MITS5002 Cloud Computing: Encryption Algorithms for Data Security
VerifiedAdded on 2022/12/15
|13
|780
|167
Report
AI Summary
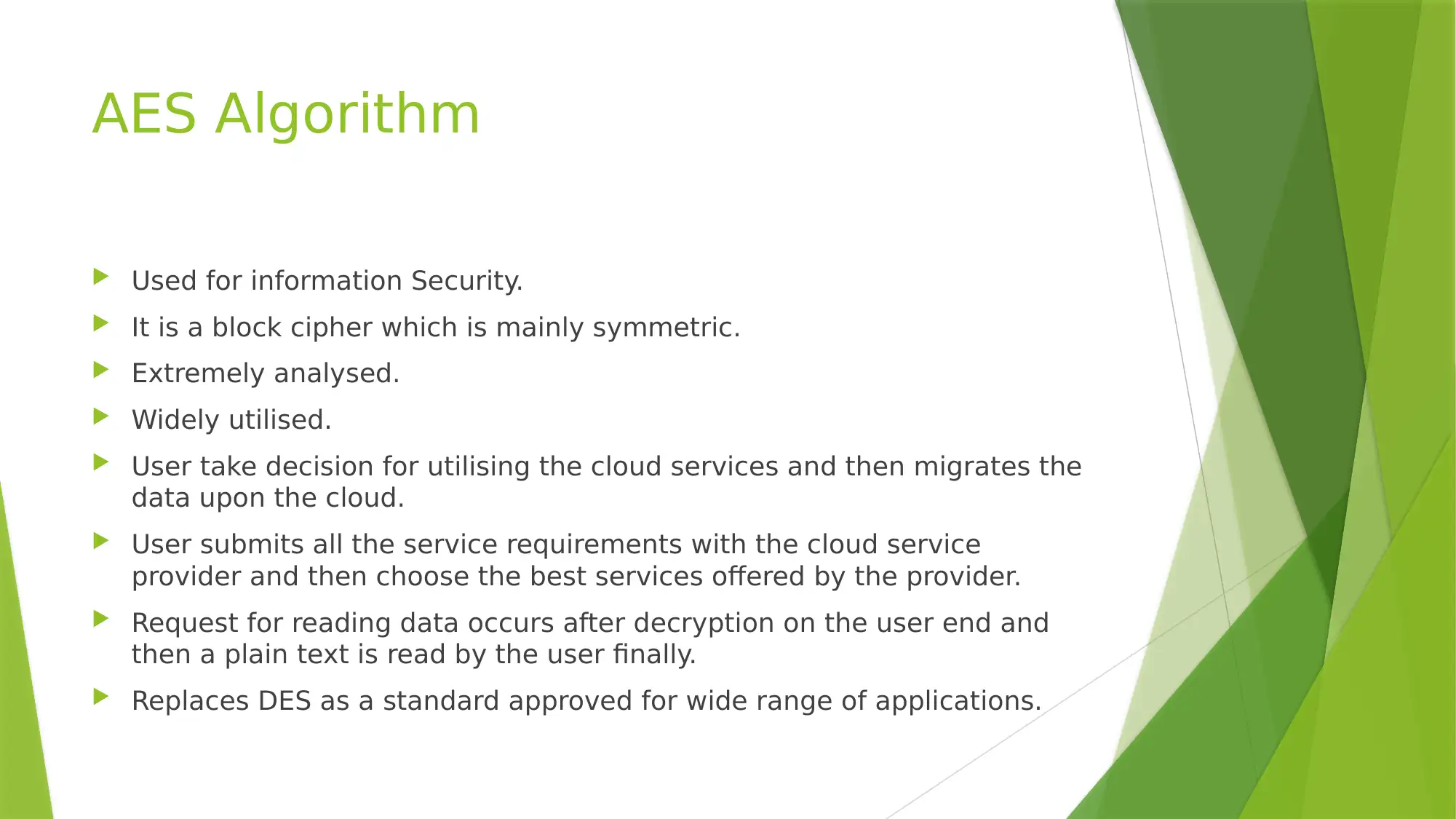
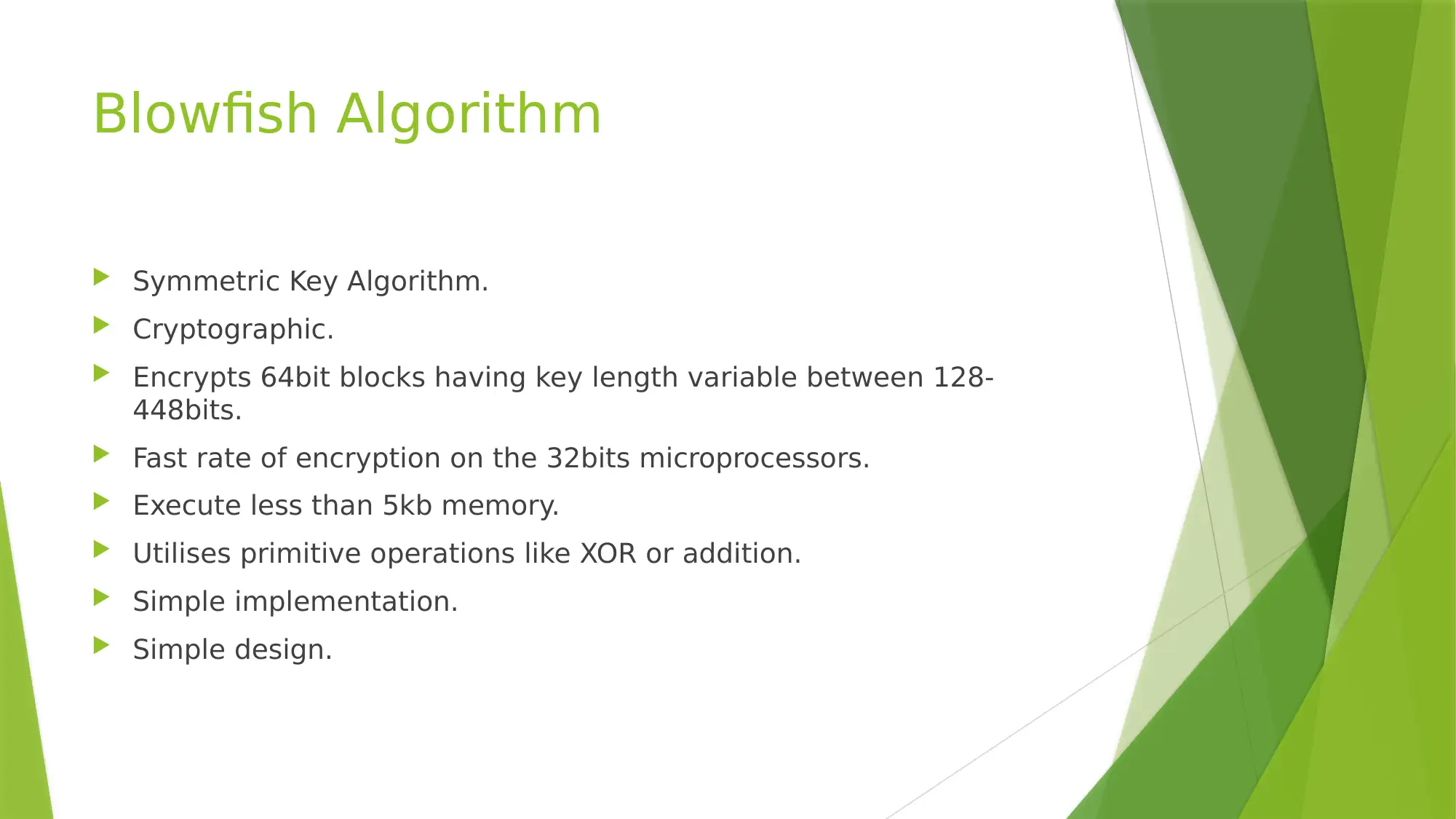
This report explores the critical aspects of securing user data within cloud computing environments. It begins by highlighting the transformative impact of cloud computing on IT and the challenges it presents, particularly concerning data security, ownership, and integrity. The report proposes the use of security algorithms to address these concerns, focusing on four key encryption methods: RSA, AES, DES, and Blowfish. It details the functionality of each algorithm, explaining how they contribute to data protection, user authentication, and secure data storage and retrieval. The report concludes by emphasizing the increasing importance of both cloud and user security, asserting that these algorithms play a crucial role in mitigating security risks and meeting current and future demands. References to relevant academic papers are provided to support the analysis.
1 out of 13














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)