Next-Generation Cybertap for Corporate Intrusion Detection Servers
VerifiedAdded on 2019/10/12
|10
|4380
|172
Project
AI Summary
This project delves into the realm of Next-Generation Cybertap for corporate intrusion detection and prevention servers, focusing on how these systems safeguard enterprise businesses from cyber threats. The project begins by defining Intrusion Detection & Prevention Systems (IDPS) and their role in monitoring network activities, protecting data, and mitigating both existing and emerging cyberattacks. It aims to explain mitigation methodologies used for storing information in network systems to prevent attackers from penetrating the system. The project also discusses the importance of identifying attack types and methods to implement effective protective technologies. The objectives include assessing organizational security measures against cyberattacks, evaluating the effectiveness of current security standards, and exploring the capabilities of Cybertap products in analyzing network traffic, providing network visibility, and offering data security strategies. The project further reviews various intrusion detection and prevention providers like McAfee, Trend Micro, Darktrace, NSFocus, H3C, Huawei, and Cisco, detailing their respective technologies and features. The project emphasizes the significance of IDPS in identifying threats, logging information, and generating reports to protect enterprise networks.

Next-Generation Cybertap For Corporate Intrusion Detection Servers and
Intrusion Prevention Servers in Enterprise Business
Abstract
Next Generation Intrusion Prevention Systems is also term as Intrusion Detection & Prevention
Systems (IDPS). Here we can see that Next Generation Cybertap for coporate intrusion detections
server and intrusion prevention servers in Enterprise business are consist of so many different
network security applications which monitor the network and the system suspicious activities.
These system going to protect the business from already existing and upcoming attacks as well as
provide regular control over the system , prevention from cyberthreat. Expertise of Next generation
intrusion prevention system helps in protecting the important data and information as well as
applications from more advanced cyber attack without harming the enterprise production and its
system performance. Our project is mainly aim to explain the different mitigation methodologies or
techniques used by corporate for storing information and data which is going to used in network
system. We are going to discuss more about these things further in our paper. In this type of
mitigation plan the attackers are not able to penetrate in the system and our system then fully
secure. After implementing these system in corporate we will be able to find the attacks types and
methods used by the attackers so that we can easily install those technolgy in our system to protect
information and data against different types of cyber threats.
Aims and Objectives
The main aim of this project is to find out that whether the organizations have enough security
measures to protect or prevent the information and data from cyber attacks on the world wide web.
The main objectives behind for selecting this project is to find out whether the available security
standards and security practices are capable to protect the organizational data and information from
outside security threats and attacks. Cuybertap products nowadays installed in the private and public
sectors all over the world. Cybertrap products mainly applies to analyze the big data to monitor the
traffic of the network and provide visibility on both the end of the network of the organizations . It
also provide a plan for the organization to how they can secure their data and information. Also the
cybertap system is going to provide the information about IP and other suspicious activities of user
as well as system administrator. The cybertap technology is going to support the differenet type of
technology now currently available in the market and from other different type of security threat
situations. Nowadays so many different type of organizations which have daily multiple type of
traffic generations at the applications level and from other different type of security threats uses
cybertap to protect their network. Nowadays there are so many different type of security threats so
that most of the largest global organization uses cybertap methods to manage and secure the
information and identities as well as their technology infrastructure. Cybertap is the leading
solutions which can provide security to lost of data and information over the system network of the
organizations.
Intrusion Prevention Servers in Enterprise Business
Abstract
Next Generation Intrusion Prevention Systems is also term as Intrusion Detection & Prevention
Systems (IDPS). Here we can see that Next Generation Cybertap for coporate intrusion detections
server and intrusion prevention servers in Enterprise business are consist of so many different
network security applications which monitor the network and the system suspicious activities.
These system going to protect the business from already existing and upcoming attacks as well as
provide regular control over the system , prevention from cyberthreat. Expertise of Next generation
intrusion prevention system helps in protecting the important data and information as well as
applications from more advanced cyber attack without harming the enterprise production and its
system performance. Our project is mainly aim to explain the different mitigation methodologies or
techniques used by corporate for storing information and data which is going to used in network
system. We are going to discuss more about these things further in our paper. In this type of
mitigation plan the attackers are not able to penetrate in the system and our system then fully
secure. After implementing these system in corporate we will be able to find the attacks types and
methods used by the attackers so that we can easily install those technolgy in our system to protect
information and data against different types of cyber threats.
Aims and Objectives
The main aim of this project is to find out that whether the organizations have enough security
measures to protect or prevent the information and data from cyber attacks on the world wide web.
The main objectives behind for selecting this project is to find out whether the available security
standards and security practices are capable to protect the organizational data and information from
outside security threats and attacks. Cuybertap products nowadays installed in the private and public
sectors all over the world. Cybertrap products mainly applies to analyze the big data to monitor the
traffic of the network and provide visibility on both the end of the network of the organizations . It
also provide a plan for the organization to how they can secure their data and information. Also the
cybertap system is going to provide the information about IP and other suspicious activities of user
as well as system administrator. The cybertap technology is going to support the differenet type of
technology now currently available in the market and from other different type of security threat
situations. Nowadays so many different type of organizations which have daily multiple type of
traffic generations at the applications level and from other different type of security threats uses
cybertap to protect their network. Nowadays there are so many different type of security threats so
that most of the largest global organization uses cybertap methods to manage and secure the
information and identities as well as their technology infrastructure. Cybertap is the leading
solutions which can provide security to lost of data and information over the system network of the
organizations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
As we see that nowadays network is form of the business . Many of the organization and enterprise
as well as agencies of government have created user friendly and tough networks of information are
developed according to the need of the business and users. At current scenario most of the
technologies come with encryption facilities , wireless, VOIP and secure data storage as well as
different type of web technology through which web services are going to be accessed by the
system of the organization. In today times most of the customer know and do transaction by using
the network of the organization . For attackers and hackers these network path is making the
network system more vulnerable due to which they have to put only little effort to break the security
breach of the network. Currently so many people look at the internet as a platform to gather the
important and sensitive data as well as information. But at the same time we see that intrusion
detection and prevention systems (IDPS) point out the threats or intruders before they can harm any
thing of the network as well as system of the organization. Intrusion detection system is a type of
software application which monitors the networks and suspicious activities in the system. These
suspicious activities is going to be reported to network administrator as well as Security information
and event management (SIEM) system. SIEM system is basically a combination of various output
sources and also they use techniques of alarm filtering to spot the suspicious activities on the
network by activating false alarm.
In organization when the system have capabilities of response then they normally comes under
intrusion prevention system. As we see that when any type of business rise and evolve , then they
need to dvelop their already existing network as well as needs to upgrade their network. To
implement this we should analyze the current existing network and also the needs of new network
which is important to the company. By doing this we can easily find out what new equipments and
other related things are required to sure that the new network of the company fully supports the
current and future requirements of the organization. n so many different cases according to the
needs of business there are different types of network connection technologies . To add new user so
many small and medium companies start adding different type of hardware devices with different
qualities and from different manufacturers. Due to new users the network strength start degrading.
If these things continue then the available network not able to support the traffic which network
generated due to increase in the numbers of users.
When network start failing then company decide to redesign their network. Also the network
service provider and ISP generally provides the installation facilities of new devices and an advice
on how to maintain the upgradation of the network. The design of the network is mainly depend
upon the present and future demands of the business to ensure the development of the company by
implementing the right technology. This paper going to discuss about the benefits of next
generation cybertap for intrusion prevention server and intrusion detection servers in corporate or
enterprise business . In this we also going to explain the IDS product benefits and also the
technology which IDS is going to provide for effective protection to the data and information of the
enterprise or corporate business. It also provide knowledge about different standard of security and
methods to protect the daata and information of the organization from the outside attack as well as
cyber attack.
As we see that nowadays network is form of the business . Many of the organization and enterprise
as well as agencies of government have created user friendly and tough networks of information are
developed according to the need of the business and users. At current scenario most of the
technologies come with encryption facilities , wireless, VOIP and secure data storage as well as
different type of web technology through which web services are going to be accessed by the
system of the organization. In today times most of the customer know and do transaction by using
the network of the organization . For attackers and hackers these network path is making the
network system more vulnerable due to which they have to put only little effort to break the security
breach of the network. Currently so many people look at the internet as a platform to gather the
important and sensitive data as well as information. But at the same time we see that intrusion
detection and prevention systems (IDPS) point out the threats or intruders before they can harm any
thing of the network as well as system of the organization. Intrusion detection system is a type of
software application which monitors the networks and suspicious activities in the system. These
suspicious activities is going to be reported to network administrator as well as Security information
and event management (SIEM) system. SIEM system is basically a combination of various output
sources and also they use techniques of alarm filtering to spot the suspicious activities on the
network by activating false alarm.
In organization when the system have capabilities of response then they normally comes under
intrusion prevention system. As we see that when any type of business rise and evolve , then they
need to dvelop their already existing network as well as needs to upgrade their network. To
implement this we should analyze the current existing network and also the needs of new network
which is important to the company. By doing this we can easily find out what new equipments and
other related things are required to sure that the new network of the company fully supports the
current and future requirements of the organization. n so many different cases according to the
needs of business there are different types of network connection technologies . To add new user so
many small and medium companies start adding different type of hardware devices with different
qualities and from different manufacturers. Due to new users the network strength start degrading.
If these things continue then the available network not able to support the traffic which network
generated due to increase in the numbers of users.
When network start failing then company decide to redesign their network. Also the network
service provider and ISP generally provides the installation facilities of new devices and an advice
on how to maintain the upgradation of the network. The design of the network is mainly depend
upon the present and future demands of the business to ensure the development of the company by
implementing the right technology. This paper going to discuss about the benefits of next
generation cybertap for intrusion prevention server and intrusion detection servers in corporate or
enterprise business . In this we also going to explain the IDS product benefits and also the
technology which IDS is going to provide for effective protection to the data and information of the
enterprise or corporate business. It also provide knowledge about different standard of security and
methods to protect the daata and information of the organization from the outside attack as well as
cyber attack.

Literature Review
As we see that in today times due to rise in use of new internet and computer technology in every
sector of life, increases the problems related to the security and privacy of data and information
during the their transmission period. Today in modern times so many people are working on
distribution, collection and execution of data as well as information in every business they do.
Currently there are millions of computers and other different IOT devices collecting as well as
sharing the data and information every second in the whole world at the same time. Due to this at
the same time we are facing so many issues in this information age. As we know that data and
informations is responsible for formation of intellectual property by which people craft their life and
secure their privacy and dignity. Personal data and information related to legal issues is collected
by court and other legal authority. Change from paper to electronic or digital record needs a change
in the security methods and various security measures to prevent this type of threat. The social
problem cause due to this can be solved with full dignity in this information age. In this there are so
many different types of ethical issues are present.
Here we see that most of the network intrusion system of detection normally placed at that point in
the network from where they can easily monitor the traffic of every devices which are present on
the network. Once the threats and attack is spotted as well as any abnormal behaviour of system
detected then an alert message is sent to the network administrator of the organization system.
These system going to protect the business from already existing and upcoming attacks as well as
provide regular control over the system , prevention from cyberthreat. Expertise of Next generation
intrusion prevention system helps in protecting the important data and information as well as
applications from more advanced cyber attack without harming the enterprise production and its
system performance. Our project is mainly aim to explain the different mitigation methodologies or
techniques used by corporate for storing information and data which is going to used in network
system.
Technologies and Resources
Network intrusions now become the very normal things nowadays. According to the recent research
it is found that phising attacks are 5.3 billion industry and other business attack is expected to
increase by 9 billion by the end of 2018. here we can see that there are various type of security tools
like intrusion detection and prevention system to find out the intruders before they can do serious
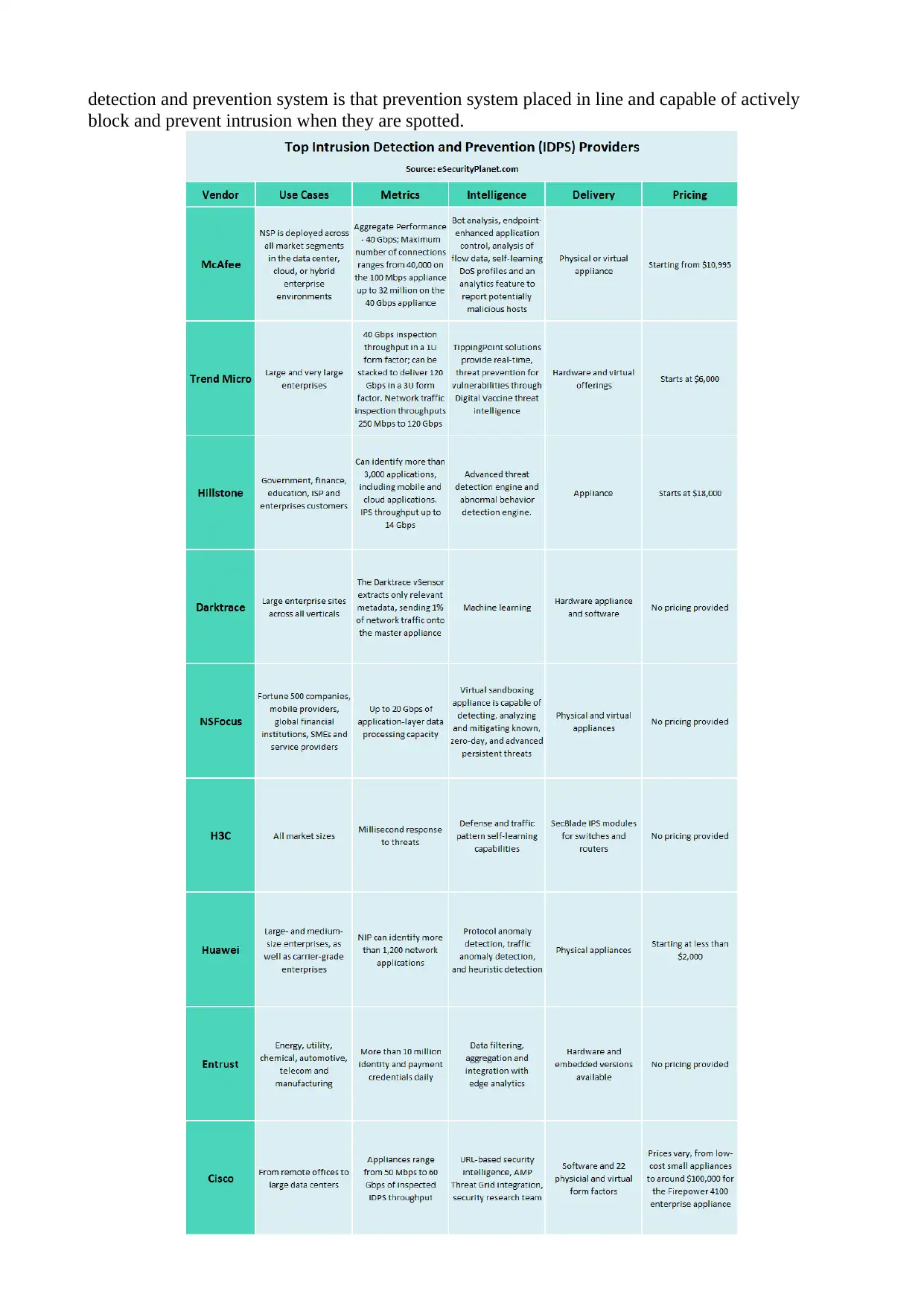
damage. Following are the TOP Intrusion Detection and Prevention (IDPS) providers in the currrent
scenario :
a) McAfee Network Security Plan
This plan provides a intrusion prevention and network threat solution which protects the system and
data of the organization in their data center. It can provides support upto 32 million connections on
a sinle devices which is mainly going to uses intelligence to find out the advanced cyber attacks on
the entire network of the system.
b) Trend Micro Tipping Point
It is mainly used to spot and block the suspicious activities in the network of the system to prevent
the free movement of the malware and ensure that the availability of network enhances their
performance. It can be installed in the network without IP address and easily remove the unwanted
and suspicious activities. This type of security normally cover the entire footprint of the network
system.
As we see that in today times due to rise in use of new internet and computer technology in every
sector of life, increases the problems related to the security and privacy of data and information
during the their transmission period. Today in modern times so many people are working on
distribution, collection and execution of data as well as information in every business they do.
Currently there are millions of computers and other different IOT devices collecting as well as
sharing the data and information every second in the whole world at the same time. Due to this at
the same time we are facing so many issues in this information age. As we know that data and
informations is responsible for formation of intellectual property by which people craft their life and
secure their privacy and dignity. Personal data and information related to legal issues is collected
by court and other legal authority. Change from paper to electronic or digital record needs a change
in the security methods and various security measures to prevent this type of threat. The social
problem cause due to this can be solved with full dignity in this information age. In this there are so
many different types of ethical issues are present.
Here we see that most of the network intrusion system of detection normally placed at that point in
the network from where they can easily monitor the traffic of every devices which are present on
the network. Once the threats and attack is spotted as well as any abnormal behaviour of system
detected then an alert message is sent to the network administrator of the organization system.
These system going to protect the business from already existing and upcoming attacks as well as
provide regular control over the system , prevention from cyberthreat. Expertise of Next generation
intrusion prevention system helps in protecting the important data and information as well as
applications from more advanced cyber attack without harming the enterprise production and its
system performance. Our project is mainly aim to explain the different mitigation methodologies or
techniques used by corporate for storing information and data which is going to used in network
system.
Technologies and Resources
Network intrusions now become the very normal things nowadays. According to the recent research
it is found that phising attacks are 5.3 billion industry and other business attack is expected to
increase by 9 billion by the end of 2018. here we can see that there are various type of security tools
like intrusion detection and prevention system to find out the intruders before they can do serious
damage. Following are the TOP Intrusion Detection and Prevention (IDPS) providers in the currrent
scenario :
a) McAfee Network Security Plan
This plan provides a intrusion prevention and network threat solution which protects the system and
data of the organization in their data center. It can provides support upto 32 million connections on
a sinle devices which is mainly going to uses intelligence to find out the advanced cyber attacks on
the entire network of the system.
b) Trend Micro Tipping Point
It is mainly used to spot and block the suspicious activities in the network of the system to prevent
the free movement of the malware and ensure that the availability of network enhances their
performance. It can be installed in the network without IP address and easily remove the unwanted
and suspicious activities. This type of security normally cover the entire footprint of the network
system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

c) Darktrace Enterprise Immune System
This system is basically a machine learning and AI technology for the defense of the cyber threats .
Normally it can easily learn unique pattern for every device and user available on the network.
d) NSFocus
Here we can see that NSFocus Next Generation Prevention System provides the security threats
protection from block intrusions, various security breaches and other available assets. It basically
uses a multilayers approach to spot the suspicious threats to protect from the various malware ,
spyware, protocol attacks and different type of web threats.
e) H3C SecBlade IPS
It is a module for H3C switches and other different types of routers. It integrate with the system and
provide functions like intrusion detection, prevention , management of bandwidth and filtering of
virus. It can mainly provide layer 4-7 depth analysis , detection of cyber threats and other different
types of attacks with self learning as well as response capabilities.
f) Huawei NIP
Huawei network intelligent protection provides the virtual patches , protection to web application,
protection of client application , antimalware and also provide vulnerability based detection
facilities to protect against the cyber worm infections as well as different types of cyberattacks.
g) Cisco Firepower NGIPS
Here we can see that cisco next generation intrusion prevention systems comes in a software,
physical and virtual devices for small as well as large enterprise and corporation . NGIPS mainly
provides URL based security intelligence and other threat grid integration techniques.
Nowadays most of the system try to stop an intrusion which is not required and not expected from a
monitoring system. Intrusion detection and prevention systems (IDPS) are mainly aims upon
finding the upcoming threats, logging information and other various types of logging as well as
reporting attempts. Most of the organization uses IDPS for other purposes like spotting the
problems with security policies , documentation of already available threats and violating the
security policies. So we can say that IDPS become the important addition to the security
infrastructure of nearly every organization. IDPS generally collect the information related to the
suspicious activities and inform the systen network administrators about important events and
reports of the suspicious activities which occur over the network of the system. They also provide
different type of response techniques which mainly involves in changing the environment of the
security or helps in changing the content of different type of attacks.
Intrusion prevention system also known as the intrusion detection and prevention system which
provide network security devices which monitor the network and various type of system activities
for suspicious activities. The main work of intrusion prevention system is to find out the suspicious
activities , log information , report it and prevent it. Intrusion prevention system are normally
considered as extension of intrusion detection systems because both of them monitor the network
traffic and system activities for suspicious activities. The main difference between intrusion
This system is basically a machine learning and AI technology for the defense of the cyber threats .
Normally it can easily learn unique pattern for every device and user available on the network.
d) NSFocus
Here we can see that NSFocus Next Generation Prevention System provides the security threats
protection from block intrusions, various security breaches and other available assets. It basically
uses a multilayers approach to spot the suspicious threats to protect from the various malware ,
spyware, protocol attacks and different type of web threats.
e) H3C SecBlade IPS
It is a module for H3C switches and other different types of routers. It integrate with the system and
provide functions like intrusion detection, prevention , management of bandwidth and filtering of
virus. It can mainly provide layer 4-7 depth analysis , detection of cyber threats and other different
types of attacks with self learning as well as response capabilities.
f) Huawei NIP
Huawei network intelligent protection provides the virtual patches , protection to web application,
protection of client application , antimalware and also provide vulnerability based detection
facilities to protect against the cyber worm infections as well as different types of cyberattacks.
g) Cisco Firepower NGIPS
Here we can see that cisco next generation intrusion prevention systems comes in a software,
physical and virtual devices for small as well as large enterprise and corporation . NGIPS mainly
provides URL based security intelligence and other threat grid integration techniques.
Nowadays most of the system try to stop an intrusion which is not required and not expected from a
monitoring system. Intrusion detection and prevention systems (IDPS) are mainly aims upon
finding the upcoming threats, logging information and other various types of logging as well as
reporting attempts. Most of the organization uses IDPS for other purposes like spotting the
problems with security policies , documentation of already available threats and violating the
security policies. So we can say that IDPS become the important addition to the security
infrastructure of nearly every organization. IDPS generally collect the information related to the
suspicious activities and inform the systen network administrators about important events and
reports of the suspicious activities which occur over the network of the system. They also provide
different type of response techniques which mainly involves in changing the environment of the
security or helps in changing the content of different type of attacks.
Intrusion prevention system also known as the intrusion detection and prevention system which
provide network security devices which monitor the network and various type of system activities
for suspicious activities. The main work of intrusion prevention system is to find out the suspicious
activities , log information , report it and prevent it. Intrusion prevention system are normally
considered as extension of intrusion detection systems because both of them monitor the network
traffic and system activities for suspicious activities. The main difference between intrusion
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
detection and prevention system is that prevention system placed in line and capable of actively
block and prevent intrusion when they are spotted.
block and prevent intrusion when they are spotted.

Methods and Workplan
There are so many methods and workplan by which we can achieve the security of data and
information of any organization. Nowadays in most of the business patron want to use the
applications in a different way so that they can easily do their work with more accuracy and
security. As we know that in current time most of the organizations uses virtualization to reduce
their expenses. It provides file system or host the illusion that there is more physical space is
available than the actual available space. When servers start working fully then its very necessary to
monitor them constantly. As we all see that this cisco internet working model is largely used in the
industry to design a scalable, reliable and cost efficient internet work. To fullfill the basic goals of
an organization a network must be create on an architecture which allow both growth and
flexibility. The three layer model helps in designing , implementing and creating a reliable cost
effective network. Each layer of this model has its own functionality and features which help in
decreasing the complexity of network. Using a hierarchical model to develop IT infrastructure of
organization can help in minimize costs.
Design of the network in IT infrastructure is a very larger field and its needs high level of
knowledge and experience. The cisco organization model gives all the benefits of hierarchical
network design on the infrastructure of the campus, and provides the design of bigger and more
scalable networks. It provides flexibility in the design of the network and helps in
troubleshooting as well implementation of its functionality. Togather these submodules provides
increased security and flexibility using the access management.
Here we can see that intrsion prevention system are basically divided in to following different
types :
a) NIPS : it is known as network based intrusion prevention system which going to monitor the
whole network for different type of suspicious activities by analyzing the protocol activities.
b) WIPS : it is term as wireless intrusion prevention system to mainly monitor the wireless network
for malicious activities by monitoring the wireless networking protocols.
c) NBA : Network behaviour analysis used to analyze the traffic of the network to spot the risk
which cause due to unusal flow of traffic and other different types of attack like DdoS attack, and
other different voilation of policy as well as malware attack.
d) HIPS : it is basically known as host based intrusion prevention system. It is a type of install
software package which basically monitor the suspicious activities by analyzing the events which
occur in the network system.
There are also different types of detection methods which determine the organization security
measures due to which they can easily protect or prevent the data and information from different
type of security threats . These detection methods are enough to provide the security from outside
attacks to the network system of the organization. Most of the intrusion prevention system generally
uses three types of detection methods :
a) Detection based on signature
There are so many methods and workplan by which we can achieve the security of data and
information of any organization. Nowadays in most of the business patron want to use the
applications in a different way so that they can easily do their work with more accuracy and
security. As we know that in current time most of the organizations uses virtualization to reduce
their expenses. It provides file system or host the illusion that there is more physical space is
available than the actual available space. When servers start working fully then its very necessary to
monitor them constantly. As we all see that this cisco internet working model is largely used in the
industry to design a scalable, reliable and cost efficient internet work. To fullfill the basic goals of
an organization a network must be create on an architecture which allow both growth and
flexibility. The three layer model helps in designing , implementing and creating a reliable cost
effective network. Each layer of this model has its own functionality and features which help in
decreasing the complexity of network. Using a hierarchical model to develop IT infrastructure of
organization can help in minimize costs.
Design of the network in IT infrastructure is a very larger field and its needs high level of
knowledge and experience. The cisco organization model gives all the benefits of hierarchical
network design on the infrastructure of the campus, and provides the design of bigger and more
scalable networks. It provides flexibility in the design of the network and helps in
troubleshooting as well implementation of its functionality. Togather these submodules provides
increased security and flexibility using the access management.
Here we can see that intrsion prevention system are basically divided in to following different
types :
a) NIPS : it is known as network based intrusion prevention system which going to monitor the
whole network for different type of suspicious activities by analyzing the protocol activities.
b) WIPS : it is term as wireless intrusion prevention system to mainly monitor the wireless network
for malicious activities by monitoring the wireless networking protocols.
c) NBA : Network behaviour analysis used to analyze the traffic of the network to spot the risk
which cause due to unusal flow of traffic and other different types of attack like DdoS attack, and
other different voilation of policy as well as malware attack.
d) HIPS : it is basically known as host based intrusion prevention system. It is a type of install
software package which basically monitor the suspicious activities by analyzing the events which
occur in the network system.
There are also different types of detection methods which determine the organization security
measures due to which they can easily protect or prevent the data and information from different
type of security threats . These detection methods are enough to provide the security from outside
attacks to the network system of the organization. Most of the intrusion prevention system generally
uses three types of detection methods :
a) Detection based on signature
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In this detection methods we monitors the packet in the network and compare it with pre determine
and configured patterns of attacks which also term as signatures.
b) Detection based on statistics
Intrusion detection system is totally based upon monitor network traffic and compare it against the
fixed baseline.
c) Stateful protocol analysis detection
This method mainly spot the protocol by comparing the already available data and information.
AS we know that cloud computing is a model for enabling easy and user friendly on demand
network access to a shared applications or services which have contineousely released with less
effort and interaction with the service provider. Many of the organizations or company can use this
facilities to run,host and develop as well as provides services according to the demand of the user at
anywhere,anytime and on any device. According to report by 2020, 24% of the total addressable IT
market will be cloud. Integrated security protects the effects of worm, viruses and other attacks on
the design of the network. The module of the data center support the network management service
for our organisation like logging, monitoring and other management features along with
troubleshooting from the end. The data center of the organization mainly contains the email and
domain name system for the internal user of the company. Before redesigning their network and its
upgradation firstly send a technician onsite to do the survey of the site and documenting the
complete network structure of the company. It is very important to investigate and document the
whole physical structure of the structure to decide where new devices and equipment should be
installed . Nowadays all types of network wether it is small, medium and lage have similar types of
fundamentals requirements.
Ethics aspects
As we know that in recent time data and information is knowledge and knowledge is power and
invariably power converts into money. Now the more the data you have the more money you make.
It is proved that data & information both work as an support system for both consumer and
business. The main problem rises when privacy is invaded, as well as sensitive information and data
is lost and stored. Due to this individual or company security and privacy ethics become very
vulnerable. Many of the business houses uses so many advanced algorithmic analysis to extract data
and information so that they can use it to spot the trends of the market and also prevent from the
different ethical issues. The way nowadays the people use the internet ,it is very high probablity that
someone out there knows more about the people than people know about himself. Misuse of
information is also comes under major risk . Information which is obtain ethically can be used for
different unethical purposes . As we see that cyberspace is full of security threats like theft of
identity, misuse of social platform, and cyberterrorism. It effects the life of people personally,
creates threats for national security, and undertake the economy of any country. A cybersecurity
threats related issues can impact in any form like organised cyberattack can cause huge harm to the
structure of information transffer .Data and information which are in the form of documents,
persentations , emails, and databases are the lifeline of the most of the companies and application
which protect and run your organisations requires a lot of space. The threats or risks in
cybersecurity attack is mainly depend upon three factors like who is attacking, weakness where they
attack, and impact of attacks . The security threats are present external as well as internal. Policy of
usage for computers and other IOT resources play a significant role in cybersecurity.
and configured patterns of attacks which also term as signatures.
b) Detection based on statistics
Intrusion detection system is totally based upon monitor network traffic and compare it against the
fixed baseline.
c) Stateful protocol analysis detection
This method mainly spot the protocol by comparing the already available data and information.
AS we know that cloud computing is a model for enabling easy and user friendly on demand
network access to a shared applications or services which have contineousely released with less
effort and interaction with the service provider. Many of the organizations or company can use this
facilities to run,host and develop as well as provides services according to the demand of the user at
anywhere,anytime and on any device. According to report by 2020, 24% of the total addressable IT
market will be cloud. Integrated security protects the effects of worm, viruses and other attacks on
the design of the network. The module of the data center support the network management service
for our organisation like logging, monitoring and other management features along with
troubleshooting from the end. The data center of the organization mainly contains the email and
domain name system for the internal user of the company. Before redesigning their network and its
upgradation firstly send a technician onsite to do the survey of the site and documenting the
complete network structure of the company. It is very important to investigate and document the
whole physical structure of the structure to decide where new devices and equipment should be
installed . Nowadays all types of network wether it is small, medium and lage have similar types of
fundamentals requirements.
Ethics aspects
As we know that in recent time data and information is knowledge and knowledge is power and
invariably power converts into money. Now the more the data you have the more money you make.
It is proved that data & information both work as an support system for both consumer and
business. The main problem rises when privacy is invaded, as well as sensitive information and data
is lost and stored. Due to this individual or company security and privacy ethics become very
vulnerable. Many of the business houses uses so many advanced algorithmic analysis to extract data
and information so that they can use it to spot the trends of the market and also prevent from the
different ethical issues. The way nowadays the people use the internet ,it is very high probablity that
someone out there knows more about the people than people know about himself. Misuse of
information is also comes under major risk . Information which is obtain ethically can be used for
different unethical purposes . As we see that cyberspace is full of security threats like theft of
identity, misuse of social platform, and cyberterrorism. It effects the life of people personally,
creates threats for national security, and undertake the economy of any country. A cybersecurity
threats related issues can impact in any form like organised cyberattack can cause huge harm to the
structure of information transffer .Data and information which are in the form of documents,
persentations , emails, and databases are the lifeline of the most of the companies and application
which protect and run your organisations requires a lot of space. The threats or risks in
cybersecurity attack is mainly depend upon three factors like who is attacking, weakness where they
attack, and impact of attacks . The security threats are present external as well as internal. Policy of
usage for computers and other IOT resources play a significant role in cybersecurity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
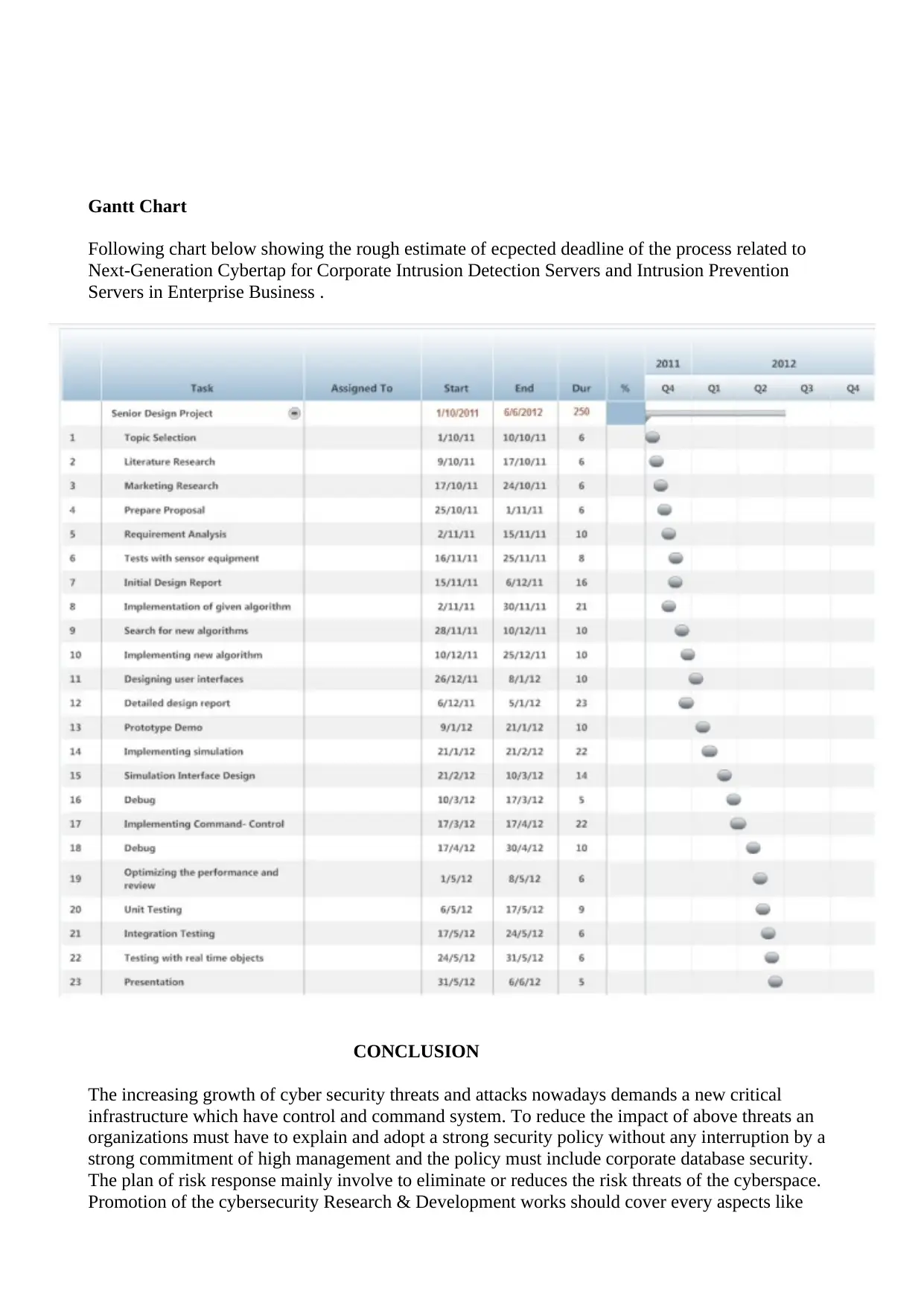
Gantt Chart
Following chart below showing the rough estimate of ecpected deadline of the process related to
Next-Generation Cybertap for Corporate Intrusion Detection Servers and Intrusion Prevention
Servers in Enterprise Business .
CONCLUSION
The increasing growth of cyber security threats and attacks nowadays demands a new critical
infrastructure which have control and command system. To reduce the impact of above threats an
organizations must have to explain and adopt a strong security policy without any interruption by a
strong commitment of high management and the policy must include corporate database security.
The plan of risk response mainly involve to eliminate or reduces the risk threats of the cyberspace.
Promotion of the cybersecurity Research & Development works should cover every aspects like
Following chart below showing the rough estimate of ecpected deadline of the process related to
Next-Generation Cybertap for Corporate Intrusion Detection Servers and Intrusion Prevention
Servers in Enterprise Business .
CONCLUSION
The increasing growth of cyber security threats and attacks nowadays demands a new critical
infrastructure which have control and command system. To reduce the impact of above threats an
organizations must have to explain and adopt a strong security policy without any interruption by a
strong commitment of high management and the policy must include corporate database security.
The plan of risk response mainly involve to eliminate or reduces the risk threats of the cyberspace.
Promotion of the cybersecurity Research & Development works should cover every aspects like

developing system which is trustworthy , installments and update in whole life cycle provides new
cybersecurity technology. At the end we can say that cybersecurity have to be upgraded regularly
at different levels, considering the high rates of cyber threats . The government makes cybersecurity
policy framework very tough by integrating privacy saftey which win the trust and confidence of
the user. There is no any security methods which going to protect your organization from threats ,
only they can lower it. when the project is completed of the organization then we need one more
basic step of official approval from all the section of organization, that whether the system is
correctly working or not to final close of the project. The signoff process mainly responsible for
accountability and control the specific abilities of the network system. The key of project signoff
mainly consist of basic information about the project and specific sign off field.
Reference
Debar, H., Becker, M., and Siboni, D. (1992). A neural network component for an intrusion
detection system. In Proceedings of the 1992 IEEE Computer Society Symposium on Research in
Computer .~’~- curity and Privacy, 240-250.
Denning, D. E. (1987). An intrusion detection model. IEEE Transactions on Software Engineering,
SE13:222-232.
Fox, K. L., Henning, l:t. 1~., l~eed, J. H., and Simonian. R. (1990). A neural network approach
towards intrusion detection. In Proceedings of the 13th ,V~ltional Computer Security Conference,
125-134
Frank, J. (1994). Artificial intelligence and intrusion detection: Current and future directions. In
Proceedings of the National 17th Computer Sec~lrttt/ Conference.
Garvey, T. D., and Lunt, T. F. (1991). Model-based intrusion detection. In Proceedings of the
14th .V,ttional Computer Security Conference.
Miyata, Y. (1991). A User’s Guide to PlaNet t; rsion 5.6 - A Tool for Constructing, Running, mtd
Looking in to a PDP Network. Computer Science Department, University of Colorado, Boulder,
Boulder, CO.
.Mukherjee, B., Ileberlein, L. T., and Levitt, K. N. (199,1). Network intrusion detection. IEEE
Network. 26 -.i 1.
Porr~, P. A.. llgun, K., and Kemmerer, R. A. (1998). State transition analysis: A rule-based
intrusion detection approach. IEEE Transactions on Software Engineering, SE-21:181-199.
Teng, II. S., Chen. K., and Lu, S. C. (1990). Adaptive real-! ime anomaly detection using
inductively generated sequential patterns. In Proceedings of th~ 1990 IEEE Srlmposimn on
Research m ComImtcr ,’,’~curzt~l and PrlvactI, 278-284
Wikipedia, The Free Encyclopedia. (2009, December). Retrieved October 19, 2011, from
Wikipedia: http://en.wikipedia.org/wiki/Geophone
Audette, W. E., Kynor, D. B., Wilbur, J. C., Gagne, J. R., & Peck, L. (2009). Improved Intruder
Detection Using Seismic Sensors and Adaptive Noise Cancellation.
cybersecurity technology. At the end we can say that cybersecurity have to be upgraded regularly
at different levels, considering the high rates of cyber threats . The government makes cybersecurity
policy framework very tough by integrating privacy saftey which win the trust and confidence of
the user. There is no any security methods which going to protect your organization from threats ,
only they can lower it. when the project is completed of the organization then we need one more
basic step of official approval from all the section of organization, that whether the system is
correctly working or not to final close of the project. The signoff process mainly responsible for
accountability and control the specific abilities of the network system. The key of project signoff
mainly consist of basic information about the project and specific sign off field.
Reference
Debar, H., Becker, M., and Siboni, D. (1992). A neural network component for an intrusion
detection system. In Proceedings of the 1992 IEEE Computer Society Symposium on Research in
Computer .~’~- curity and Privacy, 240-250.
Denning, D. E. (1987). An intrusion detection model. IEEE Transactions on Software Engineering,
SE13:222-232.
Fox, K. L., Henning, l:t. 1~., l~eed, J. H., and Simonian. R. (1990). A neural network approach
towards intrusion detection. In Proceedings of the 13th ,V~ltional Computer Security Conference,
125-134
Frank, J. (1994). Artificial intelligence and intrusion detection: Current and future directions. In
Proceedings of the National 17th Computer Sec~lrttt/ Conference.
Garvey, T. D., and Lunt, T. F. (1991). Model-based intrusion detection. In Proceedings of the
14th .V,ttional Computer Security Conference.
Miyata, Y. (1991). A User’s Guide to PlaNet t; rsion 5.6 - A Tool for Constructing, Running, mtd
Looking in to a PDP Network. Computer Science Department, University of Colorado, Boulder,
Boulder, CO.
.Mukherjee, B., Ileberlein, L. T., and Levitt, K. N. (199,1). Network intrusion detection. IEEE
Network. 26 -.i 1.
Porr~, P. A.. llgun, K., and Kemmerer, R. A. (1998). State transition analysis: A rule-based
intrusion detection approach. IEEE Transactions on Software Engineering, SE-21:181-199.
Teng, II. S., Chen. K., and Lu, S. C. (1990). Adaptive real-! ime anomaly detection using
inductively generated sequential patterns. In Proceedings of th~ 1990 IEEE Srlmposimn on
Research m ComImtcr ,’,’~curzt~l and PrlvactI, 278-284
Wikipedia, The Free Encyclopedia. (2009, December). Retrieved October 19, 2011, from
Wikipedia: http://en.wikipedia.org/wiki/Geophone
Audette, W. E., Kynor, D. B., Wilbur, J. C., Gagne, J. R., & Peck, L. (2009). Improved Intruder
Detection Using Seismic Sensors and Adaptive Noise Cancellation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Clarke, B. (2007, July 23). Retrieved October 20, 2011, from PSR-1 Seismic Intrusion Detector:
http://www.prc68.com/I/PSR1.shtml
Pakhomov, A., Sicignano, A., Sandy, M., & Goldburt, T. (2003). Seismic Footstep Signal
Characterization. NY
K. Borders, “Protecting confidential information from malicious software,” Ph.D. Dissertation,
Dept. University of Michigan, Ann Arbor, MI, USA, 2009.
H. I. Bulbul, I. Batmaz, and M. Ozel, “Wireless network security: comparison of WEP (Wired
Equivalent Privacy) mechanism, WPA (Wi-Fi Protected Access) and RSN (Robust Security
Network) security protocols,” in Proc. 1st international conference on Forensic applications and
techniques in telecommunications, information, and multimedia, Adelaide, Australia, January,
2008.
XuXiaohui “Study on Security Problems and Key Technologies of the Internet of
Things”Computational and Information Sciences (ICCIS), 2013 Fifth International Conference on,
Issue Date: 21-23 June 2013
http://www.prc68.com/I/PSR1.shtml
Pakhomov, A., Sicignano, A., Sandy, M., & Goldburt, T. (2003). Seismic Footstep Signal
Characterization. NY
K. Borders, “Protecting confidential information from malicious software,” Ph.D. Dissertation,
Dept. University of Michigan, Ann Arbor, MI, USA, 2009.
H. I. Bulbul, I. Batmaz, and M. Ozel, “Wireless network security: comparison of WEP (Wired
Equivalent Privacy) mechanism, WPA (Wi-Fi Protected Access) and RSN (Robust Security
Network) security protocols,” in Proc. 1st international conference on Forensic applications and
techniques in telecommunications, information, and multimedia, Adelaide, Australia, January,
2008.
XuXiaohui “Study on Security Problems and Key Technologies of the Internet of
Things”Computational and Information Sciences (ICCIS), 2013 Fifth International Conference on,
Issue Date: 21-23 June 2013
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





