NMAP in Cyber Security: Scanning and Analyzing Network Devices
VerifiedAdded on 2023/06/03
|6
|502
|339
Practical Assignment
AI Summary
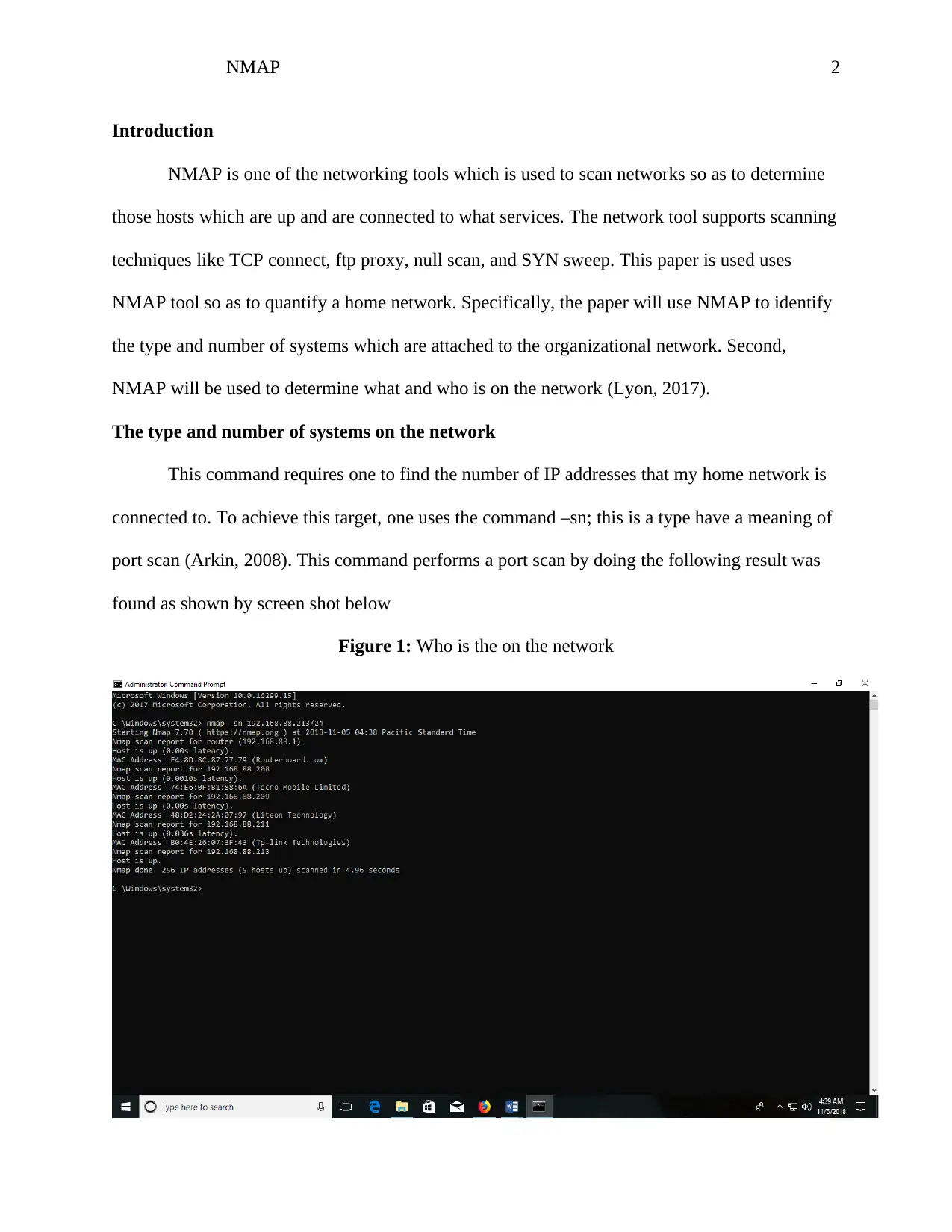
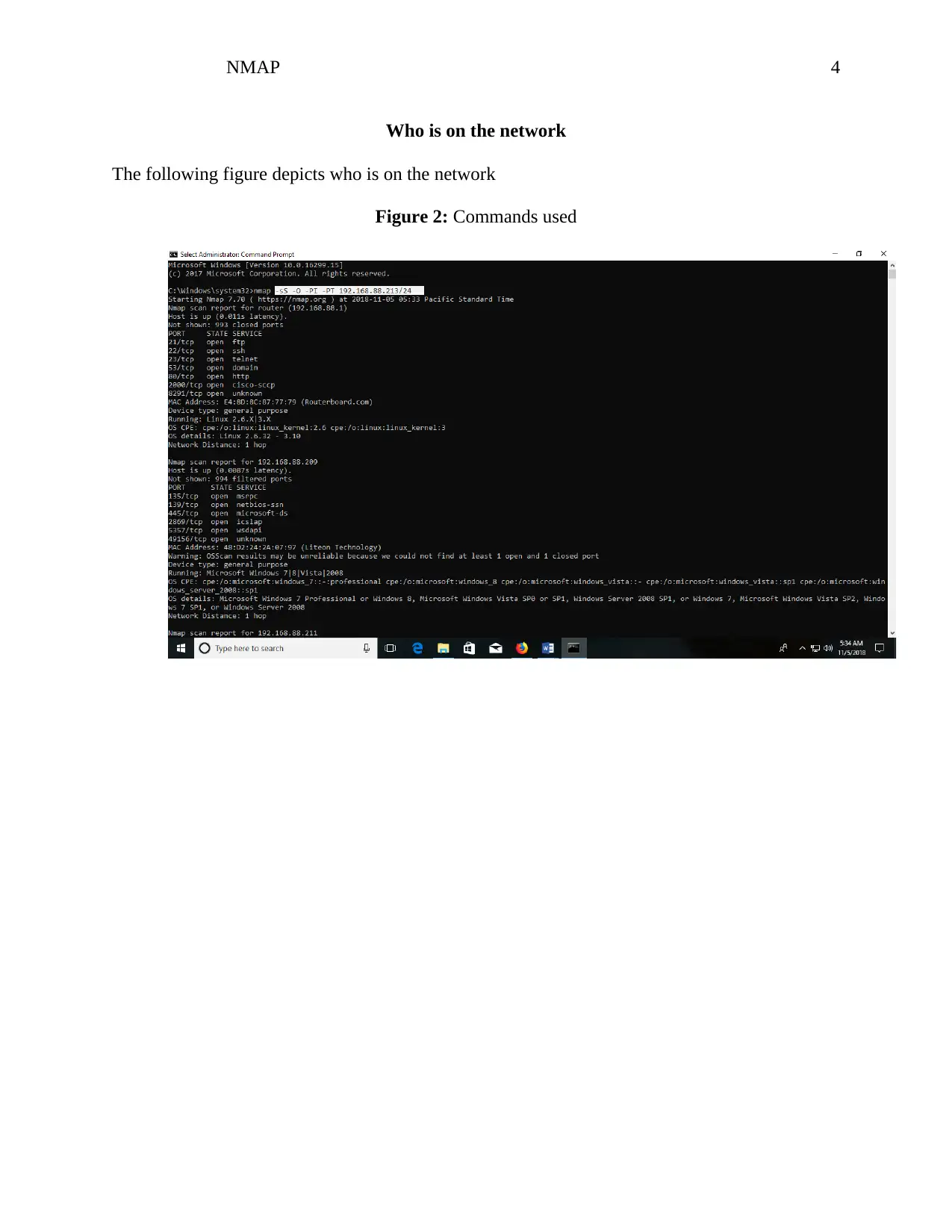
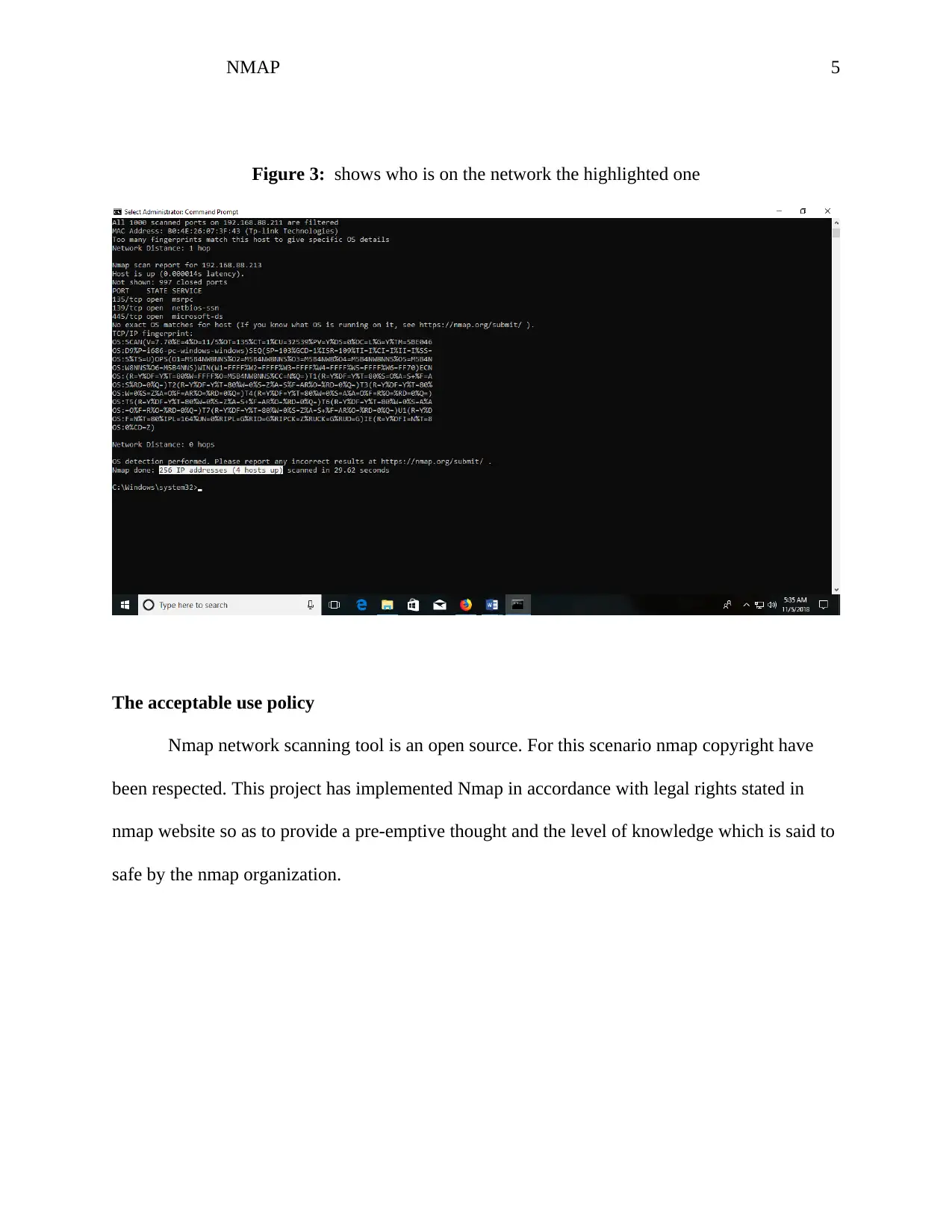
This assignment employs the NMAP network scanning tool to analyze a home network and identify connected devices. The analysis begins by using the command '-sn' to determine the number of IP addresses connected to the network, revealing five hosts including a router, Techno Mobile device, Liteon technology device, and a TP-Link device. Each device's IP address is identified, and the assignment includes screenshots demonstrating the commands used and the results obtained. The acceptable use policy of NMAP is respected, ensuring the project adheres to the legal rights stated on the NMAP website. The aim is to provide a preemptive understanding and knowledge level deemed safe by the NMAP organization, enhancing network security awareness.
1 out of 6









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)