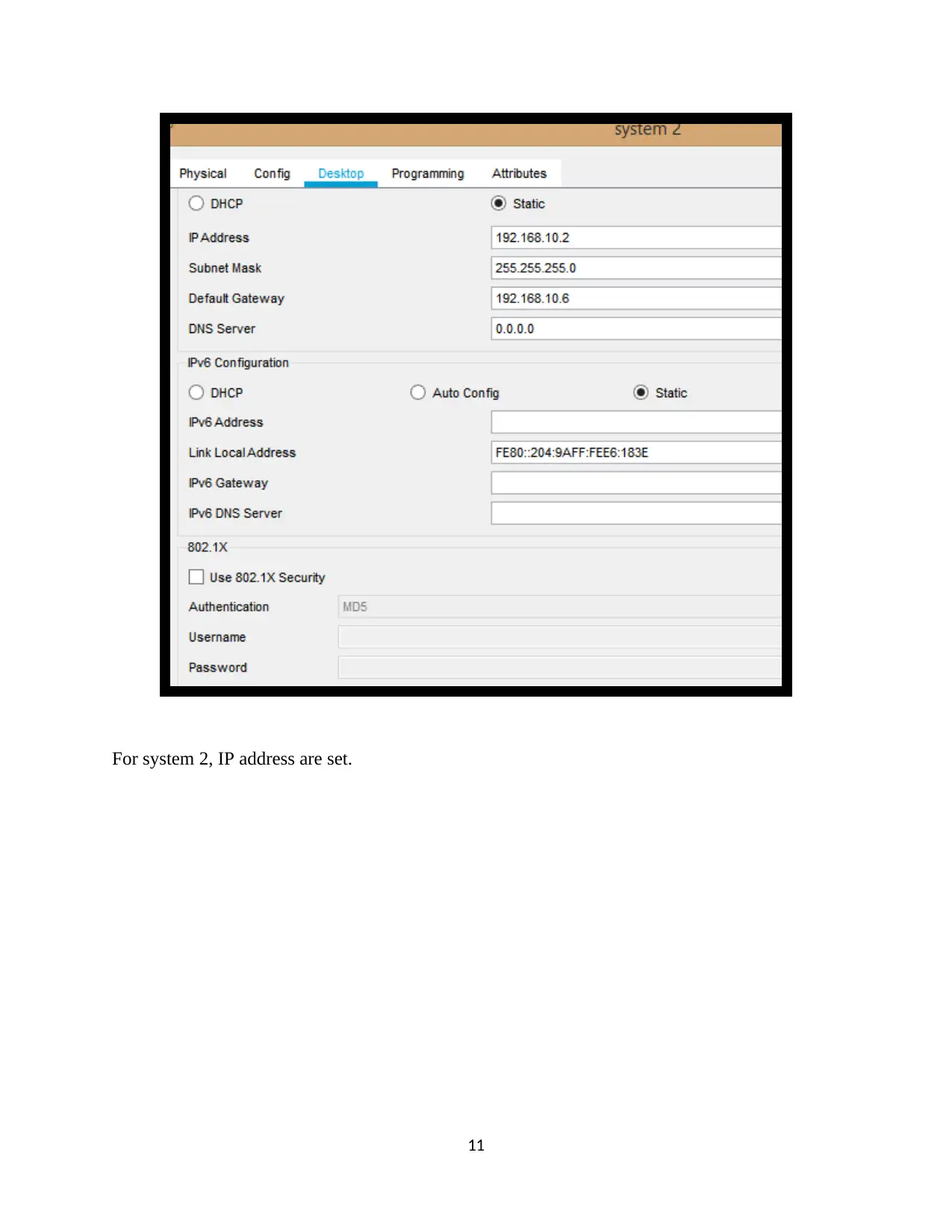
For system 2, IP address are set.
11
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




