Network Security: Report on OSI Security Architecture and Cryptographic Algorithms
Added on 2023-04-20
16 Pages2776 Words371 Views
Ruining Head: Network Security 0
Network Security
Report
Student name
Network Security
Report
Student name
Network Security 1
Executive Summary:
In this report, key concepts of OSI security architecture will discuss including cryptographic
algorithms. It will explain about design and implementation of prevention and detection system
using common security standards and protocols, such as IPsec, and many others.
XYZ retails ltd is a company that has up to 100 computer systems. This report will provide
network design with security techniques, such as public key encryption, authentication, access
controls, digital signatures, and identity management.
Executive Summary:
In this report, key concepts of OSI security architecture will discuss including cryptographic
algorithms. It will explain about design and implementation of prevention and detection system
using common security standards and protocols, such as IPsec, and many others.
XYZ retails ltd is a company that has up to 100 computer systems. This report will provide
network design with security techniques, such as public key encryption, authentication, access
controls, digital signatures, and identity management.
Network Security 2
Introduction:
Data communication is highly required to communicate between different systems. Network is
basic need of a company in present era. There are many things that are based on the computer
systems, such as billing, sales, marketing, and many others. This report will design network
architecture with high security to protect computer networks from cyber-attacks (Bradford,
2018).
Cyber security is necessary because most of the organizations are having their 20 percent
confidential data on the computer systems. Therefore, it is necessary to make them secure form
the cyber-attacks. In this report, key concepts of OSI security design will discuss including
cryptographic algorithms. It will explain about design and implementation of prevention and
detection system using common security standards and protocols, such as IPsec, and many others
(Cowley, 2012).
Authentication provides a security to a system and it is a way to make data and information
secure from the hackers and cyber-attacks. This report will provide network design with security
techniques, such as public key encryption, authentication, access controls, digital signatures,
and identity management ( Dosal, 2018).
Requirements:
Computer network requires many things to secure unauthenticated access from outside of the
network as well as internal access. To design and implement security policies in server and
firewalls, system requires security techniques, such as digital signature, authentication, access
control, public key encryption, and identity management ( Schilling , 2017). Cryptographic
algorithms are very helpful in security of a network. It is a best way to encrypt the data to
prevent from attackers. There are many cryptographic algorithms, which are making secure users
data from attackers in a public network (Dye, et al., 2007).
XYZ retails ltd can implement secure architecture for their organization. It requires basic
algorithm, such as symmetric and asymmetric algorithms. It is a way to secure resources and
data from unauthorized users. They will require digital signature to secure confidential data of
Introduction:
Data communication is highly required to communicate between different systems. Network is
basic need of a company in present era. There are many things that are based on the computer
systems, such as billing, sales, marketing, and many others. This report will design network
architecture with high security to protect computer networks from cyber-attacks (Bradford,
2018).
Cyber security is necessary because most of the organizations are having their 20 percent
confidential data on the computer systems. Therefore, it is necessary to make them secure form
the cyber-attacks. In this report, key concepts of OSI security design will discuss including
cryptographic algorithms. It will explain about design and implementation of prevention and
detection system using common security standards and protocols, such as IPsec, and many others
(Cowley, 2012).
Authentication provides a security to a system and it is a way to make data and information
secure from the hackers and cyber-attacks. This report will provide network design with security
techniques, such as public key encryption, authentication, access controls, digital signatures,
and identity management ( Dosal, 2018).
Requirements:
Computer network requires many things to secure unauthenticated access from outside of the
network as well as internal access. To design and implement security policies in server and
firewalls, system requires security techniques, such as digital signature, authentication, access
control, public key encryption, and identity management ( Schilling , 2017). Cryptographic
algorithms are very helpful in security of a network. It is a best way to encrypt the data to
prevent from attackers. There are many cryptographic algorithms, which are making secure users
data from attackers in a public network (Dye, et al., 2007).
XYZ retails ltd can implement secure architecture for their organization. It requires basic
algorithm, such as symmetric and asymmetric algorithms. It is a way to secure resources and
data from unauthorized users. They will require digital signature to secure confidential data of

Network Security 3
their business and other things. It is a basic thing to secure confidential information from cyber-
attacks. They will require firewalls and IDS/IPS to secure their network (Forouzan, 2007).
Solution Design
Secure network is first requirement of an organization. However, no one is secure from cyber-
attacks, as hacker’s uses new techniques for hacking computer systems and network of an
organization. There are many security techniques, which makes a network secure form the cyber-
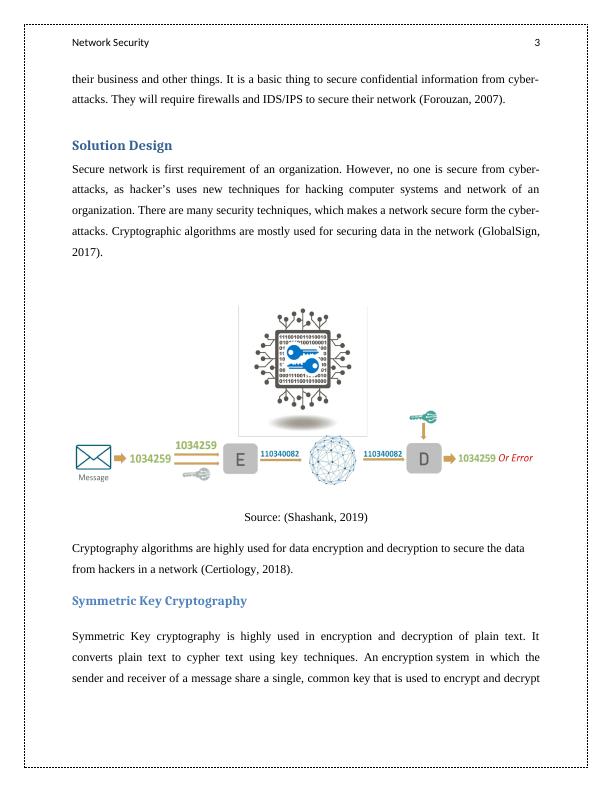
attacks. Cryptographic algorithms are mostly used for securing data in the network (GlobalSign,
2017).
Source: (Shashank, 2019)
Cryptography algorithms are highly used for data encryption and decryption to secure the data
from hackers in a network (Certiology, 2018).
Symmetric Key Cryptography
Symmetric Key cryptography is highly used in encryption and decryption of plain text. It
converts plain text to cypher text using key techniques. An encryption system in which the
sender and receiver of a message share a single, common key that is used to encrypt and decrypt
their business and other things. It is a basic thing to secure confidential information from cyber-
attacks. They will require firewalls and IDS/IPS to secure their network (Forouzan, 2007).
Solution Design
Secure network is first requirement of an organization. However, no one is secure from cyber-
attacks, as hacker’s uses new techniques for hacking computer systems and network of an
organization. There are many security techniques, which makes a network secure form the cyber-
attacks. Cryptographic algorithms are mostly used for securing data in the network (GlobalSign,
2017).
Source: (Shashank, 2019)
Cryptography algorithms are highly used for data encryption and decryption to secure the data
from hackers in a network (Certiology, 2018).
Symmetric Key Cryptography
Symmetric Key cryptography is highly used in encryption and decryption of plain text. It
converts plain text to cypher text using key techniques. An encryption system in which the
sender and receiver of a message share a single, common key that is used to encrypt and decrypt
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Network Security: Concepts and Techniqueslg...
|11
|718
|27
Engineering and Computing Master of Sciencelg...
|6
|4182
|211
Information Systems Securitylg...
|5
|791
|494
Cyber Security: Attacks and Mitigation Techniqueslg...
|11
|2291
|301
Electronic Securitylg...
|2
|1473
|73
Cryptography and Security Protocols for Data Protection - Deskliblg...
|6
|1420
|320
