Project Management and Cyber-Resilience
VerifiedAdded on 2021/04/21
|13
|2437
|101
AI Summary
This assignment provides a detailed project plan for implementing project management principles to increase the cyber-resilience of healthcare infrastructures. It includes a study into data analysis and visualisation, as well as attribute-based keyword search efficiency enhancement via an online/offline approach. The assignment also covers online/offline attribute-based encryption and secure data sharing in cloud computing. A key focus is on ensuring the security of sensitive information and preventing cyber-attacks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: SECURE ENCRYPTION TECHNOLOGIES
Secure Encryption Technologies
Name of the Student
Name of the University
Secure Encryption Technologies
Name of the Student
Name of the University
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1SECURE ENCRYPTION TECHNOLOGIES
Table of Contents
1.0 Project Overview.......................................................................................................................2
2.0 Client Overview.........................................................................................................................2
3.0 Scope..........................................................................................................................................3
4.0 Project Assessment Report........................................................................................................3
4.1 Introduction............................................................................................................................3
4.2 Project Findings.....................................................................................................................3
4.3 Project Recommendations.....................................................................................................4
4.4 Possible OHS Concerns.........................................................................................................5
5.0 Project Analysis and Design......................................................................................................5
5.1 Project Estimated Duration....................................................................................................5
5.2 Target Audience.....................................................................................................................5
5.3 Mock-Up Design...................................................................................................................6
6.0 Project Management..................................................................................................................7
6.1 Preliminary Evaluation of Technologies...............................................................................7
6.2 Project Timeline.....................................................................................................................7
6.3 Budget..................................................................................................................................10
6.4 Copyright and Legal Issues.................................................................................................10
7.0 Project Sign Off.......................................................................................................................10
References......................................................................................................................................12
Table of Contents
1.0 Project Overview.......................................................................................................................2
2.0 Client Overview.........................................................................................................................2
3.0 Scope..........................................................................................................................................3
4.0 Project Assessment Report........................................................................................................3
4.1 Introduction............................................................................................................................3
4.2 Project Findings.....................................................................................................................3
4.3 Project Recommendations.....................................................................................................4
4.4 Possible OHS Concerns.........................................................................................................5
5.0 Project Analysis and Design......................................................................................................5
5.1 Project Estimated Duration....................................................................................................5
5.2 Target Audience.....................................................................................................................5
5.3 Mock-Up Design...................................................................................................................6
6.0 Project Management..................................................................................................................7
6.1 Preliminary Evaluation of Technologies...............................................................................7
6.2 Project Timeline.....................................................................................................................7
6.3 Budget..................................................................................................................................10
6.4 Copyright and Legal Issues.................................................................................................10
7.0 Project Sign Off.......................................................................................................................10
References......................................................................................................................................12

2SECURE ENCRYPTION TECHNOLOGIES
1.0 Project Overview
The project is based on the development of data encryption system for RCH in order to
protect sensitive information of their patients that are stored in their online database. In the
previous system, data was managed manually and stored in the form of paper documents.
However, the hospital has now developed information system and all the patient information is
now stored in online virtual media. In addition, when the doctors and nurses travel to other
healthcare facilities of the hospital, they carry the information in their electronic devices like
laptops and smartphones. Due to the lack of sufficient security measures, it is risky to carry such
information in the devices (Gupta & Singh, 2015). If the devices somehow get stolen, the
sensitive and secure information may be broken by some other people for unethical use. Hence,
this project aims to deliver a suitable encryption technology that will help to secure such data and
information from falling to the hands of the wrong individuals.
2.0 Client Overview
The client Royal Children’s Hospital (RCH) provides healthcare care assist to children in
Melbourne, Australia since 1870. Although the hospital initiated its services in one building
only, with the growing number of healthcare requirements of children, the hospital has opened
several other branches including emergency locations, specialty care centers and outreach clinics
in other parts of the city as well as other nearby cities. The company is fully committed to
providing healthcare assistance to the children of Australia and has expanded their services in
order to treat more children within more area coverage.
1.0 Project Overview
The project is based on the development of data encryption system for RCH in order to
protect sensitive information of their patients that are stored in their online database. In the
previous system, data was managed manually and stored in the form of paper documents.
However, the hospital has now developed information system and all the patient information is
now stored in online virtual media. In addition, when the doctors and nurses travel to other
healthcare facilities of the hospital, they carry the information in their electronic devices like
laptops and smartphones. Due to the lack of sufficient security measures, it is risky to carry such
information in the devices (Gupta & Singh, 2015). If the devices somehow get stolen, the
sensitive and secure information may be broken by some other people for unethical use. Hence,
this project aims to deliver a suitable encryption technology that will help to secure such data and
information from falling to the hands of the wrong individuals.
2.0 Client Overview
The client Royal Children’s Hospital (RCH) provides healthcare care assist to children in
Melbourne, Australia since 1870. Although the hospital initiated its services in one building
only, with the growing number of healthcare requirements of children, the hospital has opened
several other branches including emergency locations, specialty care centers and outreach clinics
in other parts of the city as well as other nearby cities. The company is fully committed to
providing healthcare assistance to the children of Australia and has expanded their services in
order to treat more children within more area coverage.

3SECURE ENCRYPTION TECHNOLOGIES
3.0 Scope
The scope of the project includes the following.
Analyzing the type of data to be protected is within the scope of the project.
Analyzing the available encryption techniques is within the scope of this project.
Selection of a suitable encryption tool is within the scope of the project.
4.0 Project Assessment Report
4.1 Introduction
The project looks to address the data security problem faced by the travelling doctors and
nurses of the hospital who carry secure and sensitive patient information in their laptops while
moving from one facility to another. The main security risk is that if the laptop somehow gets
stolen or if an individual attempts phishing on the laptop, they may be able to access the sensitive
information that they may misuse. Hence, the suggested solution for this issue is to apply a
suitable encryption technique that will protect the sensitive information from unauthorized
access.
4.2 Project Findings
In order to complete the project, some suitable encryption techniques are to be
determined and evaluated. After that, analyzing the requirement for the client, the most suitable
encryption technique should be chosen and implementation plan has to be prepared.
From the findings of initial analysis, the following possible encryption technologies have
been found.
3.0 Scope
The scope of the project includes the following.
Analyzing the type of data to be protected is within the scope of the project.
Analyzing the available encryption techniques is within the scope of this project.
Selection of a suitable encryption tool is within the scope of the project.
4.0 Project Assessment Report
4.1 Introduction
The project looks to address the data security problem faced by the travelling doctors and
nurses of the hospital who carry secure and sensitive patient information in their laptops while
moving from one facility to another. The main security risk is that if the laptop somehow gets
stolen or if an individual attempts phishing on the laptop, they may be able to access the sensitive
information that they may misuse. Hence, the suggested solution for this issue is to apply a
suitable encryption technique that will protect the sensitive information from unauthorized
access.
4.2 Project Findings
In order to complete the project, some suitable encryption techniques are to be
determined and evaluated. After that, analyzing the requirement for the client, the most suitable
encryption technique should be chosen and implementation plan has to be prepared.
From the findings of initial analysis, the following possible encryption technologies have
been found.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4SECURE ENCRYPTION TECHNOLOGIES
Full Disc Encryption – For encrypting the entire hard drive of the laptop
Folder Encryption – For encrypting the particular folder that contains the information
Removable Drive Encryption – For encrypting removable drive like pen drive, portable
hard drive and others
Multilayered Encryption – For encrypting more than one of hard drive, portable drive
and folders
System Encryption – For encrypting the entire system in order to prevent unauthorized
access to the system
4.3 Project Recommendations
From the analysis of the options, the recommended encryption technology is the system
encryption. This will prevent any unauthorized access to the system itself and thus helping to
protect the information contained in the system. However, multiple layer encryption is also a
possible option although unlocking of multiple layers will consume significant amount of time.
The required system requirements for such system encryptions are as follows.
Hardware
Cryptographic Coprocessor Feature
PCI X Cryptographic Coprocessor
Crypto Express2 Coprocessor
Software
Key Server (web application for managing the encryption key)
Full Disc Encryption – For encrypting the entire hard drive of the laptop
Folder Encryption – For encrypting the particular folder that contains the information
Removable Drive Encryption – For encrypting removable drive like pen drive, portable
hard drive and others
Multilayered Encryption – For encrypting more than one of hard drive, portable drive
and folders
System Encryption – For encrypting the entire system in order to prevent unauthorized
access to the system
4.3 Project Recommendations
From the analysis of the options, the recommended encryption technology is the system
encryption. This will prevent any unauthorized access to the system itself and thus helping to
protect the information contained in the system. However, multiple layer encryption is also a
possible option although unlocking of multiple layers will consume significant amount of time.
The required system requirements for such system encryptions are as follows.
Hardware
Cryptographic Coprocessor Feature
PCI X Cryptographic Coprocessor
Crypto Express2 Coprocessor
Software
Key Server (web application for managing the encryption key)

5SECURE ENCRYPTION TECHNOLOGIES
Java Server (web application for managing encryption from admin server)
Desktop Client Application (Java)
4.4 Possible OHS Concerns
The possible OHS concerns that may arise during the project includes possible phishing
and monitoring attempts where an unethical employee of the hospital may try to see the
encryption and passwords used in the system and later use them for accessing the files of the
system (Liu, Wang & Wu, 2014). Other OHS concerns include possible infection in the project
team caused due to some contagious disease of a patient in the hospital. Hence, it is to be ensured
that the project team gets to work is a separate room after application of sufficient amount
disinfectants inside.
5.0 Project Analysis and Design
5.1 Project Estimated Duration
The estimated duration for the project is expected to be 64 days, starting from 12/3/2018
and ending on 7/6/18.
5.2 Target Audience
The target audiences for the project are the doctors and nurses who carry information in
the laptops while travelling from one branch of the hospital to another. It has been found that
while travelling in public transport, the laptops may get stolen and unethical users may try to
steal sensitive information from the system (Li et al., 2018). Hence, the encryption procedures
are proposed so that even in cases of stolen devices, the sensitive information and data are not
leaked.
Java Server (web application for managing encryption from admin server)
Desktop Client Application (Java)
4.4 Possible OHS Concerns
The possible OHS concerns that may arise during the project includes possible phishing
and monitoring attempts where an unethical employee of the hospital may try to see the
encryption and passwords used in the system and later use them for accessing the files of the
system (Liu, Wang & Wu, 2014). Other OHS concerns include possible infection in the project
team caused due to some contagious disease of a patient in the hospital. Hence, it is to be ensured
that the project team gets to work is a separate room after application of sufficient amount
disinfectants inside.
5.0 Project Analysis and Design
5.1 Project Estimated Duration
The estimated duration for the project is expected to be 64 days, starting from 12/3/2018
and ending on 7/6/18.
5.2 Target Audience
The target audiences for the project are the doctors and nurses who carry information in
the laptops while travelling from one branch of the hospital to another. It has been found that
while travelling in public transport, the laptops may get stolen and unethical users may try to
steal sensitive information from the system (Li et al., 2018). Hence, the encryption procedures
are proposed so that even in cases of stolen devices, the sensitive information and data are not
leaked.

6SECURE ENCRYPTION TECHNOLOGIES
5.3 Mock-Up Design
The mock-up design for the proposed encryption model is as follows.
Figure 1: Mock Up Design for Proposed Encryption Model
(Source: Created by Author)
The diagram shows a window that will automatically pop up when a user (doctor or
nurse) opens the system to access information. In this window, the user needed to click on the
“Start RCH Agent” that will open a new window asking for user verification ID and password.
When the user enters both the options successfully, the files will be decrypted and the list of files
will be shown in the window (of the above diagram) under their respective types (Yan et al.,
2016). However, if the user enters wrong id / password / both three times, it will automatically
lock the system for a certain amount of time. The RCH agent will also allow authorized users to
add additional encryption keys to the files stored in the system.
5.3 Mock-Up Design
The mock-up design for the proposed encryption model is as follows.
Figure 1: Mock Up Design for Proposed Encryption Model
(Source: Created by Author)
The diagram shows a window that will automatically pop up when a user (doctor or
nurse) opens the system to access information. In this window, the user needed to click on the
“Start RCH Agent” that will open a new window asking for user verification ID and password.
When the user enters both the options successfully, the files will be decrypted and the list of files
will be shown in the window (of the above diagram) under their respective types (Yan et al.,
2016). However, if the user enters wrong id / password / both three times, it will automatically
lock the system for a certain amount of time. The RCH agent will also allow authorized users to
add additional encryption keys to the files stored in the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SECURE ENCRYPTION TECHNOLOGIES
6.0 Project Management
6.1 Preliminary Evaluation of Technologies
The application of encryption technology requires upgradation of the hardwares of the
systems used to the best possible configuration. The old laptops can be replaced by new and
upgraded laptops. Furthermore, some encryption softwares will be required that require high
configurations of the system for running properly (Hohenberger & Waters, 2014). The software
requirements for the system include Key Server (web application for managing the encryption
key), Java Server (web application for managing encryption from admin server) and Desktop
Client Application (Java).
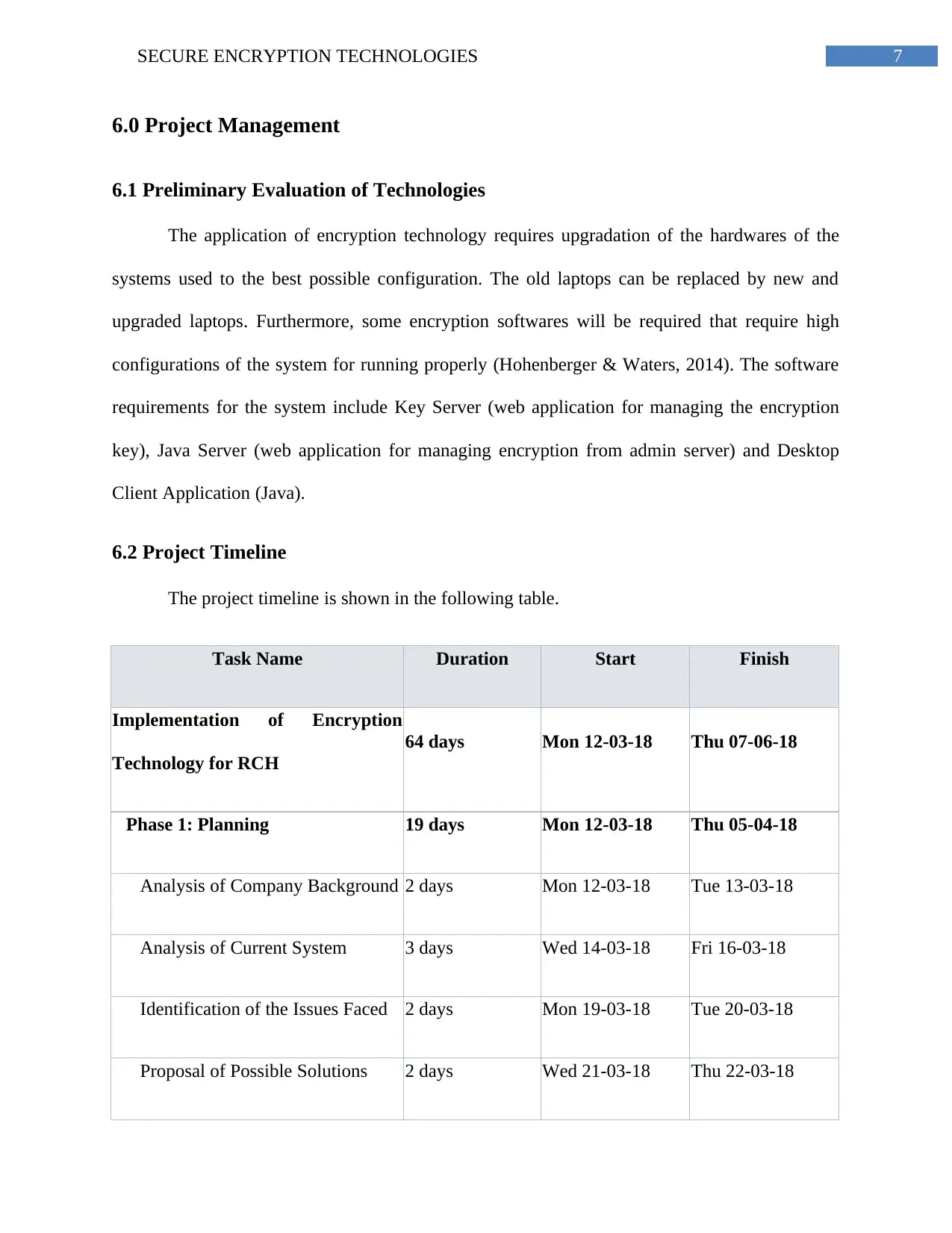
6.2 Project Timeline
The project timeline is shown in the following table.
Task Name Duration Start Finish
Implementation of Encryption
Technology for RCH
64 days Mon 12-03-18 Thu 07-06-18
Phase 1: Planning 19 days Mon 12-03-18 Thu 05-04-18
Analysis of Company Background 2 days Mon 12-03-18 Tue 13-03-18
Analysis of Current System 3 days Wed 14-03-18 Fri 16-03-18
Identification of the Issues Faced 2 days Mon 19-03-18 Tue 20-03-18
Proposal of Possible Solutions 2 days Wed 21-03-18 Thu 22-03-18
6.0 Project Management
6.1 Preliminary Evaluation of Technologies
The application of encryption technology requires upgradation of the hardwares of the
systems used to the best possible configuration. The old laptops can be replaced by new and
upgraded laptops. Furthermore, some encryption softwares will be required that require high
configurations of the system for running properly (Hohenberger & Waters, 2014). The software
requirements for the system include Key Server (web application for managing the encryption
key), Java Server (web application for managing encryption from admin server) and Desktop
Client Application (Java).
6.2 Project Timeline
The project timeline is shown in the following table.
Task Name Duration Start Finish
Implementation of Encryption
Technology for RCH
64 days Mon 12-03-18 Thu 07-06-18
Phase 1: Planning 19 days Mon 12-03-18 Thu 05-04-18
Analysis of Company Background 2 days Mon 12-03-18 Tue 13-03-18
Analysis of Current System 3 days Wed 14-03-18 Fri 16-03-18
Identification of the Issues Faced 2 days Mon 19-03-18 Tue 20-03-18
Proposal of Possible Solutions 2 days Wed 21-03-18 Thu 22-03-18
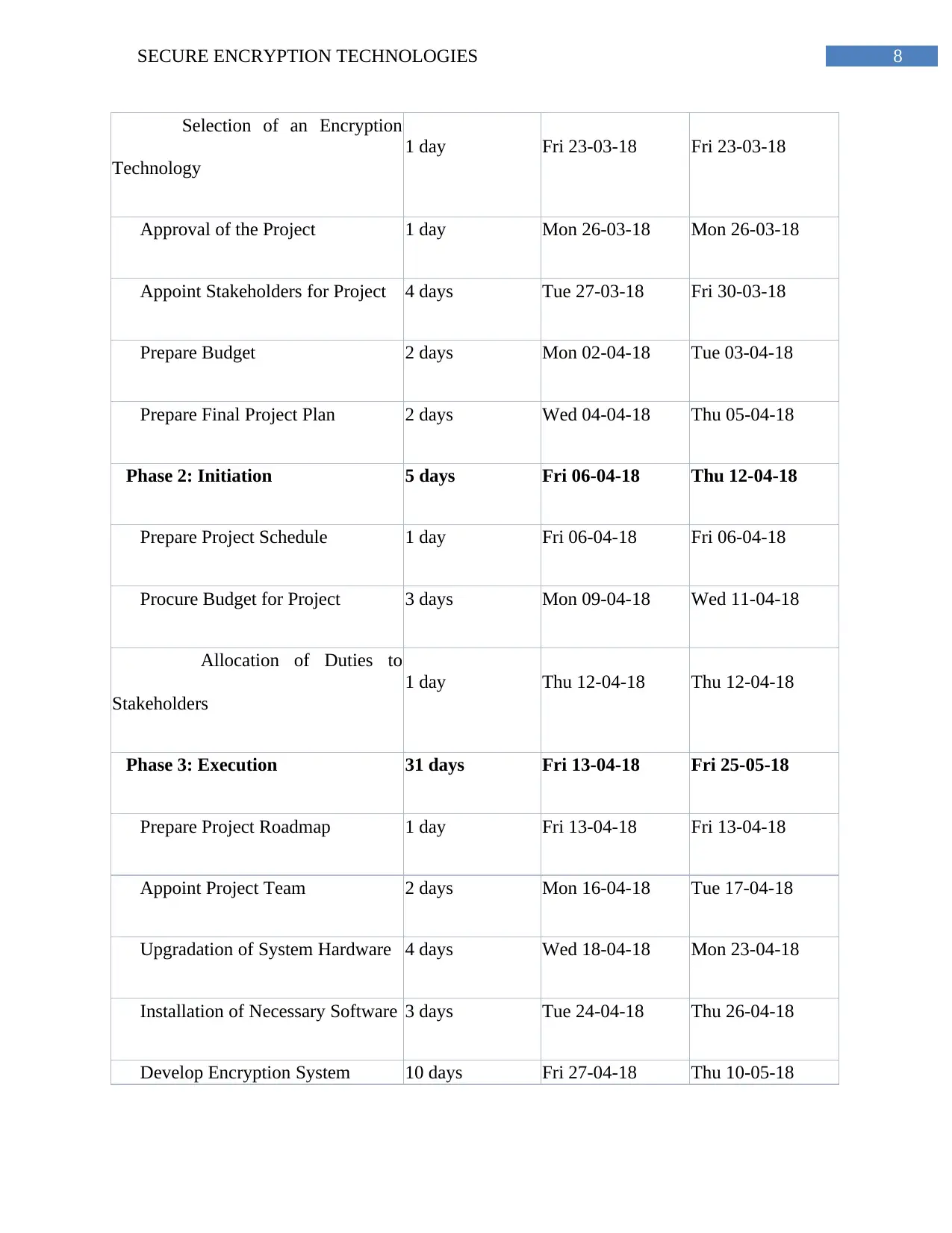
8SECURE ENCRYPTION TECHNOLOGIES
Selection of an Encryption
Technology
1 day Fri 23-03-18 Fri 23-03-18
Approval of the Project 1 day Mon 26-03-18 Mon 26-03-18
Appoint Stakeholders for Project 4 days Tue 27-03-18 Fri 30-03-18
Prepare Budget 2 days Mon 02-04-18 Tue 03-04-18
Prepare Final Project Plan 2 days Wed 04-04-18 Thu 05-04-18
Phase 2: Initiation 5 days Fri 06-04-18 Thu 12-04-18
Prepare Project Schedule 1 day Fri 06-04-18 Fri 06-04-18
Procure Budget for Project 3 days Mon 09-04-18 Wed 11-04-18
Allocation of Duties to
Stakeholders
1 day Thu 12-04-18 Thu 12-04-18
Phase 3: Execution 31 days Fri 13-04-18 Fri 25-05-18
Prepare Project Roadmap 1 day Fri 13-04-18 Fri 13-04-18
Appoint Project Team 2 days Mon 16-04-18 Tue 17-04-18
Upgradation of System Hardware 4 days Wed 18-04-18 Mon 23-04-18
Installation of Necessary Software 3 days Tue 24-04-18 Thu 26-04-18
Develop Encryption System 10 days Fri 27-04-18 Thu 10-05-18
Selection of an Encryption
Technology
1 day Fri 23-03-18 Fri 23-03-18
Approval of the Project 1 day Mon 26-03-18 Mon 26-03-18
Appoint Stakeholders for Project 4 days Tue 27-03-18 Fri 30-03-18
Prepare Budget 2 days Mon 02-04-18 Tue 03-04-18
Prepare Final Project Plan 2 days Wed 04-04-18 Thu 05-04-18
Phase 2: Initiation 5 days Fri 06-04-18 Thu 12-04-18
Prepare Project Schedule 1 day Fri 06-04-18 Fri 06-04-18
Procure Budget for Project 3 days Mon 09-04-18 Wed 11-04-18
Allocation of Duties to
Stakeholders
1 day Thu 12-04-18 Thu 12-04-18
Phase 3: Execution 31 days Fri 13-04-18 Fri 25-05-18
Prepare Project Roadmap 1 day Fri 13-04-18 Fri 13-04-18
Appoint Project Team 2 days Mon 16-04-18 Tue 17-04-18
Upgradation of System Hardware 4 days Wed 18-04-18 Mon 23-04-18
Installation of Necessary Software 3 days Tue 24-04-18 Thu 26-04-18
Develop Encryption System 10 days Fri 27-04-18 Thu 10-05-18
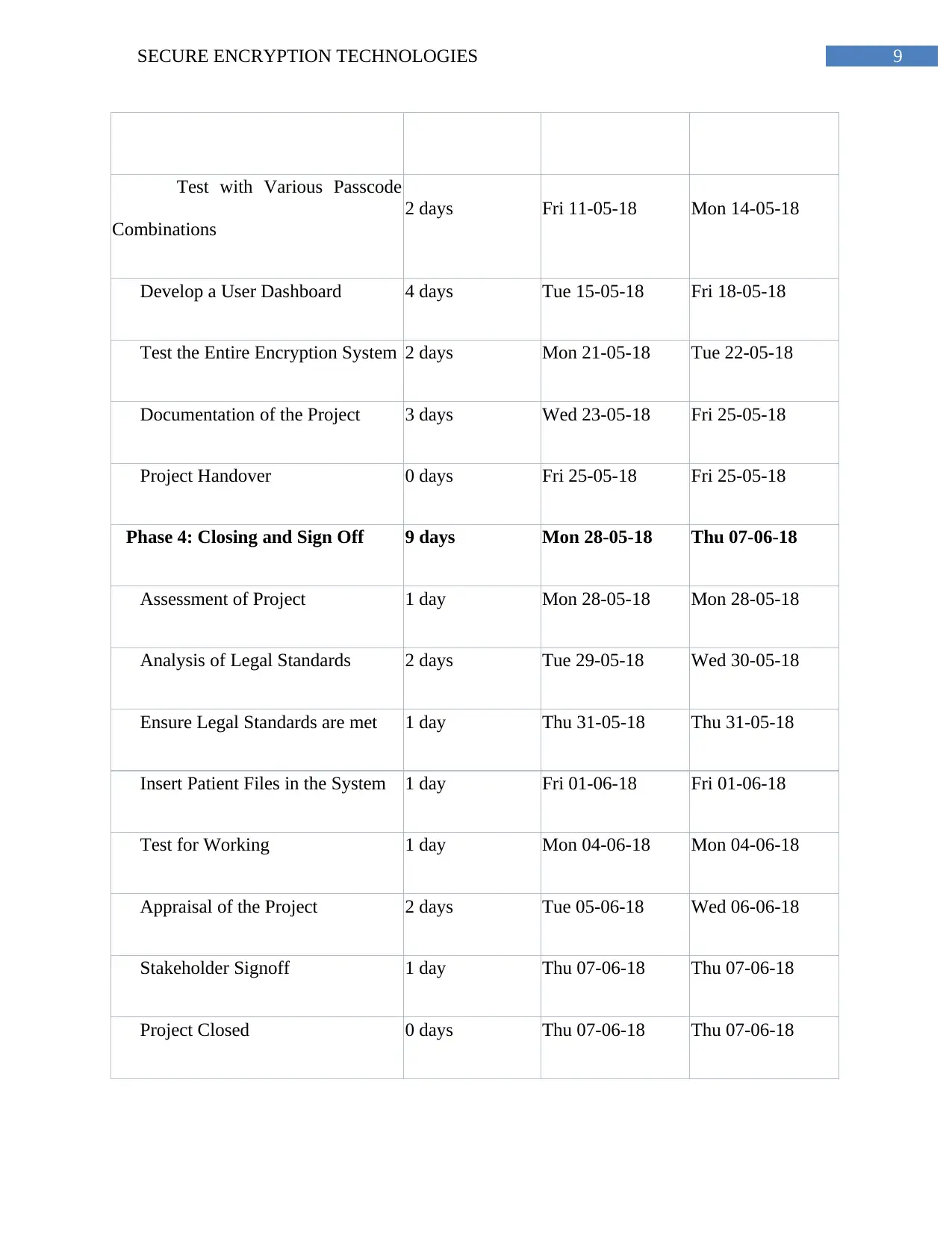
9SECURE ENCRYPTION TECHNOLOGIES
Test with Various Passcode
Combinations
2 days Fri 11-05-18 Mon 14-05-18
Develop a User Dashboard 4 days Tue 15-05-18 Fri 18-05-18
Test the Entire Encryption System 2 days Mon 21-05-18 Tue 22-05-18
Documentation of the Project 3 days Wed 23-05-18 Fri 25-05-18
Project Handover 0 days Fri 25-05-18 Fri 25-05-18
Phase 4: Closing and Sign Off 9 days Mon 28-05-18 Thu 07-06-18
Assessment of Project 1 day Mon 28-05-18 Mon 28-05-18
Analysis of Legal Standards 2 days Tue 29-05-18 Wed 30-05-18
Ensure Legal Standards are met 1 day Thu 31-05-18 Thu 31-05-18
Insert Patient Files in the System 1 day Fri 01-06-18 Fri 01-06-18
Test for Working 1 day Mon 04-06-18 Mon 04-06-18
Appraisal of the Project 2 days Tue 05-06-18 Wed 06-06-18
Stakeholder Signoff 1 day Thu 07-06-18 Thu 07-06-18
Project Closed 0 days Thu 07-06-18 Thu 07-06-18
Test with Various Passcode
Combinations
2 days Fri 11-05-18 Mon 14-05-18
Develop a User Dashboard 4 days Tue 15-05-18 Fri 18-05-18
Test the Entire Encryption System 2 days Mon 21-05-18 Tue 22-05-18
Documentation of the Project 3 days Wed 23-05-18 Fri 25-05-18
Project Handover 0 days Fri 25-05-18 Fri 25-05-18
Phase 4: Closing and Sign Off 9 days Mon 28-05-18 Thu 07-06-18
Assessment of Project 1 day Mon 28-05-18 Mon 28-05-18
Analysis of Legal Standards 2 days Tue 29-05-18 Wed 30-05-18
Ensure Legal Standards are met 1 day Thu 31-05-18 Thu 31-05-18
Insert Patient Files in the System 1 day Fri 01-06-18 Fri 01-06-18
Test for Working 1 day Mon 04-06-18 Mon 04-06-18
Appraisal of the Project 2 days Tue 05-06-18 Wed 06-06-18
Stakeholder Signoff 1 day Thu 07-06-18 Thu 07-06-18
Project Closed 0 days Thu 07-06-18 Thu 07-06-18
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10SECURE ENCRYPTION TECHNOLOGIES
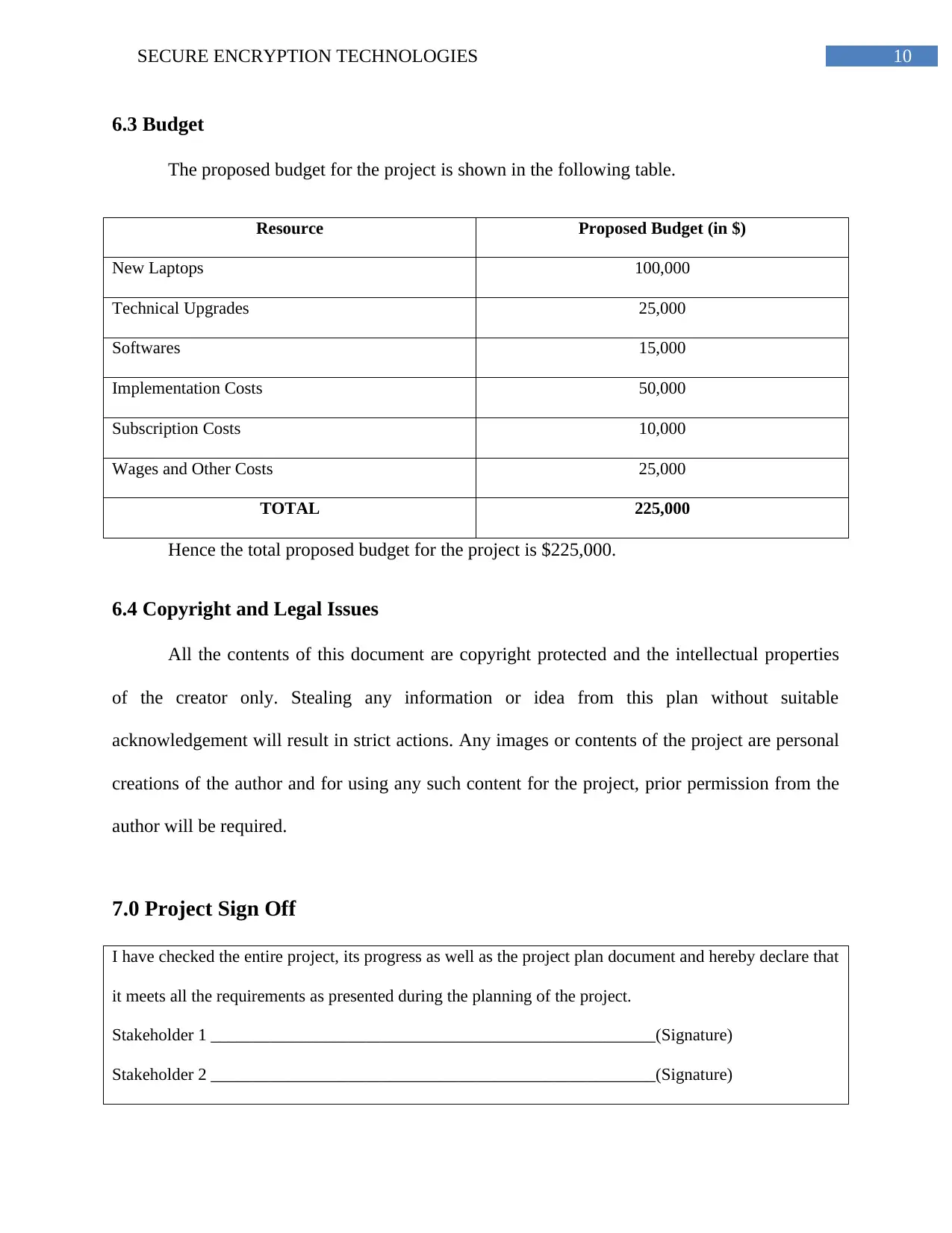
6.3 Budget
The proposed budget for the project is shown in the following table.
Resource Proposed Budget (in $)
New Laptops 100,000
Technical Upgrades 25,000
Softwares 15,000
Implementation Costs 50,000
Subscription Costs 10,000
Wages and Other Costs 25,000
TOTAL 225,000
Hence the total proposed budget for the project is $225,000.
6.4 Copyright and Legal Issues
All the contents of this document are copyright protected and the intellectual properties
of the creator only. Stealing any information or idea from this plan without suitable
acknowledgement will result in strict actions. Any images or contents of the project are personal
creations of the author and for using any such content for the project, prior permission from the
author will be required.
7.0 Project Sign Off
I have checked the entire project, its progress as well as the project plan document and hereby declare that
it meets all the requirements as presented during the planning of the project.
Stakeholder 1 ____________________________________________________(Signature)
Stakeholder 2 ____________________________________________________(Signature)
6.3 Budget
The proposed budget for the project is shown in the following table.
Resource Proposed Budget (in $)
New Laptops 100,000
Technical Upgrades 25,000
Softwares 15,000
Implementation Costs 50,000
Subscription Costs 10,000
Wages and Other Costs 25,000
TOTAL 225,000
Hence the total proposed budget for the project is $225,000.
6.4 Copyright and Legal Issues
All the contents of this document are copyright protected and the intellectual properties
of the creator only. Stealing any information or idea from this plan without suitable
acknowledgement will result in strict actions. Any images or contents of the project are personal
creations of the author and for using any such content for the project, prior permission from the
author will be required.
7.0 Project Sign Off
I have checked the entire project, its progress as well as the project plan document and hereby declare that
it meets all the requirements as presented during the planning of the project.
Stakeholder 1 ____________________________________________________(Signature)
Stakeholder 2 ____________________________________________________(Signature)

11SECURE ENCRYPTION TECHNOLOGIES
Stakeholder 3 ____________________________________________________(Signature)
Stakeholder 4 ____________________________________________________(Signature)
Stakeholder 5 ____________________________________________________(Signature)
Stakeholder 6 ____________________________________________________(Signature)
Stakeholder 7 ____________________________________________________(Signature)
Stakeholder 8 ____________________________________________________(Signature)
Date: ___________________________________________________________________
Stakeholder 3 ____________________________________________________(Signature)
Stakeholder 4 ____________________________________________________(Signature)
Stakeholder 5 ____________________________________________________(Signature)
Stakeholder 6 ____________________________________________________(Signature)
Stakeholder 7 ____________________________________________________(Signature)
Stakeholder 8 ____________________________________________________(Signature)
Date: ___________________________________________________________________

12SECURE ENCRYPTION TECHNOLOGIES
References
Boddy, A., Hurst, W., Mackay, M., & El Rhalibi, A. (2017). A Study into Data Analysis and
Visualisation to increase the Cyber-Resilience of Healthcare Infrastructures.
Dong, Q., Guan, Z. and Chen, Z., (2015, December). Attribute-based keyword search efficiency
enhancement via an online/offline approach. In Parallel and Distributed Systems
(ICPADS), 2015 IEEE 21st International Conference on (pp. 298-305). IEEE.
Fleming, Q. W., & Koppelman, J. M. (2016, December). Earned value project management.
Project Management Institute.
Fuller, M. A., Valacich, J. S., George, J. F., & Schneider, C. (2017). Information Systems Project
Management: A Process and Team Approach, Edition 1.1. Prospect Press.
Gupta, R., & Singh, R. K. (2015, August). An improved substitution method for data encryption
using DNA sequence and CDMB. In International Symposium on Security in Computing
and Communication (pp. 197-206). Springer, Cham.
Heagney, J. (2016). Fundamentals of project management. AMACOM Div American Mgmt
Assn.
Hohenberger, S., & Waters, B. (2014, March). Online/offline attribute-based encryption. In
International Workshop on Public Key Cryptography (pp. 293-310). Springer, Berlin,
Heidelberg.
Kerzner, H., & Kerzner, H. R. (2017). Project management: a systems approach to planning,
scheduling, and controlling. John Wiley & Sons.
References
Boddy, A., Hurst, W., Mackay, M., & El Rhalibi, A. (2017). A Study into Data Analysis and
Visualisation to increase the Cyber-Resilience of Healthcare Infrastructures.
Dong, Q., Guan, Z. and Chen, Z., (2015, December). Attribute-based keyword search efficiency
enhancement via an online/offline approach. In Parallel and Distributed Systems
(ICPADS), 2015 IEEE 21st International Conference on (pp. 298-305). IEEE.
Fleming, Q. W., & Koppelman, J. M. (2016, December). Earned value project management.
Project Management Institute.
Fuller, M. A., Valacich, J. S., George, J. F., & Schneider, C. (2017). Information Systems Project
Management: A Process and Team Approach, Edition 1.1. Prospect Press.
Gupta, R., & Singh, R. K. (2015, August). An improved substitution method for data encryption
using DNA sequence and CDMB. In International Symposium on Security in Computing
and Communication (pp. 197-206). Springer, Cham.
Heagney, J. (2016). Fundamentals of project management. AMACOM Div American Mgmt
Assn.
Hohenberger, S., & Waters, B. (2014, March). Online/offline attribute-based encryption. In
International Workshop on Public Key Cryptography (pp. 293-310). Springer, Berlin,
Heidelberg.
Kerzner, H., & Kerzner, H. R. (2017). Project management: a systems approach to planning,
scheduling, and controlling. John Wiley & Sons.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



