Risk Assessment for CONVXYZ Organization
VerifiedAdded on 2023/01/23
|12
|2947
|68
AI Summary
This report provides a detailed risk assessment of the organization CONVXYZ, including the identification of threats to primary and secondary assets. It also discusses the vulnerability of each asset and provides a risk register and risk matrix.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: RISK ASSESMENT
RISK ASSESSMENT
Name of the Student
Name of the University
Author Note:
Table of Contents
RISK ASSESSMENT
Name of the Student
Name of the University
Author Note:
Table of Contents
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
Risk Assessment
Introduction:..........................................................................................................................1
Risk Assessment –...............................................................................................................1
Organizational Assets:...................................................................................................1
Threat Identification –........................................................................................................1
Identification of threats from primary assets:......................................................1
Router-.............................................................................................................................1
Authentication Server-...............................................................................................2
Switch-.............................................................................................................................2
Mail Server-....................................................................................................................2
Web Server-...................................................................................................................2
PCs-...................................................................................................................................2
Identification of threats from secondary assets:.................................................3
Operating System (Windows)-................................................................................3
Website-..........................................................................................................................3
Database-.......................................................................................................................3
Firewall-...........................................................................................................................3
Vulnerability of the Assets:..............................................................................................3
Risk Register:........................................................................................................................5
Risk Matrix:............................................................................................................................6
Conclusion:.............................................................................................................................6
Risk Assessment
Introduction:..........................................................................................................................1
Risk Assessment –...............................................................................................................1
Organizational Assets:...................................................................................................1
Threat Identification –........................................................................................................1
Identification of threats from primary assets:......................................................1
Router-.............................................................................................................................1
Authentication Server-...............................................................................................2
Switch-.............................................................................................................................2
Mail Server-....................................................................................................................2
Web Server-...................................................................................................................2
PCs-...................................................................................................................................2
Identification of threats from secondary assets:.................................................3
Operating System (Windows)-................................................................................3
Website-..........................................................................................................................3
Database-.......................................................................................................................3
Firewall-...........................................................................................................................3
Vulnerability of the Assets:..............................................................................................3
Risk Register:........................................................................................................................5
Risk Matrix:............................................................................................................................6
Conclusion:.............................................................................................................................6

2
Risk Assessment
Introduction:
The fundamental objective of this report is to elaborate the risk
assessment of the organization CONVXYZ. In order to identify the hazards and
threats of the mentioned organization this paper has utilized the what-if
technique for risk assessment. The purpose to utilize the what-if technique for
the assessment process in order to improve the decision making approach as it
has better scope to analyse the requirements as well as the business operation it
provides effective decision making results. Followed by this report it has also
covered a detail specification of primary and secondary assets, owner
specification along with that is has also included the identification of the
vulnerability and threats for each assets, computation level of likelihood. Apart
from the above aspects it has also covered the impact of the likelihood
computation on the risk assessment as well as it a detail elaboration of the risk
identification by utilizing the features of risk matrix which is also present in the
report. Finally, this paper will conclude with an appropriate conclusion by which it
will effectively mention its findings and it will also consist a recommendation for
the board of director which will help to reduce the business risks.
Risk Assessment –
Organizational Assets:
After successfully analysing the organizational aspects as well as followed
by several studies based on the organizational assets, it has classified the
organizational assets into two parts which includes the Primary Assets and
Secondary Assets. A primary asset of any organizations stands to represent any
important information or any services of the organization. Along with that a
secondary assets stands to represent the services of information which supports
the primary assets in between the organization. After investigating the
organizational assets it has been noticed that the organization CONVXYZ has the
primary assets which includes the Router, Authentication server, Switch, Mail
server, Web server and PCs. Followed by these primary assets the secondary
assets of this organization includes the operating systems (Windows), employ,
website, customer’s as well as database of asset, firewall to protect the server,
VPN, IP address and the organizational information. While discussing about the
primary and secondary assets of the organization, studies has revealed that the
primary assets are one of the most essential property or features of any
organization which invokes to import the other assets like secondary elements or
other elements into the business structure. The purpose behind the selection of
the above primary assets is the features of those hardware and servers which
will surely help the organization to incorporate several beneficial features into
the services of the organization. Apart from that the incorporation of secondary
assets has the purpose to support the features of the primary assets in order to
enhance their services. In order to support the above statement the selection of
the assets in this organization needs to be focused as it shows that the primary
asset PC will not work without the support of the secondary asset windows
operating system. Similarly the web servers are useless without the application
of website. Thus, from the above discussion it can be state that in between the
Risk Assessment
Introduction:
The fundamental objective of this report is to elaborate the risk
assessment of the organization CONVXYZ. In order to identify the hazards and
threats of the mentioned organization this paper has utilized the what-if
technique for risk assessment. The purpose to utilize the what-if technique for
the assessment process in order to improve the decision making approach as it
has better scope to analyse the requirements as well as the business operation it
provides effective decision making results. Followed by this report it has also
covered a detail specification of primary and secondary assets, owner
specification along with that is has also included the identification of the
vulnerability and threats for each assets, computation level of likelihood. Apart
from the above aspects it has also covered the impact of the likelihood
computation on the risk assessment as well as it a detail elaboration of the risk
identification by utilizing the features of risk matrix which is also present in the
report. Finally, this paper will conclude with an appropriate conclusion by which it
will effectively mention its findings and it will also consist a recommendation for
the board of director which will help to reduce the business risks.
Risk Assessment –
Organizational Assets:
After successfully analysing the organizational aspects as well as followed
by several studies based on the organizational assets, it has classified the
organizational assets into two parts which includes the Primary Assets and
Secondary Assets. A primary asset of any organizations stands to represent any
important information or any services of the organization. Along with that a
secondary assets stands to represent the services of information which supports
the primary assets in between the organization. After investigating the
organizational assets it has been noticed that the organization CONVXYZ has the
primary assets which includes the Router, Authentication server, Switch, Mail
server, Web server and PCs. Followed by these primary assets the secondary
assets of this organization includes the operating systems (Windows), employ,
website, customer’s as well as database of asset, firewall to protect the server,
VPN, IP address and the organizational information. While discussing about the
primary and secondary assets of the organization, studies has revealed that the
primary assets are one of the most essential property or features of any
organization which invokes to import the other assets like secondary elements or
other elements into the business structure. The purpose behind the selection of
the above primary assets is the features of those hardware and servers which
will surely help the organization to incorporate several beneficial features into
the services of the organization. Apart from that the incorporation of secondary
assets has the purpose to support the features of the primary assets in order to
enhance their services. In order to support the above statement the selection of
the assets in this organization needs to be focused as it shows that the primary
asset PC will not work without the support of the secondary asset windows
operating system. Similarly the web servers are useless without the application
of website. Thus, from the above discussion it can be state that in between the

3
Risk Assessment
organization CONVXYZ, all of the primary and secondary assets has a significant
purpose to enhance the business effectiveness by improving their services (Chen
et al., 2013).
Threat Identification –
Identification of threats from primary assets:
Router-
Threats present in the operations of router includes the aspects of
unauthorised access, password hacking, session hijacking, masquerading as well
as the threat of death attack. Along with these attacks the possibility to get the
threat from the router protocol attack and replay attack cannot be ignored. Due
to the above mentioned attacks the operations and working of the router can be
hampered for significant time or it might destroyed forever (Salas et al., 2014).
Authentication Server-
Threat present in the applications of the Authentication servers refers to
such types of attacks by which it can get access of the organizational activities
from an unauthorised user. From the analysis of the previous records it has been
noticed that the hackers initiated this attack by the phishing technique as well as
it opt to inject malicious programs in order to get the access. As the
authentication server opt to provide access to only the authorised server the
above mentioned threat has been introduced to penetrate the service of
Authentication server (Kiravuo et al., 2013).
Switch-
The main purpose of switch is to connect two or more network devices. In
other words switch is a bridge by which network devices are interconnected.
However, there are several advantage of switch there still some threats present
in the application of switch which includes the attacks of CDP manipulation which
enables the user to analyse the information of the organization in order to
perform illegal operations by the help of those information (Fonseca et al., 2014).
Mail Server-
Fundamental objective of the utilization of mail server is to provide
effective communication process to the organization by which the organization
can send or receive information from the stakeholders vie network. Thus, in
order to get access of the organizational information hackers are opt to hack the
mail server by utilizing the phishing virus which can the unauthorised access of
the organizational data. As weak authentication server can cause a damage in
the organizational security. Along with the attack of phishing the possibility of
getting hacked by the utilization of DoS attack, data leakage also cannot be
ignored (Nostro et al., 2014).
Web Server-
Apart from the above threats of the assets one of the most significant
threat present in the services of web server in the organizational field as in the
features of web server it has incorporated the organizational database,
Risk Assessment
organization CONVXYZ, all of the primary and secondary assets has a significant
purpose to enhance the business effectiveness by improving their services (Chen
et al., 2013).
Threat Identification –
Identification of threats from primary assets:
Router-
Threats present in the operations of router includes the aspects of
unauthorised access, password hacking, session hijacking, masquerading as well
as the threat of death attack. Along with these attacks the possibility to get the
threat from the router protocol attack and replay attack cannot be ignored. Due
to the above mentioned attacks the operations and working of the router can be
hampered for significant time or it might destroyed forever (Salas et al., 2014).
Authentication Server-
Threat present in the applications of the Authentication servers refers to
such types of attacks by which it can get access of the organizational activities
from an unauthorised user. From the analysis of the previous records it has been
noticed that the hackers initiated this attack by the phishing technique as well as
it opt to inject malicious programs in order to get the access. As the
authentication server opt to provide access to only the authorised server the
above mentioned threat has been introduced to penetrate the service of
Authentication server (Kiravuo et al., 2013).
Switch-
The main purpose of switch is to connect two or more network devices. In
other words switch is a bridge by which network devices are interconnected.
However, there are several advantage of switch there still some threats present
in the application of switch which includes the attacks of CDP manipulation which
enables the user to analyse the information of the organization in order to
perform illegal operations by the help of those information (Fonseca et al., 2014).
Mail Server-
Fundamental objective of the utilization of mail server is to provide
effective communication process to the organization by which the organization
can send or receive information from the stakeholders vie network. Thus, in
order to get access of the organizational information hackers are opt to hack the
mail server by utilizing the phishing virus which can the unauthorised access of
the organizational data. As weak authentication server can cause a damage in
the organizational security. Along with the attack of phishing the possibility of
getting hacked by the utilization of DoS attack, data leakage also cannot be
ignored (Nostro et al., 2014).
Web Server-
Apart from the above threats of the assets one of the most significant
threat present in the services of web server in the organizational field as in the
features of web server it has incorporated the organizational database,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
Risk Assessment
applications, networks connection as well as the operating system. Thus, by
attacking the web server can have a significant effect on the organizational
security. In order to hack or infect the web servers the cyber criminals opt for
DoS attacks, data leakage as well as the phishing attacks. However, followed by
the studies there also significant impact of website defacement, misconfiguration
as well as directory traversal is present in the organizational security (Taylor et
al., 2014).
PCs-
In order to fetch the organizational data or permanently delete the
organizational data one of the most utilized method used by the hacker to attack
the PCs and computer systems. Followed by the above purpose the cyber
criminals utilizes the method of internet worm, browser hijacker, rootkit, email
virus as well as it manipulated the employees of the organization to destroy or
block the targeted data of the respective organization which may have
significant effect on the organizational security and reputation (Skrzewski et al.,
2014).
Identification of threats from secondary assets:
Operating System (Windows)-
While analysing the threat factors of the operating system it has been
observed that due to the utilization of phishing and virus the operating systems
of an organization can be hacked. The purpose of the attacker to opt for
operating system hacking is to block the systems of the organization which may
cause a significant impact on the organizational performance, productivity as
well as the performance (Rathore et al., 2017).
Website-
Along with the above the threat one of the major threat present in the
services of website have a significant impact on the organizational services. By
utilizing the DoS attacks, phishing as well as the ransomware are very impactful
in order to harm the services of a website (Puthal et al., 2016).
Database-
Followed by the analysis related to the identification of the organizational
assets one of the most significant secondary asset in the application of database
which keep the records of the information which includes the data related to the
employ as well as the company services. Thus, by attacking the database of an
organization can cause a huge impact on the services of the respective
organization. The purpose of this attacks is to temporarily or permanently block
the organizational database by the database injection attack, malware attack as
well as vulnerable database manipulation (Puthal et al., 2016).
Firewall-
As the fundamental objective of this asset is to protect the organizational
networks from the external risk factors. Thus, from the analysis of the studies
related to the services of firewall it has been observed that the application of
DDoS and deep packet inspection can effectively harm the services of firewall
(Puthal et al., 2017).
Risk Assessment
applications, networks connection as well as the operating system. Thus, by
attacking the web server can have a significant effect on the organizational
security. In order to hack or infect the web servers the cyber criminals opt for
DoS attacks, data leakage as well as the phishing attacks. However, followed by
the studies there also significant impact of website defacement, misconfiguration
as well as directory traversal is present in the organizational security (Taylor et
al., 2014).
PCs-
In order to fetch the organizational data or permanently delete the
organizational data one of the most utilized method used by the hacker to attack
the PCs and computer systems. Followed by the above purpose the cyber
criminals utilizes the method of internet worm, browser hijacker, rootkit, email
virus as well as it manipulated the employees of the organization to destroy or
block the targeted data of the respective organization which may have
significant effect on the organizational security and reputation (Skrzewski et al.,
2014).
Identification of threats from secondary assets:
Operating System (Windows)-
While analysing the threat factors of the operating system it has been
observed that due to the utilization of phishing and virus the operating systems
of an organization can be hacked. The purpose of the attacker to opt for
operating system hacking is to block the systems of the organization which may
cause a significant impact on the organizational performance, productivity as
well as the performance (Rathore et al., 2017).
Website-
Along with the above the threat one of the major threat present in the
services of website have a significant impact on the organizational services. By
utilizing the DoS attacks, phishing as well as the ransomware are very impactful
in order to harm the services of a website (Puthal et al., 2016).
Database-
Followed by the analysis related to the identification of the organizational
assets one of the most significant secondary asset in the application of database
which keep the records of the information which includes the data related to the
employ as well as the company services. Thus, by attacking the database of an
organization can cause a huge impact on the services of the respective
organization. The purpose of this attacks is to temporarily or permanently block
the organizational database by the database injection attack, malware attack as
well as vulnerable database manipulation (Puthal et al., 2016).
Firewall-
As the fundamental objective of this asset is to protect the organizational
networks from the external risk factors. Thus, from the analysis of the studies
related to the services of firewall it has been observed that the application of
DDoS and deep packet inspection can effectively harm the services of firewall
(Puthal et al., 2017).
5
Risk Assessment
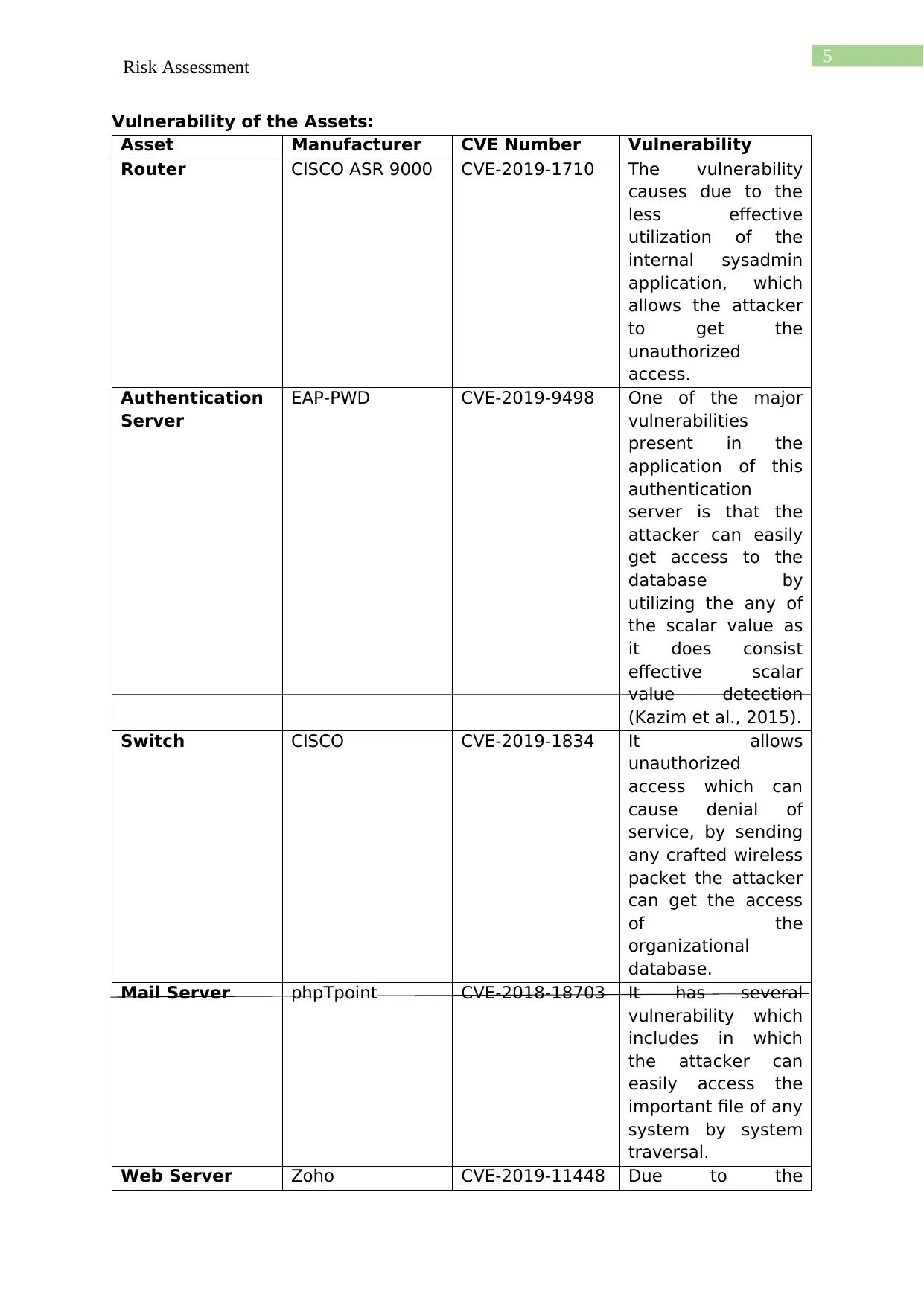
Vulnerability of the Assets:
Asset Manufacturer CVE Number Vulnerability
Router CISCO ASR 9000 CVE-2019-1710 The vulnerability
causes due to the
less effective
utilization of the
internal sysadmin
application, which
allows the attacker
to get the
unauthorized
access.
Authentication
Server
EAP-PWD CVE-2019-9498 One of the major
vulnerabilities
present in the
application of this
authentication
server is that the
attacker can easily
get access to the
database by
utilizing the any of
the scalar value as
it does consist
effective scalar
value detection
(Kazim et al., 2015).
Switch CISCO CVE-2019-1834 It allows
unauthorized
access which can
cause denial of
service, by sending
any crafted wireless
packet the attacker
can get the access
of the
organizational
database.
Mail Server phpTpoint CVE-2018-18703 It has several
vulnerability which
includes in which
the attacker can
easily access the
important file of any
system by system
traversal.
Web Server Zoho CVE-2019-11448 Due to the
Risk Assessment
Vulnerability of the Assets:
Asset Manufacturer CVE Number Vulnerability
Router CISCO ASR 9000 CVE-2019-1710 The vulnerability
causes due to the
less effective
utilization of the
internal sysadmin
application, which
allows the attacker
to get the
unauthorized
access.
Authentication
Server
EAP-PWD CVE-2019-9498 One of the major
vulnerabilities
present in the
application of this
authentication
server is that the
attacker can easily
get access to the
database by
utilizing the any of
the scalar value as
it does consist
effective scalar
value detection
(Kazim et al., 2015).
Switch CISCO CVE-2019-1834 It allows
unauthorized
access which can
cause denial of
service, by sending
any crafted wireless
packet the attacker
can get the access
of the
organizational
database.
Mail Server phpTpoint CVE-2018-18703 It has several
vulnerability which
includes in which
the attacker can
easily access the
important file of any
system by system
traversal.
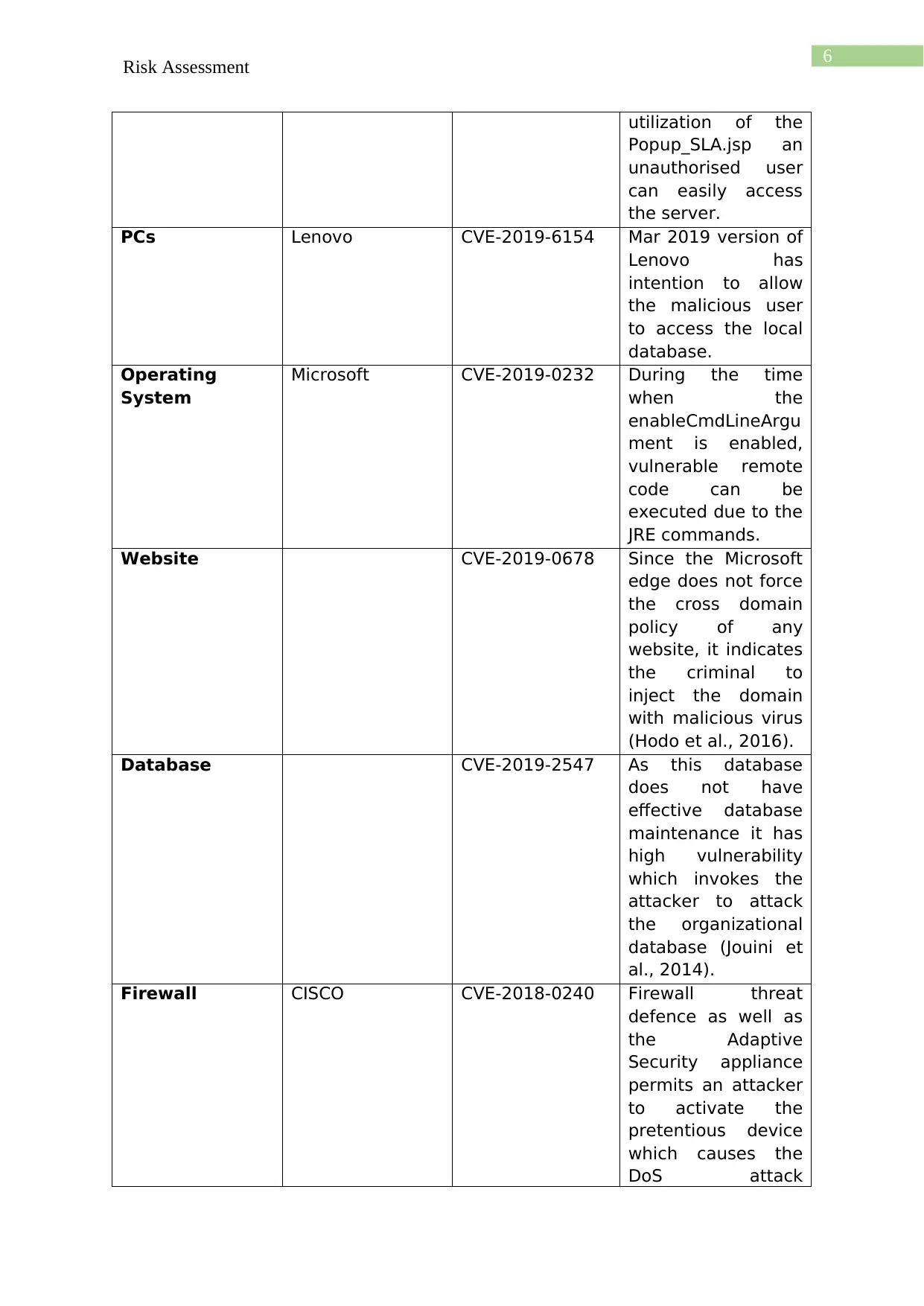
Web Server Zoho CVE-2019-11448 Due to the
6
Risk Assessment
utilization of the
Popup_SLA.jsp an
unauthorised user
can easily access
the server.
PCs Lenovo CVE-2019-6154 Mar 2019 version of
Lenovo has
intention to allow
the malicious user
to access the local
database.
Operating
System
Microsoft CVE-2019-0232 During the time
when the
enableCmdLineArgu
ment is enabled,
vulnerable remote
code can be
executed due to the
JRE commands.
Website CVE-2019-0678 Since the Microsoft
edge does not force
the cross domain
policy of any
website, it indicates
the criminal to
inject the domain
with malicious virus
(Hodo et al., 2016).
Database CVE-2019-2547 As this database
does not have
effective database
maintenance it has
high vulnerability
which invokes the
attacker to attack
the organizational
database (Jouini et
al., 2014).
Firewall CISCO CVE-2018-0240 Firewall threat
defence as well as
the Adaptive
Security appliance
permits an attacker
to activate the
pretentious device
which causes the
DoS attack
Risk Assessment
utilization of the
Popup_SLA.jsp an
unauthorised user
can easily access
the server.
PCs Lenovo CVE-2019-6154 Mar 2019 version of
Lenovo has
intention to allow
the malicious user
to access the local
database.
Operating
System
Microsoft CVE-2019-0232 During the time
when the
enableCmdLineArgu
ment is enabled,
vulnerable remote
code can be
executed due to the
JRE commands.
Website CVE-2019-0678 Since the Microsoft
edge does not force
the cross domain
policy of any
website, it indicates
the criminal to
inject the domain
with malicious virus
(Hodo et al., 2016).
Database CVE-2019-2547 As this database
does not have
effective database
maintenance it has
high vulnerability
which invokes the
attacker to attack
the organizational
database (Jouini et
al., 2014).
Firewall CISCO CVE-2018-0240 Firewall threat
defence as well as
the Adaptive
Security appliance
permits an attacker
to activate the
pretentious device
which causes the
DoS attack
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
Risk Assessment
(Kuusijärvi et al.,
2016).
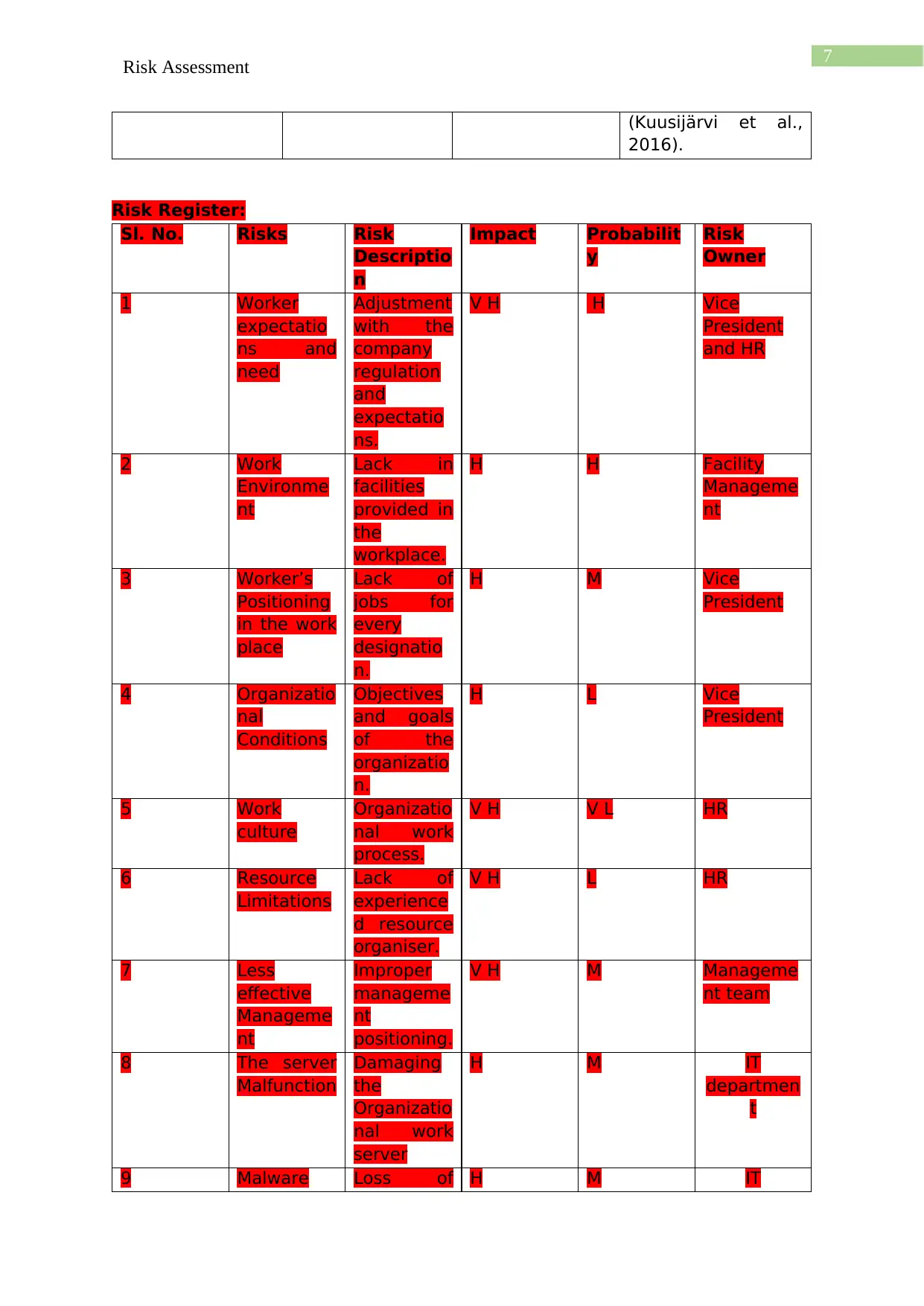
Risk Register:
Sl. No. Risks Risk
Descriptio
n
Impact Probabilit
y
Risk
Owner
1 Worker
expectatio
ns and
need
Adjustment
with the
company
regulation
and
expectatio
ns.
V H H Vice
President
and HR
2 Work
Environme
nt
Lack in
facilities
provided in
the
workplace.
H H Facility
Manageme
nt
3 Worker’s
Positioning
in the work
place
Lack of
jobs for
every
designatio
n.
H M Vice
President
4 Organizatio
nal
Conditions
Objectives
and goals
of the
organizatio
n.
H L Vice
President
5 Work
culture
Organizatio
nal work
process.
V H V L HR
6 Resource
Limitations
Lack of
experience
d resource
organiser.
V H L HR
7 Less
effective
Manageme
nt
Improper
manageme
nt
positioning.
V H M Manageme
nt team
8 The server
Malfunction
Damaging
the
Organizatio
nal work
server
H M IT
departmen
t
9 Malware Loss of H M IT
Risk Assessment
(Kuusijärvi et al.,
2016).
Risk Register:
Sl. No. Risks Risk
Descriptio
n
Impact Probabilit
y
Risk
Owner
1 Worker
expectatio
ns and
need
Adjustment
with the
company
regulation
and
expectatio
ns.
V H H Vice
President
and HR
2 Work
Environme
nt
Lack in
facilities
provided in
the
workplace.
H H Facility
Manageme
nt
3 Worker’s
Positioning
in the work
place
Lack of
jobs for
every
designatio
n.
H M Vice
President
4 Organizatio
nal
Conditions
Objectives
and goals
of the
organizatio
n.
H L Vice
President
5 Work
culture
Organizatio
nal work
process.
V H V L HR
6 Resource
Limitations
Lack of
experience
d resource
organiser.
V H L HR
7 Less
effective
Manageme
nt
Improper
manageme
nt
positioning.
V H M Manageme
nt team
8 The server
Malfunction
Damaging
the
Organizatio
nal work
server
H M IT
departmen
t
9 Malware Loss of H M IT
8
Risk Assessment
Attack database
and
attacks of
the cyber-
criminal.
departmen
t
10 Less
effective
resources
manageme
nt
Improper
resource
manageme
nt.
L VL Resource
managing
departmen
t
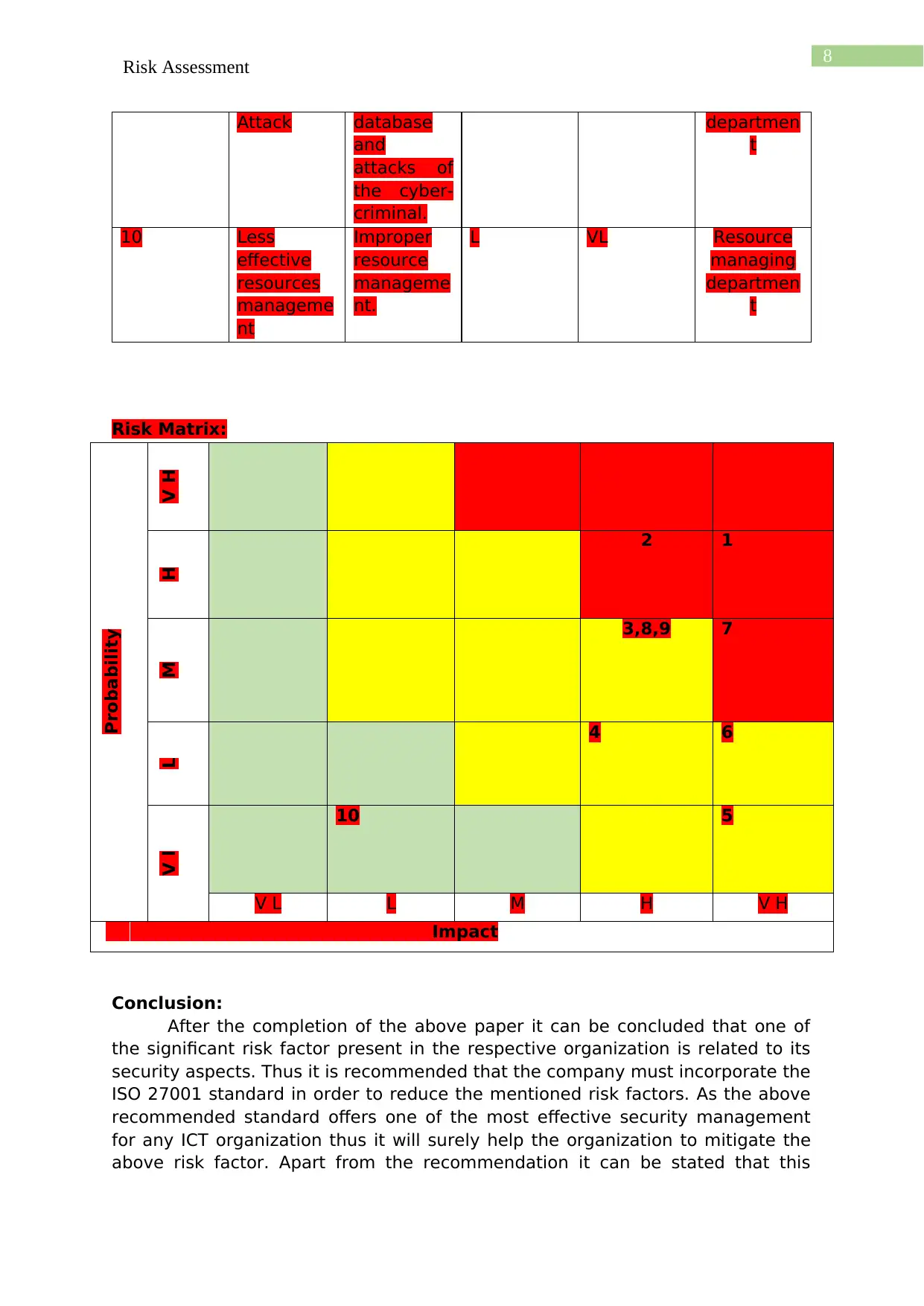
Risk Matrix:
Probability
V HH
2 1
M
3,8,9 7
L
4 6
V l
10 5
V L L M H V H
Impact
Conclusion:
After the completion of the above paper it can be concluded that one of
the significant risk factor present in the respective organization is related to its
security aspects. Thus it is recommended that the company must incorporate the
ISO 27001 standard in order to reduce the mentioned risk factors. As the above
recommended standard offers one of the most effective security management
for any ICT organization thus it will surely help the organization to mitigate the
above risk factor. Apart from the recommendation it can be stated that this
Risk Assessment
Attack database
and
attacks of
the cyber-
criminal.
departmen
t
10 Less
effective
resources
manageme
nt
Improper
resource
manageme
nt.
L VL Resource
managing
departmen
t
Risk Matrix:
Probability
V HH
2 1
M
3,8,9 7
L
4 6
V l
10 5
V L L M H V H
Impact
Conclusion:
After the completion of the above paper it can be concluded that one of
the significant risk factor present in the respective organization is related to its
security aspects. Thus it is recommended that the company must incorporate the
ISO 27001 standard in order to reduce the mentioned risk factors. As the above
recommended standard offers one of the most effective security management
for any ICT organization thus it will surely help the organization to mitigate the
above risk factor. Apart from the recommendation it can be stated that this

9
Risk Assessment
report has successfully identified the organizational assets as well as it has
identified the threat and vulnerability present in the organizational assets. Thus,
followed by the above aspects it can be stated that based on the above analysis
and effective implementation of the mentioned recommendation the
organization can effectively mitigate its risk factors.
Risk Assessment
report has successfully identified the organizational assets as well as it has
identified the threat and vulnerability present in the organizational assets. Thus,
followed by the above aspects it can be stated that based on the above analysis
and effective implementation of the mentioned recommendation the
organization can effectively mitigate its risk factors.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
Risk Assessment
Reference:
Hodo, E., Bellekens, X., Hamilton, A., Dubouilh, P.L., Iorkyase, E., Tachtatzis, C.
and Atkinson, R., 2016, May. Threat analysis of IoT networks using artificial
neural network intrusion detection system. In 2016 International Symposium on
Networks, Computers and Communications (ISNCC) (pp. 1-6). IEEE.
Jouini, M., Rabai, L.B.A. and Aissa, A.B., 2014. Classification of security threats in
information systems. Procedia Computer Science, 32, pp.489-496.
Kazim, M. and Zhu, S.Y., 2015. A survey on top security threats in cloud
computing.
Kuusijärvi, J., Savola, R., Savolainen, P. and Evesti, A., 2016, December.
Mitigating IoT security threats with a trusted Network element. In 2016 11th
International Conference for Internet Technology and Secured Transactions
(ICITST) (pp. 260-265). IEEE.
Puthal, D., Mohanty, S.P., Nanda, P. and Choppali, U., 2017. Building security
perimeters to protect network systems against cyber threats [future
directions]. IEEE Consumer Electronics Magazine, 6(4), pp.24-27.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2016. Threats to networking cloud
and edge datacenters in the Internet of Things. IEEE Cloud Computing, 3(3),
pp.64-71.
Rathore, S., Sharma, P.K., Loia, V., Jeong, Y.S. and Park, J.H., 2017. Social
network security: Issues, challenges, threats, and solutions. Information
sciences, 421, pp.43-69.
Skrzewski, M., 2014, June. System network activity monitoring for malware
threats detection. In International Conference on Computer Networks (pp. 138-
146). Springer, Cham.
Risk Assessment
Reference:
Hodo, E., Bellekens, X., Hamilton, A., Dubouilh, P.L., Iorkyase, E., Tachtatzis, C.
and Atkinson, R., 2016, May. Threat analysis of IoT networks using artificial
neural network intrusion detection system. In 2016 International Symposium on
Networks, Computers and Communications (ISNCC) (pp. 1-6). IEEE.
Jouini, M., Rabai, L.B.A. and Aissa, A.B., 2014. Classification of security threats in
information systems. Procedia Computer Science, 32, pp.489-496.
Kazim, M. and Zhu, S.Y., 2015. A survey on top security threats in cloud
computing.
Kuusijärvi, J., Savola, R., Savolainen, P. and Evesti, A., 2016, December.
Mitigating IoT security threats with a trusted Network element. In 2016 11th
International Conference for Internet Technology and Secured Transactions
(ICITST) (pp. 260-265). IEEE.
Puthal, D., Mohanty, S.P., Nanda, P. and Choppali, U., 2017. Building security
perimeters to protect network systems against cyber threats [future
directions]. IEEE Consumer Electronics Magazine, 6(4), pp.24-27.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2016. Threats to networking cloud
and edge datacenters in the Internet of Things. IEEE Cloud Computing, 3(3),
pp.64-71.
Rathore, S., Sharma, P.K., Loia, V., Jeong, Y.S. and Park, J.H., 2017. Social
network security: Issues, challenges, threats, and solutions. Information
sciences, 421, pp.43-69.
Skrzewski, M., 2014, June. System network activity monitoring for malware
threats detection. In International Conference on Computer Networks (pp. 138-
146). Springer, Cham.

11
Risk Assessment
Taylor, R.W., Fritsch, E.J. and Liederbach, J., 2014. Digital crime and digital
terrorism. Prentice Hall Press.
Nostro, N., Ceccarelli, A., Bondavalli, A. and Brancati, F., 2014. Insider threat
assessment: A model-based methodology. ACM SIGOPS Operating Systems
Review, 48(2), pp.3-12.
Amoozadeh, M., Raghuramu, A., Chuah, C.N., Ghosal, D., Zhang, H.M., Rowe, J.
and Levitt, K., 2015. Security vulnerabilities of connected vehicle streams and
their impact on cooperative driving. IEEE Communications Magazine, 53(6),
pp.126-132.
Fonseca, J., Vieira, M. and Madeira, H., 2014. Evaluation of web security
mechanisms using vulnerability & attack injection. IEEE Transactions on
dependable and secure computing, 11(5), pp.440-453.
Kiravuo, T., Sarela, M. and Manner, J., 2013. A survey of Ethernet LAN
security. IEEE Communications Surveys & Tutorials, 15(3), pp.1477-1491.
Salas, M.I.P. and Martins, E., 2014. Security testing methodology for
vulnerabilities detection of xss in web services and ws-security. Electronic Notes
in Theoretical Computer Science, 302, pp.133-154.
Young, F., CONTROLSCAN Inc, 2013. Web application vulnerability scanner. U.S.
Patent 8,365,290.
Chen, Y., Boehm, B.W. and Sheppard, L., University of Southern California (USC),
2013. Value-adaptive security threat modeling and vulnerability ranking. U.S.
Patent 8,392,997.
Risk Assessment
Taylor, R.W., Fritsch, E.J. and Liederbach, J., 2014. Digital crime and digital
terrorism. Prentice Hall Press.
Nostro, N., Ceccarelli, A., Bondavalli, A. and Brancati, F., 2014. Insider threat
assessment: A model-based methodology. ACM SIGOPS Operating Systems
Review, 48(2), pp.3-12.
Amoozadeh, M., Raghuramu, A., Chuah, C.N., Ghosal, D., Zhang, H.M., Rowe, J.
and Levitt, K., 2015. Security vulnerabilities of connected vehicle streams and
their impact on cooperative driving. IEEE Communications Magazine, 53(6),
pp.126-132.
Fonseca, J., Vieira, M. and Madeira, H., 2014. Evaluation of web security
mechanisms using vulnerability & attack injection. IEEE Transactions on
dependable and secure computing, 11(5), pp.440-453.
Kiravuo, T., Sarela, M. and Manner, J., 2013. A survey of Ethernet LAN
security. IEEE Communications Surveys & Tutorials, 15(3), pp.1477-1491.
Salas, M.I.P. and Martins, E., 2014. Security testing methodology for
vulnerabilities detection of xss in web services and ws-security. Electronic Notes
in Theoretical Computer Science, 302, pp.133-154.
Young, F., CONTROLSCAN Inc, 2013. Web application vulnerability scanner. U.S.
Patent 8,365,290.
Chen, Y., Boehm, B.W. and Sheppard, L., University of Southern California (USC),
2013. Value-adaptive security threat modeling and vulnerability ranking. U.S.
Patent 8,392,997.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





