QAC020N254: Cloud Computing | Task Report
Added on 2022-08-17
33 Pages2741 Words20 Views
Running head: QAC020N254: CLOUD COMPUTING
QAC020N254: Cloud Computing
Name of the Student
Name of the University
Authors note
QAC020N254: Cloud Computing
Name of the Student
Name of the University
Authors note

QAC020N254: CLOUD COMPUTING
1
Table of Contents
Task 1...............................................................................................................................................2
1.Proposal........................................................................................................................2
Proposal for selection of Cloud Service Providers..........................................................2
2.Evaluation of IAM services and creation of Groups....................................................4
Use of IAM and Creation of users and roles...............................................................5
3. Amazon EC2 Web Service's features........................................................................11
Task 2.............................................................................................................................................17
1.Critical evaluation of Amazon Relational Database Service......................................17
Database instance deployment and connecting through Mysql.....................................18
Task 3.............................................................................................................................................22
AWS storage services....................................................................................................22
S3...............................................................................................................................22
Glacier........................................................................................................................22
AWS Backup.............................................................................................................22
2.Critical evaluation of Amazon Website and App Services........................................22
Bibliography..................................................................................................................................31
1
Table of Contents
Task 1...............................................................................................................................................2
1.Proposal........................................................................................................................2
Proposal for selection of Cloud Service Providers..........................................................2
2.Evaluation of IAM services and creation of Groups....................................................4
Use of IAM and Creation of users and roles...............................................................5
3. Amazon EC2 Web Service's features........................................................................11
Task 2.............................................................................................................................................17
1.Critical evaluation of Amazon Relational Database Service......................................17
Database instance deployment and connecting through Mysql.....................................18
Task 3.............................................................................................................................................22
AWS storage services....................................................................................................22
S3...............................................................................................................................22
Glacier........................................................................................................................22
AWS Backup.............................................................................................................22
2.Critical evaluation of Amazon Website and App Services........................................22
Bibliography..................................................................................................................................31

QAC020N254: CLOUD COMPUTING
2
Task 1
1.Proposal
Proposal for selection of Cloud Service Providers
With the steady growth in the business of Retail4Profit it is important for the
organization in order to maintain the availability and accessibility to their website through
deploying the website on the cloud environment. Through the use of cloud, it enables the
businesses organizations in order to use hardware as well as software applications that are
completely managed/observed by the third-party service providers at some remote center.
As the Cloud computing uses the pay as you go price model and the organization only
have to pay for the services/computation resources usage depending on the quantity and usage
duration. Mostly all the cloud service providers provide similar kind of services.
Currently there are two major cloud service providers which are Microsoft Azure and
Amazon AWS. For the current scenario and requirements, the Azure provides numerous
application deployment options for the organization and the application developers. This
includes App Services, Service Fabric, Container based Service, WebJobs, Batch and so on
irrespective of the application type which is going to be deployed (Patawari and Aggarwal 2018).
Thus, it can be stated that Azure provides great tools in with their cloud services that helps in
deployment as well as scaling the same.
On the other hand, the AWS offers similar solutions along with the Elastic Beanstalk,
Container Service, Lambda and Batch services. As presently the Containers are considered as the
preferred mechanism presently for deploying applications for different open source applications.
Therefore, Retail4 profit organization should consider choosing the AWS cloud platform in order
to deploy the application to improve availability of the services to their customers and improve
revenue from the business.
While considering the deployment model, there are 4 deployment models are available.
In the next section these three models are discussed.
Private Cloud
2
Task 1
1.Proposal
Proposal for selection of Cloud Service Providers
With the steady growth in the business of Retail4Profit it is important for the
organization in order to maintain the availability and accessibility to their website through
deploying the website on the cloud environment. Through the use of cloud, it enables the
businesses organizations in order to use hardware as well as software applications that are
completely managed/observed by the third-party service providers at some remote center.
As the Cloud computing uses the pay as you go price model and the organization only
have to pay for the services/computation resources usage depending on the quantity and usage
duration. Mostly all the cloud service providers provide similar kind of services.
Currently there are two major cloud service providers which are Microsoft Azure and
Amazon AWS. For the current scenario and requirements, the Azure provides numerous
application deployment options for the organization and the application developers. This
includes App Services, Service Fabric, Container based Service, WebJobs, Batch and so on
irrespective of the application type which is going to be deployed (Patawari and Aggarwal 2018).
Thus, it can be stated that Azure provides great tools in with their cloud services that helps in
deployment as well as scaling the same.
On the other hand, the AWS offers similar solutions along with the Elastic Beanstalk,
Container Service, Lambda and Batch services. As presently the Containers are considered as the
preferred mechanism presently for deploying applications for different open source applications.
Therefore, Retail4 profit organization should consider choosing the AWS cloud platform in order
to deploy the application to improve availability of the services to their customers and improve
revenue from the business.
While considering the deployment model, there are 4 deployment models are available.
In the next section these three models are discussed.
Private Cloud

QAC020N254: CLOUD COMPUTING
3
This cloud deployment model is preferred and used by the stand-alone organizations in
order to leverage the provided control and security. Data collected from the deployed
application is backed and secured by firewall. The private cloud deployments model is perfect
for the organizations that requires intense management, availability requirements as well as high-
security of its data as well as applications.
Public Cloud
This type of cloud deployment model is provided on a network. In this model the
customer organizations do not have any control over the location of assigned infrastructure. This
model is based on shared cost mode. Multiple users use the resources in a shared manner in the
form of licensing policy. This kind of deployment model is suitable for the business
organizations that have growing as well as shifting demands. This model is suitable for business
organizations who want to only deploy the web applications, webmail applications as well as for
storing data of non-sensitive application/business data.
Community Cloud
This is a mutually shared cloud deployment model that are used between different
organizations which are connected to some specific organizations like government authorities,
banks, different commercial institutions. The deployment is used by the group of users who
usually share similar kind of privacy and security issues. The community deployment model is
usually managed by a third-party or the internal administrators.
Hybrid Cloud
The final model is combination of the best features of both private, public cloud
deployments. In this deployment model the internal, or external resource providers are
responsible for providing resources. This deployment model is best option for the organizations
that requires scalability, flexibility, and security of data/application at the same time.
After considering all the deployment options described above, it suggested that,
Retail4Profit should go with the hybrid cloud deployment model in which they can deploy the
website e-commerce application on public cloud and maintain the customer and business data in
the private cloud.
3
This cloud deployment model is preferred and used by the stand-alone organizations in
order to leverage the provided control and security. Data collected from the deployed
application is backed and secured by firewall. The private cloud deployments model is perfect
for the organizations that requires intense management, availability requirements as well as high-
security of its data as well as applications.
Public Cloud
This type of cloud deployment model is provided on a network. In this model the
customer organizations do not have any control over the location of assigned infrastructure. This
model is based on shared cost mode. Multiple users use the resources in a shared manner in the
form of licensing policy. This kind of deployment model is suitable for the business
organizations that have growing as well as shifting demands. This model is suitable for business
organizations who want to only deploy the web applications, webmail applications as well as for
storing data of non-sensitive application/business data.
Community Cloud
This is a mutually shared cloud deployment model that are used between different
organizations which are connected to some specific organizations like government authorities,
banks, different commercial institutions. The deployment is used by the group of users who
usually share similar kind of privacy and security issues. The community deployment model is
usually managed by a third-party or the internal administrators.
Hybrid Cloud
The final model is combination of the best features of both private, public cloud
deployments. In this deployment model the internal, or external resource providers are
responsible for providing resources. This deployment model is best option for the organizations
that requires scalability, flexibility, and security of data/application at the same time.
After considering all the deployment options described above, it suggested that,
Retail4Profit should go with the hybrid cloud deployment model in which they can deploy the
website e-commerce application on public cloud and maintain the customer and business data in
the private cloud.

QAC020N254: CLOUD COMPUTING
4
2.Evaluation of IAM services and creation of Groups
With the increasing adoption of the cloud computing, the major concern was security
while moving/migrating applications, data or services in the cloud. In order to secure different
services as well as applications in a cloud environment it is essential to place measures to
manage user identities in the cloud environment. In this way it will be possible to control the
authorization for accessing the cloud resources that in turn helps in the securing those resources
from exploitation.
In AWS, the IAM is a service provided to the customers under “Security-as-a-Service”
Components. This comes under the identity and Access Management delivery inside the cloud
environment. This service can be considered as the Identity-as-a-Service in AWS. Through the
use of the IAM in the cloud, it makes the process of maintenance and security while managing
the hybrid infrastructures that are often cumbersome (Zahoor, Asma and Perrin 2017). Through
the use of the IAM it is possible to Shared access to AWS accounts as well as resources. IAM
helps the administrator in order to create multiple separate usernames with respective passwords
for the individual users so that delegate access can be assigned to resources.
With the use of the IAM it is possible to provide granular permissions to the users.
Restrictions for access can be easily applied to different resource requests inside the cloud
environment. As an example, it can be sated that the administrator can allow some users in order
to download some data but at the same time deny those specific users to update the data through
the access policies.
One of the most important components in IAM is the MFA or Multifactor
authentication. While using IAM, the users enters username, password along with the one-time
password from their smart phones. This password is randomly generated that is utilized as an
extra authentication factor to access the resources.
4
2.Evaluation of IAM services and creation of Groups
With the increasing adoption of the cloud computing, the major concern was security
while moving/migrating applications, data or services in the cloud. In order to secure different
services as well as applications in a cloud environment it is essential to place measures to
manage user identities in the cloud environment. In this way it will be possible to control the
authorization for accessing the cloud resources that in turn helps in the securing those resources
from exploitation.
In AWS, the IAM is a service provided to the customers under “Security-as-a-Service”
Components. This comes under the identity and Access Management delivery inside the cloud
environment. This service can be considered as the Identity-as-a-Service in AWS. Through the
use of the IAM in the cloud, it makes the process of maintenance and security while managing
the hybrid infrastructures that are often cumbersome (Zahoor, Asma and Perrin 2017). Through
the use of the IAM it is possible to Shared access to AWS accounts as well as resources. IAM
helps the administrator in order to create multiple separate usernames with respective passwords
for the individual users so that delegate access can be assigned to resources.
With the use of the IAM it is possible to provide granular permissions to the users.
Restrictions for access can be easily applied to different resource requests inside the cloud
environment. As an example, it can be sated that the administrator can allow some users in order
to download some data but at the same time deny those specific users to update the data through
the access policies.
One of the most important components in IAM is the MFA or Multifactor
authentication. While using IAM, the users enters username, password along with the one-time
password from their smart phones. This password is randomly generated that is utilized as an
extra authentication factor to access the resources.

QAC020N254: CLOUD COMPUTING
5
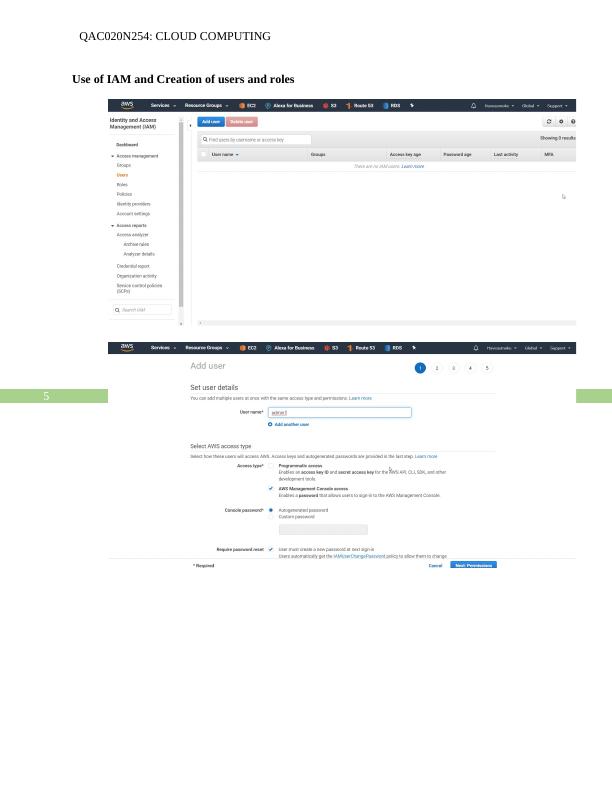
Use of IAM and Creation of users and roles
5
Use of IAM and Creation of users and roles
QAC020N254: CLOUD COMPUTING
6
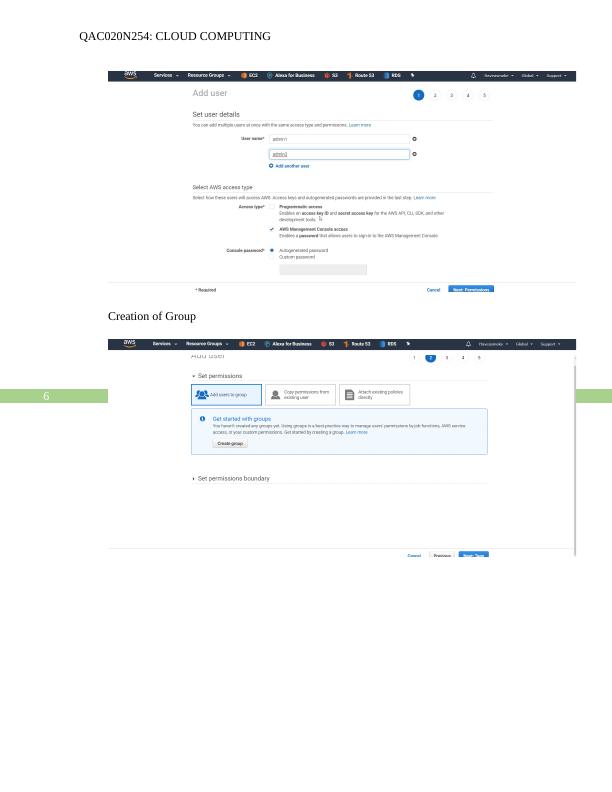
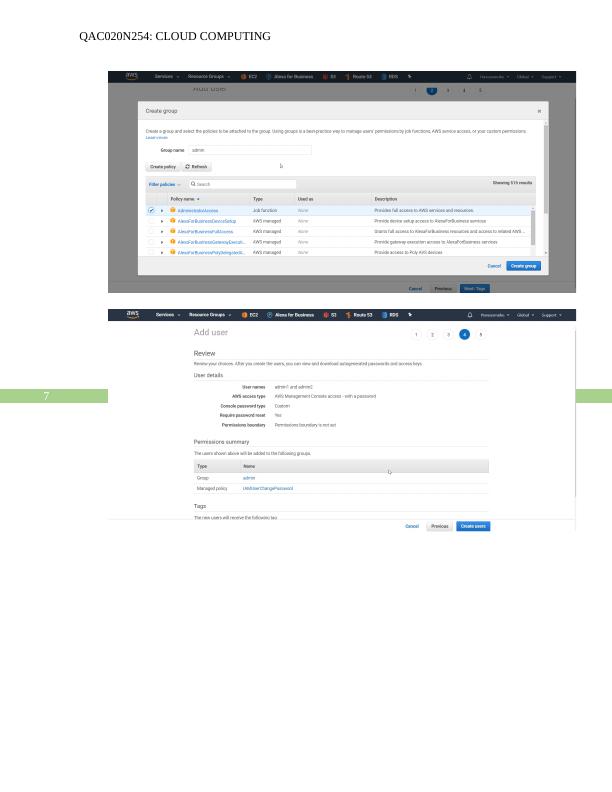
Creation of Group
6
Creation of Group
QAC020N254: CLOUD COMPUTING
7
7
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Cloud Computing On AWS and Azurelg...
|17
|2896
|448
Linux Server Administration - Amazonlg...
|20
|1255
|165
Cloud Computing Services Providers Assignmentlg...
|19
|2052
|68
ITC514 Linux Server Administration Assignmentlg...
|21
|2602
|205
Cloud Computing: Services, IAM, EC2 Features, RDS Storagelg...
|21
|4846
|30
Deployment of Drupal CMS on AWS Cloud Infrastructurelg...
|6
|596
|424