Cyber Security Threats, Solutions, and Recommendations Report
VerifiedAdded on 2020/02/24
|11
|1654
|258
Report
AI Summary
This report examines cyber security in the context of business organizations, highlighting the increasing threats posed by cyber-attacks, viruses, and malware. It analyzes the impact of data breaches and the importance of data protection. The report utilizes the 4 levels of thinking model to assess the factors affecting cyber security. It then discusses various initiatives and strategies for mitigating cyber security problems, including enhanced security protocols, data encryption, and compliance with data protection regulations. The report recommends the use of updated firewalls and anti-virus software, along with monitoring security needs and regular checkups. The conclusion emphasizes the importance of cyber security for business success and the need for proactive measures to combat evolving threats. This report is a contribution to Desklib, a platform providing AI-based study tools for students.

Running head: CYBER SECURITY
Cyber Security
Name of the Student
Name of the University
Author’s Note
Cyber Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER SECURITY
Executive Summary
This report deals with the cyber security in the business organization. The various threats and
problems in the cyber security has been mentioned in the report. The proper solution of the
problems has also been disc used in the report. The use of the 4 levels of thinking have helped in
analyzing the factors affecting the cyber security in the business organization.
CYBER SECURITY
Executive Summary
This report deals with the cyber security in the business organization. The various threats and
problems in the cyber security has been mentioned in the report. The proper solution of the
problems has also been disc used in the report. The use of the 4 levels of thinking have helped in
analyzing the factors affecting the cyber security in the business organization.

2
CYBER SECURITY
Table of Contents
Introduction......................................................................................................................................3
Cyber Security.................................................................................................................................3
4 levels of Thinking.........................................................................................................................6
Initiatives for mitigating problems..................................................................................................7
Recommendations............................................................................................................................9
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
CYBER SECURITY
Table of Contents
Introduction......................................................................................................................................3
Cyber Security.................................................................................................................................3
4 levels of Thinking.........................................................................................................................6
Initiatives for mitigating problems..................................................................................................7
Recommendations............................................................................................................................9
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
CYBER SECURITY
Introduction
The Information Technology have been growing rapidly in the modern market by
providing benefits to the business organization. The use of different technologies in the business
operation have provided growth in the revenue of the business organization.
This report deals with the risks and threats in the business organization after using the different
technologies over the internet.
This report outlines the different factors that are causing problems in the cyber world. There are
some initiatives taken to minimize the identified problems.
Cyber Security
The security of the data and information over the internet s termed as the cyber security.
It has become a serious issue for the business organization all over the world. There is an
increase in the number of cyber-attacks all over the world (Von Solms and Van Niekerk, 2013).
The installation of the anonymous software has been a big problem for the business organization.
The installation of the unwanted software has been stopped that has reduced the hardware crash
and other problems (Wang and Lu, 2013).
CYBER SECURITY
Introduction
The Information Technology have been growing rapidly in the modern market by
providing benefits to the business organization. The use of different technologies in the business
operation have provided growth in the revenue of the business organization.
This report deals with the risks and threats in the business organization after using the different
technologies over the internet.
This report outlines the different factors that are causing problems in the cyber world. There are
some initiatives taken to minimize the identified problems.
Cyber Security
The security of the data and information over the internet s termed as the cyber security.
It has become a serious issue for the business organization all over the world. There is an
increase in the number of cyber-attacks all over the world (Von Solms and Van Niekerk, 2013).
The installation of the anonymous software has been a big problem for the business organization.
The installation of the unwanted software has been stopped that has reduced the hardware crash
and other problems (Wang and Lu, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CYBER SECURITY
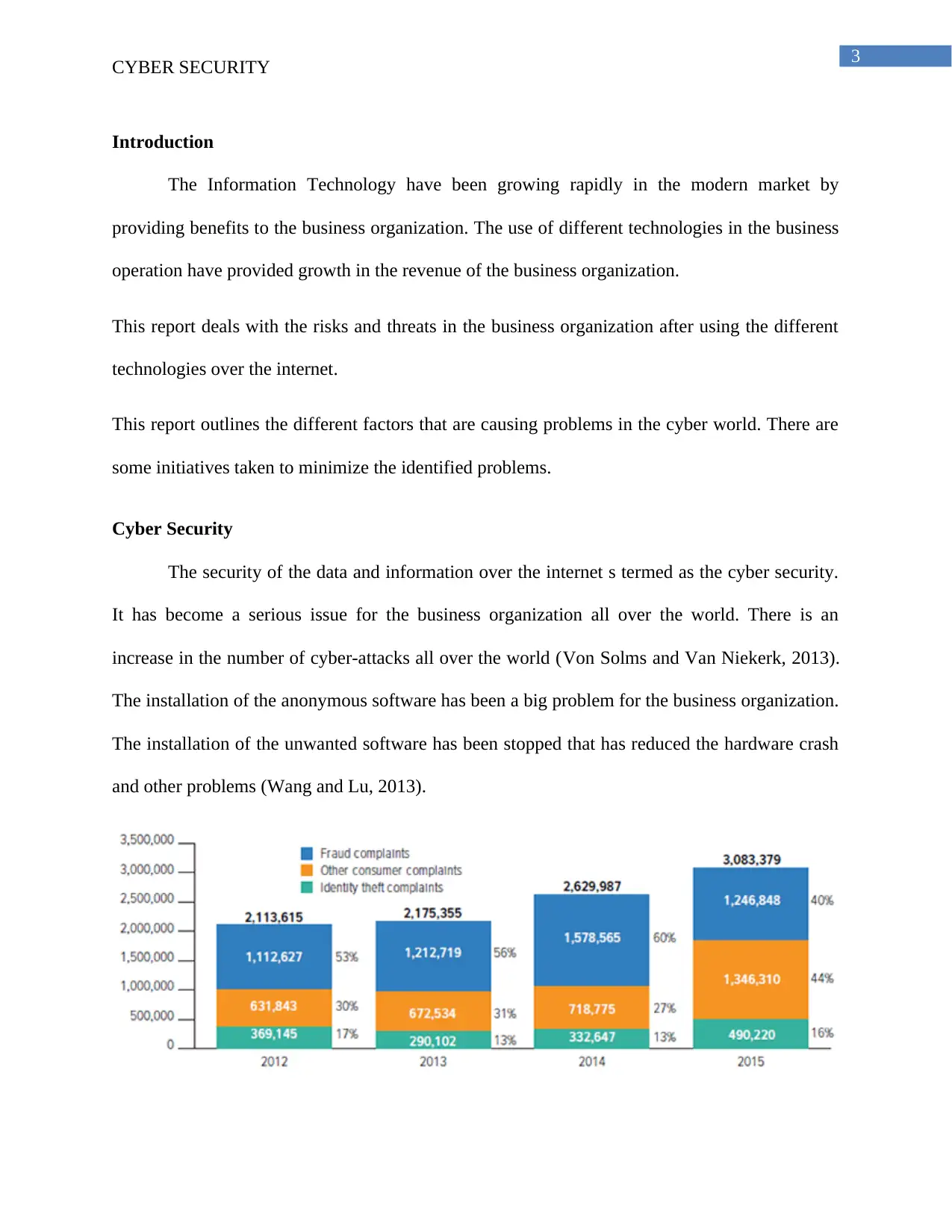
Figure 1: Cyber-attack vs data breach
(Source: Von Solms and Van Niekerk, 2013)
The above figure depicts about the comparison between the data breach and cyber-attack
all over the world. It can be analyzed that the ratio of cyber-attacks has been more than the data
breach in the companies. The major problem for the cyber security is the threat of viruses and
malwares. These viruses and malwares re responsible for the cyber-attacks in the server over the
internet (Hahn et al., 2013). The hackers used to hack the websites and online databases of the
company by sending phishing mails, viruses and malwares. These types of hackings are used by
the hackers to cause data loss of the data and asks for ransom against the data and information
(Amin et al., 2013).
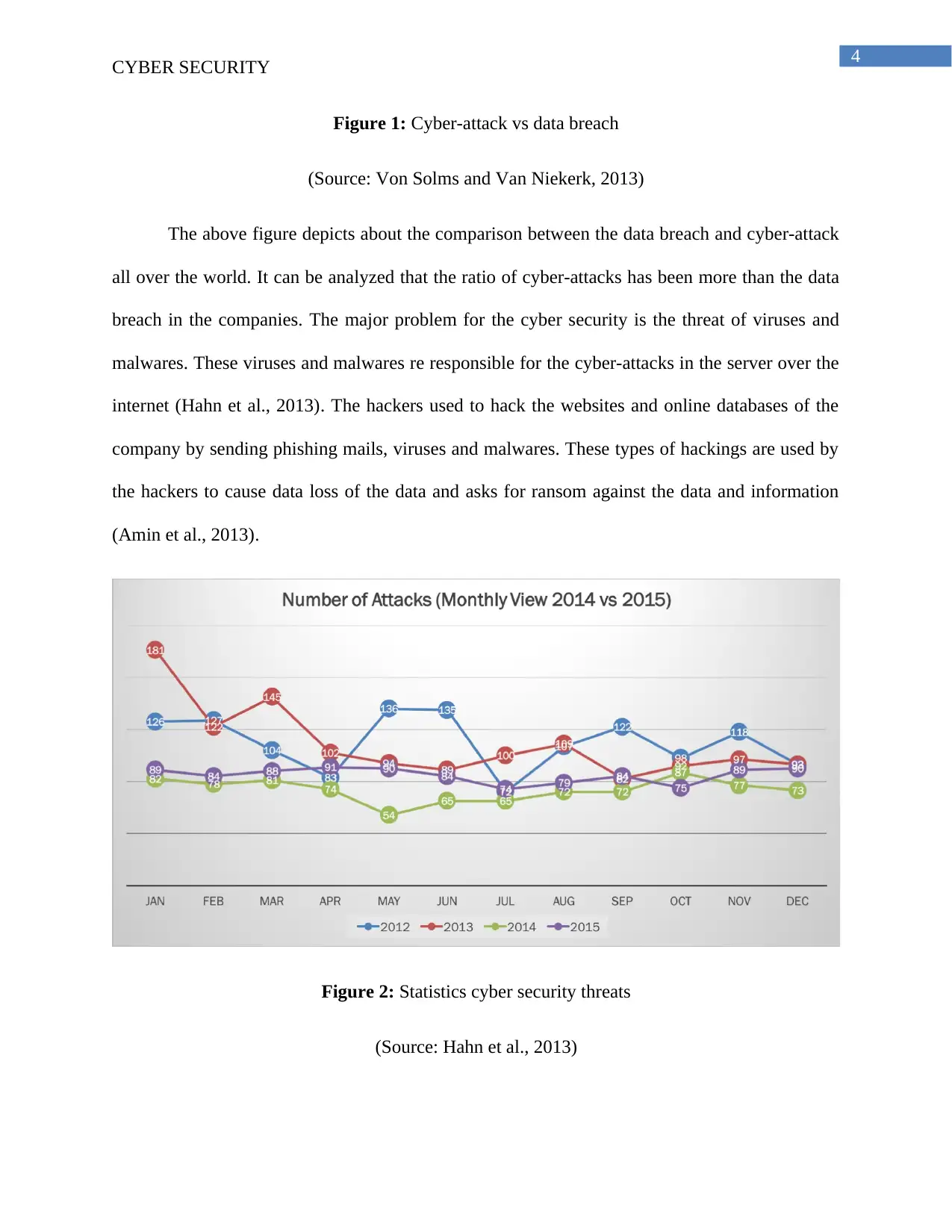
Figure 2: Statistics cyber security threats
(Source: Hahn et al., 2013)
CYBER SECURITY
Figure 1: Cyber-attack vs data breach
(Source: Von Solms and Van Niekerk, 2013)
The above figure depicts about the comparison between the data breach and cyber-attack
all over the world. It can be analyzed that the ratio of cyber-attacks has been more than the data
breach in the companies. The major problem for the cyber security is the threat of viruses and
malwares. These viruses and malwares re responsible for the cyber-attacks in the server over the
internet (Hahn et al., 2013). The hackers used to hack the websites and online databases of the
company by sending phishing mails, viruses and malwares. These types of hackings are used by
the hackers to cause data loss of the data and asks for ransom against the data and information
(Amin et al., 2013).
Figure 2: Statistics cyber security threats
(Source: Hahn et al., 2013)
5
CYBER SECURITY
The multi-disciplinary affairs of the business organization have led to the threats of
cybercrime and cyber-attacks in the business organization (Gordon et al., 2015). The cyber
security has been continuously evolving in the internet technology sector.
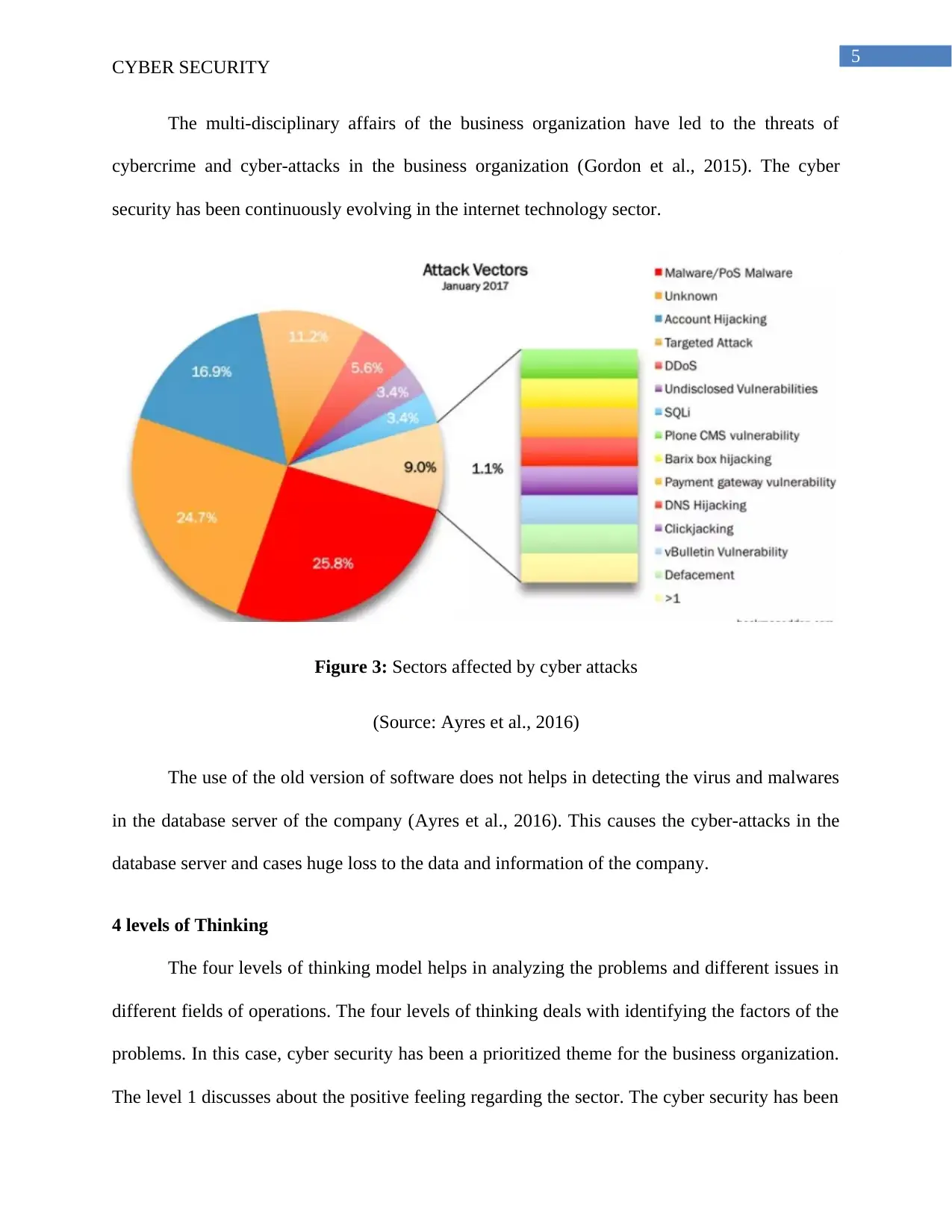
Figure 3: Sectors affected by cyber attacks
(Source: Ayres et al., 2016)
The use of the old version of software does not helps in detecting the virus and malwares
in the database server of the company (Ayres et al., 2016). This causes the cyber-attacks in the
database server and cases huge loss to the data and information of the company.
4 levels of Thinking
The four levels of thinking model helps in analyzing the problems and different issues in
different fields of operations. The four levels of thinking deals with identifying the factors of the
problems. In this case, cyber security has been a prioritized theme for the business organization.
The level 1 discusses about the positive feeling regarding the sector. The cyber security has been
CYBER SECURITY
The multi-disciplinary affairs of the business organization have led to the threats of
cybercrime and cyber-attacks in the business organization (Gordon et al., 2015). The cyber
security has been continuously evolving in the internet technology sector.
Figure 3: Sectors affected by cyber attacks
(Source: Ayres et al., 2016)
The use of the old version of software does not helps in detecting the virus and malwares
in the database server of the company (Ayres et al., 2016). This causes the cyber-attacks in the
database server and cases huge loss to the data and information of the company.
4 levels of Thinking
The four levels of thinking model helps in analyzing the problems and different issues in
different fields of operations. The four levels of thinking deals with identifying the factors of the
problems. In this case, cyber security has been a prioritized theme for the business organization.
The level 1 discusses about the positive feeling regarding the sector. The cyber security has been
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER SECURITY
an important sector for the business organization and has provided many benefits to the
organization.
Figure 4: 4 levels of thinking model
(Source: Herrera, Ron and Rabadão, 2017)
The level 2 of thinking deals with the negative feeling for related topics. The cyber-
attacks has been causing a huge loss in the data and information of the companies in the market
(Herrera, Ron and Rabadão, 2017). The level 3 deals with the positive thinking but not well for
the business organization. The use of old firewalls and anti-viruses is causing threat for the
company related to the cybercrime. The level 4 of thinking deals with the thinking that does not
feel good and not good for others. The use of the unsecure gateway has been a cause for the
cyber-attacks in the business origination.
Event
s
Patterns
Systematic structures
Mental Models
CYBER SECURITY
an important sector for the business organization and has provided many benefits to the
organization.
Figure 4: 4 levels of thinking model
(Source: Herrera, Ron and Rabadão, 2017)
The level 2 of thinking deals with the negative feeling for related topics. The cyber-
attacks has been causing a huge loss in the data and information of the companies in the market
(Herrera, Ron and Rabadão, 2017). The level 3 deals with the positive thinking but not well for
the business organization. The use of old firewalls and anti-viruses is causing threat for the
company related to the cybercrime. The level 4 of thinking deals with the thinking that does not
feel good and not good for others. The use of the unsecure gateway has been a cause for the
cyber-attacks in the business origination.
Event
s
Patterns
Systematic structures
Mental Models
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CYBER SECURITY
Initiatives for mitigating problems
There are various strategies and initiatives are made to mitigate the cyber security
problems in the organization.
Security Strategy
The security methods of the company have to be enhanced to restrict the viruses and
malwares in the server of the company. The critical resources of the company have to be
maintained by the security strategies of the company in the market. The security protocols of the
companies have to be upgraded. The strategies of the company in order to provide security to the
data and information includes the encryption technique the data transfer in the company is done
with the help of data encryption method that helps in securing the data packets from hacking
(Buczak and Guven, 2016). The encryption o data is done with the help of a pattern and a key
that is only known by the receiver and sender.
Data Protection and privacy
The data and information of the company have to be secured or the success of the
company in the market. The Data Protection Act 1998 has been properly implemented in the
companies. This act helps in securing the personal information of the employees and other staffs
of the organization (Inan et al., 2016). No personal data and information is shared with anyone
without the permission. Therefore, this has helped in maintaining the security of the data and
information.
Inadequate software
The installation of the anonymous software has been a big problem for the business
organization. The installation of the unwanted software has been stopped that has reduced the
CYBER SECURITY
Initiatives for mitigating problems
There are various strategies and initiatives are made to mitigate the cyber security
problems in the organization.
Security Strategy
The security methods of the company have to be enhanced to restrict the viruses and
malwares in the server of the company. The critical resources of the company have to be
maintained by the security strategies of the company in the market. The security protocols of the
companies have to be upgraded. The strategies of the company in order to provide security to the
data and information includes the encryption technique the data transfer in the company is done
with the help of data encryption method that helps in securing the data packets from hacking
(Buczak and Guven, 2016). The encryption o data is done with the help of a pattern and a key
that is only known by the receiver and sender.
Data Protection and privacy
The data and information of the company have to be secured or the success of the
company in the market. The Data Protection Act 1998 has been properly implemented in the
companies. This act helps in securing the personal information of the employees and other staffs
of the organization (Inan et al., 2016). No personal data and information is shared with anyone
without the permission. Therefore, this has helped in maintaining the security of the data and
information.
Inadequate software
The installation of the anonymous software has been a big problem for the business
organization. The installation of the unwanted software has been stopped that has reduced the

8
CYBER SECURITY
hardware crash and other problems (Von Solms and Van Niekerk, 2013). Only the licensed
software is installed in the server of the companies.
Recommendations
The IT solutions to the cyber-attacks in the world have become ab important agenda for
the business organization in the market. The companies needs to use updated firewalls and anti-
virus software that helps in restricting the dangerous viruses and malwares from entering into the
database server of the company. The unauthorized users are not allowed to use the portal of the
company. There is prior need of monitoring the security needs of the company. A regular
checkup of the security solutions are done for analyzing the security levels of the company in the
market.
Conclusion
It can be concluded that the cyber security has been an important part or the business
organization in the market. The cyber-attacks has been the main problems to the cyber security.
Various viruses and malwares are used for the attacks in the server of the company for causing
data breach of the company. The use of the updated firewalls and anti-viruses software help in
maintaining the security of the server from the cyber-attacks over the internet.
CYBER SECURITY
hardware crash and other problems (Von Solms and Van Niekerk, 2013). Only the licensed
software is installed in the server of the companies.
Recommendations
The IT solutions to the cyber-attacks in the world have become ab important agenda for
the business organization in the market. The companies needs to use updated firewalls and anti-
virus software that helps in restricting the dangerous viruses and malwares from entering into the
database server of the company. The unauthorized users are not allowed to use the portal of the
company. There is prior need of monitoring the security needs of the company. A regular
checkup of the security solutions are done for analyzing the security levels of the company in the
market.
Conclusion
It can be concluded that the cyber security has been an important part or the business
organization in the market. The cyber-attacks has been the main problems to the cyber security.
Various viruses and malwares are used for the attacks in the server of the company for causing
data breach of the company. The use of the updated firewalls and anti-viruses software help in
maintaining the security of the server from the cyber-attacks over the internet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CYBER SECURITY
References
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE Transactions
on Control Systems Technology, 21(5), pp.1963-1970.
Ayres, N., Maglaras, L., Janicke, H., Smith, R. and He, Y., 2016. The mimetic virus: A vector
for cyber security.
Buczak, A.L. and Guven, E., 2016. A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-
1176.
Gordon, L.A., Loeb, M.P., Lucyshyn, W. and Zhou, L., 2015. Externalities and the magnitude of
cyber security underinvestment by private sector firms: a modification of the Gordon-Loeb
model. Journal of Information Security, 6(1), p.24.
Hahn, A., Ashok, A., Sridhar, S. and Govindarasu, M., 2013. Cyber-physical security testbeds:
Architecture, application, and evaluation for smart grid. IEEE Transactions on Smart Grid, 4(2),
pp.847-855.
Herrera, A.V., Ron, M. and Rabadão, C., 2017, June. National cyber-security policies oriented to
BYOD (bring your own device): Systematic review. In Information Systems and Technologies
(CISTI), 2017 12th Iberian Conference on (pp. 1-4). IEEE.
Inan, F.A., Namin, A.S., Pogrund, R.L. and Jones, K.S., 2016. Internet use and cybersecurity
concerns of individuals with visual impairments. Journal of Educational Technology &
Society, 19(1), p.28.
CYBER SECURITY
References
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE Transactions
on Control Systems Technology, 21(5), pp.1963-1970.
Ayres, N., Maglaras, L., Janicke, H., Smith, R. and He, Y., 2016. The mimetic virus: A vector
for cyber security.
Buczak, A.L. and Guven, E., 2016. A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-
1176.
Gordon, L.A., Loeb, M.P., Lucyshyn, W. and Zhou, L., 2015. Externalities and the magnitude of
cyber security underinvestment by private sector firms: a modification of the Gordon-Loeb
model. Journal of Information Security, 6(1), p.24.
Hahn, A., Ashok, A., Sridhar, S. and Govindarasu, M., 2013. Cyber-physical security testbeds:
Architecture, application, and evaluation for smart grid. IEEE Transactions on Smart Grid, 4(2),
pp.847-855.
Herrera, A.V., Ron, M. and Rabadão, C., 2017, June. National cyber-security policies oriented to
BYOD (bring your own device): Systematic review. In Information Systems and Technologies
(CISTI), 2017 12th Iberian Conference on (pp. 1-4). IEEE.
Inan, F.A., Namin, A.S., Pogrund, R.L. and Jones, K.S., 2016. Internet use and cybersecurity
concerns of individuals with visual impairments. Journal of Educational Technology &
Society, 19(1), p.28.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CYBER SECURITY
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
Wang, W. and Lu, Z., 2013. Cyber security in the Smart Grid: Survey and challenges. Computer
Networks, 57(5), pp.1344-1371.
CYBER SECURITY
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
Wang, W. and Lu, Z., 2013. Cyber security in the Smart Grid: Survey and challenges. Computer
Networks, 57(5), pp.1344-1371.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





