Privacy Issues of IoT
VerifiedAdded on 2023/03/17
|14
|3402
|79
AI Summary
This research proposal aims to evaluate and identify the privacy and security issues of IoT devices used in commercial organizations and society. It discusses the security challenges, compatibility issues, and the role of risk management in addressing these issues. The proposal also includes a research plan and publication strategy.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: PRIVACY ISSUES OF IOT
Privacy issues of IoT
Name of the Student
Name of the University
Author’s Note:
Privacy issues of IoT
Name of the Student
Name of the University
Author’s Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1PRIVACY ISSUES OF IOT
Table of Contents
Introduction................................................................................................................................2
Research Questions................................................................................................................2
Date Collection of the research proposal...............................................................................2
Background study of the paper..................................................................................................3
Aims and Significance...............................................................................................................6
Research Plan.............................................................................................................................7
Publication strategy of the proposal.......................................................................................7
Conclusion..................................................................................................................................8
Reference....................................................................................................................................9
Table of Contents
Introduction................................................................................................................................2
Research Questions................................................................................................................2
Date Collection of the research proposal...............................................................................2
Background study of the paper..................................................................................................3
Aims and Significance...............................................................................................................6
Research Plan.............................................................................................................................7
Publication strategy of the proposal.......................................................................................7
Conclusion..................................................................................................................................8
Reference....................................................................................................................................9

2PRIVACY ISSUES OF IOT
Introduction
The prime objective of this research proposal is to evaluate and identify the privacy
along with the security issues of the IoT devices which are increasingly used in commercial
organizations as well as in our society. Numerous security issues associated with IoT devices
such as the compatibility issues, scalability issues, and cloud server issues are seen these
days. The inefficient testing and updating procedure can be the reason behind the privacy and
the security issues of the IoT devices. The use of the default passwords may be the other
privacy concern of the IoT devices as botnets such as the Mirai botnet can easily access the
IoT devices if the default passwords are not changed by the users. The following unit of the
paper will be presenting the research questions of this proposal
Research Questions
What are the security issues of the IoT devices which are used in our society?
What are the privacy concerns of the IoT devices which are used in business
organizations?
What is the role of the risk management team to address the security issues of the IoT
devices?
Date Collection of the research proposal
All the data which will be discussed in this research proposal will be collected from
reputed and reliable journals. Only peer-reviewed articles will be selected to understand the
chosen topic of the paper in a detailed manner. Scholars and researcher who have stated their
stand about the privacy and security issues of IoT devices will be considered in this paper.
Mostly recent journals will be chosen for this research proposal. The research gaps will be
addressed very professionally in this proposal, as opinion of different researchers will be
Introduction
The prime objective of this research proposal is to evaluate and identify the privacy
along with the security issues of the IoT devices which are increasingly used in commercial
organizations as well as in our society. Numerous security issues associated with IoT devices
such as the compatibility issues, scalability issues, and cloud server issues are seen these
days. The inefficient testing and updating procedure can be the reason behind the privacy and
the security issues of the IoT devices. The use of the default passwords may be the other
privacy concern of the IoT devices as botnets such as the Mirai botnet can easily access the
IoT devices if the default passwords are not changed by the users. The following unit of the
paper will be presenting the research questions of this proposal
Research Questions
What are the security issues of the IoT devices which are used in our society?
What are the privacy concerns of the IoT devices which are used in business
organizations?
What is the role of the risk management team to address the security issues of the IoT
devices?
Date Collection of the research proposal
All the data which will be discussed in this research proposal will be collected from
reputed and reliable journals. Only peer-reviewed articles will be selected to understand the
chosen topic of the paper in a detailed manner. Scholars and researcher who have stated their
stand about the privacy and security issues of IoT devices will be considered in this paper.
Mostly recent journals will be chosen for this research proposal. The research gaps will be
addressed very professionally in this proposal, as opinion of different researchers will be

3PRIVACY ISSUES OF IOT
considered for any security issues of the IoT devices. The following unit of this research
proposal will be the project background where 30 peer-reviewed articles will be presented in
an organized manner.
Background study of the paper
According to Adat and Gupta (2018), there are lots of security challenges associated
with most of the IoT devices which are used in our society like temperature sensors and smart
watches which are connected in the private network. The researcher of the paper stated the
security challenges such as authorization and the authentication (Kumar, Vealey and
Srivastava 2016). The paper was very much important to identify the privacy issues of the
cloud based servers which are often connected with the IoT devices. The researcher of the
paper stated that most of the IoT devices should be frequently updated as these updates help
in covering up the security loopholes of the IoT devices (Mahmoud et al. 2015). The
investigator of the paper also focused on the data privacy issues of the IoT systems which are
increasingly used in most of the global commercial organizations. The high availability of the
cloud applications can be the other source of concern for most of the IoT based devices
(Ammar, Russello and Crispo 2018). The investigators of this resource also stated about the
role of the network administrators as well as the risk mitigation team who can actively help to
secure the IoT devices from cyber security threats such as the Phishing emails and
ransomeware.
However, according to Guizani (2017), the physical devices connected with IoT
systems can be a source of anxiety for the users of the IoT services. The investigator of this
paper highlighted the role of the malware with worm capabilities as it has a direct impact on
the functionality of the IoT products and services (Borgohain, Kumar and Sanyal 2015). The
researcher of the paper showed the techniques which are used by most of the social engineers
considered for any security issues of the IoT devices. The following unit of this research
proposal will be the project background where 30 peer-reviewed articles will be presented in
an organized manner.
Background study of the paper
According to Adat and Gupta (2018), there are lots of security challenges associated
with most of the IoT devices which are used in our society like temperature sensors and smart
watches which are connected in the private network. The researcher of the paper stated the
security challenges such as authorization and the authentication (Kumar, Vealey and
Srivastava 2016). The paper was very much important to identify the privacy issues of the
cloud based servers which are often connected with the IoT devices. The researcher of the
paper stated that most of the IoT devices should be frequently updated as these updates help
in covering up the security loopholes of the IoT devices (Mahmoud et al. 2015). The
investigator of the paper also focused on the data privacy issues of the IoT systems which are
increasingly used in most of the global commercial organizations. The high availability of the
cloud applications can be the other source of concern for most of the IoT based devices
(Ammar, Russello and Crispo 2018). The investigators of this resource also stated about the
role of the network administrators as well as the risk mitigation team who can actively help to
secure the IoT devices from cyber security threats such as the Phishing emails and
ransomeware.
However, according to Guizani (2017), the physical devices connected with IoT
systems can be a source of anxiety for the users of the IoT services. The investigator of this
paper highlighted the role of the malware with worm capabilities as it has a direct impact on
the functionality of the IoT products and services (Borgohain, Kumar and Sanyal 2015). The
researcher of the paper showed the techniques which are used by most of the social engineers
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4PRIVACY ISSUES OF IOT
when they try to hack any IoT device (Moosavi 2016). The paper explained how the
functionality of the IoT devices such as the temperature sensors are revised by the social
engineers using different source codes (Barcena and Wueest 2015). The researcher of the
paper said that any sort of connection with the public Wi-Fi could have an undesirable impact
on the IoT devices due to the security vulnerabilities of the IoT systems (Abomhara 2015).
The researcher of the paper stated about the shadow broker tools is one of the foremost
security challenges of most of the IoT devices which are used in our society. The
vulnerability coming from the mobile carriers were also highlighted by the investigator of
this resource (Sadeghi, Wachsmann and Waidner 2015). There are lots of scalability and
networking issues in most of the IoT devices which are used in our society such as the
automated door-alarms as mentioned by the researcher (Lee 2015). The paper also
highlighted the cloud configuration issues of the IoT devices as these cloud configurations
issues can be very costly to mitigate for the users of the IoT devices. The paper has lots of
good and bad points (Li, Da and Zhao 2015). The notable advantage of this paper is that it
helps in addressing most of the recent security issues of the IoT devices. The main limitation
of the paper does not discusses the security challenges with case studies (Li, Tryfonas and Li
2016). Thus, based on the above paper the research gap which can be identified from the
paper is these paper have not discussed the plan to address these privacy issues of the IoT
devices.
As argued by Arias (2015), compatibility issues of IoT devices is distress for most of
the users of IoT devices. The researcher of the paper also highlighted the legal issues of the
IoT devices in terms of the cross border dataflow, data destruction, data retention, and
conflict between laws, civil rights, security breaches and the privacy lapse (Sfar et al. 2018).
The researcher of the paper stated that the cloud attacks is one of the most significant
problem of most of the IoT devices. The paper as very much helpful to understand the
when they try to hack any IoT device (Moosavi 2016). The paper explained how the
functionality of the IoT devices such as the temperature sensors are revised by the social
engineers using different source codes (Barcena and Wueest 2015). The researcher of the
paper said that any sort of connection with the public Wi-Fi could have an undesirable impact
on the IoT devices due to the security vulnerabilities of the IoT systems (Abomhara 2015).
The researcher of the paper stated about the shadow broker tools is one of the foremost
security challenges of most of the IoT devices which are used in our society. The
vulnerability coming from the mobile carriers were also highlighted by the investigator of
this resource (Sadeghi, Wachsmann and Waidner 2015). There are lots of scalability and
networking issues in most of the IoT devices which are used in our society such as the
automated door-alarms as mentioned by the researcher (Lee 2015). The paper also
highlighted the cloud configuration issues of the IoT devices as these cloud configurations
issues can be very costly to mitigate for the users of the IoT devices. The paper has lots of
good and bad points (Li, Da and Zhao 2015). The notable advantage of this paper is that it
helps in addressing most of the recent security issues of the IoT devices. The main limitation
of the paper does not discusses the security challenges with case studies (Li, Tryfonas and Li
2016). Thus, based on the above paper the research gap which can be identified from the
paper is these paper have not discussed the plan to address these privacy issues of the IoT
devices.
As argued by Arias (2015), compatibility issues of IoT devices is distress for most of
the users of IoT devices. The researcher of the paper also highlighted the legal issues of the
IoT devices in terms of the cross border dataflow, data destruction, data retention, and
conflict between laws, civil rights, security breaches and the privacy lapse (Sfar et al. 2018).
The researcher of the paper stated that the cloud attacks is one of the most significant
problem of most of the IoT devices. The paper as very much helpful to understand the

5PRIVACY ISSUES OF IOT
importance of the walled off internet (Farooq 2015). The investigator of the paper
successfully identifies the role of the AI built security issues which can have a huge financial
impact on the commercial organization using the IoT devices (Kolias (2016). The researcher
of the paper also mentioned that some of the users of the home based IoT devices lacks
confidence to control and use the IoT devices which can be one of the most significant
problems of this technology, thus the researcher of the paper focused hugely on the
understand the mechanisms of the IoT devices (Granjal, Monteiro and Silva 2015).
However, as argued by Li, Da and Zhao (2018), infrastructure issue is the most
significant security issues associated with the IoT devices (Li and Da Xu 2017). The
investigator of this journal mentioned that the security issues of the IoT devices can have an
undesirable impact on the developers of the IoT devices as well (Lin et al. 2017). The
researcher of the paper focused on the challenges faced by the developers of the IoT devices
such as the compatibility issues, data connectivity issues and the different sort of analytics
challenges (Alrawais 2017). The data security issues of the IoT devices are very much
important to be addressed as it have the capability to involve all the other technologies in the
surrounding environment.
As conferred by Conti (2018), processing issues is a big problem for the complex IoT
systems which are used in the business enterprises. The researcher of the paper stated that the
processing issues of the IoT devices can lead to serious complexities in the IoT devices which
can be utilized by the social engineers to get access to the system. The investigator of this
resource stated that the connectivity challenges of the IoT devices must be addressed in the
first place with the help of the IT project governance plan (Razzaq 2017). The investigators
also added the security loopholes of the smart wearable IoT based technologies which are
used in our society. The challenges and the limitations of the smart sensors are quantified by
importance of the walled off internet (Farooq 2015). The investigator of the paper
successfully identifies the role of the AI built security issues which can have a huge financial
impact on the commercial organization using the IoT devices (Kolias (2016). The researcher
of the paper also mentioned that some of the users of the home based IoT devices lacks
confidence to control and use the IoT devices which can be one of the most significant
problems of this technology, thus the researcher of the paper focused hugely on the
understand the mechanisms of the IoT devices (Granjal, Monteiro and Silva 2015).
However, as argued by Li, Da and Zhao (2018), infrastructure issue is the most
significant security issues associated with the IoT devices (Li and Da Xu 2017). The
investigator of this journal mentioned that the security issues of the IoT devices can have an
undesirable impact on the developers of the IoT devices as well (Lin et al. 2017). The
researcher of the paper focused on the challenges faced by the developers of the IoT devices
such as the compatibility issues, data connectivity issues and the different sort of analytics
challenges (Alrawais 2017). The data security issues of the IoT devices are very much
important to be addressed as it have the capability to involve all the other technologies in the
surrounding environment.
As conferred by Conti (2018), processing issues is a big problem for the complex IoT
systems which are used in the business enterprises. The researcher of the paper stated that the
processing issues of the IoT devices can lead to serious complexities in the IoT devices which
can be utilized by the social engineers to get access to the system. The investigator of this
resource stated that the connectivity challenges of the IoT devices must be addressed in the
first place with the help of the IT project governance plan (Razzaq 2017). The investigators
also added the security loopholes of the smart wearable IoT based technologies which are
used in our society. The challenges and the limitations of the smart sensors are quantified by

6PRIVACY ISSUES OF IOT
the investigators of this resource. The paper successfully identifies most of the reason behind
the security issues of IoT devices and products. However as argued by Sicari et al. (2015),
the security issues of the IoT devices not only have an undesirable impact on the users of the
technology but also on the devices itself (Yang et al. 2017). The researcher of the paper
focused on the performance and the scaling issues of the IoT devices which are used in the
global business corporations (Mosenia and Jha 2016). The researcher of the paper described
the security threats on each level of the IoT devices such as the end user level, system level,
session protocol level as well as the physical level (Dastjerdi and Buyya 2016). The other
specific challenges of the IoT devices which can be one of the reasons behind the security
issues in the IoT devices are hyper-connectivity, homogeneity, longevity, and transparency.
This paper has both advantages as well as disadvantages. The chief advantage of the paper is
it that it helps in identifying most of the reason behind the security issues (Nawir 2016). The
main limitation of the paper is that most of the discussion made in the paper are strictly based
on assumptions, as data was collected from secondary resources. Considering the above
papers, the research gap which can be identified is none of the paper stated about the ethical
considerations as well as the manufacturing defects of the IoT devices as these two can be the
two significant reason behind the privacy concerns of the IoT devices.
Aims and Significance
The notable determination of this research proposal is to identify most of the major
privacy issues of IoT devices.
the investigators of this resource. The paper successfully identifies most of the reason behind
the security issues of IoT devices and products. However as argued by Sicari et al. (2015),
the security issues of the IoT devices not only have an undesirable impact on the users of the
technology but also on the devices itself (Yang et al. 2017). The researcher of the paper
focused on the performance and the scaling issues of the IoT devices which are used in the
global business corporations (Mosenia and Jha 2016). The researcher of the paper described
the security threats on each level of the IoT devices such as the end user level, system level,
session protocol level as well as the physical level (Dastjerdi and Buyya 2016). The other
specific challenges of the IoT devices which can be one of the reasons behind the security
issues in the IoT devices are hyper-connectivity, homogeneity, longevity, and transparency.
This paper has both advantages as well as disadvantages. The chief advantage of the paper is
it that it helps in identifying most of the reason behind the security issues (Nawir 2016). The
main limitation of the paper is that most of the discussion made in the paper are strictly based
on assumptions, as data was collected from secondary resources. Considering the above
papers, the research gap which can be identified is none of the paper stated about the ethical
considerations as well as the manufacturing defects of the IoT devices as these two can be the
two significant reason behind the privacy concerns of the IoT devices.
Aims and Significance
The notable determination of this research proposal is to identify most of the major
privacy issues of IoT devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
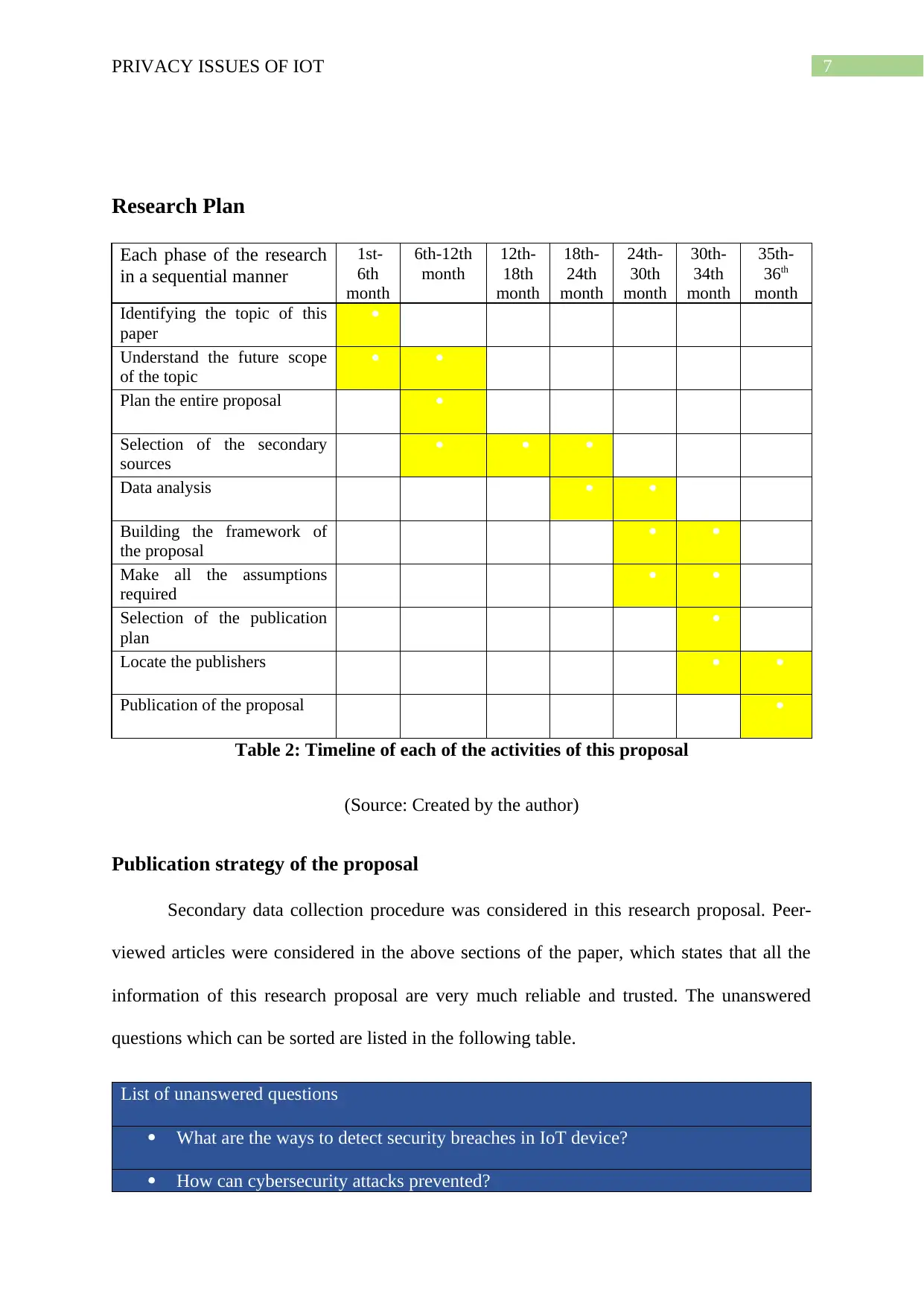
7PRIVACY ISSUES OF IOT
Research Plan
Each phase of the research
in a sequential manner
1st-
6th
month
6th-12th
month
12th-
18th
month
18th-
24th
month
24th-
30th
month
30th-
34th
month
35th-
36th
month
Identifying the topic of this
paper
Understand the future scope
of the topic
Plan the entire proposal
Selection of the secondary
sources
Data analysis
Building the framework of
the proposal
Make all the assumptions
required
Selection of the publication
plan
Locate the publishers
Publication of the proposal
Table 2: Timeline of each of the activities of this proposal
(Source: Created by the author)
Publication strategy of the proposal
Secondary data collection procedure was considered in this research proposal. Peer-
viewed articles were considered in the above sections of the paper, which states that all the
information of this research proposal are very much reliable and trusted. The unanswered
questions which can be sorted are listed in the following table.
List of unanswered questions
What are the ways to detect security breaches in IoT device?
How can cybersecurity attacks prevented?
Research Plan
Each phase of the research
in a sequential manner
1st-
6th
month
6th-12th
month
12th-
18th
month
18th-
24th
month
24th-
30th
month
30th-
34th
month
35th-
36th
month
Identifying the topic of this
paper
Understand the future scope
of the topic
Plan the entire proposal
Selection of the secondary
sources
Data analysis
Building the framework of
the proposal
Make all the assumptions
required
Selection of the publication
plan
Locate the publishers
Publication of the proposal
Table 2: Timeline of each of the activities of this proposal
(Source: Created by the author)
Publication strategy of the proposal
Secondary data collection procedure was considered in this research proposal. Peer-
viewed articles were considered in the above sections of the paper, which states that all the
information of this research proposal are very much reliable and trusted. The unanswered
questions which can be sorted are listed in the following table.
List of unanswered questions
What are the ways to detect security breaches in IoT device?
How can cybersecurity attacks prevented?

8PRIVACY ISSUES OF IOT
How can the manufacturing defects of the IoT devices resolved?
What are the ethical deliberations of the recent IoT devices?
How can the cloud server issues of IoT devices resolved?
Table 1: List of unanswered questions
(Source: created by the author)
Conclusion
The research proposal help in identifying different categories of privacy issues of the
IoT devices such as the scalability issues, compatibility issues and the issues coming from
social engineers such as ransomware.
How can the manufacturing defects of the IoT devices resolved?
What are the ethical deliberations of the recent IoT devices?
How can the cloud server issues of IoT devices resolved?
Table 1: List of unanswered questions
(Source: created by the author)
Conclusion
The research proposal help in identifying different categories of privacy issues of the
IoT devices such as the scalability issues, compatibility issues and the issues coming from
social engineers such as ransomware.

9PRIVACY ISSUES OF IOT
Reference
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Adat, V. and Gupta, B.B., 2018. Security in Internet of Things: issues, challenges, taxonomy,
and architecture. Telecommunication Systems, 67(3), pp.423-441.
Alrawais, A., Alhothaily, A., Hu, C. and Cheng, X., 2017. Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), pp.34-42.
Ammar, M., Russello, G. and Crispo, B., 2018. Internet of Things: A survey on the security
of IoT frameworks. Journal of Information Security and Applications, 38, pp.8-27.
Arias, O., Wurm, J., Hoang, K. and Jin, Y., 2015. Privacy and security in internet of things
and wearable devices. IEEE Transactions on Multi-Scale Computing Systems, 1(2), pp.99-
109.
Barcena, M.B. and Wueest, C., 2015. Insecurity in the Internet of Things. Security response,
symantec.
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Conti, M., Dehghantanha, A., Franke, K. and Watson, S., 2018. Internet of Things security
and forensics: Challenges and opportunities.
Dastjerdi, A.V. and Buyya, R., 2016. Fog computing: Helping the Internet of Things realize
its potential. Computer, 49(8), pp.112-116.
Reference
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Adat, V. and Gupta, B.B., 2018. Security in Internet of Things: issues, challenges, taxonomy,
and architecture. Telecommunication Systems, 67(3), pp.423-441.
Alrawais, A., Alhothaily, A., Hu, C. and Cheng, X., 2017. Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), pp.34-42.
Ammar, M., Russello, G. and Crispo, B., 2018. Internet of Things: A survey on the security
of IoT frameworks. Journal of Information Security and Applications, 38, pp.8-27.
Arias, O., Wurm, J., Hoang, K. and Jin, Y., 2015. Privacy and security in internet of things
and wearable devices. IEEE Transactions on Multi-Scale Computing Systems, 1(2), pp.99-
109.
Barcena, M.B. and Wueest, C., 2015. Insecurity in the Internet of Things. Security response,
symantec.
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Conti, M., Dehghantanha, A., Franke, K. and Watson, S., 2018. Internet of Things security
and forensics: Challenges and opportunities.
Dastjerdi, A.V. and Buyya, R., 2016. Fog computing: Helping the Internet of Things realize
its potential. Computer, 49(8), pp.112-116.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10PRIVACY ISSUES OF IOT
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer Applications,
111(7).
Granjal, J., Monteiro, E. and Silva, J.S., 2015. Security for the internet of things: a survey of
existing protocols and open research issues. IEEE Communications Surveys & Tutorials,
17(3), pp.1294-1312.
Kolias, C., Stavrou, A., Voas, J., Bojanova, I. and Kuhn, R., 2016. Learning internet-of-
things security" hands-on". IEEE Security & Privacy, 14(1), pp.37-46.
Kumar, S.A., Vealey, T. and Srivastava, H., 2016, January. Security in internet of things:
Challenges, solutions and future directions. In 2016 49th Hawaii International Conference
on System Sciences (HICSS) (pp. 5772-5781). IEEE.
Lee, K., Kim, D., Ha, D., Rajput, U. and Oh, H., 2015, September. On security and privacy
issues of fog computing supported Internet of Things environment. In 2015 6th International
Conference on the Network of the Future (NOF) (pp. 1-3). IEEE.
Li, S. and Da Xu, L., 2017. Securing the internet of things. Syngress.
Li, S., Da Xu, L. and Zhao, S., 2015. The internet of things: a survey. Information Systems
Frontiers, 17(2), pp.243-259.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Li, S., Tryfonas, T. and Li, H., 2016. The Internet of Things: a security point of view.
Internet Research, 26(2), pp.337-359.
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer Applications,
111(7).
Granjal, J., Monteiro, E. and Silva, J.S., 2015. Security for the internet of things: a survey of
existing protocols and open research issues. IEEE Communications Surveys & Tutorials,
17(3), pp.1294-1312.
Kolias, C., Stavrou, A., Voas, J., Bojanova, I. and Kuhn, R., 2016. Learning internet-of-
things security" hands-on". IEEE Security & Privacy, 14(1), pp.37-46.
Kumar, S.A., Vealey, T. and Srivastava, H., 2016, January. Security in internet of things:
Challenges, solutions and future directions. In 2016 49th Hawaii International Conference
on System Sciences (HICSS) (pp. 5772-5781). IEEE.
Lee, K., Kim, D., Ha, D., Rajput, U. and Oh, H., 2015, September. On security and privacy
issues of fog computing supported Internet of Things environment. In 2015 6th International
Conference on the Network of the Future (NOF) (pp. 1-3). IEEE.
Li, S. and Da Xu, L., 2017. Securing the internet of things. Syngress.
Li, S., Da Xu, L. and Zhao, S., 2015. The internet of things: a survey. Information Systems
Frontiers, 17(2), pp.243-259.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Li, S., Tryfonas, T. and Li, H., 2016. The Internet of Things: a security point of view.
Internet Research, 26(2), pp.337-359.

11PRIVACY ISSUES OF IOT
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.
Mahmoud, R., Yousuf, T., Aloul, F. and Zualkernan, I., 2015, December. Internet of things
(IoT) security: Current status, challenges and prospective measures. In 2015 10th
International Conference for Internet Technology and Secured Transactions (ICITST) (pp.
336-341). IEEE.
Moosavi, S.R., Gia, T.N., Nigussie, E., Rahmani, A.M., Virtanen, S., Tenhunen, H. and
Isoaho, J., 2016. End-to-end security scheme for mobility enabled healthcare Internet of
Things. Future Generation Computer Systems, 64, pp.108-124.
Mosenia, A. and Jha, N.K., 2016. A comprehensive study of security of internet-of-things.
IEEE Transactions on Emerging Topics in Computing, 5(4), pp.586-602.
Nawir, M., Amir, A., Yaakob, N. and Lynn, O.B., 2016, August. Internet of Things (IoT):
Taxonomy of security attacks. In 2016 3rd International Conference on Electronic Design
(ICED) (pp. 321-326). IEEE.
Razzaq, M.A., Gill, S.H., Qureshi, M.A. and Ullah, S., 2017. Security issues in the Internet of
Things (IoT): a comprehensive study. International Journal of Advanced Computer Science
and Applications (IJACSA), 8(6), pp.383-388.
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015, June. Security and privacy challenges
in industrial internet of things. In 2015 52nd ACM/EDAC/IEEE Design Automation
Conference (DAC) (pp. 1-6). IEEE.
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.
Mahmoud, R., Yousuf, T., Aloul, F. and Zualkernan, I., 2015, December. Internet of things
(IoT) security: Current status, challenges and prospective measures. In 2015 10th
International Conference for Internet Technology and Secured Transactions (ICITST) (pp.
336-341). IEEE.
Moosavi, S.R., Gia, T.N., Nigussie, E., Rahmani, A.M., Virtanen, S., Tenhunen, H. and
Isoaho, J., 2016. End-to-end security scheme for mobility enabled healthcare Internet of
Things. Future Generation Computer Systems, 64, pp.108-124.
Mosenia, A. and Jha, N.K., 2016. A comprehensive study of security of internet-of-things.
IEEE Transactions on Emerging Topics in Computing, 5(4), pp.586-602.
Nawir, M., Amir, A., Yaakob, N. and Lynn, O.B., 2016, August. Internet of Things (IoT):
Taxonomy of security attacks. In 2016 3rd International Conference on Electronic Design
(ICED) (pp. 321-326). IEEE.
Razzaq, M.A., Gill, S.H., Qureshi, M.A. and Ullah, S., 2017. Security issues in the Internet of
Things (IoT): a comprehensive study. International Journal of Advanced Computer Science
and Applications (IJACSA), 8(6), pp.383-388.
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015, June. Security and privacy challenges
in industrial internet of things. In 2015 52nd ACM/EDAC/IEEE Design Automation
Conference (DAC) (pp. 1-6). IEEE.

12PRIVACY ISSUES OF IOT
Sfar, A.R., Natalizio, E., Challal, Y. and Chtourou, Z., 2018. A roadmap for security
challenges in the Internet of Things. Digital Communications and Networks, 4(2), pp.118-
137.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust
in Internet of Things: The road ahead. Computer networks, 76, pp.146-164.
Whitmore, A., Agarwal, A. and Da Xu, L., 2015. The Internet of Things—A survey of topics
and trends. Information Systems Frontiers, 17(2), pp.261-274.
Yang, Y., Wu, L., Yin, G., Li, L. and Zhao, H., 2017. A survey on security and privacy issues
in Internet-of-Things. IEEE Internet of Things Journal, 4(5), pp.1250-1258.
Yaqoob, I., Ahmed, E., ur Rehman, M.H., Ahmed, A.I.A., Al-garadi, M.A., Imran, M. and
Guizani, M., 2017. The rise of ransomware and emerging security challenges in the Internet
of Things. Computer Networks, 129, pp.444-458.
Sfar, A.R., Natalizio, E., Challal, Y. and Chtourou, Z., 2018. A roadmap for security
challenges in the Internet of Things. Digital Communications and Networks, 4(2), pp.118-
137.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust
in Internet of Things: The road ahead. Computer networks, 76, pp.146-164.
Whitmore, A., Agarwal, A. and Da Xu, L., 2015. The Internet of Things—A survey of topics
and trends. Information Systems Frontiers, 17(2), pp.261-274.
Yang, Y., Wu, L., Yin, G., Li, L. and Zhao, H., 2017. A survey on security and privacy issues
in Internet-of-Things. IEEE Internet of Things Journal, 4(5), pp.1250-1258.
Yaqoob, I., Ahmed, E., ur Rehman, M.H., Ahmed, A.I.A., Al-garadi, M.A., Imran, M. and
Guizani, M., 2017. The rise of ransomware and emerging security challenges in the Internet
of Things. Computer Networks, 129, pp.444-458.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13PRIVACY ISSUES OF IOT
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




