Offline Mobile Based Library Circulation System Report 2022
VerifiedAdded on 2022/10/11
|56
|11940
|14
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

OFFLINE MOBILE BASED LIBRARY CIRCULATION SYSTEM
[Document subtitle]
[DATE]
[Document subtitle]
[DATE]
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
pg. 1

Table of Contents
CHAPTER ONE..................................................................................................................................4
1. INTRODUCTION.......................................................................................................................4
1.1. Background..........................................................................................................................4
1.1.1 Existing Problem..........................................................................................................9
1.1.2 Situation......................................................................................................................10
1.2 Motivation..........................................................................................................................11
1.3 Project Aim........................................................................................................................11
1.4 Project Objectives..............................................................................................................11
CHAPTER TWO...............................................................................................................................13
2. REQUIREMENT ANALYSIS..................................................................................................13
2.1 Introduction.............................................................................................................................13
2.2 Stakeholders.............................................................................................................................13
2.3 System Interface......................................................................................................................14
2.4 User Interface...........................................................................................................................17
2.5 Characteristics.........................................................................................................................20
2.6 Scope of the System.................................................................................................................20
2.7 Functional Requirements........................................................................................................21
2.8 Non-Functional Requirements................................................................................................21
CHAPTER THREE...........................................................................................................................23
3. RESEARCH/ LITERATURE REVIEW.................................................................................23
3.1 Introduction.............................................................................................................................23
3.2 Library System........................................................................................................................23
3.2.1 Introduction........................................................................................................................23
3.2.2 MARC21 File Format...........................................................................................................27
3.2.3 Scanning Process................................................................................................................31
3.2.4 Conclusion..........................................................................................................................31
3.3 Software Development Technologies......................................................................................32
3.3.1 Introduction........................................................................................................................32
3.3.2 Java.....................................................................................................................................32
3.3.3 JSON....................................................................................................................................33
3.3.4 MySQL.................................................................................................................................33
3.3.5 Conclusion..........................................................................................................................34
CHAPTER FOUR.............................................................................................................................36
4 PRODUCT DESIGN......................................................................................................................36
pg. 2
CHAPTER ONE..................................................................................................................................4
1. INTRODUCTION.......................................................................................................................4
1.1. Background..........................................................................................................................4
1.1.1 Existing Problem..........................................................................................................9
1.1.2 Situation......................................................................................................................10
1.2 Motivation..........................................................................................................................11
1.3 Project Aim........................................................................................................................11
1.4 Project Objectives..............................................................................................................11
CHAPTER TWO...............................................................................................................................13
2. REQUIREMENT ANALYSIS..................................................................................................13
2.1 Introduction.............................................................................................................................13
2.2 Stakeholders.............................................................................................................................13
2.3 System Interface......................................................................................................................14
2.4 User Interface...........................................................................................................................17
2.5 Characteristics.........................................................................................................................20
2.6 Scope of the System.................................................................................................................20
2.7 Functional Requirements........................................................................................................21
2.8 Non-Functional Requirements................................................................................................21
CHAPTER THREE...........................................................................................................................23
3. RESEARCH/ LITERATURE REVIEW.................................................................................23
3.1 Introduction.............................................................................................................................23
3.2 Library System........................................................................................................................23
3.2.1 Introduction........................................................................................................................23
3.2.2 MARC21 File Format...........................................................................................................27
3.2.3 Scanning Process................................................................................................................31
3.2.4 Conclusion..........................................................................................................................31
3.3 Software Development Technologies......................................................................................32
3.3.1 Introduction........................................................................................................................32
3.3.2 Java.....................................................................................................................................32
3.3.3 JSON....................................................................................................................................33
3.3.4 MySQL.................................................................................................................................33
3.3.5 Conclusion..........................................................................................................................34
CHAPTER FOUR.............................................................................................................................36
4 PRODUCT DESIGN......................................................................................................................36
pg. 2

4.1 Technologies.............................................................................................................................36
4.2 Architecture.............................................................................................................................38
4.3 Data Models.............................................................................................................................39
4.4 Security.....................................................................................................................................40
CHAPTER FIVE...............................................................................................................................41
5 IMPLEMENTATION....................................................................................................................41
5.1 Interface...................................................................................................................................41
5.2 Technical Details......................................................................................................................42
5.2.1 Scanning Barcode................................................................................................................42
5.2.2 Storing Details.....................................................................................................................43
5.2.3 Client-side Technologies.....................................................................................................43
CHAPTER SIX..................................................................................................................................44
6 TESTING........................................................................................................................................44
CHAPTER SEVEN...........................................................................................................................45
7 PROJECT MANAGEMENT.........................................................................................................45
7.1 Schedule....................................................................................................................................45
7.2 Project Deliverables.................................................................................................................46
7.3 Risk Management....................................................................................................................46
7.4 Communication with Client....................................................................................................47
CHAPTER EIGHT...........................................................................................................................48
8 PROJECT EVALUATION............................................................................................................48
8.1 Software Quality......................................................................................................................48
8.2 Ease of Use...............................................................................................................................48
8.3 Methodology Choice................................................................................................................49
8.4 Future Improvement...............................................................................................................49
CHAPTER NINE...............................................................................................................................50
9 REFLECTION................................................................................................................................50
9.1 Achievements...........................................................................................................................50
9.2 Challenges................................................................................................................................51
9.3 Conclusion................................................................................................................................52
References and Bibliography............................................................................................................53
pg. 3
4.2 Architecture.............................................................................................................................38
4.3 Data Models.............................................................................................................................39
4.4 Security.....................................................................................................................................40
CHAPTER FIVE...............................................................................................................................41
5 IMPLEMENTATION....................................................................................................................41
5.1 Interface...................................................................................................................................41
5.2 Technical Details......................................................................................................................42
5.2.1 Scanning Barcode................................................................................................................42
5.2.2 Storing Details.....................................................................................................................43
5.2.3 Client-side Technologies.....................................................................................................43
CHAPTER SIX..................................................................................................................................44
6 TESTING........................................................................................................................................44
CHAPTER SEVEN...........................................................................................................................45
7 PROJECT MANAGEMENT.........................................................................................................45
7.1 Schedule....................................................................................................................................45
7.2 Project Deliverables.................................................................................................................46
7.3 Risk Management....................................................................................................................46
7.4 Communication with Client....................................................................................................47
CHAPTER EIGHT...........................................................................................................................48
8 PROJECT EVALUATION............................................................................................................48
8.1 Software Quality......................................................................................................................48
8.2 Ease of Use...............................................................................................................................48
8.3 Methodology Choice................................................................................................................49
8.4 Future Improvement...............................................................................................................49
CHAPTER NINE...............................................................................................................................50
9 REFLECTION................................................................................................................................50
9.1 Achievements...........................................................................................................................50
9.2 Challenges................................................................................................................................51
9.3 Conclusion................................................................................................................................52
References and Bibliography............................................................................................................53
pg. 3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CHAPTER ONE
1. INTRODUCTION
This is the very first chapter of the report. The chapter introduces general information about
library management system. In this chapter, the background of library management system
will be discussed in details, the background of the system will be divided into general and
specific background. General background information will discuss all the general information
which pertains library management system from its definitive state. Specific background
information will discuss the topic under investigation which is the library information system
in mobile devices, the background of mobile based library circulation system will be
discussed too. The objectives which are supposed to be achieved will also be outlines as the
project has to achieve the set objectives to be termed as complete and satisfactory project.
The aim purpose or the aim of carrying out the project will also be established in this chapter,
the motivation factor behind getting into researching this particular topic and its benefits that
will come as a result of successfully completing and implementing the project is also
discussed. The statement of the problem which contains the existing problem which
prompted research and implementation of the project is a discussed too.
1.1. Background
A library is a sorted out gathering of data sources which is made available to the
individuals. The library generally contains the data physically or in a digitized
arrangement. In the bygone time frame the entrance was for the most part in the
library room as the innovation grew up the entrance that was made on the web
(Dinesh et al.,2015). Library is a quickly developing life form. The antiquated
strategies to keep up it are never again unique and proficient. For quick recovery and
pg. 4
1. INTRODUCTION
This is the very first chapter of the report. The chapter introduces general information about
library management system. In this chapter, the background of library management system
will be discussed in details, the background of the system will be divided into general and
specific background. General background information will discuss all the general information
which pertains library management system from its definitive state. Specific background
information will discuss the topic under investigation which is the library information system
in mobile devices, the background of mobile based library circulation system will be
discussed too. The objectives which are supposed to be achieved will also be outlines as the
project has to achieve the set objectives to be termed as complete and satisfactory project.
The aim purpose or the aim of carrying out the project will also be established in this chapter,
the motivation factor behind getting into researching this particular topic and its benefits that
will come as a result of successfully completing and implementing the project is also
discussed. The statement of the problem which contains the existing problem which
prompted research and implementation of the project is a discussed too.
1.1. Background
A library is a sorted out gathering of data sources which is made available to the
individuals. The library generally contains the data physically or in a digitized
arrangement. In the bygone time frame the entrance was for the most part in the
library room as the innovation grew up the entrance that was made on the web
(Dinesh et al.,2015). Library is a quickly developing life form. The antiquated
strategies to keep up it are never again unique and proficient. For quick recovery and
pg. 4

scattering of data and better administration for the customers, use of current
procedures has turned out to be totally imperative (Neelakandan et al., 2010).
A library is involved the accompanying areas, in light of the administrations
rendered.
i. Acquisition Section: The books requested by various divisions are finished by
the Acquisition area. College book focus is additionally working in this area for
supply of books to the libraries in this college.
ii. Technical Section: To arrange, index, OPAC, Barcode and so forth the
archives of the University Library this segment is working. 2
iii. Circulation Section: This segment gives reports to the individuals and clients
of library for home perusing just as perusing in the library. The archives are
organized on the racks in stacks according to the Dewey Decimal Classification
Scheme.
iv. Periodical Section: To acquire, keep up and orchestrate periodicals
administrations to library individuals. Periodical area furnishes reference
administration as for the necessity of the peruser. Reference area is connected to
periodical segment for accommodation of the Library clients.
v. Databases: Databases like OPAC, CAB-CD ROM abstracting databases,
DELNET online Network Service and so on are accessible for the library
individuals.
vi. Reprographic Section: This Section has two programmed plain paper copiers
and a copying machine through which the administrations of photocopy are given to
the perusers.
pg. 5
procedures has turned out to be totally imperative (Neelakandan et al., 2010).
A library is involved the accompanying areas, in light of the administrations
rendered.
i. Acquisition Section: The books requested by various divisions are finished by
the Acquisition area. College book focus is additionally working in this area for
supply of books to the libraries in this college.
ii. Technical Section: To arrange, index, OPAC, Barcode and so forth the
archives of the University Library this segment is working. 2
iii. Circulation Section: This segment gives reports to the individuals and clients
of library for home perusing just as perusing in the library. The archives are
organized on the racks in stacks according to the Dewey Decimal Classification
Scheme.
iv. Periodical Section: To acquire, keep up and orchestrate periodicals
administrations to library individuals. Periodical area furnishes reference
administration as for the necessity of the peruser. Reference area is connected to
periodical segment for accommodation of the Library clients.
v. Databases: Databases like OPAC, CAB-CD ROM abstracting databases,
DELNET online Network Service and so on are accessible for the library
individuals.
vi. Reprographic Section: This Section has two programmed plain paper copiers
and a copying machine through which the administrations of photocopy are given to
the perusers.
pg. 5

vii. Binding Section: This segment is working for restricting work of the harmed
books. Back Volumes and different reports of this Library. The required restricting
apparatus is accessible in this area.
Library the board is a sub-control of institutional administration that spotlights on
explicit issues looked by libraries and library the board experts. Library the
executives envelops typical administration errands just as scholarly opportunity,
against control, and gathering pledges undertakings. Issues looked in library the
board habitually cover those looked in the executives of non-benefit
organizations(Sharma et al.,2005).Library Management System is an application that
pictures library framework which could be commonly little or medium in size. It is
utilized by the bookkeeper to completely deal with the library by the uprightness of
utilizing an automated framework where he/she can record different exchanges like
issue of books, return of books, expansion of new books, expansion of new
understudies and so forth. (Ashutosh and Ashish., 2011). 3 Books and client upkeep
modules are additionally incorporated into this framework which would monitor the
clients utilizing the library and furthermore a point by point portrayal about the
books a library contains. With this automated framework there will be no loss of
book record or part record which by and large happens when a non-electronic
framework is utilized. Moreover, report module is likewise incorporated into Library
Management System (Anon, n.d.). On the off chance that client's position is
administrator, the client can produce various types of reports like arrangements of
clients enrolled, rundown of books, issue and return reports. Every one of these
modules can assist administrator with managing the library with more
accommodation and in a progressively proficient manner when contrasted with
library frameworks which are not automated. Under review as permitted by the
pg. 6
books. Back Volumes and different reports of this Library. The required restricting
apparatus is accessible in this area.
Library the board is a sub-control of institutional administration that spotlights on
explicit issues looked by libraries and library the board experts. Library the
executives envelops typical administration errands just as scholarly opportunity,
against control, and gathering pledges undertakings. Issues looked in library the
board habitually cover those looked in the executives of non-benefit
organizations(Sharma et al.,2005).Library Management System is an application that
pictures library framework which could be commonly little or medium in size. It is
utilized by the bookkeeper to completely deal with the library by the uprightness of
utilizing an automated framework where he/she can record different exchanges like
issue of books, return of books, expansion of new books, expansion of new
understudies and so forth. (Ashutosh and Ashish., 2011). 3 Books and client upkeep
modules are additionally incorporated into this framework which would monitor the
clients utilizing the library and furthermore a point by point portrayal about the
books a library contains. With this automated framework there will be no loss of
book record or part record which by and large happens when a non-electronic
framework is utilized. Moreover, report module is likewise incorporated into Library
Management System (Anon, n.d.). On the off chance that client's position is
administrator, the client can produce various types of reports like arrangements of
clients enrolled, rundown of books, issue and return reports. Every one of these
modules can assist administrator with managing the library with more
accommodation and in a progressively proficient manner when contrasted with
library frameworks which are not automated. Under review as permitted by the
pg. 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

literature research, another system for the libraries is the capital software which is
able vital and important in the overall management of the library items. The system
has the following main advantages which includes the ability to increase the staff
available support especially in modernized library facilities, the system has provided
efficiency , it is also easy and most time effective as it saves time by improving the
experience of the user. the management system fro the library under there normal
circumstance, contains the relational database, the graphical user interface also
known as the GUI in its abbreviation format, and the administrator platform. In
most cases for the library systems which are integrated, they have software functions
which are separate and categorized into the programs that are discrete called the
modules, in this, each module is integrated using a unified user interface. This
framework will be created and intended to enable administrator to record each book
exchange to decrease and kill issue of loss of books and documents in the library.
1.1.1 Existing Problem
The main problem which is existing in the current system is the possibility of
having a smooth check in and check out of book by the borrowers and its general
management when the system is down due to network connection. The current
system is networked system which employs the use of internet in processing details
in the library. Sometime network connectivity can be down in such a way that the
system is not in a position to continue processing the check in and check out of
book or its very slow hence making it very difficult to serve the large number of
borrowers available in the facility. This forced the library management to embark
on the manual way of information recording which is time wasting and tedious. A
lot of time is taken in borrowing books or returning the books which have been
pg. 7
able vital and important in the overall management of the library items. The system
has the following main advantages which includes the ability to increase the staff
available support especially in modernized library facilities, the system has provided
efficiency , it is also easy and most time effective as it saves time by improving the
experience of the user. the management system fro the library under there normal
circumstance, contains the relational database, the graphical user interface also
known as the GUI in its abbreviation format, and the administrator platform. In
most cases for the library systems which are integrated, they have software functions
which are separate and categorized into the programs that are discrete called the
modules, in this, each module is integrated using a unified user interface. This
framework will be created and intended to enable administrator to record each book
exchange to decrease and kill issue of loss of books and documents in the library.
1.1.1 Existing Problem
The main problem which is existing in the current system is the possibility of
having a smooth check in and check out of book by the borrowers and its general
management when the system is down due to network connection. The current
system is networked system which employs the use of internet in processing details
in the library. Sometime network connectivity can be down in such a way that the
system is not in a position to continue processing the check in and check out of
book or its very slow hence making it very difficult to serve the large number of
borrowers available in the facility. This forced the library management to embark
on the manual way of information recording which is time wasting and tedious. A
lot of time is taken in borrowing books or returning the books which have been
pg. 7

borrowed as well as searching the member details to confirm the number of booms
which has been borrowed by the member of the library. This normally happens
when the system network connection is down which in turn makes the whole
process very slow and tedious. Searching process might take a lot of time on one
single member hence making is very difficult to serve large number of people
making returns and borrowing books from the library. This is because the librarian
has to wait for network connection to regain its connection strength so that they
can be able to operate the system smoothly hence affecting the whole process of
service delivery. At most of the time, the librarian could opt for manual method of
data recording and management especially when the system is down. The library
staff could be forced to write down the member who have borrowed books and
those who have returned the books in separate sheets, then when the network
regains its strength, then they will be able to enter the data into the system at a later
time, This means that they have to spend extra time working in the library to make
sure that that data has been posted and updated so that the book can be marked as
borrowed or vacancy by the system. This whole process wastes a lot of time and its
also very tiresome to the staff which in turn affects service delivery as well as the
general process of library management.
1.1.2 Situation
By using the current system, it has made the librarian taking a lot of time clearing a
single person who has returned or borrowed a book. The current situation in the
library is not complete and technologically stable as the work done when the
system is down is very hence and slow which is contrary to any technology put in
place whose aim is always to reduce time wasted as well as making work more
pg. 8
which has been borrowed by the member of the library. This normally happens
when the system network connection is down which in turn makes the whole
process very slow and tedious. Searching process might take a lot of time on one
single member hence making is very difficult to serve large number of people
making returns and borrowing books from the library. This is because the librarian
has to wait for network connection to regain its connection strength so that they
can be able to operate the system smoothly hence affecting the whole process of
service delivery. At most of the time, the librarian could opt for manual method of
data recording and management especially when the system is down. The library
staff could be forced to write down the member who have borrowed books and
those who have returned the books in separate sheets, then when the network
regains its strength, then they will be able to enter the data into the system at a later
time, This means that they have to spend extra time working in the library to make
sure that that data has been posted and updated so that the book can be marked as
borrowed or vacancy by the system. This whole process wastes a lot of time and its
also very tiresome to the staff which in turn affects service delivery as well as the
general process of library management.
1.1.2 Situation
By using the current system, it has made the librarian taking a lot of time clearing a
single person who has returned or borrowed a book. The current situation in the
library is not complete and technologically stable as the work done when the
system is down is very hence and slow which is contrary to any technology put in
place whose aim is always to reduce time wasted as well as making work more
pg. 8

easy. It is very much difficult to operate under the current situation as paper work
is sometimes involves especially in the late hours when the library is almost being
closed and members are almost checking out yet the system is down due to
network unavailability. Network is always propagated rom its central place, there
are so many issues which might cause network availability to be affected, this
includes power blackout as network propagation machines like routers and
switches uses electricity in their general operation. Too many users can also cause
network bandwidth being affected hence affecting the speed of the upload and
download in a network. This whole situation is problematic as it stands till there is
a proper way of curbing it, and hence the main reason as to why a mobile based
library circulation system has been proposed in order to curb the current stalemate.
1.2 Motivation
Trying to check on how the proposed system will be able to positively impact the
whole institution in terms of saving time, reducing work load of writing data in a piece
of paper so that data can be entered at a later time when the strength has been regained
for smooth operation of the system as well as efficiency when it comes to service
delivery, implementing the system will be able to completely solve the stalemate
which is being witnessed in the library management system of book management. The
system proposed is an android system, this means that the system is portable and can
be operated at hand held at any location within the library. Besides that, the application
is locally hosted, it doesn’t need the availability of the network connection for its
general operation hence checking out and checking in of books and scanning process
will be instant hence saving a lot of time. The application will also be able to
synchronize data recorded once network connection in the main system has been
pg. 9
is sometimes involves especially in the late hours when the library is almost being
closed and members are almost checking out yet the system is down due to
network unavailability. Network is always propagated rom its central place, there
are so many issues which might cause network availability to be affected, this
includes power blackout as network propagation machines like routers and
switches uses electricity in their general operation. Too many users can also cause
network bandwidth being affected hence affecting the speed of the upload and
download in a network. This whole situation is problematic as it stands till there is
a proper way of curbing it, and hence the main reason as to why a mobile based
library circulation system has been proposed in order to curb the current stalemate.
1.2 Motivation
Trying to check on how the proposed system will be able to positively impact the
whole institution in terms of saving time, reducing work load of writing data in a piece
of paper so that data can be entered at a later time when the strength has been regained
for smooth operation of the system as well as efficiency when it comes to service
delivery, implementing the system will be able to completely solve the stalemate
which is being witnessed in the library management system of book management. The
system proposed is an android system, this means that the system is portable and can
be operated at hand held at any location within the library. Besides that, the application
is locally hosted, it doesn’t need the availability of the network connection for its
general operation hence checking out and checking in of books and scanning process
will be instant hence saving a lot of time. The application will also be able to
synchronize data recorded once network connection in the main system has been
pg. 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

regained. This whole positivity’s will positively impact the operation of the library to
its efficiency standards.
1.3 Project Aim
The major aim of the project is to design, develop and implement an offline mobile based
library management application which is effective and efficient enough in handling library
transactions when the main system is down.
1.4 Project Objectives
The objectives of this projects includes the following:
i. Designing an offline based android library management application which will be
able to evacuate all the problems which are being faced in the library when the
current system is down due to network strength.
ii. Developing the designed system using android studio IDE with java programming
language as the core language.
iii. Integrating the application with SQLite database for its offline use.
iv. Implementing the system in android studio.
v. Evaluation and testing of the system in terms of its general performance and
efficiency in accordance with the requirements set.
vi. Synchronization of the recorded data into the main system when the network
strength has been regained.
vii. Analysing MARC 21 format data file and checking if catalogues which have been
stored in the file can be converted to SQLite fit, and displayed in the android
application.
pg. 10
its efficiency standards.
1.3 Project Aim
The major aim of the project is to design, develop and implement an offline mobile based
library management application which is effective and efficient enough in handling library
transactions when the main system is down.
1.4 Project Objectives
The objectives of this projects includes the following:
i. Designing an offline based android library management application which will be
able to evacuate all the problems which are being faced in the library when the
current system is down due to network strength.
ii. Developing the designed system using android studio IDE with java programming
language as the core language.
iii. Integrating the application with SQLite database for its offline use.
iv. Implementing the system in android studio.
v. Evaluation and testing of the system in terms of its general performance and
efficiency in accordance with the requirements set.
vi. Synchronization of the recorded data into the main system when the network
strength has been regained.
vii. Analysing MARC 21 format data file and checking if catalogues which have been
stored in the file can be converted to SQLite fit, and displayed in the android
application.
pg. 10
viii. Reviewing other literatures and checking if the developed application can be
improved in the future in terms of service delivery as well as efficiency.
pg. 11
improved in the future in terms of service delivery as well as efficiency.
pg. 11

CHAPTER TWO
2. REQUIREMENT ANALYSIS
2.1 Introduction
This is the second chapter of the report which entirely gives a discussion on the requirement
analysis of the report. Under this particular chapter, the stakeholders of the system will be
highlighted, the system interface will also be provided in the rough copy, The interface of
the user will also be described as well as the characteristics of the system as far as
objectives’ are concerned, scope of the system, functional and the non-functional
requirements will also be described in details. In order to develop an android library
circulation system, the it becomes necessary to develop an analysis of the requirement.
There are 3 main stages under which design and development of the new system has to take
place. This stages includes gathering of data, design development and implementation stage
and finally testing and deployment stage. Different tactics are employed within the 3 stages
named above in order to come up with the very best results in terms of a system which has
the ability of maintaining a high level of accessibility or usability.
2.2 Stakeholders
These people who support the implementation of the system directly as they are taking part
to making sure that the system has been design and developed. As far as library circulation
android application is concerned the following tare the stakeholders in this particular system
development and implementation.
a. Library management: this are the owners of the system once it is done. They are also the
owners of the library facility where the system is set to operate from. They play a very
pg. 12
2. REQUIREMENT ANALYSIS
2.1 Introduction
This is the second chapter of the report which entirely gives a discussion on the requirement
analysis of the report. Under this particular chapter, the stakeholders of the system will be
highlighted, the system interface will also be provided in the rough copy, The interface of
the user will also be described as well as the characteristics of the system as far as
objectives’ are concerned, scope of the system, functional and the non-functional
requirements will also be described in details. In order to develop an android library
circulation system, the it becomes necessary to develop an analysis of the requirement.
There are 3 main stages under which design and development of the new system has to take
place. This stages includes gathering of data, design development and implementation stage
and finally testing and deployment stage. Different tactics are employed within the 3 stages
named above in order to come up with the very best results in terms of a system which has
the ability of maintaining a high level of accessibility or usability.
2.2 Stakeholders
These people who support the implementation of the system directly as they are taking part
to making sure that the system has been design and developed. As far as library circulation
android application is concerned the following tare the stakeholders in this particular system
development and implementation.
a. Library management: this are the owners of the system once it is done. They are also the
owners of the library facility where the system is set to operate from. They play a very
pg. 12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

central role in making sure that the system has been designed and implemented and also
deployed since they are the only financiers of the system, they also give an open space
for the developer to get information on how the system has to be developed.
b. Library staff: This are the employees working in the library. They are again one of the
main stakeholders in making the system successfully implemented according to the
existing gap. For this reason, they are the one who gives information of how exactly the
system has to operate, the gap which is there in the operation of the current system and
how the closure of the gap will help in creating a good environment for their own
operation as well as improving the service delivery for the members who depend on the
library facility.
c. Android library circulation system developer: The developer is the implementer of the
system, the developer is also important as he is the one who is responsible in making the
plan into a reality by developing a system which will be able to serve and help in
opening up a new chapter in the overall operation of the system.
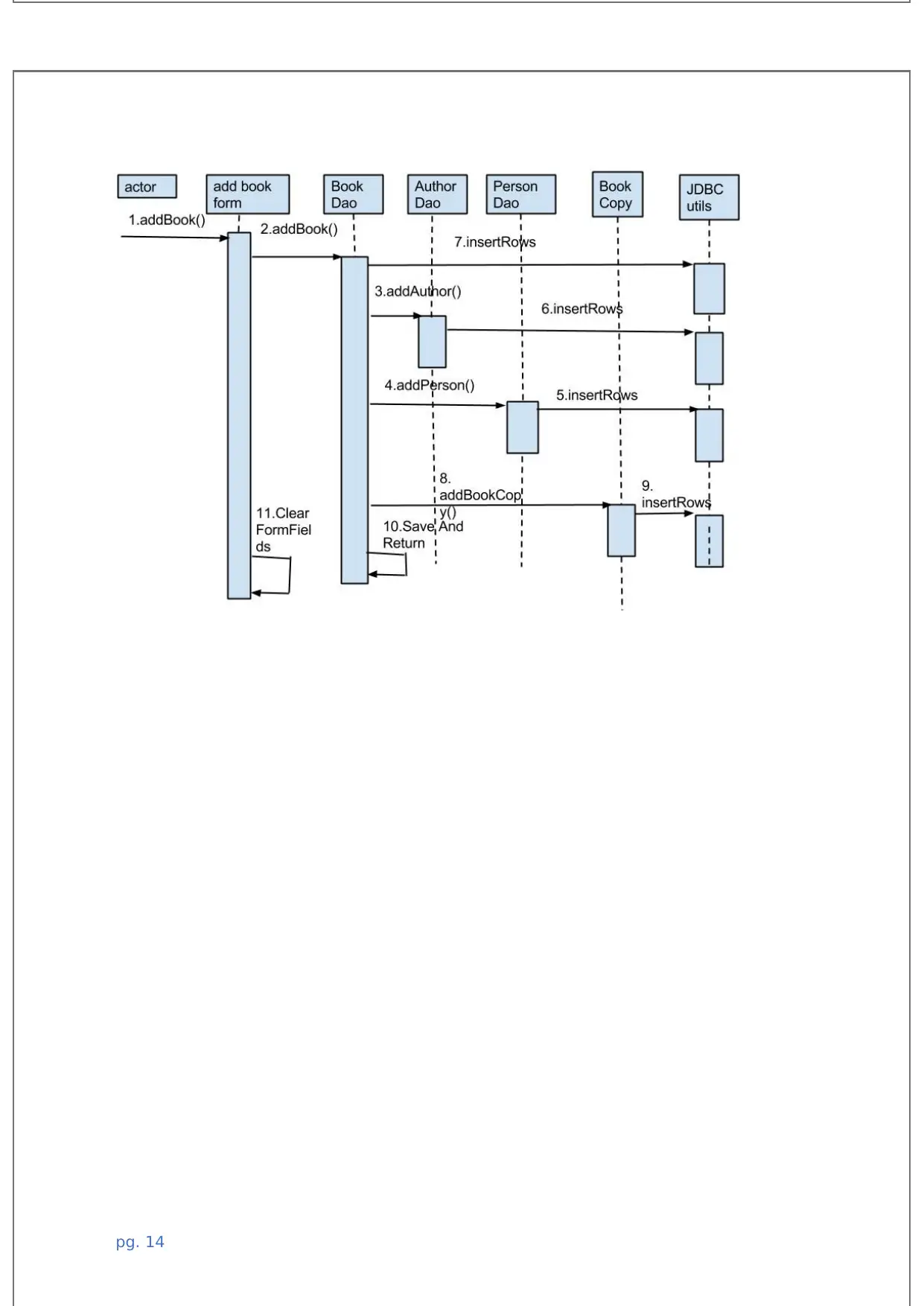
2.3 System Interface
The system interface is the boundary which shows how the system communicates, how the
interfaces communicates with each other. The system interface is described using the
sequence diagrams as below
pg. 13
deployed since they are the only financiers of the system, they also give an open space
for the developer to get information on how the system has to be developed.
b. Library staff: This are the employees working in the library. They are again one of the
main stakeholders in making the system successfully implemented according to the
existing gap. For this reason, they are the one who gives information of how exactly the
system has to operate, the gap which is there in the operation of the current system and
how the closure of the gap will help in creating a good environment for their own
operation as well as improving the service delivery for the members who depend on the
library facility.
c. Android library circulation system developer: The developer is the implementer of the
system, the developer is also important as he is the one who is responsible in making the
plan into a reality by developing a system which will be able to serve and help in
opening up a new chapter in the overall operation of the system.
2.3 System Interface
The system interface is the boundary which shows how the system communicates, how the
interfaces communicates with each other. The system interface is described using the
sequence diagrams as below
pg. 13
pg. 14
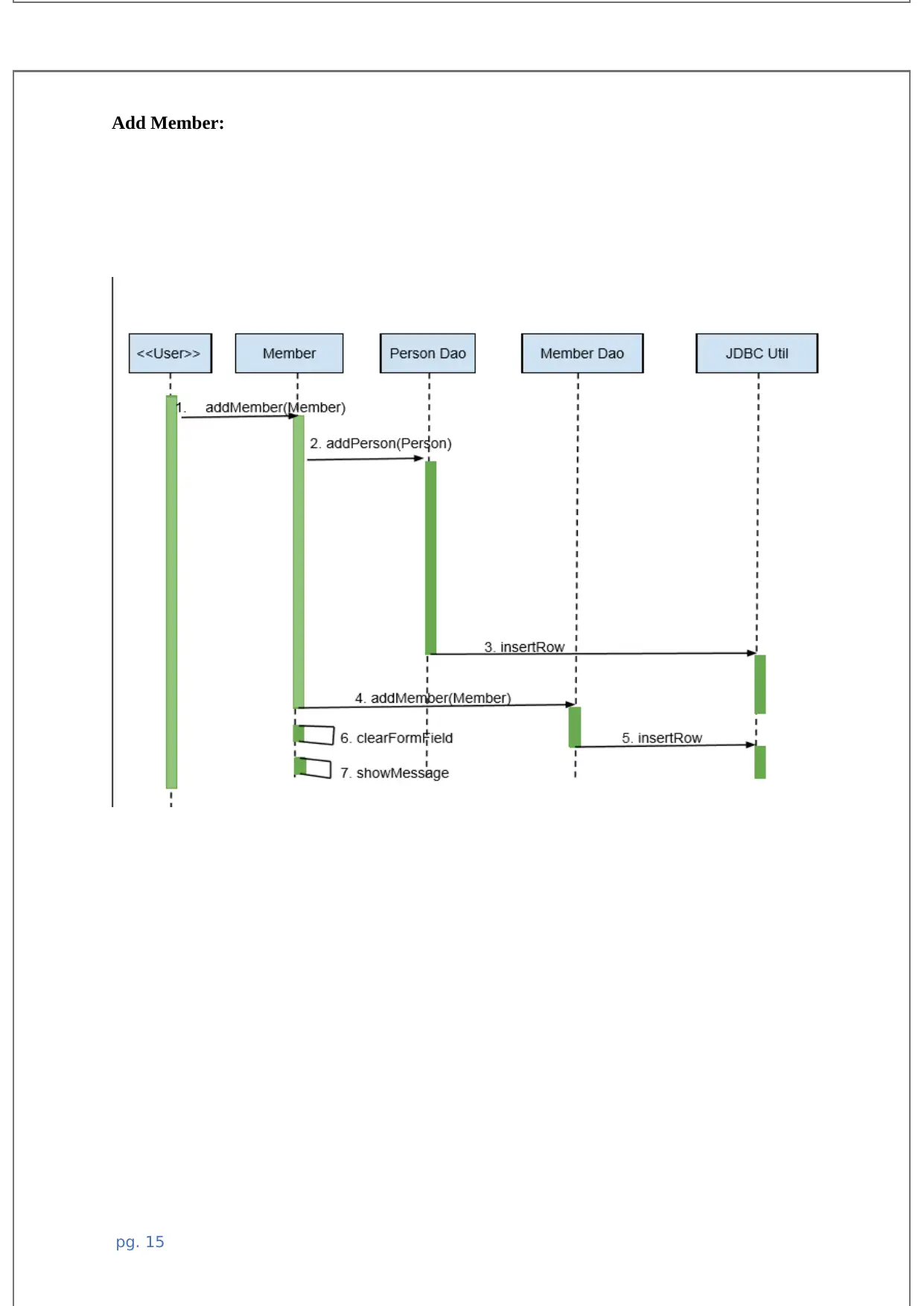
Add Member:
pg. 15
pg. 15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
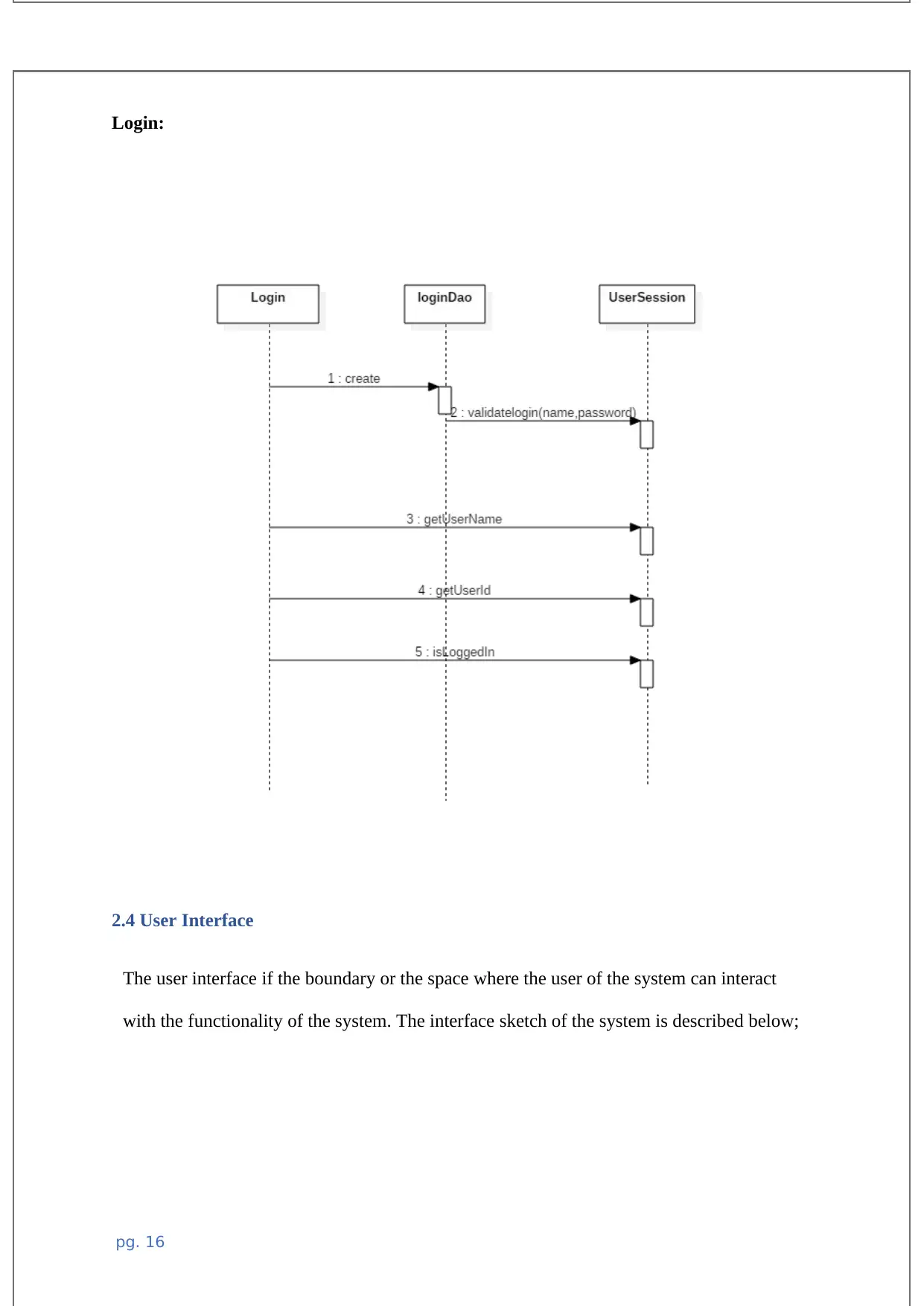
Login:
2.4 User Interface
The user interface if the boundary or the space where the user of the system can interact
with the functionality of the system. The interface sketch of the system is described below;
pg. 16
2.4 User Interface
The user interface if the boundary or the space where the user of the system can interact
with the functionality of the system. The interface sketch of the system is described below;
pg. 16

The above user interface sketch is the is where the users are signing in to the system. The
user has to enter login credentials which includes the user ID and the password which is
encrypted by MD5 technology of security data hiding.
In this interface, books barcodes are scanned in order to check all the details of the book
including the book details, if it has already been borrowed or if its being returned. Checking
in and checking out of the books are done by the use of this unique technology.
pg. 17
user has to enter login credentials which includes the user ID and the password which is
encrypted by MD5 technology of security data hiding.
In this interface, books barcodes are scanned in order to check all the details of the book
including the book details, if it has already been borrowed or if its being returned. Checking
in and checking out of the books are done by the use of this unique technology.
pg. 17
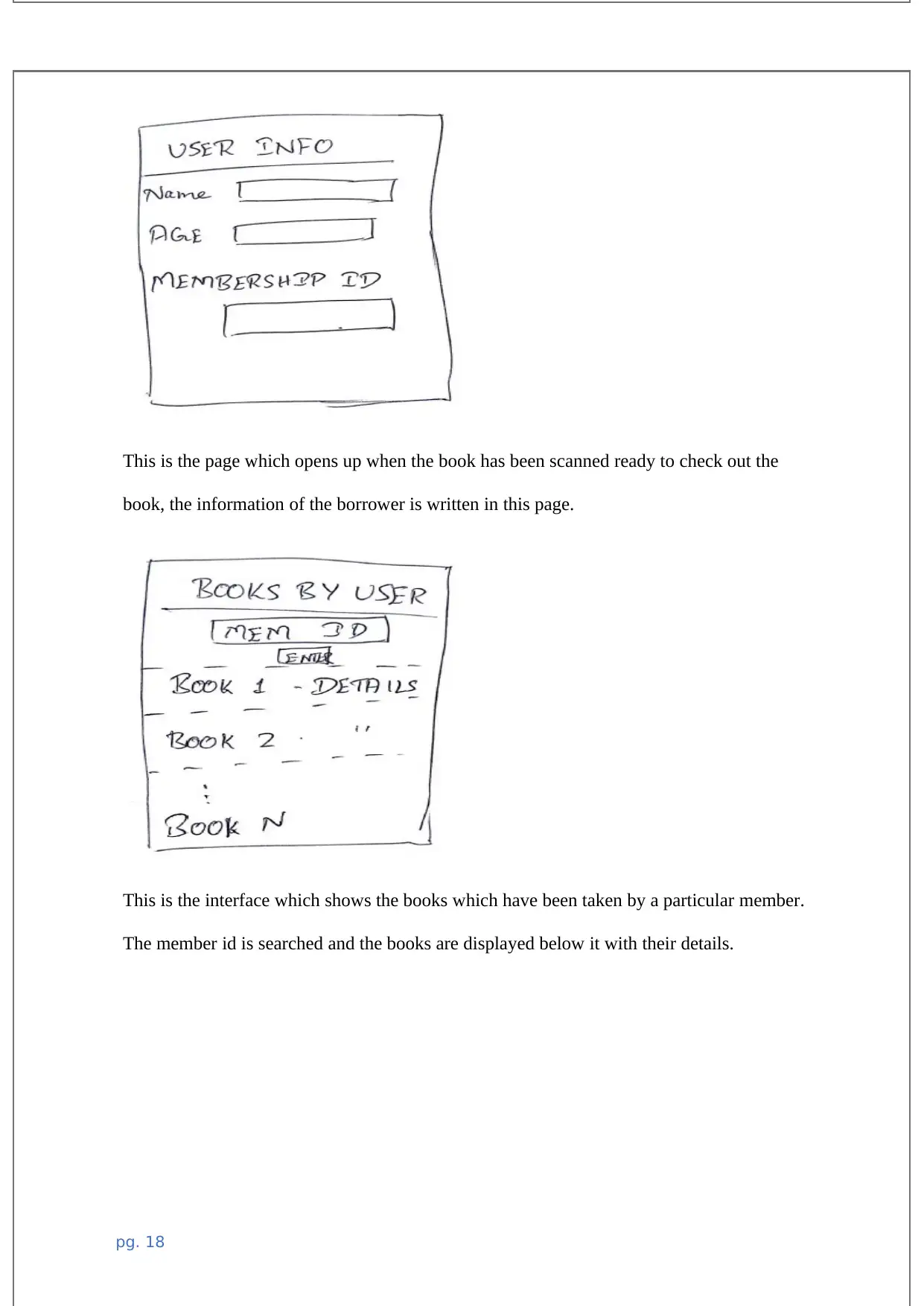
This is the page which opens up when the book has been scanned ready to check out the
book, the information of the borrower is written in this page.
This is the interface which shows the books which have been taken by a particular member.
The member id is searched and the books are displayed below it with their details.
pg. 18
book, the information of the borrower is written in this page.
This is the interface which shows the books which have been taken by a particular member.
The member id is searched and the books are displayed below it with their details.
pg. 18
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This interface is where the book is scanned and checked if its already taken or its available
for members to borrow, the status of the book is displayed in this interface when the book
has been scanned using its barcode attached.
2.5 Characteristics
The characteristics of the system developed involves all the features that the user who are
the staff of the library will be able to interact with in their course of operation after
deployment. The following therefore are the core features of the mobile based library
circulation system developed.
a. User sign up capability
b. User and admin sign in.
c. Barcode scanning feature
d. Search box feature for members and book details
e. Book check in and check out
f. Admin panel for settings and controls
2.6 Scope of the System
pg. 19
for members to borrow, the status of the book is displayed in this interface when the book
has been scanned using its barcode attached.
2.5 Characteristics
The characteristics of the system developed involves all the features that the user who are
the staff of the library will be able to interact with in their course of operation after
deployment. The following therefore are the core features of the mobile based library
circulation system developed.
a. User sign up capability
b. User and admin sign in.
c. Barcode scanning feature
d. Search box feature for members and book details
e. Book check in and check out
f. Admin panel for settings and controls
2.6 Scope of the System
pg. 19

This is worthy noting that the system developed is strictly developed for the library
circulation purposes when the current system is down due to network reasons. Therefore
this application is not the main application to be used by the library since it is offline and
data stored are not networked. The system also only does book check in and book check out
only and its limited to that only.
2.7 Functional Requirements
This gives a description of what the system is supposed to perform. The system develops is
meant to do the following;
a) The user who is an employee of the library can sign up to the system
b) The user of the system is able to sign in to the system
c) The application shows the person signed in on the top of the interface.
d) The user is able to scan the book in order to check the person who has borrowed the
book.
e) The user is able to search for the member and be able to check the total number of the
books borrowed by the member.
f) The system is able to check in and check out books.
g) Book details can be searched in the system.
h) The system has the admin panel where all settings are set before the user is able to use
the system.
2.8 Non-Functional Requirements
This are the constraints on how the application was supposed to do. These includes the
following;
pg. 20
circulation purposes when the current system is down due to network reasons. Therefore
this application is not the main application to be used by the library since it is offline and
data stored are not networked. The system also only does book check in and book check out
only and its limited to that only.
2.7 Functional Requirements
This gives a description of what the system is supposed to perform. The system develops is
meant to do the following;
a) The user who is an employee of the library can sign up to the system
b) The user of the system is able to sign in to the system
c) The application shows the person signed in on the top of the interface.
d) The user is able to scan the book in order to check the person who has borrowed the
book.
e) The user is able to search for the member and be able to check the total number of the
books borrowed by the member.
f) The system is able to check in and check out books.
g) Book details can be searched in the system.
h) The system has the admin panel where all settings are set before the user is able to use
the system.
2.8 Non-Functional Requirements
This are the constraints on how the application was supposed to do. These includes the
following;
pg. 20

a) The system has an effective searching ability for the members and the books.
b) The application is very reliable in the process of providing the whole functionalities
which are expected.
c) The application is very stable and breakdowns have been limited.
d) The application is easy to use.
e) The system is secure and free from unauthorized access and use.
pg. 21
b) The application is very reliable in the process of providing the whole functionalities
which are expected.
c) The application is very stable and breakdowns have been limited.
d) The application is easy to use.
e) The system is secure and free from unauthorized access and use.
pg. 21
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CHAPTER THREE
3. RESEARCH/ LITERATURE REVIEW
3.1 Introduction
This is the third chapter of the report. In this chapter therefore the review of the writing
done by other researches as far as library management system is concerned will be
discussed in details. Marc21 File format system will also be discussed as it’s the file system
which contains cataloguing data. The process under which scanning of barcode by use of
the barcode scanner will also be discussed in this particular chapter. Literature review is a
collection of past researches which were made by other experts who were researching in the
field of interest. Through the literature review, one is able to make efficient comparing
between most the extend of research carried out and the researches of other people.
3.2 Library System
3.2.1 Introduction
In most of the cases around the world, a library is considered as the cerebrum of each and
every institution around the world, it is very understood that most of the organisations knows
the basic important and functions of a library in terms of societal growth as well as economic
growth. This is a centre where researches are done and knowledge is expanded. Though the
library, one is able to get the ancient artefacts and writings which can help in creating the
most wonderful research paper in order to improve the knowledge and the economy of the
world. The management system which is called the library management system in
accordance to the definition which is set aside and proved by (Adamson et al., 2008) referred
to it as an enterprise system of planning of the libraries, the system is particularly utilized in
tracking the items which are stored in the library, the number of orders for leasing items
pg. 22
3. RESEARCH/ LITERATURE REVIEW
3.1 Introduction
This is the third chapter of the report. In this chapter therefore the review of the writing
done by other researches as far as library management system is concerned will be
discussed in details. Marc21 File format system will also be discussed as it’s the file system
which contains cataloguing data. The process under which scanning of barcode by use of
the barcode scanner will also be discussed in this particular chapter. Literature review is a
collection of past researches which were made by other experts who were researching in the
field of interest. Through the literature review, one is able to make efficient comparing
between most the extend of research carried out and the researches of other people.
3.2 Library System
3.2.1 Introduction
In most of the cases around the world, a library is considered as the cerebrum of each and
every institution around the world, it is very understood that most of the organisations knows
the basic important and functions of a library in terms of societal growth as well as economic
growth. This is a centre where researches are done and knowledge is expanded. Though the
library, one is able to get the ancient artefacts and writings which can help in creating the
most wonderful research paper in order to improve the knowledge and the economy of the
world. The management system which is called the library management system in
accordance to the definition which is set aside and proved by (Adamson et al., 2008) referred
to it as an enterprise system of planning of the libraries, the system is particularly utilized in
tracking the items which are stored in the library, the number of orders for leasing items
pg. 22

made, the returns which have been made as well as the billing system for the facility at large.
Also in accordance with another researcher by the name (Ashutosh and Ashish., 2012), the
system for the library was defines as the software which is used for management and
monitoring of the transactions which are taking place in the library. The system is utilized in
supporting the general functions of the library as far as the items of the library are concerned.
some of the functionalities includes the acquisition of the items, cataloguing of the items in
the library, and circulation which is taking place in the library section among other sections.
Before computers were invented across the world, there were different methods which were
being used in the management of records in a library which was being called records keeping.
The records were being kept on a shelve in a library whereby each and every shelve section
is named according to the alphabetical numbers and letters with each section of the named
shelve having books of a particular categories (Ashutosh and Ashish., 2012). The books
categories are then written in the book for confirmation purposes during the time of
borrowing and returning. After the computers were invented and made available for public
use, around seven researchers carried out proper research on the best ways under which items
in the library can be able to be organized in a more simplest way possible to make work
easier when issuing and receiving borrowed items from the library. This particular project is
also all about the same approaches of management of library facility. The very first library
management system which was reviewed was the KOHA system for library and information
management. KOHA was implemented in the year 1999 after several years of research and
modernization. This particular approach of library atomization has been adopted in so many
library facility across the whole world. Though its seen that each and every facility adds more
feature to the very first approach hence making the system more and more acceptable across
the world (Ashutosh and Ashish., 2012). The KOHA system was also released in 2005 for the
latest version 3.0 of that time which was later integrated with the more powerful engine
pg. 23
Also in accordance with another researcher by the name (Ashutosh and Ashish., 2012), the
system for the library was defines as the software which is used for management and
monitoring of the transactions which are taking place in the library. The system is utilized in
supporting the general functions of the library as far as the items of the library are concerned.
some of the functionalities includes the acquisition of the items, cataloguing of the items in
the library, and circulation which is taking place in the library section among other sections.
Before computers were invented across the world, there were different methods which were
being used in the management of records in a library which was being called records keeping.
The records were being kept on a shelve in a library whereby each and every shelve section
is named according to the alphabetical numbers and letters with each section of the named
shelve having books of a particular categories (Ashutosh and Ashish., 2012). The books
categories are then written in the book for confirmation purposes during the time of
borrowing and returning. After the computers were invented and made available for public
use, around seven researchers carried out proper research on the best ways under which items
in the library can be able to be organized in a more simplest way possible to make work
easier when issuing and receiving borrowed items from the library. This particular project is
also all about the same approaches of management of library facility. The very first library
management system which was reviewed was the KOHA system for library and information
management. KOHA was implemented in the year 1999 after several years of research and
modernization. This particular approach of library atomization has been adopted in so many
library facility across the whole world. Though its seen that each and every facility adds more
feature to the very first approach hence making the system more and more acceptable across
the world (Ashutosh and Ashish., 2012). The KOHA system was also released in 2005 for the
latest version 3.0 of that time which was later integrated with the more powerful engine
pg. 23

called the zebra engine for indexing. This made KPOHA to become for scalable, viable and
stable solution for the library facilities across all nations around the world. Which the
existence of the most recent features in the KOHA system, KOHA is now the most stale,
selling and functional open source library management integrated system till now in the
market hence making the centre of our research today (Anon, n.d.). The main limitation that
this system is having is that the system is web based hosted in the online servers, this has
made the system to be more vulnerable to hackers and cyber threats, hackers can hack the
system by accessing the database of the system and making some changes on the data which
has been saved by the customers hence its security is not guaranteed as such. Under review as
permitted by the literature research, another system for the libraries is the capital software
which is able vital and important in the overall management of the library items. The system
has the following main advantages which includes the ability to increase the staff available
support especially in modernized library facilities, the system has provided efficiency (Anon,
n.d.), it is also easy and most time effective as it saves time by improving the experience of
the user. the management system fro the library under there normal circumstance, contains
the relational database, the graphical user interface also known as the GUI in its abbreviation
format, and the administrator platform. In most cases for the library systems which are
integrated, they have software functions which are separate and categorized into the programs
that are discrete called the modules, in this, each module is integrated using a unified user
interface.
3.2.2 MARC21 File Format
The MARC alias Machine Readable Cataloguing is a set digital formats standards which
are used for the purpose describing the items which have been catalogued in the library,
pg. 24
stable solution for the library facilities across all nations around the world. Which the
existence of the most recent features in the KOHA system, KOHA is now the most stale,
selling and functional open source library management integrated system till now in the
market hence making the centre of our research today (Anon, n.d.). The main limitation that
this system is having is that the system is web based hosted in the online servers, this has
made the system to be more vulnerable to hackers and cyber threats, hackers can hack the
system by accessing the database of the system and making some changes on the data which
has been saved by the customers hence its security is not guaranteed as such. Under review as
permitted by the literature research, another system for the libraries is the capital software
which is able vital and important in the overall management of the library items. The system
has the following main advantages which includes the ability to increase the staff available
support especially in modernized library facilities, the system has provided efficiency (Anon,
n.d.), it is also easy and most time effective as it saves time by improving the experience of
the user. the management system fro the library under there normal circumstance, contains
the relational database, the graphical user interface also known as the GUI in its abbreviation
format, and the administrator platform. In most cases for the library systems which are
integrated, they have software functions which are separate and categorized into the programs
that are discrete called the modules, in this, each module is integrated using a unified user
interface.
3.2.2 MARC21 File Format
The MARC alias Machine Readable Cataloguing is a set digital formats standards which
are used for the purpose describing the items which have been catalogued in the library,
pg. 24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

this includes books and other items. As introduced in the Library of Congress by Henriette
Avram who is an American Computer Scientist, he developed this MARC standard in the
year 1963 with the purpose of create a record which could be easily read using a computer
and shared later on among the computers in the libraries. This was improved and
popularized in the year 1971 when it become an international standard of cataloguing.
MARC21 was then introduced in 1999 due to harmonization of the United states and the
Canadian MRAC file formatting as well as UNIMARC which was being used in Europe
(Sharma et al.,2005).
Field designations
Each field in a MARC record gives specific data about the thing the record is depicting,
for example, the creator, title, distributer, date, language, media type, and so on. Since it
was first created when figuring force was low, and space valuable, MARC utilizes a basic
three-digit numeric code in order to distinguish each field in the record. MARC
characterizes field 100 as the essential creator of a work, field 245 as the title and field 260
as the distributer, for instance.
Fields over 008 are additionally isolated into subfields utilizing a solitary letter or number
assignment. The 260, for instance, is additionally isolated into subfield "a" for the spot of
distribution, "b" for the name of the distributer, and "c" for the date of production.
The objective of substance assignment is to recognize and describe the information
components that involve a MARC record with adequate exactness to help control of the
information for an assortment of capacities (Sharma et al.,2005).
MARC content assignment is intended to help works that include:
pg. 25
Avram who is an American Computer Scientist, he developed this MARC standard in the
year 1963 with the purpose of create a record which could be easily read using a computer
and shared later on among the computers in the libraries. This was improved and
popularized in the year 1971 when it become an international standard of cataloguing.
MARC21 was then introduced in 1999 due to harmonization of the United states and the
Canadian MRAC file formatting as well as UNIMARC which was being used in Europe
(Sharma et al.,2005).
Field designations
Each field in a MARC record gives specific data about the thing the record is depicting,
for example, the creator, title, distributer, date, language, media type, and so on. Since it
was first created when figuring force was low, and space valuable, MARC utilizes a basic
three-digit numeric code in order to distinguish each field in the record. MARC
characterizes field 100 as the essential creator of a work, field 245 as the title and field 260
as the distributer, for instance.
Fields over 008 are additionally isolated into subfields utilizing a solitary letter or number
assignment. The 260, for instance, is additionally isolated into subfield "a" for the spot of
distribution, "b" for the name of the distributer, and "c" for the date of production.
The objective of substance assignment is to recognize and describe the information
components that involve a MARC record with adequate exactness to help control of the
information for an assortment of capacities (Sharma et al.,2005).
MARC content assignment is intended to help works that include:
pg. 25

Show - the designing of information for screen show, for imprinting on 3x5 cards or in
book indexes, for generation of COM lists, or for other visual introduction of the
information.
Data recovery - the ID, classification, and recovery of any recognizable information
component in a record.
A few fields serve numerous capacities. For instance, field 245 (Title Statement) serves
both as the bibliographic translation of the title and the announcement of obligation and as
a passage for the title.
The MARC 21 organizations accommodate show constants. A showcase steady is a term,
expression, or potentially dispersing or accentuation show that might be framework
produced under recommended conditions to make a visual introduction of information in a
record increasingly significant to a client. Such showcase constants are not conveyed in
the information, yet might be provided for presentation by the preparing framework. For
instance, subfield $x in Series Statement field 490 (and in some different fields) suggests
the presentation steady ISSN; additionally, the mix of label 780 (Preceding Entry) and
second pointer esteem 2 infers the showcase consistent Supersedes (Sharma et al.,2005).
The MARC 21 organizations help the arranging of information just to a restricted degree.
As a rule, arranging must be practiced through the utilization of outer calculations to the
information.
Record structure
MARC records are ordinarily put away and transmitted as twofold documents, as a rule
with a few MARC records connected together into a solitary document. MARC utilizes
pg. 26
book indexes, for generation of COM lists, or for other visual introduction of the
information.
Data recovery - the ID, classification, and recovery of any recognizable information
component in a record.
A few fields serve numerous capacities. For instance, field 245 (Title Statement) serves
both as the bibliographic translation of the title and the announcement of obligation and as
a passage for the title.
The MARC 21 organizations accommodate show constants. A showcase steady is a term,
expression, or potentially dispersing or accentuation show that might be framework
produced under recommended conditions to make a visual introduction of information in a
record increasingly significant to a client. Such showcase constants are not conveyed in
the information, yet might be provided for presentation by the preparing framework. For
instance, subfield $x in Series Statement field 490 (and in some different fields) suggests
the presentation steady ISSN; additionally, the mix of label 780 (Preceding Entry) and
second pointer esteem 2 infers the showcase consistent Supersedes (Sharma et al.,2005).
The MARC 21 organizations help the arranging of information just to a restricted degree.
As a rule, arranging must be practiced through the utilization of outer calculations to the
information.
Record structure
MARC records are ordinarily put away and transmitted as twofold documents, as a rule
with a few MARC records connected together into a solitary document. MARC utilizes
pg. 26

the ISO 2709 standard to characterize the structure of each record. This incorporates a
marker to demonstrate where each record starts and finishes, just as a lot of characters
toward the start of each record that give a catalog to finding the fields and subfields inside
the record.
In the year of 2002, the Library of Congress built up the MARCXML composition as an
elective record structure, permitting MARC records to be spoken to in XML; the fields
continue as before, yet those fields are communicated in the record in XML markup.
Libraries regularly uncover their records as MARCXML by means of a web
administration, frequently following the SRU or OAI-PMH principles (Sharma et
al.,2005).
A MARC record comprises of three primary areas: the pioneer, the registry, and the
variable fields.
The pioneer comprises of information components that contain coded values and are
recognized by relative character position. Information components in the pioneer
characterize parameters for preparing the record. The pioneer is fixed long (24 characters)
and happens toward the start of every MARC record.
The index contains the tag, beginning area, and length of each field inside the record.
Registry passages for variable control fields show up first, in climbing label request.
Sections for variable information fields pursue, masterminded in rising request as
indicated by the primary character of the tag. The request for the fields in the record does
not really relate to the request for catalog passages. Copy labels are recognized distinctly
by area of the individual fields inside the record. The length of the index passage is
characterized in the section map components in Leader/20-23. In the MARC 21 organizes,
pg. 27
marker to demonstrate where each record starts and finishes, just as a lot of characters
toward the start of each record that give a catalog to finding the fields and subfields inside
the record.
In the year of 2002, the Library of Congress built up the MARCXML composition as an
elective record structure, permitting MARC records to be spoken to in XML; the fields
continue as before, yet those fields are communicated in the record in XML markup.
Libraries regularly uncover their records as MARCXML by means of a web
administration, frequently following the SRU or OAI-PMH principles (Sharma et
al.,2005).
A MARC record comprises of three primary areas: the pioneer, the registry, and the
variable fields.
The pioneer comprises of information components that contain coded values and are
recognized by relative character position. Information components in the pioneer
characterize parameters for preparing the record. The pioneer is fixed long (24 characters)
and happens toward the start of every MARC record.
The index contains the tag, beginning area, and length of each field inside the record.
Registry passages for variable control fields show up first, in climbing label request.
Sections for variable information fields pursue, masterminded in rising request as
indicated by the primary character of the tag. The request for the fields in the record does
not really relate to the request for catalog passages. Copy labels are recognized distinctly
by area of the individual fields inside the record. The length of the index passage is
characterized in the section map components in Leader/20-23. In the MARC 21 organizes,
pg. 27
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

the length of a registry passage is 12 characters. The registry closes with a field eliminator
character (Sharma et al.,2005).
The information substance of a record is isolated into variable fields. The MARC 21
organizations recognize two kinds of variable fields: variable control fields and variable
information fields. Control and information fields are recognized uniquely by structure
(see areas 7 and 8 beneath). The term fixed fields is incidentally utilized in MARC 21
documentation, alluding either to control fields for the most part or to explicit coded-
information fields.
Content
MARC encodes data about a bibliographic thing, not about the substance of that thing; this
implies it is a metadata transmission standard, not a substance standard. The genuine
substance that a cataloger puts in every MARC field is normally administered and
characterized by models outside of MARC, with the exception of a bunch of fixed fields
characterized by the MARC gauges themselves. Asset Description and Access, for
instance, characterizes how the physical attributes of books and different things ought to
be communicated. The Library of Congress Subject Headings (LCSH) are a rundown of
approved subject terms used to depict the primary subject substance of the work. Other
listing guidelines and grouping timetables can likewise be utilized (Sharma et al.,2005).
3.2.3 Scanning Process
A standardized barcode scanner normally comprises of three distinct parts including the
enlightenment framework, the sensor, and the decoder.
pg. 28
character (Sharma et al.,2005).
The information substance of a record is isolated into variable fields. The MARC 21
organizations recognize two kinds of variable fields: variable control fields and variable
information fields. Control and information fields are recognized uniquely by structure
(see areas 7 and 8 beneath). The term fixed fields is incidentally utilized in MARC 21
documentation, alluding either to control fields for the most part or to explicit coded-
information fields.
Content
MARC encodes data about a bibliographic thing, not about the substance of that thing; this
implies it is a metadata transmission standard, not a substance standard. The genuine
substance that a cataloger puts in every MARC field is normally administered and
characterized by models outside of MARC, with the exception of a bunch of fixed fields
characterized by the MARC gauges themselves. Asset Description and Access, for
instance, characterizes how the physical attributes of books and different things ought to
be communicated. The Library of Congress Subject Headings (LCSH) are a rundown of
approved subject terms used to depict the primary subject substance of the work. Other
listing guidelines and grouping timetables can likewise be utilized (Sharma et al.,2005).
3.2.3 Scanning Process
A standardized barcode scanner normally comprises of three distinct parts including the
enlightenment framework, the sensor, and the decoder.
pg. 28

All in all, a standardized identification scanner "checks" the high contrast components of a
scanner tag by enlightening the code with a red light, which is then changed over into
coordinating content. All the more explicitly, the sensor in the standardized identification
scanner identifies the reflected light from the brightening framework (the red light) and
produces a simple sign that is sent to the decoder. The decoder translates that signal,
approves the standardized tag utilizing the check digit, and changes over it into content
(Sharma et al.,2005).
This changed over content is conveyed by the scanner to a PC programming framework
holding a database of the creator, cost, and amount of all items sold.
3.2.4 Conclusion
From the review of the literature done above, it is seen that library management system
has to have the most modern way of curbing downtime and network problems. The
literature has given the description of how the MARC21 was introduced into the system as
well as how cataloguing is done in using the MARC21 file format. This will therefore
enable the developer to be in position to know on the way under which the file can be
converted to SQLite for easy implementation using java android language of
programming. The scanning process by use of barcode reader and scanner is also checked
and described in order t help the developer of the application to have knowledge on how
the process of scanning happens and how it can be integrated into the application to ease
the work to be done in checking in and out of the members and books at large.
3.3 Software Development Technologies
3.3.1 Introduction
In the design and development of a mobile based android library circulation system, there
are several technologies which are employed in order to ensure that the design process to
pg. 29
scanner tag by enlightening the code with a red light, which is then changed over into
coordinating content. All the more explicitly, the sensor in the standardized identification
scanner identifies the reflected light from the brightening framework (the red light) and
produces a simple sign that is sent to the decoder. The decoder translates that signal,
approves the standardized tag utilizing the check digit, and changes over it into content
(Sharma et al.,2005).
This changed over content is conveyed by the scanner to a PC programming framework
holding a database of the creator, cost, and amount of all items sold.
3.2.4 Conclusion
From the review of the literature done above, it is seen that library management system
has to have the most modern way of curbing downtime and network problems. The
literature has given the description of how the MARC21 was introduced into the system as
well as how cataloguing is done in using the MARC21 file format. This will therefore
enable the developer to be in position to know on the way under which the file can be
converted to SQLite for easy implementation using java android language of
programming. The scanning process by use of barcode reader and scanner is also checked
and described in order t help the developer of the application to have knowledge on how
the process of scanning happens and how it can be integrated into the application to ease
the work to be done in checking in and out of the members and books at large.
3.3 Software Development Technologies
3.3.1 Introduction
In the design and development of a mobile based android library circulation system, there
are several technologies which are employed in order to ensure that the design process to
pg. 29

testing process has been successful. For this reason, the development of library circulation
system under prospective report made use of different technologies and languages. For
example, the application was integrated with barcode scanning technology which enable
the application to be able to detect the book with the person who was allocated the book.
Its details are scanned and detected.
3.3.2 Java
Java is an object oriented programming language, classed based and it is designed to have
the smallest number of dependencies as possible. Java programming language is capable
of facilitating development of web based systems, mobile based systems and desktop
application. In mobile based systems, the language can be used in the design and
development of application which runs on android devices. This development is made
possible using android studio IDE.
In java programming language, the source file is normally named after the public class
they have , with the suffix .java being appended for example barcode.java. by the use of
java compiler, the class is then compiled to bytecode with suffix .class hence barcode.java
will have its correspondent compiler bytecode named as barcode.class. Only after this has
been compiled it is when the same can be executed. The source file of java language of
have a single public class though it can have more than one classes as long as others
created as public inner classes or the public access modifiers. In case of the multiple
classes then one class will be introduced as class keyword then the public keyword. The
class which has no declaration as a public class in java can be stored in any file with .java
suffix then the compiler in return will be generating the classes which are defined in the
source file.
pg. 30
system under prospective report made use of different technologies and languages. For
example, the application was integrated with barcode scanning technology which enable
the application to be able to detect the book with the person who was allocated the book.
Its details are scanned and detected.
3.3.2 Java
Java is an object oriented programming language, classed based and it is designed to have
the smallest number of dependencies as possible. Java programming language is capable
of facilitating development of web based systems, mobile based systems and desktop
application. In mobile based systems, the language can be used in the design and
development of application which runs on android devices. This development is made
possible using android studio IDE.
In java programming language, the source file is normally named after the public class
they have , with the suffix .java being appended for example barcode.java. by the use of
java compiler, the class is then compiled to bytecode with suffix .class hence barcode.java
will have its correspondent compiler bytecode named as barcode.class. Only after this has
been compiled it is when the same can be executed. The source file of java language of
have a single public class though it can have more than one classes as long as others
created as public inner classes or the public access modifiers. In case of the multiple
classes then one class will be introduced as class keyword then the public keyword. The
class which has no declaration as a public class in java can be stored in any file with .java
suffix then the compiler in return will be generating the classes which are defined in the
source file.
pg. 30
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The keyword public in the java class shows that the method is free to be called from the
code of any other classes and also in case in is used in the class it shows that the class can
be used by other classes in the class hierarchy . there are other access modifiers in java
language which includes the protected and the private modifiers.
3.3.3 JSON
This is a light weight data exchanging format that is open standard format of a file which
makes use of human readable text in the whole process of data object transmission. JSON
is a most commonly used in the asynchronous browser server communication which in
this case includes the replacement of the XML in systems styles developed using AJAX
language of programming. It is a independent language in data formatting as it was
derived directly from Javascript hence the name Javascript Object Notation. JSON was
specified in the early 2000s by Dauglas Crockford though it was standardized in 2013 and
published for the very first time with a standard format in 2017 and also certified by ISO
in the very same year.
3.3.4 MySQL
This is can open source relational database whose name was taken from the “My”
combination of Michael Daughter and the SQL which is an abbreviation of Structural
Query Language. MySQL is an open source and given for free under the GNU licenses
and also available in proprietary license. The MySQL was first owned by the Swedish
company which was called MySQL AB then later bought by Oracle company which was
previously Sun MicroSystems. This was created using C++ programming language though
its parser for SQL was created in vac with the lexical analyser. The SQL makes it possible
for the developer to be able to store data which is very vital for future retrieval. This is the
pg. 31
code of any other classes and also in case in is used in the class it shows that the class can
be used by other classes in the class hierarchy . there are other access modifiers in java
language which includes the protected and the private modifiers.
3.3.3 JSON
This is a light weight data exchanging format that is open standard format of a file which
makes use of human readable text in the whole process of data object transmission. JSON
is a most commonly used in the asynchronous browser server communication which in
this case includes the replacement of the XML in systems styles developed using AJAX
language of programming. It is a independent language in data formatting as it was
derived directly from Javascript hence the name Javascript Object Notation. JSON was
specified in the early 2000s by Dauglas Crockford though it was standardized in 2013 and
published for the very first time with a standard format in 2017 and also certified by ISO
in the very same year.
3.3.4 MySQL
This is can open source relational database whose name was taken from the “My”
combination of Michael Daughter and the SQL which is an abbreviation of Structural
Query Language. MySQL is an open source and given for free under the GNU licenses
and also available in proprietary license. The MySQL was first owned by the Swedish
company which was called MySQL AB then later bought by Oracle company which was
previously Sun MicroSystems. This was created using C++ programming language though
its parser for SQL was created in vac with the lexical analyser. The SQL makes it possible
for the developer to be able to store data which is very vital for future retrieval. This is the
pg. 31

basis of technology and system development, data is stored in the SQL database, then it
can be accessed by the user with ease and faster since the user is able to search the
database using a keyword. This is done over the interface that the user interacts with the
database. Coding and programming is involved in this, The database is connected with the
interface using the code and JSON file formatting for easy conversion. This helped so
much in the development of the offline mobile based library management system since the
database is able to store data without the need of internet connection. Also data can be
retrieved from the database without the need of internet connection hence making is very
fast for the process to take place. JSON is used in this case to make it possible for the java
android programming language to be able to connect and read file which have been stored
in the database.
3.3.5 Conclusion
In conclusion, there are different technologies which are employed in the design and
development of an application. All these technologies are very much important in the
development of the application. Java programming language is used in the coding and
development of the interface which are used by the users to access the database, MySQL
is used for data storage and JSON is a file formatting language which is used for
interchangeable file formatting of readable text. Hence every technology is vital for
ensuring that the system is well developed and the set objectives have been achieved.
pg. 32
can be accessed by the user with ease and faster since the user is able to search the
database using a keyword. This is done over the interface that the user interacts with the
database. Coding and programming is involved in this, The database is connected with the
interface using the code and JSON file formatting for easy conversion. This helped so
much in the development of the offline mobile based library management system since the
database is able to store data without the need of internet connection. Also data can be
retrieved from the database without the need of internet connection hence making is very
fast for the process to take place. JSON is used in this case to make it possible for the java
android programming language to be able to connect and read file which have been stored
in the database.
3.3.5 Conclusion
In conclusion, there are different technologies which are employed in the design and
development of an application. All these technologies are very much important in the
development of the application. Java programming language is used in the coding and
development of the interface which are used by the users to access the database, MySQL
is used for data storage and JSON is a file formatting language which is used for
interchangeable file formatting of readable text. Hence every technology is vital for
ensuring that the system is well developed and the set objectives have been achieved.
pg. 32

CHAPTER FOUR
4 PRODUCT DESIGN
4.1 Technologies
In the design and development of a mobile based android library circulation system, there
are several technologies which are employed in order to ensure that the design process to
testing process has been successful.
Java Technology
Java is an object oriented programming language, classed based and it is designed to have
the smallest number of dependencies as possible. Java programming language is capable
of facilitating development of web based systems, mobile based systems and desktop
application. In mobile based systems, the language can be used in the design and
development of application which runs on android devices. This development is made
possible using android studio IDE.
JSON Technology
This is a light weight data exchanging format that is open standard format of a file which
makes use of human readable text in the whole process of data object transmission. JSON
is a most commonly used in the asynchronous browser server communication which in
this case includes the replacement of the XML in systems styles developed using AJAX
language of programming.
SQL Technology
The SQL makes it possible for the developer to be able to store data which is very vital for
future retrieval. This is the basis of technology and system development, data is stored in
the SQL database, then it can be accessed by the user with ease and faster since the user is
pg. 33
4 PRODUCT DESIGN
4.1 Technologies
In the design and development of a mobile based android library circulation system, there
are several technologies which are employed in order to ensure that the design process to
testing process has been successful.
Java Technology
Java is an object oriented programming language, classed based and it is designed to have
the smallest number of dependencies as possible. Java programming language is capable
of facilitating development of web based systems, mobile based systems and desktop
application. In mobile based systems, the language can be used in the design and
development of application which runs on android devices. This development is made
possible using android studio IDE.
JSON Technology
This is a light weight data exchanging format that is open standard format of a file which
makes use of human readable text in the whole process of data object transmission. JSON
is a most commonly used in the asynchronous browser server communication which in
this case includes the replacement of the XML in systems styles developed using AJAX
language of programming.
SQL Technology
The SQL makes it possible for the developer to be able to store data which is very vital for
future retrieval. This is the basis of technology and system development, data is stored in
the SQL database, then it can be accessed by the user with ease and faster since the user is
pg. 33
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

able to search the database using a keyword. This is done over the interface that the user
interacts with the database. Coding and programming is involved in this, The database is
connected with the interface using the code and JSON file formatting for easy conversion.
This helped so much in the development of the offline mobile based library management
system since the database is able to store data without the need of internet connection.
Barcode Scanning Technology
This technology is made possible using java programming language in android. The
barcode scanning technology is implemented in java using the barcode plugin which is
imported into the application development kit.
pg. 34
interacts with the database. Coding and programming is involved in this, The database is
connected with the interface using the code and JSON file formatting for easy conversion.
This helped so much in the development of the offline mobile based library management
system since the database is able to store data without the need of internet connection.
Barcode Scanning Technology
This technology is made possible using java programming language in android. The
barcode scanning technology is implemented in java using the barcode plugin which is
imported into the application development kit.
pg. 34
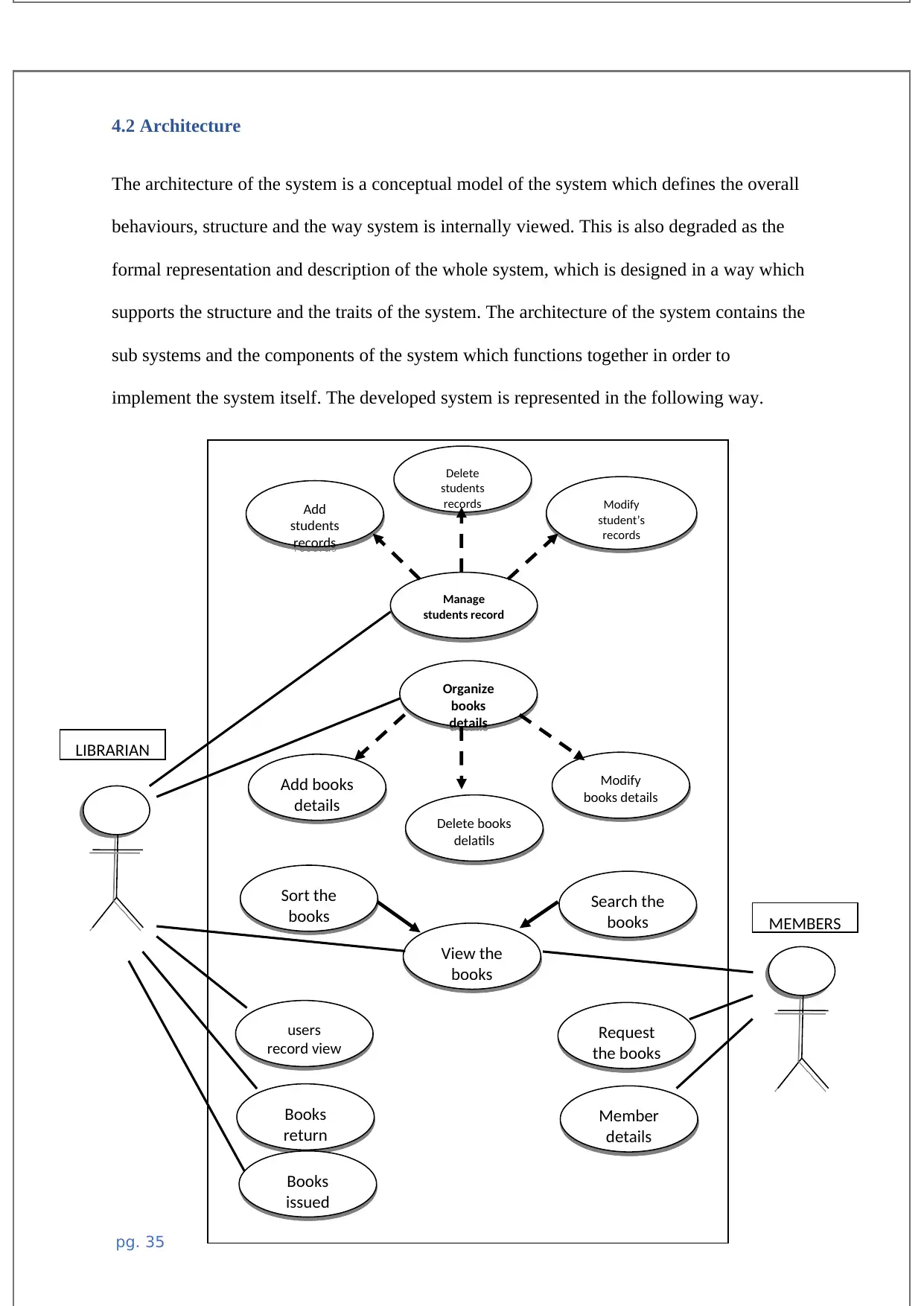
4.2 Architecture
The architecture of the system is a conceptual model of the system which defines the overall
behaviours, structure and the way system is internally viewed. This is also degraded as the
formal representation and description of the whole system, which is designed in a way which
supports the structure and the traits of the system. The architecture of the system contains the
sub systems and the components of the system which functions together in order to
implement the system itself. The developed system is represented in the following way.
pg. 35
Add
students
records
Delete
students
records Modify
student’s
records
Manage
students record
Add books
details
Organize
books
details
Modify
books details
Delete books
delatils
Sort the
books
View the
books
Search the
books
Request
the books
Member
details
users
record view
Books
return
LIBRARIAN
MEMBERS
Books
issued
The architecture of the system is a conceptual model of the system which defines the overall
behaviours, structure and the way system is internally viewed. This is also degraded as the
formal representation and description of the whole system, which is designed in a way which
supports the structure and the traits of the system. The architecture of the system contains the
sub systems and the components of the system which functions together in order to
implement the system itself. The developed system is represented in the following way.
pg. 35
Add
students
records
Delete
students
records Modify
student’s
records
Manage
students record
Add books
details
Organize
books
details
Modify
books details
Delete books
delatils
Sort the
books
View the
books
Search the
books
Request
the books
Member
details
users
record view
Books
return
LIBRARIAN
MEMBERS
Books
issued
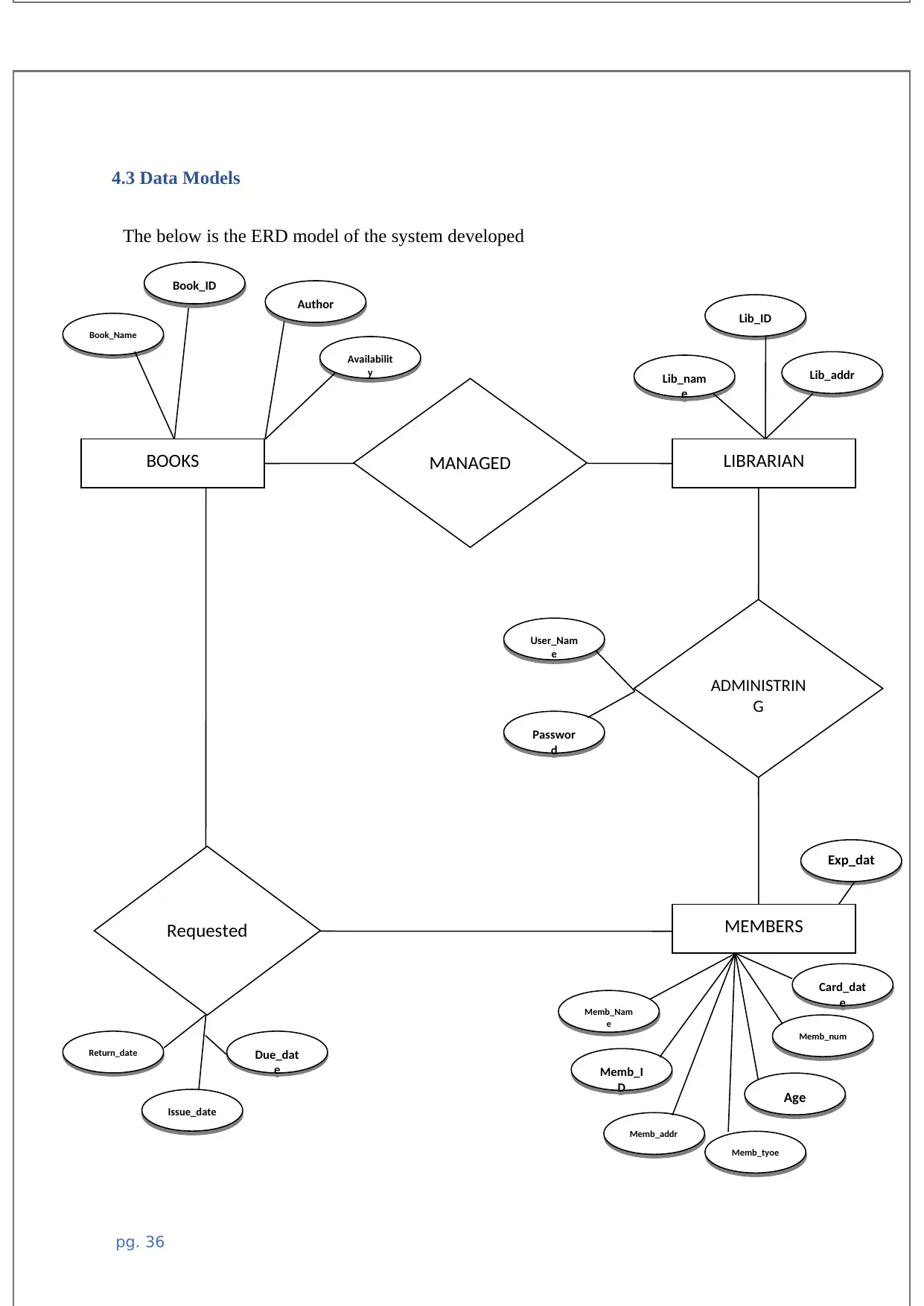
4.3 Data Models
The below is the ERD model of the system developed
pg. 36
Exp_dat
e
Card_dat
e
Memb_num
Memb_addr
Memb_I
D
Memb_Nam
e
Due_dat
e
Issue_date
Return_date
Age
Memb_tyoe
MEMBERSRequested
ADMINISTRIN
G
User_Nam
e
Passwor
d
BOOKS LIBRARIANMANAGED
Availabilit
y
Author
Book_Name
Lib_addr
Lib_ID
Lib_nam
e
Book_ID
The below is the ERD model of the system developed
pg. 36
Exp_dat
e
Card_dat
e
Memb_num
Memb_addr
Memb_I
D
Memb_Nam
e
Due_dat
e
Issue_date
Return_date
Age
Memb_tyoe
MEMBERSRequested
ADMINISTRIN
G
User_Nam
e
Passwor
d
BOOKS LIBRARIANMANAGED
Availabilit
y
Author
Book_Name
Lib_addr
Lib_ID
Lib_nam
e
Book_ID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4.4 Security
Security is a very important factor in the development of any application today due to many
cases of software hacking and phishing. The developed system has been developed with
security factor into consideration. This is described as follows;
a. The software cannot be accessed by an-authorized user since every user has to sign in
using their own login credentials which are known by themselves. This is the best way
of limiting unauthorized users and hackers from accessing the application.
b. Soft hacking cannot be possible since the password field has been encrypted with the
MD5 encryption technology which hides the digits which are being entered as password
therefore making it very difficult for a person to steal the password of the user when
they are entering the password.
c. The application has the admin panel which controls the number of users signing into the
system. The admin is able to check the users who are currently using the system with
there details hence any intruder in the system is automatically blocked in time.
d. The system is offline used, therefore there is no way hacker can access the application
remotely. For the person to be able to use the system then must have the system with
them in there hands which is actually not possible as the system is only used when the
system is down. Usage within that limit is only important otherwise useless as data is
backed up each and every time.
pg. 37
Security is a very important factor in the development of any application today due to many
cases of software hacking and phishing. The developed system has been developed with
security factor into consideration. This is described as follows;
a. The software cannot be accessed by an-authorized user since every user has to sign in
using their own login credentials which are known by themselves. This is the best way
of limiting unauthorized users and hackers from accessing the application.
b. Soft hacking cannot be possible since the password field has been encrypted with the
MD5 encryption technology which hides the digits which are being entered as password
therefore making it very difficult for a person to steal the password of the user when
they are entering the password.
c. The application has the admin panel which controls the number of users signing into the
system. The admin is able to check the users who are currently using the system with
there details hence any intruder in the system is automatically blocked in time.
d. The system is offline used, therefore there is no way hacker can access the application
remotely. For the person to be able to use the system then must have the system with
them in there hands which is actually not possible as the system is only used when the
system is down. Usage within that limit is only important otherwise useless as data is
backed up each and every time.
pg. 37
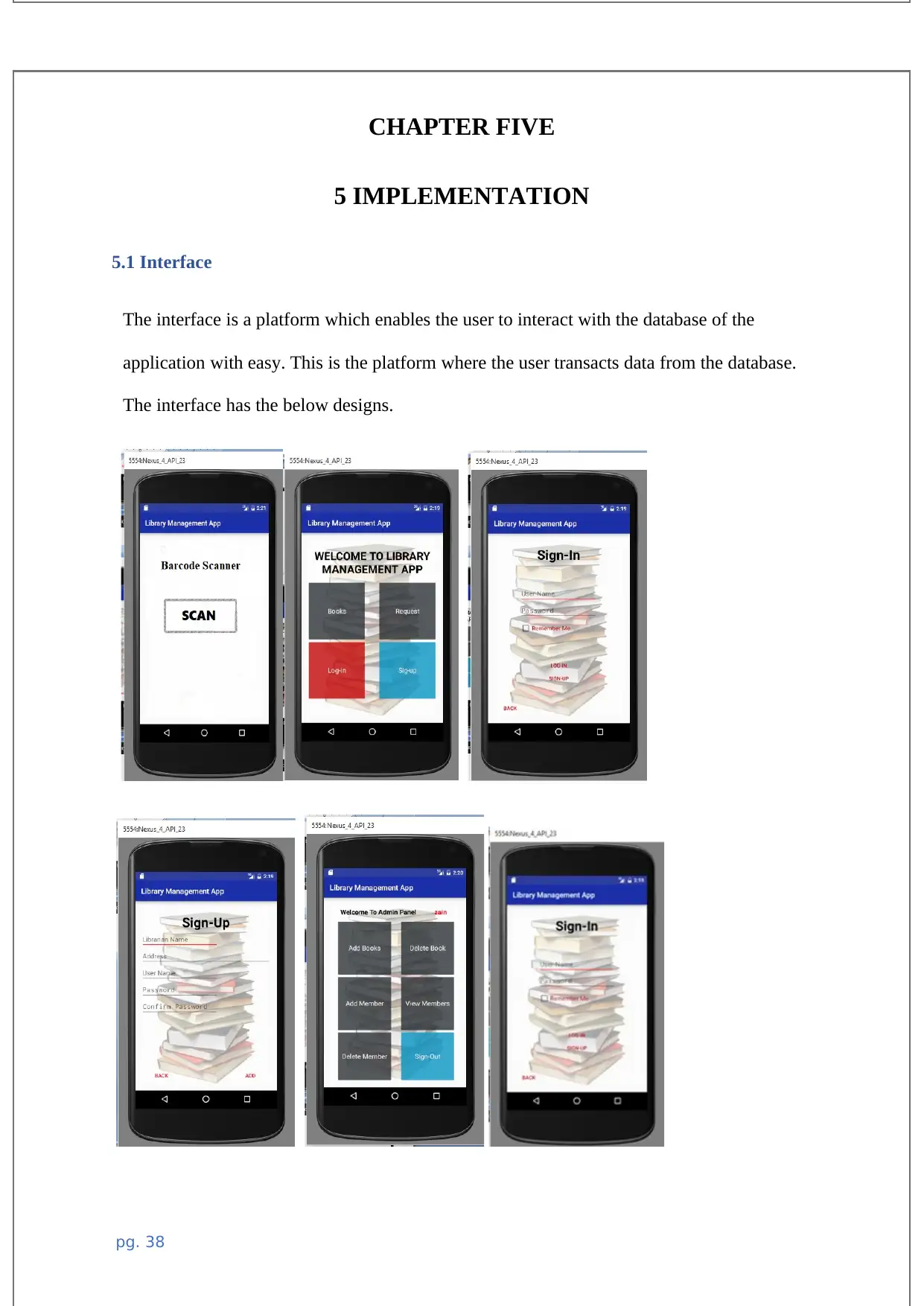
CHAPTER FIVE
5 IMPLEMENTATION
5.1 Interface
The interface is a platform which enables the user to interact with the database of the
application with easy. This is the platform where the user transacts data from the database.
The interface has the below designs.
pg. 38
5 IMPLEMENTATION
5.1 Interface
The interface is a platform which enables the user to interact with the database of the
application with easy. This is the platform where the user transacts data from the database.
The interface has the below designs.
pg. 38
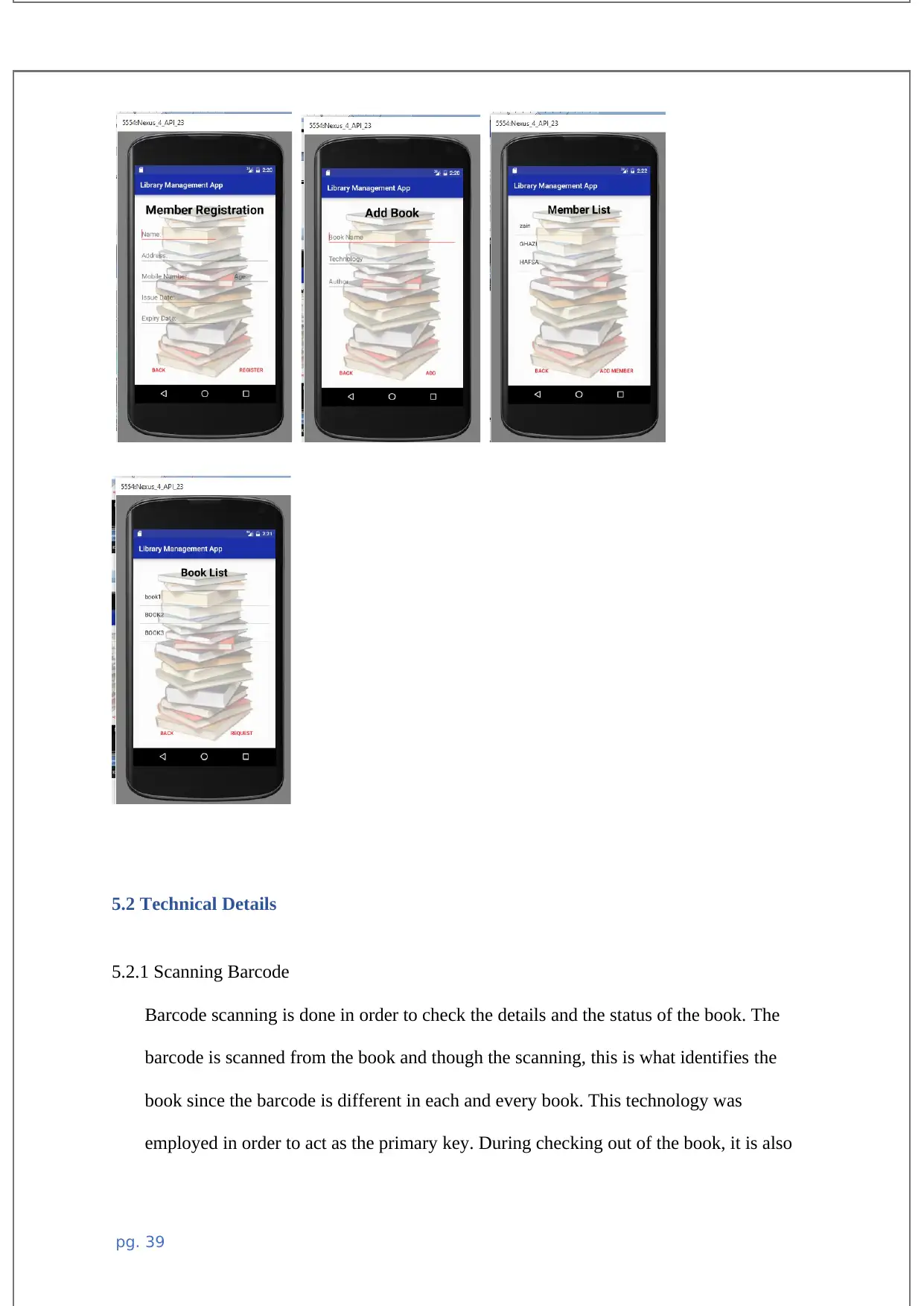
5.2 Technical Details
5.2.1 Scanning Barcode
Barcode scanning is done in order to check the details and the status of the book. The
barcode is scanned from the book and though the scanning, this is what identifies the
book since the barcode is different in each and every book. This technology was
employed in order to act as the primary key. During checking out of the book, it is also
pg. 39
5.2.1 Scanning Barcode
Barcode scanning is done in order to check the details and the status of the book. The
barcode is scanned from the book and though the scanning, this is what identifies the
book since the barcode is different in each and every book. This technology was
employed in order to act as the primary key. During checking out of the book, it is also
pg. 39
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

scanned and the interface for borrowing the book will appear where the user will enter
the borrower details to check out the book.
5.2.2 Storing Details
The application developed is an offline application which stored its data in an offline
SQLite database. The data captured is stored in the offline SQLite database which will
later be synchronized to the main system when the network coverage has been regained.
5.2.3 Client-side Technologies
The client side of the system is developed using java programming language. This is the
interface which interacts with the user of the system who is the library employee. The
barcode technology is also in the client side where the client/user of the application will
be able to scan the barcode of the book while checking the book details.
pg. 40
the borrower details to check out the book.
5.2.2 Storing Details
The application developed is an offline application which stored its data in an offline
SQLite database. The data captured is stored in the offline SQLite database which will
later be synchronized to the main system when the network coverage has been regained.
5.2.3 Client-side Technologies
The client side of the system is developed using java programming language. This is the
interface which interacts with the user of the system who is the library employee. The
barcode technology is also in the client side where the client/user of the application will
be able to scan the barcode of the book while checking the book details.
pg. 40

CHAPTER SIX
6 TESTING
Testing of the application is done using the validation model alias V-model, in this model
each and every stage of verifying contains its separate stage of validation (De spautz et al.,
2008). In the V-model validation, the following are the phases used;
a. Unit Testing: This is developed at the design stage, the UTP is done in order to
eliminate errors and bugs at the unit level or the code level. As its defined, the unit is
the smallest entity that exists independently like the module of the program. This type
of testing makes verification on the smallest entity that it can be able to work
correctly when it is executed separately from the other part of the code. During the
development of the mobile library circulation system, each and every module was
tested separately and the code was running correctly at every module (Anon, n.d.).
b. Integration testing: This phase of testing is done during the phase of architectural
design. This test is done with the aim of ensuring that the unit code which had been
tested can be able to communicate and work correctly among themselves. The
application was tested in integrated test and every module was able to communicate
with each other in an efficient and effective manner.
c. System Testing: This type of testing is done at the system design stage. At this stage
of testing, it ensures that the requirements of the application are met and the system
has achieved its objectives.
This system test was done to the application and the system was proved that it has met
all the expectation of the user to curb the problem which led to the development of the
system (Anon, n.d.).
pg. 41
6 TESTING
Testing of the application is done using the validation model alias V-model, in this model
each and every stage of verifying contains its separate stage of validation (De spautz et al.,
2008). In the V-model validation, the following are the phases used;
a. Unit Testing: This is developed at the design stage, the UTP is done in order to
eliminate errors and bugs at the unit level or the code level. As its defined, the unit is
the smallest entity that exists independently like the module of the program. This type
of testing makes verification on the smallest entity that it can be able to work
correctly when it is executed separately from the other part of the code. During the
development of the mobile library circulation system, each and every module was
tested separately and the code was running correctly at every module (Anon, n.d.).
b. Integration testing: This phase of testing is done during the phase of architectural
design. This test is done with the aim of ensuring that the unit code which had been
tested can be able to communicate and work correctly among themselves. The
application was tested in integrated test and every module was able to communicate
with each other in an efficient and effective manner.
c. System Testing: This type of testing is done at the system design stage. At this stage
of testing, it ensures that the requirements of the application are met and the system
has achieved its objectives.
This system test was done to the application and the system was proved that it has met
all the expectation of the user to curb the problem which led to the development of the
system (Anon, n.d.).
pg. 41
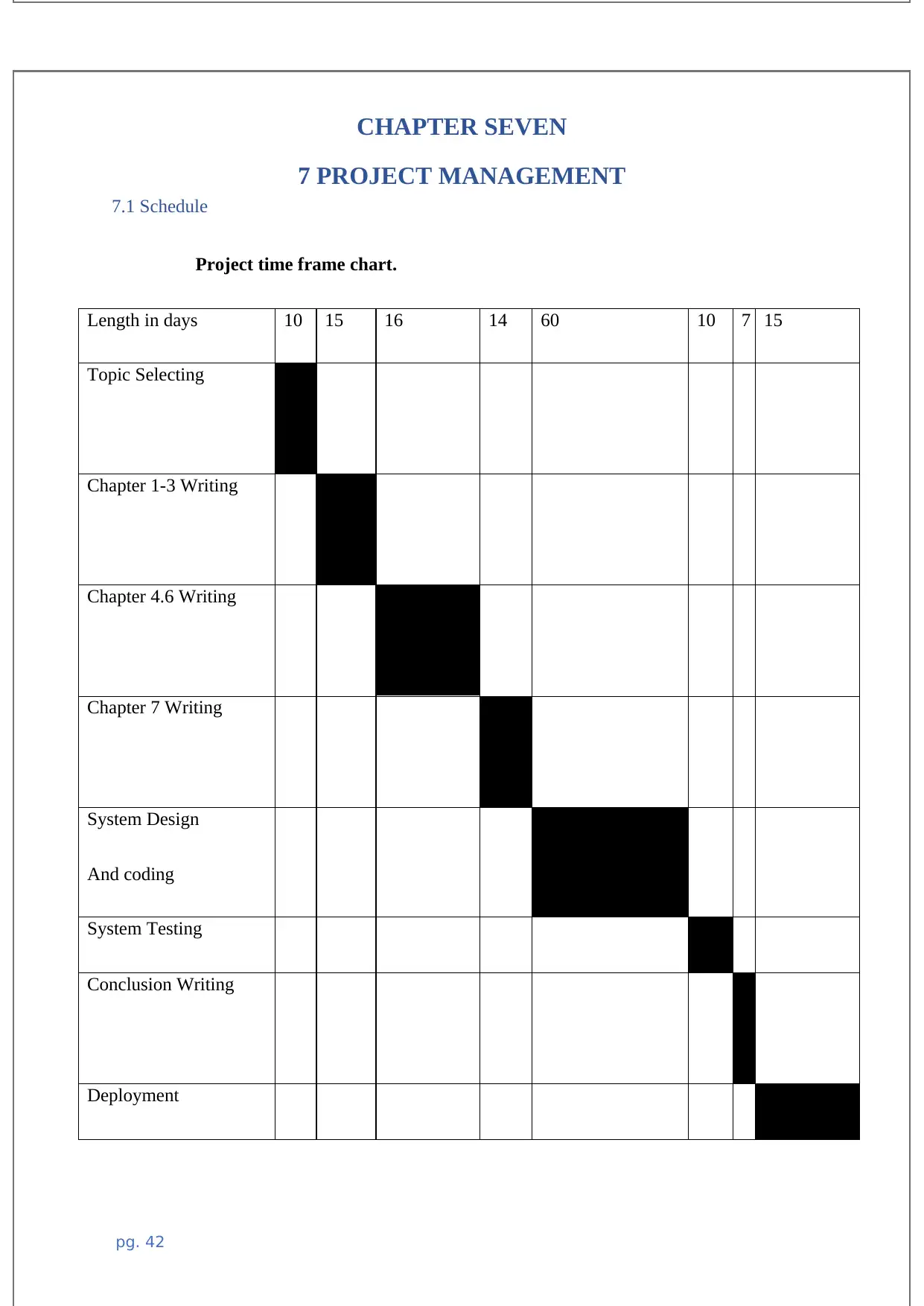
CHAPTER SEVEN
7 PROJECT MANAGEMENT
7.1 Schedule
Project time frame chart.
Length in days 10 15 16 14 60 10 7 15
Topic Selecting
Chapter 1-3 Writing
Chapter 4.6 Writing
Chapter 7 Writing
System Design
And coding
System Testing
Conclusion Writing
Deployment
pg. 42
7 PROJECT MANAGEMENT
7.1 Schedule
Project time frame chart.
Length in days 10 15 16 14 60 10 7 15
Topic Selecting
Chapter 1-3 Writing
Chapter 4.6 Writing
Chapter 7 Writing
System Design
And coding
System Testing
Conclusion Writing
Deployment
pg. 42
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7.2 Project Deliverables
A deliverable is a tangible or intangible good or service produced as a result of a project that
is intended to be delivered to a customer. A deliverable could be a report, a document, a
software product, a server upgrade or any other building block of an overall project
The project deliverable of a system is a tangible and the intangible things which are given
out when the project is supposed to be given to the customer. The deliverables in this
project therefore includes the following;
a. A software system which is an android based circulation system.
b. A software specification document which describes the minimum requirements under
which the software is able to operate.
c. Documentation of the software which describes the overall operation and functionality
of the system.
d. A license copyright which indicates that the rights have been bought and therefore the
customer is allowed to use the software.
e. Training services for all new users of the system.
7.3 Risk Management
Risk management in system development involves identification, evaluation and prioritizing
the possibility of the system to fail. Any system has the possibility to fail and therefore it
becomes good and positive if the risk can be identified, the risk evaluated and then it is
measured in terms of possibility and intensity of the risk to happen and if it happens the
possibility of the risk to demolish the whole project. The application developed was also
risked and the management methods put in place which will be employed in the near future
if the risk happens (Anon, n.d.). The table below shows the summary of the risk
pg. 43
A deliverable is a tangible or intangible good or service produced as a result of a project that
is intended to be delivered to a customer. A deliverable could be a report, a document, a
software product, a server upgrade or any other building block of an overall project
The project deliverable of a system is a tangible and the intangible things which are given
out when the project is supposed to be given to the customer. The deliverables in this
project therefore includes the following;
a. A software system which is an android based circulation system.
b. A software specification document which describes the minimum requirements under
which the software is able to operate.
c. Documentation of the software which describes the overall operation and functionality
of the system.
d. A license copyright which indicates that the rights have been bought and therefore the
customer is allowed to use the software.
e. Training services for all new users of the system.
7.3 Risk Management
Risk management in system development involves identification, evaluation and prioritizing
the possibility of the system to fail. Any system has the possibility to fail and therefore it
becomes good and positive if the risk can be identified, the risk evaluated and then it is
measured in terms of possibility and intensity of the risk to happen and if it happens the
possibility of the risk to demolish the whole project. The application developed was also
risked and the management methods put in place which will be employed in the near future
if the risk happens (Anon, n.d.). The table below shows the summary of the risk
pg. 43
management process. The risk was assessed in from level 1 to 10 according to the
complexity of the system
Risk Identification Risk assessment 1-10 Risk management Priority
Application Hacking 3 Encrypted password
during login,
Low
System crushing 1 The system testing
done and errors and
bugs removed
low
Application being
slow
5 The application has
been made with
offline database hence
being slow has been
curbed and prevented.
Medium
Application stopped
working
10 This is prevented by
the third part since the
application is installed
in the android mobile
phone.
High
7.4 Communication with Client
The system communication with the client is the most vital factor as it determines the
perspective under which the client will choose towards the quality of the software. For
better communication with the client regarding the system developed, demonstration
method shall be applied where the client will get demonstration of how the application
pg. 44
complexity of the system
Risk Identification Risk assessment 1-10 Risk management Priority
Application Hacking 3 Encrypted password
during login,
Low
System crushing 1 The system testing
done and errors and
bugs removed
low
Application being
slow
5 The application has
been made with
offline database hence
being slow has been
curbed and prevented.
Medium
Application stopped
working
10 This is prevented by
the third part since the
application is installed
in the android mobile
phone.
High
7.4 Communication with Client
The system communication with the client is the most vital factor as it determines the
perspective under which the client will choose towards the quality of the software. For
better communication with the client regarding the system developed, demonstration
method shall be applied where the client will get demonstration of how the application
pg. 44

works. This is aimed at getting comments and feedback from the software owner since they
are the financiers of the application, without them then the application cannot be deployed
in the library for use.
pg. 45
are the financiers of the application, without them then the application cannot be deployed
in the library for use.
pg. 45
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CHAPTER EIGHT
8 PROJECT EVALUATION
8.1 Software Quality
The quality of the software is determined in accordance with the set objectives. The
question which is supposed to be answered in order to determine if the quality of the
software has been achieved is, Does the software developed meet the minimum
requirement which were set aside? Does the software achieve the objectives set? Was the
testing process successful?
Now in regard to the library circulation system developed, it is ascertained that the
objectives which were set have been achieved. The testing and evaluation were done and
the application was able to run with no error at all hence there are no errors which includes
syntax, runtime and execution error, The application was able to take respected input and
produce the desired output. The quality of the software therefore is confirmed to be up to
the mark and the software is ready for deployment.
8.2 Ease of Use
This is the most important factor in software development. The software has to be very
simple to the person who is operating the system. This can be done by designing a very
interacting and easy to navigate interfaces. The software developed is very simple and
easy in terms of usage as it has the most minimum number of buttons and fields which can
be used for the users to enter data. Most of the parts are fully automated. The interfaces are
easy to use and easy to navigate as the names have been given to easy and every field and
buttons for easy reading and understanding especially to a person who does not have any
pg. 46
8 PROJECT EVALUATION
8.1 Software Quality
The quality of the software is determined in accordance with the set objectives. The
question which is supposed to be answered in order to determine if the quality of the
software has been achieved is, Does the software developed meet the minimum
requirement which were set aside? Does the software achieve the objectives set? Was the
testing process successful?
Now in regard to the library circulation system developed, it is ascertained that the
objectives which were set have been achieved. The testing and evaluation were done and
the application was able to run with no error at all hence there are no errors which includes
syntax, runtime and execution error, The application was able to take respected input and
produce the desired output. The quality of the software therefore is confirmed to be up to
the mark and the software is ready for deployment.
8.2 Ease of Use
This is the most important factor in software development. The software has to be very
simple to the person who is operating the system. This can be done by designing a very
interacting and easy to navigate interfaces. The software developed is very simple and
easy in terms of usage as it has the most minimum number of buttons and fields which can
be used for the users to enter data. Most of the parts are fully automated. The interfaces are
easy to use and easy to navigate as the names have been given to easy and every field and
buttons for easy reading and understanding especially to a person who does not have any
pg. 46

knowledge of the system. From the screenshots shared in chapter 5, its seen that the
interface is user friendly and easy to navigate through.
8.3 Methodology Choice
The use of methodology subject the project into the output of the final result. A choice of a
good methodology impacts positively the final result of the application developed. The
methodology which were chosen in this case was divided into 3 major stages, which
includes the collection of necessary and crucial information, design and development of
the application then finally testing and evaluation of the developed application. This
methodology ensues that the system is systematically developed and non of the gap has
been left unhandled.
8.4 Future Improvement
The application has a room for improvement in the future. The development has been
made for only check in and check out services though it there will be need to improve the
system to have a fully functional library management system then the app is able to take
necessary improvements which are needed. Upgrades and change of some colours when
needs is also possible since all the variable and methods are globally called.
pg. 47
interface is user friendly and easy to navigate through.
8.3 Methodology Choice
The use of methodology subject the project into the output of the final result. A choice of a
good methodology impacts positively the final result of the application developed. The
methodology which were chosen in this case was divided into 3 major stages, which
includes the collection of necessary and crucial information, design and development of
the application then finally testing and evaluation of the developed application. This
methodology ensues that the system is systematically developed and non of the gap has
been left unhandled.
8.4 Future Improvement
The application has a room for improvement in the future. The development has been
made for only check in and check out services though it there will be need to improve the
system to have a fully functional library management system then the app is able to take
necessary improvements which are needed. Upgrades and change of some colours when
needs is also possible since all the variable and methods are globally called.
pg. 47

CHAPTER NINE
9 REFLECTION
9.1 Achievements
Development of this particular system has not been easy though I have tried as much as I
could to achieve the set objectives as a means of making the work be termed as functional.
The following therefore are the achievements which has have made as far as the objectives
are concerned.
a) I have designed an offline based android library management application which will
be able to evacuate all the problems which are being faced in the library when the
current system is down due to network strength.
b) I have developed the designed system using android studio IDE with java
programming language as the core language.
c) I have integrated the application with SQLite database for its offline use.
d) I have implemented the system in android studio.
e) I have evaluated and tested the system in terms of its general performance and
efficiency in accordance with the requirements set and I have ascertained that the
application meets its requirements.
f) I have managed synchronization of the recorded data into the main system when the
network strength has been regained.
g) Have analysed MARC 21 format data file and checked if catalogues which have
been stored in the file can be converted to SQLite fit, and displayed in the android
application.
pg. 48
9 REFLECTION
9.1 Achievements
Development of this particular system has not been easy though I have tried as much as I
could to achieve the set objectives as a means of making the work be termed as functional.
The following therefore are the achievements which has have made as far as the objectives
are concerned.
a) I have designed an offline based android library management application which will
be able to evacuate all the problems which are being faced in the library when the
current system is down due to network strength.
b) I have developed the designed system using android studio IDE with java
programming language as the core language.
c) I have integrated the application with SQLite database for its offline use.
d) I have implemented the system in android studio.
e) I have evaluated and tested the system in terms of its general performance and
efficiency in accordance with the requirements set and I have ascertained that the
application meets its requirements.
f) I have managed synchronization of the recorded data into the main system when the
network strength has been regained.
g) Have analysed MARC 21 format data file and checked if catalogues which have
been stored in the file can be converted to SQLite fit, and displayed in the android
application.
pg. 48
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

h) Reviewed other literatures and checked if the developed application can be
improved in the future in terms of service delivery as well as efficiency and I have
ascertained that it can be improved further.
9.2 Challenges
For successfully achieving the set objectives in the design and development of the
application, challenges must be encountered in the process as the whole process cannot just
be smooth. One of the most common challenges I faced during the development of the
application is the errors. Errors in programming are divided into different categories, though
want I faced most were two types of errors one being the runtime error and the syntax error.
In the development of the any system, errors have to be expected, these errors might range
from easy to solve errors and technical errors. Each time I do development of the application
errors emerge which wastes a lot of time in terms of solving, researching on how some of the
errors can be solved wastes a lot of time.
Another challenge which I face in the course of development of the application is the
conversion of the MAR21 file format to SQLite compatible formats. This process takes a lot
of time to be completed as one has to use java software to make this process successful.
Implementation of barcode scanning capability into the application was another challenge
which I face in the process. Hardware integration into the system is always challenging and
technical in terms of implementation, a lot of time was taken to integrate the code and
making sure that the code is working correcting without any problems.
All the above challenges are some of the most common challenges developers face in there
course of development and therefore an one of them I had to pass through the same system as
pg. 49
improved in the future in terms of service delivery as well as efficiency and I have
ascertained that it can be improved further.
9.2 Challenges
For successfully achieving the set objectives in the design and development of the
application, challenges must be encountered in the process as the whole process cannot just
be smooth. One of the most common challenges I faced during the development of the
application is the errors. Errors in programming are divided into different categories, though
want I faced most were two types of errors one being the runtime error and the syntax error.
In the development of the any system, errors have to be expected, these errors might range
from easy to solve errors and technical errors. Each time I do development of the application
errors emerge which wastes a lot of time in terms of solving, researching on how some of the
errors can be solved wastes a lot of time.
Another challenge which I face in the course of development of the application is the
conversion of the MAR21 file format to SQLite compatible formats. This process takes a lot
of time to be completed as one has to use java software to make this process successful.
Implementation of barcode scanning capability into the application was another challenge
which I face in the process. Hardware integration into the system is always challenging and
technical in terms of implementation, a lot of time was taken to integrate the code and
making sure that the code is working correcting without any problems.
All the above challenges are some of the most common challenges developers face in there
course of development and therefore an one of them I had to pass through the same system as
pg. 49

part of the work in order to create a more comprehensive application which meets the needs
of the library under investigation.
9.3 Conclusion
In conclusion, in order to achieve the requirements and the set objectives, then the developer
has to get across some challenges which will try to drug the whole process behind. Most of
the challenges are common but others are specific in accordance to the type of the system
which is being developed. The development of a mobile based application for the library
circulation and management was made possible through some other set objectives and aim
too. The system is conformed to be more efficient and effective to solve all the problems
which were found in the current system which made the core source of investigation. From
the overall report and project, it is concluded that the set objectives were met and achieved.
The application was also tested and evaluated to check for errors and if it meets the minimum
requirement and it can also be concluded that the system is set for use, all the errors were
debugged hence it is able to solve the problem with the current system which will in turn
change or improve the delivery of the services in the library under investigation as well as
making work easier throughout the process of checking in and checking out when the internet
connection is down. The application developed therefore is recommended for deployment in
the library as explained above.
pg. 50
of the library under investigation.
9.3 Conclusion
In conclusion, in order to achieve the requirements and the set objectives, then the developer
has to get across some challenges which will try to drug the whole process behind. Most of
the challenges are common but others are specific in accordance to the type of the system
which is being developed. The development of a mobile based application for the library
circulation and management was made possible through some other set objectives and aim
too. The system is conformed to be more efficient and effective to solve all the problems
which were found in the current system which made the core source of investigation. From
the overall report and project, it is concluded that the set objectives were met and achieved.
The application was also tested and evaluated to check for errors and if it meets the minimum
requirement and it can also be concluded that the system is set for use, all the errors were
debugged hence it is able to solve the problem with the current system which will in turn
change or improve the delivery of the services in the library under investigation as well as
making work easier throughout the process of checking in and checking out when the internet
connection is down. The application developed therefore is recommended for deployment in
the library as explained above.
pg. 50

REFERENCES
Adamson, P. & Veronica, H. (2008). JISC & SCONUL Library Management Systems Study .
Sheffield, UK: Sero Consulting. p. 51.
Ademodi, D.T., & Adepoju, E. O. (2009). Computer skill among Librarians in Academic
Libraries on Ondo and Ekiti States, Nigeria. Library Philosophy & Practice.
Adomi, E. E., & Anie, S. O. (2006). An Assessment of Computer Literacy Skills of
Professionals in Nigerian University libraries. Library Hi Tech News, Vol.23 (2) pp.10-14.
Anon, (n.d.). Data Structures and Algorithms | Coursera. [online] Available at:
https://www.coursera.org/specializations/data-structures-algorithms [Accessed 27 May
2019].
Anon, (n.d.). Data Structures and Algorithms | Udacity. [online] Available at:
https://www.udacity.com/course/data-structures-and-algorithms-nanodegree--nd256
[Accessed 27 May 2019].
Anon, (n.d.). Data Structures and Algorithms. [online] Available at:
https://www.cs.princeton.edu/courses/archive/spr11/cos217/lectures/08DsAlg.pdf [Accessed
27 May 2019].
Ashutosh, T & Ashish,S. (2012). Online Library Management System. IOSR Journal of
Engineering (IOSRJEN). Vol. 2 (2), pp. 180- 186.
Dasgupta, A. (2009). Preparing future librarians in India: A vision for LIS Schools of Indian
Universities in the 21st Century. IFLA. Available:
http://www.ifla.org/files/hq/papers/ifla75/126-dasgupta-en.pdf.
DeSpautz, J., Kenneth S. K., Gerhard, W. (2008). GAMP Standards for Validation of
Automated Systems. Pharmaceutical Processing.
Dinesh, R., Pravin, S., Aravindhan, M & Rajeswari, D. 2015. Library access system
Smartphone Application using Android. International Journal of Computer Science and
Mobile Computing. Vol.4 (3), pp. 142-149.
pg. 51
Adamson, P. & Veronica, H. (2008). JISC & SCONUL Library Management Systems Study .
Sheffield, UK: Sero Consulting. p. 51.
Ademodi, D.T., & Adepoju, E. O. (2009). Computer skill among Librarians in Academic
Libraries on Ondo and Ekiti States, Nigeria. Library Philosophy & Practice.
Adomi, E. E., & Anie, S. O. (2006). An Assessment of Computer Literacy Skills of
Professionals in Nigerian University libraries. Library Hi Tech News, Vol.23 (2) pp.10-14.
Anon, (n.d.). Data Structures and Algorithms | Coursera. [online] Available at:
https://www.coursera.org/specializations/data-structures-algorithms [Accessed 27 May
2019].
Anon, (n.d.). Data Structures and Algorithms | Udacity. [online] Available at:
https://www.udacity.com/course/data-structures-and-algorithms-nanodegree--nd256
[Accessed 27 May 2019].
Anon, (n.d.). Data Structures and Algorithms. [online] Available at:
https://www.cs.princeton.edu/courses/archive/spr11/cos217/lectures/08DsAlg.pdf [Accessed
27 May 2019].
Ashutosh, T & Ashish,S. (2012). Online Library Management System. IOSR Journal of
Engineering (IOSRJEN). Vol. 2 (2), pp. 180- 186.
Dasgupta, A. (2009). Preparing future librarians in India: A vision for LIS Schools of Indian
Universities in the 21st Century. IFLA. Available:
http://www.ifla.org/files/hq/papers/ifla75/126-dasgupta-en.pdf.
DeSpautz, J., Kenneth S. K., Gerhard, W. (2008). GAMP Standards for Validation of
Automated Systems. Pharmaceutical Processing.
Dinesh, R., Pravin, S., Aravindhan, M & Rajeswari, D. 2015. Library access system
Smartphone Application using Android. International Journal of Computer Science and
Mobile Computing. Vol.4 (3), pp. 142-149.
pg. 51
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Gavgani,V.Z., Shokraneh,F. & Shiramin,A.R. (2011). Need for content Re-engineering of
The medical library and information science curriculum in Iran. Library Philosophy &
Practice. Available: http://unllib.unl.edu/LPP/gavgani- shokraneh-shiramin.html.
Johnson, C.A. (2007). Library and information science education in developing countries.
The International Information & Library Review, Vol. 39, pp. 64-71.
Neelakandan,B., Duraisekar,S., Balasubramani,R & Srinivasa,S. 2010. Implementation of
Automated Library Management System in the School of Chemistry Bharathidasan
University using Koha Open Source Software. International Journal of Applied Engineering
Research, Dindigul, Vol. (1), pp. 149-167.
Prabhakar, K., Rahul, K., Rajat, S., & Vikram, S. (2014). Library Management System.
Division of Computer Science School of Engineering Cochin University of Science &
Technology Kochi-682022.
Rahman, A. I. M. J., Khatun, M., & Islam, M. M. (2008). Library Education in Bangladesh:
Strengths, Problems and Suggestions. Library Philosophy & Practice. Available:
http://unllib.unl.edu/LPP/rahman-khatun-mezbahulislam.html.
Sarawut, M. (2015). Library management system. Division of computer science school of arts
and science Tanku Abdul Rahman College Kuala Lampur.
Sarawut, M. (2015). Offering Library Resources through Web-site and Mobile Systems with
Web Services for Central Library Suratthani Rajabhat University.World Journal of Computer
Application and Technology, Vol.3 (1) pp. 1-8.
Sharma,C.K., Singh,H., & Khiran, R. (2005). Library Management System. Available:
en.wkipedia. org/wiki/Library_management.
pg. 52
The medical library and information science curriculum in Iran. Library Philosophy &
Practice. Available: http://unllib.unl.edu/LPP/gavgani- shokraneh-shiramin.html.
Johnson, C.A. (2007). Library and information science education in developing countries.
The International Information & Library Review, Vol. 39, pp. 64-71.
Neelakandan,B., Duraisekar,S., Balasubramani,R & Srinivasa,S. 2010. Implementation of
Automated Library Management System in the School of Chemistry Bharathidasan
University using Koha Open Source Software. International Journal of Applied Engineering
Research, Dindigul, Vol. (1), pp. 149-167.
Prabhakar, K., Rahul, K., Rajat, S., & Vikram, S. (2014). Library Management System.
Division of Computer Science School of Engineering Cochin University of Science &
Technology Kochi-682022.
Rahman, A. I. M. J., Khatun, M., & Islam, M. M. (2008). Library Education in Bangladesh:
Strengths, Problems and Suggestions. Library Philosophy & Practice. Available:
http://unllib.unl.edu/LPP/rahman-khatun-mezbahulislam.html.
Sarawut, M. (2015). Library management system. Division of computer science school of arts
and science Tanku Abdul Rahman College Kuala Lampur.
Sarawut, M. (2015). Offering Library Resources through Web-site and Mobile Systems with
Web Services for Central Library Suratthani Rajabhat University.World Journal of Computer
Application and Technology, Vol.3 (1) pp. 1-8.
Sharma,C.K., Singh,H., & Khiran, R. (2005). Library Management System. Available:
en.wkipedia. org/wiki/Library_management.
pg. 52

Siwakoti, S. (2008). Status of school library development in Nepal. Sri Lanka Journal of 52
Librarianship & Information Management, Vol.1 (1), pp.13-19. Available:
http://www.cmb.ac.lk/academic/institutes/nilis/reports/Nepal.pdf. APPENDIX: CODE
BIBLIOGRAPHY
Anon, (n.d.). 7 Apps for Cataloguing Your Home Library | GradHacker. [online] Available
at: https://www.insidehighered.com/blogs/gradhacker/7-apps-cataloguing-your-home-library
[Accessed 2019].
Anon, (n.d.). Android Project On Library Management System - YouTube. [online] Available
at: https://www.youtube.com/watch?v=TKum0Eg206c [Accessed 2019].
Anon, (n.d.). GitHub - prabhakar267/library-management-system: An .... [online] Available
at: https://github.com/prabhakar267/library-management-system [Accessed 2019].
Anon, (n.d.). How to create an Android based library management system .... [online]
Available at: https://www.quora.com/How-do-I-create-an-Android-based-library-
management-system-I-dont-need-source-code-but-full-method-Im-learning-Java-and-this-
will-be-my-first-project [Accessed 2019].
Anon, (n.d.). Java mini projects With Source Code - ProjectsGeek. [online] Available at:
https://projectsgeek.com/ [Accessed 2019].
Anon, (n.d.). Libib.com - Home library management web app. [online] Available at:
https://www.libib.com/ [Accessed 2019].
Anon, (n.d.). Library management application,Android project ideas .... [online] Available
at: https://www.kashipara.com/project/idea/Android/library-management-application_23.html
[Accessed 2019].
Anon, (n.d.). Library Management System - Cochin University of Science .... [online]
Available at: http://dspace.cusat.ac.in/jspui/bitstream/123456789/8218/1/library
%20management%20system.pdf [Accessed 2019].
Anon, (n.d.). Library Management System - Student Project Code. [online] Available at:
http://www.studentprojectcode.com/csharp/library-management-system/ [Accessed 2019].
Anon, (n.d.). Library Management System | Free Source Code & Tutorials. [online]
Available at: https://www.sourcecodester.com/microsoft-access/library-management-
system.html [Accessed 2019].
pg. 53
Librarianship & Information Management, Vol.1 (1), pp.13-19. Available:
http://www.cmb.ac.lk/academic/institutes/nilis/reports/Nepal.pdf. APPENDIX: CODE
BIBLIOGRAPHY
Anon, (n.d.). 7 Apps for Cataloguing Your Home Library | GradHacker. [online] Available
at: https://www.insidehighered.com/blogs/gradhacker/7-apps-cataloguing-your-home-library
[Accessed 2019].
Anon, (n.d.). Android Project On Library Management System - YouTube. [online] Available
at: https://www.youtube.com/watch?v=TKum0Eg206c [Accessed 2019].
Anon, (n.d.). GitHub - prabhakar267/library-management-system: An .... [online] Available
at: https://github.com/prabhakar267/library-management-system [Accessed 2019].
Anon, (n.d.). How to create an Android based library management system .... [online]
Available at: https://www.quora.com/How-do-I-create-an-Android-based-library-
management-system-I-dont-need-source-code-but-full-method-Im-learning-Java-and-this-
will-be-my-first-project [Accessed 2019].
Anon, (n.d.). Java mini projects With Source Code - ProjectsGeek. [online] Available at:
https://projectsgeek.com/ [Accessed 2019].
Anon, (n.d.). Libib.com - Home library management web app. [online] Available at:
https://www.libib.com/ [Accessed 2019].
Anon, (n.d.). Library management application,Android project ideas .... [online] Available
at: https://www.kashipara.com/project/idea/Android/library-management-application_23.html
[Accessed 2019].
Anon, (n.d.). Library Management System - Cochin University of Science .... [online]
Available at: http://dspace.cusat.ac.in/jspui/bitstream/123456789/8218/1/library
%20management%20system.pdf [Accessed 2019].
Anon, (n.d.). Library Management System - Student Project Code. [online] Available at:
http://www.studentprojectcode.com/csharp/library-management-system/ [Accessed 2019].
Anon, (n.d.). Library Management System | Free Source Code & Tutorials. [online]
Available at: https://www.sourcecodester.com/microsoft-access/library-management-
system.html [Accessed 2019].
pg. 53

Anon, (n.d.). Library Management System For Final Year ( PHP, Java, Andriod). [online]
Available at: http://services.lovelycoding.org/library-management-system/ [Accessed 2019].
Anon, (n.d.). Library Management System in Java Swing Project - javatpoint. [online]
Available at: https://www.javatpoint.com/library-management-system-in-java-swing
[Accessed 2019].
Anon, (n.d.). Library Management System Project - 1000projects.org. [online] Available at:
https://1000projects.org/library-management-system-project.html [Accessed 2019].
Anon, (n.d.). Library Management System Project - nevonprojects.com. [online] Available at:
https://nevonprojects.com/e-library-project/ [Accessed 2019].
Anon, (n.d.). Library Management System Project - ProjectsGeek. [online] Available at:
https://projectsgeek.com/2014/02/library-management-system-project.html [Accessed 2019].
Anon, (n.d.). Library Management System Project in Java with Source Code. [online]
Available at: https://1000projects.org/library-management-system-project-in-java-with-
source-code.html [Accessed 2019].
Anon, (n.d.). Library Management System Project Report - Student Projects. [online]
Available at: https://www.studentprojectguide.com/project-report/library-management-
system-project-report/ [Accessed 2019].
Anon, (n.d.). Simple Library Management App In Android + Firebase With .... [online]
Available at: https://www.youtube.com/watch?v=HCQPtRrPPcE [Accessed 2019].
Anon, (n.d.). System | Android Developers. [online] Available at:
https://developer.android.com/reference/java/lang/System [Accessed 2019].
Bannon, L.J., 2009. From human factors to human actors: The role of psychology and
human-computer interaction studies in system design. In Readings in Human–Computer
Interaction(pp. 205-214).
Blanchard, B.S., Fabrycky, W.J. and Fabrycky, W.J., 2016. Systems engineering and
analysis (Vol. 4). Englewood Cliffs, NJ: Prentice Hall.
Czaja, S.J., Rogers, W.A., Fisk, A.D., Charness, N. and Sharit, J., 2009. Designing for older
adults: Principles and creative human factors approaches. CRC press.
Deterding, S., Sicart, M., Nacke, L., O'Hara, K. and Dixon, D., 2011, May. Gamification.
using game-design elements in non-gaming contexts. In CHI'11 extended abstracts on human
factors in computing systems (pp. 2425-2428). ACM.
Kumar, S. and Gupta, P. (2015). Phrase Prioritization Algorithm and Supporting Data
Structure for Retrieval. International Journal of Computer Applications, 126(12), pp.29-35.
pg. 54
Available at: http://services.lovelycoding.org/library-management-system/ [Accessed 2019].
Anon, (n.d.). Library Management System in Java Swing Project - javatpoint. [online]
Available at: https://www.javatpoint.com/library-management-system-in-java-swing
[Accessed 2019].
Anon, (n.d.). Library Management System Project - 1000projects.org. [online] Available at:
https://1000projects.org/library-management-system-project.html [Accessed 2019].
Anon, (n.d.). Library Management System Project - nevonprojects.com. [online] Available at:
https://nevonprojects.com/e-library-project/ [Accessed 2019].
Anon, (n.d.). Library Management System Project - ProjectsGeek. [online] Available at:
https://projectsgeek.com/2014/02/library-management-system-project.html [Accessed 2019].
Anon, (n.d.). Library Management System Project in Java with Source Code. [online]
Available at: https://1000projects.org/library-management-system-project-in-java-with-
source-code.html [Accessed 2019].
Anon, (n.d.). Library Management System Project Report - Student Projects. [online]
Available at: https://www.studentprojectguide.com/project-report/library-management-
system-project-report/ [Accessed 2019].
Anon, (n.d.). Simple Library Management App In Android + Firebase With .... [online]
Available at: https://www.youtube.com/watch?v=HCQPtRrPPcE [Accessed 2019].
Anon, (n.d.). System | Android Developers. [online] Available at:
https://developer.android.com/reference/java/lang/System [Accessed 2019].
Bannon, L.J., 2009. From human factors to human actors: The role of psychology and
human-computer interaction studies in system design. In Readings in Human–Computer
Interaction(pp. 205-214).
Blanchard, B.S., Fabrycky, W.J. and Fabrycky, W.J., 2016. Systems engineering and
analysis (Vol. 4). Englewood Cliffs, NJ: Prentice Hall.
Czaja, S.J., Rogers, W.A., Fisk, A.D., Charness, N. and Sharit, J., 2009. Designing for older
adults: Principles and creative human factors approaches. CRC press.
Deterding, S., Sicart, M., Nacke, L., O'Hara, K. and Dixon, D., 2011, May. Gamification.
using game-design elements in non-gaming contexts. In CHI'11 extended abstracts on human
factors in computing systems (pp. 2425-2428). ACM.
Kumar, S. and Gupta, P. (2015). Phrase Prioritization Algorithm and Supporting Data
Structure for Retrieval. International Journal of Computer Applications, 126(12), pp.29-35.
pg. 54
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Oinas-Kukkonen, H. and Harjumaa, M., 2009. Persuasive systems design: Key issues,
process model, and system features. Communications of the Association for Information
Systems, 24(1), p.28.
Proctor, R.W. and Van Zandt, T., 2018. Human factors in simple and complex systems. CRC
press.
Sheridan, T.B., 2012. Humans and automation: System design and research issues. Human
Factors and Ergonomics Society.
Stanton, N.A., Salmon, P.M., Rafferty, L.A., Walker, G.H., Baber, C. and Jenkins, D.P.,
2017. Human factors methods: a practical guide for engineering and design. CRC Press.
Wiegmann, D.A. and Shappell, S.A., 2017. A human error approach to aviation accident
analysis: The human factors analysis and classification system. Routledge.
Woodson, W.E., Tillman, B. and Tillman, P., 2010. Human factors design handbook:
information and guidelines for the design of systems, facilities, equipment, and products for
human use.
Yang, S., Chen, A. and Chen, H. (2017). Seismic data filtering using non-local means
algorithm based on structure tensor. Open Geosciences, 9(1).
Zhang, B., Tang, X., Yang, Y. and YAan, W. (2010). Sub-region data structure and its
composition algorithm in pattern generator. Journal of Computer Applications, 29(12),
pp.3314-3316.
pg. 55
process model, and system features. Communications of the Association for Information
Systems, 24(1), p.28.
Proctor, R.W. and Van Zandt, T., 2018. Human factors in simple and complex systems. CRC
press.
Sheridan, T.B., 2012. Humans and automation: System design and research issues. Human
Factors and Ergonomics Society.
Stanton, N.A., Salmon, P.M., Rafferty, L.A., Walker, G.H., Baber, C. and Jenkins, D.P.,
2017. Human factors methods: a practical guide for engineering and design. CRC Press.
Wiegmann, D.A. and Shappell, S.A., 2017. A human error approach to aviation accident
analysis: The human factors analysis and classification system. Routledge.
Woodson, W.E., Tillman, B. and Tillman, P., 2010. Human factors design handbook:
information and guidelines for the design of systems, facilities, equipment, and products for
human use.
Yang, S., Chen, A. and Chen, H. (2017). Seismic data filtering using non-local means
algorithm based on structure tensor. Open Geosciences, 9(1).
Zhang, B., Tang, X., Yang, Y. and YAan, W. (2010). Sub-region data structure and its
composition algorithm in pattern generator. Journal of Computer Applications, 29(12),
pp.3314-3316.
pg. 55
1 out of 56
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





