Information Security: Designing Policies to Limit Damage - Report
VerifiedAdded on 2023/04/05
|14
|2209
|498
Report
AI Summary
This report comprehensively addresses information security, emphasizing policies designed to mitigate damage from both accidental and malicious users. The report begins by outlining the necessity of an Information Security Management System (ISMS), highlighting the ISO 27001 standard and its application to an IT company, Highlander Computing Solutions Limited. It then delves into physical security measures, discussing various physical attacks like theft and accidents, and proposes strategies to protect against them. The report further explores IT control and audit processes, including the role of certifications like ISO/IEC 27001 and the importance of cyber security insurance. It also examines the use of firewalls, intrusion detection systems (IDS), and ethical hacking as crucial components of a robust security framework. The report concludes by analyzing the security practices of DCSL Software, emphasizing the significance of GDPR compliance and the implementation of security policies to safeguard data and resources.
Running Head: Security 0
Security
Individual task
Student name
Security
Individual task
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security 1
Answer 1:
Information Security Management System (ISMS) is necessary to secure an Information System.
Different issues arise in security of Information System. Therefore, it is necessary to secure
Information System form different types of security risks. ISO 27001 is an international standard
to secure organizations from many types of security issues because of vulnerabilities of system
(iso27001security.com, 2019).
Highlander Computing Solutions Limited is an IT company, which is provides solutions to
different clients for their security related to data (highlanderuk.com, 2019). It is a common thing
in present world that organization follows security standards to manage different things as well
as protect from huge risks to the organization. It is necessary to establish security policy to avoid
risks to information assets of the organization.
Highlander Computing Solutions Limited is having ISO 27001 certification to secure their
different resources. Information System (IS) of any organization is a backbone of that
organization. Therefore, there should be proper security policy to avoid risks, and if any risk
occurred in the system then there is a solution for that particular risk ( Giandomenico & Groot,
2018).
Highlander Computing Solutions Limited is having responsibility of different client’s data and
security of their products and services from cyber-attacks. Physical security is necessary to
Information System because of many security reasons. Information Systems is having different
devices for connectivity and data transfer. Therefore, there should be high and tight security
maintained by the organization (pressbooks.com, 2019).
Some security rules are here:
1. No one can enter without permission
2. Access level should be there for security purposes
3. Proper damage recovery
4. Internal and external people take entry with all the procedure
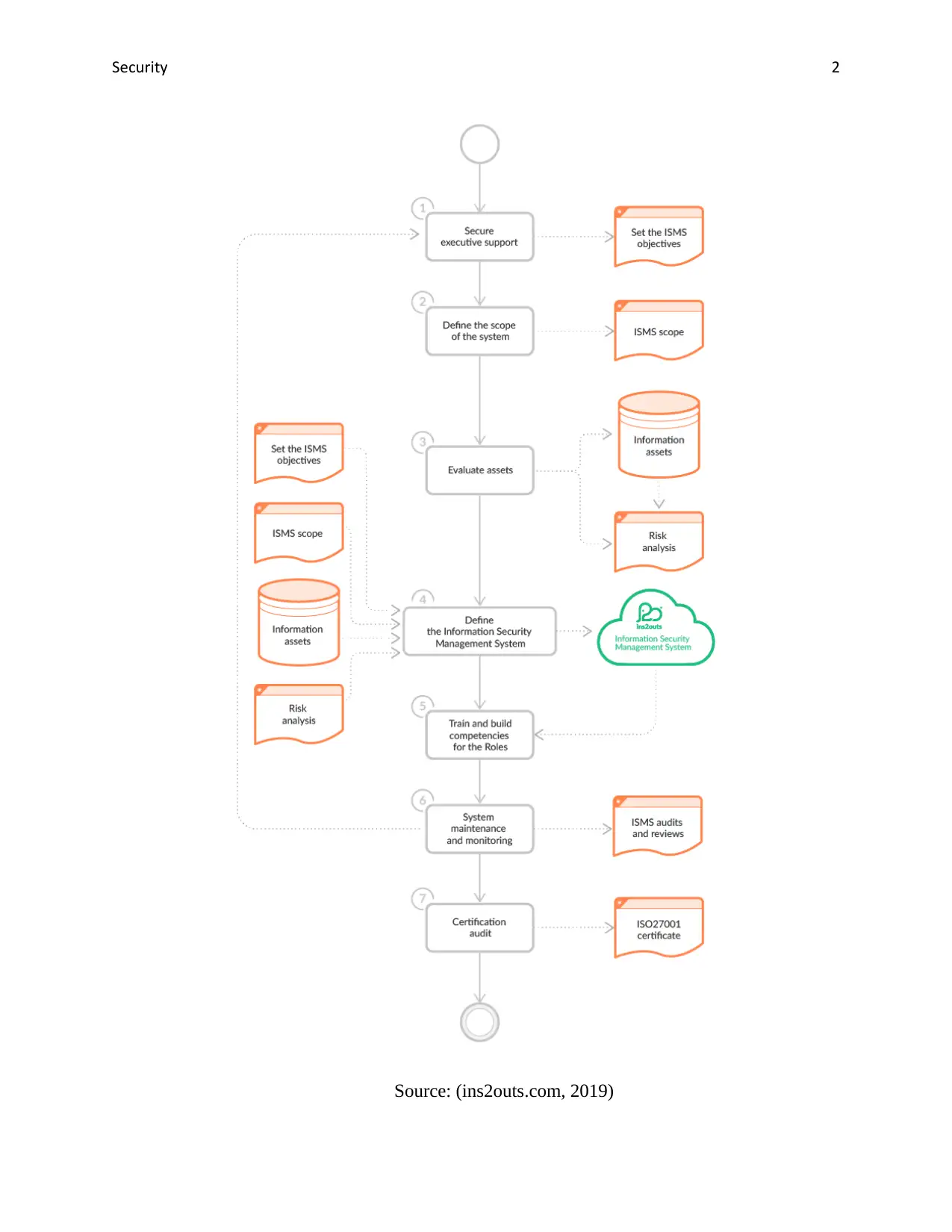
In below figure a process of ISMS system implementation is shows.
Answer 1:
Information Security Management System (ISMS) is necessary to secure an Information System.
Different issues arise in security of Information System. Therefore, it is necessary to secure
Information System form different types of security risks. ISO 27001 is an international standard
to secure organizations from many types of security issues because of vulnerabilities of system
(iso27001security.com, 2019).
Highlander Computing Solutions Limited is an IT company, which is provides solutions to
different clients for their security related to data (highlanderuk.com, 2019). It is a common thing
in present world that organization follows security standards to manage different things as well
as protect from huge risks to the organization. It is necessary to establish security policy to avoid
risks to information assets of the organization.
Highlander Computing Solutions Limited is having ISO 27001 certification to secure their
different resources. Information System (IS) of any organization is a backbone of that
organization. Therefore, there should be proper security policy to avoid risks, and if any risk
occurred in the system then there is a solution for that particular risk ( Giandomenico & Groot,
2018).
Highlander Computing Solutions Limited is having responsibility of different client’s data and
security of their products and services from cyber-attacks. Physical security is necessary to
Information System because of many security reasons. Information Systems is having different
devices for connectivity and data transfer. Therefore, there should be high and tight security
maintained by the organization (pressbooks.com, 2019).
Some security rules are here:
1. No one can enter without permission
2. Access level should be there for security purposes
3. Proper damage recovery
4. Internal and external people take entry with all the procedure
In below figure a process of ISMS system implementation is shows.
Security 2
Source: (ins2outs.com, 2019)
Source: (ins2outs.com, 2019)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security 3
Answer 2:
Physical attacks are common in the information. However, physical attacks are also damage the
business of an organization. Backup data is necessary to business continuity. Therefore, it is
necessary to provide full physical protection to the information system as well as backup
services. There are few types of physical attacks and their solutions (DCSL, 2018).
Theft
The loss of important hardware, software, or data can have significant effects on an
organization’s effectiveness .Theft can be divided into three basic categories: physical theft, data
theft, and identity theft (NCSC, 2019).
Hardware is an important part of an information system. Therefore, it is require a high security
system that protect IS from unauthorized access. It is compulsory to create lock system to all the
hardware parts of an Information System. Damages of hardware can make significant effects on
effectiveness of an organization.
Criminals can theft the hardware, such as hard disk, RAM, processor, any many other things of a
computer system, because of their small size and high cost. Physical theft results in the loss of
data stored on the hard drives of information system. Because of physical theft, organization can
face loss of confidentiality and reliability of users. Therefore, it is necessary to secure physical
devices through wall and locks in a building. Server is always in custody of human being as well
as mechanical locks (risk.net, 2018).
Accidents
Accidents are major issues in front of organization and their information system. It has
happened, because of human errors. Ignorance of the security can convert into accidents most of
time. Therefore, it is necessary to secure the premises of information system’s hardware. It is
necessary to have a security channel to enter in the premises. Without purpose no one can entry
in that premises. It can avoid accidents and provide more security to the system ( Giandomenico
& Groot, 2018).
Answer 2:
Physical attacks are common in the information. However, physical attacks are also damage the
business of an organization. Backup data is necessary to business continuity. Therefore, it is
necessary to provide full physical protection to the information system as well as backup
services. There are few types of physical attacks and their solutions (DCSL, 2018).
Theft
The loss of important hardware, software, or data can have significant effects on an
organization’s effectiveness .Theft can be divided into three basic categories: physical theft, data
theft, and identity theft (NCSC, 2019).
Hardware is an important part of an information system. Therefore, it is require a high security
system that protect IS from unauthorized access. It is compulsory to create lock system to all the
hardware parts of an Information System. Damages of hardware can make significant effects on
effectiveness of an organization.
Criminals can theft the hardware, such as hard disk, RAM, processor, any many other things of a
computer system, because of their small size and high cost. Physical theft results in the loss of
data stored on the hard drives of information system. Because of physical theft, organization can
face loss of confidentiality and reliability of users. Therefore, it is necessary to secure physical
devices through wall and locks in a building. Server is always in custody of human being as well
as mechanical locks (risk.net, 2018).
Accidents
Accidents are major issues in front of organization and their information system. It has
happened, because of human errors. Ignorance of the security can convert into accidents most of
time. Therefore, it is necessary to secure the premises of information system’s hardware. It is
necessary to have a security channel to enter in the premises. Without purpose no one can entry
in that premises. It can avoid accidents and provide more security to the system ( Giandomenico
& Groot, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security 4
Answer 3:
IT control and audit process are different processes and they are having some similarity to
complete it. Both IT control and audit process are used to secure information system of an
organization. It is necessary to secure information system through risk analysis and other
processes. Audit process can be used for finding vulnerabilities of the information system.
Therefore, organization can make a control list to reduce vulnerabilities. They should have
control to handle each issue of the information system (ICAEW, 2016).
The UK government is having some security certification to protect the organization from cyber-
attacks. It is affecting the economy of the country. ISO/IEC 27001 is a certification, which has
provided by registered companies to those organizations that fulfill all the security levels.
IT insurance coverage is based on the data loss, restoration, data breach, and legal actions, such
as cyber-insurance. It is related to the information technology infrastructure security and its
activities. Data breach insurance is useful to mitigate the risk of penalties and civil litigation. It
provides access to assistance by professionals of IT, which can provide help in businesses
comply with applicable laws and regulations (sahouri.com, 2019).
Cyber security insurance is covering all these things to secure all the data of an organization. It is
also provide help to organization to overcome risks of cyber-attacks (AIG, 2019).
Answer 3:
IT control and audit process are different processes and they are having some similarity to
complete it. Both IT control and audit process are used to secure information system of an
organization. It is necessary to secure information system through risk analysis and other
processes. Audit process can be used for finding vulnerabilities of the information system.
Therefore, organization can make a control list to reduce vulnerabilities. They should have
control to handle each issue of the information system (ICAEW, 2016).
The UK government is having some security certification to protect the organization from cyber-
attacks. It is affecting the economy of the country. ISO/IEC 27001 is a certification, which has
provided by registered companies to those organizations that fulfill all the security levels.
IT insurance coverage is based on the data loss, restoration, data breach, and legal actions, such
as cyber-insurance. It is related to the information technology infrastructure security and its
activities. Data breach insurance is useful to mitigate the risk of penalties and civil litigation. It
provides access to assistance by professionals of IT, which can provide help in businesses
comply with applicable laws and regulations (sahouri.com, 2019).
Cyber security insurance is covering all these things to secure all the data of an organization. It is
also provide help to organization to overcome risks of cyber-attacks (AIG, 2019).

Security 5
Answer 4:
Insurance companies are providing full coverage of all the losses though legal laws and
regulations. They are having some standards to secure the organization. Therefore, they cannot
have any type of risk and security issues in their information system. For providing insurance,
they should require some basic arrangement by the organization, such as firewalls and IDS
(instruction detention systems). All the insurance companies are having risk. In case of IT
industry, there is new threats are occur because of some mistakes. In few cases same risks were
introduced, which can easily handle by the firewalls (risk.net, 2018).
Risk management program is used to find out vulnerabilities of the information system. It will
provide all the threats of the system. Therefore, administrator can design proper control to
mitigate the risks of information system. In addition, it is a complex process to mitigate risks of
the information system (Scognamiglio , 2015).
Firewalls are best thing to mitigate all the risks of information system. It checks all the access
from outside and inside on the system. Therefore, no one can access the unauthorized services of
the information system. Risk management process is providing benefits to the organization as
well as insurance company (Senft & Gallegos, 2010).
Insurance is necessary to secure resources of the organization. Data of an organization is having
a huge value for them. Therefore, it is necessary to secure that data.
Answer 4:
Insurance companies are providing full coverage of all the losses though legal laws and
regulations. They are having some standards to secure the organization. Therefore, they cannot
have any type of risk and security issues in their information system. For providing insurance,
they should require some basic arrangement by the organization, such as firewalls and IDS
(instruction detention systems). All the insurance companies are having risk. In case of IT
industry, there is new threats are occur because of some mistakes. In few cases same risks were
introduced, which can easily handle by the firewalls (risk.net, 2018).
Risk management program is used to find out vulnerabilities of the information system. It will
provide all the threats of the system. Therefore, administrator can design proper control to
mitigate the risks of information system. In addition, it is a complex process to mitigate risks of
the information system (Scognamiglio , 2015).
Firewalls are best thing to mitigate all the risks of information system. It checks all the access
from outside and inside on the system. Therefore, no one can access the unauthorized services of
the information system. Risk management process is providing benefits to the organization as
well as insurance company (Senft & Gallegos, 2010).
Insurance is necessary to secure resources of the organization. Data of an organization is having
a huge value for them. Therefore, it is necessary to secure that data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Security 6
Answer 5:
Many devices have used to protect the information system. It is a process in which different
mechanism are applied on the networking devices. Therefore, no one can easily access the
system without authentication. Firewalls and instruction detection systems are highly used for
security of the network and information system. Both are preventing unauthorized access
between information system and computer networks (Yadav, 2018).
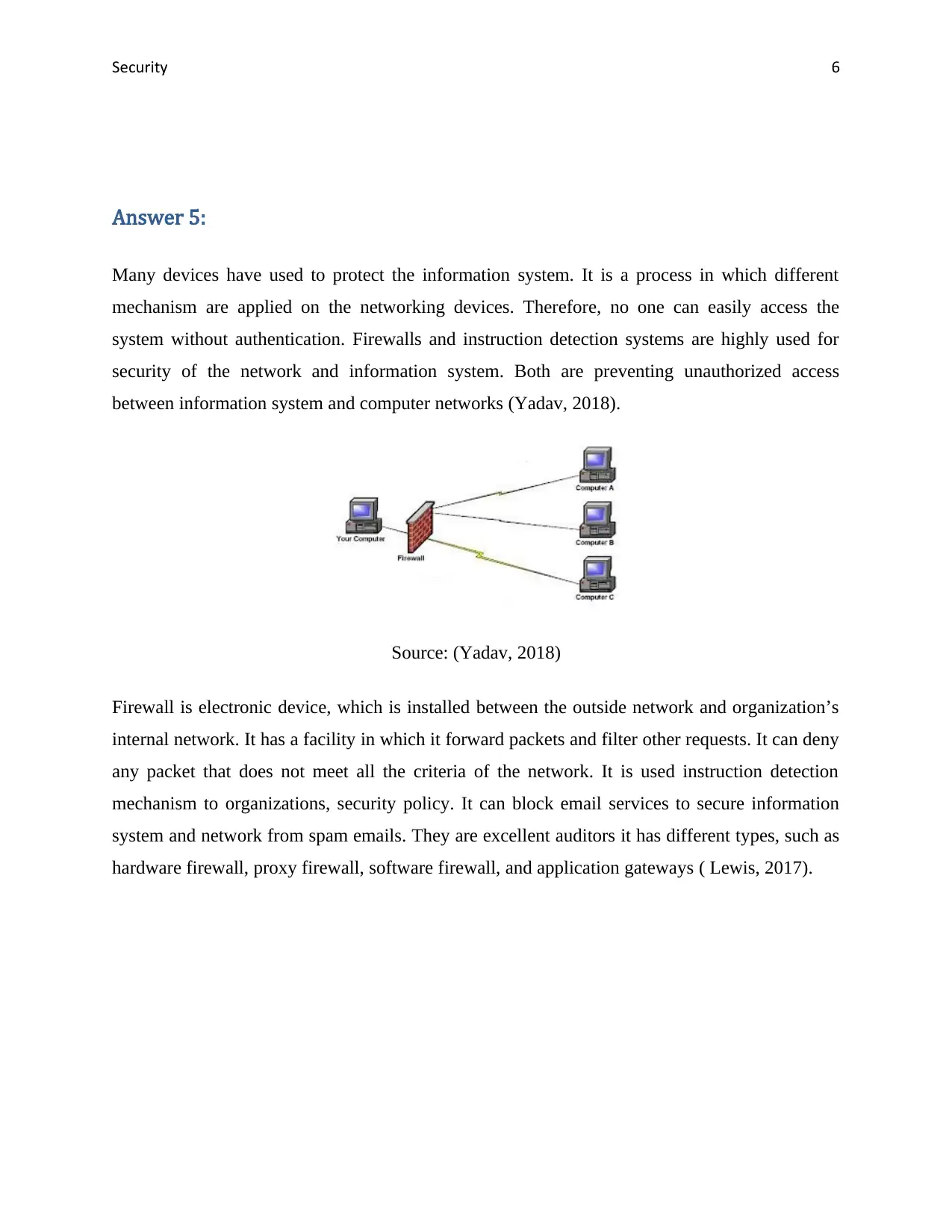
Source: (Yadav, 2018)
Firewall is electronic device, which is installed between the outside network and organization’s
internal network. It has a facility in which it forward packets and filter other requests. It can deny
any packet that does not meet all the criteria of the network. It is used instruction detection
mechanism to organizations, security policy. It can block email services to secure information
system and network from spam emails. They are excellent auditors it has different types, such as
hardware firewall, proxy firewall, software firewall, and application gateways ( Lewis, 2017).
Answer 5:
Many devices have used to protect the information system. It is a process in which different
mechanism are applied on the networking devices. Therefore, no one can easily access the
system without authentication. Firewalls and instruction detection systems are highly used for
security of the network and information system. Both are preventing unauthorized access
between information system and computer networks (Yadav, 2018).
Source: (Yadav, 2018)
Firewall is electronic device, which is installed between the outside network and organization’s
internal network. It has a facility in which it forward packets and filter other requests. It can deny
any packet that does not meet all the criteria of the network. It is used instruction detection
mechanism to organizations, security policy. It can block email services to secure information
system and network from spam emails. They are excellent auditors it has different types, such as
hardware firewall, proxy firewall, software firewall, and application gateways ( Lewis, 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Security 7
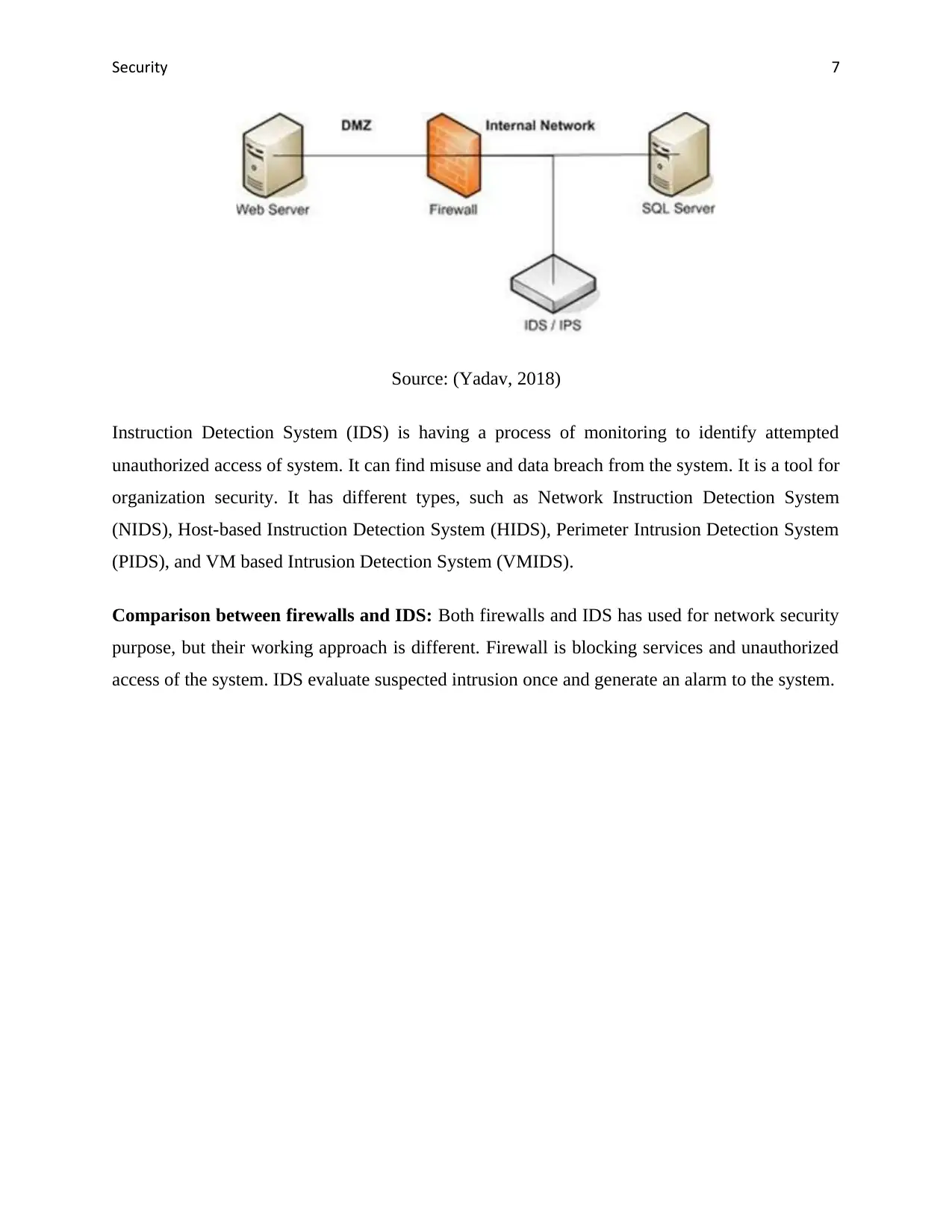
Source: (Yadav, 2018)
Instruction Detection System (IDS) is having a process of monitoring to identify attempted
unauthorized access of system. It can find misuse and data breach from the system. It is a tool for
organization security. It has different types, such as Network Instruction Detection System
(NIDS), Host-based Instruction Detection System (HIDS), Perimeter Intrusion Detection System
(PIDS), and VM based Intrusion Detection System (VMIDS).
Comparison between firewalls and IDS: Both firewalls and IDS has used for network security
purpose, but their working approach is different. Firewall is blocking services and unauthorized
access of the system. IDS evaluate suspected intrusion once and generate an alarm to the system.
Source: (Yadav, 2018)
Instruction Detection System (IDS) is having a process of monitoring to identify attempted
unauthorized access of system. It can find misuse and data breach from the system. It is a tool for
organization security. It has different types, such as Network Instruction Detection System
(NIDS), Host-based Instruction Detection System (HIDS), Perimeter Intrusion Detection System
(PIDS), and VM based Intrusion Detection System (VMIDS).
Comparison between firewalls and IDS: Both firewalls and IDS has used for network security
purpose, but their working approach is different. Firewall is blocking services and unauthorized
access of the system. IDS evaluate suspected intrusion once and generate an alarm to the system.
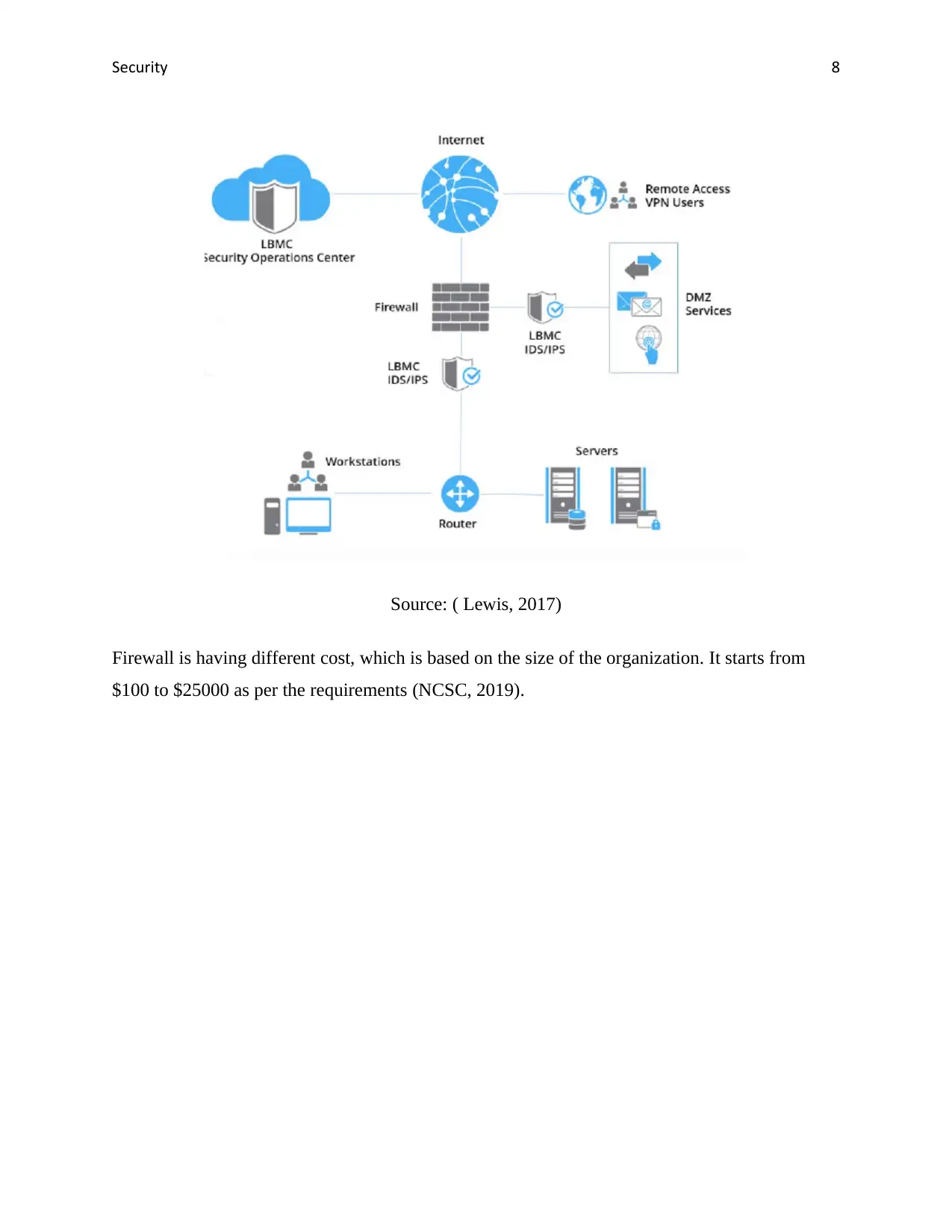
Security 8
Source: ( Lewis, 2017)
Firewall is having different cost, which is based on the size of the organization. It starts from
$100 to $25000 as per the requirements (NCSC, 2019).
Source: ( Lewis, 2017)
Firewall is having different cost, which is based on the size of the organization. It starts from
$100 to $25000 as per the requirements (NCSC, 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security 9
Answer 6:
Ethical hacking is a process in which a person is having responsibilities to secure own system
from cyber-attacks through different tools and mechanisms. Ethical hacker is uses tools for
access the port and data of own system and other systems, such as Nmap. Ethical hacker can
avoid all the security essentials, which are created for system security. It is an ethical process to
secure system. They can break firewall, IDS, IPS, web server, and its applications (cybrary,
2019).
Ethical hacking is legal process in which teacher can provide hacking techniques to the students
to secure their system from such types of things. It can be possible to teach students about
hacking techniques. All the process of security is ethical, as they are used for security purpose.
Ethical hacker is a person that provides changes in the security policies and working process of
the system (Meredith , 2018).
Ethical hacking is legal as it is a process of checking the unauthorized access of own system.
Ethical hacker uses different techniques for hacking those system, which are attempt an
unauthorized access ( Rivas, 2018).
Ethical hacker should report about their finding to the top management for required changes in
the security system.
Graduate students can get the certification of ethical hacker in which they should clear an
examination, which is having 200 multiple questions. ( Hopping, 2019)
Answer 6:
Ethical hacking is a process in which a person is having responsibilities to secure own system
from cyber-attacks through different tools and mechanisms. Ethical hacker is uses tools for
access the port and data of own system and other systems, such as Nmap. Ethical hacker can
avoid all the security essentials, which are created for system security. It is an ethical process to
secure system. They can break firewall, IDS, IPS, web server, and its applications (cybrary,
2019).
Ethical hacking is legal process in which teacher can provide hacking techniques to the students
to secure their system from such types of things. It can be possible to teach students about
hacking techniques. All the process of security is ethical, as they are used for security purpose.
Ethical hacker is a person that provides changes in the security policies and working process of
the system (Meredith , 2018).
Ethical hacking is legal as it is a process of checking the unauthorized access of own system.
Ethical hacker uses different techniques for hacking those system, which are attempt an
unauthorized access ( Rivas, 2018).
Ethical hacker should report about their finding to the top management for required changes in
the security system.
Graduate students can get the certification of ethical hacker in which they should clear an
examination, which is having 200 multiple questions. ( Hopping, 2019)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security 10
Answer 7:
DCSL Software is a leading software development country of United Kingdom. They are design
web applications, mobile apps, and many other services to their clients. It has business with
many leading companies, such as Virgin Media, NHS, IKEA, BT, and many others.
In 2018, UK’s government changes the EU Data Protection Directive from the EU General Data
Protection Regulation (GDPR). DCSL is certified with the ISO/IEC 27001, which is a certificate
to ensure about the security of data and other resources. DCSL is having an IT security
certificate because it is having a responsibility to secure data of their clients as well as DCSL
data. DCSL is also having a responsibility to provide security to their products and services.
Security standards are responsible to secure the whole system from cyber-attacks (DCSL, 2018).
GDPR is latest criteria to secure the information system as well as other operations and resources
of the organization. It is a necessary thing to complete the IT audit and find the risks of the
system and design proper controls for those risk mitigation. It is a common issue that
organization should have controls to mitigate raised risk in the system.
DCSL is having their own security policies to overcome the risks of the information system.
They design their system according GDPR policies (DCSLSOFTWARE, 2019).
Security policies are having different things to secure resources as well as all the operations of
organization (export.gov, 2019). UK is having government agencies, which are provide security
to the various companies (NCSC, 2019).
Answer 7:
DCSL Software is a leading software development country of United Kingdom. They are design
web applications, mobile apps, and many other services to their clients. It has business with
many leading companies, such as Virgin Media, NHS, IKEA, BT, and many others.
In 2018, UK’s government changes the EU Data Protection Directive from the EU General Data
Protection Regulation (GDPR). DCSL is certified with the ISO/IEC 27001, which is a certificate
to ensure about the security of data and other resources. DCSL is having an IT security
certificate because it is having a responsibility to secure data of their clients as well as DCSL
data. DCSL is also having a responsibility to provide security to their products and services.
Security standards are responsible to secure the whole system from cyber-attacks (DCSL, 2018).
GDPR is latest criteria to secure the information system as well as other operations and resources
of the organization. It is a necessary thing to complete the IT audit and find the risks of the
system and design proper controls for those risk mitigation. It is a common issue that
organization should have controls to mitigate raised risk in the system.
DCSL is having their own security policies to overcome the risks of the information system.
They design their system according GDPR policies (DCSLSOFTWARE, 2019).
Security policies are having different things to secure resources as well as all the operations of
organization (export.gov, 2019). UK is having government agencies, which are provide security
to the various companies (NCSC, 2019).

Security 11
References
Giandomenico, N. & Groot, J. d., 2018. Insider vs. Outsider Data Security Threats: What’s the
Greater Risk?. [Online]
Available at: https://digitalguardian.com/blog/insider-outsider-data-security-threats
[Accessed 9 March 2019].
Hopping, C., 2019. How do you become an ethical hacker?. [Online]
Available at: https://www.itpro.co.uk/641470/so-you-want-to-be-an-ethical-hacker
[Accessed 14 March 2019].
Lewis, . T., 2017. IDS and IPS 101: How Each System Works and Why You Need Them. [Online]
Available at: https://www.lbmc.com/blog/ids-ips-101-how-each-system-works
[Accessed 14 March 2019].
Rivas, G., 2018. Pentesting: The Ethical Hacking at the service of vulnerability detection.
[Online]
Available at: https://www.gb-advisors.com/pentesting-2/
[Accessed 14 March 2019].
AIG, 2019. Communications, Media & Technology. [Online]
Available at: https://www.aig.co.uk/business/industries/technology
[Accessed 14 March 2019].
cybrary, 2019. Responsibilities of Ethical Hackers. [Online]
Available at: https://www.cybrary.it/cybrary-0p3n/ethical-hacking/responsibilities-of-ethical-
hackers/
[Accessed 14 March 2019].
DCSL, 2018. General Data Protection Regulation (GDPR). [Online]
Available at: https://www.dcslsoftware.com/general-data-protection-regulation-gdpr/
[Accessed 14 March 2019].
References
Giandomenico, N. & Groot, J. d., 2018. Insider vs. Outsider Data Security Threats: What’s the
Greater Risk?. [Online]
Available at: https://digitalguardian.com/blog/insider-outsider-data-security-threats
[Accessed 9 March 2019].
Hopping, C., 2019. How do you become an ethical hacker?. [Online]
Available at: https://www.itpro.co.uk/641470/so-you-want-to-be-an-ethical-hacker
[Accessed 14 March 2019].
Lewis, . T., 2017. IDS and IPS 101: How Each System Works and Why You Need Them. [Online]
Available at: https://www.lbmc.com/blog/ids-ips-101-how-each-system-works
[Accessed 14 March 2019].
Rivas, G., 2018. Pentesting: The Ethical Hacking at the service of vulnerability detection.
[Online]
Available at: https://www.gb-advisors.com/pentesting-2/
[Accessed 14 March 2019].
AIG, 2019. Communications, Media & Technology. [Online]
Available at: https://www.aig.co.uk/business/industries/technology
[Accessed 14 March 2019].
cybrary, 2019. Responsibilities of Ethical Hackers. [Online]
Available at: https://www.cybrary.it/cybrary-0p3n/ethical-hacking/responsibilities-of-ethical-
hackers/
[Accessed 14 March 2019].
DCSL, 2018. General Data Protection Regulation (GDPR). [Online]
Available at: https://www.dcslsoftware.com/general-data-protection-regulation-gdpr/
[Accessed 14 March 2019].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





