Different Kinds of Scams and Fraudulent Acts on Computer Networks
VerifiedAdded on 2023/01/19
|12
|3315
|76
AI Summary
This article discusses the various types of scams and fraudulent acts that can occur on computer networks, such as phishing email scams, Nigerian scams, and credit card number scams. It also provides tips on how to protect your network from data theft over the internet.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: NETWORKING
NETWORKING
(Student’s Name)
(Professor’s Name)
(Course Title)
(Date of Submission)
NETWORKING
(Student’s Name)
(Professor’s Name)
(Course Title)
(Date of Submission)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

NETWORKING 2
QUESTION ONE
The different kinds of scams and fraudulent on computer network over the internet
They are various kinds of scams and fraudulent acts that one can fall when on the
internet. One of the scam is phishing email scam. These are types of malicious attachments
sent to someone when they are online. Phishing scams are based on the online
communication made through email or ion the social networks. In here cyber criminals sends
users messaged or emails by trying to trick them to provide sensitive and valuable data. These
emails seems to come from an official source such as banking institution or any other
financial authority which is said to be legitimate. Some of the common techniques used are
social engineering where scammers create a sense of urgency. Another common known scam
is the Nigerian scam. This scam involves the use of emotional emails, text messages or social
engineering messages. Another known online scam is the credit card number scam. This is a
type of scam where the scammers sign-up to freely monitor credit card numbers of
individuals. In addition, the scam is used to watch over people accounts closely.
Some types of frauds are identity theft fraud. This is a type of fraud which uses
computer intrusion techniques where cyber criminals steal PIN numbers of individuals.
Credit card fraud is another type of fraud where users are duped into submitting information
of their credit card on websites which are deceitful. Other types of frauds are auction fraud
where buyers are not able to get the services that they paid for or the item that they bought.
Other types of frauds are investment fraud where hackers pretend to have knowledge and
connections in finance bait people to invest on a venture or a company, work-at-home scam
which promises financial independence and huge money for little effort of work when at
home (Blanc & Cotton, 2014).
QUESTION ONE
The different kinds of scams and fraudulent on computer network over the internet
They are various kinds of scams and fraudulent acts that one can fall when on the
internet. One of the scam is phishing email scam. These are types of malicious attachments
sent to someone when they are online. Phishing scams are based on the online
communication made through email or ion the social networks. In here cyber criminals sends
users messaged or emails by trying to trick them to provide sensitive and valuable data. These
emails seems to come from an official source such as banking institution or any other
financial authority which is said to be legitimate. Some of the common techniques used are
social engineering where scammers create a sense of urgency. Another common known scam
is the Nigerian scam. This scam involves the use of emotional emails, text messages or social
engineering messages. Another known online scam is the credit card number scam. This is a
type of scam where the scammers sign-up to freely monitor credit card numbers of
individuals. In addition, the scam is used to watch over people accounts closely.
Some types of frauds are identity theft fraud. This is a type of fraud which uses
computer intrusion techniques where cyber criminals steal PIN numbers of individuals.
Credit card fraud is another type of fraud where users are duped into submitting information
of their credit card on websites which are deceitful. Other types of frauds are auction fraud
where buyers are not able to get the services that they paid for or the item that they bought.
Other types of frauds are investment fraud where hackers pretend to have knowledge and
connections in finance bait people to invest on a venture or a company, work-at-home scam
which promises financial independence and huge money for little effort of work when at
home (Blanc & Cotton, 2014).

NETWORKING 3
How to protect one network from data theft over the internet
To protect one smartphone and computer from data theft over the internet, one need to
have an up-to-date security software. The most effective software which is currently utilized
by most of the organizations is Kaspersky’s or Norton antivirus; first is to learn to spot scams
and spams. This can be achieved is never to click on click that appears to malicious. Third,
one need to use a very strong password; a combination of special characters, numbers and
letters. Third, one need to monitor their credit scores and review it regularly. Third one need
to use sites which are valid when making purchases and avoid those companies that one have
never heard of their reputation. Always stays alert for false information on credit reports
which includes addresses and social credit card numbers. In addition, one need to be wary of
the public WiFi. Also one need to stay alert on getting new credit cards and having their
credit approved or denied or being subjected to high-interest rate for no apparent reason
(Imperva, 2018).
Privacy and security settings for any well-known browser
Optimizing one browser’s setting is a very important step if one wants to use internet
privately and securely. The current internet browsers have inbuilt security features but most
are the times computer users fail to optimize their browser security settings during the
installation of the browser. Some of the tips for secure browsing using google chrome can be
accessed via advanced settings or through navigating through chrome then to settings. To
implement security on Google chrome one needs to enable malware and phishing protection
which is done under privacy section. The other settings is turning off instant search feature
which ought to be done for optimal security. The other security setting is not to sync i.e. one
ought not to synchronize their email account from their browser under the tab “person stuff”.
Lastly, one ought to configure content settings by configuring cookies, in here one needs to
keep local data until they quit on the browser. Second, one need not to allow any site to run
How to protect one network from data theft over the internet
To protect one smartphone and computer from data theft over the internet, one need to
have an up-to-date security software. The most effective software which is currently utilized
by most of the organizations is Kaspersky’s or Norton antivirus; first is to learn to spot scams
and spams. This can be achieved is never to click on click that appears to malicious. Third,
one need to use a very strong password; a combination of special characters, numbers and
letters. Third, one need to monitor their credit scores and review it regularly. Third one need
to use sites which are valid when making purchases and avoid those companies that one have
never heard of their reputation. Always stays alert for false information on credit reports
which includes addresses and social credit card numbers. In addition, one need to be wary of
the public WiFi. Also one need to stay alert on getting new credit cards and having their
credit approved or denied or being subjected to high-interest rate for no apparent reason
(Imperva, 2018).
Privacy and security settings for any well-known browser
Optimizing one browser’s setting is a very important step if one wants to use internet
privately and securely. The current internet browsers have inbuilt security features but most
are the times computer users fail to optimize their browser security settings during the
installation of the browser. Some of the tips for secure browsing using google chrome can be
accessed via advanced settings or through navigating through chrome then to settings. To
implement security on Google chrome one needs to enable malware and phishing protection
which is done under privacy section. The other settings is turning off instant search feature
which ought to be done for optimal security. The other security setting is not to sync i.e. one
ought not to synchronize their email account from their browser under the tab “person stuff”.
Lastly, one ought to configure content settings by configuring cookies, in here one needs to
keep local data until they quit on the browser. Second, one need not to allow any site to run

NETWORKING 4
JavaScript or show pop-ups or even track their physical location. Lastly, one needs to disable
all autofill and deselect (Kurose & Ross, 2017).
QUESTION TWO
How different types of spyware and malware can threaten one computer.
There are different types of malware example are viruses, adware, fake security
software, and spyware. Trojan types of computer viruses can threaten one computer as there
are usually bundled with other software and can be installed without the knowledge of the
users. Second once adware are in one computer they are very difficult to remove as they hide
in unexpected places examples in system files thus making their removal time consuming and
complicated. Third, fake security software threatens once privacy; fake security software is
known to threaten once privacy by gathering information on the computer and relying on it to
advertise other parties. Third malware usually threatens the privacy of the computer security.
To prevent one computer from these types of malwares one need to first know those
times when the computer have malwares. Some of the features are browser closing
unexpectedly or it stops responding. When one views when toolbars are added onto the
computer browser unexpectedly, and poor system performance. Second one needs to install
once computer with anti-virus programs such as Norton and Kaspersky’s program.
The main legislations regarding cyber-crimes in New Zealand
Cybercrime is one of the problems in the current 21st century. There are specific
legislative provisions in New Zealand designed to counter cybercrimes. These legislations are
specifically designed to address specific problems presented by cybercrimes.
To start with in New Zealand cybercrime is defines as the process of using computers
and internet to carry out an illegal action. One of the provisions is hacking and related
offences. This hacking is related to unauthorized access to the organization computer
JavaScript or show pop-ups or even track their physical location. Lastly, one needs to disable
all autofill and deselect (Kurose & Ross, 2017).
QUESTION TWO
How different types of spyware and malware can threaten one computer.
There are different types of malware example are viruses, adware, fake security
software, and spyware. Trojan types of computer viruses can threaten one computer as there
are usually bundled with other software and can be installed without the knowledge of the
users. Second once adware are in one computer they are very difficult to remove as they hide
in unexpected places examples in system files thus making their removal time consuming and
complicated. Third, fake security software threatens once privacy; fake security software is
known to threaten once privacy by gathering information on the computer and relying on it to
advertise other parties. Third malware usually threatens the privacy of the computer security.
To prevent one computer from these types of malwares one need to first know those
times when the computer have malwares. Some of the features are browser closing
unexpectedly or it stops responding. When one views when toolbars are added onto the
computer browser unexpectedly, and poor system performance. Second one needs to install
once computer with anti-virus programs such as Norton and Kaspersky’s program.
The main legislations regarding cyber-crimes in New Zealand
Cybercrime is one of the problems in the current 21st century. There are specific
legislative provisions in New Zealand designed to counter cybercrimes. These legislations are
specifically designed to address specific problems presented by cybercrimes.
To start with in New Zealand cybercrime is defines as the process of using computers
and internet to carry out an illegal action. One of the provisions is hacking and related
offences. This hacking is related to unauthorized access to the organization computer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING 5
systems. This is restricted by telecommunications Act 1987. Another bill which was passed
in June 2015 by the New Zealand parliament is harmful digital communication bill. This
legislations establishes complaint mechanism for victims like revenge on porn, harassment,
and cyberbullying. Another legislation which has been laid down is the crime act 1961. In
here one is liable for imprisonment for a term not exceeding seven years who indirectly or
directly accesses any computer system by deception or by dishonest. In addition under this
legislation, one is liable for imprisonment for a term which does not exceed five years who
access a computer or the internet to cause harm or loss to another person or to obtain
privilege or any property.
Legislation which can help prevent cyber-crimes in New Zealand
Some of the legislations in New Zealand which can assists in preventing cyber-crimes
are the ten communication principles in cyber-crimes where digital communication ought not
to disclose sentitive personal facts about another person. Second, any form that can denigrate
an individual by reasons of their race or color. Third, a digital communication ought not to be
obscene (Vasudevan, 2017).
QUESTION THREE
The different kinds of Denial of Services (DoS) and how DoS can interrupt one
networking systems.
Denial of service (DoS) is a network system attack with the main intention of denying
legitimate user(s) access to a system resource, operation or even a function. It has become a
very common threat to modern computer networks.
There are different kind of Denial of Services which includes; TCP SYN Flooding
which is an attack to the server and consume network protocols where client’s address are
forged resulting to half open connection. ICMP Smurf Flooding is another DoS which
depends on misconfigured network where attacker send numerous IP packets using a stolen
systems. This is restricted by telecommunications Act 1987. Another bill which was passed
in June 2015 by the New Zealand parliament is harmful digital communication bill. This
legislations establishes complaint mechanism for victims like revenge on porn, harassment,
and cyberbullying. Another legislation which has been laid down is the crime act 1961. In
here one is liable for imprisonment for a term not exceeding seven years who indirectly or
directly accesses any computer system by deception or by dishonest. In addition under this
legislation, one is liable for imprisonment for a term which does not exceed five years who
access a computer or the internet to cause harm or loss to another person or to obtain
privilege or any property.
Legislation which can help prevent cyber-crimes in New Zealand
Some of the legislations in New Zealand which can assists in preventing cyber-crimes
are the ten communication principles in cyber-crimes where digital communication ought not
to disclose sentitive personal facts about another person. Second, any form that can denigrate
an individual by reasons of their race or color. Third, a digital communication ought not to be
obscene (Vasudevan, 2017).
QUESTION THREE
The different kinds of Denial of Services (DoS) and how DoS can interrupt one
networking systems.
Denial of service (DoS) is a network system attack with the main intention of denying
legitimate user(s) access to a system resource, operation or even a function. It has become a
very common threat to modern computer networks.
There are different kind of Denial of Services which includes; TCP SYN Flooding
which is an attack to the server and consume network protocols where client’s address are
forged resulting to half open connection. ICMP Smurf Flooding is another DoS which
depends on misconfigured network where attacker send numerous IP packets using a stolen
NETWORKING 6
address across all computers in a network and then amplifies themInvalid source specified..
LAND Attack is an attack that send spoof TCP SYN packet to targeted computer which
causes it to constantly respond to itself and eventually cause it to crash. Lastly, User
Datagram Protocol (UDP) is a fraggle attack where attacker uses UDP echo traffic using a
fake address.
DoS can be use either network based attacks or host based attacks. On network based
attacks, DoS utilizes network protocols to gain access to a networking systems. On the other
hand, host based attacks exploits either algorithms, memory structure, implementation,
authentication protocols (Crosby & Wallach, 2003; Cowan et al. 2003)
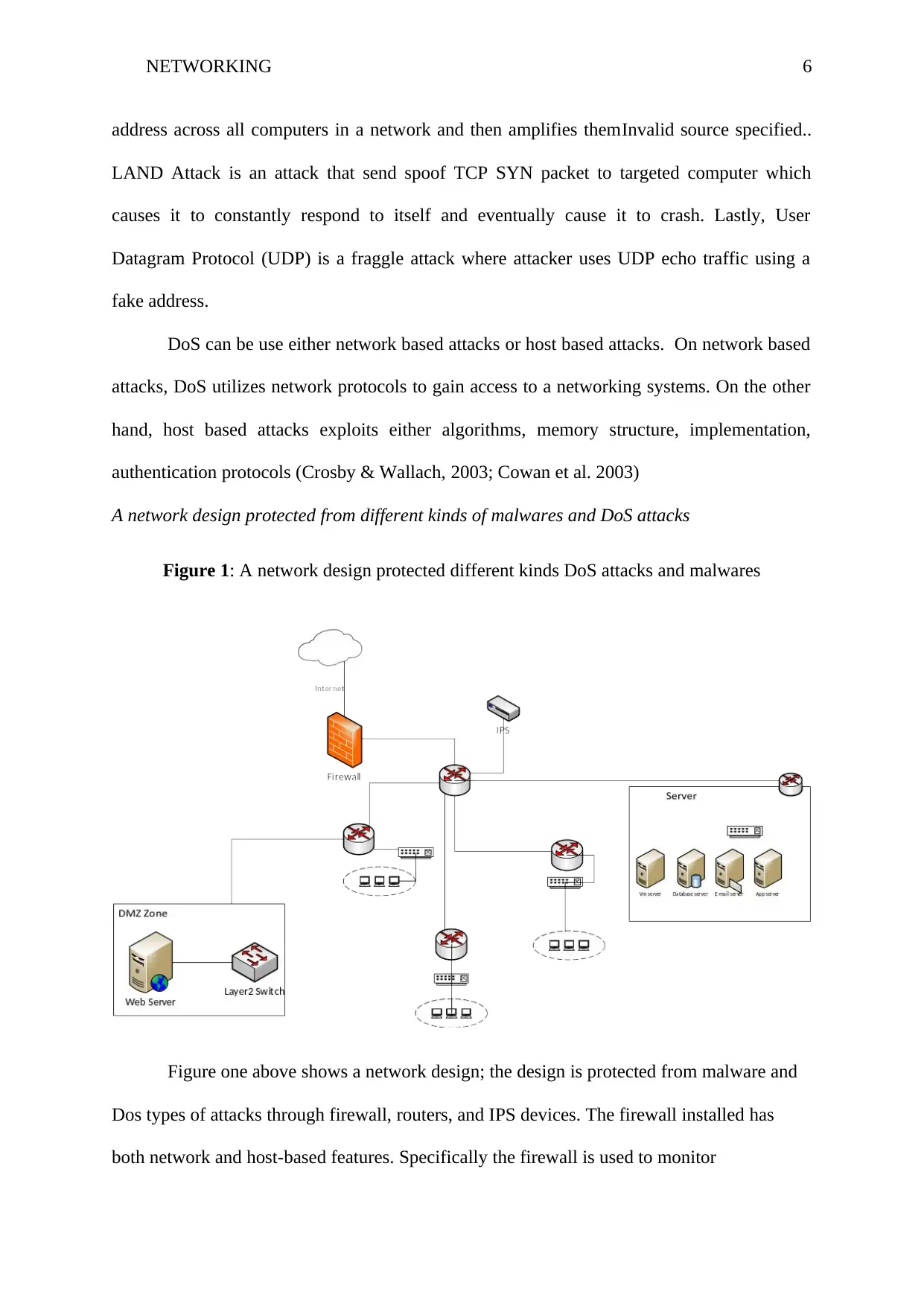
A network design protected from different kinds of malwares and DoS attacks
Figure 1: A network design protected different kinds DoS attacks and malwares
Figure one above shows a network design; the design is protected from malware and
Dos types of attacks through firewall, routers, and IPS devices. The firewall installed has
both network and host-based features. Specifically the firewall is used to monitor
address across all computers in a network and then amplifies themInvalid source specified..
LAND Attack is an attack that send spoof TCP SYN packet to targeted computer which
causes it to constantly respond to itself and eventually cause it to crash. Lastly, User
Datagram Protocol (UDP) is a fraggle attack where attacker uses UDP echo traffic using a
fake address.
DoS can be use either network based attacks or host based attacks. On network based
attacks, DoS utilizes network protocols to gain access to a networking systems. On the other
hand, host based attacks exploits either algorithms, memory structure, implementation,
authentication protocols (Crosby & Wallach, 2003; Cowan et al. 2003)
A network design protected from different kinds of malwares and DoS attacks
Figure 1: A network design protected different kinds DoS attacks and malwares
Figure one above shows a network design; the design is protected from malware and
Dos types of attacks through firewall, routers, and IPS devices. The firewall installed has
both network and host-based features. Specifically the firewall is used to monitor

NETWORKING 7
communication between outside sources and inside computers. The firewall can be used to
restrict certain sites and IP addresses and services which can Denial of Service. The host-
based feature is used to monitor local computers from email viruses, pop-ups windows and
cookies. IPS is used to detect any form of attack onto the organization network. The tool also
have the ability of performing logging on real-time analysis and IP networks. In case a virus
is detected the device raises an alarm to the system administrator. Router device is used to
monitor network protocols
QUESTION FOUR
Software tools to secure one network from malware and spyware
There are various software tools utilized by organizations to prevent the organization
from spyware and malwares. One of the software tools utilized is avast. This is an anti-virus
for windows. The anti-virus is said to score high on malware detection tests. Some of the
security features offered by the software are network security inspection, pass management,
software updater, file cleaning to free up hard drive space. Another common anti-virus is the
AVAG anti-virus. This is software anti-malware tool which offer data protection, email and
web protection. Malwarebytes is another anti-malware tool. The tool is specifically used to
scan registry and performing heuristic analysis so as to find any resilient spyware and
unknown rootkits and viruses. The tool also offers real-time protection, browser protection
and scheduled and automatic scanning. Another common security tool is the adware; this is a
security tool used to block an incoming spyware before it can infect the organization PC. The
security tool offers protection against registry attacks, suspicious processes and rootkits.
Another common type of anti-malware software is Emsisoft emergency kit; this is a type of
software which is able to detect and remove spyware, rootkits, key loggers, and malwares.
Spybot is another common type of software anti-malware the software is used to search and
destroy any type of malware existing in the computer system. The anti-malware software tool
communication between outside sources and inside computers. The firewall can be used to
restrict certain sites and IP addresses and services which can Denial of Service. The host-
based feature is used to monitor local computers from email viruses, pop-ups windows and
cookies. IPS is used to detect any form of attack onto the organization network. The tool also
have the ability of performing logging on real-time analysis and IP networks. In case a virus
is detected the device raises an alarm to the system administrator. Router device is used to
monitor network protocols
QUESTION FOUR
Software tools to secure one network from malware and spyware
There are various software tools utilized by organizations to prevent the organization
from spyware and malwares. One of the software tools utilized is avast. This is an anti-virus
for windows. The anti-virus is said to score high on malware detection tests. Some of the
security features offered by the software are network security inspection, pass management,
software updater, file cleaning to free up hard drive space. Another common anti-virus is the
AVAG anti-virus. This is software anti-malware tool which offer data protection, email and
web protection. Malwarebytes is another anti-malware tool. The tool is specifically used to
scan registry and performing heuristic analysis so as to find any resilient spyware and
unknown rootkits and viruses. The tool also offers real-time protection, browser protection
and scheduled and automatic scanning. Another common security tool is the adware; this is a
security tool used to block an incoming spyware before it can infect the organization PC. The
security tool offers protection against registry attacks, suspicious processes and rootkits.
Another common type of anti-malware software is Emsisoft emergency kit; this is a type of
software which is able to detect and remove spyware, rootkits, key loggers, and malwares.
Spybot is another common type of software anti-malware the software is used to search and
destroy any type of malware existing in the computer system. The anti-malware software tool
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

NETWORKING 8
also comes with startup tools, rootkit scanning and system immunization. To protect one
organization network one needs to use avast, Norton, or Kaspersky’s type of ant-malware
programs.
The different types of cryptography used to protect one network from the attackers
Cryptography is the art of secret writing; there are five functions of cryptography
currently being used these are key exchange, non-repudiation, integrity, authentication,
privacy and confidentiality. The three types of cryptography used to protect a network are has
functions, public key cryptography, and secret key cryptography. The hash function type of
cryptography uses mathematical transformation to encrypt information, and to provide digital
finger print. Specifically this type of cryptography is used to provide message integrity.
Public Key cryptography uses only one key for encryption and the other decryption. The
encryption key is used by the sender while decryption key is used by the person receiving the
message. Specifically this type of cryptography is used for authentication, key-exchange, and
non-repudiation. Public key type of encryption is used also used in digital signatures such as
RSA and digital signature algorithm. The last type of cryptography is the secret key
cryptography which is also known as symmetric encryption; this is as shown in figure 1
below. This type of encryption uses only one key for decryption and encryption; the sender
sends a message to encrypt a plain text and then sends the cipher text to the receiver of the
message. The receiver then applies the same key to decrypt the message or to recover the
plain text specifically this key used for confidentiality and privacy purposes. Some of the
common Secret key cryptography used today are data encryption standard and advanced
encryption standard (AES)
also comes with startup tools, rootkit scanning and system immunization. To protect one
organization network one needs to use avast, Norton, or Kaspersky’s type of ant-malware
programs.
The different types of cryptography used to protect one network from the attackers
Cryptography is the art of secret writing; there are five functions of cryptography
currently being used these are key exchange, non-repudiation, integrity, authentication,
privacy and confidentiality. The three types of cryptography used to protect a network are has
functions, public key cryptography, and secret key cryptography. The hash function type of
cryptography uses mathematical transformation to encrypt information, and to provide digital
finger print. Specifically this type of cryptography is used to provide message integrity.
Public Key cryptography uses only one key for encryption and the other decryption. The
encryption key is used by the sender while decryption key is used by the person receiving the
message. Specifically this type of cryptography is used for authentication, key-exchange, and
non-repudiation. Public key type of encryption is used also used in digital signatures such as
RSA and digital signature algorithm. The last type of cryptography is the secret key
cryptography which is also known as symmetric encryption; this is as shown in figure 1
below. This type of encryption uses only one key for decryption and encryption; the sender
sends a message to encrypt a plain text and then sends the cipher text to the receiver of the
message. The receiver then applies the same key to decrypt the message or to recover the
plain text specifically this key used for confidentiality and privacy purposes. Some of the
common Secret key cryptography used today are data encryption standard and advanced
encryption standard (AES)
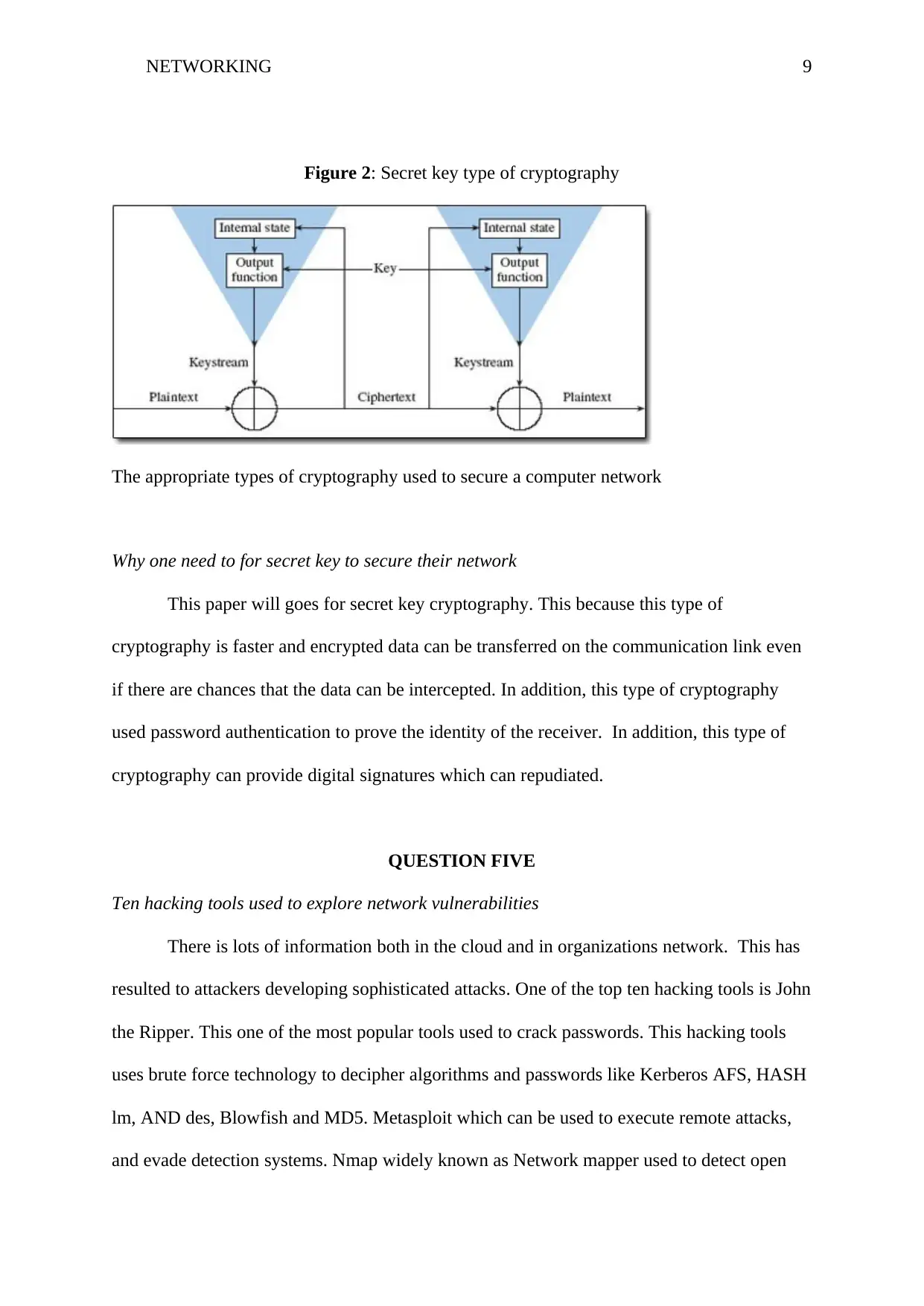
NETWORKING 9
Figure 2: Secret key type of cryptography
The appropriate types of cryptography used to secure a computer network
Why one need to for secret key to secure their network
This paper will goes for secret key cryptography. This because this type of
cryptography is faster and encrypted data can be transferred on the communication link even
if there are chances that the data can be intercepted. In addition, this type of cryptography
used password authentication to prove the identity of the receiver. In addition, this type of
cryptography can provide digital signatures which can repudiated.
QUESTION FIVE
Ten hacking tools used to explore network vulnerabilities
There is lots of information both in the cloud and in organizations network. This has
resulted to attackers developing sophisticated attacks. One of the top ten hacking tools is John
the Ripper. This one of the most popular tools used to crack passwords. This hacking tools
uses brute force technology to decipher algorithms and passwords like Kerberos AFS, HASH
lm, AND des, Blowfish and MD5. Metasploit which can be used to execute remote attacks,
and evade detection systems. Nmap widely known as Network mapper used to detect open
Figure 2: Secret key type of cryptography
The appropriate types of cryptography used to secure a computer network
Why one need to for secret key to secure their network
This paper will goes for secret key cryptography. This because this type of
cryptography is faster and encrypted data can be transferred on the communication link even
if there are chances that the data can be intercepted. In addition, this type of cryptography
used password authentication to prove the identity of the receiver. In addition, this type of
cryptography can provide digital signatures which can repudiated.
QUESTION FIVE
Ten hacking tools used to explore network vulnerabilities
There is lots of information both in the cloud and in organizations network. This has
resulted to attackers developing sophisticated attacks. One of the top ten hacking tools is John
the Ripper. This one of the most popular tools used to crack passwords. This hacking tools
uses brute force technology to decipher algorithms and passwords like Kerberos AFS, HASH
lm, AND des, Blowfish and MD5. Metasploit which can be used to execute remote attacks,
and evade detection systems. Nmap widely known as Network mapper used to detect open

NETWORKING 10
ports on remote hosts and launch massive DNS queries against sub-domains and domains.
Wireshark is used by hackers to monitor network packets.
IronWASP is another hacking tool used by hackers to hack web servers and exporting
results to RTF and HTML file format. SQLmap is another hacking tool used by hackers to
perform SQL injection tests top a database server. SQLNinja another common tool used by
attackers to exploit web apps. This tool performs different types of modes like verbose mode
and test mode. Wapiti is another hacking tool developed in python used by hackers to find
security flaws in a web application. Maltego is another hack tool use for data reconnaissance
and Intel gathering. The tool is also used to look, for online API services and investigate the
correlation between internet-based infrastructures.
Three tools used to protect one network from hackers
There are various tools implemented by organizations to protect one network from
attack. One of the tool used is virtual private network tool. This is a privacy tool used to
encrypt and protect one network connection. When an organization uses this tool, it is able to
hide real IP address so that hackers cannot monitor or see the organization’s browsing
activities. In addition, with this tool makes it impossible for hackers to penetrate into a
network protected with VPN. Other benefits of this tool include protecting financial
transactions and uses not able to access malicious sites. The second tool is firewall protection
tool. This is a security tool which creates a barrier around the organization Operating System.
The tool protect the organization from brute force attacks. It also triggers security alarm after
any attempt by hackers to penetrate into an organization network. It closes all the entry points
used by hackers immediately. Anti-spyware and antivirus is another security tool used by
organizations to prevent an organization from viruses. It also increases the device security. It
also helps in protecting the organization system from threats. Other security tool utilized by
organizations include file encryption tool; used to encrypt important organization files.
ports on remote hosts and launch massive DNS queries against sub-domains and domains.
Wireshark is used by hackers to monitor network packets.
IronWASP is another hacking tool used by hackers to hack web servers and exporting
results to RTF and HTML file format. SQLmap is another hacking tool used by hackers to
perform SQL injection tests top a database server. SQLNinja another common tool used by
attackers to exploit web apps. This tool performs different types of modes like verbose mode
and test mode. Wapiti is another hacking tool developed in python used by hackers to find
security flaws in a web application. Maltego is another hack tool use for data reconnaissance
and Intel gathering. The tool is also used to look, for online API services and investigate the
correlation between internet-based infrastructures.
Three tools used to protect one network from hackers
There are various tools implemented by organizations to protect one network from
attack. One of the tool used is virtual private network tool. This is a privacy tool used to
encrypt and protect one network connection. When an organization uses this tool, it is able to
hide real IP address so that hackers cannot monitor or see the organization’s browsing
activities. In addition, with this tool makes it impossible for hackers to penetrate into a
network protected with VPN. Other benefits of this tool include protecting financial
transactions and uses not able to access malicious sites. The second tool is firewall protection
tool. This is a security tool which creates a barrier around the organization Operating System.
The tool protect the organization from brute force attacks. It also triggers security alarm after
any attempt by hackers to penetrate into an organization network. It closes all the entry points
used by hackers immediately. Anti-spyware and antivirus is another security tool used by
organizations to prevent an organization from viruses. It also increases the device security. It
also helps in protecting the organization system from threats. Other security tool utilized by
organizations include file encryption tool; used to encrypt important organization files.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING 11
Vulnerabilities on the target system
SSYN flood is a type of DoS attack which exploits parts of TCP three way handshake.
By implementing OpenVAS software tool, some of the vulnerabilities found are OS
command injection, buffer overflow, missing authorization, use of broken algorithm, cross-
site scripting and forgery, and SL injection
Mitigation of the vulnerabilities
First one needs to implement micro-block technique. This a technique where the IT
administrators allocates a micro-record into the organizational server for each of the SYN
request. The second method is the use of SYN cookies where the server sends SYN-ACK
response. The third method is the use of RST cookies; this is a technique where the server is
able to tell that something is wrong after the client generates the RST packet. The forth
method is the use of stack tweaking. In here the administrator is required to tweak TCP stacks
so as to mitigate the effect of SYN floods which involves the reduction of timeout until a
stack frees the memory or it selectively drops any incoming connections. The last method is
installing IPS/IDS system so as to detect DoS attacks (Imperva, 2018). Other mitigation
strategies are blocking users from visiting some websites, filtering internet activity by day
and applying what computer scientist refer to as bandwidth checks and completing a report
on tools one need to have to let one demo0nsttrate effectiveness of web security and
analyzing on browsing activity (Odom, 2009).
Vulnerabilities on the target system
SSYN flood is a type of DoS attack which exploits parts of TCP three way handshake.
By implementing OpenVAS software tool, some of the vulnerabilities found are OS
command injection, buffer overflow, missing authorization, use of broken algorithm, cross-
site scripting and forgery, and SL injection
Mitigation of the vulnerabilities
First one needs to implement micro-block technique. This a technique where the IT
administrators allocates a micro-record into the organizational server for each of the SYN
request. The second method is the use of SYN cookies where the server sends SYN-ACK
response. The third method is the use of RST cookies; this is a technique where the server is
able to tell that something is wrong after the client generates the RST packet. The forth
method is the use of stack tweaking. In here the administrator is required to tweak TCP stacks
so as to mitigate the effect of SYN floods which involves the reduction of timeout until a
stack frees the memory or it selectively drops any incoming connections. The last method is
installing IPS/IDS system so as to detect DoS attacks (Imperva, 2018). Other mitigation
strategies are blocking users from visiting some websites, filtering internet activity by day
and applying what computer scientist refer to as bandwidth checks and completing a report
on tools one need to have to let one demo0nsttrate effectiveness of web security and
analyzing on browsing activity (Odom, 2009).

NETWORKING 12
References
Blanc, R. P., & Cotton, I. W. (2014). Computer networking by Robert P Blanc (2nd ed.).
Amsterdam: RTU Publishing House.
Imperva. (2018). What is a SYN flood attack. Retrieved April 18, 2019, from
https://www.imperva.com/learn/application-security/syn-flood/?
utm_campaign=Incapsula-moved
Kurose, J. F., & Ross, K. W. (2017). Computer networking : a top-down approach. Computer
networking .
Matthews, J. (2007). Computer networking : Internet protocols in action (1st edition ed.).
New York: Springer.
Odom, W. (2009). Computer networking first-step by Wendell Odom (3rd ed.). New York:
John & Wiley Press.
Vasudevan, S. K. (2017). Computer networking. by Shriram K Vasudevan (1st ed.). New
York: Oxford Press.
References
Blanc, R. P., & Cotton, I. W. (2014). Computer networking by Robert P Blanc (2nd ed.).
Amsterdam: RTU Publishing House.
Imperva. (2018). What is a SYN flood attack. Retrieved April 18, 2019, from
https://www.imperva.com/learn/application-security/syn-flood/?
utm_campaign=Incapsula-moved
Kurose, J. F., & Ross, K. W. (2017). Computer networking : a top-down approach. Computer
networking .
Matthews, J. (2007). Computer networking : Internet protocols in action (1st edition ed.).
New York: Springer.
Odom, W. (2009). Computer networking first-step by Wendell Odom (3rd ed.). New York:
John & Wiley Press.
Vasudevan, S. K. (2017). Computer networking. by Shriram K Vasudevan (1st ed.). New
York: Oxford Press.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




