Security and Privacy Issues in IoT
VerifiedAdded on 2023/01/13
|16
|5849
|49
AI Summary
This document discusses the security and privacy issues in IoT, specifically in the context of smart environment, smart transport, smart healthcare system, and smart city. It explores the challenges and vulnerabilities in these areas and provides solutions to address them. The document also highlights the importance of confidentiality, integrity, and availability in smart transport and discusses the privacy concerns in the same. Overall, it provides insights into the security and privacy aspects of IoT.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Security and Privacy Issues in
IoT
IoT
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction......................................................................................................................................1
Smart Environment..........................................................................................................................2
Smart & Privacy Issues in Smart Environment...............................................................................3
Smart Transport /Traffic System.....................................................................................................3
Smart transport / traffic system....................................................................................................3
Smart transport / traffic architecture:...........................................................................................3
Smart Health Care System...............................................................................................................6
Architecture.................................................................................................................................6
Security issues.............................................................................................................................7
Privacy issues...............................................................................................................................8
Solution for issues........................................................................................................................8
Smart City........................................................................................................................................9
Smart City architecture................................................................................................................9
Security issues in smart city......................................................................................................10
Privacy issues in smart city........................................................................................................11
Solution of discussed security and privacy issues of smart city................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
Introduction......................................................................................................................................1
Smart Environment..........................................................................................................................2
Smart & Privacy Issues in Smart Environment...............................................................................3
Smart Transport /Traffic System.....................................................................................................3
Smart transport / traffic system....................................................................................................3
Smart transport / traffic architecture:...........................................................................................3
Smart Health Care System...............................................................................................................6
Architecture.................................................................................................................................6
Security issues.............................................................................................................................7
Privacy issues...............................................................................................................................8
Solution for issues........................................................................................................................8
Smart City........................................................................................................................................9
Smart City architecture................................................................................................................9
Security issues in smart city......................................................................................................10
Privacy issues in smart city........................................................................................................11
Solution of discussed security and privacy issues of smart city................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13

Introduction
The internet of things refers to system of interconnected computing devices, digital and
mechanical machines, animals, people or objects which are being rendered with unique
identifiers as well as possess ability for transferring data over network without any kind of
human-to-computer or human-to-human interaction (Al‐Turjman, Zahmatkesh and Shahroze,
2019). It is a concept of interconnecting devices to internet and with other devices. It illustrates a
giant network for connected people as well as things all of which data is being collected and
sharing data related with way they are being utilised. They are being embedded with software,
sensor and other technologies for exchange of data with other systems and devices. Technology
connecting things to internet are accomplished through the existence of three components: they
include analytics & applications, connection & infrastructure and physical devices & sensors.
There are various challenges which have to be accomplished for encouraging higher
growth rate of IoT and furnish opportunities for having competencies along with capacities. They
are infrastructure (smart cities, intelligent transport system, ubiquitous health care and many
others), data & information, security & privacy and ecosystem. It is necessary to acknowledge all
these challenges in an effectual manner so that desired results can be attained (Alhalafi and
Veeraraghavan, 2019). When interconnected devices join IoT ecosystem then wide range of
security tests are applied for exposing IoT vulnerabilities to ensure that security aspects are
known. The major threats with respect to this involves: threat posed through compromised
devices, communication link and master. In order to ensure integrity when data is in-transit while
travelling through IoT cloud hosting, it has to be encrypted within the network layer for
prevention of interception. In addition to this, stored data must be in active-active mode and to
avoid data theft seamlessly encryption can be applied. An IoT application denotes prebuilt SaaS
apps which are liable for analysing and presenting sensor data to business users through
dashboards.
Smart environment refers to link with computers and other smart devices with respect to
everyday settings as well as tasks. It is crucial to identify the loopholes along with challenges so
that appropriate security measures and policies can be formulated with respect to that. This
report comprises of security and privacy aspects associated with smart environment along with
smart transport, smart healthcare system and smart city. Along with this, each will be discussed
1
The internet of things refers to system of interconnected computing devices, digital and
mechanical machines, animals, people or objects which are being rendered with unique
identifiers as well as possess ability for transferring data over network without any kind of
human-to-computer or human-to-human interaction (Al‐Turjman, Zahmatkesh and Shahroze,
2019). It is a concept of interconnecting devices to internet and with other devices. It illustrates a
giant network for connected people as well as things all of which data is being collected and
sharing data related with way they are being utilised. They are being embedded with software,
sensor and other technologies for exchange of data with other systems and devices. Technology
connecting things to internet are accomplished through the existence of three components: they
include analytics & applications, connection & infrastructure and physical devices & sensors.
There are various challenges which have to be accomplished for encouraging higher
growth rate of IoT and furnish opportunities for having competencies along with capacities. They
are infrastructure (smart cities, intelligent transport system, ubiquitous health care and many
others), data & information, security & privacy and ecosystem. It is necessary to acknowledge all
these challenges in an effectual manner so that desired results can be attained (Alhalafi and
Veeraraghavan, 2019). When interconnected devices join IoT ecosystem then wide range of
security tests are applied for exposing IoT vulnerabilities to ensure that security aspects are
known. The major threats with respect to this involves: threat posed through compromised
devices, communication link and master. In order to ensure integrity when data is in-transit while
travelling through IoT cloud hosting, it has to be encrypted within the network layer for
prevention of interception. In addition to this, stored data must be in active-active mode and to
avoid data theft seamlessly encryption can be applied. An IoT application denotes prebuilt SaaS
apps which are liable for analysing and presenting sensor data to business users through
dashboards.
Smart environment refers to link with computers and other smart devices with respect to
everyday settings as well as tasks. It is crucial to identify the loopholes along with challenges so
that appropriate security measures and policies can be formulated with respect to that. This
report comprises of security and privacy aspects associated with smart environment along with
smart transport, smart healthcare system and smart city. Along with this, each will be discussed
1

in context of security and privacy issues. Furthermore, solutions for handling those are being
mentioned. A brief overview will be provided with respect to these three concepts.
Smart Environment
Envisions of future in which multitude of systems are seamlessly embedded within day to day
objects of physical world is referred to as smart environment. This comprises of all kind of smart
world activities which involves continuous working for making lives of inhabitants much more
comfortable (Alloghani and et. al, 2020). It is an intelligent agent which perceives state of
resident as well as physical surroundings through the usage of sensors as well as acts on
environment by making use of controllers in such a way that peculiar performance measures are
being optimised. The designing of smart environment software algorithms leads to track location
as well as activities associated with hazardous conditions. Smart environments can be captured
by making use of distinct media on the basis of target environment. They embody this trend
through linking systems as well as other devices to day to day settings. It is defined as one that is
able to acquire as well as apply knowledge related with environment and adapt to their
inhabitants for improvisation of experience. The major feature which is being possessed by smart
environment is degree of autonomy, adapting to altering environment as well as interact with
humans within natural manner. Intelligent automation leads to reduction within amount of
communication needed by inhabitants, minimise utility consumptions along with potential
wastages (Alshohoumi and et. al, 2019).
Advancements within technical areas has made smart environment possible along with
different interaction solution for IoT devices. They are classified into two components: general-
purpose Constrained-Node Network (CNN) and Radio Frequency Identification (RFID). The
highly and numerous heterogeneous solutions which renders unlike features as well as
performance trade-offs. All smart environments are liable for collection, processing along with
this acting on distinct peculiar smart environments at wide scales. Furthermore, vertical domains
(like smart city/health) comes with diverse needs which creates an impact on tactics related with
how as well as where data is being processed along with ways to act on data in a peculiar context
(Amaraweera and Halgamuge, 2019). Apart from this, there are various kind of environment that
evolve: some vertical domains are being evaluated as well as opt for new technologies in faster
pace (such as smart health or home), while others involve (like smart city and factories). For this
it is necessary to handle legacy systems. This leads to complications within choosing interactive
2
mentioned. A brief overview will be provided with respect to these three concepts.
Smart Environment
Envisions of future in which multitude of systems are seamlessly embedded within day to day
objects of physical world is referred to as smart environment. This comprises of all kind of smart
world activities which involves continuous working for making lives of inhabitants much more
comfortable (Alloghani and et. al, 2020). It is an intelligent agent which perceives state of
resident as well as physical surroundings through the usage of sensors as well as acts on
environment by making use of controllers in such a way that peculiar performance measures are
being optimised. The designing of smart environment software algorithms leads to track location
as well as activities associated with hazardous conditions. Smart environments can be captured
by making use of distinct media on the basis of target environment. They embody this trend
through linking systems as well as other devices to day to day settings. It is defined as one that is
able to acquire as well as apply knowledge related with environment and adapt to their
inhabitants for improvisation of experience. The major feature which is being possessed by smart
environment is degree of autonomy, adapting to altering environment as well as interact with
humans within natural manner. Intelligent automation leads to reduction within amount of
communication needed by inhabitants, minimise utility consumptions along with potential
wastages (Alshohoumi and et. al, 2019).
Advancements within technical areas has made smart environment possible along with
different interaction solution for IoT devices. They are classified into two components: general-
purpose Constrained-Node Network (CNN) and Radio Frequency Identification (RFID). The
highly and numerous heterogeneous solutions which renders unlike features as well as
performance trade-offs. All smart environments are liable for collection, processing along with
this acting on distinct peculiar smart environments at wide scales. Furthermore, vertical domains
(like smart city/health) comes with diverse needs which creates an impact on tactics related with
how as well as where data is being processed along with ways to act on data in a peculiar context
(Amaraweera and Halgamuge, 2019). Apart from this, there are various kind of environment that
evolve: some vertical domains are being evaluated as well as opt for new technologies in faster
pace (such as smart health or home), while others involve (like smart city and factories). For this
it is necessary to handle legacy systems. This leads to complications within choosing interactive
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

technologies as well as availability of solutions for peculiar smart environments. There are
certain security and privacy aspects related with this and they have to be considered so that
appropriate measures as well as policies can be formulated for handling them.
Smart & Privacy Issues in Smart Environment
Smart Transport /Traffic System
Smart transport / traffic system
An intelligent transportation system (ITS) is an advanced application which aims to
provide innovative services relating to different modes of transport and traffic management and
enable users to be better informed and make safer, more coordinated, and 'smarter' use of
transport networks (Celik and et. al, 2019).
Smart transport / traffic architecture:
In order to improve the level of intelligence, information and humanization of transportation
system, the basic function of intelligent transportation system was analysed. Based on the
technology of radio frequency identification (RFID), global positioning system (GPS), GPRS,
GIS, according to some agreements of internet of things, the intelligent transportation system
connected with the internet, and carried out the intelligent recognition, location, tracking and
monitoring of buses through exchanging information and communication.
Figure 1Smart Environment
3
certain security and privacy aspects related with this and they have to be considered so that
appropriate measures as well as policies can be formulated for handling them.
Smart & Privacy Issues in Smart Environment
Smart Transport /Traffic System
Smart transport / traffic system
An intelligent transportation system (ITS) is an advanced application which aims to
provide innovative services relating to different modes of transport and traffic management and
enable users to be better informed and make safer, more coordinated, and 'smarter' use of
transport networks (Celik and et. al, 2019).
Smart transport / traffic architecture:
In order to improve the level of intelligence, information and humanization of transportation
system, the basic function of intelligent transportation system was analysed. Based on the
technology of radio frequency identification (RFID), global positioning system (GPS), GPRS,
GIS, according to some agreements of internet of things, the intelligent transportation system
connected with the internet, and carried out the intelligent recognition, location, tracking and
monitoring of buses through exchanging information and communication.
Figure 1Smart Environment
3

Within the computer system, it can easily be said that considering the smart transport the
information of the data can easily be transferred from one system to another without any issues
(Dabbagh and Rayes, 2019). In the real world as well this type of technology is being connected
with the help of internet of things where traffic is directly managed considering number of
elements. This consists of number of benefits and this could be anything from:
Reduction in stops and delays at intersections : With the help of smart transport it has become
really very effective that it it is successfully helped system to get upgraded where reduction took
place among the stop and delay time into the interactions wherever that took place within the
computer system (Devarakonda, Halgamuge and Mohammad, 2019).
Speed control & improvement : Considering traffic system, it has become really very easy to
control the speed of the data in the computer system along with the vehicles that are continuously
running on the roads. Through this, number of improvements has already took place where delay
process has already got improvised and so on.
The adaptation of these technologies to transportation requires the knowledge from many
engineering majors for example, electrical, mechanical, industrial and their related disciplines.
Majority of transportations problems are caused by lack of timely and accurate information and
from the lack of appropriate coordination individuals in the system.
Security issues in smart transport / traffic system
There are number of security related issues that came in front of smart transport are given
underneath:
Confidentiality: This feature ensures that only authorized ITS users have access to data. The
data cannot be snooped or hindered by unauthorized users. Confidentiality is an important
service in ITS, during the pseudonym registration and obtaining phases (Hahn, Munir and
Behzadan, 2019). Thus, it is important to ensure confidentiality of ITS. Therefore, advanced
cryptographic techniques should be considered.
Integrity: this is also being considered as another reason all the concerned for security
because it has been analysed that exact delivery of messages is most appropriately is required
considering the smart transport. It is very possible that wrong or tampered information could
directly misguide the user of the traffic system and may lead to deal with the big problem as
well. Therefore it is much required for the smart transport system to have increased integrity as
4
information of the data can easily be transferred from one system to another without any issues
(Dabbagh and Rayes, 2019). In the real world as well this type of technology is being connected
with the help of internet of things where traffic is directly managed considering number of
elements. This consists of number of benefits and this could be anything from:
Reduction in stops and delays at intersections : With the help of smart transport it has become
really very effective that it it is successfully helped system to get upgraded where reduction took
place among the stop and delay time into the interactions wherever that took place within the
computer system (Devarakonda, Halgamuge and Mohammad, 2019).
Speed control & improvement : Considering traffic system, it has become really very easy to
control the speed of the data in the computer system along with the vehicles that are continuously
running on the roads. Through this, number of improvements has already took place where delay
process has already got improvised and so on.
The adaptation of these technologies to transportation requires the knowledge from many
engineering majors for example, electrical, mechanical, industrial and their related disciplines.
Majority of transportations problems are caused by lack of timely and accurate information and
from the lack of appropriate coordination individuals in the system.
Security issues in smart transport / traffic system
There are number of security related issues that came in front of smart transport are given
underneath:
Confidentiality: This feature ensures that only authorized ITS users have access to data. The
data cannot be snooped or hindered by unauthorized users. Confidentiality is an important
service in ITS, during the pseudonym registration and obtaining phases (Hahn, Munir and
Behzadan, 2019). Thus, it is important to ensure confidentiality of ITS. Therefore, advanced
cryptographic techniques should be considered.
Integrity: this is also being considered as another reason all the concerned for security
because it has been analysed that exact delivery of messages is most appropriately is required
considering the smart transport. It is very possible that wrong or tampered information could
directly misguide the user of the traffic system and may lead to deal with the big problem as
well. Therefore it is much required for the smart transport system to have increased integrity as
4

this would directly avoid expected the unexpected interventions that are available or present
within the communication system that has been utilised by the user (Kartheek and Bhushan,
2020). This can effectively be resolved through developing and effective security band based on
the mechanism that is utilised by the user.
Availability: Within the present time this can also be taken into consideration as a security
concern while considering traffic system. Basically the reason is that availability is required in
the real time because without this it is may be possible that thread may arise in front of the user
of traffic system (Mahmood, 2019). This can effectively be resolved through considering
appropriate security approaches.
Privacy issues in smart transport / traffic system
Identification: Another one of the most crucial security concern that is identification where
ITS-S (vehicles) cannot be linked in ITS. This can lead to go through malware practices because
there are many factors that are sitting in the market that may hack the system and could
effectively use the identity of any other person. Due to this, it can be said that an individuals
vehicle can be utilised by any other person, which is a problem that needs proper attention at the
moment.
Authentication: Authentication can ensure that the messages received are legitimate.
However, authentication can be carried out in ITS without revealing the real identity of the
vehicle. Efficient approaches are needed to deal with this feature. Authenticity plays an efficient
role within the above system that has already been discussed above (Mewada, Dave and
Prajapati, 2019). Because without taken into consideration it is may be possible that the whole
system would not work in an effective manner and since the real world of the upcoming world is
full of technologies where considering an approach male lead to enhance the system in an
effective manner.
Trust: Another reason that rust can guarantee the preceding security and anonymous
communication features to be accomplished during the give and take phases among distinct
entities. In ITS, the feature of trust can be divided between applications and entities. In order to
achieve trust in ITS, there is a need to develop trustworthy. On the other hand, it is also must for
user to keep on look into the security system so that no issues put a place where he or she could
effectively change the password of the available software on a regular basis so that no issues
could take place (Mohanty and et. al, 2020).
5
within the communication system that has been utilised by the user (Kartheek and Bhushan,
2020). This can effectively be resolved through developing and effective security band based on
the mechanism that is utilised by the user.
Availability: Within the present time this can also be taken into consideration as a security
concern while considering traffic system. Basically the reason is that availability is required in
the real time because without this it is may be possible that thread may arise in front of the user
of traffic system (Mahmood, 2019). This can effectively be resolved through considering
appropriate security approaches.
Privacy issues in smart transport / traffic system
Identification: Another one of the most crucial security concern that is identification where
ITS-S (vehicles) cannot be linked in ITS. This can lead to go through malware practices because
there are many factors that are sitting in the market that may hack the system and could
effectively use the identity of any other person. Due to this, it can be said that an individuals
vehicle can be utilised by any other person, which is a problem that needs proper attention at the
moment.
Authentication: Authentication can ensure that the messages received are legitimate.
However, authentication can be carried out in ITS without revealing the real identity of the
vehicle. Efficient approaches are needed to deal with this feature. Authenticity plays an efficient
role within the above system that has already been discussed above (Mewada, Dave and
Prajapati, 2019). Because without taken into consideration it is may be possible that the whole
system would not work in an effective manner and since the real world of the upcoming world is
full of technologies where considering an approach male lead to enhance the system in an
effective manner.
Trust: Another reason that rust can guarantee the preceding security and anonymous
communication features to be accomplished during the give and take phases among distinct
entities. In ITS, the feature of trust can be divided between applications and entities. In order to
achieve trust in ITS, there is a need to develop trustworthy. On the other hand, it is also must for
user to keep on look into the security system so that no issues put a place where he or she could
effectively change the password of the available software on a regular basis so that no issues
could take place (Mohanty and et. al, 2020).
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Solutions to above discussed privacy and security related issues of traffic system
Considering all the privacy and security related issues that has already been discussed of traffic
system where there is only one way of solving these issues and i.e. utilisation of strong
mechanism based security approach. With the help of this it can easily said that issues in relation
to authenticity, privacy, trust, identification, availability, integrity, confidentiality and many
more major concerns could effectively be resolved right on time (Mukherjee and et. al, 2020).
Including this, it can also be said that change the companies are manufacturing high number of
cars for their customers therefore the traffic is also increasing day by day therefore considering
these approaches in relation to security may help or lead the company’s to themselves solve the
problem of heavy trafficking in all over the world. Another solution that can effectively be
adopted within the traffic system is is developing the stronger access layer considering number
of bans so that no issue take place and the authorised individual would only e access the
information that is available within the system (Nisar and Sahar, 2019)
. With the help of this, right amount of information can be given to the user and malware
practices can also be reduced to minimal.
Smart Health Care System
IoT applications are liable for turning reactive medical-based system within proactive
wellness-based systems. The resources which are being used within current medical research
which is being utilised lacks critical real-world data (Nour and et. al, 2019). It mostly makes use
of data which is being leftover, volunteers and controlled environment for medical examination.
IoT is liable for opening ways to a valuable data within real-time field data, testing and analysis.
Architecture
The healthcare industry will be benefitted by IoT revolution. By making its use within
clinics and hospital as well as establishment of internet of things based outpatient monitoring
solutions (Roy, Chowdhury and Aslam, 2020). Through this access to patient care can be
improvised as well as it will lead to enhancement within care quality and minimise operating
cost associated with this. The architecture of healthcare system is illustrated here:
The basic block of IoT system involves sensor which are liable for collection of data of
patients, internet gateways are being utilised for transmission of data as well as cloud
computing is being utilised for storage and processing of data.
6
Considering all the privacy and security related issues that has already been discussed of traffic
system where there is only one way of solving these issues and i.e. utilisation of strong
mechanism based security approach. With the help of this it can easily said that issues in relation
to authenticity, privacy, trust, identification, availability, integrity, confidentiality and many
more major concerns could effectively be resolved right on time (Mukherjee and et. al, 2020).
Including this, it can also be said that change the companies are manufacturing high number of
cars for their customers therefore the traffic is also increasing day by day therefore considering
these approaches in relation to security may help or lead the company’s to themselves solve the
problem of heavy trafficking in all over the world. Another solution that can effectively be
adopted within the traffic system is is developing the stronger access layer considering number
of bans so that no issue take place and the authorised individual would only e access the
information that is available within the system (Nisar and Sahar, 2019)
. With the help of this, right amount of information can be given to the user and malware
practices can also be reduced to minimal.
Smart Health Care System
IoT applications are liable for turning reactive medical-based system within proactive
wellness-based systems. The resources which are being used within current medical research
which is being utilised lacks critical real-world data (Nour and et. al, 2019). It mostly makes use
of data which is being leftover, volunteers and controlled environment for medical examination.
IoT is liable for opening ways to a valuable data within real-time field data, testing and analysis.
Architecture
The healthcare industry will be benefitted by IoT revolution. By making its use within
clinics and hospital as well as establishment of internet of things based outpatient monitoring
solutions (Roy, Chowdhury and Aslam, 2020). Through this access to patient care can be
improvised as well as it will lead to enhancement within care quality and minimise operating
cost associated with this. The architecture of healthcare system is illustrated here:
The basic block of IoT system involves sensor which are liable for collection of data of
patients, internet gateways are being utilised for transmission of data as well as cloud
computing is being utilised for storage and processing of data.
6
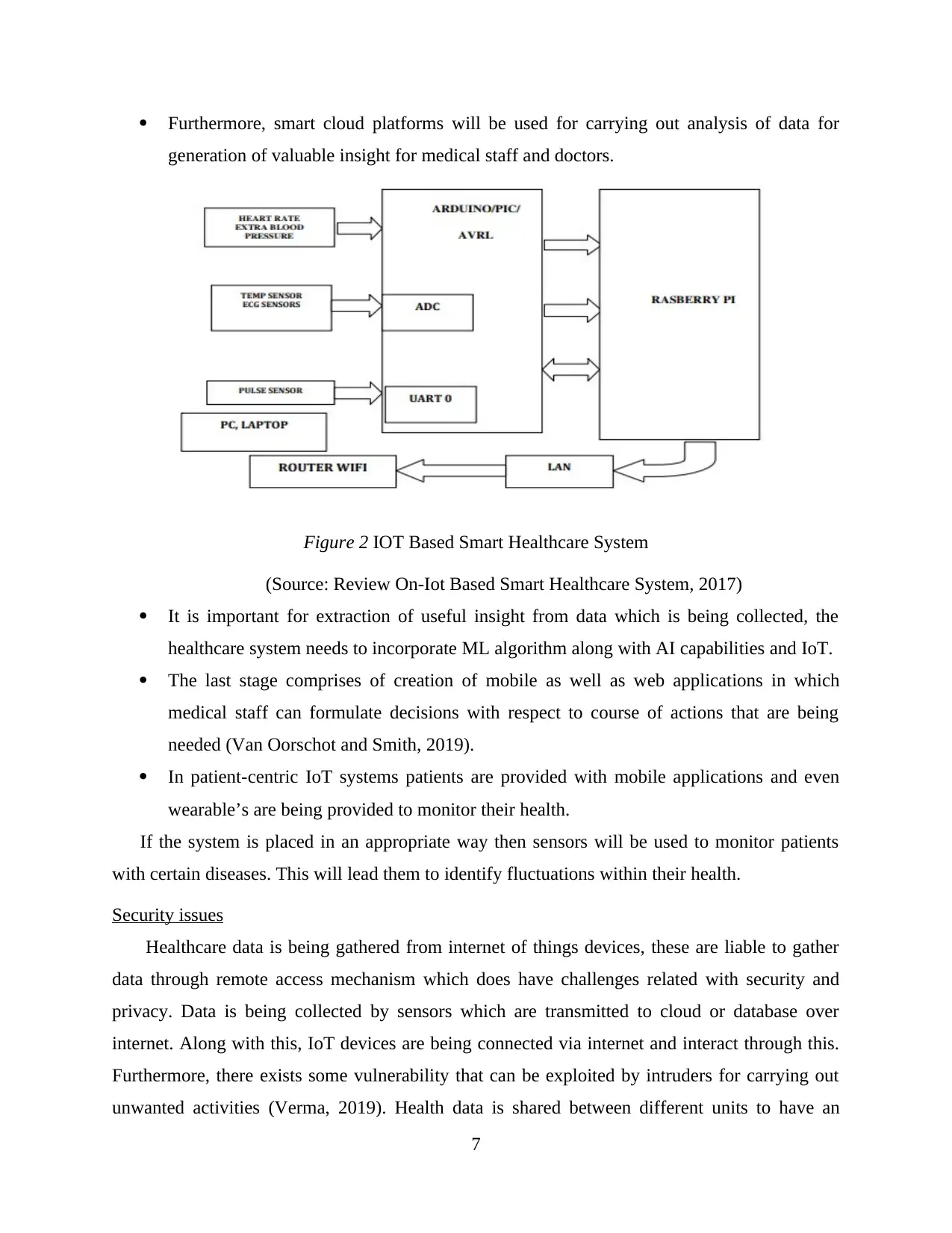
Furthermore, smart cloud platforms will be used for carrying out analysis of data for
generation of valuable insight for medical staff and doctors.
Figure 2 IOT Based Smart Healthcare System
(Source: Review On-Iot Based Smart Healthcare System, 2017)
It is important for extraction of useful insight from data which is being collected, the
healthcare system needs to incorporate ML algorithm along with AI capabilities and IoT.
The last stage comprises of creation of mobile as well as web applications in which
medical staff can formulate decisions with respect to course of actions that are being
needed (Van Oorschot and Smith, 2019).
In patient-centric IoT systems patients are provided with mobile applications and even
wearable’s are being provided to monitor their health.
If the system is placed in an appropriate way then sensors will be used to monitor patients
with certain diseases. This will lead them to identify fluctuations within their health.
Security issues
Healthcare data is being gathered from internet of things devices, these are liable to gather
data through remote access mechanism which does have challenges related with security and
privacy. Data is being collected by sensors which are transmitted to cloud or database over
internet. Along with this, IoT devices are being connected via internet and interact through this.
Furthermore, there exists some vulnerability that can be exploited by intruders for carrying out
unwanted activities (Verma, 2019). Health data is shared between different units to have an
7
generation of valuable insight for medical staff and doctors.
Figure 2 IOT Based Smart Healthcare System
(Source: Review On-Iot Based Smart Healthcare System, 2017)
It is important for extraction of useful insight from data which is being collected, the
healthcare system needs to incorporate ML algorithm along with AI capabilities and IoT.
The last stage comprises of creation of mobile as well as web applications in which
medical staff can formulate decisions with respect to course of actions that are being
needed (Van Oorschot and Smith, 2019).
In patient-centric IoT systems patients are provided with mobile applications and even
wearable’s are being provided to monitor their health.
If the system is placed in an appropriate way then sensors will be used to monitor patients
with certain diseases. This will lead them to identify fluctuations within their health.
Security issues
Healthcare data is being gathered from internet of things devices, these are liable to gather
data through remote access mechanism which does have challenges related with security and
privacy. Data is being collected by sensors which are transmitted to cloud or database over
internet. Along with this, IoT devices are being connected via internet and interact through this.
Furthermore, there exists some vulnerability that can be exploited by intruders for carrying out
unwanted activities (Verma, 2019). Health data is shared between different units to have an
7

appropriate analysis with respect to problems that are being faced by an individual. This makes it
more easy for intruder to have an access to data as if one system is having enhanced security
features then it is not necessary that all the system in network will have same features and will
leave the door for exploitation or loophole.
Privacy issues
Enhanced usage of social networks leads to increase the challenges related with expose of
personal data without consent from the owners. A young individual takes it as their priority for
seeking solution for problems they go through or share with their close one. It becomes irrelevant
to blame healthcare operators in case patient reveal their information within social network (Zhu,
Gai and Li, 2019). Along with this, some operators furnish their own social network for
individuals for exchanging their data, then with respect to this, user have liabilities to consult via
social groups. If the information is being shared with friends, then if their accounts are being
hacked then the messages or interaction which took place in between two people will be seen by
intruder. Furthermore, it can be utilised by someone by carrying out some irrelevant practices.
Attacks like data alteration, stealing and creating damage to information are common. They
are being utilised for unwanted practices and also hamper the stakes of hospital. Information
related with health is sensitive as well as crucial for each individual (Al‐Turjman, Zahmatkesh
and Shahroze, 2019). An instance can be taken to understand this aspect, if a drug has to be
prepared for treating cancer and information related with formulation of medicine is changed
then it will lead to wrong medicine. If this occurs then it will probably be dangerous and might
take lives of lots of people. Data is being sent through multiple paths within IoT. These are IoT
devices (data receiver, data generator and aggregation point), cloud (data stored), internet (multi-
directional data transport), the machine (big data repositories, application services, analytic).
Attackers steal this data for carrying out malicious activities and might blackmail patients if they
get some sensitive information. As per the example, data have been altered; this will lead doctors
to formulate wrong decisions as well as diagnosis as information is modified. Apart from this, if
data is being lost and individual is in a serious condition then also it will lead to create a serious
problem as same tests cannot be carried out.
Solution for issues
The security and privacy issues can be addressed through transmission of data via password
protected module which can be further encrypted through the usage of AES128 password
8
more easy for intruder to have an access to data as if one system is having enhanced security
features then it is not necessary that all the system in network will have same features and will
leave the door for exploitation or loophole.
Privacy issues
Enhanced usage of social networks leads to increase the challenges related with expose of
personal data without consent from the owners. A young individual takes it as their priority for
seeking solution for problems they go through or share with their close one. It becomes irrelevant
to blame healthcare operators in case patient reveal their information within social network (Zhu,
Gai and Li, 2019). Along with this, some operators furnish their own social network for
individuals for exchanging their data, then with respect to this, user have liabilities to consult via
social groups. If the information is being shared with friends, then if their accounts are being
hacked then the messages or interaction which took place in between two people will be seen by
intruder. Furthermore, it can be utilised by someone by carrying out some irrelevant practices.
Attacks like data alteration, stealing and creating damage to information are common. They
are being utilised for unwanted practices and also hamper the stakes of hospital. Information
related with health is sensitive as well as crucial for each individual (Al‐Turjman, Zahmatkesh
and Shahroze, 2019). An instance can be taken to understand this aspect, if a drug has to be
prepared for treating cancer and information related with formulation of medicine is changed
then it will lead to wrong medicine. If this occurs then it will probably be dangerous and might
take lives of lots of people. Data is being sent through multiple paths within IoT. These are IoT
devices (data receiver, data generator and aggregation point), cloud (data stored), internet (multi-
directional data transport), the machine (big data repositories, application services, analytic).
Attackers steal this data for carrying out malicious activities and might blackmail patients if they
get some sensitive information. As per the example, data have been altered; this will lead doctors
to formulate wrong decisions as well as diagnosis as information is modified. Apart from this, if
data is being lost and individual is in a serious condition then also it will lead to create a serious
problem as same tests cannot be carried out.
Solution for issues
The security and privacy issues can be addressed through transmission of data via password
protected module which can be further encrypted through the usage of AES128 password
8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

(Alhalafi and Veeraraghavan, 2019). Furthermore, the doctors and users can have access to data
by logging within the html pages. In case there is a condition of extremity then the message will
be transmitted via GSM module that is being interconnected with controller. There has to be a
dedicated network while transmission of a information for ensuring that data is being transmitted
through secured channels. Furthermore, appropriate security policies or procedures like IPSec
have to be utilised so that man-in-middle attack, denial of service attack do not occur (Alloghani
and et. al, 2020). Along with this, if any occurs then also the information which is being
transmitted must not be accessed and for this encryption can be used but there also strong
passwords have to be applied which must not broken up by any password cracker tool or
software.
Smart City
A Smart City can be referred to as an urban area which makes use of several forms of
electronic Internet of Things sensors with the aim of collecting wide range of information and
then using such insight for the purpose of management of resource, asset and services in an
effectual manner (Alshohoumi and et. al, 2019). This encompasses information gathered by way
of device, people and assets, which is then processed as well as examined with the intent of
monitoring along with managing power plant, waste management, information system, school,
hospital, library, power plant, detecting crime, utility, traffic & transport and several other such
types of activities.
Smart City architecture
The overall concept of smart city accumulates ICT as well as a range of physical devices
linked to Internet of Things network for the purpose of optimising the effectualness of activities
and practices pertaining to the city and thereby setting connection with wide base of people.
Smart city makes use of a technical system which makes it accessible for the officials of the city
to set connection with infrastructure and community, thereby setting base for monitoring the
incidence taking place within the city and its overall evolution (Amaraweera and Halgamuge,
2019). Hereby, information and communication technology is applied so that interaction, quality
and efficiency of urban services can be enhanced, thereby facilitating a simultaneous reduction in
cost and usage of resources. This even implies inflated communication between the
governmental authorities and the citizens of that city. Smart city applications are created with the
9
by logging within the html pages. In case there is a condition of extremity then the message will
be transmitted via GSM module that is being interconnected with controller. There has to be a
dedicated network while transmission of a information for ensuring that data is being transmitted
through secured channels. Furthermore, appropriate security policies or procedures like IPSec
have to be utilised so that man-in-middle attack, denial of service attack do not occur (Alloghani
and et. al, 2020). Along with this, if any occurs then also the information which is being
transmitted must not be accessed and for this encryption can be used but there also strong
passwords have to be applied which must not broken up by any password cracker tool or
software.
Smart City
A Smart City can be referred to as an urban area which makes use of several forms of
electronic Internet of Things sensors with the aim of collecting wide range of information and
then using such insight for the purpose of management of resource, asset and services in an
effectual manner (Alshohoumi and et. al, 2019). This encompasses information gathered by way
of device, people and assets, which is then processed as well as examined with the intent of
monitoring along with managing power plant, waste management, information system, school,
hospital, library, power plant, detecting crime, utility, traffic & transport and several other such
types of activities.
Smart City architecture
The overall concept of smart city accumulates ICT as well as a range of physical devices
linked to Internet of Things network for the purpose of optimising the effectualness of activities
and practices pertaining to the city and thereby setting connection with wide base of people.
Smart city makes use of a technical system which makes it accessible for the officials of the city
to set connection with infrastructure and community, thereby setting base for monitoring the
incidence taking place within the city and its overall evolution (Amaraweera and Halgamuge,
2019). Hereby, information and communication technology is applied so that interaction, quality
and efficiency of urban services can be enhanced, thereby facilitating a simultaneous reduction in
cost and usage of resources. This even implies inflated communication between the
governmental authorities and the citizens of that city. Smart city applications are created with the
9

motive of effectively managing the urban flow and allowing real time response activities. Thus,
this can be said to be arrangement which is designed in a manner such that it is more responsive
to challenges than the city which possesses a transactional relation with its members.
Within the confines of a Smart City, 2 main types of architectures can be identified. First is
the one that screens the outsides of the city, for example, its boulevards and roads, parks and
recreation regions, and so on. The other one is the architecture that screens the inside of
structures, the flow of individuals and merchandise, air conditioner water and many more of such
things (Celik and et. al, 2019). The engineering applied with the confines of such city for
extrinsic monitoring largely depends upon long run correspondence protocol in order to ensure
that the whole city can be secured with hardly any gadgets. Such types of communication
protocols cannot gain access within the buildings because of obstruction with dividers and
electrical or piping establishments. The engineering used with a view to develop the Smart City
exploits the telecommunication infrastructural facilities or, failing that, the wired electrical
system, it is simpler and less expensive to depend on these services. In territories having
troublesome access or without wired establishments, remote protocol, for example, Wi-Fi, RFID
or Bluetooth are put to use. These protocols have coverage ranging from 0.5 m to 10/15 m
(Dabbagh and Rayes, 2019). A right determination of outside and interior structures adjusted to
the geometries and separations to be secured would permit a right correspondence with every one
of the sensors and equipments of the city and a right or latencies of important information for the
investigation and improvement of pool of resource.
10
this can be said to be arrangement which is designed in a manner such that it is more responsive
to challenges than the city which possesses a transactional relation with its members.
Within the confines of a Smart City, 2 main types of architectures can be identified. First is
the one that screens the outsides of the city, for example, its boulevards and roads, parks and
recreation regions, and so on. The other one is the architecture that screens the inside of
structures, the flow of individuals and merchandise, air conditioner water and many more of such
things (Celik and et. al, 2019). The engineering applied with the confines of such city for
extrinsic monitoring largely depends upon long run correspondence protocol in order to ensure
that the whole city can be secured with hardly any gadgets. Such types of communication
protocols cannot gain access within the buildings because of obstruction with dividers and
electrical or piping establishments. The engineering used with a view to develop the Smart City
exploits the telecommunication infrastructural facilities or, failing that, the wired electrical
system, it is simpler and less expensive to depend on these services. In territories having
troublesome access or without wired establishments, remote protocol, for example, Wi-Fi, RFID
or Bluetooth are put to use. These protocols have coverage ranging from 0.5 m to 10/15 m
(Dabbagh and Rayes, 2019). A right determination of outside and interior structures adjusted to
the geometries and separations to be secured would permit a right correspondence with every one
of the sensors and equipments of the city and a right or latencies of important information for the
investigation and improvement of pool of resource.
10

Security issues in smart city
Smart City is the one which is developed with the application of a number of technologies
and systems. This inflates the level of risk or concerns for the city. In this relation, it is identified
that there are several types of security issues that have a chance of occurrence within the
confines of Smart City. In this regard, it is determined that one of the biggest issues is Man in
the middle whereby an attacker breaches, interrupts or spoofs the interaction taking place
between the system. For instance: the Man in the middle attack taking place on a smart valve can
be utilized for purposely causing waste water overflows (Devarakonda, Halgamuge and
Mohammad, 2019). Yet another security issue pertaining to smart city can be ascertained to be
data and identity theft whereby the information generated by way of unprotected smart city
infrastructure like EV charging station, parking garage and surveillance feed render cyber
attackers wide range of targeted personal detail which can be used for the purpose of committing
fraud transaction or activity. It can even be done for identity theft. Yet another major security
concern for Smart City is device hijacking whereby an attacker hijacks and thereby gains control
over a device. Such kinds of attacks are usually tough in terms of detection as in many of the
instances the attacker does not aim at altering the basic functioning of device. With respect to
smart city, a cyber criminal has the potential to exploit hijacked smart meters with an aim of
launching ransom attack upon Energy Management Systems (EMS) (Hahn, Munir and
Behzadan, 2019). Thus, it is important to bear in mind that such issues may prevail within a
Smart city and measures should be undertaken to deal with them in an effective manner.
Privacy issues in smart city
Apart from security concerns, it is also important to take into account the various types of
privacy issues that may take place within the confines of a smart city. In this regard, one of the
biggest privacy issues is acknowledged to be Distributed Denial of Service whereby DoS attack
aims at rendering machinery or network resources inaccessible to its users by temporarily
disrupting facilities of a host linked with Internet (Kartheek and Bhushan, 2020). Yet another
significant threat in this relation is identified to be Permanent Denial of Service which is
acknowledged to be an attack which has the potential to cause massive damage to device such
that it may even require replacing the hardware as a whole. In relation to smart city, hijacked
parking meter pose the threat of being sabotaged and may even be required to be substituted.
11
Smart City is the one which is developed with the application of a number of technologies
and systems. This inflates the level of risk or concerns for the city. In this relation, it is identified
that there are several types of security issues that have a chance of occurrence within the
confines of Smart City. In this regard, it is determined that one of the biggest issues is Man in
the middle whereby an attacker breaches, interrupts or spoofs the interaction taking place
between the system. For instance: the Man in the middle attack taking place on a smart valve can
be utilized for purposely causing waste water overflows (Devarakonda, Halgamuge and
Mohammad, 2019). Yet another security issue pertaining to smart city can be ascertained to be
data and identity theft whereby the information generated by way of unprotected smart city
infrastructure like EV charging station, parking garage and surveillance feed render cyber
attackers wide range of targeted personal detail which can be used for the purpose of committing
fraud transaction or activity. It can even be done for identity theft. Yet another major security
concern for Smart City is device hijacking whereby an attacker hijacks and thereby gains control
over a device. Such kinds of attacks are usually tough in terms of detection as in many of the
instances the attacker does not aim at altering the basic functioning of device. With respect to
smart city, a cyber criminal has the potential to exploit hijacked smart meters with an aim of
launching ransom attack upon Energy Management Systems (EMS) (Hahn, Munir and
Behzadan, 2019). Thus, it is important to bear in mind that such issues may prevail within a
Smart city and measures should be undertaken to deal with them in an effective manner.
Privacy issues in smart city
Apart from security concerns, it is also important to take into account the various types of
privacy issues that may take place within the confines of a smart city. In this regard, one of the
biggest privacy issues is acknowledged to be Distributed Denial of Service whereby DoS attack
aims at rendering machinery or network resources inaccessible to its users by temporarily
disrupting facilities of a host linked with Internet (Kartheek and Bhushan, 2020). Yet another
significant threat in this relation is identified to be Permanent Denial of Service which is
acknowledged to be an attack which has the potential to cause massive damage to device such
that it may even require replacing the hardware as a whole. In relation to smart city, hijacked
parking meter pose the threat of being sabotaged and may even be required to be substituted.
11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Solution of discussed security and privacy issues of smart city
In order to protect the smart city from being exposed to or being affected by the wide range
of security or privacy concerns, it is of immense significance that the connected smart city
devices are protected through the utilisation of an IoT security solution (device to cloud)
(Mahmood, 2019). Some of the most crucial elements of such kind of protection would be
Firmware integrity and secure boot, Mutual authentication, Security monitoring and analysis and
Security lifecycle management. All of these will thus provide aid to Smart City in protecting
itself against the different types of privacy and security issues.
Conclusion
From above, it can be concluded that security and privacy are important aspects while
making use of network to transmit the information. The reason behind this is that attacks like
man-in-middle, session hijacking, denial of service and many other attacks can be carried out on
internet of things. Thus, it makes information more vulnerable. As well as it makes it mandatory
to make use of certain countermeasures through which these attacks can be prevented and there
has to be certain ways if attack has occurred still then information is not being accessed by third
person. Smart environment provides remote control for distinct devices, aids within interaction,
acquisition of information, impelling services through intelligent devices along with predictive as
well as decision making capabilities. IoT furnishes different environments through which things
can be made easy. Smart traffic environment emphasise on optimisation of internal features of
vehicles so that a new revolution can be brought up in the automobile sector. Smart healthcare
environment is being developed for providing an ease to individuals so that they can have on
time services and stay active with respect to their health concerns. Smart city environment
involves smart surveillance, energy management system, water distribution, environmental
monitoring and many other aspects so that the factors which create impact can be eliminated.
Each has certain security and privacy concerns related with authentication, integrity, availability
and confidentiality. For dealing with them, a dedicated network can be formulated through which
sensitive information can be transmitted. Along with this encryption can be used for protecting
the information and maintaining the crucial aspects related security of information.
12
In order to protect the smart city from being exposed to or being affected by the wide range
of security or privacy concerns, it is of immense significance that the connected smart city
devices are protected through the utilisation of an IoT security solution (device to cloud)
(Mahmood, 2019). Some of the most crucial elements of such kind of protection would be
Firmware integrity and secure boot, Mutual authentication, Security monitoring and analysis and
Security lifecycle management. All of these will thus provide aid to Smart City in protecting
itself against the different types of privacy and security issues.
Conclusion
From above, it can be concluded that security and privacy are important aspects while
making use of network to transmit the information. The reason behind this is that attacks like
man-in-middle, session hijacking, denial of service and many other attacks can be carried out on
internet of things. Thus, it makes information more vulnerable. As well as it makes it mandatory
to make use of certain countermeasures through which these attacks can be prevented and there
has to be certain ways if attack has occurred still then information is not being accessed by third
person. Smart environment provides remote control for distinct devices, aids within interaction,
acquisition of information, impelling services through intelligent devices along with predictive as
well as decision making capabilities. IoT furnishes different environments through which things
can be made easy. Smart traffic environment emphasise on optimisation of internal features of
vehicles so that a new revolution can be brought up in the automobile sector. Smart healthcare
environment is being developed for providing an ease to individuals so that they can have on
time services and stay active with respect to their health concerns. Smart city environment
involves smart surveillance, energy management system, water distribution, environmental
monitoring and many other aspects so that the factors which create impact can be eliminated.
Each has certain security and privacy concerns related with authentication, integrity, availability
and confidentiality. For dealing with them, a dedicated network can be formulated through which
sensitive information can be transmitted. Along with this encryption can be used for protecting
the information and maintaining the crucial aspects related security of information.
12

References
Books & Journals
Al‐Turjman, F., Zahmatkesh, H., & Shahroze, R. (2019). An overview of security and privacy in
smart cities' IoT communications. Transactions on Emerging Telecommunications
Technologies, e3677.
Alhalafi, N., & Veeraraghavan, P. (2019, August). Privacy and Security Challenges and
Solutions in IOT: A review. In IOP Conference Series: Earth and Environmental
Science (Vol. 322, No. 1, p. 012013). IOP Publishing.
Alloghani, M. & et. al, (2020). A Systematic Review on Security and Privacy Issues in Mobile
Devices and Systems. In Handbook of Computer Networks and Cyber Security (pp. 585-
608). Springer, Cham.
Alshohoumi, F. & et. al, (2019). Systematic review of existing iot architectures security and
privacy issues and concerns. International Journal of Advanced Computer Science and
Applications, 10(01).
Amaraweera, S. P., & Halgamuge, M. N. (2019). Internet of Things in the Healthcare Sector:
Overview of Security and Privacy Issues. In Security, Privacy and Trust in the IoT
Environment (pp. 153-179). Springer, Cham.
Celik, Z. B. & et. al, (2019). Program analysis of commodity IoT applications for security and
privacy: Challenges and opportunities. ACM Computing Surveys (CSUR), 52(4), 1-30.
Dabbagh, M., & Rayes, A. (2019). Internet of things security and privacy. In Internet of Things
from hype to reality (pp. 211-238). Springer, Cham.
Devarakonda, S., Halgamuge, M. N., & Mohammad, A. (2019). Critical issues in the invasion of
the Internet of Things (IoT): Security, privacy, and other vulnerabilities. In Handbook of
Research on Big Data and the IoT (pp. 174-196). IGI Global.
Hahn, D. A., Munir, A., & Behzadan, V. (2019). Security and Privacy Issues in Intelligent
Transportation Systems: Classification and Challenges. IEEE Intell. Transp. Syst.
Kartheek, D. N., & Bhushan, B. (2020). Security issues in fog computing for internet of things.
In Architecture and Security Issues in Fog Computing Applications (pp. 53-63). IGI
Global.
Mahmood, Z. (Ed.). (2019). Security, Privacy and Trust in the IoT Environment. Springer.
Mewada, D., Dave, N., & Prajapati, R. K. (2019). A Survey: Prospects of Internet of Things
(IoT) Using Cryptography Based on its Subsequent Challenges. Australian Journal of
Wireless Technologies, Mobility and Security, 1(1), 28-30.
Mohanty, S. N. & et. al, (2020). An efficient Lightweight integrated Blockchain (ELIB) model
for IoT security and privacy. Future Generation Computer Systems, 102, 1027-1037.
Mukherjee, M. & et. al, (2020). Security and Privacy Issues and Solutions for Fog. Fog and
Fogonomics: Challenges and Practices of Fog Computing, Communication,
Networking, Strategy, and Economics.
Nisar, R., & Sahar, S. G. (2019, January). Security and privacy issues. In 2019 2nd International
Conference on Computing, Mathematics and Engineering Technologies (iCoMET) (pp.
1-6). IEEE.
Nour, B. & et. al, (2019). Security and Privacy Challenges in Information Centric Wireless IoT
Networks.
13
Books & Journals
Al‐Turjman, F., Zahmatkesh, H., & Shahroze, R. (2019). An overview of security and privacy in
smart cities' IoT communications. Transactions on Emerging Telecommunications
Technologies, e3677.
Alhalafi, N., & Veeraraghavan, P. (2019, August). Privacy and Security Challenges and
Solutions in IOT: A review. In IOP Conference Series: Earth and Environmental
Science (Vol. 322, No. 1, p. 012013). IOP Publishing.
Alloghani, M. & et. al, (2020). A Systematic Review on Security and Privacy Issues in Mobile
Devices and Systems. In Handbook of Computer Networks and Cyber Security (pp. 585-
608). Springer, Cham.
Alshohoumi, F. & et. al, (2019). Systematic review of existing iot architectures security and
privacy issues and concerns. International Journal of Advanced Computer Science and
Applications, 10(01).
Amaraweera, S. P., & Halgamuge, M. N. (2019). Internet of Things in the Healthcare Sector:
Overview of Security and Privacy Issues. In Security, Privacy and Trust in the IoT
Environment (pp. 153-179). Springer, Cham.
Celik, Z. B. & et. al, (2019). Program analysis of commodity IoT applications for security and
privacy: Challenges and opportunities. ACM Computing Surveys (CSUR), 52(4), 1-30.
Dabbagh, M., & Rayes, A. (2019). Internet of things security and privacy. In Internet of Things
from hype to reality (pp. 211-238). Springer, Cham.
Devarakonda, S., Halgamuge, M. N., & Mohammad, A. (2019). Critical issues in the invasion of
the Internet of Things (IoT): Security, privacy, and other vulnerabilities. In Handbook of
Research on Big Data and the IoT (pp. 174-196). IGI Global.
Hahn, D. A., Munir, A., & Behzadan, V. (2019). Security and Privacy Issues in Intelligent
Transportation Systems: Classification and Challenges. IEEE Intell. Transp. Syst.
Kartheek, D. N., & Bhushan, B. (2020). Security issues in fog computing for internet of things.
In Architecture and Security Issues in Fog Computing Applications (pp. 53-63). IGI
Global.
Mahmood, Z. (Ed.). (2019). Security, Privacy and Trust in the IoT Environment. Springer.
Mewada, D., Dave, N., & Prajapati, R. K. (2019). A Survey: Prospects of Internet of Things
(IoT) Using Cryptography Based on its Subsequent Challenges. Australian Journal of
Wireless Technologies, Mobility and Security, 1(1), 28-30.
Mohanty, S. N. & et. al, (2020). An efficient Lightweight integrated Blockchain (ELIB) model
for IoT security and privacy. Future Generation Computer Systems, 102, 1027-1037.
Mukherjee, M. & et. al, (2020). Security and Privacy Issues and Solutions for Fog. Fog and
Fogonomics: Challenges and Practices of Fog Computing, Communication,
Networking, Strategy, and Economics.
Nisar, R., & Sahar, S. G. (2019, January). Security and privacy issues. In 2019 2nd International
Conference on Computing, Mathematics and Engineering Technologies (iCoMET) (pp.
1-6). IEEE.
Nour, B. & et. al, (2019). Security and Privacy Challenges in Information Centric Wireless IoT
Networks.
13

Roy, M., Chowdhury, C., & Aslam, N. (2020). Security and Privacy Issues in Wireless Sensor
and Body Area Networks. In Handbook of Computer Networks and Cyber Security (pp.
173-200). Springer, Cham.
Van Oorschot, P. C., & Smith, S. W. (2019). The Internet of Things: Security Challenges. IEEE
Security & Privacy, 17(5), 7-9.
Verma, V. K. (2019). Blockchain technology: Systematic review of security and privacy
problems and its scope with Internet of Things (IoT). Journal of Network Security, 7(1),
24-28.
Zhu, L., Gai, K., & Li, M. (2019). Security and Privacy Issues in Internet of Things.
In Blockchain Technology in Internet of Things (pp. 29-40). Springer, Cham.
Online
Patil, A.A. & Suralkar, D.S., (2017). Review on-IOT Based Smart Healthcare
System. International Journal of Advanced Research in Engineering and
Technology, 8(3).
14
and Body Area Networks. In Handbook of Computer Networks and Cyber Security (pp.
173-200). Springer, Cham.
Van Oorschot, P. C., & Smith, S. W. (2019). The Internet of Things: Security Challenges. IEEE
Security & Privacy, 17(5), 7-9.
Verma, V. K. (2019). Blockchain technology: Systematic review of security and privacy
problems and its scope with Internet of Things (IoT). Journal of Network Security, 7(1),
24-28.
Zhu, L., Gai, K., & Li, M. (2019). Security and Privacy Issues in Internet of Things.
In Blockchain Technology in Internet of Things (pp. 29-40). Springer, Cham.
Online
Patil, A.A. & Suralkar, D.S., (2017). Review on-IOT Based Smart Healthcare
System. International Journal of Advanced Research in Engineering and
Technology, 8(3).
14
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



