Operating System - Study Material and Solved Assignments
VerifiedAdded on 2023/06/07
|13
|1244
|355
AI Summary
This document provides study material and solved assignments on Operating System. It covers topics such as deadlock state, fixed and variable length fields, relative and complete file names, and commands like chmod, grep, ls, and mkdir. The bibliography lists relevant sources for further reading.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: OPERATING SYSTEM
Operating System
Name of the Student:
Name of the University:
Author Note
Operating System
Name of the Student:
Name of the University:
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
1
OPERATING SYSTEM
Answer to question number B - Q1
a)
i)
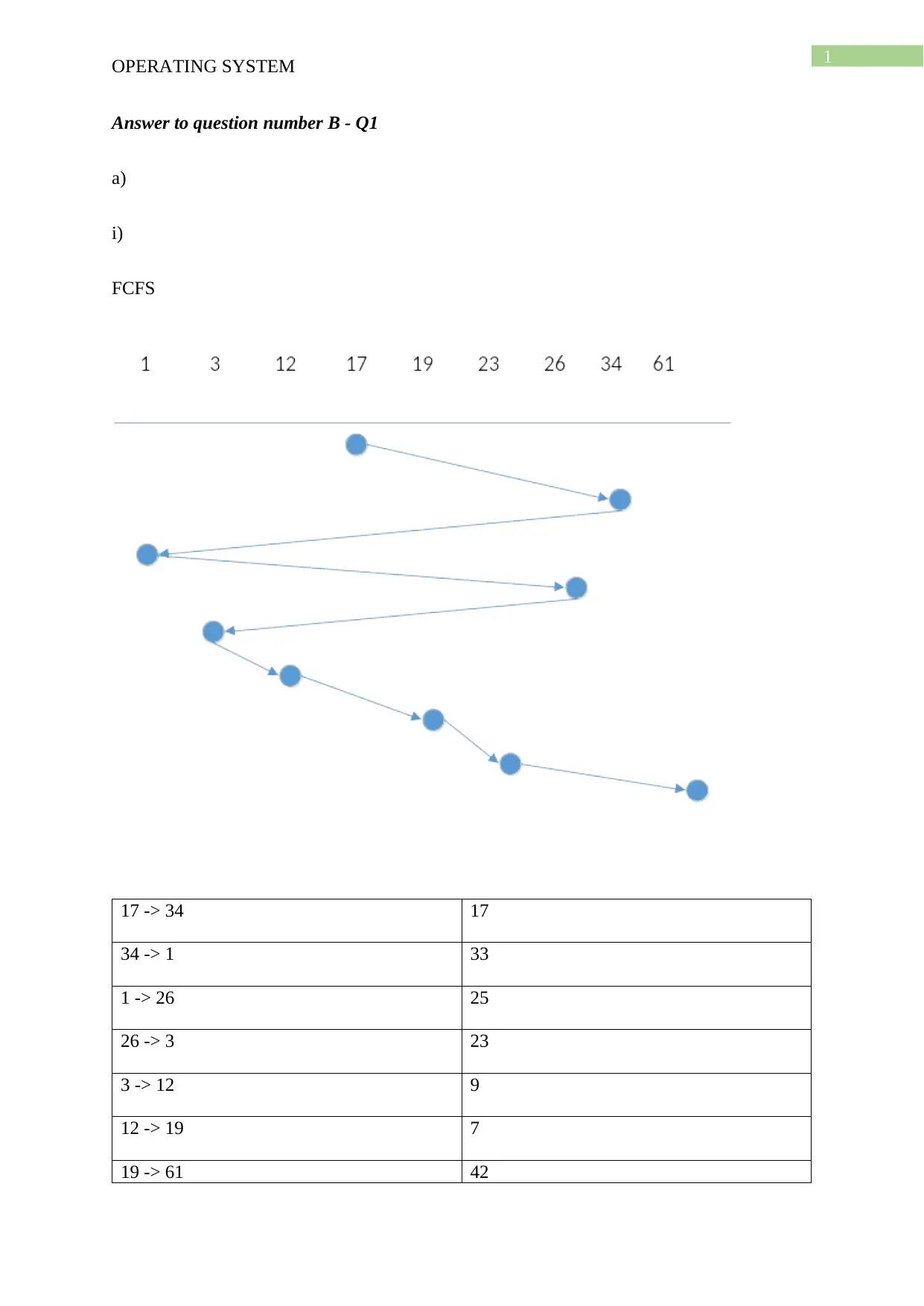
FCFS
17 -> 34 17
34 -> 1 33
1 -> 26 25
26 -> 3 23
3 -> 12 9
12 -> 19 7
19 -> 61 42
OPERATING SYSTEM
Answer to question number B - Q1
a)
i)
FCFS
17 -> 34 17
34 -> 1 33
1 -> 26 25
26 -> 3 23
3 -> 12 9
12 -> 19 7
19 -> 61 42
2
OPERATING SYSTEM
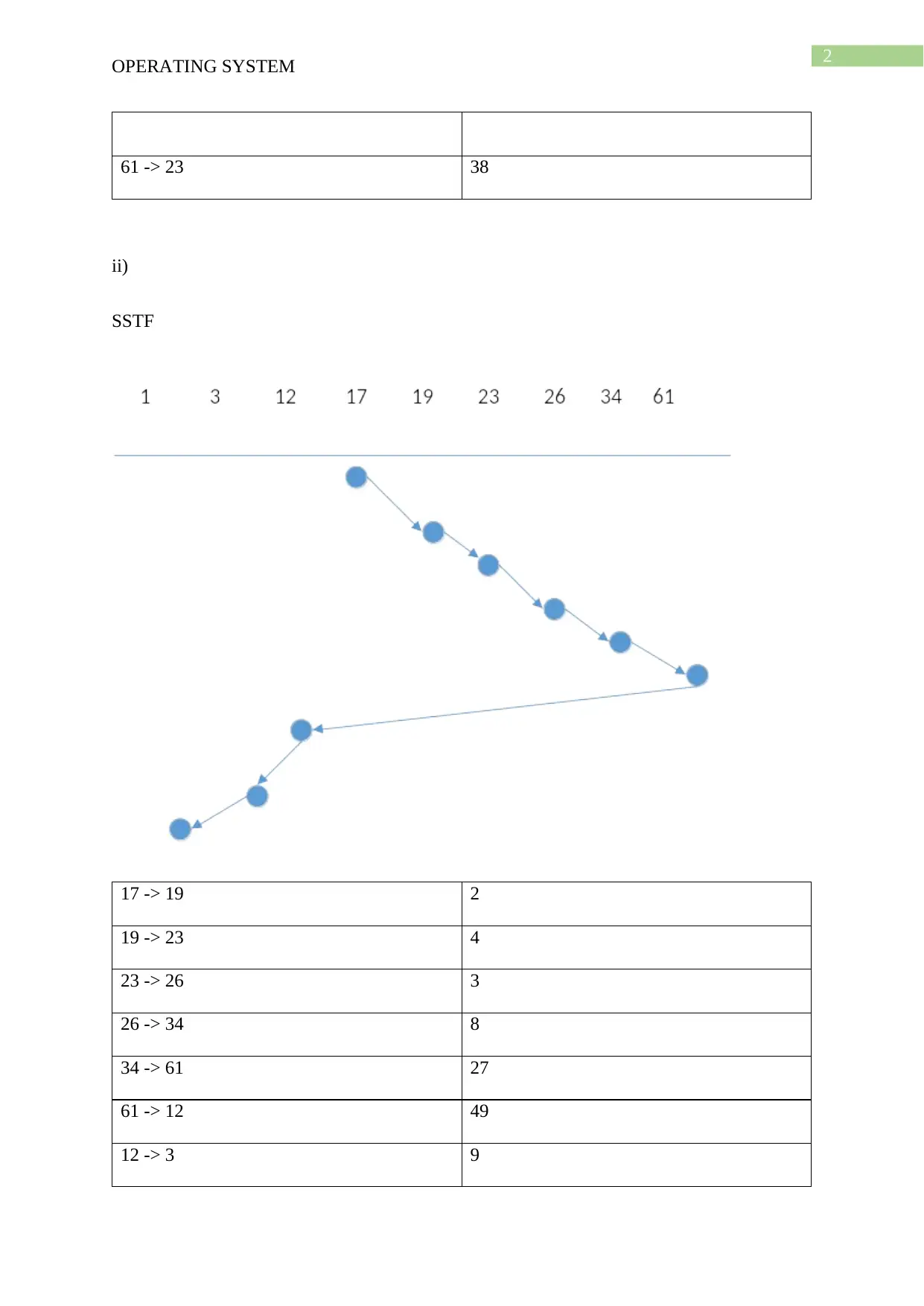
61 -> 23 38
ii)
SSTF
17 -> 19 2
19 -> 23 4
23 -> 26 3
26 -> 34 8
34 -> 61 27
61 -> 12 49
12 -> 3 9
OPERATING SYSTEM
61 -> 23 38
ii)
SSTF
17 -> 19 2
19 -> 23 4
23 -> 26 3
26 -> 34 8
34 -> 61 27
61 -> 12 49
12 -> 3 9
3
OPERATING SYSTEM
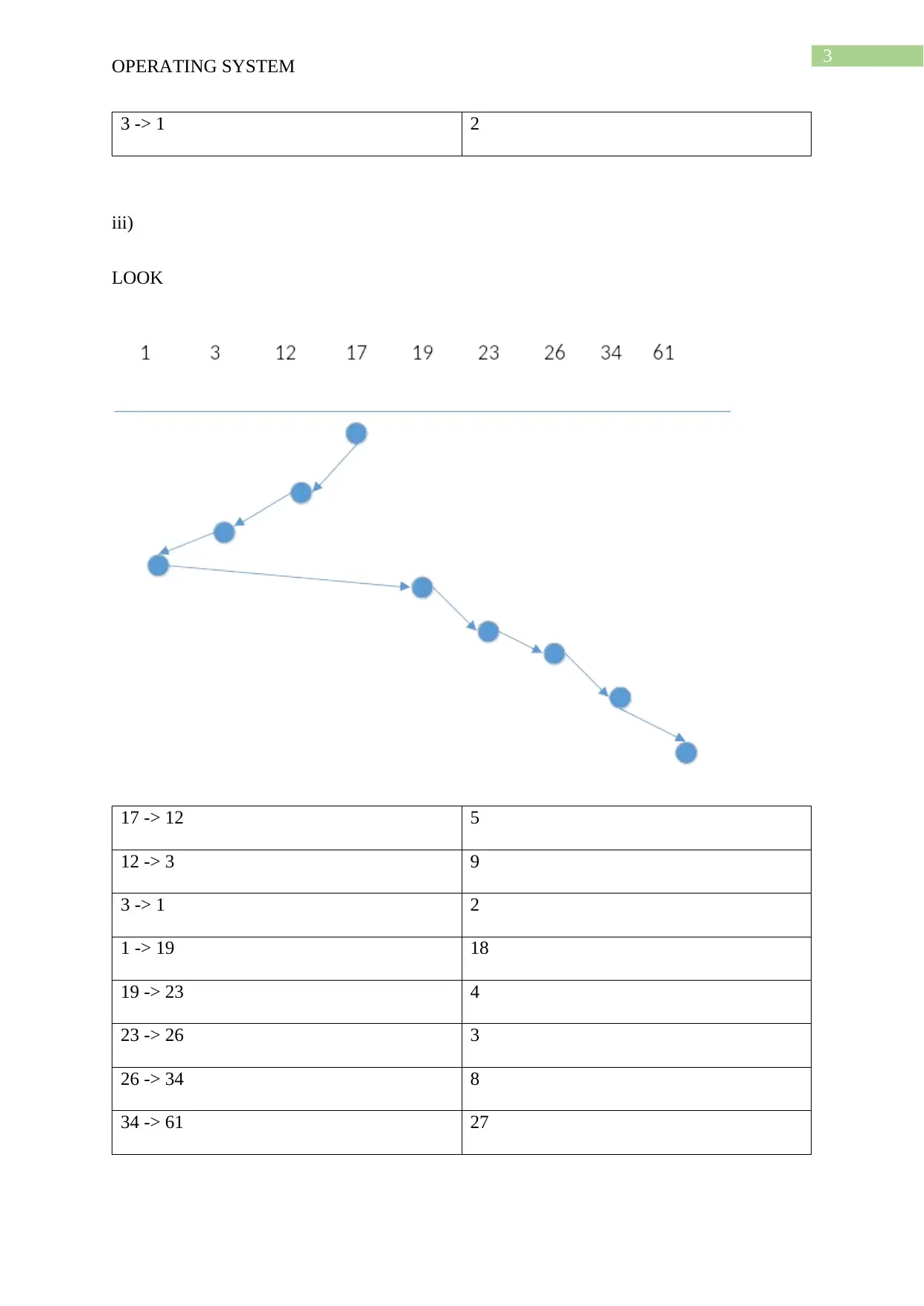
3 -> 1 2
iii)
LOOK
17 -> 12 5
12 -> 3 9
3 -> 1 2
1 -> 19 18
19 -> 23 4
23 -> 26 3
26 -> 34 8
34 -> 61 27
OPERATING SYSTEM
3 -> 1 2
iii)
LOOK
17 -> 12 5
12 -> 3 9
3 -> 1 2
1 -> 19 18
19 -> 23 4
23 -> 26 3
26 -> 34 8
34 -> 61 27
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
OPERATING SYSTEM
b)
i) FCFS
The total number of tracks are: (17 + 33 + 25 + 23 + 9 + 7 + 42 + 38) = 194 tracks
Average number of tracks: (194/8) = 24.25
ii) SSTF
The total number of tracks are: (2 + 4 + 3 + 8 + 27 + 49 + 9 + 2) = 104 tracks
Average no of tracks: (104/ 8) = 13
iii) LOOK
The total number of tracks are: (5 + 9 + 2 + 18 + 4 + 3 + 8 + 27) = 76 tracks
Average no of tracks: (76/ 8) = 9.5
Answer to question number B – Q2
a)
The deadlock state is basically a situation where the set of processes in a blocked state
as each of the processes are holding a resource and waiting to be completed but is unable to
complete as the other process is not able to get the required resource which is again locked by
some other process. This occurs in the cyclic format.
b)
OPERATING SYSTEM
b)
i) FCFS
The total number of tracks are: (17 + 33 + 25 + 23 + 9 + 7 + 42 + 38) = 194 tracks
Average number of tracks: (194/8) = 24.25
ii) SSTF
The total number of tracks are: (2 + 4 + 3 + 8 + 27 + 49 + 9 + 2) = 104 tracks
Average no of tracks: (104/ 8) = 13
iii) LOOK
The total number of tracks are: (5 + 9 + 2 + 18 + 4 + 3 + 8 + 27) = 76 tracks
Average no of tracks: (76/ 8) = 9.5
Answer to question number B – Q2
a)
The deadlock state is basically a situation where the set of processes in a blocked state
as each of the processes are holding a resource and waiting to be completed but is unable to
complete as the other process is not able to get the required resource which is again locked by
some other process. This occurs in the cyclic format.
b)
5
OPERATING SYSTEM
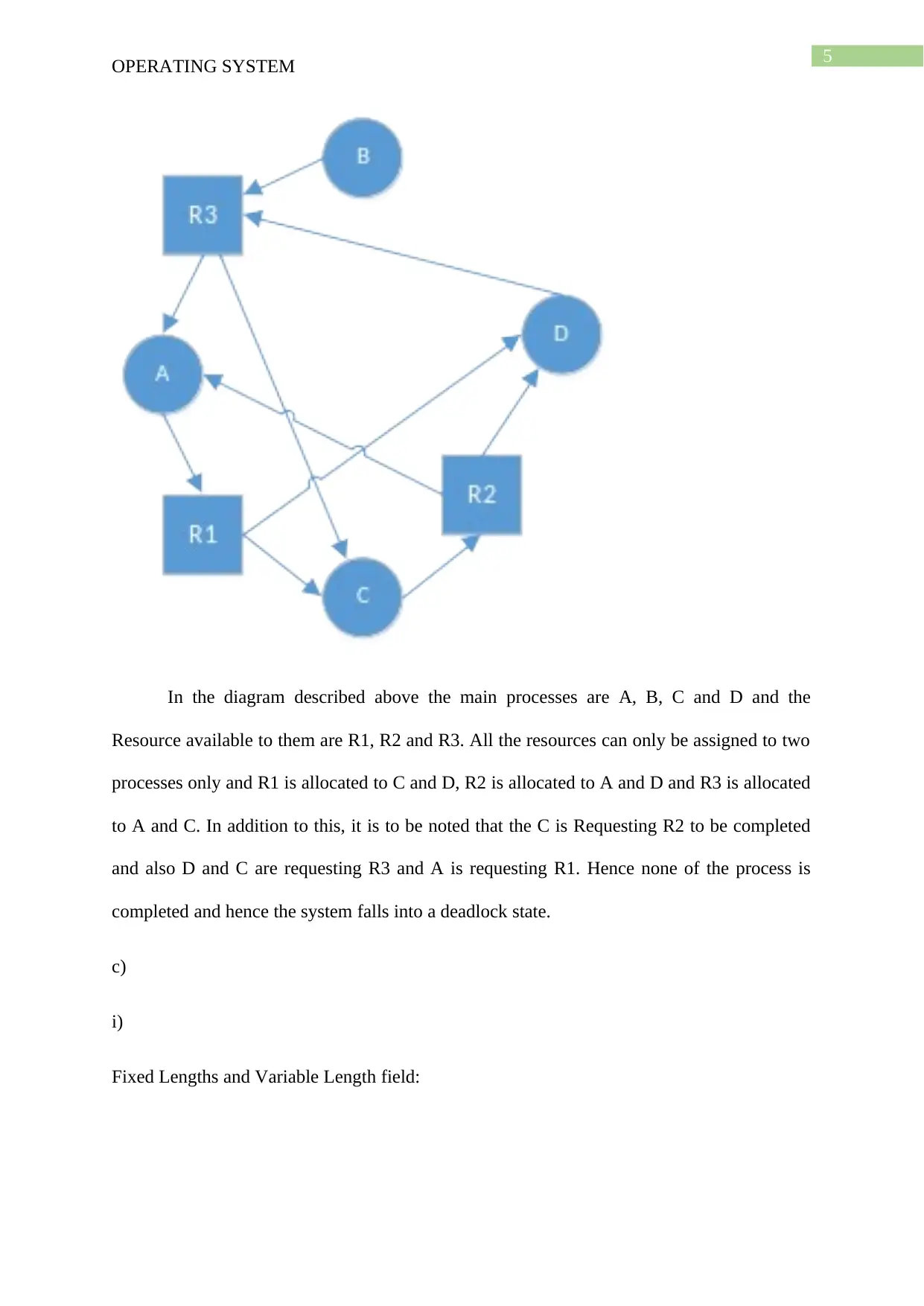
In the diagram described above the main processes are A, B, C and D and the
Resource available to them are R1, R2 and R3. All the resources can only be assigned to two
processes only and R1 is allocated to C and D, R2 is allocated to A and D and R3 is allocated
to A and C. In addition to this, it is to be noted that the C is Requesting R2 to be completed
and also D and C are requesting R3 and A is requesting R1. Hence none of the process is
completed and hence the system falls into a deadlock state.
c)
i)
Fixed Lengths and Variable Length field:
OPERATING SYSTEM
In the diagram described above the main processes are A, B, C and D and the
Resource available to them are R1, R2 and R3. All the resources can only be assigned to two
processes only and R1 is allocated to C and D, R2 is allocated to A and D and R3 is allocated
to A and C. In addition to this, it is to be noted that the C is Requesting R2 to be completed
and also D and C are requesting R3 and A is requesting R1. Hence none of the process is
completed and hence the system falls into a deadlock state.
c)
i)
Fixed Lengths and Variable Length field:

6
OPERATING SYSTEM
The fixed length and variable length also is referred to the entire record, however a
fixed-length record is one in which all the field and fixed length. On the other hand, a
variable –length record has at least of a variable-length field.
For example:
The data storage of the student’s name and details of the university has been considered in
this case.
For the fixed length variable of 5 the situation provided below can be considered.
ID S001
Name TOMHA
ADDRESS 1BENS
The data stored in variable length would be represented as:
ID S001
Name TOMHARDY
ADDRESS 1BENSONROAD
ii)
Relative and Complete File name:
The relative file name can be used for the specification of the directory name that would be
using the root and the file can be called as a Complete file name. In addition to this, the
specification of the position of the file in file storage system which is relative to any default
directory is called a relative file name.
Examples of the complete file:
C:\Documents\smaple.docx
http://www.google.com/image.jpg
Example of a relative file:
OPERATING SYSTEM
The fixed length and variable length also is referred to the entire record, however a
fixed-length record is one in which all the field and fixed length. On the other hand, a
variable –length record has at least of a variable-length field.
For example:
The data storage of the student’s name and details of the university has been considered in
this case.
For the fixed length variable of 5 the situation provided below can be considered.
ID S001
Name TOMHA
ADDRESS 1BENS
The data stored in variable length would be represented as:
ID S001
Name TOMHARDY
ADDRESS 1BENSONROAD
ii)
Relative and Complete File name:
The relative file name can be used for the specification of the directory name that would be
using the root and the file can be called as a Complete file name. In addition to this, the
specification of the position of the file in file storage system which is relative to any default
directory is called a relative file name.
Examples of the complete file:
C:\Documents\smaple.docx
http://www.google.com/image.jpg
Example of a relative file:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
OPERATING SYSTEM
Dashboard/46488.img
Student\student1\cv.docx
Answer to question number B-Q3
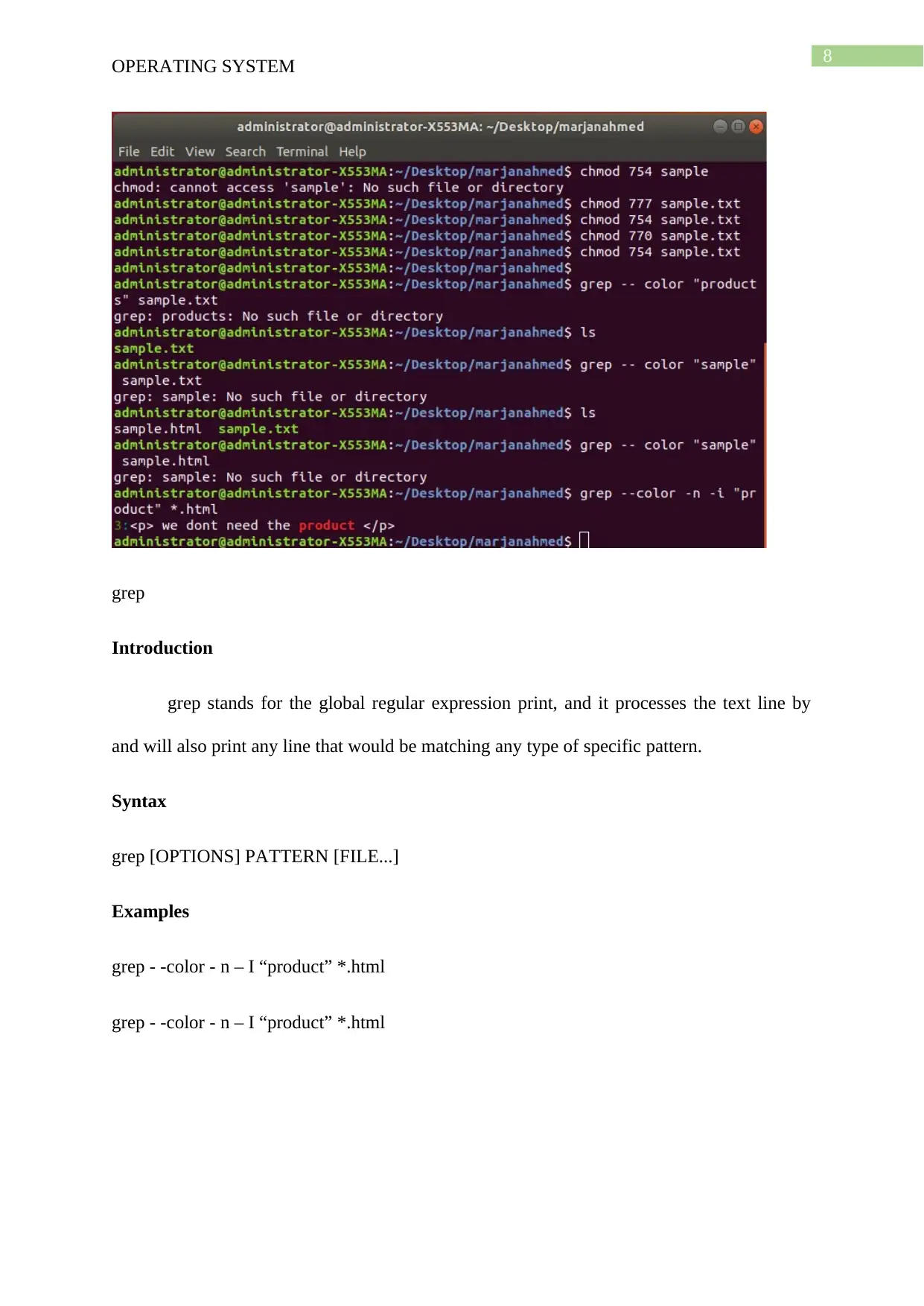
chmod
Introduction
chmod is used for changing the permission of the files and the directories. The
command stands for the change mode and it defines the way in which a file is to be accessed.
Syntax
chmod [OPTION]... MODE[,MODE]... FILE...
chmod [OPTION]... OCTAL-MODE FILE...
chmod [OPTION]... --reference=RFILE FILE...
Examples
chmod 754
chmod 777
chmod 754
OPERATING SYSTEM
Dashboard/46488.img
Student\student1\cv.docx
Answer to question number B-Q3
chmod
Introduction
chmod is used for changing the permission of the files and the directories. The
command stands for the change mode and it defines the way in which a file is to be accessed.
Syntax
chmod [OPTION]... MODE[,MODE]... FILE...
chmod [OPTION]... OCTAL-MODE FILE...
chmod [OPTION]... --reference=RFILE FILE...
Examples
chmod 754
chmod 777
chmod 754
8
OPERATING SYSTEM
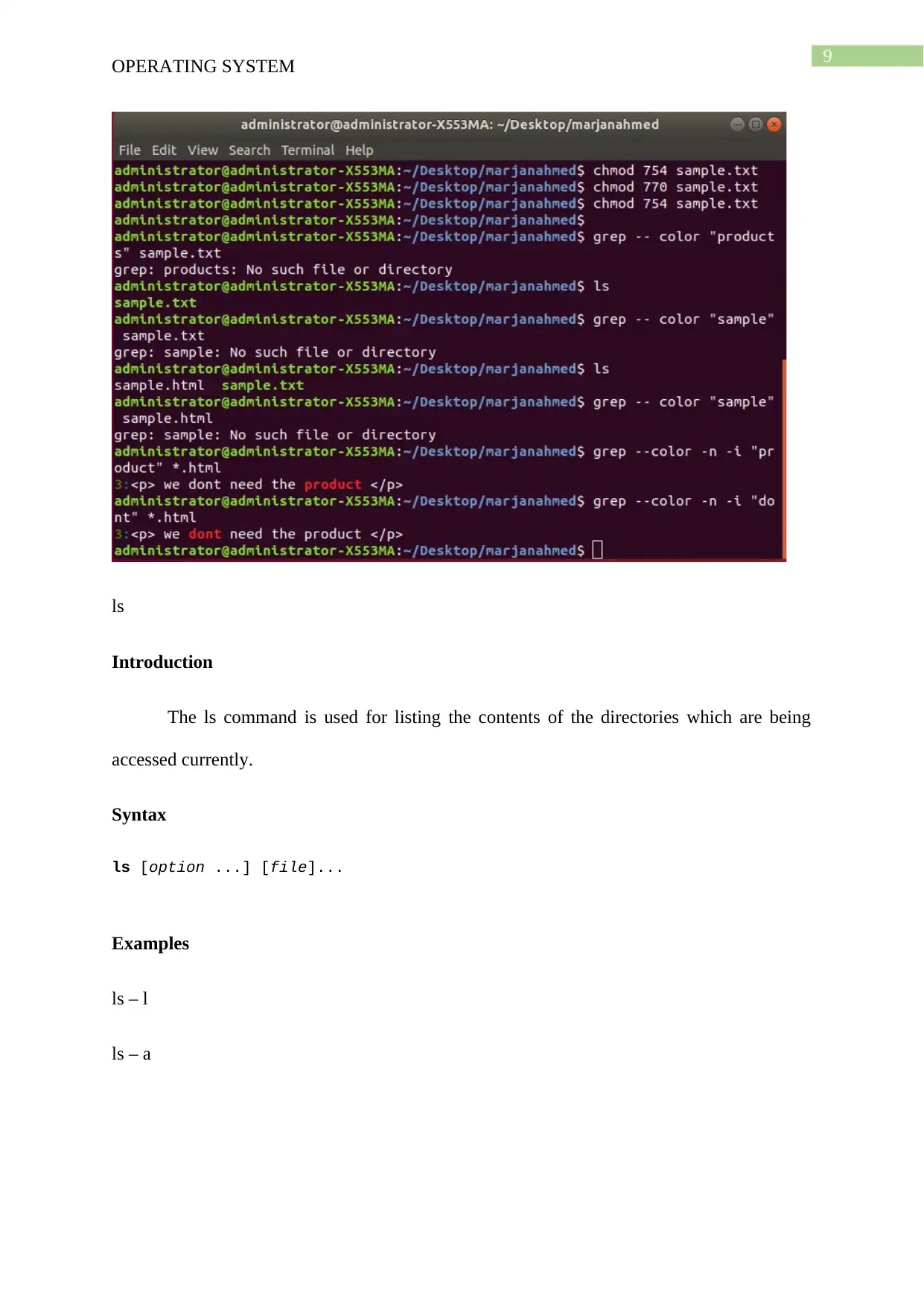
grep
Introduction
grep stands for the global regular expression print, and it processes the text line by
and will also print any line that would be matching any type of specific pattern.
Syntax
grep [OPTIONS] PATTERN [FILE...]
Examples
grep - -color - n – I “product” *.html
grep - -color - n – I “product” *.html
OPERATING SYSTEM
grep
Introduction
grep stands for the global regular expression print, and it processes the text line by
and will also print any line that would be matching any type of specific pattern.
Syntax
grep [OPTIONS] PATTERN [FILE...]
Examples
grep - -color - n – I “product” *.html
grep - -color - n – I “product” *.html
9
OPERATING SYSTEM
ls
Introduction
The ls command is used for listing the contents of the directories which are being
accessed currently.
Syntax
ls [option ...] [file]...
Examples
ls – l
ls – a
OPERATING SYSTEM
ls
Introduction
The ls command is used for listing the contents of the directories which are being
accessed currently.
Syntax
ls [option ...] [file]...
Examples
ls – l
ls – a
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10
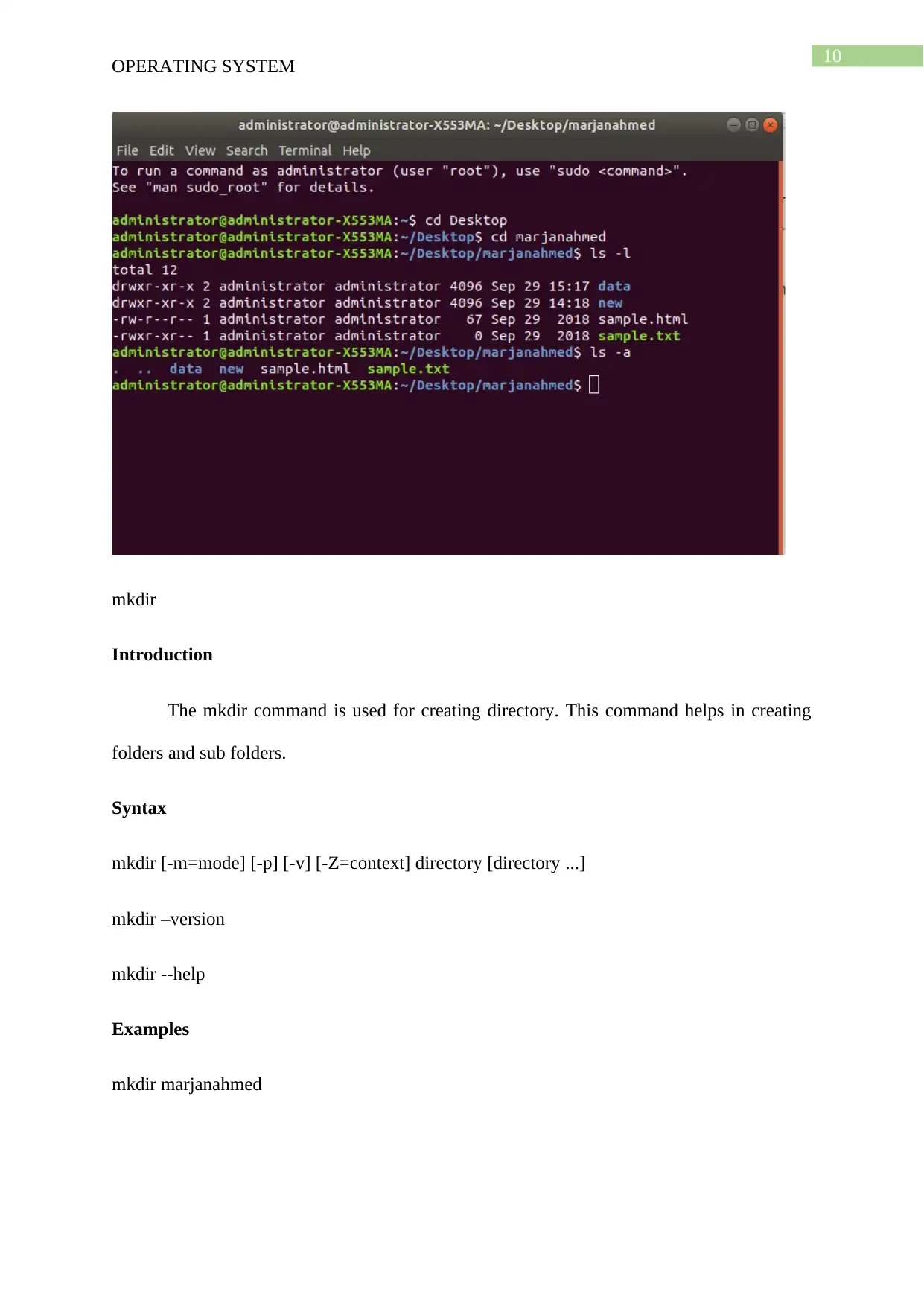
OPERATING SYSTEM
mkdir
Introduction
The mkdir command is used for creating directory. This command helps in creating
folders and sub folders.
Syntax
mkdir [-m=mode] [-p] [-v] [-Z=context] directory [directory ...]
mkdir –version
mkdir --help
Examples
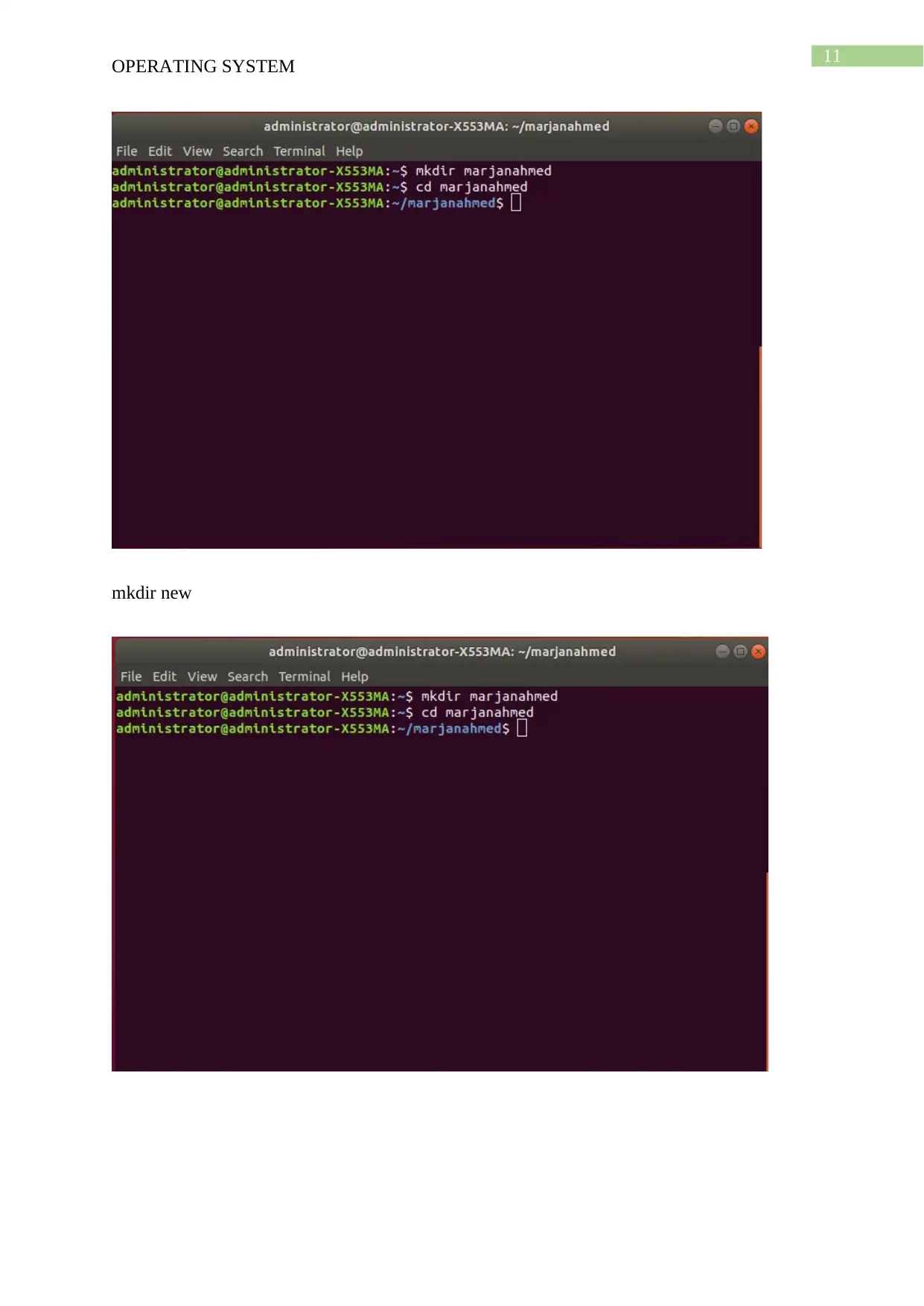
mkdir marjanahmed
OPERATING SYSTEM
mkdir
Introduction
The mkdir command is used for creating directory. This command helps in creating
folders and sub folders.
Syntax
mkdir [-m=mode] [-p] [-v] [-Z=context] directory [directory ...]
mkdir –version
mkdir --help
Examples
mkdir marjanahmed
11
OPERATING SYSTEM
mkdir new
OPERATING SYSTEM
mkdir new

12
OPERATING SYSTEM
Bibliography
[1] Silberschatz, A., Galvin, P.B. and Gagne, G. Operating system concepts essentials. John
Wiley & Sons, Inc., 2014.
[2] Peter, S., Li, J., Zhang, I., Ports, D.R., Woos, D., Krishnamurthy, A., Anderson, T. and
Roscoe, T. Arrakis: The operating system is the control plane. ACM Transactions on
Computer Systems (TOCS), 33(4), p.11., 2016.
[3] Belay, A., Prekas, G., Klimovic, A., Grossman, S., Kozyrakis, C. and Bugnion, E.x IX: A
protected dataplane operating system for high throughput and low latency. In Proceedings of
the 11th USENIX Symposium on Operating System Design and Implementation (OSDI) (No.
EPFL-CONF-201671). USENIX., 2015
[4] Dautenhahn, N., Kasampalis, T., Dietz, W., Criswell, J. and Adve, V., March. Nested
kernel: An operating system architecture for intra-kernel privilege separation. In ACM
SIGPLAN Notices (Vol. 50, No. 4, pp. 191-206). ACM., 2015.
[5] Shin, S., Song, Y., Lee, T., Lee, S., Chung, J., Porras, P., Yegneswaran, V., Noh, J. and
Kang, B.B., November. Rosemary: A robust, secure, and high-performance network
operating system. In Proceedings of the 2014 ACM SIGSAC conference on computer and
communications security (pp. 78-89). ACM., 2014.
OPERATING SYSTEM
Bibliography
[1] Silberschatz, A., Galvin, P.B. and Gagne, G. Operating system concepts essentials. John
Wiley & Sons, Inc., 2014.
[2] Peter, S., Li, J., Zhang, I., Ports, D.R., Woos, D., Krishnamurthy, A., Anderson, T. and
Roscoe, T. Arrakis: The operating system is the control plane. ACM Transactions on
Computer Systems (TOCS), 33(4), p.11., 2016.
[3] Belay, A., Prekas, G., Klimovic, A., Grossman, S., Kozyrakis, C. and Bugnion, E.x IX: A
protected dataplane operating system for high throughput and low latency. In Proceedings of
the 11th USENIX Symposium on Operating System Design and Implementation (OSDI) (No.
EPFL-CONF-201671). USENIX., 2015
[4] Dautenhahn, N., Kasampalis, T., Dietz, W., Criswell, J. and Adve, V., March. Nested
kernel: An operating system architecture for intra-kernel privilege separation. In ACM
SIGPLAN Notices (Vol. 50, No. 4, pp. 191-206). ACM., 2015.
[5] Shin, S., Song, Y., Lee, T., Lee, S., Chung, J., Porras, P., Yegneswaran, V., Noh, J. and
Kang, B.B., November. Rosemary: A robust, secure, and high-performance network
operating system. In Proceedings of the 2014 ACM SIGSAC conference on computer and
communications security (pp. 78-89). ACM., 2014.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




