Automatic Network Configuration Using Dynamic Host Configuration Protocol (DHCP)
VerifiedAdded on 2019/11/26
|22
|5978
|247
Report
AI Summary
The installation of a web server is described as a process that involves analyzing configuration preferences and validating the installation by clicking the 'Install' button. The Dynamic Host Configuration Protocol (DHCP) is also discussed, which is used to automatically assign IP addresses and other network settings to devices on a network. This protocol provides benefits such as automatic resource allocation, reusing of IP addresses, and reconfiguring without modifying each user device. Additionally, the article highlights the importance of embracing cloud computing in order to reduce data center footprint and improve business agility.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head; IT INFRASTTRUCTURE 1
IT Infrastructure
Name
Affiliate Institution
IT Infrastructure
Name
Affiliate Institution
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Running Head; IT INFRASTTRUCTURE 2
Table of Contents
Introduction.................................................................................................................................................3
IT Infrastructure Components......................................................................................................................3
Hierarchical Model......................................................................................................................................4
Current and Future Itech IT Infrastructure Requirements............................................................................7
Geographical Scope of the Network............................................................................................................8
Scalability of iTech Network.......................................................................................................................9
Dedicated Server.........................................................................................................................................9
Logical Network Design............................................................................................................................10
Cloud based design....................................................................................................................................12
Access Layer Diagram..............................................................................................................................12
Configuring DHCP....................................................................................................................................13
Configuring a DNS Server........................................................................................................................14
Configuring a Web Server.........................................................................................................................15
How Clients Obtain Network Configuration Automatically......................................................................19
Conclusion.................................................................................................................................................20
Recommendation.......................................................................................................................................20
References.................................................................................................................................................21
Table of Contents
Introduction.................................................................................................................................................3
IT Infrastructure Components......................................................................................................................3
Hierarchical Model......................................................................................................................................4
Current and Future Itech IT Infrastructure Requirements............................................................................7
Geographical Scope of the Network............................................................................................................8
Scalability of iTech Network.......................................................................................................................9
Dedicated Server.........................................................................................................................................9
Logical Network Design............................................................................................................................10
Cloud based design....................................................................................................................................12
Access Layer Diagram..............................................................................................................................12
Configuring DHCP....................................................................................................................................13
Configuring a DNS Server........................................................................................................................14
Configuring a Web Server.........................................................................................................................15
How Clients Obtain Network Configuration Automatically......................................................................19
Conclusion.................................................................................................................................................20
Recommendation.......................................................................................................................................20
References.................................................................................................................................................21

Running Head; IT INFRASTTRUCTURE 3
Introduction
The objectives of this report is to develop a logical design for the data center building for iTech
company. It should include a set of required servers, network devices and their connections. This
report will also focus on IT infrastructure components, the several types of dedicated servers,
cloud computing and network simulation. The current network setup in iTech is poorly design
and wants it replaced completely by considering either dedicated server techniques and cloud
hosting.
IT Infrastructure Components
Switches
A network switch is an equipment that offers connectivity between a Local Area Network and
network devices. A switch has several ports that connect directly to other network apparatus, for
example servers, routers and other switches. Switches enable two devices on the network to
communicate with each other without broadcasting traffic to other devices on the network. Furht,
& Escalante, (2010).
Routers
Routers enhance movement of packets across networks. Routing allows devices on different
network segments to talk to each other by resolving the route that will enable the network packet
to reach its destination. In most cases the default gateway value on a workstation connected to a
network is normally the IP address of the router.
Firewalls
Firewalls are the first level security of any network. It can be regarded as the gatekeeper. A set of
guidelines determines the kind of network traffic to be blocked or passed through the firewall.
Rules can be developed in the simplest way of a firewall to allow unique port from a group of
devices to another cluster of devices. For instance: two firewall rules from hosting a web server
with limited web traffic, would typically look like this:
Source Destination Protocol Description
Any 10.0.1.80 90 / http Web traffic accepted
Any 10.0.1.80 334/ https Secure web traffic accepted
Originating device in this case is the source. Any means that computers can talk to each other.
Destination on the other hand represents internal web server IP address. Protocol describes the
type of traffic permitted from the source to the destination. Reese, (2009).
Servers
Introduction
The objectives of this report is to develop a logical design for the data center building for iTech
company. It should include a set of required servers, network devices and their connections. This
report will also focus on IT infrastructure components, the several types of dedicated servers,
cloud computing and network simulation. The current network setup in iTech is poorly design
and wants it replaced completely by considering either dedicated server techniques and cloud
hosting.
IT Infrastructure Components
Switches
A network switch is an equipment that offers connectivity between a Local Area Network and
network devices. A switch has several ports that connect directly to other network apparatus, for
example servers, routers and other switches. Switches enable two devices on the network to
communicate with each other without broadcasting traffic to other devices on the network. Furht,
& Escalante, (2010).
Routers
Routers enhance movement of packets across networks. Routing allows devices on different
network segments to talk to each other by resolving the route that will enable the network packet
to reach its destination. In most cases the default gateway value on a workstation connected to a
network is normally the IP address of the router.
Firewalls
Firewalls are the first level security of any network. It can be regarded as the gatekeeper. A set of
guidelines determines the kind of network traffic to be blocked or passed through the firewall.
Rules can be developed in the simplest way of a firewall to allow unique port from a group of
devices to another cluster of devices. For instance: two firewall rules from hosting a web server
with limited web traffic, would typically look like this:
Source Destination Protocol Description
Any 10.0.1.80 90 / http Web traffic accepted
Any 10.0.1.80 334/ https Secure web traffic accepted
Originating device in this case is the source. Any means that computers can talk to each other.
Destination on the other hand represents internal web server IP address. Protocol describes the
type of traffic permitted from the source to the destination. Reese, (2009).
Servers

Running Head; IT INFRASTTRUCTURE 4
A network server is a super computer that has more resources in terms of capacity, speed among
others. A server allows several users to share and access its resources simultaneously. There are
various types of servers including the file server which provides a common location for storing
files for it end users. They can also be configured to limit access of specific files by users.
Directory server is another type of server which provides centralized database of accounts for
users. Therefore, it facilitates easy management of client credentials used to explore server
resources. Web server is the most common form of server that uses Hyper Text Transfer Protocol
(HTTP) that enables user to access files through a web browser. Others include print servers,
application servers and database servers. Abdoulaye, (2014).
Physical plant
This is the actual layout of network devices in the server rooms, data center and office spaces.
This infrastructure is often ignored yet very crucial and failure to manage it properly can cause
system downfall. For example, if cables are not laid out well on the floor or along the walls,
users can accidentally pull the off thus cutting short resource access. The two main cabling
infrastructure are fiber and CAT 5/6/7.
People
Although people are not regarded as part of the network infrastructure capabilities of a company
can be limited if there are inadequate qualified and competent individuals to run and maintain the
infrastructure. In larger firms, there are reserved positions for every sector of the network
infrastructure. However, for smaller companies, the system administrator can manage these
duties.
Server rooms / Data center
In large companies, the server room is considered to be the backbone of the network setup. This
is where all the servers are installed and acts as the central core of several networks.
Infrastructure Software
Server operating system is considered the grayest component. If there were no multi-user
operating systems, then infrastructure functions could not have been achieved.
Hierarchical Model
Introduction
A hierarchical network model entails splitting a network into separate exceptional and unique
tiers. In the hierarchy, every tier or layer, provides discrete functionalities that describes its
responsibilities and roles in the network. This will aid the network architect and designer in
selection and optimization of the correct network software and hardware features to execute
distinct functions for that particular network tier. Hierarchical design is applicable to wide area
network and local area network models. Heisterberg & Verma, (2014).
Subdivision of flat network into smaller segments have several advantages one of which is to
ensure that internal traffic continue being local. Traffic that is intended for other different
A network server is a super computer that has more resources in terms of capacity, speed among
others. A server allows several users to share and access its resources simultaneously. There are
various types of servers including the file server which provides a common location for storing
files for it end users. They can also be configured to limit access of specific files by users.
Directory server is another type of server which provides centralized database of accounts for
users. Therefore, it facilitates easy management of client credentials used to explore server
resources. Web server is the most common form of server that uses Hyper Text Transfer Protocol
(HTTP) that enables user to access files through a web browser. Others include print servers,
application servers and database servers. Abdoulaye, (2014).
Physical plant
This is the actual layout of network devices in the server rooms, data center and office spaces.
This infrastructure is often ignored yet very crucial and failure to manage it properly can cause
system downfall. For example, if cables are not laid out well on the floor or along the walls,
users can accidentally pull the off thus cutting short resource access. The two main cabling
infrastructure are fiber and CAT 5/6/7.
People
Although people are not regarded as part of the network infrastructure capabilities of a company
can be limited if there are inadequate qualified and competent individuals to run and maintain the
infrastructure. In larger firms, there are reserved positions for every sector of the network
infrastructure. However, for smaller companies, the system administrator can manage these
duties.
Server rooms / Data center
In large companies, the server room is considered to be the backbone of the network setup. This
is where all the servers are installed and acts as the central core of several networks.
Infrastructure Software
Server operating system is considered the grayest component. If there were no multi-user
operating systems, then infrastructure functions could not have been achieved.
Hierarchical Model
Introduction
A hierarchical network model entails splitting a network into separate exceptional and unique
tiers. In the hierarchy, every tier or layer, provides discrete functionalities that describes its
responsibilities and roles in the network. This will aid the network architect and designer in
selection and optimization of the correct network software and hardware features to execute
distinct functions for that particular network tier. Hierarchical design is applicable to wide area
network and local area network models. Heisterberg & Verma, (2014).
Subdivision of flat network into smaller segments have several advantages one of which is to
ensure that internal traffic continue being local. Traffic that is intended for other different
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
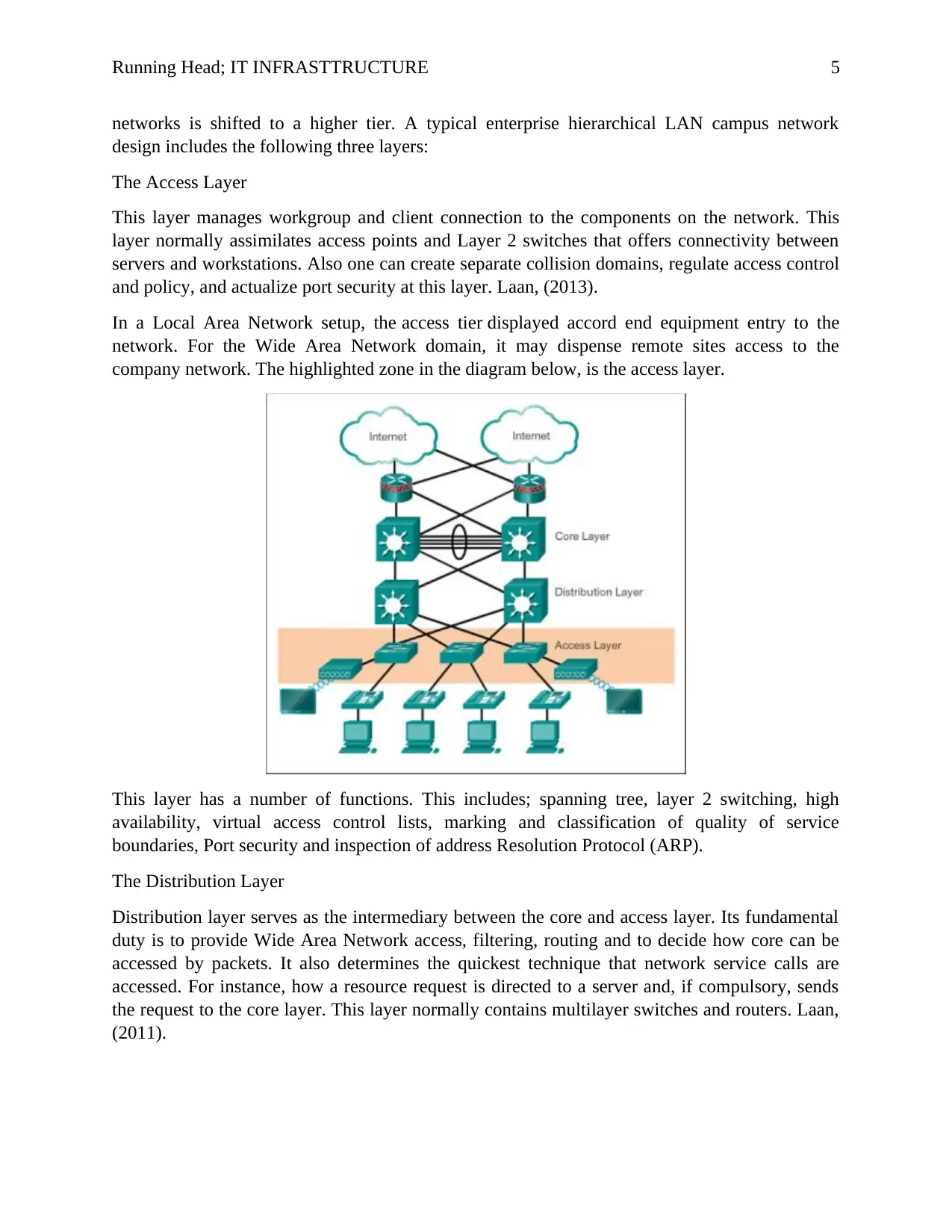
Running Head; IT INFRASTTRUCTURE 5
networks is shifted to a higher tier. A typical enterprise hierarchical LAN campus network
design includes the following three layers:
The Access Layer
This layer manages workgroup and client connection to the components on the network. This
layer normally assimilates access points and Layer 2 switches that offers connectivity between
servers and workstations. Also one can create separate collision domains, regulate access control
and policy, and actualize port security at this layer. Laan, (2013).
In a Local Area Network setup, the access tier displayed accord end equipment entry to the
network. For the Wide Area Network domain, it may dispense remote sites access to the
company network. The highlighted zone in the diagram below, is the access layer.
This layer has a number of functions. This includes; spanning tree, layer 2 switching, high
availability, virtual access control lists, marking and classification of quality of service
boundaries, Port security and inspection of address Resolution Protocol (ARP).
The Distribution Layer
Distribution layer serves as the intermediary between the core and access layer. Its fundamental
duty is to provide Wide Area Network access, filtering, routing and to decide how core can be
accessed by packets. It also determines the quickest technique that network service calls are
accessed. For instance, how a resource request is directed to a server and, if compulsory, sends
the request to the core layer. This layer normally contains multilayer switches and routers. Laan,
(2011).
networks is shifted to a higher tier. A typical enterprise hierarchical LAN campus network
design includes the following three layers:
The Access Layer
This layer manages workgroup and client connection to the components on the network. This
layer normally assimilates access points and Layer 2 switches that offers connectivity between
servers and workstations. Also one can create separate collision domains, regulate access control
and policy, and actualize port security at this layer. Laan, (2013).
In a Local Area Network setup, the access tier displayed accord end equipment entry to the
network. For the Wide Area Network domain, it may dispense remote sites access to the
company network. The highlighted zone in the diagram below, is the access layer.
This layer has a number of functions. This includes; spanning tree, layer 2 switching, high
availability, virtual access control lists, marking and classification of quality of service
boundaries, Port security and inspection of address Resolution Protocol (ARP).
The Distribution Layer
Distribution layer serves as the intermediary between the core and access layer. Its fundamental
duty is to provide Wide Area Network access, filtering, routing and to decide how core can be
accessed by packets. It also determines the quickest technique that network service calls are
accessed. For instance, how a resource request is directed to a server and, if compulsory, sends
the request to the core layer. This layer normally contains multilayer switches and routers. Laan,
(2011).
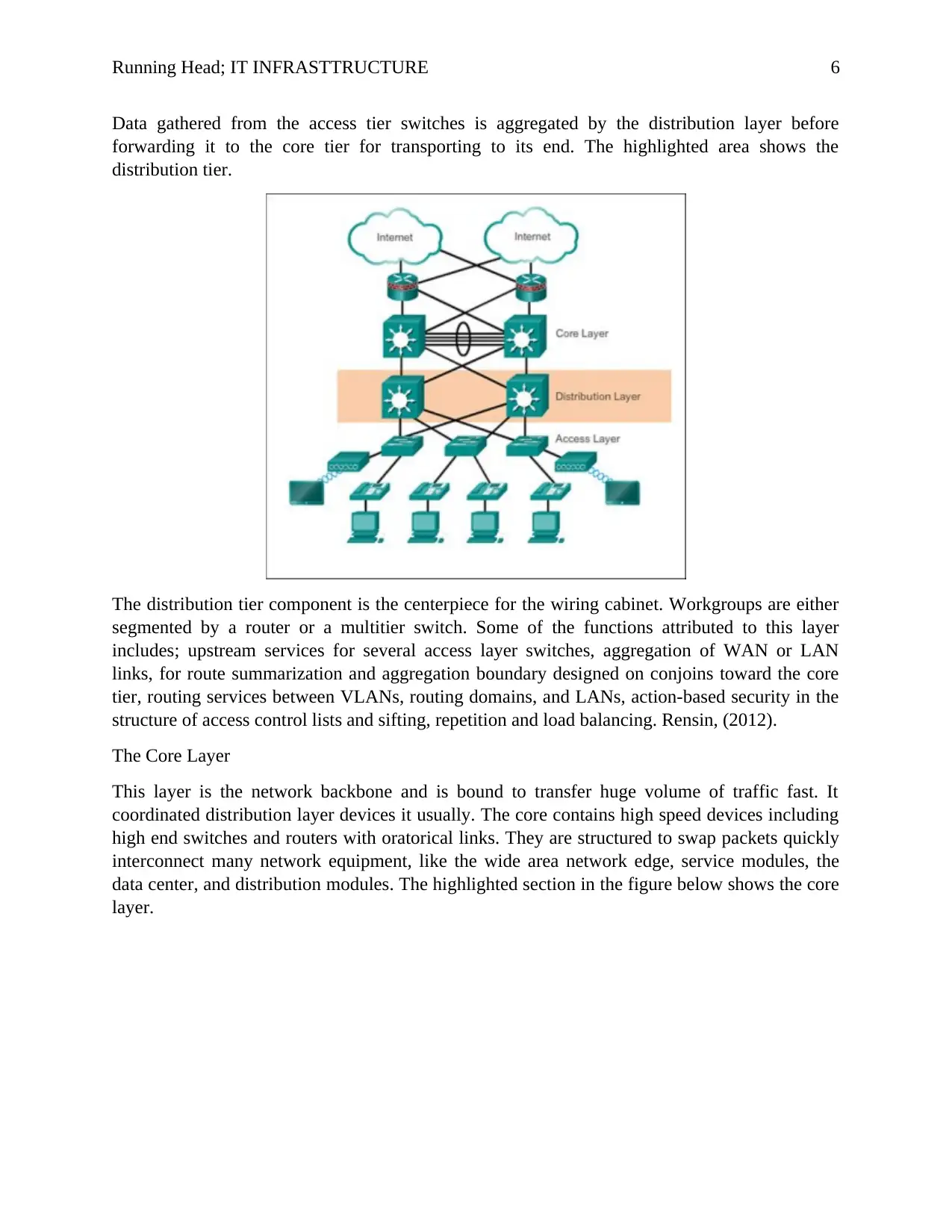
Running Head; IT INFRASTTRUCTURE 6
Data gathered from the access tier switches is aggregated by the distribution layer before
forwarding it to the core tier for transporting to its end. The highlighted area shows the
distribution tier.
The distribution tier component is the centerpiece for the wiring cabinet. Workgroups are either
segmented by a router or a multitier switch. Some of the functions attributed to this layer
includes; upstream services for several access layer switches, aggregation of WAN or LAN
links, for route summarization and aggregation boundary designed on conjoins toward the core
tier, routing services between VLANs, routing domains, and LANs, action-based security in the
structure of access control lists and sifting, repetition and load balancing. Rensin, (2012).
The Core Layer
This layer is the network backbone and is bound to transfer huge volume of traffic fast. It
coordinated distribution layer devices it usually. The core contains high speed devices including
high end switches and routers with oratorical links. They are structured to swap packets quickly
interconnect many network equipment, like the wide area network edge, service modules, the
data center, and distribution modules. The highlighted section in the figure below shows the core
layer.
Data gathered from the access tier switches is aggregated by the distribution layer before
forwarding it to the core tier for transporting to its end. The highlighted area shows the
distribution tier.
The distribution tier component is the centerpiece for the wiring cabinet. Workgroups are either
segmented by a router or a multitier switch. Some of the functions attributed to this layer
includes; upstream services for several access layer switches, aggregation of WAN or LAN
links, for route summarization and aggregation boundary designed on conjoins toward the core
tier, routing services between VLANs, routing domains, and LANs, action-based security in the
structure of access control lists and sifting, repetition and load balancing. Rensin, (2012).
The Core Layer
This layer is the network backbone and is bound to transfer huge volume of traffic fast. It
coordinated distribution layer devices it usually. The core contains high speed devices including
high end switches and routers with oratorical links. They are structured to swap packets quickly
interconnect many network equipment, like the wide area network edge, service modules, the
data center, and distribution modules. The highlighted section in the figure below shows the core
layer.
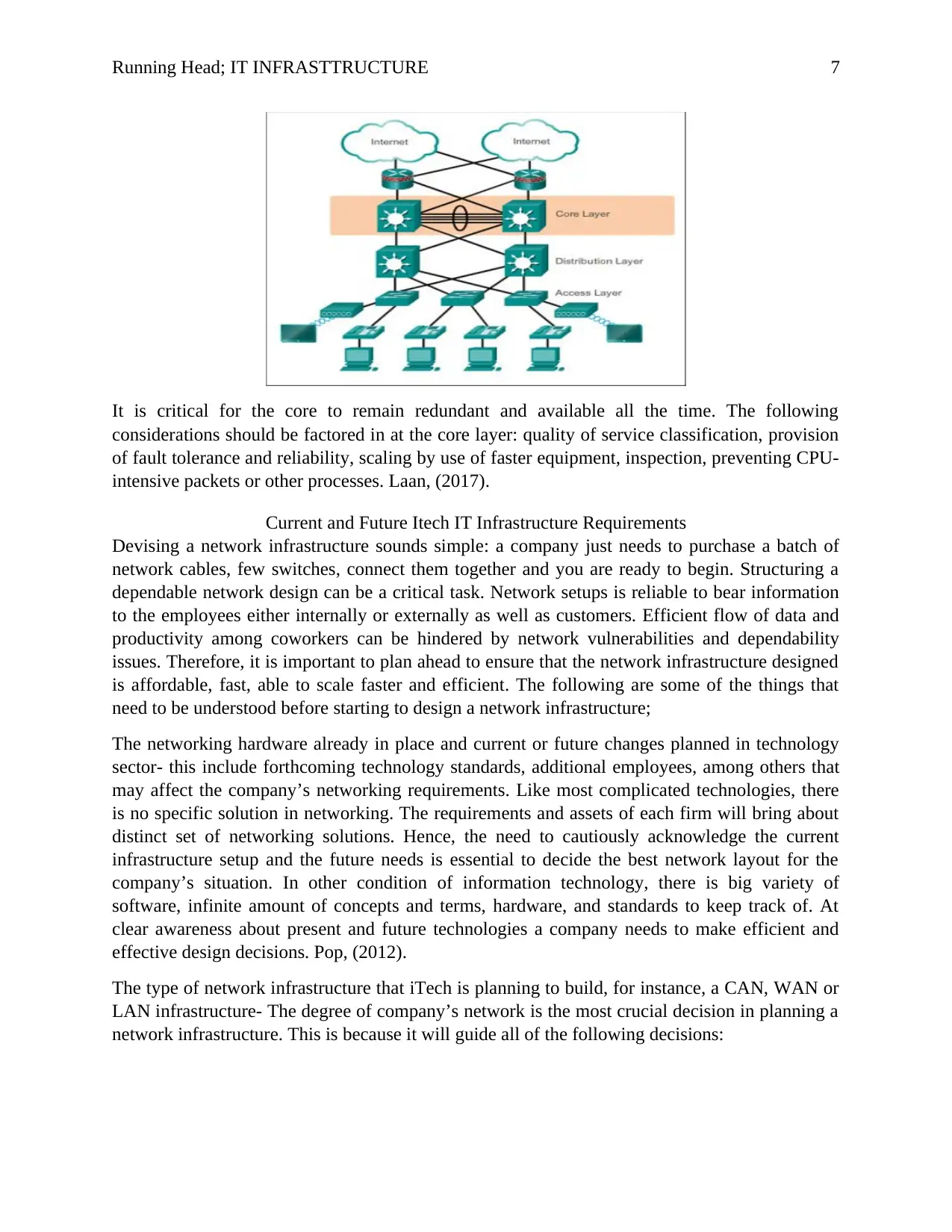
Running Head; IT INFRASTTRUCTURE 7
It is critical for the core to remain redundant and available all the time. The following
considerations should be factored in at the core layer: quality of service classification, provision
of fault tolerance and reliability, scaling by use of faster equipment, inspection, preventing CPU-
intensive packets or other processes. Laan, (2017).
Current and Future Itech IT Infrastructure Requirements
Devising a network infrastructure sounds simple: a company just needs to purchase a batch of
network cables, few switches, connect them together and you are ready to begin. Structuring a
dependable network design can be a critical task. Network setups is reliable to bear information
to the employees either internally or externally as well as customers. Efficient flow of data and
productivity among coworkers can be hindered by network vulnerabilities and dependability
issues. Therefore, it is important to plan ahead to ensure that the network infrastructure designed
is affordable, fast, able to scale faster and efficient. The following are some of the things that
need to be understood before starting to design a network infrastructure;
The networking hardware already in place and current or future changes planned in technology
sector- this include forthcoming technology standards, additional employees, among others that
may affect the company’s networking requirements. Like most complicated technologies, there
is no specific solution in networking. The requirements and assets of each firm will bring about
distinct set of networking solutions. Hence, the need to cautiously acknowledge the current
infrastructure setup and the future needs is essential to decide the best network layout for the
company’s situation. In other condition of information technology, there is big variety of
software, infinite amount of concepts and terms, hardware, and standards to keep track of. At
clear awareness about present and future technologies a company needs to make efficient and
effective design decisions. Pop, (2012).
The type of network infrastructure that iTech is planning to build, for instance, a CAN, WAN or
LAN infrastructure- The degree of company’s network is the most crucial decision in planning a
network infrastructure. This is because it will guide all of the following decisions:
It is critical for the core to remain redundant and available all the time. The following
considerations should be factored in at the core layer: quality of service classification, provision
of fault tolerance and reliability, scaling by use of faster equipment, inspection, preventing CPU-
intensive packets or other processes. Laan, (2017).
Current and Future Itech IT Infrastructure Requirements
Devising a network infrastructure sounds simple: a company just needs to purchase a batch of
network cables, few switches, connect them together and you are ready to begin. Structuring a
dependable network design can be a critical task. Network setups is reliable to bear information
to the employees either internally or externally as well as customers. Efficient flow of data and
productivity among coworkers can be hindered by network vulnerabilities and dependability
issues. Therefore, it is important to plan ahead to ensure that the network infrastructure designed
is affordable, fast, able to scale faster and efficient. The following are some of the things that
need to be understood before starting to design a network infrastructure;
The networking hardware already in place and current or future changes planned in technology
sector- this include forthcoming technology standards, additional employees, among others that
may affect the company’s networking requirements. Like most complicated technologies, there
is no specific solution in networking. The requirements and assets of each firm will bring about
distinct set of networking solutions. Hence, the need to cautiously acknowledge the current
infrastructure setup and the future needs is essential to decide the best network layout for the
company’s situation. In other condition of information technology, there is big variety of
software, infinite amount of concepts and terms, hardware, and standards to keep track of. At
clear awareness about present and future technologies a company needs to make efficient and
effective design decisions. Pop, (2012).
The type of network infrastructure that iTech is planning to build, for instance, a CAN, WAN or
LAN infrastructure- The degree of company’s network is the most crucial decision in planning a
network infrastructure. This is because it will guide all of the following decisions:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running Head; IT INFRASTTRUCTURE 8
LAN- a local area network is normally developed in a single building or office. In most
scenarios, it links the local office information technology, that is worker’s computers with the
internet as well as within the organization.
WAN- a wide area network links a single building or office to a larger network, as its parent
company’s network. WANs connection are maintained usually by telecommunication or ISPs
organizations and differ in terms of cost and bandwidth.
CAN- a campus area network links several LANs around the same organization are close to each
other. CANs connections are also maintained by ISPs or telecommunication organization.
The network applications iTech clients depend on the most, and the volume of the bandwidth
needed- iTech company should consider the following; provision of access to print servers and
file, reliability of local resources or the need of provision of links to remote logins, virtual LANs
usage or restriction of certain network access, the need of users to access application or database
servers and as such, are they frequently moving huge volume of data across the entire network.
Lammle & Tedder (2014).
The number of employees and networked devices iTech have and if this number will change in
future- depending its business, extra resources may be required to expand the network in future.
Plan should be made for the future not now.
Constraints imposed by the office setup on iTech planning and the availability of enough space
on the ceilings or floors to run network cables- the company should ensure that there is no
challenge that the office layout pose to the network infrastructure. If possible, documented and
dedicated conduits should be run entirely for the network infrastructure.
Physical software and hardware components required to develop the network infrastructure that
iTech is planning. The company should consider the location, connection, installation and
configuration of hardware components.
If iTech is to structure and build a new network infrastructure, it should consider standard that
will meet todays and future needs of the company. In addition, labor is very costly factor in the
project, so devoting in reliable cabling without utilizing its entire abilities currently might appear
more expensive now, but will be less costly than withdrawing to low-end cabling that might be
needed to reestablish 5 years later. The company should also ensure that network cabling is not
run parallel with the electrical installation. Shielded and Unshielded cabling interaction can be
disorganized by the magnetic field developed by electric cables, therefore causing bandwidth
lower considerably. Also, network cabling should be kept away from devices such as fans, a/c
units, fluorescent lighting among others. Another thing to acknowledge is cable management
usage. Addition of a network rack and arrangement of a good shelf-based cable management will
increase the cost of the project but ease maintenance process. Cable specification and length
should be verified. Also, network infrastructure should be tested using suitable tool after
configuration to ensure it suits it intended objective. Itech should set aside budget for installation
and maintenance of the new network infrastructure. Pradeep, (2016).
LAN- a local area network is normally developed in a single building or office. In most
scenarios, it links the local office information technology, that is worker’s computers with the
internet as well as within the organization.
WAN- a wide area network links a single building or office to a larger network, as its parent
company’s network. WANs connection are maintained usually by telecommunication or ISPs
organizations and differ in terms of cost and bandwidth.
CAN- a campus area network links several LANs around the same organization are close to each
other. CANs connections are also maintained by ISPs or telecommunication organization.
The network applications iTech clients depend on the most, and the volume of the bandwidth
needed- iTech company should consider the following; provision of access to print servers and
file, reliability of local resources or the need of provision of links to remote logins, virtual LANs
usage or restriction of certain network access, the need of users to access application or database
servers and as such, are they frequently moving huge volume of data across the entire network.
Lammle & Tedder (2014).
The number of employees and networked devices iTech have and if this number will change in
future- depending its business, extra resources may be required to expand the network in future.
Plan should be made for the future not now.
Constraints imposed by the office setup on iTech planning and the availability of enough space
on the ceilings or floors to run network cables- the company should ensure that there is no
challenge that the office layout pose to the network infrastructure. If possible, documented and
dedicated conduits should be run entirely for the network infrastructure.
Physical software and hardware components required to develop the network infrastructure that
iTech is planning. The company should consider the location, connection, installation and
configuration of hardware components.
If iTech is to structure and build a new network infrastructure, it should consider standard that
will meet todays and future needs of the company. In addition, labor is very costly factor in the
project, so devoting in reliable cabling without utilizing its entire abilities currently might appear
more expensive now, but will be less costly than withdrawing to low-end cabling that might be
needed to reestablish 5 years later. The company should also ensure that network cabling is not
run parallel with the electrical installation. Shielded and Unshielded cabling interaction can be
disorganized by the magnetic field developed by electric cables, therefore causing bandwidth
lower considerably. Also, network cabling should be kept away from devices such as fans, a/c
units, fluorescent lighting among others. Another thing to acknowledge is cable management
usage. Addition of a network rack and arrangement of a good shelf-based cable management will
increase the cost of the project but ease maintenance process. Cable specification and length
should be verified. Also, network infrastructure should be tested using suitable tool after
configuration to ensure it suits it intended objective. Itech should set aside budget for installation
and maintenance of the new network infrastructure. Pradeep, (2016).

Running Head; IT INFRASTTRUCTURE 9
Once the above factors have been established, the remaining phase will be easy and straight
forward. Physical infrastructure entails Purchasing, assembling and installing the required
hardware while logical infrastructure involves Installation and configuration of the software and
applications.
Geographical Scope of the Network
According to Guizani, & Wiley, (2010), a computer network can be made up of a single device
that transfers data and another remote device that receives data. Due to the geographical
complexity in the amplitude of computer networks, there has been a need to categorize these
complexities. The following are some of the types of geographical computer network;
Body Area Network (BAN) - enhances interaction between sensors attached on the human body.
Campus Area Network (CAN) – this are several LAN's linked together at educational and
governmental buildings for instance universities and colleges.
Home Area Network (HAN) - this is the linkage of domestic devices that supports networking.
Local Area Network (LAN) - The range of a LAN is bigger than that of a HAN and covers a
smaller geographical area than that of a CAN. A Local Area Network is best fit for small offices
or schools.
Metropolitan Area Network (MAN) - a MAN covers a wider geographical area than CAN and
LAN, such as a town or a city center. It integrates high speed networking devices.
Personal Area Network (PAN) – this entails interconnection between small handheld devices, for
example Bluetooth devices and smartphones among others.
Wide Area Network (WAN) – This network covers the largest geographical area. It links
national and regional computer networks.
Scalability of iTech Network
Scalability have two functions;
The capability of a computer resource either software or hardware to continue with well
performance even after there is change in volume or size in order to meet objective of the user.
Rescaling is typically increasing the size or product, for instance, a group of computer systems
with varying sizes in terms of RAM, storage, and so forth. FitzGerald & Dennis, (2009).
The second is the capability to perform as expected in the rescaled situation and to utilize such
abilities offered. For example, it would be possible to scale an application program if it can be
moved from a smaller operating system such as single user to a larger operating system such as
multiuser and utilize the benefits of the larger operating system in terms of efficiency like
execution speed and so forth and the larger number of clients’ request supported.
Upward scalability is simpler than downward because designers and developers make full
utilization of system resources. For example, the size of storage available when an application is
first developed. Scalability of a product downward may lead to a more uneasy environment.
Once the above factors have been established, the remaining phase will be easy and straight
forward. Physical infrastructure entails Purchasing, assembling and installing the required
hardware while logical infrastructure involves Installation and configuration of the software and
applications.
Geographical Scope of the Network
According to Guizani, & Wiley, (2010), a computer network can be made up of a single device
that transfers data and another remote device that receives data. Due to the geographical
complexity in the amplitude of computer networks, there has been a need to categorize these
complexities. The following are some of the types of geographical computer network;
Body Area Network (BAN) - enhances interaction between sensors attached on the human body.
Campus Area Network (CAN) – this are several LAN's linked together at educational and
governmental buildings for instance universities and colleges.
Home Area Network (HAN) - this is the linkage of domestic devices that supports networking.
Local Area Network (LAN) - The range of a LAN is bigger than that of a HAN and covers a
smaller geographical area than that of a CAN. A Local Area Network is best fit for small offices
or schools.
Metropolitan Area Network (MAN) - a MAN covers a wider geographical area than CAN and
LAN, such as a town or a city center. It integrates high speed networking devices.
Personal Area Network (PAN) – this entails interconnection between small handheld devices, for
example Bluetooth devices and smartphones among others.
Wide Area Network (WAN) – This network covers the largest geographical area. It links
national and regional computer networks.
Scalability of iTech Network
Scalability have two functions;
The capability of a computer resource either software or hardware to continue with well
performance even after there is change in volume or size in order to meet objective of the user.
Rescaling is typically increasing the size or product, for instance, a group of computer systems
with varying sizes in terms of RAM, storage, and so forth. FitzGerald & Dennis, (2009).
The second is the capability to perform as expected in the rescaled situation and to utilize such
abilities offered. For example, it would be possible to scale an application program if it can be
moved from a smaller operating system such as single user to a larger operating system such as
multiuser and utilize the benefits of the larger operating system in terms of efficiency like
execution speed and so forth and the larger number of clients’ request supported.
Upward scalability is simpler than downward because designers and developers make full
utilization of system resources. For example, the size of storage available when an application is
first developed. Scalability of a product downward may lead to a more uneasy environment.
Running Head; IT INFRASTTRUCTURE 10
Dedicated Server
A dedicated server is the computer that attends to specific user request network. If iTech is to
choose dedicated server platform, it should monitor server resources usage and the demands of
users within the organization. Once a predetermine threshold has been arrived at, rules and
policies should be implemented to make sure that users requests are met. Dedicated servers can
be categorized into two groups: Managed and unmanaged. Lockhart, (2015).
Managed Dedicated Servers- they are managed by the internet service provider (ISP). For thuis
category of servers, client tasks and requests are entirely handle by the provider. It is perfect fit
for both large and small organizations because clients feel at ease when using it. Managed
Dedicated Servers have several advantages, they include: quick server response, Maximum
server uptime, increased security, greater and easier access to the server, technical functionalities
and support are entirely addressed by the ISP. However, it also have some disadvantages like
high maintenance cost, limited access because clients are not given root admin access. Lowe,
(2010).
Unmanaged dedicated servers- for this category servers are restricted entirely to the organization.
There is no external party maintaining or monitoring their user request and data. The client is the
one responsible for performing backup processes. However, it has several disadvantages which
include, there is no external technical support, network configuration and synchronization is time
consuming, complete web business knowledge is required which may not be possessed by all
users.
As mentioned earlier, dedicated server provide a specific service. The table below describes
dedicated server services and the type of server required:
Service Type of Server
Storage of user files File server
Communication services such as fax, remote
access and e-mails.
Communication Server
Shared applications Application Server
Data storage, requests for data and database
management
Database server
Authentication of users to access resources
within the logical domain
Domain server
Management of printers connected to the
network
Print server
Logical Network Design
. When you want to design a logical network you can start from scratch, or upgrade an existing
network. Before we design it we have to consider several important factors such as the type of
services to be provided and traffic patterns. The following factors be put into consideration:
Dedicated Server
A dedicated server is the computer that attends to specific user request network. If iTech is to
choose dedicated server platform, it should monitor server resources usage and the demands of
users within the organization. Once a predetermine threshold has been arrived at, rules and
policies should be implemented to make sure that users requests are met. Dedicated servers can
be categorized into two groups: Managed and unmanaged. Lockhart, (2015).
Managed Dedicated Servers- they are managed by the internet service provider (ISP). For thuis
category of servers, client tasks and requests are entirely handle by the provider. It is perfect fit
for both large and small organizations because clients feel at ease when using it. Managed
Dedicated Servers have several advantages, they include: quick server response, Maximum
server uptime, increased security, greater and easier access to the server, technical functionalities
and support are entirely addressed by the ISP. However, it also have some disadvantages like
high maintenance cost, limited access because clients are not given root admin access. Lowe,
(2010).
Unmanaged dedicated servers- for this category servers are restricted entirely to the organization.
There is no external party maintaining or monitoring their user request and data. The client is the
one responsible for performing backup processes. However, it has several disadvantages which
include, there is no external technical support, network configuration and synchronization is time
consuming, complete web business knowledge is required which may not be possessed by all
users.
As mentioned earlier, dedicated server provide a specific service. The table below describes
dedicated server services and the type of server required:
Service Type of Server
Storage of user files File server
Communication services such as fax, remote
access and e-mails.
Communication Server
Shared applications Application Server
Data storage, requests for data and database
management
Database server
Authentication of users to access resources
within the logical domain
Domain server
Management of printers connected to the
network
Print server
Logical Network Design
. When you want to design a logical network you can start from scratch, or upgrade an existing
network. Before we design it we have to consider several important factors such as the type of
services to be provided and traffic patterns. The following factors be put into consideration:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
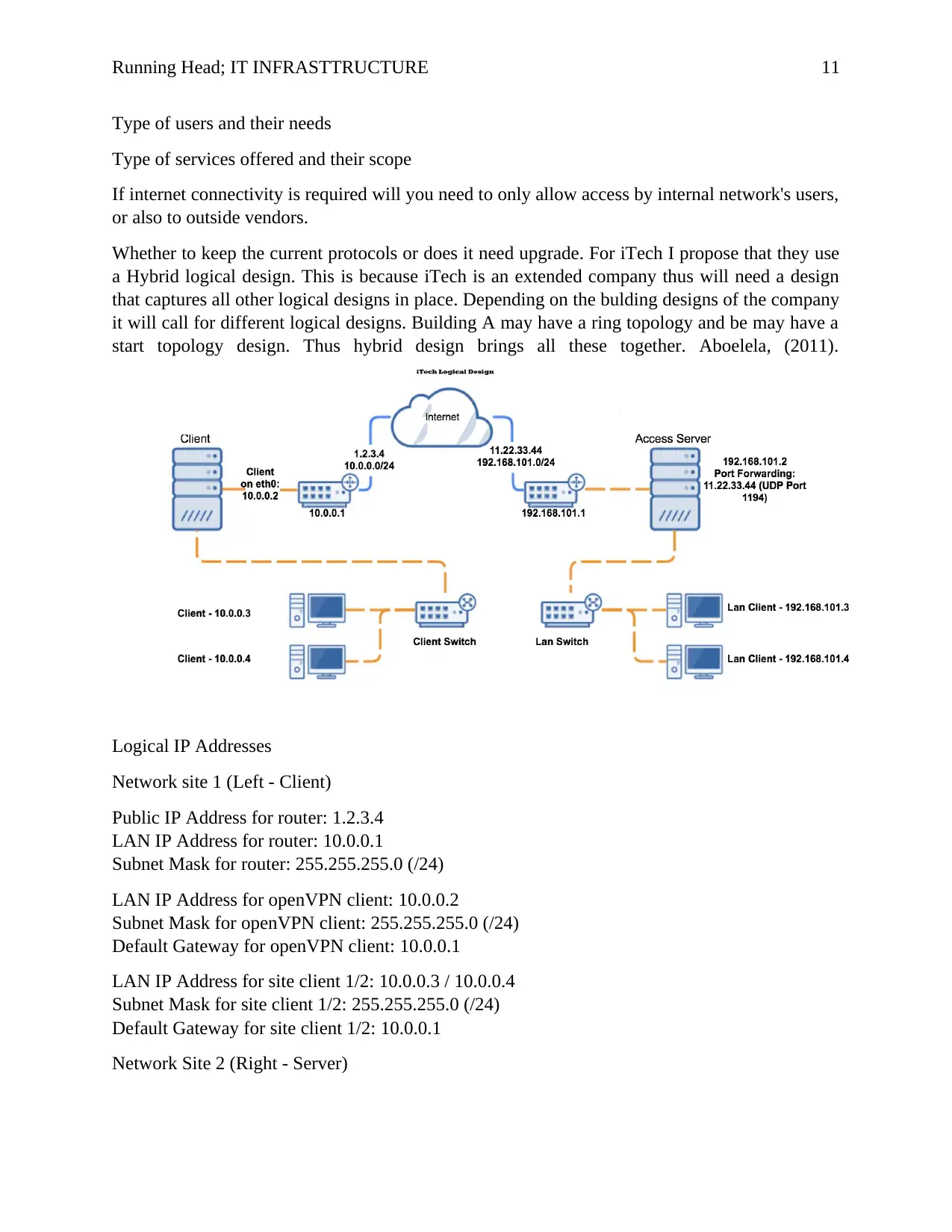
Running Head; IT INFRASTTRUCTURE 11
Type of users and their needs
Type of services offered and their scope
If internet connectivity is required will you need to only allow access by internal network's users,
or also to outside vendors.
Whether to keep the current protocols or does it need upgrade. For iTech I propose that they use
a Hybrid logical design. This is because iTech is an extended company thus will need a design
that captures all other logical designs in place. Depending on the bulding designs of the company
it will call for different logical designs. Building A may have a ring topology and be may have a
start topology design. Thus hybrid design brings all these together. Aboelela, (2011).
Logical IP Addresses
Network site 1 (Left - Client)
Public IP Address for router: 1.2.3.4
LAN IP Address for router: 10.0.0.1
Subnet Mask for router: 255.255.255.0 (/24)
LAN IP Address for openVPN client: 10.0.0.2
Subnet Mask for openVPN client: 255.255.255.0 (/24)
Default Gateway for openVPN client: 10.0.0.1
LAN IP Address for site client 1/2: 10.0.0.3 / 10.0.0.4
Subnet Mask for site client 1/2: 255.255.255.0 (/24)
Default Gateway for site client 1/2: 10.0.0.1
Network Site 2 (Right - Server)
Type of users and their needs
Type of services offered and their scope
If internet connectivity is required will you need to only allow access by internal network's users,
or also to outside vendors.
Whether to keep the current protocols or does it need upgrade. For iTech I propose that they use
a Hybrid logical design. This is because iTech is an extended company thus will need a design
that captures all other logical designs in place. Depending on the bulding designs of the company
it will call for different logical designs. Building A may have a ring topology and be may have a
start topology design. Thus hybrid design brings all these together. Aboelela, (2011).
Logical IP Addresses
Network site 1 (Left - Client)
Public IP Address for router: 1.2.3.4
LAN IP Address for router: 10.0.0.1
Subnet Mask for router: 255.255.255.0 (/24)
LAN IP Address for openVPN client: 10.0.0.2
Subnet Mask for openVPN client: 255.255.255.0 (/24)
Default Gateway for openVPN client: 10.0.0.1
LAN IP Address for site client 1/2: 10.0.0.3 / 10.0.0.4
Subnet Mask for site client 1/2: 255.255.255.0 (/24)
Default Gateway for site client 1/2: 10.0.0.1
Network Site 2 (Right - Server)

Running Head; IT INFRASTTRUCTURE 12
Public IP Address for router: 12.34.56.78
LAN IP Address for router: 192.168.101.1
Subnet Mask for router: 255.255.255.0 (/24)
LAN IP Address for OpenVPN Access Server: 192.168.101.2
Subnet Mask for OpenVPN Access Server: 255.255.255.0 (/24)
Default Gateway for OpenVPN Access Server: 192.168.101.1
LAN IP Address for site client 1/2: 192.168.0.3 / 192.168.101.4
Subnet Mask for site client 1/2: 255.255.255.0 (/24)
Default Gateway for site client 1/2: 192.168.101.1
Cloud based design
Cloud computing is used over the internet to enhance delivery of hosted services. It enables
organizations to utilize resources, like storage, virtual machine or an application, as a utility like
electricity instead of having to develop and manage computing infrastructures. The following
organization are recommended to iTech company to utilize their services;
Amazon AWS Cloud is the one leading cloud service provider. This famous company provides
some of the best and quality services at a friendly cost. AWS has highly secured server coupled
with efficient and dependable. It offers cloud-based solutions that are trustworthy to assist in
achieving the objectives. Solutions run in AWS cloud can improve the speed of application run
time and security level for the company. They also possess AWS code-commit which has 5
active users allocated 50GB storage per month. They also have several clients around the world
and have got best reviews. Its client control panel features are user friendly and makes it simpler
to maintain their services. Amazon Web Services(AWS) offer flexible prices on their services
with technical supports via phone calls, live chat, and e-mail. It has also made video tutorials for
their clients. Vermaat, (2017).
CtrlS Cloud- is a cloud provider that offer services to organizations operating on a network with
many devices and computers connected to it with a remote processing, storage and data
distribution.It ahas a sophisticated feature that in case your server fails then your data is moved
to another machine. It supports fast and user friendly hosting controls for easy administration,
maintenance and management of the company’s website. With just a click of a button CtrlS
cloud storage enables users to back up their data online.
The following are cloud computing services offered by these organizations the best suits iTech’s
network design; remote processing that allows handling of user request by the provider, cloud
storage that allows one to work on the data online, e-mails services that enables clients to
communicate without any problems, web hosting services to host iTech’s website and
continuous backup services for the company. Abdoulaye, (2014).
Access Layer Diagram
The diagram below shows and access diagram with web, DHCP and DNS server at different
VLANs. Distribution1 and Distribution 2 comprises of the Layer 3 VLAN affixes and functions
as the gateway for the hosts in the access tier.
Public IP Address for router: 12.34.56.78
LAN IP Address for router: 192.168.101.1
Subnet Mask for router: 255.255.255.0 (/24)
LAN IP Address for OpenVPN Access Server: 192.168.101.2
Subnet Mask for OpenVPN Access Server: 255.255.255.0 (/24)
Default Gateway for OpenVPN Access Server: 192.168.101.1
LAN IP Address for site client 1/2: 192.168.0.3 / 192.168.101.4
Subnet Mask for site client 1/2: 255.255.255.0 (/24)
Default Gateway for site client 1/2: 192.168.101.1
Cloud based design
Cloud computing is used over the internet to enhance delivery of hosted services. It enables
organizations to utilize resources, like storage, virtual machine or an application, as a utility like
electricity instead of having to develop and manage computing infrastructures. The following
organization are recommended to iTech company to utilize their services;
Amazon AWS Cloud is the one leading cloud service provider. This famous company provides
some of the best and quality services at a friendly cost. AWS has highly secured server coupled
with efficient and dependable. It offers cloud-based solutions that are trustworthy to assist in
achieving the objectives. Solutions run in AWS cloud can improve the speed of application run
time and security level for the company. They also possess AWS code-commit which has 5
active users allocated 50GB storage per month. They also have several clients around the world
and have got best reviews. Its client control panel features are user friendly and makes it simpler
to maintain their services. Amazon Web Services(AWS) offer flexible prices on their services
with technical supports via phone calls, live chat, and e-mail. It has also made video tutorials for
their clients. Vermaat, (2017).
CtrlS Cloud- is a cloud provider that offer services to organizations operating on a network with
many devices and computers connected to it with a remote processing, storage and data
distribution.It ahas a sophisticated feature that in case your server fails then your data is moved
to another machine. It supports fast and user friendly hosting controls for easy administration,
maintenance and management of the company’s website. With just a click of a button CtrlS
cloud storage enables users to back up their data online.
The following are cloud computing services offered by these organizations the best suits iTech’s
network design; remote processing that allows handling of user request by the provider, cloud
storage that allows one to work on the data online, e-mails services that enables clients to
communicate without any problems, web hosting services to host iTech’s website and
continuous backup services for the company. Abdoulaye, (2014).
Access Layer Diagram
The diagram below shows and access diagram with web, DHCP and DNS server at different
VLANs. Distribution1 and Distribution 2 comprises of the Layer 3 VLAN affixes and functions
as the gateway for the hosts in the access tier.
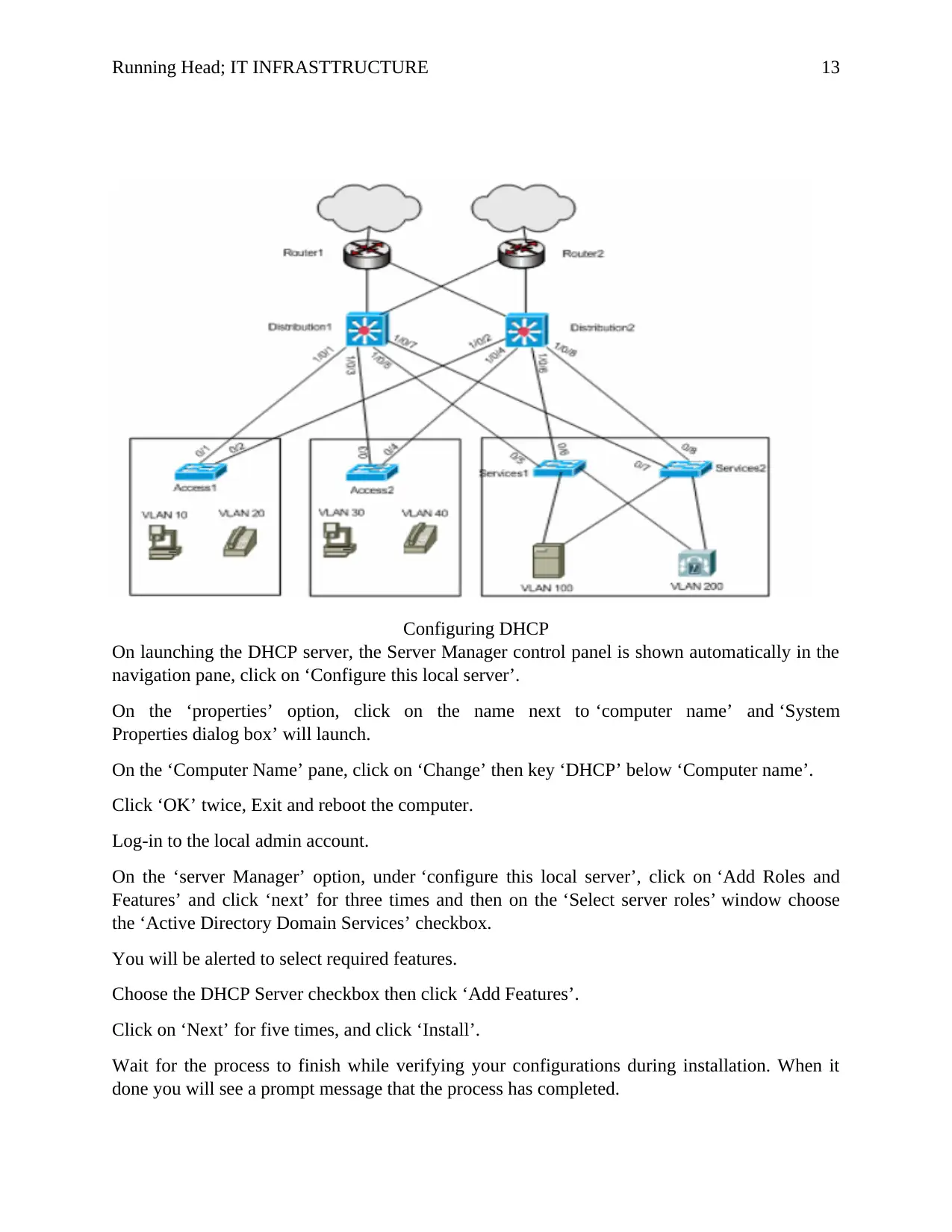
Running Head; IT INFRASTTRUCTURE 13
Configuring DHCP
On launching the DHCP server, the Server Manager control panel is shown automatically in the
navigation pane, click on ‘Configure this local server’.
On the ‘properties’ option, click on the name next to ‘computer name’ and ‘System
Properties dialog box’ will launch.
On the ‘Computer Name’ pane, click on ‘Change’ then key ‘DHCP’ below ‘Computer name’.
Click ‘OK’ twice, Exit and reboot the computer.
Log-in to the local admin account.
On the ‘server Manager’ option, under ‘configure this local server’, click on ‘Add Roles and
Features’ and click ‘next’ for three times and then on the ‘Select server roles’ window choose
the ‘Active Directory Domain Services’ checkbox.
You will be alerted to select required features.
Choose the DHCP Server checkbox then click ‘Add Features’.
Click on ‘Next’ for five times, and click ‘Install’.
Wait for the process to finish while verifying your configurations during installation. When it
done you will see a prompt message that the process has completed.
Configuring DHCP
On launching the DHCP server, the Server Manager control panel is shown automatically in the
navigation pane, click on ‘Configure this local server’.
On the ‘properties’ option, click on the name next to ‘computer name’ and ‘System
Properties dialog box’ will launch.
On the ‘Computer Name’ pane, click on ‘Change’ then key ‘DHCP’ below ‘Computer name’.
Click ‘OK’ twice, Exit and reboot the computer.
Log-in to the local admin account.
On the ‘server Manager’ option, under ‘configure this local server’, click on ‘Add Roles and
Features’ and click ‘next’ for three times and then on the ‘Select server roles’ window choose
the ‘Active Directory Domain Services’ checkbox.
You will be alerted to select required features.
Choose the DHCP Server checkbox then click ‘Add Features’.
Click on ‘Next’ for five times, and click ‘Install’.
Wait for the process to finish while verifying your configurations during installation. When it
done you will see a prompt message that the process has completed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running Head; IT INFRASTTRUCTURE 14
Click on the ‘Notification’ bar and select ‘Promote this server to a domain controller’.
The computer will automatically reboot to finish the installation activites.
Configuring a DNS Server
To setup a DNS server from scratch with the use of Windows interface
Launch ‘DNS Manager’.
Include the ‘applicable server’ to the snap-in, and then link to it if necessary.
Click on the ‘applicable DNS server’ in the ‘console tree’.
Click on ‘Configure a DNS Server’ on the ‘Action menu’ and follow the steps in the ‘Configure
a DNS Server’ Wizard.
Configuring a DNS server by use of command line.
Launch a command prompt.
Key in the command in the table below, and then press ENTER:
dnscmd <ServerName> /Config {<ZoneName>|..AllZones} <Property> {1|0}
Command Meaning
Dnscmd determines the identity of the command-line mechamism for
managing DNS servers.
<ServerName> This shows the DNS host name of the DNS server. You can also
use DNS server IP address.
/Config Command the specifies configuration of a specific zone.
{<ZoneName>|..AllZones
}
Shows the name of the zone to be set up
<Property> Specifies the zone or server property to be configured. Key
in: dnscmd /Config /help to display the list of the derivable
properties on the command prompt..
{1|0} Sets set up alternatives to either 1 (on) or 0 (off).
Click on the ‘Notification’ bar and select ‘Promote this server to a domain controller’.
The computer will automatically reboot to finish the installation activites.
Configuring a DNS Server
To setup a DNS server from scratch with the use of Windows interface
Launch ‘DNS Manager’.
Include the ‘applicable server’ to the snap-in, and then link to it if necessary.
Click on the ‘applicable DNS server’ in the ‘console tree’.
Click on ‘Configure a DNS Server’ on the ‘Action menu’ and follow the steps in the ‘Configure
a DNS Server’ Wizard.
Configuring a DNS server by use of command line.
Launch a command prompt.
Key in the command in the table below, and then press ENTER:
dnscmd <ServerName> /Config {<ZoneName>|..AllZones} <Property> {1|0}
Command Meaning
Dnscmd determines the identity of the command-line mechamism for
managing DNS servers.
<ServerName> This shows the DNS host name of the DNS server. You can also
use DNS server IP address.
/Config Command the specifies configuration of a specific zone.
{<ZoneName>|..AllZones
}
Shows the name of the zone to be set up
<Property> Specifies the zone or server property to be configured. Key
in: dnscmd /Config /help to display the list of the derivable
properties on the command prompt..
{1|0} Sets set up alternatives to either 1 (on) or 0 (off).
Running Head; IT INFRASTTRUCTURE 15
Configuring a Web Server
Configuring a Web Server demands for the administrative credentials of the IIS Web Server
Administrator role. Once logged in:
1. using one of the methods below, open the Add Roles:
Open Add Roles from the Initial Configuration Task Window on a new windows server 2008
installation.
Go to the ’Server Manager’, then to the roles manager and select Add Roles
2. you will notice some recommendations for the installation on the Add Roles Wizard click
the Next button to continue.
3. upon advice to include the Windows Process Activation function characteristic, open the
needed Features button.
4. review the box marked Web Server (IIS) from the Select Server Roles Wizard and select
next to carry forward.
Configuring a Web Server
Configuring a Web Server demands for the administrative credentials of the IIS Web Server
Administrator role. Once logged in:
1. using one of the methods below, open the Add Roles:
Open Add Roles from the Initial Configuration Task Window on a new windows server 2008
installation.
Go to the ’Server Manager’, then to the roles manager and select Add Roles
2. you will notice some recommendations for the installation on the Add Roles Wizard click
the Next button to continue.
3. upon advice to include the Windows Process Activation function characteristic, open the
needed Features button.
4. review the box marked Web Server (IIS) from the Select Server Roles Wizard and select
next to carry forward.
Running Head; IT INFRASTTRUCTURE 16
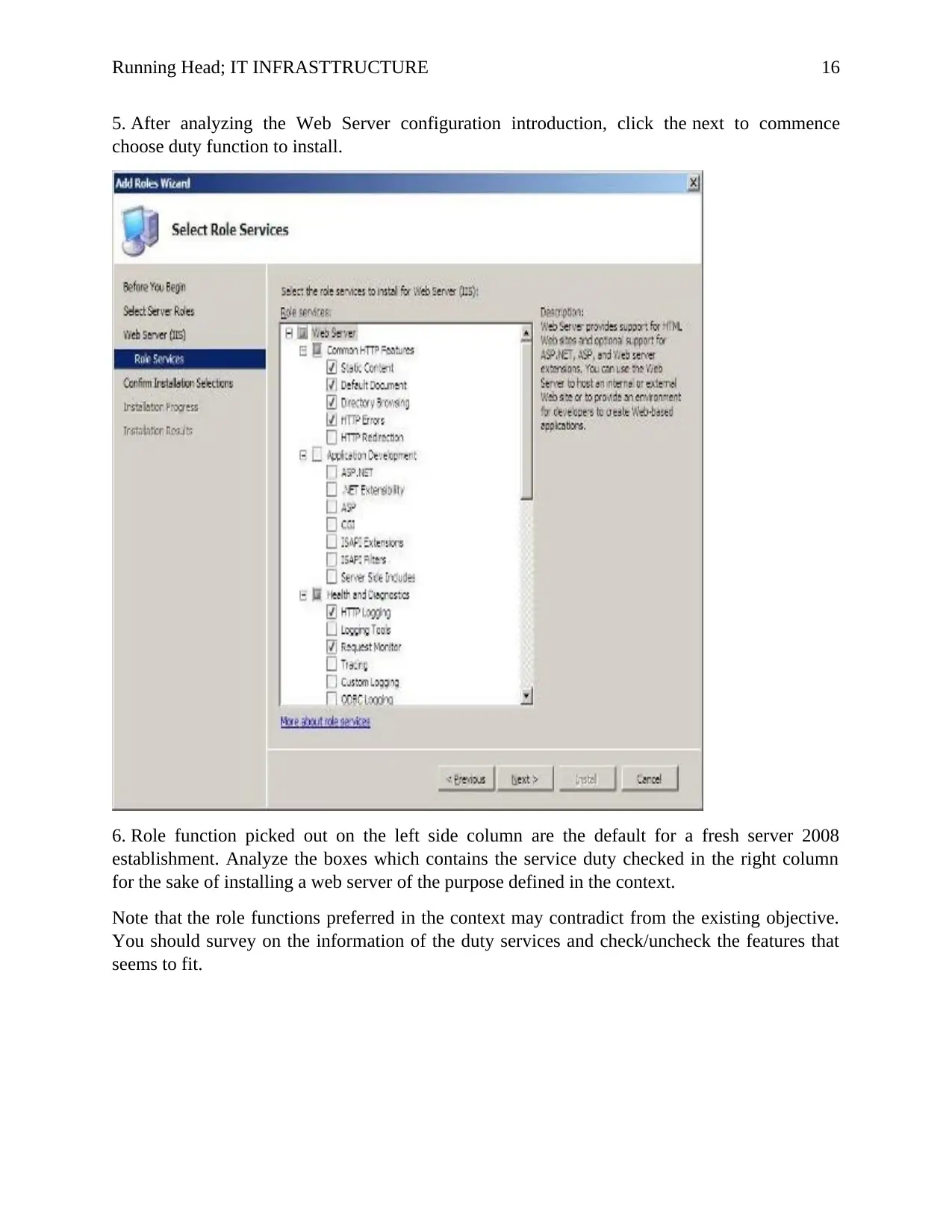
5. After analyzing the Web Server configuration introduction, click the next to commence
choose duty function to install.
6. Role function picked out on the left side column are the default for a fresh server 2008
establishment. Analyze the boxes which contains the service duty checked in the right column
for the sake of installing a web server of the purpose defined in the context.
Note that the role functions preferred in the context may contradict from the existing objective.
You should survey on the information of the duty services and check/uncheck the features that
seems to fit.
5. After analyzing the Web Server configuration introduction, click the next to commence
choose duty function to install.
6. Role function picked out on the left side column are the default for a fresh server 2008
establishment. Analyze the boxes which contains the service duty checked in the right column
for the sake of installing a web server of the purpose defined in the context.
Note that the role functions preferred in the context may contradict from the existing objective.
You should survey on the information of the duty services and check/uncheck the features that
seems to fit.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Running Head; IT INFRASTTRUCTURE 17
7. After selecting the box identified as application development, you may be requested to add the
.NET Environment, that had not been configured. Select the Add Required characteristics button
thus allowing you to advance on selecting role functions.
7. After selecting the box identified as application development, you may be requested to add the
.NET Environment, that had not been configured. Select the Add Required characteristics button
thus allowing you to advance on selecting role functions.
Running Head; IT INFRASTTRUCTURE 18
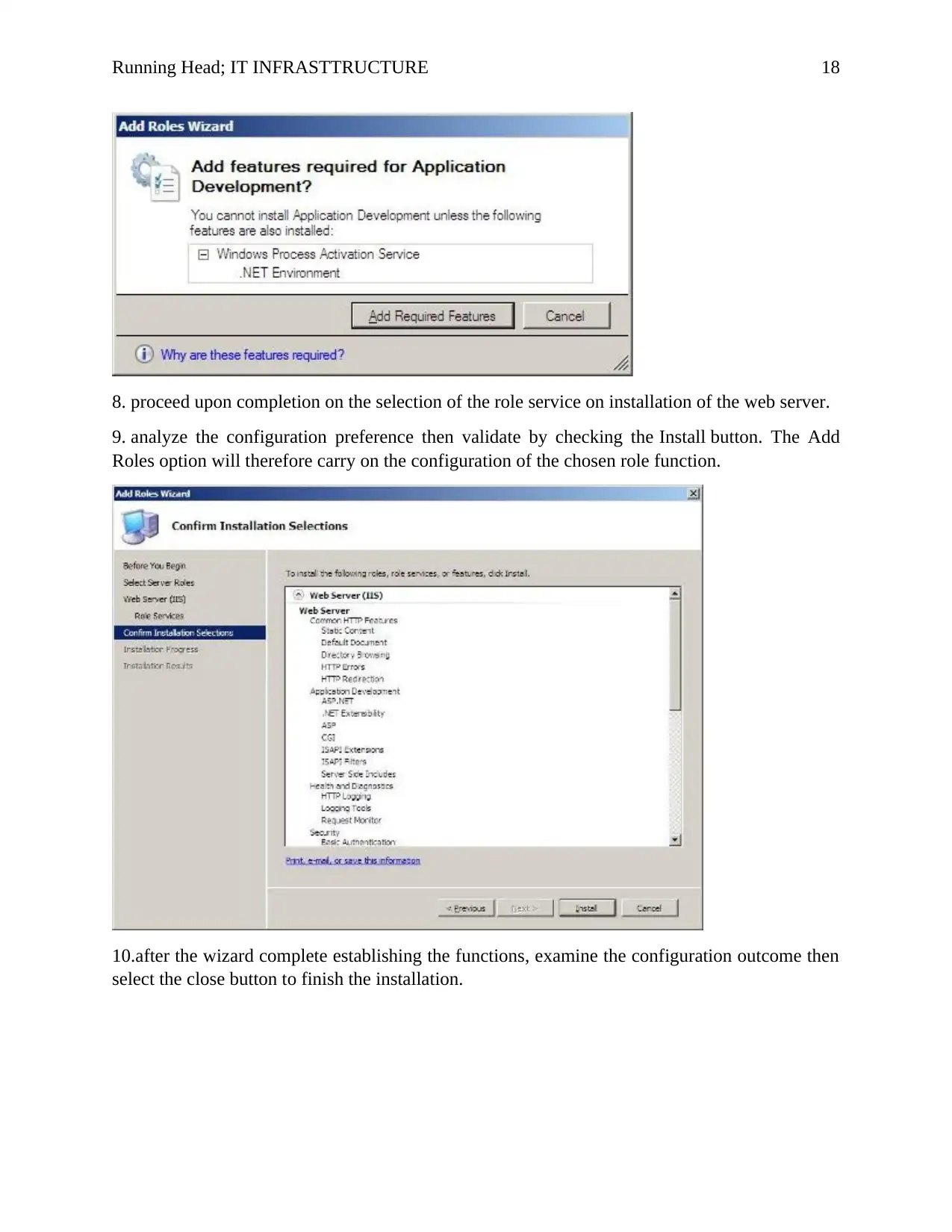
8. proceed upon completion on the selection of the role service on installation of the web server.
9. analyze the configuration preference then validate by checking the Install button. The Add
Roles option will therefore carry on the configuration of the chosen role function.
10.after the wizard complete establishing the functions, examine the configuration outcome then
select the close button to finish the installation.
8. proceed upon completion on the selection of the role service on installation of the web server.
9. analyze the configuration preference then validate by checking the Install button. The Add
Roles option will therefore carry on the configuration of the chosen role function.
10.after the wizard complete establishing the functions, examine the configuration outcome then
select the close button to finish the installation.
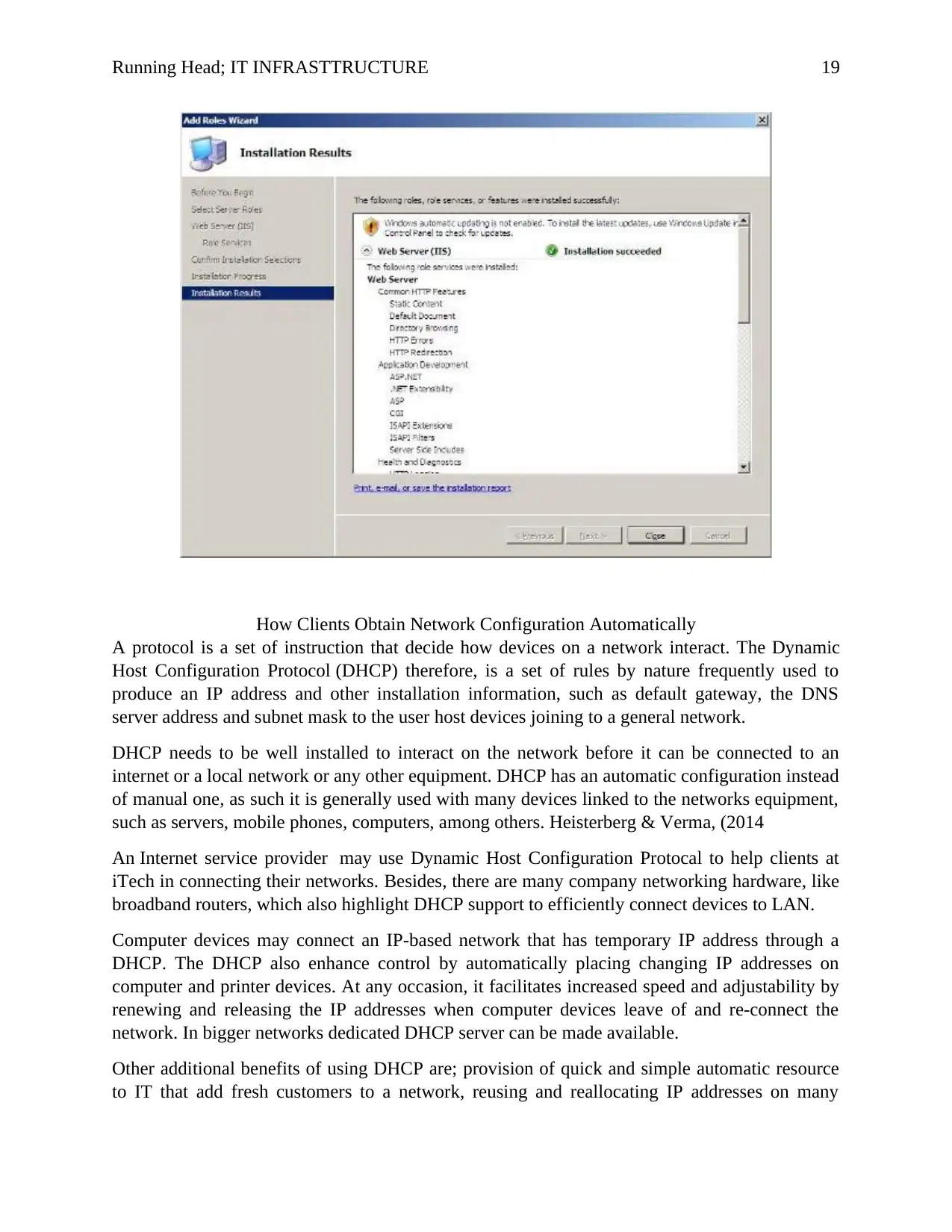
Running Head; IT INFRASTTRUCTURE 19
How Clients Obtain Network Configuration Automatically
A protocol is a set of instruction that decide how devices on a network interact. The Dynamic
Host Configuration Protocol (DHCP) therefore, is a set of rules by nature frequently used to
produce an IP address and other installation information, such as default gateway, the DNS
server address and subnet mask to the user host devices joining to a general network.
DHCP needs to be well installed to interact on the network before it can be connected to an
internet or a local network or any other equipment. DHCP has an automatic configuration instead
of manual one, as such it is generally used with many devices linked to the networks equipment,
such as servers, mobile phones, computers, among others. Heisterberg & Verma, (2014
An Internet service provider may use Dynamic Host Configuration Protocal to help clients at
iTech in connecting their networks. Besides, there are many company networking hardware, like
broadband routers, which also highlight DHCP support to efficiently connect devices to LAN.
Computer devices may connect an IP-based network that has temporary IP address through a
DHCP. The DHCP also enhance control by automatically placing changing IP addresses on
computer and printer devices. At any occasion, it facilitates increased speed and adjustability by
renewing and releasing the IP addresses when computer devices leave of and re-connect the
network. In bigger networks dedicated DHCP server can be made available.
Other additional benefits of using DHCP are; provision of quick and simple automatic resource
to IT that add fresh customers to a network, reusing and reallocating IP addresses on many
How Clients Obtain Network Configuration Automatically
A protocol is a set of instruction that decide how devices on a network interact. The Dynamic
Host Configuration Protocol (DHCP) therefore, is a set of rules by nature frequently used to
produce an IP address and other installation information, such as default gateway, the DNS
server address and subnet mask to the user host devices joining to a general network.
DHCP needs to be well installed to interact on the network before it can be connected to an
internet or a local network or any other equipment. DHCP has an automatic configuration instead
of manual one, as such it is generally used with many devices linked to the networks equipment,
such as servers, mobile phones, computers, among others. Heisterberg & Verma, (2014
An Internet service provider may use Dynamic Host Configuration Protocal to help clients at
iTech in connecting their networks. Besides, there are many company networking hardware, like
broadband routers, which also highlight DHCP support to efficiently connect devices to LAN.
Computer devices may connect an IP-based network that has temporary IP address through a
DHCP. The DHCP also enhance control by automatically placing changing IP addresses on
computer and printer devices. At any occasion, it facilitates increased speed and adjustability by
renewing and releasing the IP addresses when computer devices leave of and re-connect the
network. In bigger networks dedicated DHCP server can be made available.
Other additional benefits of using DHCP are; provision of quick and simple automatic resource
to IT that add fresh customers to a network, reusing and reallocating IP addresses on many
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running Head; IT INFRASTTRUCTURE 20
devices in accordance to the usage, which minimizes the amount of IP addresses needed across
the network and also reconfiguring DHCP server’s Internet Protocol address area without
remodifying every user device.
Dynamic Host Configuration Protocol Customer and
Servers
In the dynamic host control protocol platform, the DHCP server should be installed with the right
network setup. Within the framework there consist a pool of existing subnet masks, network
gateway, IP addresses and the name server addresses. A computer that runs the DHCP client
application can get the network settings from DHCP servers automatically. Laan, (2013).
In case a DHCP client is powered on, it is given an IP address generated from the pool of present
IP addresses. The devices are then assigned these IPs by the DHCP server for a defined period
time called lease.
Conclusion
While companies reason vary on choices, industries, businesses of all sizes and geographies are
embracing cloud computing. Investing on cloud computing infrastructure and platforms will
grow at a a company by a good percentage. Cloud computing is rising at a fast rate than it was
anticipated.
Recommendation
I recommend to iTech that if it is looking at Infrastructure-as-a-Service (IaaS) Platform-as-a-
Service (PaaS) or Software-as-a-Service (SaaS) it should embrace and consider investing in
cloud computing. With cloud computing, iTech will reduce the size of their own data centers or
do away with data center footprint.
devices in accordance to the usage, which minimizes the amount of IP addresses needed across
the network and also reconfiguring DHCP server’s Internet Protocol address area without
remodifying every user device.
Dynamic Host Configuration Protocol Customer and
Servers
In the dynamic host control protocol platform, the DHCP server should be installed with the right
network setup. Within the framework there consist a pool of existing subnet masks, network
gateway, IP addresses and the name server addresses. A computer that runs the DHCP client
application can get the network settings from DHCP servers automatically. Laan, (2013).
In case a DHCP client is powered on, it is given an IP address generated from the pool of present
IP addresses. The devices are then assigned these IPs by the DHCP server for a defined period
time called lease.
Conclusion
While companies reason vary on choices, industries, businesses of all sizes and geographies are
embracing cloud computing. Investing on cloud computing infrastructure and platforms will
grow at a a company by a good percentage. Cloud computing is rising at a fast rate than it was
anticipated.
Recommendation
I recommend to iTech that if it is looking at Infrastructure-as-a-Service (IaaS) Platform-as-a-
Service (PaaS) or Software-as-a-Service (SaaS) it should embrace and consider investing in
cloud computing. With cloud computing, iTech will reduce the size of their own data centers or
do away with data center footprint.

Running Head; IT INFRASTTRUCTURE 21
References
Furht, B., & Escalante, A. (2010). Handbook of cloud computing. New York: Springer.
Reese, G. (2009). Cloud application architectures. Sebastopol, Calif: O'Reilly Media, Inc.
Abdoulaye, P. (2014). Cloud computing - advanced business and it approaches to extract
tangible. Place of publication not identified: Lulu Com.
CloudComp (Conference), In Zhang, Y., In Peng, L., & In Youn, C.-H. (2016). Cloud
computing: 6th International Conference, CloudComp 2015, Daejeon, South Korea, October 28-
29, 2015, Proceedings.
Heisterberg, R. J., & Verma, A. (2014). Creating business agility: How convergence of cloud,
social, mobile, video, and big data enables competitive advantage.
Laan, S. (2013). It infrastructure architecture - infrastructure building blocks and concepts. Place
of publication not identified: Lulu Com.
Laan, S. (2011). It infrastructure architecture: Infrastructure building blocks and concepts. Lulu
Press.
Rensin, D. K. (2012). Building a Windows IT infrastructure in the cloud: [distributed hosted
environments with AWS]. Beijing: O'Reilly.
Laan, S. (2017). IT infrastructure architecture: Infrastructure building blocks and concepts.
Pop, P. C. (2012). Generalized Network Design Problems: Modeling and Optimization. Berlin:
De Gruyter.
Cisco Networking Academy Program,. (2014). Connecting networks.
Lammle, T., & Tedder, W. (2014). CCNA routing and switching deluxe study guide: [exam 100-
101, 200-101, and 200-120]. Indianapolis, Ind: Sybex.
Pradeep, S. (2016). Information technology. Place of publication not identified: Phi Learning.
Panek, W., Wentworth, T., & Chellis, J. (2015). MCTS Windows Server 2008 Network
Infrastructure Configuration Study Guide: Exam 70-642. New York, NY: John Wiley & Sons.
FitzGerald, J., & Dennis, A. (2009). Business data communications and networking. Hoboken,
NJ: John Wiley.
Lockhart, J. (2015). Modern PHP: New features and good practices.
Lowe, D. (2010). Networking for dummies. Hoboken, NJ: Wiley.
Vermaat, M. (2017). Discovering computers 2017: Essentials : tools, apps, devices, and the
impact of technology. Boston, MA: Cengage Learning.
Aboelela, E. (2011). Network Simulation Experiments Manual. Burlington: Elsevier Science.
References
Furht, B., & Escalante, A. (2010). Handbook of cloud computing. New York: Springer.
Reese, G. (2009). Cloud application architectures. Sebastopol, Calif: O'Reilly Media, Inc.
Abdoulaye, P. (2014). Cloud computing - advanced business and it approaches to extract
tangible. Place of publication not identified: Lulu Com.
CloudComp (Conference), In Zhang, Y., In Peng, L., & In Youn, C.-H. (2016). Cloud
computing: 6th International Conference, CloudComp 2015, Daejeon, South Korea, October 28-
29, 2015, Proceedings.
Heisterberg, R. J., & Verma, A. (2014). Creating business agility: How convergence of cloud,
social, mobile, video, and big data enables competitive advantage.
Laan, S. (2013). It infrastructure architecture - infrastructure building blocks and concepts. Place
of publication not identified: Lulu Com.
Laan, S. (2011). It infrastructure architecture: Infrastructure building blocks and concepts. Lulu
Press.
Rensin, D. K. (2012). Building a Windows IT infrastructure in the cloud: [distributed hosted
environments with AWS]. Beijing: O'Reilly.
Laan, S. (2017). IT infrastructure architecture: Infrastructure building blocks and concepts.
Pop, P. C. (2012). Generalized Network Design Problems: Modeling and Optimization. Berlin:
De Gruyter.
Cisco Networking Academy Program,. (2014). Connecting networks.
Lammle, T., & Tedder, W. (2014). CCNA routing and switching deluxe study guide: [exam 100-
101, 200-101, and 200-120]. Indianapolis, Ind: Sybex.
Pradeep, S. (2016). Information technology. Place of publication not identified: Phi Learning.
Panek, W., Wentworth, T., & Chellis, J. (2015). MCTS Windows Server 2008 Network
Infrastructure Configuration Study Guide: Exam 70-642. New York, NY: John Wiley & Sons.
FitzGerald, J., & Dennis, A. (2009). Business data communications and networking. Hoboken,
NJ: John Wiley.
Lockhart, J. (2015). Modern PHP: New features and good practices.
Lowe, D. (2010). Networking for dummies. Hoboken, NJ: Wiley.
Vermaat, M. (2017). Discovering computers 2017: Essentials : tools, apps, devices, and the
impact of technology. Boston, MA: Cengage Learning.
Aboelela, E. (2011). Network Simulation Experiments Manual. Burlington: Elsevier Science.

Running Head; IT INFRASTTRUCTURE 22
Guizani, M., & Wiley InterScience (Online service). (2010). Network modeling and simulation:
A practical perspective. Chichester, West Sussex, U.K: Wiley.
Guizani, M., & Wiley InterScience (Online service). (2010). Network modeling and simulation:
A practical perspective. Chichester, West Sussex, U.K: Wiley.
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





