Wireless and Cellular Communications Review: Assignment Report Details
VerifiedAdded on 2022/11/13
|13
|3291
|1
Report
AI Summary
This report provides a comprehensive review of cellular and wireless communications, addressing various aspects of network design and security. It begins by outlining five methods to enhance cellular system capacity, including cell site additions and smart antennas. The report then explores solutions to prevent Bluetooth interference in WLANs and compares Bluetooth and Zigbee technologies. It discusses the RTS/CTS protocol, differentiating between hard and soft handoffs, and contrasts CSMA/CD and CSMA/CA. The final section surveys the security aspects of wireless networks, including vulnerabilities like default router configurations and rogue access points, along with security protocols such as WEP, WPA, and WPA2, and countermeasures against wireless jamming.

Running head: REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
Review of Cellular and Wireless Communications
Name of the Student
Name of the University
Author Note
Review of Cellular and Wireless Communications
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
1. Ways to increase Cellular System Capacity
The five key ways by which the capacity of cellular network systems can be
improved are as follows:
1. Addition of Cell Sites
2. Addition of Sectors
3. Addition of Carriers
4. Improving Air Interface Capability
5. Use of Smart Antennas
Cell Sites: Addition of cell sites are expensive yet very effective an approach to
increasing capacity (Andryeyev and Mitschele-Thiel, 2017). Usually the process of
adding newer real estate consumes lot of time and complications.
Cell Sectors: Addition of sectors like change from three sectors to six sectors is an
effective way in approximating new cell introductions. This not necessarily doubles
the capacity since the petals of six sector coverage does not interleave so well as
three sector coverage.
Cell Carriers: Addition of carriers that is bandwidth increases capacity directly
(Bayhan, Zheng, Chen, Di Francesco, Kangasharju & Chiang, 2017). The Long Term
Evaluation or LTE standard excels in using increased bandwidth without increasing
overheads of control channels.
Air Interface Capability: Improving the capability of air interface includes evolution
from Universal Mobile Telecommunications or UMTS towards High Speed Downlink
Packet Access or HSDPA which can provide more than four times the downlink
capacity.
1. Ways to increase Cellular System Capacity
The five key ways by which the capacity of cellular network systems can be
improved are as follows:
1. Addition of Cell Sites
2. Addition of Sectors
3. Addition of Carriers
4. Improving Air Interface Capability
5. Use of Smart Antennas
Cell Sites: Addition of cell sites are expensive yet very effective an approach to
increasing capacity (Andryeyev and Mitschele-Thiel, 2017). Usually the process of
adding newer real estate consumes lot of time and complications.
Cell Sectors: Addition of sectors like change from three sectors to six sectors is an
effective way in approximating new cell introductions. This not necessarily doubles
the capacity since the petals of six sector coverage does not interleave so well as
three sector coverage.
Cell Carriers: Addition of carriers that is bandwidth increases capacity directly
(Bayhan, Zheng, Chen, Di Francesco, Kangasharju & Chiang, 2017). The Long Term
Evaluation or LTE standard excels in using increased bandwidth without increasing
overheads of control channels.
Air Interface Capability: Improving the capability of air interface includes evolution
from Universal Mobile Telecommunications or UMTS towards High Speed Downlink
Packet Access or HSDPA which can provide more than four times the downlink
capacity.

2REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
Smart Antenna: Smart Antennas provide are responsible for providing another
significant boost for the throughput. These are the adaptive antennas which have
azimuth control, beam and electrical tilt following slow variance in traffic patterns and
also intelligent antennas which can create beams towards specific users and
reduces interferences. They can also come in MIMO or Multiple Input Multiple Output
antenna schemes.
2. Ways to prevent Jamming of WLAN by Bluetooth
Jamming of WLAN networks by Bluetooth services can be reduced in the
several ways. Out of which 5 ways are:
By bringing Wi-Fi devices and /Wi-Fi routers closer to one another
By removing barriers like building materials which may cause interferences
such as walls of metal, bulletproof glass, concrete, marble and plaster.
By avoiding use of wireless devices near devices paired over Bluetooth
By changing the frequency band of wireless networks from 2.4 GHz (also
used by Bluetooth) to 5 GHz (only supported by Wi-Fi.
By making the wireless router use different Wi-Fi channels or to scan and find
channels with the least interferences. Usually these routers perform scans
automatically when starting or getting reset.
3. Comparison between Bluetooth and Zigbee Technologies
Bluetooth Zigbee
The frequency range supported by
Bluetooth varies from 2.4 GHz to 2.483
GHz.
The frequency ban supported by Zigbee
is 2.4 all across the world.
There exists 79 Radio Frequency or RF Zigbee only has 16 RF channels.
Smart Antenna: Smart Antennas provide are responsible for providing another
significant boost for the throughput. These are the adaptive antennas which have
azimuth control, beam and electrical tilt following slow variance in traffic patterns and
also intelligent antennas which can create beams towards specific users and
reduces interferences. They can also come in MIMO or Multiple Input Multiple Output
antenna schemes.
2. Ways to prevent Jamming of WLAN by Bluetooth
Jamming of WLAN networks by Bluetooth services can be reduced in the
several ways. Out of which 5 ways are:
By bringing Wi-Fi devices and /Wi-Fi routers closer to one another
By removing barriers like building materials which may cause interferences
such as walls of metal, bulletproof glass, concrete, marble and plaster.
By avoiding use of wireless devices near devices paired over Bluetooth
By changing the frequency band of wireless networks from 2.4 GHz (also
used by Bluetooth) to 5 GHz (only supported by Wi-Fi.
By making the wireless router use different Wi-Fi channels or to scan and find
channels with the least interferences. Usually these routers perform scans
automatically when starting or getting reset.
3. Comparison between Bluetooth and Zigbee Technologies
Bluetooth Zigbee
The frequency range supported by
Bluetooth varies from 2.4 GHz to 2.483
GHz.
The frequency ban supported by Zigbee
is 2.4 all across the world.
There exists 79 Radio Frequency or RF Zigbee only has 16 RF channels.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
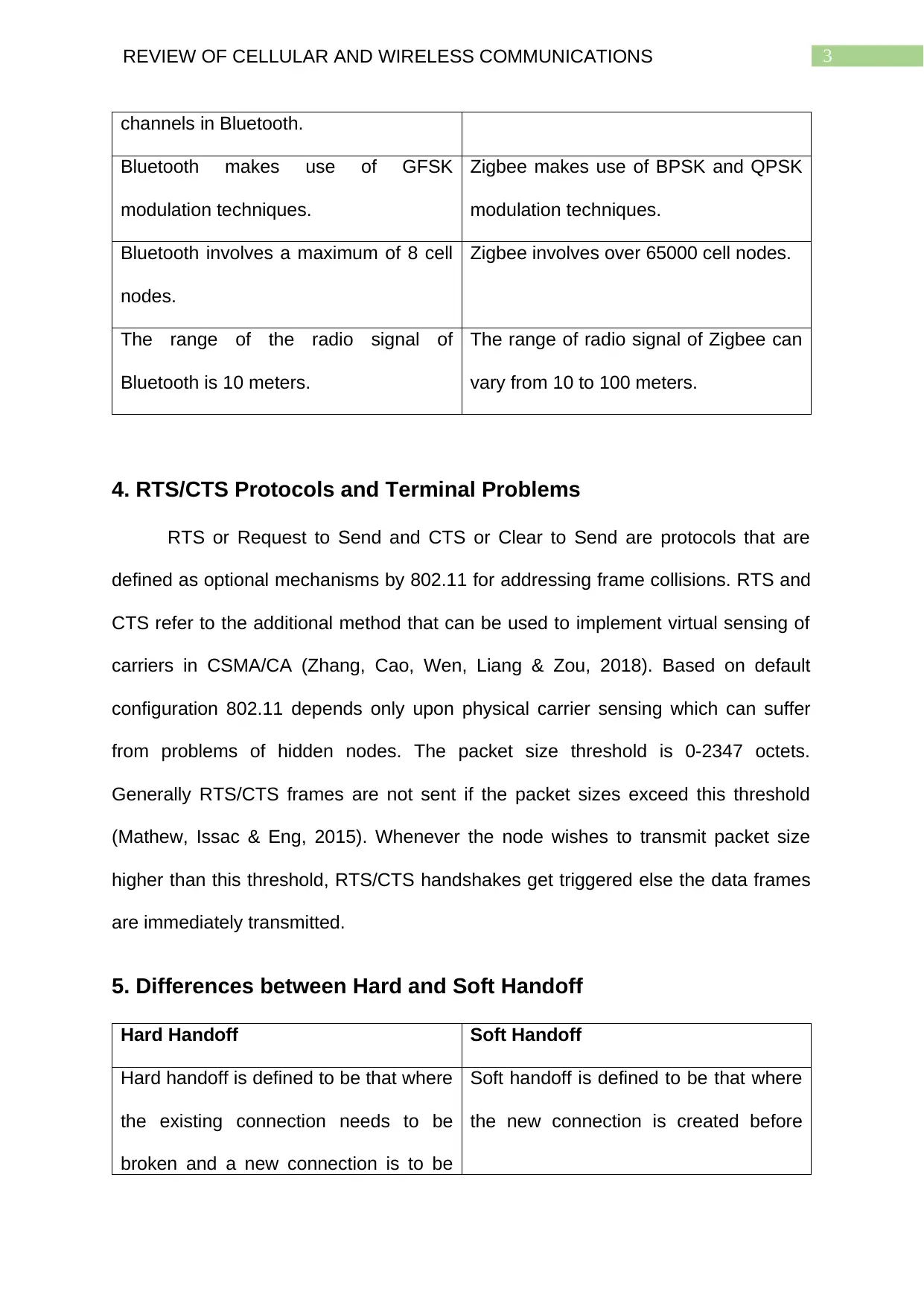
channels in Bluetooth.
Bluetooth makes use of GFSK
modulation techniques.
Zigbee makes use of BPSK and QPSK
modulation techniques.
Bluetooth involves a maximum of 8 cell
nodes.
Zigbee involves over 65000 cell nodes.
The range of the radio signal of
Bluetooth is 10 meters.
The range of radio signal of Zigbee can
vary from 10 to 100 meters.
4. RTS/CTS Protocols and Terminal Problems
RTS or Request to Send and CTS or Clear to Send are protocols that are
defined as optional mechanisms by 802.11 for addressing frame collisions. RTS and
CTS refer to the additional method that can be used to implement virtual sensing of
carriers in CSMA/CA (Zhang, Cao, Wen, Liang & Zou, 2018). Based on default
configuration 802.11 depends only upon physical carrier sensing which can suffer
from problems of hidden nodes. The packet size threshold is 0-2347 octets.
Generally RTS/CTS frames are not sent if the packet sizes exceed this threshold
(Mathew, Issac & Eng, 2015). Whenever the node wishes to transmit packet size
higher than this threshold, RTS/CTS handshakes get triggered else the data frames
are immediately transmitted.
5. Differences between Hard and Soft Handoff
Hard Handoff Soft Handoff
Hard handoff is defined to be that where
the existing connection needs to be
broken and a new connection is to be
Soft handoff is defined to be that where
the new connection is created before
channels in Bluetooth.
Bluetooth makes use of GFSK
modulation techniques.
Zigbee makes use of BPSK and QPSK
modulation techniques.
Bluetooth involves a maximum of 8 cell
nodes.
Zigbee involves over 65000 cell nodes.
The range of the radio signal of
Bluetooth is 10 meters.
The range of radio signal of Zigbee can
vary from 10 to 100 meters.
4. RTS/CTS Protocols and Terminal Problems
RTS or Request to Send and CTS or Clear to Send are protocols that are
defined as optional mechanisms by 802.11 for addressing frame collisions. RTS and
CTS refer to the additional method that can be used to implement virtual sensing of
carriers in CSMA/CA (Zhang, Cao, Wen, Liang & Zou, 2018). Based on default
configuration 802.11 depends only upon physical carrier sensing which can suffer
from problems of hidden nodes. The packet size threshold is 0-2347 octets.
Generally RTS/CTS frames are not sent if the packet sizes exceed this threshold
(Mathew, Issac & Eng, 2015). Whenever the node wishes to transmit packet size
higher than this threshold, RTS/CTS handshakes get triggered else the data frames
are immediately transmitted.
5. Differences between Hard and Soft Handoff
Hard Handoff Soft Handoff
Hard handoff is defined to be that where
the existing connection needs to be
broken and a new connection is to be
Soft handoff is defined to be that where
the new connection is created before
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
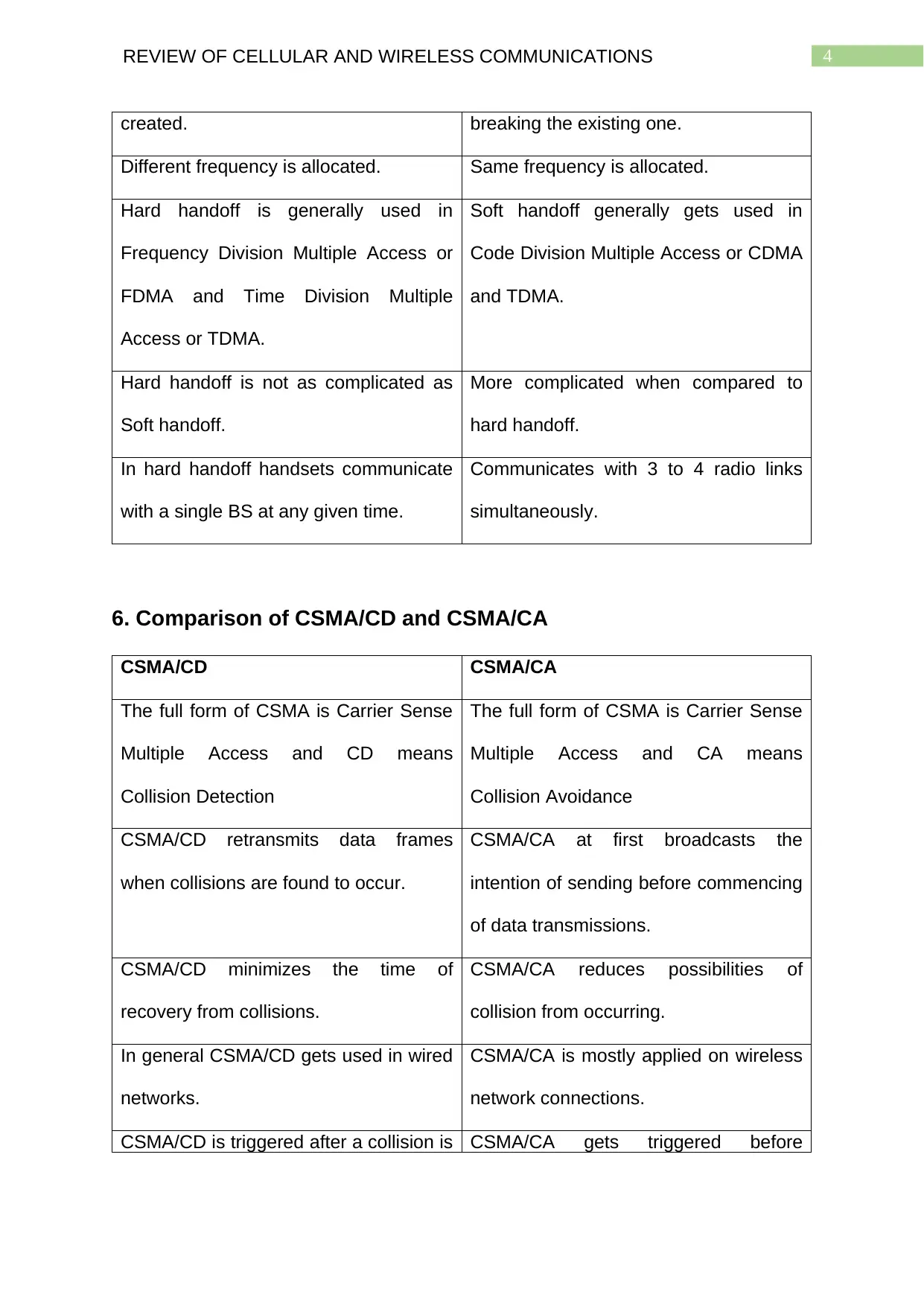
created. breaking the existing one.
Different frequency is allocated. Same frequency is allocated.
Hard handoff is generally used in
Frequency Division Multiple Access or
FDMA and Time Division Multiple
Access or TDMA.
Soft handoff generally gets used in
Code Division Multiple Access or CDMA
and TDMA.
Hard handoff is not as complicated as
Soft handoff.
More complicated when compared to
hard handoff.
In hard handoff handsets communicate
with a single BS at any given time.
Communicates with 3 to 4 radio links
simultaneously.
6. Comparison of CSMA/CD and CSMA/CA
CSMA/CD CSMA/CA
The full form of CSMA is Carrier Sense
Multiple Access and CD means
Collision Detection
The full form of CSMA is Carrier Sense
Multiple Access and CA means
Collision Avoidance
CSMA/CD retransmits data frames
when collisions are found to occur.
CSMA/CA at first broadcasts the
intention of sending before commencing
of data transmissions.
CSMA/CD minimizes the time of
recovery from collisions.
CSMA/CA reduces possibilities of
collision from occurring.
In general CSMA/CD gets used in wired
networks.
CSMA/CA is mostly applied on wireless
network connections.
CSMA/CD is triggered after a collision is CSMA/CA gets triggered before
created. breaking the existing one.
Different frequency is allocated. Same frequency is allocated.
Hard handoff is generally used in
Frequency Division Multiple Access or
FDMA and Time Division Multiple
Access or TDMA.
Soft handoff generally gets used in
Code Division Multiple Access or CDMA
and TDMA.
Hard handoff is not as complicated as
Soft handoff.
More complicated when compared to
hard handoff.
In hard handoff handsets communicate
with a single BS at any given time.
Communicates with 3 to 4 radio links
simultaneously.
6. Comparison of CSMA/CD and CSMA/CA
CSMA/CD CSMA/CA
The full form of CSMA is Carrier Sense
Multiple Access and CD means
Collision Detection
The full form of CSMA is Carrier Sense
Multiple Access and CA means
Collision Avoidance
CSMA/CD retransmits data frames
when collisions are found to occur.
CSMA/CA at first broadcasts the
intention of sending before commencing
of data transmissions.
CSMA/CD minimizes the time of
recovery from collisions.
CSMA/CA reduces possibilities of
collision from occurring.
In general CSMA/CD gets used in wired
networks.
CSMA/CA is mostly applied on wireless
network connections.
CSMA/CD is triggered after a collision is CSMA/CA gets triggered before

5REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
found to have occurred. collisions have taken place.
The mechanism is applied on IEEE
802.3 standard Ethernet network
connections.
The mechanism gets applied on IEEE
802.11 standard Ethernet network
connections.
7. Survey on Wireless Network Security
Security Requirements
In wireless network connections, the information exchange takes place across
authorized users, however this data transfer remains vulnerable to several cyber
security risks based on the nature of broadcasting done by the wireless medium
(Luong, Hoang, Wang, Niyato & Han, 2017). Therefore the wireless network
connections require protection of wireless signal transmission from attacks like DOS
attack, eavesdropping, falsification of data, compromising of nodes to name a few.
As a result, the key security requirements for wireless networks are identified to be
authenticity, confidentiality, integrity as well as availability.
Authenticity: This is about confirmation of the real identity of networking nodes for
distinguishing between authorized and unauthorized users (Zou, Zhu, Wang &
Hanzo, 2016). A couple of communicating nodes in wireless networks first performs
authentication among themselves prior to establishing a communication link to
transmit data. Here the Network Interface Cards (NIC) and Media Access Control
(MAC) are mainly used for the authentication process. However authentication can
also be implemented through the network layer, transport layer and application layer
protocols.
found to have occurred. collisions have taken place.
The mechanism is applied on IEEE
802.3 standard Ethernet network
connections.
The mechanism gets applied on IEEE
802.11 standard Ethernet network
connections.
7. Survey on Wireless Network Security
Security Requirements
In wireless network connections, the information exchange takes place across
authorized users, however this data transfer remains vulnerable to several cyber
security risks based on the nature of broadcasting done by the wireless medium
(Luong, Hoang, Wang, Niyato & Han, 2017). Therefore the wireless network
connections require protection of wireless signal transmission from attacks like DOS
attack, eavesdropping, falsification of data, compromising of nodes to name a few.
As a result, the key security requirements for wireless networks are identified to be
authenticity, confidentiality, integrity as well as availability.
Authenticity: This is about confirmation of the real identity of networking nodes for
distinguishing between authorized and unauthorized users (Zou, Zhu, Wang &
Hanzo, 2016). A couple of communicating nodes in wireless networks first performs
authentication among themselves prior to establishing a communication link to
transmit data. Here the Network Interface Cards (NIC) and Media Access Control
(MAC) are mainly used for the authentication process. However authentication can
also be implemented through the network layer, transport layer and application layer
protocols.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
Confidentiality: Confidentiality is all about limiting access of data to the particular
users and in preventing the information disclosure to the unauthorized ones. An
effective way of implementing confidentiality is by use of symmetric key encryption
where the source node takes the original content (plain text) and encrypts it via
algorithms that involve use of secret keys that get shared with only the required
destination (Yang, Wang, Geraci, Elkashlan, Yuan & Di Renzo, 2015). After this the
encrypted message (cipher text) gets transmitted to that destination which is given
the secret key to extract the cipher text.
Integrity: The information that gets transmitted in wireless networks need to be both
accurate as well as reliable at the same time for the complete duration, it is being
used (Sari & Karay, 2015). That is to say it must be ensured that the information do
not get falsified or tampered with through access by unauthorized users. This
integrity of data is most often violated by the rouge employees giving rise to insider
attacks within the organization (Andrea, Chrysostomou & Hadjichristofi, 2015). In a
more legitimate scenario, a trusted node may violate data integrity by himself being
compromised to the attackers.
Availability: This only implies availability of wireless network services to authorized
users such that the network services can be accessed by these users anywhere
within the range of the wireless network at any point of time (Salameh, Almajali,
Ayyash & Elgala, 2017). The violation of this involves attacks to the wireless network
by means of which DoS (Denial of Service) attacks are caused and thus prevent
authorized users from enjoying network connections.
Confidentiality: Confidentiality is all about limiting access of data to the particular
users and in preventing the information disclosure to the unauthorized ones. An
effective way of implementing confidentiality is by use of symmetric key encryption
where the source node takes the original content (plain text) and encrypts it via
algorithms that involve use of secret keys that get shared with only the required
destination (Yang, Wang, Geraci, Elkashlan, Yuan & Di Renzo, 2015). After this the
encrypted message (cipher text) gets transmitted to that destination which is given
the secret key to extract the cipher text.
Integrity: The information that gets transmitted in wireless networks need to be both
accurate as well as reliable at the same time for the complete duration, it is being
used (Sari & Karay, 2015). That is to say it must be ensured that the information do
not get falsified or tampered with through access by unauthorized users. This
integrity of data is most often violated by the rouge employees giving rise to insider
attacks within the organization (Andrea, Chrysostomou & Hadjichristofi, 2015). In a
more legitimate scenario, a trusted node may violate data integrity by himself being
compromised to the attackers.
Availability: This only implies availability of wireless network services to authorized
users such that the network services can be accessed by these users anywhere
within the range of the wireless network at any point of time (Salameh, Almajali,
Ayyash & Elgala, 2017). The violation of this involves attacks to the wireless network
by means of which DoS (Denial of Service) attacks are caused and thus prevent
authorized users from enjoying network connections.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
Vulnerabilities of Wireless Networks
Like wired network wireless networks also follow OSI standard model of
networking and hence has the same security loopholes and weaknesses in the
physical, network, transport and application layers as the wired networks (Qu &
Chan, 2016). Other than that the major vulnerabilities of wireless networks include
the following:
Default Configuration of WiFi routers: The default configuration which includes
default username and password to access the router page enables attackers in
easily entering the terminal and compromise the network as per his or her wishes.
Rogue Access Point: Wireless access points can easily be installed. This has led to
most of the organizational members attempting to set up authorized access points by
their own without notifying administrators (Aras, Ramachandran, Lawrence &
Hughes, 2017). These access points are mostly not securely managed and therefore
does not consist of mechanisms to determine authorized users from unauthorized
ones.
Wireless Zero Configuration: When computers connect to access points, they
usually save the credentials of logging into the network (Chen, Guo, Shen & Cao,
2017). Because of this, the next time the computer starts, it automatically re-
establishes connection with the network by using the saved credentials (Fatin,
Matos-Abiague, Scharf, & Žutić, 2016). This automatic connection is not
recommended as attackers can get access to the network these computers if they
are already infected.
Vulnerabilities of Wireless Networks
Like wired network wireless networks also follow OSI standard model of
networking and hence has the same security loopholes and weaknesses in the
physical, network, transport and application layers as the wired networks (Qu &
Chan, 2016). Other than that the major vulnerabilities of wireless networks include
the following:
Default Configuration of WiFi routers: The default configuration which includes
default username and password to access the router page enables attackers in
easily entering the terminal and compromise the network as per his or her wishes.
Rogue Access Point: Wireless access points can easily be installed. This has led to
most of the organizational members attempting to set up authorized access points by
their own without notifying administrators (Aras, Ramachandran, Lawrence &
Hughes, 2017). These access points are mostly not securely managed and therefore
does not consist of mechanisms to determine authorized users from unauthorized
ones.
Wireless Zero Configuration: When computers connect to access points, they
usually save the credentials of logging into the network (Chen, Guo, Shen & Cao,
2017). Because of this, the next time the computer starts, it automatically re-
establishes connection with the network by using the saved credentials (Fatin,
Matos-Abiague, Scharf, & Žutić, 2016). This automatic connection is not
recommended as attackers can get access to the network these computers if they
are already infected.

8REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
Security Protocols
There have been several wireless security protocols developed to provide
effective ways of securing wireless networks through appropriate authentication and
encryption techniques (Alblwi & Shujaee, 2017). These wireless security protocols
have been found to be WEP or Wired Equivalent Privacy, WPA or Wi-Fi Protected
Access and WPA2 or Wi-Fi Protected Access version 2.
WEP is the most widely used wireless security protocol (Gali, Amin Babiker &
Mustafa, 2015). The passwords of WEP authentication can be known very easily by
use of Airsnort. It does not even take an entire hour to crack busier access points.
Here higher packet capture make it quicker to crack the password.
WPA refers to an interim security enhancement that was made to WEP when the
802.11i standard of wireless security was still in development (Ren, Chen & Zhang,
2018). Many of the present day WPA implementations make use of a pre-shared key
(PSK) called the WPA Personal along with TKIP or Temporal Key Integrity Protocol
encryption type. WPA Enterprise on the other hand uses authentication servers for
generating keys and certificates.
WPA2 is the most significant enhancement made over the earlier protocols as it
follows the fully developed 802.11i wireless security standard and incorporates AES
or Advanced Encryption Standard as the type of encryption. This security which
comes with AES is strong enough and falls under the approved standard by the US
government for encrypting private and confidential files.
Counter-Measures against Wireless Jamming
Among the numerous security issues, a major one is jamming of wireless
networks (Heo, Kim, Bahk & Paek, 2017). Adversaries equipped with transceivers
Security Protocols
There have been several wireless security protocols developed to provide
effective ways of securing wireless networks through appropriate authentication and
encryption techniques (Alblwi & Shujaee, 2017). These wireless security protocols
have been found to be WEP or Wired Equivalent Privacy, WPA or Wi-Fi Protected
Access and WPA2 or Wi-Fi Protected Access version 2.
WEP is the most widely used wireless security protocol (Gali, Amin Babiker &
Mustafa, 2015). The passwords of WEP authentication can be known very easily by
use of Airsnort. It does not even take an entire hour to crack busier access points.
Here higher packet capture make it quicker to crack the password.
WPA refers to an interim security enhancement that was made to WEP when the
802.11i standard of wireless security was still in development (Ren, Chen & Zhang,
2018). Many of the present day WPA implementations make use of a pre-shared key
(PSK) called the WPA Personal along with TKIP or Temporal Key Integrity Protocol
encryption type. WPA Enterprise on the other hand uses authentication servers for
generating keys and certificates.
WPA2 is the most significant enhancement made over the earlier protocols as it
follows the fully developed 802.11i wireless security standard and incorporates AES
or Advanced Encryption Standard as the type of encryption. This security which
comes with AES is strong enough and falls under the approved standard by the US
government for encrypting private and confidential files.
Counter-Measures against Wireless Jamming
Among the numerous security issues, a major one is jamming of wireless
networks (Heo, Kim, Bahk & Paek, 2017). Adversaries equipped with transceivers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
become easily able to negatively affect that is jam wireless transmissions. Jamming
involves use of intentional radio interferences so that wireless connections get
paralyzed. There are five different kinds of wireless jammers which are constant
jammers, intermittent jammers, reactive jammers, adaptive jammers and intelligent
jammers (Liu, Garnarv and Trappe, 2016). Key counter-measures to prevent
jamming can be the following:
Non-predictable schedules: Transmission instances get randomized and are not
repeated so that jammers cannot predict the time slots for channel activity.
Non-predictable slot size: Sizes of slots are randomly given on packet specific
manner so that jammers cannot estimate the duration of channel activity.
Coordinated and scheduled transmission: The schedule of communication based
on which the nodes transmit is only known to the legitimate neighbours so they turn
the receivers on at these slots. Thus, nodes are not active when no transmission.
Coordinated changes in slot sizes: Here, every node needs to be fully informed
about the present and the future slot sizes. This increasingly becomes more
important as any incompatibility or synchronization error can severely jeopardise the
wireless communication process even between the legitimate nodes.
Collision-free transmission: The wireless communication need to satisfy the
hidden terminal problem such that transmission slots of a certain node never
conflicts with transmission slots of the given nodes within their k-hop interference
ranges.
become easily able to negatively affect that is jam wireless transmissions. Jamming
involves use of intentional radio interferences so that wireless connections get
paralyzed. There are five different kinds of wireless jammers which are constant
jammers, intermittent jammers, reactive jammers, adaptive jammers and intelligent
jammers (Liu, Garnarv and Trappe, 2016). Key counter-measures to prevent
jamming can be the following:
Non-predictable schedules: Transmission instances get randomized and are not
repeated so that jammers cannot predict the time slots for channel activity.
Non-predictable slot size: Sizes of slots are randomly given on packet specific
manner so that jammers cannot estimate the duration of channel activity.
Coordinated and scheduled transmission: The schedule of communication based
on which the nodes transmit is only known to the legitimate neighbours so they turn
the receivers on at these slots. Thus, nodes are not active when no transmission.
Coordinated changes in slot sizes: Here, every node needs to be fully informed
about the present and the future slot sizes. This increasingly becomes more
important as any incompatibility or synchronization error can severely jeopardise the
wireless communication process even between the legitimate nodes.
Collision-free transmission: The wireless communication need to satisfy the
hidden terminal problem such that transmission slots of a certain node never
conflicts with transmission slots of the given nodes within their k-hop interference
ranges.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
References
Alblwi, S., & Shujaee, K. (2017). A Survey on Wireless Security Protocol WPA2.
In Proceedings of the International Conference on Security and Management
(SAM) (pp. 12-17). The Steering Committee of The World Congress in
Computer Science, Computer Engineering and Applied Computing
(WorldComp).
Andrea, I., Chrysostomou, C., & Hadjichristofi, G. (2015, July). Internet of Things:
Security vulnerabilities and challenges. In 2015 IEEE Symposium on
Computers and Communication (ISCC) (pp. 180-187). IEEE.
Andryeyev, O., and Mitschele-Thiel, A. (2017), June. Increasing the cellular network
capacity using self-organized aerial base stations. In Proceedings of the 3rd
Workshop on Micro Aerial Vehicle Networks, Systems, and Applications (pp.
37-42). ACM.
Aras, E., Ramachandran, G. S., Lawrence, P., & Hughes, D. (2017, June). Exploring
the security vulnerabilities of LoRa. In 2017 3rd IEEE International
Conference on Cybernetics (CYBCONF) (pp. 1-6). IEEE.
Bayhan, S., Zheng, L., Chen, J., Di Francesco, M., Kangasharju, J., & Chiang, M.
(2017), May. Improving cellular capacity with white space offloading. In 2017
15th International Symposium on Modeling and Optimization in Mobile, Ad
Hoc, and Wireless Networks (WiOpt) (pp. 1-8). IEEE.
Chen, Y., Guo, M., Shen, J., & Cao, J. (2017). GraphLoc: a graph-based method for
indoor subarea localization with zero-configuration. Personal and Ubiquitous
Computing, 21(3), 489-505.
References
Alblwi, S., & Shujaee, K. (2017). A Survey on Wireless Security Protocol WPA2.
In Proceedings of the International Conference on Security and Management
(SAM) (pp. 12-17). The Steering Committee of The World Congress in
Computer Science, Computer Engineering and Applied Computing
(WorldComp).
Andrea, I., Chrysostomou, C., & Hadjichristofi, G. (2015, July). Internet of Things:
Security vulnerabilities and challenges. In 2015 IEEE Symposium on
Computers and Communication (ISCC) (pp. 180-187). IEEE.
Andryeyev, O., and Mitschele-Thiel, A. (2017), June. Increasing the cellular network
capacity using self-organized aerial base stations. In Proceedings of the 3rd
Workshop on Micro Aerial Vehicle Networks, Systems, and Applications (pp.
37-42). ACM.
Aras, E., Ramachandran, G. S., Lawrence, P., & Hughes, D. (2017, June). Exploring
the security vulnerabilities of LoRa. In 2017 3rd IEEE International
Conference on Cybernetics (CYBCONF) (pp. 1-6). IEEE.
Bayhan, S., Zheng, L., Chen, J., Di Francesco, M., Kangasharju, J., & Chiang, M.
(2017), May. Improving cellular capacity with white space offloading. In 2017
15th International Symposium on Modeling and Optimization in Mobile, Ad
Hoc, and Wireless Networks (WiOpt) (pp. 1-8). IEEE.
Chen, Y., Guo, M., Shen, J., & Cao, J. (2017). GraphLoc: a graph-based method for
indoor subarea localization with zero-configuration. Personal and Ubiquitous
Computing, 21(3), 489-505.

11REVIEW OF CELLULAR AND WIRELESS COMMUNICATIONS
Fatin, G. L., Matos-Abiague, A., Scharf, B., & Žutić, I. (2016). Wireless Majorana
bound states: From magnetic tunability to braiding. Physical review
letters, 117(7), 077002.
Gali, T. A. B., Amin Babiker, A., & Mustafa, N. (2015). A comparative study between
WEP, WPA and WPA2 security algorithms. International Journal of Science
and Research ISSN, 2319-7064.
Heo, J., Kim, J.J., Bahk, S., & Paek, J. (2017), June. Dodge-jam: Anti-jamming
technique for low-power and lossy wireless networks. In 2017 14th Annual
IEEE International Conference on Sensing, Communication, and Networking
(SECON) (pp. 1-9). IEEE.
Liu, Y., Garnarv, A., & Trappe, W. (2016). Connectivity jamming game for physical
layer attack in peer to peer networks. Security and Communication
Networks, 9(18), pp.6080-6093.
Luong, N. C., Hoang, D. T., Wang, P., Niyato, D., & Han, Z. (2017). Applications of
economic and pricing models for wireless network security: A survey. IEEE
Communications Surveys & Tutorials, 19(4), 2735-2767.
Mathew, K., Issac, B., & Eng, T. C. (2015, August). Performance analysis of
RTS/CTS protocol over Basic Access in wireless networks. In 2015 9th
International Conference on IT in Asia (CITA) (pp. 1-6). IEEE.
Qu, Y., & Chan, P. (2016, April). Assessing vulnerabilities in Bluetooth low energy
(BLE) wireless network based IoT systems. In 2016 IEEE 2nd International
Conference on Big Data Security on Cloud (BigDataSecurity), IEEE
International Conference on High Performance and Smart Computing
Fatin, G. L., Matos-Abiague, A., Scharf, B., & Žutić, I. (2016). Wireless Majorana
bound states: From magnetic tunability to braiding. Physical review
letters, 117(7), 077002.
Gali, T. A. B., Amin Babiker, A., & Mustafa, N. (2015). A comparative study between
WEP, WPA and WPA2 security algorithms. International Journal of Science
and Research ISSN, 2319-7064.
Heo, J., Kim, J.J., Bahk, S., & Paek, J. (2017), June. Dodge-jam: Anti-jamming
technique for low-power and lossy wireless networks. In 2017 14th Annual
IEEE International Conference on Sensing, Communication, and Networking
(SECON) (pp. 1-9). IEEE.
Liu, Y., Garnarv, A., & Trappe, W. (2016). Connectivity jamming game for physical
layer attack in peer to peer networks. Security and Communication
Networks, 9(18), pp.6080-6093.
Luong, N. C., Hoang, D. T., Wang, P., Niyato, D., & Han, Z. (2017). Applications of
economic and pricing models for wireless network security: A survey. IEEE
Communications Surveys & Tutorials, 19(4), 2735-2767.
Mathew, K., Issac, B., & Eng, T. C. (2015, August). Performance analysis of
RTS/CTS protocol over Basic Access in wireless networks. In 2015 9th
International Conference on IT in Asia (CITA) (pp. 1-6). IEEE.
Qu, Y., & Chan, P. (2016, April). Assessing vulnerabilities in Bluetooth low energy
(BLE) wireless network based IoT systems. In 2016 IEEE 2nd International
Conference on Big Data Security on Cloud (BigDataSecurity), IEEE
International Conference on High Performance and Smart Computing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

