Networking Overview
VerifiedAdded on 2022/12/30
|10
|1771
|28
AI Summary
This report analyzes the network requirements of businesses operating with multiple sub networks using LAN bus topology. It covers scope, requirements, network design, IP address allocation, and configuration details.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: NETWORKING OVERVIEW
Networking Overview
Name of the Student
Name of the University
Author Note
Networking Overview
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1NETWORKING OVERVIEW
Summary
The objective of the following report is about analysing network requirements of businesses which
operate with multiple sub networks for their various departments while using LAN bus topology to
connect the switches for the respective departments. This report first provides short scope of given
project after which the requirements of the network get summarised. Afterwards the design of the
network is described thoroughly with the help of a diagram while also mentioning cables and
topologies in use. Then, this report goes on to list the IP address allocation and subnet details
associated with the five different departments along with a short explanation. The report also
presents details regarding configuration of routers, switches, servers and the current security
measures in place in the network. Thereafter, the report then ends by providing observations in
conclusions section.
Summary
The objective of the following report is about analysing network requirements of businesses which
operate with multiple sub networks for their various departments while using LAN bus topology to
connect the switches for the respective departments. This report first provides short scope of given
project after which the requirements of the network get summarised. Afterwards the design of the
network is described thoroughly with the help of a diagram while also mentioning cables and
topologies in use. Then, this report goes on to list the IP address allocation and subnet details
associated with the five different departments along with a short explanation. The report also
presents details regarding configuration of routers, switches, servers and the current security
measures in place in the network. Thereafter, the report then ends by providing observations in
conclusions section.

2NETWORKING OVERVIEW
Table of Contents
Introduction...........................................................................................................................................3
Scope of Project.....................................................................................................................................3
Requirements Summary........................................................................................................................3
Network Design.....................................................................................................................................4
Physical Topology Diagram of the Network.........................................................................4
Switch Configuration.............................................................................................................4
Configuring the Router......................................................................................................5
Configuring Server and Access Point................................................................................5
Configuring Security..........................................................................................................5
IP Address Allocation.............................................................................................................................5
Conclusion.............................................................................................................................................6
References.............................................................................................................................................8
Table of Contents
Introduction...........................................................................................................................................3
Scope of Project.....................................................................................................................................3
Requirements Summary........................................................................................................................3
Network Design.....................................................................................................................................4
Physical Topology Diagram of the Network.........................................................................4
Switch Configuration.............................................................................................................4
Configuring the Router......................................................................................................5
Configuring Server and Access Point................................................................................5
Configuring Security..........................................................................................................5
IP Address Allocation.............................................................................................................................5
Conclusion.............................................................................................................................................6
References.............................................................................................................................................8

3NETWORKING OVERVIEW
Introduction
The following report deals with analysing network requirements of businesses which
operate with multiple sub networks for their various departments while using LAN bus topology to
connect the switches for the respective departments. This report begins by providing short scope of
given project after which the requirements of the network get summarised. Afterwards the design of
the network is described thoroughly with the help of a diagram while also mentioning cables and
topologies in use. Then, this report goes on to list the IP address allocation and subnet details
associated with the five different departments along with a short explanation. The report also
presents details regarding configuration of routers, switches, servers and the current security
measures in place in the network. The report then ends by providing observations in conclusions
section.
Scope of Project
An insurance and financial firm is identified that consists of five different departments.
These departments are to have their own network. Each of these departments access the fourth
switch that is hosting the database server and printer apart from the workstations for general
employees and the management. The finance department is to be barred from direct internet
access. Network communications for this department should only occur with the systems of the
Manager.
Requirements Summary
Every department operates with three workstation computers [4]. Among these
departments the fourth department or Management and Employees houses the printer and the
database servers. Both these devices are to be shared with rest of the departments.
It is assumed that every user of the firm will be requiring a laptop. Therefore, laptops
required for each department is 3 or total laptop count for the five departments are 15. The laptops
of the company’s network are connected through the wireless router installed. The company in
question based on the network requirements falls in the category of small medium enterprise (SME)
businesses.
Introduction
The following report deals with analysing network requirements of businesses which
operate with multiple sub networks for their various departments while using LAN bus topology to
connect the switches for the respective departments. This report begins by providing short scope of
given project after which the requirements of the network get summarised. Afterwards the design of
the network is described thoroughly with the help of a diagram while also mentioning cables and
topologies in use. Then, this report goes on to list the IP address allocation and subnet details
associated with the five different departments along with a short explanation. The report also
presents details regarding configuration of routers, switches, servers and the current security
measures in place in the network. The report then ends by providing observations in conclusions
section.
Scope of Project
An insurance and financial firm is identified that consists of five different departments.
These departments are to have their own network. Each of these departments access the fourth
switch that is hosting the database server and printer apart from the workstations for general
employees and the management. The finance department is to be barred from direct internet
access. Network communications for this department should only occur with the systems of the
Manager.
Requirements Summary
Every department operates with three workstation computers [4]. Among these
departments the fourth department or Management and Employees houses the printer and the
database servers. Both these devices are to be shared with rest of the departments.
It is assumed that every user of the firm will be requiring a laptop. Therefore, laptops
required for each department is 3 or total laptop count for the five departments are 15. The laptops
of the company’s network are connected through the wireless router installed. The company in
question based on the network requirements falls in the category of small medium enterprise (SME)
businesses.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
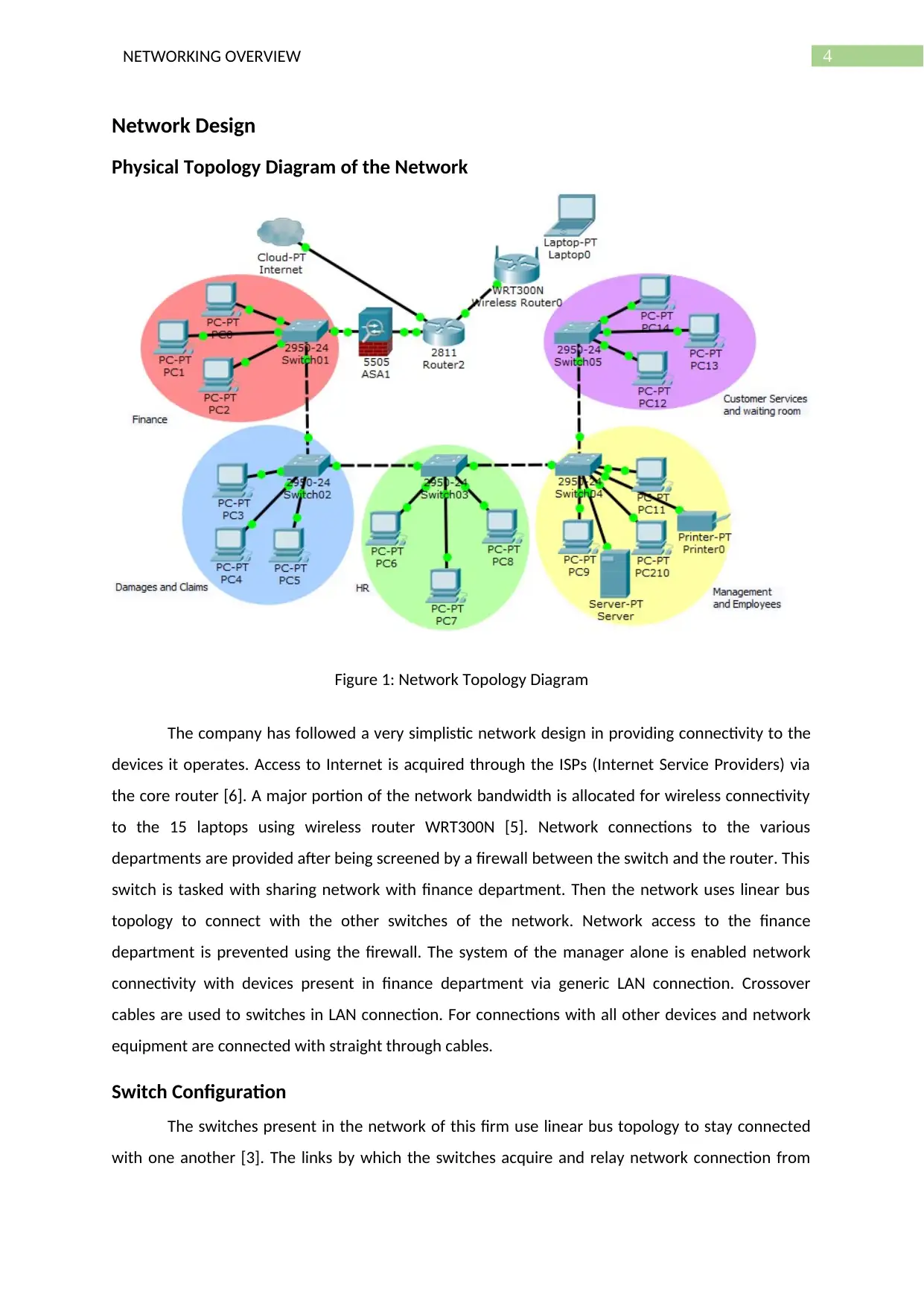
4NETWORKING OVERVIEW
Network Design
Physical Topology Diagram of the Network
Figure 1: Network Topology Diagram
The company has followed a very simplistic network design in providing connectivity to the
devices it operates. Access to Internet is acquired through the ISPs (Internet Service Providers) via
the core router [6]. A major portion of the network bandwidth is allocated for wireless connectivity
to the 15 laptops using wireless router WRT300N [5]. Network connections to the various
departments are provided after being screened by a firewall between the switch and the router. This
switch is tasked with sharing network with finance department. Then the network uses linear bus
topology to connect with the other switches of the network. Network access to the finance
department is prevented using the firewall. The system of the manager alone is enabled network
connectivity with devices present in finance department via generic LAN connection. Crossover
cables are used to switches in LAN connection. For connections with all other devices and network
equipment are connected with straight through cables.
Switch Configuration
The switches present in the network of this firm use linear bus topology to stay connected
with one another [3]. The links by which the switches acquire and relay network connection from
Network Design
Physical Topology Diagram of the Network
Figure 1: Network Topology Diagram
The company has followed a very simplistic network design in providing connectivity to the
devices it operates. Access to Internet is acquired through the ISPs (Internet Service Providers) via
the core router [6]. A major portion of the network bandwidth is allocated for wireless connectivity
to the 15 laptops using wireless router WRT300N [5]. Network connections to the various
departments are provided after being screened by a firewall between the switch and the router. This
switch is tasked with sharing network with finance department. Then the network uses linear bus
topology to connect with the other switches of the network. Network access to the finance
department is prevented using the firewall. The system of the manager alone is enabled network
connectivity with devices present in finance department via generic LAN connection. Crossover
cables are used to switches in LAN connection. For connections with all other devices and network
equipment are connected with straight through cables.
Switch Configuration
The switches present in the network of this firm use linear bus topology to stay connected
with one another [3]. The links by which the switches acquire and relay network connection from
5NETWORKING OVERVIEW
firewall to switches are configured in trunk mode as both inbound as also outbound connections
must be supported by these switches. Through the other interfaces configured in access mode
connections are directly provided to individual devices.
Configuring the Router
The core router makes use of finance department’s network for connecting the switches of
other departments to the network. For this, the interface of the router is assigned the IP address
192.168.10.33 to connect with the firewall. IP used in the interface for connecting to wireless router
is 192.168.10.73 from the router.
Configuring Server and Access Point
The wireless router connected to the core router serves as wireless access point for laptops.
The sub network being used in providing wireless network connections is 192.168.10.0 [2]. The
database server and the Ethernet printer are installed in the management and employees
department and is made accessible to other departments over LAN. IP addresses assigned to server
and printer are 192.168.10.34 and 192.168.10.38 respectively.
Configuring Security
Security has been ensured by introducing Virtual Local Area Networks (VLANs) in the firewall
(Cisco ASA 5505). These are VLANs 2 and 1 for outbound and inbound connections [1]. The firewall
interface for acquiring network accesses VLAN 2 and the interface by which connection is provided
to departments is VLAN1.
IP Address Allocation
Department
network
IP
Requirem
ents
IPs
Alloca
ted
Network
Addresse
s
CID
R
Valu
es
Subnet_Ma
sk
Assignabl
e IP
Ranges
Broadcas
t
Addresse
s
Finance Dpt 3 6 192.168.1
0.56 /29 255.255.25
5.248
192.168.1
0.57 -
192.168.1
0.62
192.168.1
0.63
Damages/Claims
Dpt 3 6 192.168.1
0.48 /29 255.255.25
5.248
192.168.1
0.49 -
192.168.1
0.54
192.168.1
0.55
firewall to switches are configured in trunk mode as both inbound as also outbound connections
must be supported by these switches. Through the other interfaces configured in access mode
connections are directly provided to individual devices.
Configuring the Router
The core router makes use of finance department’s network for connecting the switches of
other departments to the network. For this, the interface of the router is assigned the IP address
192.168.10.33 to connect with the firewall. IP used in the interface for connecting to wireless router
is 192.168.10.73 from the router.
Configuring Server and Access Point
The wireless router connected to the core router serves as wireless access point for laptops.
The sub network being used in providing wireless network connections is 192.168.10.0 [2]. The
database server and the Ethernet printer are installed in the management and employees
department and is made accessible to other departments over LAN. IP addresses assigned to server
and printer are 192.168.10.34 and 192.168.10.38 respectively.
Configuring Security
Security has been ensured by introducing Virtual Local Area Networks (VLANs) in the firewall
(Cisco ASA 5505). These are VLANs 2 and 1 for outbound and inbound connections [1]. The firewall
interface for acquiring network accesses VLAN 2 and the interface by which connection is provided
to departments is VLAN1.
IP Address Allocation
Department
network
IP
Requirem
ents
IPs
Alloca
ted
Network
Addresse
s
CID
R
Valu
es
Subnet_Ma
sk
Assignabl
e IP
Ranges
Broadcas
t
Addresse
s
Finance Dpt 3 6 192.168.1
0.56 /29 255.255.25
5.248
192.168.1
0.57 -
192.168.1
0.62
192.168.1
0.63
Damages/Claims
Dpt 3 6 192.168.1
0.48 /29 255.255.25
5.248
192.168.1
0.49 -
192.168.1
0.54
192.168.1
0.55
6NETWORKING OVERVIEW
Human Resource
Dpt 3 6 192.168.1
0.64 /29 255.255.25
5.248
192.168.1
0.65 -
192.168.1
0.70
192.168.1
0.71
Management/
Employees Dpt 5 6 192.168.1
0.32 /29 255.255.25
5.248
192.168.1
0.33 -
192.168.1
0.38
192.168.1
0.39
Customer Service
Dpt 3 6 192.168.1
0.40 /29 255.255.25
5.248
192.168.1
0.41 -
192.168.1
0.46
192.168.1
0.47
Laptops 15 30 192.168.1
0.0 /27 255.255.25
5.224
192.168.1
0.1 -
192.168.1
0.30
192.168.1
0.31
Routing 2 2 192.168.1
0.72 /30 255.255.25
5.252
192.168.1
0.73 -
192.168.1
0.74
192.168.1
0.75
This IP addressing scheme is called CIDR (Classless Inter-domain Routing) IP addressing. CIDR
is the preferred method of allocating IP addresses [7]. The major network used here is
192.168.10.0/24 in which 30% of total address space gets utilized which suggests healthy traffic as
along with desired network performance. The network 192.168.10.72 is required to connect the
wireless router with the core router.
Conclusion
To conclude, the above report successfully analyses network requirements of businesses
which operate with multiple sub networks for their various departments while using LAN bus
topology to connect the switches for the respective departments. This report begins by providing
short scope of given project after which the requirements of the network get summarised.
Afterwards the design of the network is described thoroughly with the help of a diagram while also
mentioning cables and topologies in use. Then, this report goes on to list the IP address allocation
Human Resource
Dpt 3 6 192.168.1
0.64 /29 255.255.25
5.248
192.168.1
0.65 -
192.168.1
0.70
192.168.1
0.71
Management/
Employees Dpt 5 6 192.168.1
0.32 /29 255.255.25
5.248
192.168.1
0.33 -
192.168.1
0.38
192.168.1
0.39
Customer Service
Dpt 3 6 192.168.1
0.40 /29 255.255.25
5.248
192.168.1
0.41 -
192.168.1
0.46
192.168.1
0.47
Laptops 15 30 192.168.1
0.0 /27 255.255.25
5.224
192.168.1
0.1 -
192.168.1
0.30
192.168.1
0.31
Routing 2 2 192.168.1
0.72 /30 255.255.25
5.252
192.168.1
0.73 -
192.168.1
0.74
192.168.1
0.75
This IP addressing scheme is called CIDR (Classless Inter-domain Routing) IP addressing. CIDR
is the preferred method of allocating IP addresses [7]. The major network used here is
192.168.10.0/24 in which 30% of total address space gets utilized which suggests healthy traffic as
along with desired network performance. The network 192.168.10.72 is required to connect the
wireless router with the core router.
Conclusion
To conclude, the above report successfully analyses network requirements of businesses
which operate with multiple sub networks for their various departments while using LAN bus
topology to connect the switches for the respective departments. This report begins by providing
short scope of given project after which the requirements of the network get summarised.
Afterwards the design of the network is described thoroughly with the help of a diagram while also
mentioning cables and topologies in use. Then, this report goes on to list the IP address allocation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORKING OVERVIEW
and subnet details associated with the five different departments along with a short explanation.
Additionally, the report presents details regarding configuration of routers, switches, servers and the
current security measures in place in the network.
and subnet details associated with the five different departments along with a short explanation.
Additionally, the report presents details regarding configuration of routers, switches, servers and the
current security measures in place in the network.

8NETWORKING OVERVIEW
References
[1] Akram, J., Akram, N., Mamoon, S., Ali, S. and Naseer, N., 2017. Future and Techniques of
Implementing Security in VLAN. Journal of Network Communications and Emerging Technologies
(JNCET), 7(5).
[2] Andrews, J.G., Zhang, X., Durgin, G.D. and Gupta, A.K., 2016. Are we approaching the
fundamental limits of wireless network densification?. IEEE Communications Magazine, 54(10),
pp.184-190.
[3] D. Agiakatsikas, N.T. Nguyen, Z. Zhao, T. Wu, E. Cetin, O. Diessel and L. Gong, Reconfiguration
control networks for TMR systems with module-based recovery. In 2016 IEEE 24th Annual
International Symposium on Field-Programmable Custom Computing Machines (FCCM) (pp. 88-91).
IEEE. , 2016, May.
[4] Le, P. and Marras, W.S., 2016. Evaluating the low back biomechanics of three different office
workstations: Seated, standing, and perching. Applied ergonomics, 56, pp.170-178.
[5] Sari, R.D., Supiyandi, A.P.U., Siahaan, M.M. and Ginting, R.B., 2017. A Review of IP and MAC
Address Filtering in Wireless Network Security. Int. J. Sci. Res. Sci. Technol, 3(6), pp.470-473.
[6] T.N. Quach, P. Thaichon, and C. Jebarajakirthy, Internet service providers' service quality and its
effect on customer loyalty of different usage patterns. Journal of Retailing and Consumer Services,
29, pp.104-113., 2016.
[7] W. Huitao, Y. Ruopeng and Z. Xiaofei, April. Research on IP Address Allocation of Tactical
Communication Network. In Journal of Physics: Conference Series (Vol. 1187, No. 4, p. 042105). IOP
Publishing., 2019,
[8] Y. Lee, H. Park, and Y. Lee, Ip geolocation with a crowd-sourcing broadband performance tool.
ACM SIGCOMM Computer Communication Review, 46(1), pp.12-20., 2016.
References
[1] Akram, J., Akram, N., Mamoon, S., Ali, S. and Naseer, N., 2017. Future and Techniques of
Implementing Security in VLAN. Journal of Network Communications and Emerging Technologies
(JNCET), 7(5).
[2] Andrews, J.G., Zhang, X., Durgin, G.D. and Gupta, A.K., 2016. Are we approaching the
fundamental limits of wireless network densification?. IEEE Communications Magazine, 54(10),
pp.184-190.
[3] D. Agiakatsikas, N.T. Nguyen, Z. Zhao, T. Wu, E. Cetin, O. Diessel and L. Gong, Reconfiguration
control networks for TMR systems with module-based recovery. In 2016 IEEE 24th Annual
International Symposium on Field-Programmable Custom Computing Machines (FCCM) (pp. 88-91).
IEEE. , 2016, May.
[4] Le, P. and Marras, W.S., 2016. Evaluating the low back biomechanics of three different office
workstations: Seated, standing, and perching. Applied ergonomics, 56, pp.170-178.
[5] Sari, R.D., Supiyandi, A.P.U., Siahaan, M.M. and Ginting, R.B., 2017. A Review of IP and MAC
Address Filtering in Wireless Network Security. Int. J. Sci. Res. Sci. Technol, 3(6), pp.470-473.
[6] T.N. Quach, P. Thaichon, and C. Jebarajakirthy, Internet service providers' service quality and its
effect on customer loyalty of different usage patterns. Journal of Retailing and Consumer Services,
29, pp.104-113., 2016.
[7] W. Huitao, Y. Ruopeng and Z. Xiaofei, April. Research on IP Address Allocation of Tactical
Communication Network. In Journal of Physics: Conference Series (Vol. 1187, No. 4, p. 042105). IOP
Publishing., 2019,
[8] Y. Lee, H. Park, and Y. Lee, Ip geolocation with a crowd-sourcing broadband performance tool.
ACM SIGCOMM Computer Communication Review, 46(1), pp.12-20., 2016.

9NETWORKING OVERVIEW
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





