AWS Cloud Migration
VerifiedAdded on 2019/09/23
|23
|7203
|209
Report
AI Summary
The migration of email instances to the AWS cloud involves five phases: initiation, planning, execution, control, and closure. Each phase has critical points and issues that must be considered, such as feasibility analysis, inadequate planning, security risks, and change management. The organization will provide trainings for the resources to understand each feature of the new platform and assess the performance of the newer platform. The five phases and their corresponding critical points and issues are: Initiation Phase - feasibility analysis; Planning Phase - schedule/budget overrun, resourcing issues, and quality issues; Execution Phase - security risks, data breaches, and eavesdropping attacks; Control Phase - risks associated with changes brought in by the migration process; and Closure Phase - final reviews and audits to assess performance.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Regional Gardens Ltd.
Cloud Computing
5/12/2018
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Regional Gardens Ltd.
Cloud Computing
5/12/2018
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Regional Gardens Ltd.
Table of Contents
Hybrid Cloud Architectures...................................................................................................................2
AWS Hybrid Cloud...........................................................................................................................2
Benefits of the Hybrid Cloud Architecture........................................................................................3
Issues with Hybrid Cloud Architecture..............................................................................................4
Risk Report for Hybrid Cloud & Microservices....................................................................................4
List of Risks Identified......................................................................................................................4
Risk Register.....................................................................................................................................5
Treatment Strategies & Controls.......................................................................................................7
Proposed Information Security Controls................................................................................................8
Administrative Controls....................................................................................................................9
Technical/Logical Controls.............................................................................................................10
Physical Controls.............................................................................................................................11
BCP Changes.......................................................................................................................................12
Application Resilience.....................................................................................................................12
Data Storage and Backup.................................................................................................................12
Disaster Recovery............................................................................................................................13
Hybrid Cloud Administration & SLA Management............................................................................14
Remote Administration....................................................................................................................14
Resource Management....................................................................................................................15
SLA Management............................................................................................................................16
Migration Plan.....................................................................................................................................17
Purpose of the Plan..........................................................................................................................17
Migration Approach........................................................................................................................17
Phases in Migration.........................................................................................................................17
Initiation Phase............................................................................................................................17
Planning Phase.............................................................................................................................17
Execution Phase...........................................................................................................................18
Control Phase...............................................................................................................................18
Closure Phase..............................................................................................................................19
Critical Points & Issues...................................................................................................................19
References...........................................................................................................................................21
1
Table of Contents
Hybrid Cloud Architectures...................................................................................................................2
AWS Hybrid Cloud...........................................................................................................................2
Benefits of the Hybrid Cloud Architecture........................................................................................3
Issues with Hybrid Cloud Architecture..............................................................................................4
Risk Report for Hybrid Cloud & Microservices....................................................................................4
List of Risks Identified......................................................................................................................4
Risk Register.....................................................................................................................................5
Treatment Strategies & Controls.......................................................................................................7
Proposed Information Security Controls................................................................................................8
Administrative Controls....................................................................................................................9
Technical/Logical Controls.............................................................................................................10
Physical Controls.............................................................................................................................11
BCP Changes.......................................................................................................................................12
Application Resilience.....................................................................................................................12
Data Storage and Backup.................................................................................................................12
Disaster Recovery............................................................................................................................13
Hybrid Cloud Administration & SLA Management............................................................................14
Remote Administration....................................................................................................................14
Resource Management....................................................................................................................15
SLA Management............................................................................................................................16
Migration Plan.....................................................................................................................................17
Purpose of the Plan..........................................................................................................................17
Migration Approach........................................................................................................................17
Phases in Migration.........................................................................................................................17
Initiation Phase............................................................................................................................17
Planning Phase.............................................................................................................................17
Execution Phase...........................................................................................................................18
Control Phase...............................................................................................................................18
Closure Phase..............................................................................................................................19
Critical Points & Issues...................................................................................................................19
References...........................................................................................................................................21
1
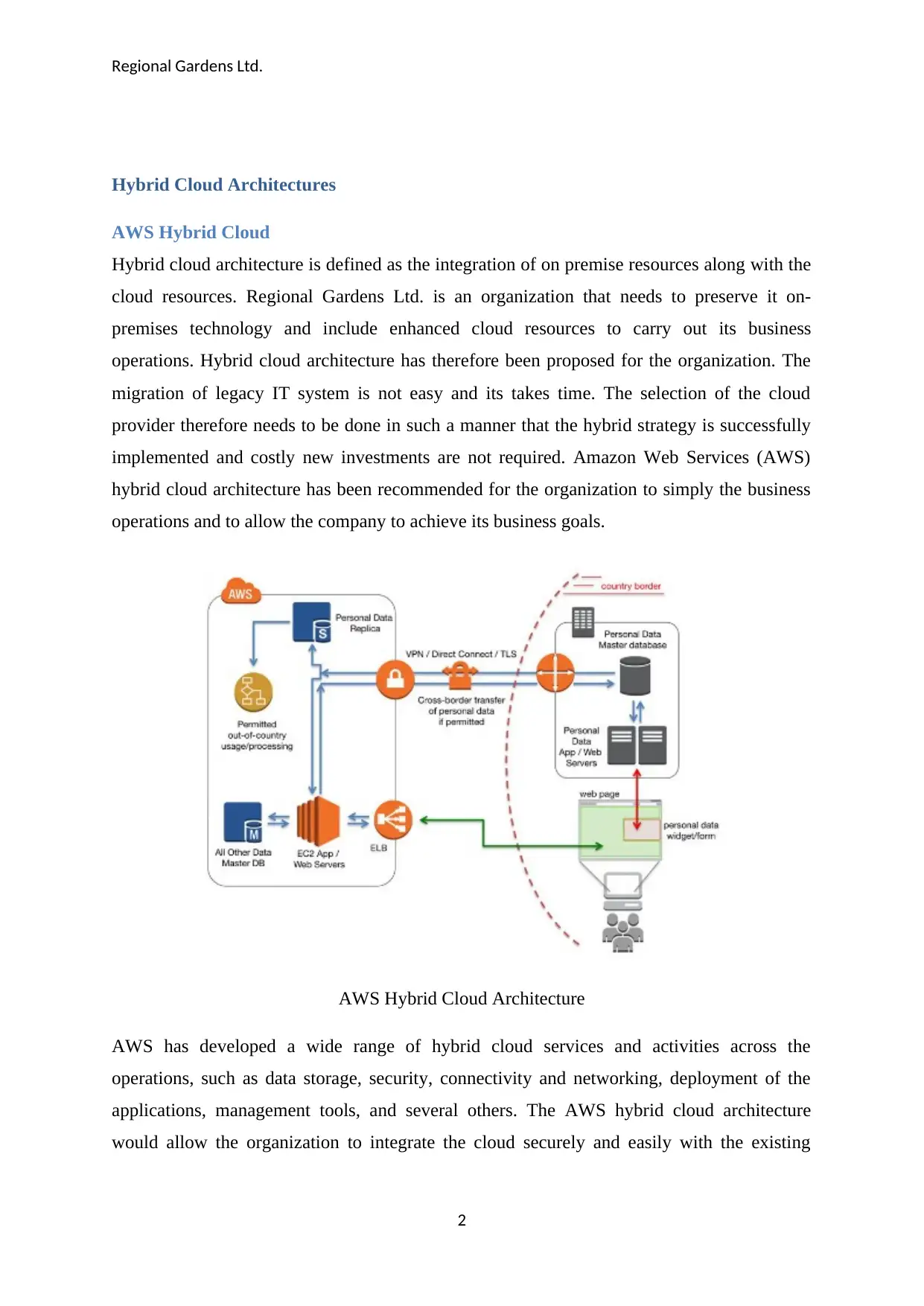
Regional Gardens Ltd.
Hybrid Cloud Architectures
AWS Hybrid Cloud
Hybrid cloud architecture is defined as the integration of on premise resources along with the
cloud resources. Regional Gardens Ltd. is an organization that needs to preserve it on-
premises technology and include enhanced cloud resources to carry out its business
operations. Hybrid cloud architecture has therefore been proposed for the organization. The
migration of legacy IT system is not easy and its takes time. The selection of the cloud
provider therefore needs to be done in such a manner that the hybrid strategy is successfully
implemented and costly new investments are not required. Amazon Web Services (AWS)
hybrid cloud architecture has been recommended for the organization to simply the business
operations and to allow the company to achieve its business goals.
AWS Hybrid Cloud Architecture
AWS has developed a wide range of hybrid cloud services and activities across the
operations, such as data storage, security, connectivity and networking, deployment of the
applications, management tools, and several others. The AWS hybrid cloud architecture
would allow the organization to integrate the cloud securely and easily with the existing
2
Hybrid Cloud Architectures
AWS Hybrid Cloud
Hybrid cloud architecture is defined as the integration of on premise resources along with the
cloud resources. Regional Gardens Ltd. is an organization that needs to preserve it on-
premises technology and include enhanced cloud resources to carry out its business
operations. Hybrid cloud architecture has therefore been proposed for the organization. The
migration of legacy IT system is not easy and its takes time. The selection of the cloud
provider therefore needs to be done in such a manner that the hybrid strategy is successfully
implemented and costly new investments are not required. Amazon Web Services (AWS)
hybrid cloud architecture has been recommended for the organization to simply the business
operations and to allow the company to achieve its business goals.
AWS Hybrid Cloud Architecture
AWS has developed a wide range of hybrid cloud services and activities across the
operations, such as data storage, security, connectivity and networking, deployment of the
applications, management tools, and several others. The AWS hybrid cloud architecture
would allow the organization to integrate the cloud securely and easily with the existing
2

Regional Gardens Ltd.
architecture by extending the current investments (Aws, 2018). The AWS hybrid cloud
architecture has been shown in the figure above.
It has been recommended for the organization as it will economically store massive sets of
data and will provide mechanisms to utilize the new cloud-native databases. The customer
will be able to clearly view the data sets and there will be enhanced transparency developed
between the customers and the organization. The backup of the data sets will be possible to
be developed in a cost effective manner. The hybrid cloud architecture comes with a storage
gateway service. The service will seamlessly integrate the existing and newer cloud
components. It follows a multi-protocol storage appliance coupled with extremely efficient
network connection to deliver enhanced performance to the users.
The second layer of the hybrid cloud architecture provides the mechanism to connect the on-
premises and cloud resources with the aid of a common network to develop a single
enterprise environment for enhanced security. The extension of the network connections may
be easily done so that the AWS resources operate the cloud operations as part of the
organization. The physical connectivity may also be extended so that a dedicated and private
network connection may be set-up. Integrated identity and access strategy is another reason
that is present behind the selection of the cloud architecture. The cloud architecture will allow
the creation and management of the various users, user groups, access, permissions, and
identity in extreme detail. There are managed services that are offered by AWS to connect the
resources with Microsoft Active Directory and to merge the policy with the existing set of
tools. The extremely robust hybrid architecture involved integration of the application
development, application deployment, and management strategies across the various
environments. VMware is also one of the close associates of AWS and there is a relationship
that has been developed between AWS and VMware to carry out the cloud operations and
activities.
Benefits of the Hybrid Cloud Architecture
The primary benefit that hybrid cloud architecture will provide to the organization will be in
terms of flexibility and scalability. The business operations of Regional Gardens Ltd. are
continuously changing and there may be increase or decrease in the demands of cloud
services that may be observed in the years to come. The hybrid cloud architecture will allow
the organization with the opportunity to explore the new products and business operations at
all times. One of the primary concerns with cloud platforms is the downtime due to
3
architecture by extending the current investments (Aws, 2018). The AWS hybrid cloud
architecture has been shown in the figure above.
It has been recommended for the organization as it will economically store massive sets of
data and will provide mechanisms to utilize the new cloud-native databases. The customer
will be able to clearly view the data sets and there will be enhanced transparency developed
between the customers and the organization. The backup of the data sets will be possible to
be developed in a cost effective manner. The hybrid cloud architecture comes with a storage
gateway service. The service will seamlessly integrate the existing and newer cloud
components. It follows a multi-protocol storage appliance coupled with extremely efficient
network connection to deliver enhanced performance to the users.
The second layer of the hybrid cloud architecture provides the mechanism to connect the on-
premises and cloud resources with the aid of a common network to develop a single
enterprise environment for enhanced security. The extension of the network connections may
be easily done so that the AWS resources operate the cloud operations as part of the
organization. The physical connectivity may also be extended so that a dedicated and private
network connection may be set-up. Integrated identity and access strategy is another reason
that is present behind the selection of the cloud architecture. The cloud architecture will allow
the creation and management of the various users, user groups, access, permissions, and
identity in extreme detail. There are managed services that are offered by AWS to connect the
resources with Microsoft Active Directory and to merge the policy with the existing set of
tools. The extremely robust hybrid architecture involved integration of the application
development, application deployment, and management strategies across the various
environments. VMware is also one of the close associates of AWS and there is a relationship
that has been developed between AWS and VMware to carry out the cloud operations and
activities.
Benefits of the Hybrid Cloud Architecture
The primary benefit that hybrid cloud architecture will provide to the organization will be in
terms of flexibility and scalability. The business operations of Regional Gardens Ltd. are
continuously changing and there may be increase or decrease in the demands of cloud
services that may be observed in the years to come. The hybrid cloud architecture will allow
the organization with the opportunity to explore the new products and business operations at
all times. One of the primary concerns with cloud platforms is the downtime due to
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Regional Gardens Ltd.
occurrence of security risks or availability issues. There is also a lot of maintenance time that
is demanded by the other cloud platforms in the market. However, hybrid cloud architecture
is stable as it includes the features of private as well as public cloud (Xue & Xin, 2016).
There is highest degree of stability that is promised and comes along with hybrid cloud.
These cloud architectures are also cost-effective in nature and have reduced latency.
Issues with Hybrid Cloud Architecture
There is an increased infrastructure dependency that comes along with hybrid cloud
architecture. For any of the cloud-related issue or outage, there is a lot of reliance on the
internal IT staff. Security is another primary concern that is witnessed with the hybrid cloud
architecture. There may be security issues as lack of encryption, denial of service and
distributed denial of service attacks, malware attacks, data leakage, authentication issues, etc.
that may come up (Jenkins, 2014).
Risk Report for Hybrid Cloud & Microservices
List of Risks Identified
Risk Name Description of the Risk
Encryption Issues The data sets present on the cloud platform may not be
encrypted properly leading to the exposure of information
properties and contents
Denial of Service &
Distributed Denial of
Service Attacks
The malicious entities may launch garbage traffic on the cloud
connections which may disrupt the availability of the service
and the data sets
Malware Attacks There may be attacks of malicious codes, such as viruses,
worms, logic bombs, ransomware, and others
Data Leakage The data and information present on the hybrid cloud
architecture may get leaked in between that may impact the
integrity of the information sets
Unprotected APIs API endpoints may be utilized by the malevolent entities to
expose the sensitive data and information sets
Authentication & Identity
Issues
Access to the sensitive and confidential data sets to the
unauthorized entities due to poor authentication and identity
management
4
occurrence of security risks or availability issues. There is also a lot of maintenance time that
is demanded by the other cloud platforms in the market. However, hybrid cloud architecture
is stable as it includes the features of private as well as public cloud (Xue & Xin, 2016).
There is highest degree of stability that is promised and comes along with hybrid cloud.
These cloud architectures are also cost-effective in nature and have reduced latency.
Issues with Hybrid Cloud Architecture
There is an increased infrastructure dependency that comes along with hybrid cloud
architecture. For any of the cloud-related issue or outage, there is a lot of reliance on the
internal IT staff. Security is another primary concern that is witnessed with the hybrid cloud
architecture. There may be security issues as lack of encryption, denial of service and
distributed denial of service attacks, malware attacks, data leakage, authentication issues, etc.
that may come up (Jenkins, 2014).
Risk Report for Hybrid Cloud & Microservices
List of Risks Identified
Risk Name Description of the Risk
Encryption Issues The data sets present on the cloud platform may not be
encrypted properly leading to the exposure of information
properties and contents
Denial of Service &
Distributed Denial of
Service Attacks
The malicious entities may launch garbage traffic on the cloud
connections which may disrupt the availability of the service
and the data sets
Malware Attacks There may be attacks of malicious codes, such as viruses,
worms, logic bombs, ransomware, and others
Data Leakage The data and information present on the hybrid cloud
architecture may get leaked in between that may impact the
integrity of the information sets
Unprotected APIs API endpoints may be utilized by the malevolent entities to
expose the sensitive data and information sets
Authentication & Identity
Issues
Access to the sensitive and confidential data sets to the
unauthorized entities due to poor authentication and identity
management
4
Regional Gardens Ltd.
Poor IP Protection The protection measures installed for the sensitive and
confidential data sets may not be adequate (An, Zaaba &
Samsudin, 2016)
Weak Security
Management
There may be too many enterprise managers involved that may
lead to the presence of conflicts and inability to develop strong
security policies. This may lead to the presence of security
vulnerabilities
Eavesdropping Attacks The attackers may intrude the network channels and monitor the
network activities to obtain confidential information
Lack of Data Ownership There may be too many data owners involved that may lead to
poor ownership and control leading to the presence of security
vulnerabilities
Insider Threats & Attacks The employees of Regional Gardens may pass on the
information to the unauthorized entities violating the security
norms. This may be deliberate or accidental
Risk Register
Risk Name Impact Score
(Very High – 5
High – 4
Average – 3
Minor – 2
Low – 1)
Likelihood
Score (Very
High – 5
High – 4
Average – 3
Minor – 2
Low – 1)
Risk
Score/Rank
(Impact x
Likelihood)
Treatment & Response
Strategy
Encryption Issues 4 3 12 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Denial of Service &
Distributed Denial of
Service Attacks
5 4 20 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
5
Poor IP Protection The protection measures installed for the sensitive and
confidential data sets may not be adequate (An, Zaaba &
Samsudin, 2016)
Weak Security
Management
There may be too many enterprise managers involved that may
lead to the presence of conflicts and inability to develop strong
security policies. This may lead to the presence of security
vulnerabilities
Eavesdropping Attacks The attackers may intrude the network channels and monitor the
network activities to obtain confidential information
Lack of Data Ownership There may be too many data owners involved that may lead to
poor ownership and control leading to the presence of security
vulnerabilities
Insider Threats & Attacks The employees of Regional Gardens may pass on the
information to the unauthorized entities violating the security
norms. This may be deliberate or accidental
Risk Register
Risk Name Impact Score
(Very High – 5
High – 4
Average – 3
Minor – 2
Low – 1)
Likelihood
Score (Very
High – 5
High – 4
Average – 3
Minor – 2
Low – 1)
Risk
Score/Rank
(Impact x
Likelihood)
Treatment & Response
Strategy
Encryption Issues 4 3 12 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Denial of Service &
Distributed Denial of
Service Attacks
5 4 20 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
5
Regional Gardens Ltd.
control the risk. Risk
mitigation may be used in
case of occurrence.
Malware Attacks 4 4 16 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Data Leakage 4 4 16 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Unprotected APIs 4 3 12 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Authentication & Identity
Issues
4 2 8 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Poor IP Protection 5 2 10 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Weak Security 4 3 12 Risk avoidance shall be the
6
control the risk. Risk
mitigation may be used in
case of occurrence.
Malware Attacks 4 4 16 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Data Leakage 4 4 16 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Unprotected APIs 4 3 12 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Authentication & Identity
Issues
4 2 8 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Poor IP Protection 5 2 10 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Weak Security 4 3 12 Risk avoidance shall be the
6
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Regional Gardens Ltd.
Management treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Eavesdropping Attacks 4 4 16 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Lack of Data Ownership 3 3 9 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Insider Threats & Attacks 4 3 12 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Treatment Strategies & Controls
Risk Name Treatment Strategies
Encryption Issues The cryptographic and encryption protocols and algorithms that are
utilized by the organization must ensure that the latest available norms
are used and implemented. Reliable proxy server and secure shell
network must be utilized.
Denial of Service &
Distributed Denial
of Service Attacks
There are anti-denial tools that are available in the market and these
tools must be implemented across the organization. Flow analytics shall
also be used to assess the network flow and the patterns involved in the
7
Management treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Eavesdropping Attacks 4 4 16 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Lack of Data Ownership 3 3 9 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Insider Threats & Attacks 4 3 12 Risk avoidance shall be the
treatment strategy adopted
to prevent, detect, and
control the risk. Risk
mitigation may be used in
case of occurrence.
Treatment Strategies & Controls
Risk Name Treatment Strategies
Encryption Issues The cryptographic and encryption protocols and algorithms that are
utilized by the organization must ensure that the latest available norms
are used and implemented. Reliable proxy server and secure shell
network must be utilized.
Denial of Service &
Distributed Denial
of Service Attacks
There are anti-denial tools that are available in the market and these
tools must be implemented across the organization. Flow analytics shall
also be used to assess the network flow and the patterns involved in the
7
Regional Gardens Ltd.
same.
Malware Attacks Anti-malware tools must be used and deployed across the organization.
Data Leakage The leakage and beaching of information may take place due to security
vulnerabilities. There shall be data loss prevention measures that shall
be used. Also, advanced access control and authentication protocols
shall be utilized so that such occurrences do not take place.
Unprotected APIs The third-parties associated with the organization shall be verified
before they are handed over the security key. Also, the vulnerability
assessment shall be done regularly (Vurukonda & Rao, 2016).
Authentication &
Identity Issues
There shall be multi-path asymmetric and symmetric access control,
role-based and attribute-based access control that shall be used. Multi-
fold authentication using the combination of user credentials, one time
passwords, single sign on, and biometric recognition shall be done.
Poor IP Protection The network security shall be enhanced with the use of installation of
automated network scanner and auditors. System logs shall also be
automatically captured and analysed.
Weak Security
Management
The organization must develop security plans and policies that shall be
followed and implemented and there must be automated tools used to
assess the compliance of the same.
Eavesdropping
Attacks
There are network-based intrusion detection and prevention tools
developed along with automated network monitors that must be
implemented.
Lack of Data
Ownership
The data ownership shall be defined and store in the centralized
repository and the databased and the permissions and rights shall be set
up accordingly.
Insider Threats &
Attacks
The employees of the organization shall be provided with the security
and ethical trainings and there performance shall be monitored using
automated performance assessment tools (Mathkunti, 2014).
Proposed Information Security Controls
There are various security risks and issues that may take place in any of the business
organization. The data sets present with the organization may not be encrypted properly
leading to the exposure of information properties and contents. The malicious entities may
8
same.
Malware Attacks Anti-malware tools must be used and deployed across the organization.
Data Leakage The leakage and beaching of information may take place due to security
vulnerabilities. There shall be data loss prevention measures that shall
be used. Also, advanced access control and authentication protocols
shall be utilized so that such occurrences do not take place.
Unprotected APIs The third-parties associated with the organization shall be verified
before they are handed over the security key. Also, the vulnerability
assessment shall be done regularly (Vurukonda & Rao, 2016).
Authentication &
Identity Issues
There shall be multi-path asymmetric and symmetric access control,
role-based and attribute-based access control that shall be used. Multi-
fold authentication using the combination of user credentials, one time
passwords, single sign on, and biometric recognition shall be done.
Poor IP Protection The network security shall be enhanced with the use of installation of
automated network scanner and auditors. System logs shall also be
automatically captured and analysed.
Weak Security
Management
The organization must develop security plans and policies that shall be
followed and implemented and there must be automated tools used to
assess the compliance of the same.
Eavesdropping
Attacks
There are network-based intrusion detection and prevention tools
developed along with automated network monitors that must be
implemented.
Lack of Data
Ownership
The data ownership shall be defined and store in the centralized
repository and the databased and the permissions and rights shall be set
up accordingly.
Insider Threats &
Attacks
The employees of the organization shall be provided with the security
and ethical trainings and there performance shall be monitored using
automated performance assessment tools (Mathkunti, 2014).
Proposed Information Security Controls
There are various security risks and issues that may take place in any of the business
organization. The data sets present with the organization may not be encrypted properly
leading to the exposure of information properties and contents. The malicious entities may
8

Regional Gardens Ltd.
launch garbage traffic on the cloud connections which may disrupt the availability of the
service and the data sets. There may be attacks of malicious codes, such as viruses, worms,
logic bombs, ransomware, and others. The data and information present on the cloud
architecture may get leaked in between that may impact the integrity of the information sets.
API endpoints may be utilized by the malevolent entities to expose the sensitive data and
information sets. Access to the sensitive and confidential data sets provided to the
unauthorized entities due to poor authentication and identity management. The protection
measures installed for the sensitive and confidential data sets may not be adequate. There
may be too many enterprise managers involved that may lead to the presence of conflicts and
inability to develop strong security policies. This may lead to the presence of security
vulnerabilities. The attackers may intrude the network channels and monitor the network
activities to obtain confidential information. There may be too many data owners involved
that may lead to poor ownership and control leading to the presence of security
vulnerabilities. The employees of an organization may pass on the information to the
unauthorized entities violating the security norms. This may be deliberate or accidental.
Administrative Controls
The primary responsibility of an organization is to develop an information security plan and
policy that shall be implemented across the organization. The plan and policies must
comprise of the security standards and practices that shall be followed, possible security
risks, impact of these risks on the resources and organizations, and the set of controls that
shall be applied. These plans shall be regularly updated. The responsibility of these tasks
shall be on the Chief Information Security Officer (CIO) along with the other resources in the
security team.
CIO, Security Manager, Security Auditor, and Security Analysts must carry out regular and
frequent security audits and inspections. Such practices will highlight the possible security
loopholes and the areas of improvement. The team must publish the security do(s) and
don’t(s) for the resources and the review reports shall also be shared (Anderson, Baskerville
& Kaul, 2017).
Vulnerability and risk assessment policy shall also be developed according to which there
must be regular assessment of possible security weaknesses in the organization. It would also
be essential to develop risk management plans comprising of the steps as risk identification,
risk assessment, risk evaluation, risk treatment, risk monitoring, and risk closure. The risk
9
launch garbage traffic on the cloud connections which may disrupt the availability of the
service and the data sets. There may be attacks of malicious codes, such as viruses, worms,
logic bombs, ransomware, and others. The data and information present on the cloud
architecture may get leaked in between that may impact the integrity of the information sets.
API endpoints may be utilized by the malevolent entities to expose the sensitive data and
information sets. Access to the sensitive and confidential data sets provided to the
unauthorized entities due to poor authentication and identity management. The protection
measures installed for the sensitive and confidential data sets may not be adequate. There
may be too many enterprise managers involved that may lead to the presence of conflicts and
inability to develop strong security policies. This may lead to the presence of security
vulnerabilities. The attackers may intrude the network channels and monitor the network
activities to obtain confidential information. There may be too many data owners involved
that may lead to poor ownership and control leading to the presence of security
vulnerabilities. The employees of an organization may pass on the information to the
unauthorized entities violating the security norms. This may be deliberate or accidental.
Administrative Controls
The primary responsibility of an organization is to develop an information security plan and
policy that shall be implemented across the organization. The plan and policies must
comprise of the security standards and practices that shall be followed, possible security
risks, impact of these risks on the resources and organizations, and the set of controls that
shall be applied. These plans shall be regularly updated. The responsibility of these tasks
shall be on the Chief Information Security Officer (CIO) along with the other resources in the
security team.
CIO, Security Manager, Security Auditor, and Security Analysts must carry out regular and
frequent security audits and inspections. Such practices will highlight the possible security
loopholes and the areas of improvement. The team must publish the security do(s) and
don’t(s) for the resources and the review reports shall also be shared (Anderson, Baskerville
& Kaul, 2017).
Vulnerability and risk assessment policy shall also be developed according to which there
must be regular assessment of possible security weaknesses in the organization. It would also
be essential to develop risk management plans comprising of the steps as risk identification,
risk assessment, risk evaluation, risk treatment, risk monitoring, and risk closure. The risk
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Regional Gardens Ltd.
register shall be prepared for the risks that are identified and shall be updated to incorporate
newer risks in the register.
The employees must be made aware of the security practices that they shall follow through
the organization of the security trainings and sessions. There are deliberate or accidental
occurrences given shape by the employees wherein they transfer the sensitive information
sets to the unauthorized entities (Otero, 2010). The employees must be aware of the possible
outcomes of such a situation and shall also be provided with the ethical trainings and
principles. The ethical codes shall be known to the employees.
Technical/Logical Controls
The organizations in the current times are making use of the schemes, such as remote
working and Bring Your Own Devices (BYOD) at work. Such schemes enhance the
employee satisfaction levels but bring in a lot many device related security issues. The
employees are provided with the ability to access the sensitive data and information
associated with the business on their personal gadgets. The connectivity of such devices to
unsecure networks or exposure of the sensitive information to unauthorized entities may lead
to the emergence of security risks and attacks. For this purpose, there shall be device security
controls, such as device trackers, encryption of the device data, and device logs that shall be
included.
There are certain basic security practices that shall be followed, such as use and
implementation of proxy server and firewalls. The use of weak or poor passwords by the
users is one of the prime reasons that provide the attackers with the ability to give shape to
the security attacks. Such incidents may be avoided by using stronger passwords. The
cryptographic and encryption protocols and algorithms that are utilized by the organization
must ensure that the latest available norms are used and implemented. Reliable proxy server
and secure shell network must be utilized. There are anti-denial tools that are available in the
market and these tools must be implemented across the organization. Flow analytics shall
also be used to assess the network flow and the patterns involved in the same. Anti-malware
tools must be used and deployed across the organization. The leakage and beaching of
information may take place due to security vulnerabilities. There shall be data loss prevention
measures that shall be used. Also, advanced access control and authentication protocols shall
be utilized so that such occurrences do not take place. The third-parties associated with the
organization shall be verified before they are handed over the security key. Also, the
10
register shall be prepared for the risks that are identified and shall be updated to incorporate
newer risks in the register.
The employees must be made aware of the security practices that they shall follow through
the organization of the security trainings and sessions. There are deliberate or accidental
occurrences given shape by the employees wherein they transfer the sensitive information
sets to the unauthorized entities (Otero, 2010). The employees must be aware of the possible
outcomes of such a situation and shall also be provided with the ethical trainings and
principles. The ethical codes shall be known to the employees.
Technical/Logical Controls
The organizations in the current times are making use of the schemes, such as remote
working and Bring Your Own Devices (BYOD) at work. Such schemes enhance the
employee satisfaction levels but bring in a lot many device related security issues. The
employees are provided with the ability to access the sensitive data and information
associated with the business on their personal gadgets. The connectivity of such devices to
unsecure networks or exposure of the sensitive information to unauthorized entities may lead
to the emergence of security risks and attacks. For this purpose, there shall be device security
controls, such as device trackers, encryption of the device data, and device logs that shall be
included.
There are certain basic security practices that shall be followed, such as use and
implementation of proxy server and firewalls. The use of weak or poor passwords by the
users is one of the prime reasons that provide the attackers with the ability to give shape to
the security attacks. Such incidents may be avoided by using stronger passwords. The
cryptographic and encryption protocols and algorithms that are utilized by the organization
must ensure that the latest available norms are used and implemented. Reliable proxy server
and secure shell network must be utilized. There are anti-denial tools that are available in the
market and these tools must be implemented across the organization. Flow analytics shall
also be used to assess the network flow and the patterns involved in the same. Anti-malware
tools must be used and deployed across the organization. The leakage and beaching of
information may take place due to security vulnerabilities. There shall be data loss prevention
measures that shall be used. Also, advanced access control and authentication protocols shall
be utilized so that such occurrences do not take place. The third-parties associated with the
organization shall be verified before they are handed over the security key. Also, the
10

Regional Gardens Ltd.
vulnerability assessment shall be done regularly. There shall be multi-path asymmetric and
symmetric access control, role-based and attribute-based access control that shall be used.
Multi-fold authentication using the combination of user credentials, one time passwords,
single sign on, and biometric recognition shall be done. The network security shall be
enhanced with the use of installation of automated network scanner and auditors. System logs
shall also be automatically captured and analysed. The organization must develop security
plans and policies that shall be followed and implemented and there must be automated tools
used to assess the compliance of the same. There are network-based intrusion detection and
prevention tools developed along with automated network monitors that must be
implemented (Fazlida & Said, 2015). The data ownership shall be defined and store in the
centralized repository and the databased and the permissions and rights shall be set up
accordingly. The employees of the organization shall be provided with the security and
ethical trainings and there performance shall be monitored using automated performance
assessment tools. Disaster recovery is a method that may be used to put check on the damage
that may be caused after the occurrence of the security risk or other disaster. The readiness of
an organization to deal with such situations must be updated at all times. There are automated
backup and disaster recovery tools that shall be set in place.
Physical Controls
With the development of the technical controls and measures, the security architects and team
have started ignoring the importance of physical security controls for an organization.
There must be entry of only the authorized entities that shall be allowed in the premises of a
business organization. Physical security plays a great role in ensuring the same. There must
be security guards and personnel deployed at all of the entry and exit gates and the identity
verification, and bag checking shall be performed while entering and exiting from the
premises.
There shall also be physical security of the sensitive areas, such as server rooms and data
centres that shall be enhanced with security personnel. The monitoring of the security shall be
manually and physically done to avoid the occurrence of any security risk.
11
vulnerability assessment shall be done regularly. There shall be multi-path asymmetric and
symmetric access control, role-based and attribute-based access control that shall be used.
Multi-fold authentication using the combination of user credentials, one time passwords,
single sign on, and biometric recognition shall be done. The network security shall be
enhanced with the use of installation of automated network scanner and auditors. System logs
shall also be automatically captured and analysed. The organization must develop security
plans and policies that shall be followed and implemented and there must be automated tools
used to assess the compliance of the same. There are network-based intrusion detection and
prevention tools developed along with automated network monitors that must be
implemented (Fazlida & Said, 2015). The data ownership shall be defined and store in the
centralized repository and the databased and the permissions and rights shall be set up
accordingly. The employees of the organization shall be provided with the security and
ethical trainings and there performance shall be monitored using automated performance
assessment tools. Disaster recovery is a method that may be used to put check on the damage
that may be caused after the occurrence of the security risk or other disaster. The readiness of
an organization to deal with such situations must be updated at all times. There are automated
backup and disaster recovery tools that shall be set in place.
Physical Controls
With the development of the technical controls and measures, the security architects and team
have started ignoring the importance of physical security controls for an organization.
There must be entry of only the authorized entities that shall be allowed in the premises of a
business organization. Physical security plays a great role in ensuring the same. There must
be security guards and personnel deployed at all of the entry and exit gates and the identity
verification, and bag checking shall be performed while entering and exiting from the
premises.
There shall also be physical security of the sensitive areas, such as server rooms and data
centres that shall be enhanced with security personnel. The monitoring of the security shall be
manually and physically done to avoid the occurrence of any security risk.
11

Regional Gardens Ltd.
BCP Changes
Application Resilience
The cloud requirements of the Regional Gardens Ltd include availability of the services and
applications as one of the most important and relevant properties. There are a certain steps
that are recommended and may be used to meet this requirement. This includes numerous
availability zones in specific areas of operations, load balancing, automated scaling of the
cloud and other technical components involved with the company, regular reviews and data
recovery mechanisms. The steps included in the strategy are listed below.
Fault tolerance as one of the prime properties of the applications and cloud services
that are designed and developed for the organziation
Inclusion of the latest security norms and principles
Enhanced data storage options
Hybrid cloud archietcture and platform
Data Storage and Backup
AWS hybrid cloud archietcture can be easily integrated with its in-house and other data
storage options. There are Big Data tools and NoSQL databases recommended for data
storage and backup.
Hadoop
Hadoop is one of the Big Data tools that is open source and may be used to store tha
massive clusters of data associated with the organization. The tools has been
developed using Java as the prgramming language and offers a number of benefits.
The tools is scalable in nature and will make it possible to meet the flexible
requirements of the organization. The changes will be easily incorporated. The tool is
open soruce and therefore, it will prove to be cost-effective for the organization as
compared to the other options in the market (Dhyani & Barthwal, 2014). Fault
tolerance is another basic property that comes easy with the tool.
Hyperscale Storage Architecture
It is another option that may be considered for data storage and backup. It makes use
of Direct-attached storage (DAS) which will provide the orgainization to carry out
enahnced data analytics and warehousing of the data sets. In case of a failure or issue
in any of the components then the replacement will be easy.
12
BCP Changes
Application Resilience
The cloud requirements of the Regional Gardens Ltd include availability of the services and
applications as one of the most important and relevant properties. There are a certain steps
that are recommended and may be used to meet this requirement. This includes numerous
availability zones in specific areas of operations, load balancing, automated scaling of the
cloud and other technical components involved with the company, regular reviews and data
recovery mechanisms. The steps included in the strategy are listed below.
Fault tolerance as one of the prime properties of the applications and cloud services
that are designed and developed for the organziation
Inclusion of the latest security norms and principles
Enhanced data storage options
Hybrid cloud archietcture and platform
Data Storage and Backup
AWS hybrid cloud archietcture can be easily integrated with its in-house and other data
storage options. There are Big Data tools and NoSQL databases recommended for data
storage and backup.
Hadoop
Hadoop is one of the Big Data tools that is open source and may be used to store tha
massive clusters of data associated with the organization. The tools has been
developed using Java as the prgramming language and offers a number of benefits.
The tools is scalable in nature and will make it possible to meet the flexible
requirements of the organization. The changes will be easily incorporated. The tool is
open soruce and therefore, it will prove to be cost-effective for the organization as
compared to the other options in the market (Dhyani & Barthwal, 2014). Fault
tolerance is another basic property that comes easy with the tool.
Hyperscale Storage Architecture
It is another option that may be considered for data storage and backup. It makes use
of Direct-attached storage (DAS) which will provide the orgainization to carry out
enahnced data analytics and warehousing of the data sets. In case of a failure or issue
in any of the components then the replacement will be easy.
12
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Regional Gardens Ltd.
NoSQL databases may also be considered to store the data sets associated with the
organziation and to perfrom the backup operations. These databases will be able to carry out
the Big Data analytics along with the other data related operations easily. The mode of
exploration will be flexible and there will be various parameters associated with it, such as
time, location, profits, users, quantites, etc. Predictive analysis and clustering will also be
easier to perform on the data sets.
There are numerous NoSQL databases that are available in the market. Some of the options
that may be considered are as listed below.
MongoDB
The database is developed on the principles of agile framework and will therefore
offer enhanced scalability and flexibility.
Elasticsearch
The database will support the multi-tenancy architecture of cloud and will allow the
execution of SOAP as well as REST services.
CouchDB
The indexes may be queries using any of the web browsers and the database will also
allow the storage of the documents.
AmazonSimpleDB
There will be enhanced database administration and maintenance that will be offered
by this tool apart from the usual data related services.
MarkLogicServer
The database is designed to be deployed at the enterprise level and it will allow the
easy integration of the other technical tools and components.
Terrastore
Scalability, flexibility, massive data storage, document storage, document extraction,
indexing, and others will be possible with the use of the database (Pokorny, 2013).
Disaster Recovery
Security is another primary concern that is witnessed with the hybrid cloud architecture.
There may be security issues as lack of encryption, denial of service and distributed denial of
service attacks, malware attacks, data leakage, authentication issues, etc. that may come up.
The malicious entities may launch garbage traffic on the cloud connections which may
disrupt the availability of the service and the data sets. There may be attacks of malicious
13
NoSQL databases may also be considered to store the data sets associated with the
organziation and to perfrom the backup operations. These databases will be able to carry out
the Big Data analytics along with the other data related operations easily. The mode of
exploration will be flexible and there will be various parameters associated with it, such as
time, location, profits, users, quantites, etc. Predictive analysis and clustering will also be
easier to perform on the data sets.
There are numerous NoSQL databases that are available in the market. Some of the options
that may be considered are as listed below.
MongoDB
The database is developed on the principles of agile framework and will therefore
offer enhanced scalability and flexibility.
Elasticsearch
The database will support the multi-tenancy architecture of cloud and will allow the
execution of SOAP as well as REST services.
CouchDB
The indexes may be queries using any of the web browsers and the database will also
allow the storage of the documents.
AmazonSimpleDB
There will be enhanced database administration and maintenance that will be offered
by this tool apart from the usual data related services.
MarkLogicServer
The database is designed to be deployed at the enterprise level and it will allow the
easy integration of the other technical tools and components.
Terrastore
Scalability, flexibility, massive data storage, document storage, document extraction,
indexing, and others will be possible with the use of the database (Pokorny, 2013).
Disaster Recovery
Security is another primary concern that is witnessed with the hybrid cloud architecture.
There may be security issues as lack of encryption, denial of service and distributed denial of
service attacks, malware attacks, data leakage, authentication issues, etc. that may come up.
The malicious entities may launch garbage traffic on the cloud connections which may
disrupt the availability of the service and the data sets. There may be attacks of malicious
13

Regional Gardens Ltd.
codes, such as viruses, worms, logic bombs, ransomware, and others. These and the other
security issues may be extremely adverse for the organization and there are recovery tools
and controls that shall be used to deal with such issues.
Preventative: The primary security controls, such as the use of firewalls, use of strong
passwords, identity and access control measures, etc. shall be used so that the
occurrence of the security risks are prevented.
Reactive: There may be scenarios wherein the security risk may take place and
controls, such as backups and encryption will come in the picture in such cases.
Detective: There are tools developed that detect any of the suspicious activity, such as
anti-malware tools, intrusion detection tools, etc. that shall be used.
Administrative: The management of the organization shall be proactive and must have
defined security norms and controls in place so that the security risks and attacks are
avoided.
Disaster recovery is a method that may be used to put check on the damage that may be
caused after the occurrence of the security risk or other disaster. The readiness of an
organization to deal with such situations must be updated at all times.
Hybrid Cloud Administration & SLA Management
Remote Administration
Remote Administration is defined as the process of controlling the computer systems and
associated components from any of the remote locations instead of being physically available
for the task. The use and execution of remote administration is not encouraged because of the
drawbacks and issues that it comes along. There are scenarios wherein the tools being used in
the administration activities may turn faulty or may not scale as per the requirement. This
may lead to the issues for the administrator to carry on with the activities on the network with
varied speeds without hampering the security. There are also issues witnessed in the area of
multi-platform support. The business organizations make of use of varied operating systems,
such as Windows, Linux, UNIX, Macintosh, and others. The case is the same with Regional
Gardens Ltd. apart from the varied operating systems, there are varied mobile devices that are
also used. The use of such devices and operating systems and the presence of the tools to
administer them all may be an issue.
14
codes, such as viruses, worms, logic bombs, ransomware, and others. These and the other
security issues may be extremely adverse for the organization and there are recovery tools
and controls that shall be used to deal with such issues.
Preventative: The primary security controls, such as the use of firewalls, use of strong
passwords, identity and access control measures, etc. shall be used so that the
occurrence of the security risks are prevented.
Reactive: There may be scenarios wherein the security risk may take place and
controls, such as backups and encryption will come in the picture in such cases.
Detective: There are tools developed that detect any of the suspicious activity, such as
anti-malware tools, intrusion detection tools, etc. that shall be used.
Administrative: The management of the organization shall be proactive and must have
defined security norms and controls in place so that the security risks and attacks are
avoided.
Disaster recovery is a method that may be used to put check on the damage that may be
caused after the occurrence of the security risk or other disaster. The readiness of an
organization to deal with such situations must be updated at all times.
Hybrid Cloud Administration & SLA Management
Remote Administration
Remote Administration is defined as the process of controlling the computer systems and
associated components from any of the remote locations instead of being physically available
for the task. The use and execution of remote administration is not encouraged because of the
drawbacks and issues that it comes along. There are scenarios wherein the tools being used in
the administration activities may turn faulty or may not scale as per the requirement. This
may lead to the issues for the administrator to carry on with the activities on the network with
varied speeds without hampering the security. There are also issues witnessed in the area of
multi-platform support. The business organizations make of use of varied operating systems,
such as Windows, Linux, UNIX, Macintosh, and others. The case is the same with Regional
Gardens Ltd. apart from the varied operating systems, there are varied mobile devices that are
also used. The use of such devices and operating systems and the presence of the tools to
administer them all may be an issue.
14

Regional Gardens Ltd.
However, hybrid cloud architecture provides the ability to remotely administer the resources,
operations, applications, and services. It is because of the scalability and flexibility that
comes along with the architecture.
Resource Management
Another area that shall be managed for the organization in association with the hybrid cloud
architecture and migration to the cloud is resource management. There are a lot many
resources that are associated with the business organization, such as the senior leaders and
managers, directors, marketing associates, support staff, members of the operational team,
sales staff, and many others. There are also stakeholders that are associated with the business
that need to be managed.
It is required for the organization to develop the strategy to effectuvely manage all of the
internal, external, and remote resources distributed across the various departments. The
following points shall be kept in consideration while developing the strategy.
The resource tagging and management strategy that is currently being followed by the
organization.
The number of departments and the inter linking of different departments as required
by the business operations and activties.
The set of steps that are followed while allocation or deallocation of the resource from
a project.
The utilization of the resources in th events of overrun of schedule and cost in a
project.
The availability of the metadata with the organization.
There are also various advantages that will be provided to the organization with the
implementation of the resource management startegy.
The management will be able to understand the skill set of the employees along with
their respective areas of expertise.
The data and the information sets will be stored in a centralized repository and the
access to the data sets will become easier.
The transparency between the employees and the management will be improved.
The processes of managing the changes, budget, schedule, and effort will become
easier.
15
However, hybrid cloud architecture provides the ability to remotely administer the resources,
operations, applications, and services. It is because of the scalability and flexibility that
comes along with the architecture.
Resource Management
Another area that shall be managed for the organization in association with the hybrid cloud
architecture and migration to the cloud is resource management. There are a lot many
resources that are associated with the business organization, such as the senior leaders and
managers, directors, marketing associates, support staff, members of the operational team,
sales staff, and many others. There are also stakeholders that are associated with the business
that need to be managed.
It is required for the organization to develop the strategy to effectuvely manage all of the
internal, external, and remote resources distributed across the various departments. The
following points shall be kept in consideration while developing the strategy.
The resource tagging and management strategy that is currently being followed by the
organization.
The number of departments and the inter linking of different departments as required
by the business operations and activties.
The set of steps that are followed while allocation or deallocation of the resource from
a project.
The utilization of the resources in th events of overrun of schedule and cost in a
project.
The availability of the metadata with the organization.
There are also various advantages that will be provided to the organization with the
implementation of the resource management startegy.
The management will be able to understand the skill set of the employees along with
their respective areas of expertise.
The data and the information sets will be stored in a centralized repository and the
access to the data sets will become easier.
The transparency between the employees and the management will be improved.
The processes of managing the changes, budget, schedule, and effort will become
easier.
15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Regional Gardens Ltd.
There will be strategic alignment formed between the individual goals of an employee
and the organizational objectives.
The resource utilization will be improved which will lead to the decrease in employee
turnover rate and it will also lead to the enhancement of the resource engagement with
the organziation.
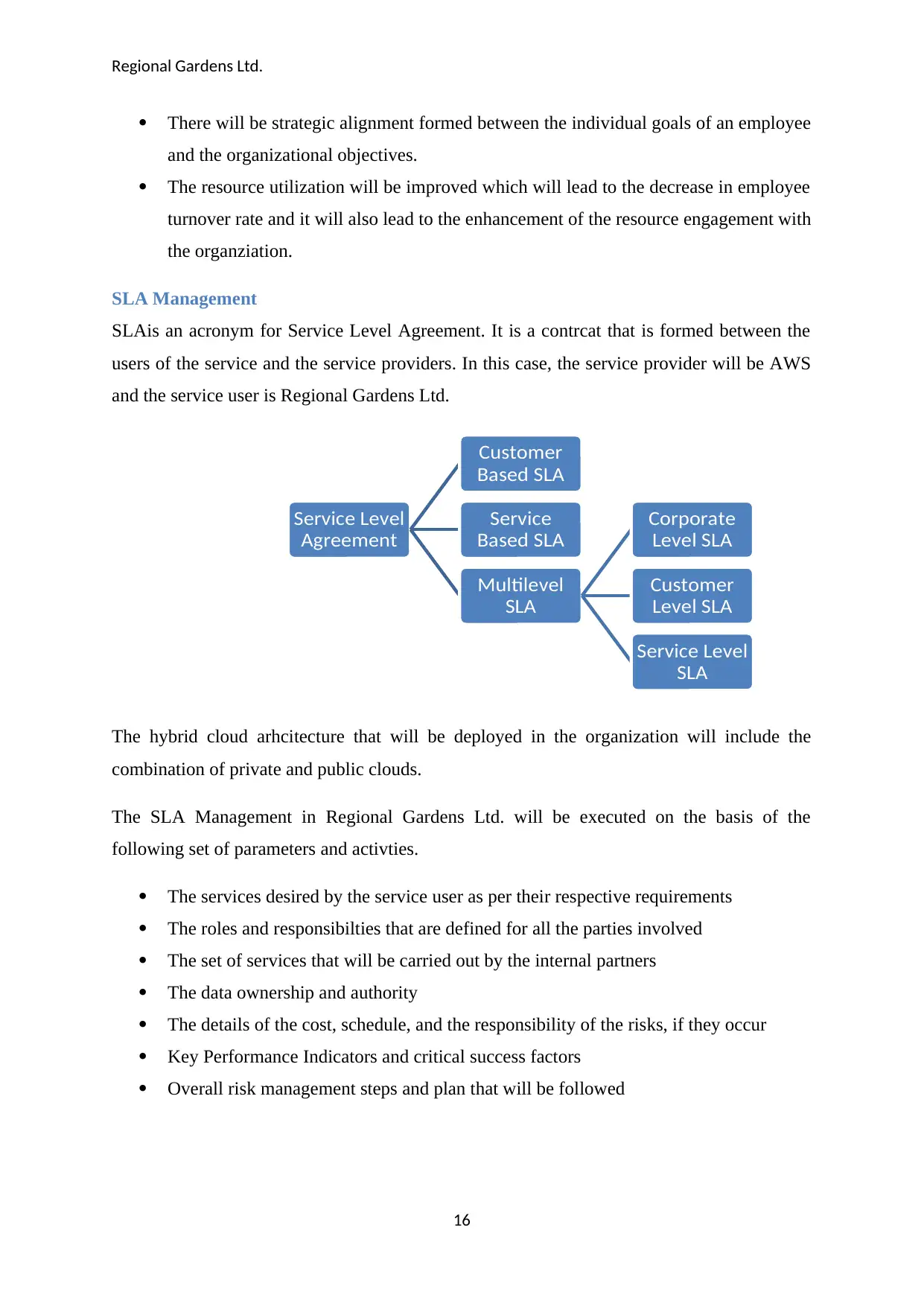
SLA Management
SLAis an acronym for Service Level Agreement. It is a contrcat that is formed between the
users of the service and the service providers. In this case, the service provider will be AWS
and the service user is Regional Gardens Ltd.
The hybrid cloud arhcitecture that will be deployed in the organization will include the
combination of private and public clouds.
The SLA Management in Regional Gardens Ltd. will be executed on the basis of the
following set of parameters and activties.
The services desired by the service user as per their respective requirements
The roles and responsibilties that are defined for all the parties involved
The set of services that will be carried out by the internal partners
The data ownership and authority
The details of the cost, schedule, and the responsibility of the risks, if they occur
Key Performance Indicators and critical success factors
Overall risk management steps and plan that will be followed
16
Service Level
Agreement
Customer
Based SLA
Service
Based SLA
Multilevel
SLA
Corporate
Level SLA
Customer
Level SLA
Service Level
SLA
There will be strategic alignment formed between the individual goals of an employee
and the organizational objectives.
The resource utilization will be improved which will lead to the decrease in employee
turnover rate and it will also lead to the enhancement of the resource engagement with
the organziation.
SLA Management
SLAis an acronym for Service Level Agreement. It is a contrcat that is formed between the
users of the service and the service providers. In this case, the service provider will be AWS
and the service user is Regional Gardens Ltd.
The hybrid cloud arhcitecture that will be deployed in the organization will include the
combination of private and public clouds.
The SLA Management in Regional Gardens Ltd. will be executed on the basis of the
following set of parameters and activties.
The services desired by the service user as per their respective requirements
The roles and responsibilties that are defined for all the parties involved
The set of services that will be carried out by the internal partners
The data ownership and authority
The details of the cost, schedule, and the responsibility of the risks, if they occur
Key Performance Indicators and critical success factors
Overall risk management steps and plan that will be followed
16
Service Level
Agreement
Customer
Based SLA
Service
Based SLA
Multilevel
SLA
Corporate
Level SLA
Customer
Level SLA
Service Level
SLA

Regional Gardens Ltd.
Migration Plan
The company has decided to move their email instance to the AWS cloud and there will be a
migration plan necessary to be put in place for the same.
Purpose of the Plan
The purpose of the plan is to list down the steps that will be followed in migrating email
instances to AWS cloud and develop countermeasures to deal with the issues that may come
up.
Migration Approach
The migration of the services will be done in a phased approach rather than implementing all
of it at once. The Big Bang migration is being avoided because it may lead to the presence of
increased number of risks and higher chances of failure. With the phased approach, the
overall management will be easy and it will be easier to handle the issues that may come up.
Phases in Migration
Initiation Phase
The first phase that will be involved in the process of migration will be the initiation phase. It
will start with the highlighting of the activities that will be performed in the process of
moving the email instances to the AWS cloud. There will be feasibility studies that will be
carried out for the migration process on the steps, such as technical, operational, economic,
and environmental. The results of the feasibility studies will then be assessed to understand
the feasibility and success rate of the process.
The AWS cloud will be used for the first time in the organization and there will be
compatibility analysis that will be done. The compatibility will be calculated for the
integration of the cloud platform with the other components of the business organization.
Planning Phase
The second phase, as planning phase will be the most important phase involved in the process
of migrating email instances to the AWS cloud.
The migration will be done in primary three categories as data migration, migration of the
services, and integration of the newly migrated components with the newer platform. The
planning processes will be carried out for each of these three areas. There will be scope
definition that will be formed as the first step in the migration planning. The activities that
17
Migration Plan
The company has decided to move their email instance to the AWS cloud and there will be a
migration plan necessary to be put in place for the same.
Purpose of the Plan
The purpose of the plan is to list down the steps that will be followed in migrating email
instances to AWS cloud and develop countermeasures to deal with the issues that may come
up.
Migration Approach
The migration of the services will be done in a phased approach rather than implementing all
of it at once. The Big Bang migration is being avoided because it may lead to the presence of
increased number of risks and higher chances of failure. With the phased approach, the
overall management will be easy and it will be easier to handle the issues that may come up.
Phases in Migration
Initiation Phase
The first phase that will be involved in the process of migration will be the initiation phase. It
will start with the highlighting of the activities that will be performed in the process of
moving the email instances to the AWS cloud. There will be feasibility studies that will be
carried out for the migration process on the steps, such as technical, operational, economic,
and environmental. The results of the feasibility studies will then be assessed to understand
the feasibility and success rate of the process.
The AWS cloud will be used for the first time in the organization and there will be
compatibility analysis that will be done. The compatibility will be calculated for the
integration of the cloud platform with the other components of the business organization.
Planning Phase
The second phase, as planning phase will be the most important phase involved in the process
of migrating email instances to the AWS cloud.
The migration will be done in primary three categories as data migration, migration of the
services, and integration of the newly migrated components with the newer platform. The
planning processes will be carried out for each of these three areas. There will be scope
definition that will be formed as the first step in the migration planning. The activities that
17

Regional Gardens Ltd.
will be covered and discarded will be listed down. The next step will include the estimation
and definition of the schedule and costs. It would be necessary to adhere to a specified
schedule and budget so that the errors may be avoided.
The next steps in the planning phase will include the gathering and determination of the data
requirements, service integration, and analytics of the same. The possible risks in the process
will also be highlighted and the risk management plan shall be formed. Vulnerability and risk
assessment policy shall also be developed according to which there must be regular
assessment of possible weaknesses in the process. It would also be essential to develop risk
management plans comprising of the steps as risk identification, risk assessment, risk
evaluation, risk treatment, risk monitoring, and risk closure. The risk register shall be
prepared for the risks that are identified and shall be updated to incorporate newer risks in the
register (Zhao & Zhou, 2014).
The resources shall be allocated with the duties and responsibilities to carry out these
activities. There shall also be communication plan that shall be formed for reporting and
information sharing purposes.
Execution Phase
The deployment of AWS cloud will be done in the organization. The actual execution of the
migration activities will be done in this phase. The email instances will be migrated on the
basis of every service to the AWS cloud.
The data sets will be migrated as a first step followed by the migration of the services. Once
the migration of the services and data will be completed, it would be required to carry out the
integration of the same. The components will be integrated and run on the new AWS cloud
platform.
Control Phase
The monitoring and testing of the process will be essential so that the process is successful.
This phase will begin with the testing activities and the following test processes will be
carried out:
System Integration Tests: The execution of the services on the AWS Cloud will be
tested in terms of the functional behavior and fulfilment of the requirements. The
mapping will be done with the outcomes associated with the email instances and the
activities being carried out on the AWS cloud platform (Reavis, 2012).
18
will be covered and discarded will be listed down. The next step will include the estimation
and definition of the schedule and costs. It would be necessary to adhere to a specified
schedule and budget so that the errors may be avoided.
The next steps in the planning phase will include the gathering and determination of the data
requirements, service integration, and analytics of the same. The possible risks in the process
will also be highlighted and the risk management plan shall be formed. Vulnerability and risk
assessment policy shall also be developed according to which there must be regular
assessment of possible weaknesses in the process. It would also be essential to develop risk
management plans comprising of the steps as risk identification, risk assessment, risk
evaluation, risk treatment, risk monitoring, and risk closure. The risk register shall be
prepared for the risks that are identified and shall be updated to incorporate newer risks in the
register (Zhao & Zhou, 2014).
The resources shall be allocated with the duties and responsibilities to carry out these
activities. There shall also be communication plan that shall be formed for reporting and
information sharing purposes.
Execution Phase
The deployment of AWS cloud will be done in the organization. The actual execution of the
migration activities will be done in this phase. The email instances will be migrated on the
basis of every service to the AWS cloud.
The data sets will be migrated as a first step followed by the migration of the services. Once
the migration of the services and data will be completed, it would be required to carry out the
integration of the same. The components will be integrated and run on the new AWS cloud
platform.
Control Phase
The monitoring and testing of the process will be essential so that the process is successful.
This phase will begin with the testing activities and the following test processes will be
carried out:
System Integration Tests: The execution of the services on the AWS Cloud will be
tested in terms of the functional behavior and fulfilment of the requirements. The
mapping will be done with the outcomes associated with the email instances and the
activities being carried out on the AWS cloud platform (Reavis, 2012).
18
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Regional Gardens Ltd.
Performance Tests: The performance of the services and the data sets on the AWS
cloud will be tested in terms of the impact of load and load balancing abilities,
response time, and throughput time.
Security Tests: There are numerous security risks and events that take place due to the
presence of security vulnerabilities in the process of migration. The security tests will
be run to find out such security loopholes.
Regression Tests: There may be a few defects that may be encountered and will be
resolved. The provided resolutions will be tested along with the existing
functionalities.
The senior administrators and technical experts will be required to monitor and control the
activities. There shall be reviews and inspections of the migration process that shall be
carried out by these entities.
There will also be numerous changes that will be introduced with the migration of email
instances to the AWS cloud. These changes will be managed using a change management
plan defined and prepared for the migration process. The change management plan will
include the steps as change planning, change execution, and change management. The
resources shall be provided with the trainings on the new platform so that they may
understand each feature of the same.
Closure Phase
The last phase that will be involved in the process will be the closure phase. This phase shall
mark the end of the migration process and there shall be final reviews and audits that must be
carried out in this phase.
The performance of the newer platform shall be assessed and the continuous improvement
process shall also be defined.
Critical Points & Issues
The five phases that will be associated with the migration of the email instances to AWS
cloud will have certain critical points and issues.
The initiation phase will have the most critical element as feasibility analysis. Poor or
inadequate feasibility study may bring in technical or operational errors in the advanced
stages of the migration process. Therefore, technical experts shall be invited to validate and
verify the process and the results of the feasibility studies to avoid any risks in the future.
19
Performance Tests: The performance of the services and the data sets on the AWS
cloud will be tested in terms of the impact of load and load balancing abilities,
response time, and throughput time.
Security Tests: There are numerous security risks and events that take place due to the
presence of security vulnerabilities in the process of migration. The security tests will
be run to find out such security loopholes.
Regression Tests: There may be a few defects that may be encountered and will be
resolved. The provided resolutions will be tested along with the existing
functionalities.
The senior administrators and technical experts will be required to monitor and control the
activities. There shall be reviews and inspections of the migration process that shall be
carried out by these entities.
There will also be numerous changes that will be introduced with the migration of email
instances to the AWS cloud. These changes will be managed using a change management
plan defined and prepared for the migration process. The change management plan will
include the steps as change planning, change execution, and change management. The
resources shall be provided with the trainings on the new platform so that they may
understand each feature of the same.
Closure Phase
The last phase that will be involved in the process will be the closure phase. This phase shall
mark the end of the migration process and there shall be final reviews and audits that must be
carried out in this phase.
The performance of the newer platform shall be assessed and the continuous improvement
process shall also be defined.
Critical Points & Issues
The five phases that will be associated with the migration of the email instances to AWS
cloud will have certain critical points and issues.
The initiation phase will have the most critical element as feasibility analysis. Poor or
inadequate feasibility study may bring in technical or operational errors in the advanced
stages of the migration process. Therefore, technical experts shall be invited to validate and
verify the process and the results of the feasibility studies to avoid any risks in the future.
19

Regional Gardens Ltd.
The planning phase is the most critical phase in the process as inadequate planning may bring
in the issues of schedule/budget overrun, resourcing issues, and quality issues. The
estimations of the schedule and budget shall be done adequately so that there are no gaps and
variances in the actual and final values. There shall also be allocation of the resources as per
their skill sets to achieve the maximum success rate. The quality of the process shall be
managed by adhering to the quality standards, such as Total Quality Management and Six
Sigma.
The execution process will involve the actual migration of the email instances to the AWS
cloud. The process may bring in the presence of security loopholes as the data may be leaked
in between. There may also be increased access points that may lead to the presence of
increase vulnerabilities. These may be utilized by the malicious entities to give shape to the
security attacks and threats, such as data breaches, data leakages, eavesdropping attacks,
malware attacks and others. The occurrence of any of such security issues may lead to the
compromise of the information properties, such as confidentiality, availability, and integrity.
There must be security tools and norms that shall be considered in this process. These shall
include the use of encryption of the data sets while migrating from the existing to the new
platforms. There shall also be logs maintained along with the use of virtual private network
that must be done.
The control and closure phases will involve the risks associated with the changes that the
migration process will bring in for the resources and for the organization. AWS Cloud will be
used in the organization for the first time and the resources may take time to get used to the
same. This may have an adverse implication on the productivity and efficiency levels of the
resources. There may also be operational issues that the resources may give shape to due to
the lack of expertise. Such issues and occurrences may be avoided with the organization of
trainings for the resources. They shall be provided with the information on the functionality
of AWS cloud and the primary areas of concerns associated with the same. The resources will
become comfortable with the new platform and will be able to utilize the same as per the
expectation. There shall also be assessment and reviews that must be frequently carried out
during the initial days to understand the performance of the platform and the usage of the
same by the resources without causing any major errors or loopholes.
20
The planning phase is the most critical phase in the process as inadequate planning may bring
in the issues of schedule/budget overrun, resourcing issues, and quality issues. The
estimations of the schedule and budget shall be done adequately so that there are no gaps and
variances in the actual and final values. There shall also be allocation of the resources as per
their skill sets to achieve the maximum success rate. The quality of the process shall be
managed by adhering to the quality standards, such as Total Quality Management and Six
Sigma.
The execution process will involve the actual migration of the email instances to the AWS
cloud. The process may bring in the presence of security loopholes as the data may be leaked
in between. There may also be increased access points that may lead to the presence of
increase vulnerabilities. These may be utilized by the malicious entities to give shape to the
security attacks and threats, such as data breaches, data leakages, eavesdropping attacks,
malware attacks and others. The occurrence of any of such security issues may lead to the
compromise of the information properties, such as confidentiality, availability, and integrity.
There must be security tools and norms that shall be considered in this process. These shall
include the use of encryption of the data sets while migrating from the existing to the new
platforms. There shall also be logs maintained along with the use of virtual private network
that must be done.
The control and closure phases will involve the risks associated with the changes that the
migration process will bring in for the resources and for the organization. AWS Cloud will be
used in the organization for the first time and the resources may take time to get used to the
same. This may have an adverse implication on the productivity and efficiency levels of the
resources. There may also be operational issues that the resources may give shape to due to
the lack of expertise. Such issues and occurrences may be avoided with the organization of
trainings for the resources. They shall be provided with the information on the functionality
of AWS cloud and the primary areas of concerns associated with the same. The resources will
become comfortable with the new platform and will be able to utilize the same as per the
expectation. There shall also be assessment and reviews that must be frequently carried out
during the initial days to understand the performance of the platform and the usage of the
same by the resources without causing any major errors or loopholes.
20

Regional Gardens Ltd.
References
An, Y., Zaaba, Z., & Samsudin, N. (2016). Reviews on Security Issues and Challenges in
Cloud Computing. IOP Conference Series: Materials Science And Engineering, 160,
012106. doi: 10.1088/1757-899x/160/1/012106
Anderson, C., Baskerville, R., & Kaul, M. (2017). Information Security Control Theory:
Achieving a Sustainable Reconciliation Between Sharing and Protecting the Privacy
of Information. Journal Of Management Information Systems, 34(4), 1082-1112. doi:
10.1080/07421222.2017.1394063
Aws. (2018). Hybrid Cloud Architectures - Amazon Web Services (AWS). Retrieved from
https://aws.amazon.com/enterprise/hybrid/
Dhyani, B., & Barthwal, A. (2014). Big Data Analytics using Hadoop. International Journal
Of Computer Applications, 108(12), 1-5. doi: 10.5120/18960-0288
Fazlida, M., & Said, J. (2015). Information Security: Risk, Governance and Implementation
Setback. Procedia Economics And Finance, 28, 243-248. doi: 10.1016/s2212-
5671(15)01106-5
Jenkins, R. (2014). Hybrid Public Private Cloud Computing for the Media Industry. SMPTE
Motion Imaging Journal, 123(3), 56-59. doi: 10.5594/j18398xy
Mathkunti, N. (2014). Cloud Computing: Security Issues. International Journal Of Computer
And Communication Engineering, 3(4), 259-263. doi: 10.7763/ijcce.2014.v3.332
Otero, A. (2010). A Multi-Criteria Evaluation of Information Security Controls Using
Boolean Features. International Journal Of Network Security & Its Applications, 2(4),
1-11. doi: 10.5121/ijnsa.2010.2401
Pokorny, J. (2013). NoSQL databases: a step to database scalability in web environment.
International Journal Of Web Information Systems, 9(1), 69-82. doi:
10.1108/17440081311316398
Reavis, D. (2012). Information Evaporation: The Migration Of Information To Cloud
Computing Platforms. International Journal Of Management & Information Systems
(IJMIS), 16(4), 291. doi: 10.19030/ijmis.v16i4.7305
Vurukonda, N., & Rao, B. (2016). A Study on Data Storage Security Issues in Cloud
21
References
An, Y., Zaaba, Z., & Samsudin, N. (2016). Reviews on Security Issues and Challenges in
Cloud Computing. IOP Conference Series: Materials Science And Engineering, 160,
012106. doi: 10.1088/1757-899x/160/1/012106
Anderson, C., Baskerville, R., & Kaul, M. (2017). Information Security Control Theory:
Achieving a Sustainable Reconciliation Between Sharing and Protecting the Privacy
of Information. Journal Of Management Information Systems, 34(4), 1082-1112. doi:
10.1080/07421222.2017.1394063
Aws. (2018). Hybrid Cloud Architectures - Amazon Web Services (AWS). Retrieved from
https://aws.amazon.com/enterprise/hybrid/
Dhyani, B., & Barthwal, A. (2014). Big Data Analytics using Hadoop. International Journal
Of Computer Applications, 108(12), 1-5. doi: 10.5120/18960-0288
Fazlida, M., & Said, J. (2015). Information Security: Risk, Governance and Implementation
Setback. Procedia Economics And Finance, 28, 243-248. doi: 10.1016/s2212-
5671(15)01106-5
Jenkins, R. (2014). Hybrid Public Private Cloud Computing for the Media Industry. SMPTE
Motion Imaging Journal, 123(3), 56-59. doi: 10.5594/j18398xy
Mathkunti, N. (2014). Cloud Computing: Security Issues. International Journal Of Computer
And Communication Engineering, 3(4), 259-263. doi: 10.7763/ijcce.2014.v3.332
Otero, A. (2010). A Multi-Criteria Evaluation of Information Security Controls Using
Boolean Features. International Journal Of Network Security & Its Applications, 2(4),
1-11. doi: 10.5121/ijnsa.2010.2401
Pokorny, J. (2013). NoSQL databases: a step to database scalability in web environment.
International Journal Of Web Information Systems, 9(1), 69-82. doi:
10.1108/17440081311316398
Reavis, D. (2012). Information Evaporation: The Migration Of Information To Cloud
Computing Platforms. International Journal Of Management & Information Systems
(IJMIS), 16(4), 291. doi: 10.19030/ijmis.v16i4.7305
Vurukonda, N., & Rao, B. (2016). A Study on Data Storage Security Issues in Cloud
21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Regional Gardens Ltd.
Computing. Procedia Computer Science, 92, 128-135. doi:
10.1016/j.procs.2016.07.335
Xue, C., & Xin, F. (2016). Benefits and Challenges of the Adoption of Cloud Computing in
Business. International Journal On Cloud Computing: Services And Architecture,
6(6), 01-15. doi: 10.5121/ijccsa.2016.6601
Zhao, J., & Zhou, J. (2014). Strategies and Methods for Cloud Migration. International
Journal Of Automation And Computing, 11(2), 143-152. doi: 10.1007/s11633-014-
0776-7
22
Computing. Procedia Computer Science, 92, 128-135. doi:
10.1016/j.procs.2016.07.335
Xue, C., & Xin, F. (2016). Benefits and Challenges of the Adoption of Cloud Computing in
Business. International Journal On Cloud Computing: Services And Architecture,
6(6), 01-15. doi: 10.5121/ijccsa.2016.6601
Zhao, J., & Zhou, J. (2014). Strategies and Methods for Cloud Migration. International
Journal Of Automation And Computing, 11(2), 143-152. doi: 10.1007/s11633-014-
0776-7
22
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





