Online Shopping System Design
VerifiedAdded on 2023/03/20
|19
|4748
|66
AI Summary
This document discusses the design phase of the software development lifecycle (SDLC) for an online shopping system. It covers the goals, architectural design, and database design. It also provides insights into the development process and the technologies used.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Online Shopping System 1
Online Shopping System
By (Name)
The Name of the Class (Course)
Professor (Tutor)
The Name of the School (University)
The City and State where it is located
The Date
Online Shopping System
By (Name)
The Name of the Class (Course)
Professor (Tutor)
The Name of the School (University)
The City and State where it is located
The Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Online Shopping System 2
Online Shopping System
Design
The design phase of the software development lifecycle (SDLC) transforms software
requirements into detailed specifications by covering all aspects of the systems as defined during
the requirement engineering and data modeling phases (Yang, et al., 2008). A ‘tangible' system is
developed following a suitable software development methodology to meet or to satisfy all user
requirements that were elicited during the initial development phases. At this stage, the
development team assesses and plans for security risks and countermeasures, and aims at getting
approval to continue with the next phase in the lifecycle - development phase by transforming
the requirements into a complete into complete and detailed system design specifications and
upon its completion, the development phase takes root.
The project team has to take critical decisions regarding system design approach,
execution of decisions and how these decisions are to be continued based on the identified
system needs. Consultations held with technical resources and operations staff help the
development team to identify all technical issues related to the installation, operations and
maintenance phase of the software (Dawson, 2015). Software deliverables from this stage create
a universal system understanding among all stakeholders and serve as reminders for critical
milestones throughout the project implementation phase. These deliverables also serve as a
mapping that directs the implementation phase by suggesting best design practices.
Successful design is founded on strict adherence to standards and applicable software
laws and ethics. This phase is brought to conclusion with the team delivering: system design
documentation, system's security consensus document, security plans, and data and disaster
Online Shopping System
Design
The design phase of the software development lifecycle (SDLC) transforms software
requirements into detailed specifications by covering all aspects of the systems as defined during
the requirement engineering and data modeling phases (Yang, et al., 2008). A ‘tangible' system is
developed following a suitable software development methodology to meet or to satisfy all user
requirements that were elicited during the initial development phases. At this stage, the
development team assesses and plans for security risks and countermeasures, and aims at getting
approval to continue with the next phase in the lifecycle - development phase by transforming
the requirements into a complete into complete and detailed system design specifications and
upon its completion, the development phase takes root.
The project team has to take critical decisions regarding system design approach,
execution of decisions and how these decisions are to be continued based on the identified
system needs. Consultations held with technical resources and operations staff help the
development team to identify all technical issues related to the installation, operations and
maintenance phase of the software (Dawson, 2015). Software deliverables from this stage create
a universal system understanding among all stakeholders and serve as reminders for critical
milestones throughout the project implementation phase. These deliverables also serve as a
mapping that directs the implementation phase by suggesting best design practices.
Successful design is founded on strict adherence to standards and applicable software
laws and ethics. This phase is brought to conclusion with the team delivering: system design
documentation, system's security consensus document, security plans, and data and disaster

Online Shopping System 3
retention plans. They also define and initiate unit and integration plans, conversion documents
and the implementation plans. The system design documents outline is used to specify the
construction details of the system and how each of the components interact with each other and
external entities as well as the interfaces through which these interactions take place. The
system's security architecture, policies, security tests, and assessments any risks are also
included.
System design begins by reviewing the requirements as elicited during the requirements
engineering phase, and cascades through the phases of monitoring project performance, updating
and performing management activities, and submitting periodical reviews of updates. Design
activities are then initiated and are followed by a revalidation of the project's scope. Throughout
the designing processes, the requirement traceability matrix is constantly updated to ensure that
design for all requirements is satisfactorily met. Risk management activities are periodically
conducted to identify all project risk factors, determine their qualitative and quantitative effects,
and provide methods for risk mitigation, transfer and/or avoidance and to provide a definition of
risk tracking procedures and how response plans are to be executed. It must be understood that
after ambiguous requirements- attributed to most projects’ failure, poor design principles also
lead to projects’ failure (Whitten, et al., 2000). Decisions made at this phase greatly affect the
technology used, the project's framework, the implementation phase, and change management
activities which ensure adherence to design principles and standards.
Design goals
The design of the online shopping system involved the design of all forms of listing the
products, products searching bar, and the display of complete specification and products’
descriptions. It also involved the design of an interactive system that enables clients and admins
retention plans. They also define and initiate unit and integration plans, conversion documents
and the implementation plans. The system design documents outline is used to specify the
construction details of the system and how each of the components interact with each other and
external entities as well as the interfaces through which these interactions take place. The
system's security architecture, policies, security tests, and assessments any risks are also
included.
System design begins by reviewing the requirements as elicited during the requirements
engineering phase, and cascades through the phases of monitoring project performance, updating
and performing management activities, and submitting periodical reviews of updates. Design
activities are then initiated and are followed by a revalidation of the project's scope. Throughout
the designing processes, the requirement traceability matrix is constantly updated to ensure that
design for all requirements is satisfactorily met. Risk management activities are periodically
conducted to identify all project risk factors, determine their qualitative and quantitative effects,
and provide methods for risk mitigation, transfer and/or avoidance and to provide a definition of
risk tracking procedures and how response plans are to be executed. It must be understood that
after ambiguous requirements- attributed to most projects’ failure, poor design principles also
lead to projects’ failure (Whitten, et al., 2000). Decisions made at this phase greatly affect the
technology used, the project's framework, the implementation phase, and change management
activities which ensure adherence to design principles and standards.
Design goals
The design of the online shopping system involved the design of all forms of listing the
products, products searching bar, and the display of complete specification and products’
descriptions. It also involved the design of an interactive system that enables clients and admins

Online Shopping System 4
alike to filter products based on different parameters and that which decreases data exchanges
between system servers and the clients.
Architectural design
The above contextual diagram identifies all the information provided to the system and
that which is received from the system- represented by the arrows. Sources and sinks of the
information are represented as closed boxes. This implies that the clients will use graphical
interfaces to interact with the application.
The agile development methodology will be used in during the development phase since
it requires less planning and it works by dividing complex problems into smaller manageable
tasks which are implemented incrementally (Grässle, et al., 2005). The software development
lifecycle (SDLC) based on agile methodology consists of requirement engineering, analysis,
design, coding, testing and maintenance phases. Agile methodology is an iterative process and
alike to filter products based on different parameters and that which decreases data exchanges
between system servers and the clients.
Architectural design
The above contextual diagram identifies all the information provided to the system and
that which is received from the system- represented by the arrows. Sources and sinks of the
information are represented as closed boxes. This implies that the clients will use graphical
interfaces to interact with the application.
The agile development methodology will be used in during the development phase since
it requires less planning and it works by dividing complex problems into smaller manageable
tasks which are implemented incrementally (Grässle, et al., 2005). The software development
lifecycle (SDLC) based on agile methodology consists of requirement engineering, analysis,
design, coding, testing and maintenance phases. Agile methodology is an iterative process and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Online Shopping System 5
creates room for updates to be made according to customer needs (Sommerville, 2015). This is a
great development approach that not only simplifies the development work but also makes the
design process a very flexible one. Project team members can review and determine if what they
are building is likely to meet customer specifications and adjust accordingly (Sharma, et al.,
2012). Agile methodology can, therefore, be described as being an iterative and modular
development method. Other characteristics are incremental, adaptive, convergence,
collaborative, people oriented and parsimony.
Modular Approach
Among the modules that were included in the system include shop products, shopping
cart, and the products' description module. The shop products module runs when clients visit the
online shopping system's home page or when they search for products based on their preferred
parameters. This part of the application will be used to display all available products based on
their categories or type and the search parameters used by the clients. Search parameters to be
used include product type, brand, manufacturer, price, size, and color among other parameters.
The products’ description module will be accessed when users click on various items available in
the system. From this module, detailed description of the products including price, name, brand
and/models, manufacturer, and related purchase conditions. Additionally, clients who have used
or purchased these products before will have the option of writing a review or rating them; these
reviews are to be made visible to all other clients. The shopping cart module will be used by
clients and will consist of all items that clients are willing to buy from the firm. To be included in
this module are the functionalities of adding the number of items that the clients want to buy per
product and the capability of removing an item from the cart all the same.
creates room for updates to be made according to customer needs (Sommerville, 2015). This is a
great development approach that not only simplifies the development work but also makes the
design process a very flexible one. Project team members can review and determine if what they
are building is likely to meet customer specifications and adjust accordingly (Sharma, et al.,
2012). Agile methodology can, therefore, be described as being an iterative and modular
development method. Other characteristics are incremental, adaptive, convergence,
collaborative, people oriented and parsimony.
Modular Approach
Among the modules that were included in the system include shop products, shopping
cart, and the products' description module. The shop products module runs when clients visit the
online shopping system's home page or when they search for products based on their preferred
parameters. This part of the application will be used to display all available products based on
their categories or type and the search parameters used by the clients. Search parameters to be
used include product type, brand, manufacturer, price, size, and color among other parameters.
The products’ description module will be accessed when users click on various items available in
the system. From this module, detailed description of the products including price, name, brand
and/models, manufacturer, and related purchase conditions. Additionally, clients who have used
or purchased these products before will have the option of writing a review or rating them; these
reviews are to be made visible to all other clients. The shopping cart module will be used by
clients and will consist of all items that clients are willing to buy from the firm. To be included in
this module are the functionalities of adding the number of items that the clients want to buy per
product and the capability of removing an item from the cart all the same.
Online Shopping System 6
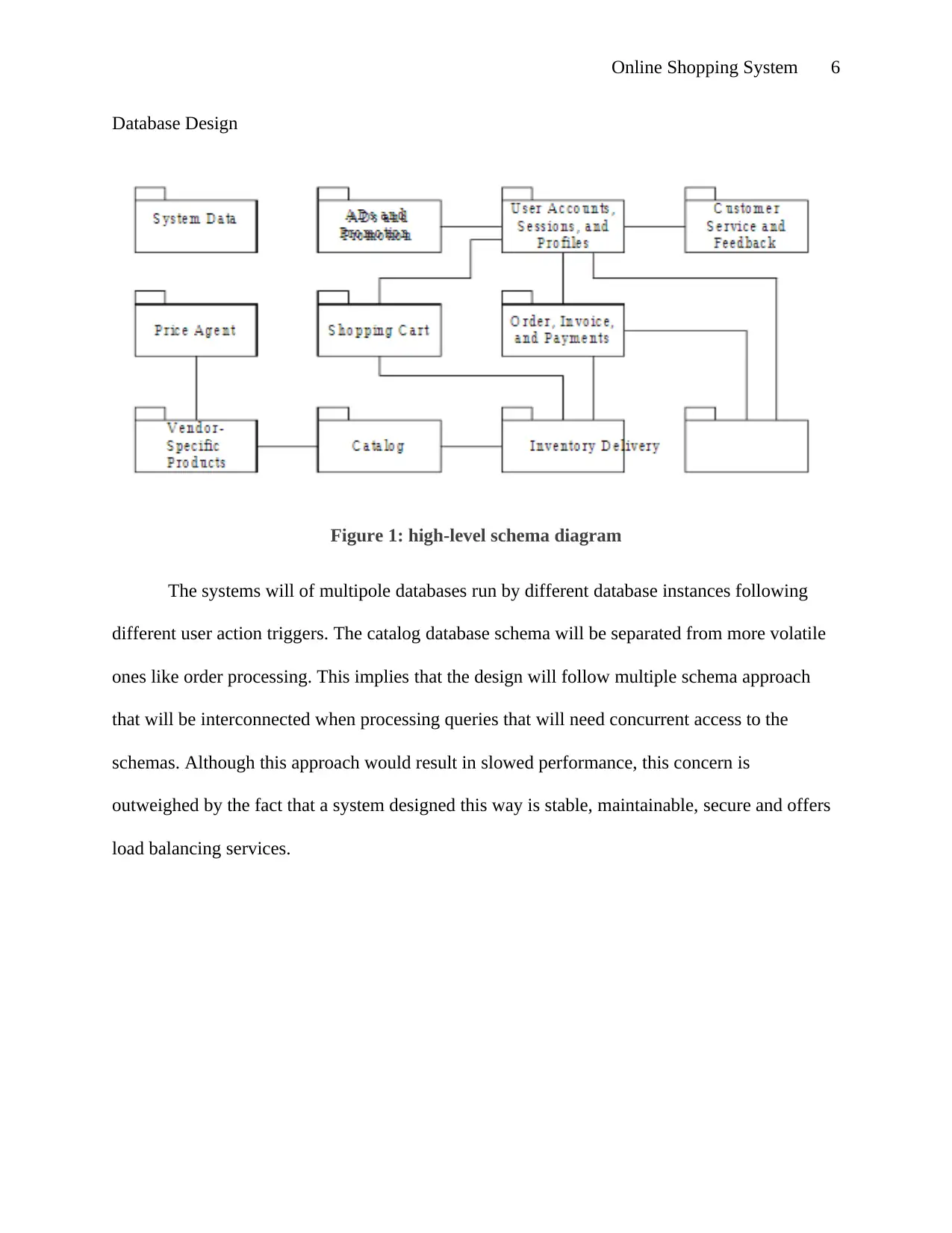
Database Design
Figure 1: high-level schema diagram
The systems will of multipole databases run by different database instances following
different user action triggers. The catalog database schema will be separated from more volatile
ones like order processing. This implies that the design will follow multiple schema approach
that will be interconnected when processing queries that will need concurrent access to the
schemas. Although this approach would result in slowed performance, this concern is
outweighed by the fact that a system designed this way is stable, maintainable, secure and offers
load balancing services.
Database Design
Figure 1: high-level schema diagram
The systems will of multipole databases run by different database instances following
different user action triggers. The catalog database schema will be separated from more volatile
ones like order processing. This implies that the design will follow multiple schema approach
that will be interconnected when processing queries that will need concurrent access to the
schemas. Although this approach would result in slowed performance, this concern is
outweighed by the fact that a system designed this way is stable, maintainable, secure and offers
load balancing services.
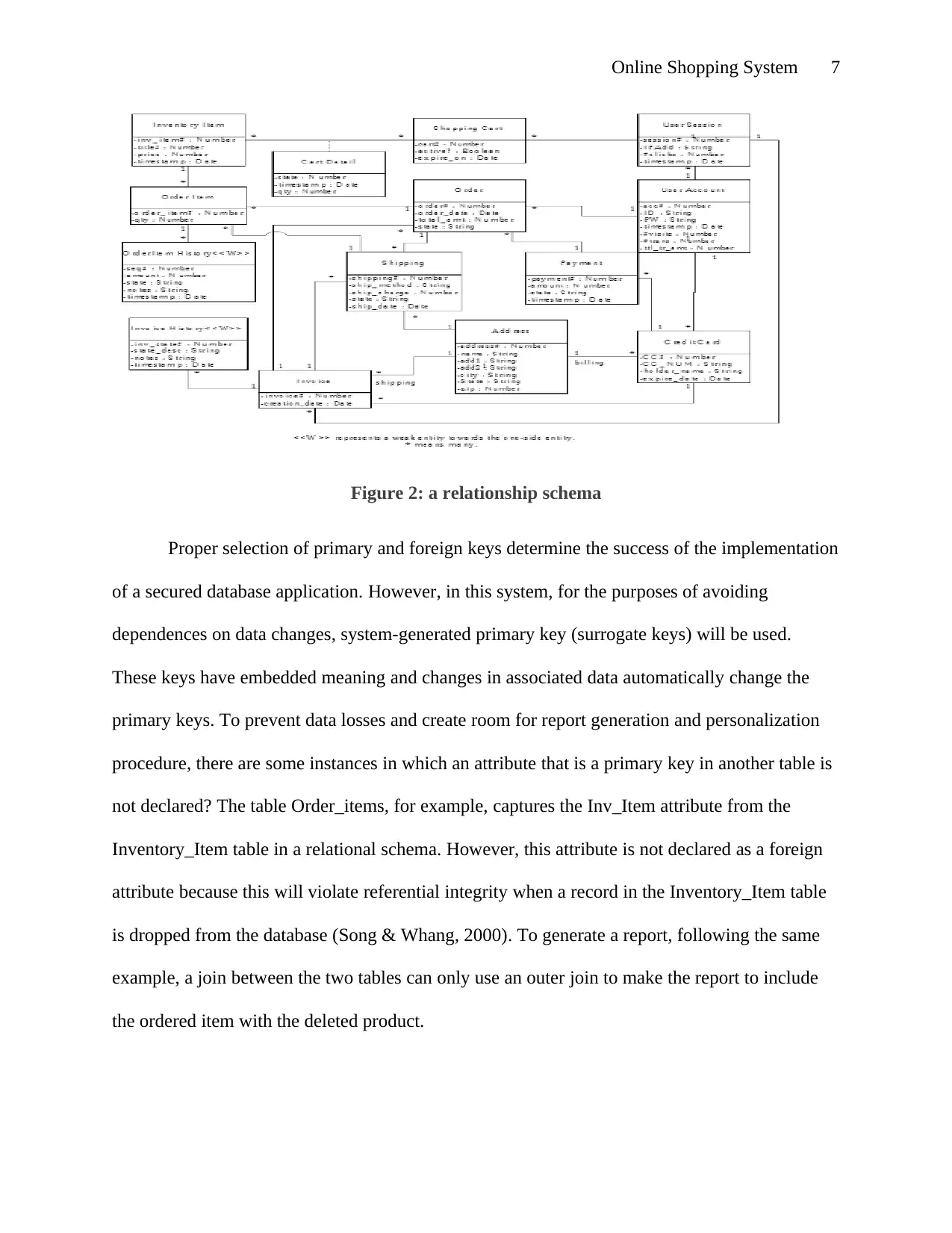
Online Shopping System 7
Figure 2: a relationship schema
Proper selection of primary and foreign keys determine the success of the implementation
of a secured database application. However, in this system, for the purposes of avoiding
dependences on data changes, system-generated primary key (surrogate keys) will be used.
These keys have embedded meaning and changes in associated data automatically change the
primary keys. To prevent data losses and create room for report generation and personalization
procedure, there are some instances in which an attribute that is a primary key in another table is
not declared? The table Order_items, for example, captures the Inv_Item attribute from the
Inventory_Item table in a relational schema. However, this attribute is not declared as a foreign
attribute because this will violate referential integrity when a record in the Inventory_Item table
is dropped from the database (Song & Whang, 2000). To generate a report, following the same
example, a join between the two tables can only use an outer join to make the report to include
the ordered item with the deleted product.
Figure 2: a relationship schema
Proper selection of primary and foreign keys determine the success of the implementation
of a secured database application. However, in this system, for the purposes of avoiding
dependences on data changes, system-generated primary key (surrogate keys) will be used.
These keys have embedded meaning and changes in associated data automatically change the
primary keys. To prevent data losses and create room for report generation and personalization
procedure, there are some instances in which an attribute that is a primary key in another table is
not declared? The table Order_items, for example, captures the Inv_Item attribute from the
Inventory_Item table in a relational schema. However, this attribute is not declared as a foreign
attribute because this will violate referential integrity when a record in the Inventory_Item table
is dropped from the database (Song & Whang, 2000). To generate a report, following the same
example, a join between the two tables can only use an outer join to make the report to include
the ordered item with the deleted product.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Online Shopping System 8
The relationship between order and OrderItem is a one-to-many relationship. The
OrderItem table is modeled as a weak entity of the Order table. As such, the primary key in the
OrderItem table will be made as a combination of the order number and a sequence of order
numbers within the order number. Other databases not included in this schema are database
tables that will be used store information related to customers- including their personal
information and shipping addresses.
Development
Before the actual design of the online shopping system was realized, a few user interfaces
were constructed to help in the visualization of the interactions that were expected to be taking
place once the system go live (Martin, et al., 2009). The interactions were modelled from user
activities in the website as they browse products, adding them to shopping carts, view
descriptions and reviews and initiate purchase transactions.
System Implementation Technologies
The purpose of this project undertaking is to develop an online shopping system to be
used in the selling of various commodities via the internet. A web server hosting the website site
will contacted when clients types the system’s URL (Universal Resource Link) in their PCs’
address fields of browser. The information will be accessed from the internet information service
(IIS) in the form of .NET framework. IIS, the web server in this case will be accepting user
requests and return the requested resources in form of hypertext transfer protocol (HTTP)
messages. Before replying to clients’ requests, the web server first decides how to process
individual request, and its decisions are based on the requested files’ extensions. Requests for
files with .aspx and .ascx extensions are, for example, handled by an ASP.NET web engine. The
The relationship between order and OrderItem is a one-to-many relationship. The
OrderItem table is modeled as a weak entity of the Order table. As such, the primary key in the
OrderItem table will be made as a combination of the order number and a sequence of order
numbers within the order number. Other databases not included in this schema are database
tables that will be used store information related to customers- including their personal
information and shipping addresses.
Development
Before the actual design of the online shopping system was realized, a few user interfaces
were constructed to help in the visualization of the interactions that were expected to be taking
place once the system go live (Martin, et al., 2009). The interactions were modelled from user
activities in the website as they browse products, adding them to shopping carts, view
descriptions and reviews and initiate purchase transactions.
System Implementation Technologies
The purpose of this project undertaking is to develop an online shopping system to be
used in the selling of various commodities via the internet. A web server hosting the website site
will contacted when clients types the system’s URL (Universal Resource Link) in their PCs’
address fields of browser. The information will be accessed from the internet information service
(IIS) in the form of .NET framework. IIS, the web server in this case will be accepting user
requests and return the requested resources in form of hypertext transfer protocol (HTTP)
messages. Before replying to clients’ requests, the web server first decides how to process
individual request, and its decisions are based on the requested files’ extensions. Requests for
files with .aspx and .ascx extensions are, for example, handled by an ASP.NET web engine. The

Online Shopping System 9
ASP.NET engine accesses the requested file, and where necessary, it contacts database
application through the ADO.NET for the required file before routing its information back to
then clients.
Internet Information Services (IIS)
The IIS is an internet service used for machines running on Windows operating systems.
Originally, it was supplied for use with Windows NT Option Pack but was later integrated with
Windows 2000 and Windows 2003 Server applications. Versions 8 and 10 (and their various
updates) include File Transfer Protocol (FTP) servers, Simple Mail Transfer Protocol (SMTP)
and the HTTP/HTTPS application layer protocols.
The ASP.NET
This refers to a programming framework which is built on common language runtime and
that which is used on different server machines to build powerful web applications. This
framework is advantageous in that it is compatible with the .NET framework. The compatibility
between the two enables developers to enjoy the benefits of faster web applications, powerful
database-driven functionalities and memory leak and crash protection. Through the common
language runtime (CLR) the programming framework is able to support codes written VB.NET,
C# and Jscript.Net among other languages.
An ASP.NET application is made up of two seperate authentication layers which flow
through the internet information service being finally handed over to the ASP.NET. Based on the
nature of a request made, the IIS decides to either permit or deny access even before the
ASP.NET is made aware of the request. The authentication process begins with the IIS
determining if incoming requests are from allowable IP addresses within the domain. It denies
ASP.NET engine accesses the requested file, and where necessary, it contacts database
application through the ADO.NET for the required file before routing its information back to
then clients.
Internet Information Services (IIS)
The IIS is an internet service used for machines running on Windows operating systems.
Originally, it was supplied for use with Windows NT Option Pack but was later integrated with
Windows 2000 and Windows 2003 Server applications. Versions 8 and 10 (and their various
updates) include File Transfer Protocol (FTP) servers, Simple Mail Transfer Protocol (SMTP)
and the HTTP/HTTPS application layer protocols.
The ASP.NET
This refers to a programming framework which is built on common language runtime and
that which is used on different server machines to build powerful web applications. This
framework is advantageous in that it is compatible with the .NET framework. The compatibility
between the two enables developers to enjoy the benefits of faster web applications, powerful
database-driven functionalities and memory leak and crash protection. Through the common
language runtime (CLR) the programming framework is able to support codes written VB.NET,
C# and Jscript.Net among other languages.
An ASP.NET application is made up of two seperate authentication layers which flow
through the internet information service being finally handed over to the ASP.NET. Based on the
nature of a request made, the IIS decides to either permit or deny access even before the
ASP.NET is made aware of the request. The authentication process begins with the IIS
determining if incoming requests are from allowable IP addresses within the domain. It denies

Online Shopping System 10
access to all ‘blacklisted’ IP addresses. Where it is not configured to authenticate user requests,
IIS performs self-authenticates user requests and by default, allows all anonymous access
requests. A request that is passed over to the ASP.NET is processed to determine if there has
been an impersonation. ASP.NET in this situation act as the original authenticated user.
MySQL Database
The backend database of the system was developed using MySQL which is a relational,
secure, fast, reliable, easy to use open-source database management system. Each of the MySQL
threads handles a single incoming request while an extra thread runs to manage the connection.
This means that multiple clients can perform simultaneous read operations concurrently. The
MySQL database was connected with the ASP.NET application using an Open Database
Connectivity (ODBC). An ODBC driver library is used to implement functions that are
supported by ADBC API. ODBC drivers process function calls made by ODBC and submit all
SQL requests to MySQL server and sends the results back to the application.
The below diagram represent a data-driven web application that use HTML documents to
get inputs and requests from users before submitting them to a web server. The web server
processes user inputs and dynamically composes a web page to reply. Programs running on the
server can either be machine language scripts or executed when clients’ requests are received on
the server side.
access to all ‘blacklisted’ IP addresses. Where it is not configured to authenticate user requests,
IIS performs self-authenticates user requests and by default, allows all anonymous access
requests. A request that is passed over to the ASP.NET is processed to determine if there has
been an impersonation. ASP.NET in this situation act as the original authenticated user.
MySQL Database
The backend database of the system was developed using MySQL which is a relational,
secure, fast, reliable, easy to use open-source database management system. Each of the MySQL
threads handles a single incoming request while an extra thread runs to manage the connection.
This means that multiple clients can perform simultaneous read operations concurrently. The
MySQL database was connected with the ASP.NET application using an Open Database
Connectivity (ODBC). An ODBC driver library is used to implement functions that are
supported by ADBC API. ODBC drivers process function calls made by ODBC and submit all
SQL requests to MySQL server and sends the results back to the application.
The below diagram represent a data-driven web application that use HTML documents to
get inputs and requests from users before submitting them to a web server. The web server
processes user inputs and dynamically composes a web page to reply. Programs running on the
server can either be machine language scripts or executed when clients’ requests are received on
the server side.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Online Shopping System 11
The development of the web-based application was based on client-server architecture
model that uses hypertext markup language (HTML), PHP, Jscript, JSon and CSS. The HHTP
protocol used in the development of the website is a stateless protocol meaning that it does not
make any association between one transaction and another. Each and every transaction is treated
as a discrete event in the system.
For the purposes of establishing database connections, ASP.NET uses ActiveX Data
Objects.NET (ADO.NET) technology to connect to the application’s database. Classic pages
developed on the ASP framework use ADO to access and modify database contents. While this
is a fairly easy to implement access interface, ADO suffers from the lack of an updated model for
use in accessing data plus other associated many limitations. Such as inability to transmit data in
a way that makes it universally available. To overcome these limitations, ADO.NET was
developed as a more scalable technology. ADO.NET technology uses core objects to allow
systems’ developers to work with data easily- data reader and the data set. For all .NET data
access pages, before connecting to a database, developers first have to import all the necessary
namespaces that would allow them to work with all the required objects efficiently. Namespace
in .NET refers to a set of classes that can be used when creating applications. The .NET
Framework has about thirty five thousand classes all which can easily be accessed through a
namespace. The online shopping system will be using a technology known as Open Data Base
The development of the web-based application was based on client-server architecture
model that uses hypertext markup language (HTML), PHP, Jscript, JSon and CSS. The HHTP
protocol used in the development of the website is a stateless protocol meaning that it does not
make any association between one transaction and another. Each and every transaction is treated
as a discrete event in the system.
For the purposes of establishing database connections, ASP.NET uses ActiveX Data
Objects.NET (ADO.NET) technology to connect to the application’s database. Classic pages
developed on the ASP framework use ADO to access and modify database contents. While this
is a fairly easy to implement access interface, ADO suffers from the lack of an updated model for
use in accessing data plus other associated many limitations. Such as inability to transmit data in
a way that makes it universally available. To overcome these limitations, ADO.NET was
developed as a more scalable technology. ADO.NET technology uses core objects to allow
systems’ developers to work with data easily- data reader and the data set. For all .NET data
access pages, before connecting to a database, developers first have to import all the necessary
namespaces that would allow them to work with all the required objects efficiently. Namespace
in .NET refers to a set of classes that can be used when creating applications. The .NET
Framework has about thirty five thousand classes all which can easily be accessed through a
namespace. The online shopping system will be using a technology known as Open Data Base

Online Shopping System 12
Connectivity (ODBC) to access the database applications; therefore all the important namespaces
must be imported first.
Implementation
Implementation and coding represent the third phase of the Software Development Life
Cycle (SDLC). This phase is preceded by requirements gathering, analysis, and software
designing phases. The system design phase paves the way for the onset of the implementation
and coding phase. The implementation process is characterized by the deployment of the new
system in its target environment. The phase is facilitated by support activities such as end user
training and preparation to change the system maintenance control over to the maintenance
personnel.
At this stage, the actual product is realized and delivered to the client. It is the most
fascinating phase since the customer's idea for the project is turned into tangible product. The
output in this particular stage is the functional specification which files all the details of the
functions implemented in the software. A software product is developed according to
specifications of the subset of design passed from the design stage. Functional specifications are
prepared for every subset included in the implementation.
For the coding process to be fully streamlined, it solely depends on the software
application being designed properly and the requirements that have been gathered accurately. In
addition, when the correct information regarding the proposed software is gathered upfront from
the customer, projects teams are able to efficiently meet the coding deadlines. The goal of the
coding phase is to translate the designed software of the system into a given programming
language. For a particular design given, coding facilitates its implementation in the best possible
Connectivity (ODBC) to access the database applications; therefore all the important namespaces
must be imported first.
Implementation
Implementation and coding represent the third phase of the Software Development Life
Cycle (SDLC). This phase is preceded by requirements gathering, analysis, and software
designing phases. The system design phase paves the way for the onset of the implementation
and coding phase. The implementation process is characterized by the deployment of the new
system in its target environment. The phase is facilitated by support activities such as end user
training and preparation to change the system maintenance control over to the maintenance
personnel.
At this stage, the actual product is realized and delivered to the client. It is the most
fascinating phase since the customer's idea for the project is turned into tangible product. The
output in this particular stage is the functional specification which files all the details of the
functions implemented in the software. A software product is developed according to
specifications of the subset of design passed from the design stage. Functional specifications are
prepared for every subset included in the implementation.
For the coding process to be fully streamlined, it solely depends on the software
application being designed properly and the requirements that have been gathered accurately. In
addition, when the correct information regarding the proposed software is gathered upfront from
the customer, projects teams are able to efficiently meet the coding deadlines. The goal of the
coding phase is to translate the designed software of the system into a given programming
language. For a particular design given, coding facilitates its implementation in the best possible

Online Shopping System 13
way. Coding affects both testing and maintenance in a great deal. A code that is well written will
reduce both testing and maintenance efforts since the testing and maintenance efforts are much
higher than the cost of coding itself. The goal of coding, therefore, should be aimed at achieving
a reduced and maintenance cost. Thus, during the process of coding, emphasis should be laid on
developing programs that are easy to write. In addition, this process should be simple and
charity-oriented.
The online shopping system design was designed to include both the admin and customer
interfaces. The client interface – also called the front end consisted of all sub-interfaces that
customers will use when interacting with the system. The admin interface comprises of all sub-
interfaces that that is to be used by the administrative staff in the management of the system.
This interface is also called the back end of a system.
Clients’ Interfaces
Home page
This was designed to serve as the starting point for the website and loads by default when
a visit to the website is made. Home pages (default web pages) are located at the root directories
of websites and many web servers allow them to have only one file name. However, the default
name page for the can be customized on IIS and Apache servers. The fact that the homepage
automatically loads from the root directory means that it does not need to have extended name
files. The home page for the online shopping business includes navigation links for other sites,
search bar, constantly changing information, and information regards the webpage. The home
page will also include such information as top-selling items, flash sales, menu, cart, latest
products, promotion offerings, and a link to creating of new accounts. In the footer of the home
way. Coding affects both testing and maintenance in a great deal. A code that is well written will
reduce both testing and maintenance efforts since the testing and maintenance efforts are much
higher than the cost of coding itself. The goal of coding, therefore, should be aimed at achieving
a reduced and maintenance cost. Thus, during the process of coding, emphasis should be laid on
developing programs that are easy to write. In addition, this process should be simple and
charity-oriented.
The online shopping system design was designed to include both the admin and customer
interfaces. The client interface – also called the front end consisted of all sub-interfaces that
customers will use when interacting with the system. The admin interface comprises of all sub-
interfaces that that is to be used by the administrative staff in the management of the system.
This interface is also called the back end of a system.
Clients’ Interfaces
Home page
This was designed to serve as the starting point for the website and loads by default when
a visit to the website is made. Home pages (default web pages) are located at the root directories
of websites and many web servers allow them to have only one file name. However, the default
name page for the can be customized on IIS and Apache servers. The fact that the homepage
automatically loads from the root directory means that it does not need to have extended name
files. The home page for the online shopping business includes navigation links for other sites,
search bar, constantly changing information, and information regards the webpage. The home
page will also include such information as top-selling items, flash sales, menu, cart, latest
products, promotion offerings, and a link to creating of new accounts. In the footer of the home
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Online Shopping System 14
page, such information as recently viewed products, contacts, and FAQs (frequently asked
questions) are included.
Login and registration pages
Customers who choose to buy items online will be required to first create an account with
the system through a registration process. Existing customers (plus new ones alike) will be
required to login to the system before they can add any items to their cart. Successful registration
will depend on the correctness (data validity) of user input and will be finalized with the system
sending an automated account activation link to the client. Strong password policy will be
effected to ensure that customers do not use easily guessable passwords which could lead to
security breaches. A link to help clients recover forgotten passwords will also be included in this
module.
Add to cart page
To complete online transactions, items will have to be added to carts and from where the
customers can also view products details by clicking on item’s descriptive name and by placing
the cursor over a product’s images. From the cart, customers can adjust (increase or decrease) the
number of items they want to purchase. From this panel, customers will complete the transaction
by adding/editing shipping information and electronically paying for the products.
Selecting a payment method
The system shall incorporate several payment methods and clients shall be allowed to use
only one method in a single transaction. The customer selects the payment method they want to
use before confirming the order.
page, such information as recently viewed products, contacts, and FAQs (frequently asked
questions) are included.
Login and registration pages
Customers who choose to buy items online will be required to first create an account with
the system through a registration process. Existing customers (plus new ones alike) will be
required to login to the system before they can add any items to their cart. Successful registration
will depend on the correctness (data validity) of user input and will be finalized with the system
sending an automated account activation link to the client. Strong password policy will be
effected to ensure that customers do not use easily guessable passwords which could lead to
security breaches. A link to help clients recover forgotten passwords will also be included in this
module.
Add to cart page
To complete online transactions, items will have to be added to carts and from where the
customers can also view products details by clicking on item’s descriptive name and by placing
the cursor over a product’s images. From the cart, customers can adjust (increase or decrease) the
number of items they want to purchase. From this panel, customers will complete the transaction
by adding/editing shipping information and electronically paying for the products.
Selecting a payment method
The system shall incorporate several payment methods and clients shall be allowed to use
only one method in a single transaction. The customer selects the payment method they want to
use before confirming the order.

Online Shopping System 15
Shopping notification
Once an order has been confirmed by a client, the page will redirect to the home page and
provide the client with a notification thanking them for shopping with the company. An order
that has been confirmed will be displayed on both admin and client side upon which the admin
will take appropriate steps to guarantee successful delivery of the product.
Admin Interface
Admin login page
This module will be so important in the system since it will provide an interface through
which system administrators will manage, control and monitor all activities in taking place in the
system. An admin starts by logging in to the system by providing their user authentication
details- username and password.
Admin’s homepage
After logging in, system admins shall be redirected to a back end front end. This home
page will have a menu that is different from the previously discussed one- category add, manage
or archive category), manufacturers menu, and a product menu from which they can manage and
archive product menu and respond to customers’ orders.
Adding new categories
This module will be used by the admin to add new categories and brand of goods. A new
category becomes published on the website when the admin selects the publish button and can
also delete them by selecting the unpublished button.
Testing
Shopping notification
Once an order has been confirmed by a client, the page will redirect to the home page and
provide the client with a notification thanking them for shopping with the company. An order
that has been confirmed will be displayed on both admin and client side upon which the admin
will take appropriate steps to guarantee successful delivery of the product.
Admin Interface
Admin login page
This module will be so important in the system since it will provide an interface through
which system administrators will manage, control and monitor all activities in taking place in the
system. An admin starts by logging in to the system by providing their user authentication
details- username and password.
Admin’s homepage
After logging in, system admins shall be redirected to a back end front end. This home
page will have a menu that is different from the previously discussed one- category add, manage
or archive category), manufacturers menu, and a product menu from which they can manage and
archive product menu and respond to customers’ orders.
Adding new categories
This module will be used by the admin to add new categories and brand of goods. A new
category becomes published on the website when the admin selects the publish button and can
also delete them by selecting the unpublished button.
Testing

Online Shopping System 16
Testing is a phase in SDLC that is centered on investigation and/or discovery of systems’
capabilities and vulnerabilities. During this phase, attention is shifted from developing the
system to establishing if a right product has been built the right way- following software
development ethics, standards and based on user requirements. The results obtained from the
testing program can thereafter be used to reduce the number of faults, errors and vulnerabilities
within the system application.
Prior to the start of testing, program developers develop a test plans which outlines the
type of testing to be used during testing, the required resources for testing, the testing procedures,
who the testers should be in each stage of testing and the testing scripts. The test scripts are used
to instruct program testers at a given stage to test the software. They test scripts ensure
consistency in the testing the programs. There are various types of testing in the testing used to
determine the correctness of the developed product. They include Quality Assurance (QA)
testing, System Integration Testing (SIT) and User Acceptance Testing (UAT).
Quality Assurance (QA)
This entails testing the software procedures and processes to ensure compliance with
customer requirements/specifications.
System Integration Testing (SIT)
This is a type of software testing done in integrated hardware and software environment
aimed at behavior verification of the system in the new environment. Testing is usually carried
Testing is a phase in SDLC that is centered on investigation and/or discovery of systems’
capabilities and vulnerabilities. During this phase, attention is shifted from developing the
system to establishing if a right product has been built the right way- following software
development ethics, standards and based on user requirements. The results obtained from the
testing program can thereafter be used to reduce the number of faults, errors and vulnerabilities
within the system application.
Prior to the start of testing, program developers develop a test plans which outlines the
type of testing to be used during testing, the required resources for testing, the testing procedures,
who the testers should be in each stage of testing and the testing scripts. The test scripts are used
to instruct program testers at a given stage to test the software. They test scripts ensure
consistency in the testing the programs. There are various types of testing in the testing used to
determine the correctness of the developed product. They include Quality Assurance (QA)
testing, System Integration Testing (SIT) and User Acceptance Testing (UAT).
Quality Assurance (QA)
This entails testing the software procedures and processes to ensure compliance with
customer requirements/specifications.
System Integration Testing (SIT)
This is a type of software testing done in integrated hardware and software environment
aimed at behavior verification of the system in the new environment. Testing is usually carried
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Online Shopping System 17
out in a complete, integrated system, to evaluate its compliance with the specified client
specifications and projected requirements.
User Acceptance Testing
This is usually the last phase in the testing process of the developed software. During this
stage, the software end-users test it to ascertain that it is competent enough to handle the tasks in
the real world scenarios according to the specifications.
Other than the aforementioned functions, testing in SDLC is also done with an aim to
identify the errors, remove hazards related to the software, for verification and validation, to
improve cost, remove any ambiguity, and improve the quality of the standard and to increase
usability.
This type of testing, however, is a multifaceted phase in its own, since it is aimed at
defining the contract between the software developer and the customer. Some of the tests done in
this type of testing include:
i) Usersnap Classic- this provides a solution by asking alpha and beta testers for
feedback. This is an easy UAT solution that helps the QA teams in the verification of
whether a particular solution works for the user. By use of feedback widget, the
testers are able to provide comprehensive feedback about the software prototype.
ii) Contract Acceptance Testing- this simply implies that the software developed has
been subjected a certain testing criterion and the predefined specifications which were
previously agreed upon in the contracting. Project team managers give relevant
criteria and specifications for particular software to be developed. The team also
agrees on testing contract terms.
out in a complete, integrated system, to evaluate its compliance with the specified client
specifications and projected requirements.
User Acceptance Testing
This is usually the last phase in the testing process of the developed software. During this
stage, the software end-users test it to ascertain that it is competent enough to handle the tasks in
the real world scenarios according to the specifications.
Other than the aforementioned functions, testing in SDLC is also done with an aim to
identify the errors, remove hazards related to the software, for verification and validation, to
improve cost, remove any ambiguity, and improve the quality of the standard and to increase
usability.
This type of testing, however, is a multifaceted phase in its own, since it is aimed at
defining the contract between the software developer and the customer. Some of the tests done in
this type of testing include:
i) Usersnap Classic- this provides a solution by asking alpha and beta testers for
feedback. This is an easy UAT solution that helps the QA teams in the verification of
whether a particular solution works for the user. By use of feedback widget, the
testers are able to provide comprehensive feedback about the software prototype.
ii) Contract Acceptance Testing- this simply implies that the software developed has
been subjected a certain testing criterion and the predefined specifications which were
previously agreed upon in the contracting. Project team managers give relevant
criteria and specifications for particular software to be developed. The team also
agrees on testing contract terms.

Online Shopping System 18
iii) Regulation Acceptance Testing- this is more of compliance testing. This particular
type of testing examines whether the software is compliant with the legal and
governmental regulations that are in place.
iv) Operational Readiness Testing- these are tests done to ensure there are workflows
available in place to allow the system or software to be used. They include checking
workflows for backup plans, end-user training, and other maintenance undertakings
and security checks.
v) Black Box Testing- this is usually categorized as functional testing but in most cases,
it falls under User Acceptance Testing (UAT). Black box method of software testing
that analyzes the functionalities without allowing the experts involved access to the
source code structure of the software. Black Box Testing is part of UAT since its tests
share similar principles with UAT. During this test, the user is only aware of the
requirements and specifications that the software should meet and not about any code
bases.
iii) Regulation Acceptance Testing- this is more of compliance testing. This particular
type of testing examines whether the software is compliant with the legal and
governmental regulations that are in place.
iv) Operational Readiness Testing- these are tests done to ensure there are workflows
available in place to allow the system or software to be used. They include checking
workflows for backup plans, end-user training, and other maintenance undertakings
and security checks.
v) Black Box Testing- this is usually categorized as functional testing but in most cases,
it falls under User Acceptance Testing (UAT). Black box method of software testing
that analyzes the functionalities without allowing the experts involved access to the
source code structure of the software. Black Box Testing is part of UAT since its tests
share similar principles with UAT. During this test, the user is only aware of the
requirements and specifications that the software should meet and not about any code
bases.

Online Shopping System 19
Bibliography
Dawson, C. W., 2015. Projects in computing and information systems: a student's guide. 3 ed.
Harlow: Prentice Hall.
Grässle, P., Henriette, B. & Philippe, B., 2005. UML 2. 0 in Action: A Project-based Tutorial.
s.l.:Packt Publishing Ltd.
Martin, R. C., Feathers, M., Ottinger, T. G. J. C. J. & Wampler, K., 2009. Clean code: a
handbook of agile software craftsmanship. 1 ed. Boston: Pearson Education Inc.
Sharma, S., Sarkar, D. & Gupta, D., 2012. Agile processes and methodologies: A conceptual
study. International journal on computer science and Engineering, 4(5), p. 892.
Sommerville, I., 2015. Software Engineering. 10 ed. Harlow: Pearson Education Limited.
Song, I.-Y. & Whang, K.-Y., 2000. Database design for real-world e-commerce systems. IEEE
Data Eng. Bull, 23(1), pp. 23-28.
Whitten, J. L., Bentley, L. D. & Dittman, K. C., 2000. Systems Analysis and Design Methods 5e.
s.l.:McGraw-Hill Higher Education.
Yang, Y. et al., 2008. Phase distribution of software development effort. s.l., ACM, pp. 61-69.
Bibliography
Dawson, C. W., 2015. Projects in computing and information systems: a student's guide. 3 ed.
Harlow: Prentice Hall.
Grässle, P., Henriette, B. & Philippe, B., 2005. UML 2. 0 in Action: A Project-based Tutorial.
s.l.:Packt Publishing Ltd.
Martin, R. C., Feathers, M., Ottinger, T. G. J. C. J. & Wampler, K., 2009. Clean code: a
handbook of agile software craftsmanship. 1 ed. Boston: Pearson Education Inc.
Sharma, S., Sarkar, D. & Gupta, D., 2012. Agile processes and methodologies: A conceptual
study. International journal on computer science and Engineering, 4(5), p. 892.
Sommerville, I., 2015. Software Engineering. 10 ed. Harlow: Pearson Education Limited.
Song, I.-Y. & Whang, K.-Y., 2000. Database design for real-world e-commerce systems. IEEE
Data Eng. Bull, 23(1), pp. 23-28.
Whitten, J. L., Bentley, L. D. & Dittman, K. C., 2000. Systems Analysis and Design Methods 5e.
s.l.:McGraw-Hill Higher Education.
Yang, Y. et al., 2008. Phase distribution of software development effort. s.l., ACM, pp. 61-69.
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





