Cloud Security Risk Assessment for Gigantic Corporation Project
VerifiedAdded on 2023/06/03
|17
|4312
|340
Report
AI Summary
This report provides a comprehensive risk assessment of cloud security for Gigantic Corporation, focusing on Distributed Denial-of-Service (DDOS) attacks and other potential threats. It explores different cloud deployment models (public, private, and hybrid) and service models (SaaS, PaaS, IaaS), highlighting the vulnerabilities associated with each. The report details various types of DDOS attacks, including bandwidth depletion and resource depletion attacks, and discusses mitigation techniques such as resource scaling, victim migration, and network-level controls. The analysis emphasizes the importance of data protection and security measures in cloud environments, particularly in the context of pay-as-you-go models, and suggests strategies for enhancing cloud service security to safeguard organizational and customer data. Desklib offers similar solved assignments and past papers for students.

Running head: RISK ASSESSMENT IN CLOUD
Risk Assessment in Cloud
Name of the student
Name of the university
Author note
Risk Assessment in Cloud
Name of the student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK ASSESSMENT IN CLOUD
Table of Contents
Introduction....................................................................................................................2
Risk assessment:.............................................................................................................5
Threats........................................................................................................................5
Bandwidth depletion attacks:.................................................................................5
Literature review:...........................................................................................................9
Conclusion....................................................................................................................10
Table of Contents
Introduction....................................................................................................................2
Risk assessment:.............................................................................................................5
Threats........................................................................................................................5
Bandwidth depletion attacks:.................................................................................5
Literature review:...........................................................................................................9
Conclusion....................................................................................................................10

2RISK ASSESSMENT IN CLOUD
Introduction
The cloud computing can be explained as servers hosted in the internet, that can be
accessed by customers. It can be said that in the recent times the use of the cloud servers have
increased a lot. There have been a number of organisations that have been using the cloud
servers for the benefit of the public. The use of the cloud computing enhances the
organisations working and reduces the chances of any risk associated with server problems
(Ahmed & Hossain, 2014). In the Gigantic the use of the cloud can help the organisations
many of the ways. Some of the major benefits of the cloud servers are explained in the
paper.
The cloud holds majority of the application that can be used by the orgasaition in the
online platform. One of the major application that is very common in the present times in the
use of the ERP or the enterprise resource planning software.
The cloud architecture can be sub divided in three different segments, namely the public
cloud, private cloud and the hybrid cloud.
Public cloud: The public clouds are the systems that are operated by the third parties.
It provides the customers with option of the pay as you go option. All the customers
in this system use the same infrastructure as provided by the orgasaition that is
hosting the cloud server (Chen et al., 2013). One of the major benefit of using the
public cloud is the fact that it haves large sum of memory on demand. There are
several major disadvantage also in this system. One of the major disadvantage is the
fact that the security of each of the servers is very poor (Choi et al., 2013). As many
organisation uses the same infrastructure for the process hence the security
automatically reduces.one of the major example of this the Google Cloud servers.
Introduction
The cloud computing can be explained as servers hosted in the internet, that can be
accessed by customers. It can be said that in the recent times the use of the cloud servers have
increased a lot. There have been a number of organisations that have been using the cloud
servers for the benefit of the public. The use of the cloud computing enhances the
organisations working and reduces the chances of any risk associated with server problems
(Ahmed & Hossain, 2014). In the Gigantic the use of the cloud can help the organisations
many of the ways. Some of the major benefits of the cloud servers are explained in the
paper.
The cloud holds majority of the application that can be used by the orgasaition in the
online platform. One of the major application that is very common in the present times in the
use of the ERP or the enterprise resource planning software.
The cloud architecture can be sub divided in three different segments, namely the public
cloud, private cloud and the hybrid cloud.
Public cloud: The public clouds are the systems that are operated by the third parties.
It provides the customers with option of the pay as you go option. All the customers
in this system use the same infrastructure as provided by the orgasaition that is
hosting the cloud server (Chen et al., 2013). One of the major benefit of using the
public cloud is the fact that it haves large sum of memory on demand. There are
several major disadvantage also in this system. One of the major disadvantage is the
fact that the security of each of the servers is very poor (Choi et al., 2013). As many
organisation uses the same infrastructure for the process hence the security
automatically reduces.one of the major example of this the Google Cloud servers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISK ASSESSMENT IN CLOUD
Private cloud: The private cloud servers are used by a single enterprise for
organisational use. These servers are hosted only for a specific organisation and the
cloud can only be accessed through system of the organisation. The private cloud can
be sub divided in the two categories.
On- Premise Private Cloud: The on premise cloud servers are hosted
using inside the office using its own data centres. This enhances the
security policy of the cloud and also helps the organisation in ensuring
the data protections. Although this increases the cost of the service
(Chouhan & Peddoju, 2013). This ensures that total control of the
cloud is in the hand of the organization and hence ensure the maximum
security.
Externally Hosted Private Cloud: This service is provided and hosted
externally though a cloud server using third party. This ensures that
the specified cloud is only used by the servers of the organisation only.
The cost of this is lower that of the on premise of the private cloud.
Hybrid Cloud: The hybrid cloud can be explained as the servers which uses both the
concepts of the private and the public servers. The service is provided by the public
servers and but provides the essentials of the private servers (Darwish, Ouda &
Capretz, 2013). This ensures that there are less amount of risk in the concept and
reduces the chances of the getting hacked.
The cloud service have some of the major service models that can be used for the process of
enhancing the features. Thus features that can be used are:
SAAS- the Saas or the software as a service is one of the major use of the application.
In this the cloud servers host the application over the servers and the organisation can
use the same (Deshmukh, & Devadkar, 2015). This can be explained as the model for
Private cloud: The private cloud servers are used by a single enterprise for
organisational use. These servers are hosted only for a specific organisation and the
cloud can only be accessed through system of the organisation. The private cloud can
be sub divided in the two categories.
On- Premise Private Cloud: The on premise cloud servers are hosted
using inside the office using its own data centres. This enhances the
security policy of the cloud and also helps the organisation in ensuring
the data protections. Although this increases the cost of the service
(Chouhan & Peddoju, 2013). This ensures that total control of the
cloud is in the hand of the organization and hence ensure the maximum
security.
Externally Hosted Private Cloud: This service is provided and hosted
externally though a cloud server using third party. This ensures that
the specified cloud is only used by the servers of the organisation only.
The cost of this is lower that of the on premise of the private cloud.
Hybrid Cloud: The hybrid cloud can be explained as the servers which uses both the
concepts of the private and the public servers. The service is provided by the public
servers and but provides the essentials of the private servers (Darwish, Ouda &
Capretz, 2013). This ensures that there are less amount of risk in the concept and
reduces the chances of the getting hacked.
The cloud service have some of the major service models that can be used for the process of
enhancing the features. Thus features that can be used are:
SAAS- the Saas or the software as a service is one of the major use of the application.
In this the cloud servers host the application over the servers and the organisation can
use the same (Deshmukh, & Devadkar, 2015). This can be explained as the model for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RISK ASSESSMENT IN CLOUD
the process of the distribution of the software. This is one of the major feature of the
public cloud systems and hence are very low costly. The major characterics of the
SAAs are, the updates of the software are automatically done and the user does not
need to worry about the same. The purchase of the servers are based of the
subscription basis. The requirement of the hardware is very low as the entire process
os done in the web.
PaaS: The PaaS or the platform as a service can be explained as the upper version of
the software as service (Girma, Garuba & Liu, 2015). The PaaS can be explained as
the integrated solution or a solution stack that is rented over the internet connection.
The PaaS have two layers of the web applications, the hardware and the software.
IaaS- The IaaS or the infrastructure
Thus, it can be understand that using the Private on premise cloud service is one of the
major point that can be used in the organisation for the betterment of the business. This
ensures that the data of the organisation is safe and hence ensuring data protection to the
customers.
(Figure1: DDOS Attack pattern)
the process of the distribution of the software. This is one of the major feature of the
public cloud systems and hence are very low costly. The major characterics of the
SAAs are, the updates of the software are automatically done and the user does not
need to worry about the same. The purchase of the servers are based of the
subscription basis. The requirement of the hardware is very low as the entire process
os done in the web.
PaaS: The PaaS or the platform as a service can be explained as the upper version of
the software as service (Girma, Garuba & Liu, 2015). The PaaS can be explained as
the integrated solution or a solution stack that is rented over the internet connection.
The PaaS have two layers of the web applications, the hardware and the software.
IaaS- The IaaS or the infrastructure
Thus, it can be understand that using the Private on premise cloud service is one of the
major point that can be used in the organisation for the betterment of the business. This
ensures that the data of the organisation is safe and hence ensuring data protection to the
customers.
(Figure1: DDOS Attack pattern)

5RISK ASSESSMENT IN CLOUD
(Source: Author)
One of the major thing that will be explained in the paper how the use of the cloud servers
can help servers of organisations form preventing by the distributed denial-of-service or the
DDOS attacks. The use of the cloud servers can help in the process of prevention of the data
of the customers and the organisational data form the DDOS attacks that attack systems. The
DDOS attack can be explained as the attacks that are made in order to flow huge amount of
data in the servers of the organisation and thus blocking the process of correct data entry
(Iyengar et al.,2014). This attacks works on the similar way on the cloud servers as it does in
the normal servers. The paper focuses on the factors that helps in the process of the
prevention form the cloud servers. Further why there is need of cloud servers is nessacery for
the organisation and how these can help in the process of enhancing the system uses are also
well explained in the paper.
Risk assessment:
As explained above the cloud computing is one of the major application that is used
by majority of the organisation now a days. Although of its advantages there are some of the
major risks that are associated with the cloud computing architecture and this reduces the
efficiency of the cloud computing. One of the risk is the DDOS attacks that is associated
(Kumar & Sharma, 2013). The DDOS or the distributed denial of service attack is one of the
major attack that are often made in the cloud servers can be explained as the process of
flooding the servers with bogus data and blocking the servers so that the legitimate data
cannot be uploaded or downloaded (lua et al., 2013). The hackers mostly exploits the
scenario of the of pay as you go model of the cloud computing and causes problem for the
victim. The major attacks that are done on the cloud servers are:
(Source: Author)
One of the major thing that will be explained in the paper how the use of the cloud servers
can help servers of organisations form preventing by the distributed denial-of-service or the
DDOS attacks. The use of the cloud servers can help in the process of prevention of the data
of the customers and the organisational data form the DDOS attacks that attack systems. The
DDOS attack can be explained as the attacks that are made in order to flow huge amount of
data in the servers of the organisation and thus blocking the process of correct data entry
(Iyengar et al.,2014). This attacks works on the similar way on the cloud servers as it does in
the normal servers. The paper focuses on the factors that helps in the process of the
prevention form the cloud servers. Further why there is need of cloud servers is nessacery for
the organisation and how these can help in the process of enhancing the system uses are also
well explained in the paper.
Risk assessment:
As explained above the cloud computing is one of the major application that is used
by majority of the organisation now a days. Although of its advantages there are some of the
major risks that are associated with the cloud computing architecture and this reduces the
efficiency of the cloud computing. One of the risk is the DDOS attacks that is associated
(Kumar & Sharma, 2013). The DDOS or the distributed denial of service attack is one of the
major attack that are often made in the cloud servers can be explained as the process of
flooding the servers with bogus data and blocking the servers so that the legitimate data
cannot be uploaded or downloaded (lua et al., 2013). The hackers mostly exploits the
scenario of the of pay as you go model of the cloud computing and causes problem for the
victim. The major attacks that are done on the cloud servers are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RISK ASSESSMENT IN CLOUD
Threats
There are several kinds of attacks that are made in the cloud servers that the
organisation needs to take care of, some of the major attacks that are made in the cloud
servers are:
Bandwidth depletion attacks:
(Figure2: DDOS Attack)
(Source : Lonea et al., 2013))
This type of the attacks consumes the bandwidth of target r the victim system. This
done by flooding unwanted traffic which reduces the bandwidth and thus effecting the
legitimate traffic form reaching the network. One of the major tool that can help in this type
of the attack is trinoo. Further the bandwidth depletion attack can be sub divided in two
categories namely the Flooding attack and amplification attack.
Flood Attacks: This type of attacks are done by the attacker in order to jam the
network of the victim by sending huge amount of data using zombie bots which clogs
up the victim network (Navaz, Sangeetha & Prabhadevi, 2013). This reduces the
bandwidth of the cloud server used by the victim (Reddy et al., 2013). The attacks
Threats
There are several kinds of attacks that are made in the cloud servers that the
organisation needs to take care of, some of the major attacks that are made in the cloud
servers are:
Bandwidth depletion attacks:
(Figure2: DDOS Attack)
(Source : Lonea et al., 2013))
This type of the attacks consumes the bandwidth of target r the victim system. This
done by flooding unwanted traffic which reduces the bandwidth and thus effecting the
legitimate traffic form reaching the network. One of the major tool that can help in this type
of the attack is trinoo. Further the bandwidth depletion attack can be sub divided in two
categories namely the Flooding attack and amplification attack.
Flood Attacks: This type of attacks are done by the attacker in order to jam the
network of the victim by sending huge amount of data using zombie bots which clogs
up the victim network (Navaz, Sangeetha & Prabhadevi, 2013). This reduces the
bandwidth of the cloud server used by the victim (Reddy et al., 2013). The attacks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISK ASSESSMENT IN CLOUD
uses the UDP that is the User Datagram packets and ICMP that is the internet Control
Message Protocol packets. The steps of the attack follows as :
The attacker sends large data sets of UDP packets to the server’s
random ports. This blocks the ports of the server.
When the port receives the data it searches for the destination port.
When the port does not get any further response it generates the
message of destination unreachable.
This ensures that the original data also does not reaches the port.
Amplification attack: In this kind of the attack the attacker sends large data sets to the
broadcast Ip address (Negi, Mishra & Gupta, 2013). This causes the broadcaster to
reply to the pings made by the attackers. This ensures that entire server is blocked
with messages from the attackers and the original pings never reaches the server.
Resource depletion attacks:
Under this kind of the attacks the attackers make sure that target server is exhausted
with malicious forms of the data and the original data does not reaches the servers (Yu et al.,
2014). There are various kinds of the resource depletion attack under the DDOS.
Protocol Exploit Attack: The primary goal of this attack is to ensure
that the attackers consume the majority of the resources present in the
servers (Osanaiye, 2015). The TCP – SYN attack is one of the major
example of this type of the attacks.
Malformed Packets attacks: Under this kind of the attacks, the
attackers sends data packets that are malformed and jams the network
of the user.
IP Address attack: The malformed packet is wrapped with same source
and destination IP address thus creating chaos in the operating system
uses the UDP that is the User Datagram packets and ICMP that is the internet Control
Message Protocol packets. The steps of the attack follows as :
The attacker sends large data sets of UDP packets to the server’s
random ports. This blocks the ports of the server.
When the port receives the data it searches for the destination port.
When the port does not get any further response it generates the
message of destination unreachable.
This ensures that the original data also does not reaches the port.
Amplification attack: In this kind of the attack the attacker sends large data sets to the
broadcast Ip address (Negi, Mishra & Gupta, 2013). This causes the broadcaster to
reply to the pings made by the attackers. This ensures that entire server is blocked
with messages from the attackers and the original pings never reaches the server.
Resource depletion attacks:
Under this kind of the attacks the attackers make sure that target server is exhausted
with malicious forms of the data and the original data does not reaches the servers (Yu et al.,
2014). There are various kinds of the resource depletion attack under the DDOS.
Protocol Exploit Attack: The primary goal of this attack is to ensure
that the attackers consume the majority of the resources present in the
servers (Osanaiye, 2015). The TCP – SYN attack is one of the major
example of this type of the attacks.
Malformed Packets attacks: Under this kind of the attacks, the
attackers sends data packets that are malformed and jams the network
of the user.
IP Address attack: The malformed packet is wrapped with same source
and destination IP address thus creating chaos in the operating system
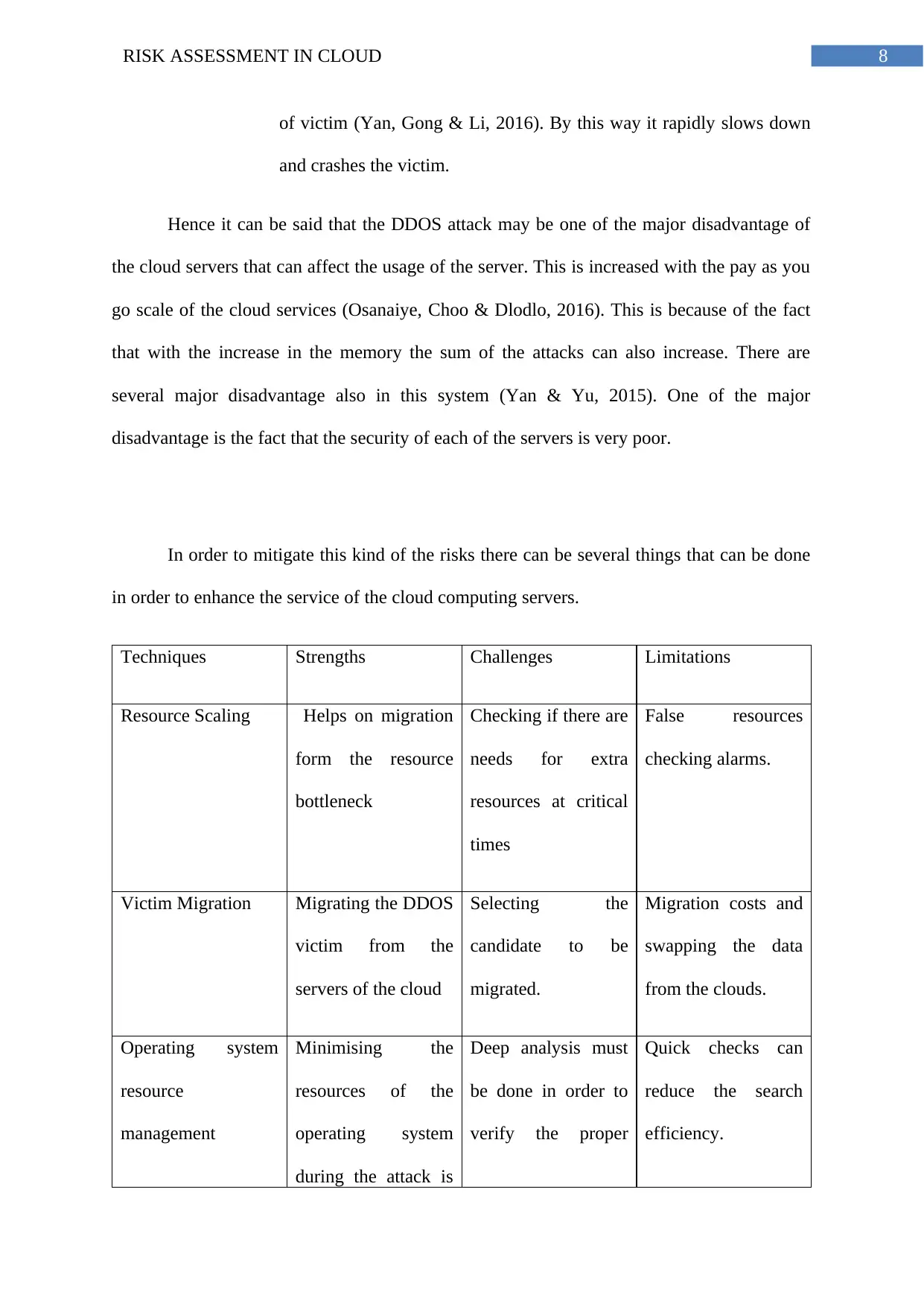
8RISK ASSESSMENT IN CLOUD
of victim (Yan, Gong & Li, 2016). By this way it rapidly slows down
and crashes the victim.
Hence it can be said that the DDOS attack may be one of the major disadvantage of
the cloud servers that can affect the usage of the server. This is increased with the pay as you
go scale of the cloud services (Osanaiye, Choo & Dlodlo, 2016). This is because of the fact
that with the increase in the memory the sum of the attacks can also increase. There are
several major disadvantage also in this system (Yan & Yu, 2015). One of the major
disadvantage is the fact that the security of each of the servers is very poor.
In order to mitigate this kind of the risks there can be several things that can be done
in order to enhance the service of the cloud computing servers.
Techniques Strengths Challenges Limitations
Resource Scaling Helps on migration
form the resource
bottleneck
Checking if there are
needs for extra
resources at critical
times
False resources
checking alarms.
Victim Migration Migrating the DDOS
victim from the
servers of the cloud
Selecting the
candidate to be
migrated.
Migration costs and
swapping the data
from the clouds.
Operating system
resource
management
Minimising the
resources of the
operating system
during the attack is
Deep analysis must
be done in order to
verify the proper
Quick checks can
reduce the search
efficiency.
of victim (Yan, Gong & Li, 2016). By this way it rapidly slows down
and crashes the victim.
Hence it can be said that the DDOS attack may be one of the major disadvantage of
the cloud servers that can affect the usage of the server. This is increased with the pay as you
go scale of the cloud services (Osanaiye, Choo & Dlodlo, 2016). This is because of the fact
that with the increase in the memory the sum of the attacks can also increase. There are
several major disadvantage also in this system (Yan & Yu, 2015). One of the major
disadvantage is the fact that the security of each of the servers is very poor.
In order to mitigate this kind of the risks there can be several things that can be done
in order to enhance the service of the cloud computing servers.
Techniques Strengths Challenges Limitations
Resource Scaling Helps on migration
form the resource
bottleneck
Checking if there are
needs for extra
resources at critical
times
False resources
checking alarms.
Victim Migration Migrating the DDOS
victim from the
servers of the cloud
Selecting the
candidate to be
migrated.
Migration costs and
swapping the data
from the clouds.
Operating system
resource
management
Minimising the
resources of the
operating system
during the attack is
Deep analysis must
be done in order to
verify the proper
Quick checks can
reduce the search
efficiency.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
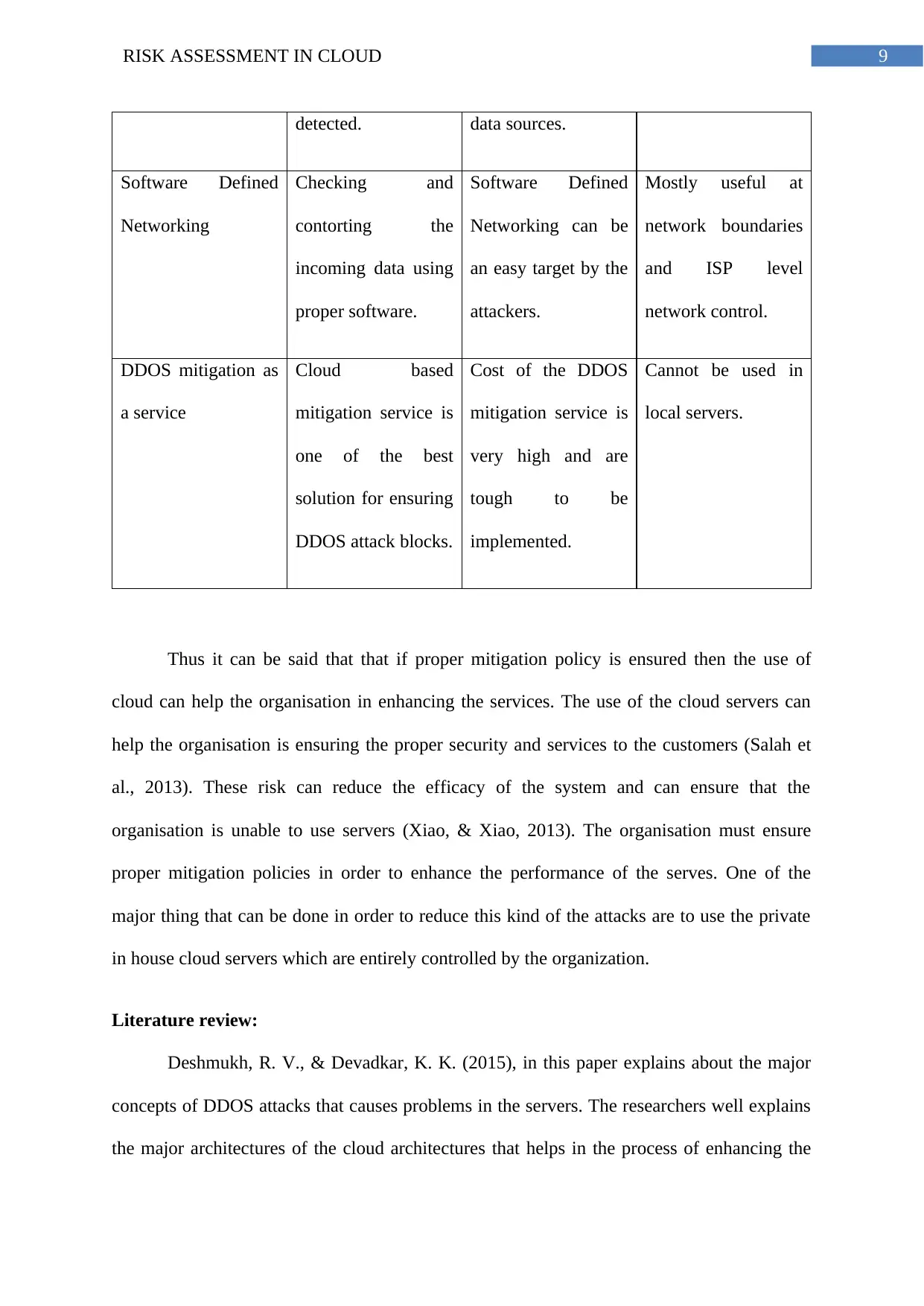
9RISK ASSESSMENT IN CLOUD
detected. data sources.
Software Defined
Networking
Checking and
contorting the
incoming data using
proper software.
Software Defined
Networking can be
an easy target by the
attackers.
Mostly useful at
network boundaries
and ISP level
network control.
DDOS mitigation as
a service
Cloud based
mitigation service is
one of the best
solution for ensuring
DDOS attack blocks.
Cost of the DDOS
mitigation service is
very high and are
tough to be
implemented.
Cannot be used in
local servers.
Thus it can be said that that if proper mitigation policy is ensured then the use of
cloud can help the organisation in enhancing the services. The use of the cloud servers can
help the organisation is ensuring the proper security and services to the customers (Salah et
al., 2013). These risk can reduce the efficacy of the system and can ensure that the
organisation is unable to use servers (Xiao, & Xiao, 2013). The organisation must ensure
proper mitigation policies in order to enhance the performance of the serves. One of the
major thing that can be done in order to reduce this kind of the attacks are to use the private
in house cloud servers which are entirely controlled by the organization.
Literature review:
Deshmukh, R. V., & Devadkar, K. K. (2015), in this paper explains about the major
concepts of DDOS attacks that causes problems in the servers. The researchers well explains
the major architectures of the cloud architectures that helps in the process of enhancing the
detected. data sources.
Software Defined
Networking
Checking and
contorting the
incoming data using
proper software.
Software Defined
Networking can be
an easy target by the
attackers.
Mostly useful at
network boundaries
and ISP level
network control.
DDOS mitigation as
a service
Cloud based
mitigation service is
one of the best
solution for ensuring
DDOS attack blocks.
Cost of the DDOS
mitigation service is
very high and are
tough to be
implemented.
Cannot be used in
local servers.
Thus it can be said that that if proper mitigation policy is ensured then the use of
cloud can help the organisation in enhancing the services. The use of the cloud servers can
help the organisation is ensuring the proper security and services to the customers (Salah et
al., 2013). These risk can reduce the efficacy of the system and can ensure that the
organisation is unable to use servers (Xiao, & Xiao, 2013). The organisation must ensure
proper mitigation policies in order to enhance the performance of the serves. One of the
major thing that can be done in order to reduce this kind of the attacks are to use the private
in house cloud servers which are entirely controlled by the organization.
Literature review:
Deshmukh, R. V., & Devadkar, K. K. (2015), in this paper explains about the major
concepts of DDOS attacks that causes problems in the servers. The researchers well explains
the major architectures of the cloud architectures that helps in the process of enhancing the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RISK ASSESSMENT IN CLOUD
process of cloud security (Wang et al., 2013). This paper well explains the processes of the
DDOS attacks that are majorly found in the servers of the organisation. Further the
researchers explains about the various types of the DDOS attacks that are commonly found in
the servers of a system. Later, in the paper the researchers well explains about the processes
that can used in order to mitigate this kind of the risks. The major DDOS attack analysing
techniques are also well explained in the paper. The paper ensures provides enough
examples that how the distributed denial of service attack can be prevented and ensure that
proper flow of the data is ensured.
In this paper Osanaiye et al., (2016). Explains about the process of software denial
networking and the DDOS attack survey and how the availability of the data can help in the
process of ensuring that data remains a challenge. The researchers explains about the major
concepts of the DDOS and its processes. The major things that the researchers explained in
this paper are Anomaly-based, Cloud Distributed Denial of Service (DDoS) attacks, Change
point detection, Distributed Denial of Service (DDoS) attack taxonomy Cloud Distributed
Denial of Service (DDoS) survey, Flooding attacks. This paper well explains the processes of
the DDOS attacks that are majorly found in the servers of the organisation (Shahzad, 2014).
Further the researchers explains about the various types of the DDOS attacks that are
commonly found in the servers of a system. This enhances the security policy of the cloud
and also helps the organisation in ensuring the data protections. Although this increases the
cost of the service these are the major concepts that are well explained in the paper. DDoS
attack tools are capable of launching such attacks targeting different cloud components (Xiao,
& Xiao, 2013). More research should also be directed towards efficient defines solutions that
can detect both high and low level DDoS attacks One of the major thing that is well
explained in the paper which are not explained in the other papers are the concept of the
XML flooding attacks. Unlike the paper of Deshmukh & Devadkar (2015), this paper is
process of cloud security (Wang et al., 2013). This paper well explains the processes of the
DDOS attacks that are majorly found in the servers of the organisation. Further the
researchers explains about the various types of the DDOS attacks that are commonly found in
the servers of a system. Later, in the paper the researchers well explains about the processes
that can used in order to mitigate this kind of the risks. The major DDOS attack analysing
techniques are also well explained in the paper. The paper ensures provides enough
examples that how the distributed denial of service attack can be prevented and ensure that
proper flow of the data is ensured.
In this paper Osanaiye et al., (2016). Explains about the process of software denial
networking and the DDOS attack survey and how the availability of the data can help in the
process of ensuring that data remains a challenge. The researchers explains about the major
concepts of the DDOS and its processes. The major things that the researchers explained in
this paper are Anomaly-based, Cloud Distributed Denial of Service (DDoS) attacks, Change
point detection, Distributed Denial of Service (DDoS) attack taxonomy Cloud Distributed
Denial of Service (DDoS) survey, Flooding attacks. This paper well explains the processes of
the DDOS attacks that are majorly found in the servers of the organisation (Shahzad, 2014).
Further the researchers explains about the various types of the DDOS attacks that are
commonly found in the servers of a system. This enhances the security policy of the cloud
and also helps the organisation in ensuring the data protections. Although this increases the
cost of the service these are the major concepts that are well explained in the paper. DDoS
attack tools are capable of launching such attacks targeting different cloud components (Xiao,
& Xiao, 2013). More research should also be directed towards efficient defines solutions that
can detect both high and low level DDoS attacks One of the major thing that is well
explained in the paper which are not explained in the other papers are the concept of the
XML flooding attacks. Unlike the paper of Deshmukh & Devadkar (2015), this paper is

11RISK ASSESSMENT IN CLOUD
unable to provide the ways on how to solve the problems of the cloud servers (Somani et al.,
2017). The paper primarily focuses on the facts about the DDOS attacks on the cloud servers.
Concluding the topic the researchers explained about the challenges that may come up in the
recent future and how these can be avoided.
Some of the major processes that can be used for the purpose of the reducing these
distributed denial of service attacks are
The most important thing that must be ensured in order to enhance the cloud
security are maintain the basic aspects of the :
o Confidentiality
o Access controllability
o Integrity
The use of the DDOS as a mechanism must be used in order to reduce the
chances of the any DDOS attack.
If any DDOS attack is encountered then victim migration technique must be
used as soon as possible.
The use of the SDN or the software defined networking can be used in order to
enhance the security of the servers.
The Operating systems that are used must ensure proper security to the
servers.
Conclusion:
Thus, concluding the topic it can be said that the use of the Cloud computing can help
the organisation Gigantic in many ways. The use of the cloud enhances the internal
operations of the organisation as well as helps in properly managing the data of the
customers. Yet there are some of the major obstacles that must not overlooked. The
unable to provide the ways on how to solve the problems of the cloud servers (Somani et al.,
2017). The paper primarily focuses on the facts about the DDOS attacks on the cloud servers.
Concluding the topic the researchers explained about the challenges that may come up in the
recent future and how these can be avoided.
Some of the major processes that can be used for the purpose of the reducing these
distributed denial of service attacks are
The most important thing that must be ensured in order to enhance the cloud
security are maintain the basic aspects of the :
o Confidentiality
o Access controllability
o Integrity
The use of the DDOS as a mechanism must be used in order to reduce the
chances of the any DDOS attack.
If any DDOS attack is encountered then victim migration technique must be
used as soon as possible.
The use of the SDN or the software defined networking can be used in order to
enhance the security of the servers.
The Operating systems that are used must ensure proper security to the
servers.
Conclusion:
Thus, concluding the topic it can be said that the use of the Cloud computing can help
the organisation Gigantic in many ways. The use of the cloud enhances the internal
operations of the organisation as well as helps in properly managing the data of the
customers. Yet there are some of the major obstacles that must not overlooked. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





