Security and Privacy of Mobile and Pervasive Systems
VerifiedAdded on 2023/01/20
|11
|2852
|87
AI Summary
This paper focuses on the security and privacy issues of mobile and pervasive systems used in an IoT enabled environment, particularly in healthcare organizations. It discusses the privacy threats, security vulnerabilities, and mitigation plans for pervasive systems. The paper also provides recommendations for addressing security issues and concludes with the importance of studying recent computing attacks due to privacy and security issues of pervasive systems.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SECURITY AND PRIVACY OF MOBILE AND PERVASIVE SYSTEMS
Name of the Student
Student Number
Topic: Security and Privacy of Mobile and Pervasive Systems
Word count: 2020 words
Name of the Student
Student Number
Topic: Security and Privacy of Mobile and Pervasive Systems
Word count: 2020 words
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
1
Introduction
The notable determination of the paper is to focus on the security and privacy of mobile
and pervasive systems which are used in an IoT enabled environment. The paper will be very
much important to understand the application of the mobile and pervasive systems in the
healthcare organizations in an organized manner.
There are lots of privacy and security issues associated with the use of the mobile and
pervasive systems in healthcare organization such as the disclosure of essential information in
terms of the location, activity and physiological parameters as well as the shadow attacks on the
pervasive systems (Davies et al., 2015). The other security issues of the pervasive systems are
the User Interaction issues, issues associated with extended computing boundary, cybersecurity
threats such as terrorism. These privacy threats can have a significant impact on the business of
the healthcare organizations thus it needs to be solved purposefully so that the effectiveness of
the mobile and pervasive systems is maintained. Thus this paper will be very much important to
understand these issues from the perspective of peer-reviewed scholars.
The primary objective of this research paper is to focus on the different types of security
issues of the mobile and pervasive systems used in healthcare organizations. The research
questions will be very much important to understand the complexities of the pervasive systems in
a detailed manner.
Research Questions
What are the privacy issues associated with the pervasive systems?
What are the mitigation plan for the security vulnerabilities of pervasive
systems?
Literature review
As mentioned by Abawajy & Hassan (2017), there are lots of security and privacy issue
regarding the use of IT technologies and innovations. The researcher stated that the complexities
of the IT technologies and the systems increase hugely due to the privacy and security issues.
The paper helps in understand the probable security concerns regarding the use of the different
types of IoT enabled devices in a business organization. The researcher of the paper stated that
SYSTEMS
1
Introduction
The notable determination of the paper is to focus on the security and privacy of mobile
and pervasive systems which are used in an IoT enabled environment. The paper will be very
much important to understand the application of the mobile and pervasive systems in the
healthcare organizations in an organized manner.
There are lots of privacy and security issues associated with the use of the mobile and
pervasive systems in healthcare organization such as the disclosure of essential information in
terms of the location, activity and physiological parameters as well as the shadow attacks on the
pervasive systems (Davies et al., 2015). The other security issues of the pervasive systems are
the User Interaction issues, issues associated with extended computing boundary, cybersecurity
threats such as terrorism. These privacy threats can have a significant impact on the business of
the healthcare organizations thus it needs to be solved purposefully so that the effectiveness of
the mobile and pervasive systems is maintained. Thus this paper will be very much important to
understand these issues from the perspective of peer-reviewed scholars.
The primary objective of this research paper is to focus on the different types of security
issues of the mobile and pervasive systems used in healthcare organizations. The research
questions will be very much important to understand the complexities of the pervasive systems in
a detailed manner.
Research Questions
What are the privacy issues associated with the pervasive systems?
What are the mitigation plan for the security vulnerabilities of pervasive
systems?
Literature review
As mentioned by Abawajy & Hassan (2017), there are lots of security and privacy issue
regarding the use of IT technologies and innovations. The researcher stated that the complexities
of the IT technologies and the systems increase hugely due to the privacy and security issues.
The paper helps in understand the probable security concerns regarding the use of the different
types of IoT enabled devices in a business organization. The researcher of the paper stated that

2SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
the networking capabilities of the organization are directly impacted due to the security and
privacy issues of the IoT enabled devices. The security threats was explained by the researcher of
this paper in a professional manner. The identified security threats are exposure of the essential
business records, loss of confidentiality of data which are circulated between the internal and the
external stakeholders of the business organizations. The researcher of the paper suggested that
the security and privacy threats can have a direct negative impact on the operating systems used
in the business organizations as well (Zhang, Xue & Huang, 2016). The researcher of the paper
also mentioned that the security issues of the IoT devices also impacts the wireless
communication devices which are used between the internal as well as the external stakeholders
of the business. The paper helps in understanding different aspects of security protocols which
are associated with the IoT devices used in the business organizations in terms of
Confidentiality, Integrity, and Availability. The main contribution of the paper is that it helps in
understanding different aspects of the security concerns regarding the use of IoT enabled devices
in business environments.
As discussed by Arapinis et al. (2017), there are lots of challenges regarding the
application of the pervasive systems in business organizations such as the limitation of the
computational infrastructure as the systems used by stakeholders from both inside or outside the
business organization and the user interaction issues (Bettini & Riboni, 2015). The researcher of
the paper also highlighted the importance of the clear interaction between the users and space
which is very important to mitigate numerous complexities of the pervasive systems. The
physical aspects of the space have to be controlled in an organized manner as instructed by the
researcher. Privacy issues of the pervasive system such as tracking the location of the users of
the pervasive systems were also highlighted in the paper as well. The role of the intruders as well
as the social engineers who put a negative impact on the growth and productivity of the business
organizations was also mentioned in the paper as well. The security threats coming from inside
the business organization was also described by the researchers of this paper. The role of the
system administrators, as well as the IT administrators in business organizations such as a
healthcare organization, was also mentioned as in this resource as well. The most significant unit
of the paper is that it helps in focusing on all the probable privacy issues which are being faced
in the business organizations. The limitation of the paper is that it does not focus on the
mitigation strategies of all the identified security issues of the pervasive system.
SYSTEMS
the networking capabilities of the organization are directly impacted due to the security and
privacy issues of the IoT enabled devices. The security threats was explained by the researcher of
this paper in a professional manner. The identified security threats are exposure of the essential
business records, loss of confidentiality of data which are circulated between the internal and the
external stakeholders of the business organizations. The researcher of the paper suggested that
the security and privacy threats can have a direct negative impact on the operating systems used
in the business organizations as well (Zhang, Xue & Huang, 2016). The researcher of the paper
also mentioned that the security issues of the IoT devices also impacts the wireless
communication devices which are used between the internal as well as the external stakeholders
of the business. The paper helps in understanding different aspects of security protocols which
are associated with the IoT devices used in the business organizations in terms of
Confidentiality, Integrity, and Availability. The main contribution of the paper is that it helps in
understanding different aspects of the security concerns regarding the use of IoT enabled devices
in business environments.
As discussed by Arapinis et al. (2017), there are lots of challenges regarding the
application of the pervasive systems in business organizations such as the limitation of the
computational infrastructure as the systems used by stakeholders from both inside or outside the
business organization and the user interaction issues (Bettini & Riboni, 2015). The researcher of
the paper also highlighted the importance of the clear interaction between the users and space
which is very important to mitigate numerous complexities of the pervasive systems. The
physical aspects of the space have to be controlled in an organized manner as instructed by the
researcher. Privacy issues of the pervasive system such as tracking the location of the users of
the pervasive systems were also highlighted in the paper as well. The role of the intruders as well
as the social engineers who put a negative impact on the growth and productivity of the business
organizations was also mentioned in the paper as well. The security threats coming from inside
the business organization was also described by the researchers of this paper. The role of the
system administrators, as well as the IT administrators in business organizations such as a
healthcare organization, was also mentioned as in this resource as well. The most significant unit
of the paper is that it helps in focusing on all the probable privacy issues which are being faced
in the business organizations. The limitation of the paper is that it does not focus on the
mitigation strategies of all the identified security issues of the pervasive system.

3SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
As mentioned by Baig, Gholam & Connolly (2015), transparency and unobtrusiveness
can be very much important to deal with the security issues of the mobile and pervasive systems
which are used in the business organizations. The researcher of the paper stated that IT risk
management policy can be very much important to deal with the security threats offered by the
IT innovations such as the IoT devices and the pervasive system. The security mechanisms of the
pervasive system were mentioned in a detailed manner in this report which can be applied in the
working environment of any business organization. The user security behavior needed in order to
deal with the security and privacy threats coming from inside the organization was the main
contribution of this paper. The paper has very less or negligible limitations.
Case study analysis
This unit of the paper will be critically analyzing the use case which has been selected in
the paper. The actors which be considered in this use case are the relatives of the patients, the
patients, Hospital staff, care-center and IT administrator. The activities of each of the actors are
important for the organizational growth of a healthcare organization.
However, it can be also said that the security and the privacy issues of the mobile and
pervasive system can have a significant impact on the efficiency and productivity of all these
actors. The dependability, accuracy and relevancy of stakeholders of healthcare organizations are
entirely dependent on the effectiveness of the pervasive system used in the healthcare
organization. The self-aware computing systems used in the healthcare environments will be also
affected as a result of the privacy and security issues in the pervasive systems.
Based on the above two paragraphs help in understanding the importance of each of the
actors associated with a healthcare organization. The impact of the security and the privacy
issues for each of the actors can be also understood from the paper (Gisdakis, Giannetsos &
Papadimitratos, 2016). Considering the above scenario it can be said that the privacy and security
issues of the mobile and pervasive systems of the healthcare organization need to be avoided or
mitigated in the first place in order to get the desired results from the pervasive system
This entity of the paper will be discussing a scenario where pervasive systems are used in
a healthcare organization. The internal capability of the pervasive systems needs to be secured in
the first place as there are lots of actors associated with the pervasive systems. There are lots of
SYSTEMS
As mentioned by Baig, Gholam & Connolly (2015), transparency and unobtrusiveness
can be very much important to deal with the security issues of the mobile and pervasive systems
which are used in the business organizations. The researcher of the paper stated that IT risk
management policy can be very much important to deal with the security threats offered by the
IT innovations such as the IoT devices and the pervasive system. The security mechanisms of the
pervasive system were mentioned in a detailed manner in this report which can be applied in the
working environment of any business organization. The user security behavior needed in order to
deal with the security and privacy threats coming from inside the organization was the main
contribution of this paper. The paper has very less or negligible limitations.
Case study analysis
This unit of the paper will be critically analyzing the use case which has been selected in
the paper. The actors which be considered in this use case are the relatives of the patients, the
patients, Hospital staff, care-center and IT administrator. The activities of each of the actors are
important for the organizational growth of a healthcare organization.
However, it can be also said that the security and the privacy issues of the mobile and
pervasive system can have a significant impact on the efficiency and productivity of all these
actors. The dependability, accuracy and relevancy of stakeholders of healthcare organizations are
entirely dependent on the effectiveness of the pervasive system used in the healthcare
organization. The self-aware computing systems used in the healthcare environments will be also
affected as a result of the privacy and security issues in the pervasive systems.
Based on the above two paragraphs help in understanding the importance of each of the
actors associated with a healthcare organization. The impact of the security and the privacy
issues for each of the actors can be also understood from the paper (Gisdakis, Giannetsos &
Papadimitratos, 2016). Considering the above scenario it can be said that the privacy and security
issues of the mobile and pervasive systems of the healthcare organization need to be avoided or
mitigated in the first place in order to get the desired results from the pervasive system
This entity of the paper will be discussing a scenario where pervasive systems are used in
a healthcare organization. The internal capability of the pervasive systems needs to be secured in
the first place as there are lots of actors associated with the pervasive systems. There are lots of
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
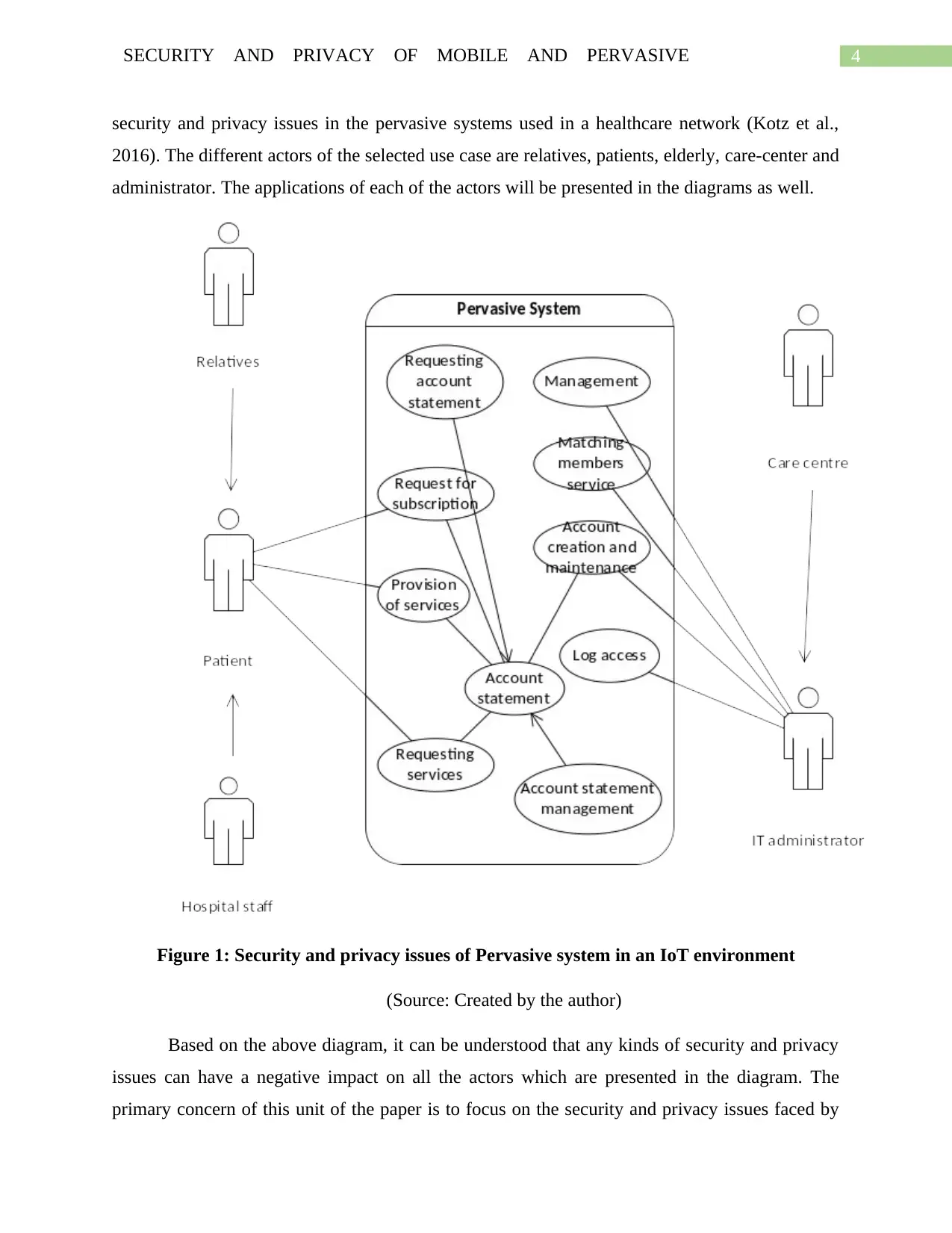
4SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
security and privacy issues in the pervasive systems used in a healthcare network (Kotz et al.,
2016). The different actors of the selected use case are relatives, patients, elderly, care-center and
administrator. The applications of each of the actors will be presented in the diagrams as well.
Figure 1: Security and privacy issues of Pervasive system in an IoT environment
(Source: Created by the author)
Based on the above diagram, it can be understood that any kinds of security and privacy
issues can have a negative impact on all the actors which are presented in the diagram. The
primary concern of this unit of the paper is to focus on the security and privacy issues faced by
SYSTEMS
security and privacy issues in the pervasive systems used in a healthcare network (Kotz et al.,
2016). The different actors of the selected use case are relatives, patients, elderly, care-center and
administrator. The applications of each of the actors will be presented in the diagrams as well.
Figure 1: Security and privacy issues of Pervasive system in an IoT environment
(Source: Created by the author)
Based on the above diagram, it can be understood that any kinds of security and privacy
issues can have a negative impact on all the actors which are presented in the diagram. The
primary concern of this unit of the paper is to focus on the security and privacy issues faced by

5SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
each stakeholder of a healthcare environment (Kumar & Xie, 2016). The security issues have the
most negative effect on the IT administrators of the healthcare organization as they manage the
entire proceedings starting from the management of the patient accounts, matching the service
provided by the healthcare organization with respect to the disease the patient is suffering from.
Thus, it can be said that the care-center which are associated with IT administrators can be also
significantly affected regarding any kinds of disruptions for the IT administrators (Mollah, Azad
& Vasilakos, 2017). The security issues of the pervasive system can lead to numerous difficulties
in managing the account statements by the patients. The subscription requests of the patients can
be managed in an organized manner as a result of the security and privacy issues of the pervasive
systems.
Evidence and examples
It can be also said that the service provided by the hospital staff to the patients in terms of
the IT innovations like temperature sensor, voice recognition security systems, artificial
intelligence based devices and wireless computing are all vulnerable to the privacy and security
issues of the mobile and pervasive systems. The computing activities of the healthcare
organization can get disrupted due to the security and privacy issues of the mobile and pervasive
systems (Omoogun et al., 2017). The system vulnerabilities can get enhanced due to the security
and vulnerabilities of the pervasive systems used in the healthcare organization. The
computations capability of the systems which are used in the hospital premises is also decreased
due to the security and privacy issues of the pervasive system.
Synthesis of the case study
Based on the above diagram it can be said that the security and the privacy issues of the
pervasive system used in a healthcare organization cab have a significant impact to each of the
stakeholders (Ren et al., 2015). The different types of stakeholders of the healthcare organization
which are affected due to the security and the privacy issues are patients, Hospital staff, family of
the patients, care-centre and IT administrators.
SYSTEMS
each stakeholder of a healthcare environment (Kumar & Xie, 2016). The security issues have the
most negative effect on the IT administrators of the healthcare organization as they manage the
entire proceedings starting from the management of the patient accounts, matching the service
provided by the healthcare organization with respect to the disease the patient is suffering from.
Thus, it can be said that the care-center which are associated with IT administrators can be also
significantly affected regarding any kinds of disruptions for the IT administrators (Mollah, Azad
& Vasilakos, 2017). The security issues of the pervasive system can lead to numerous difficulties
in managing the account statements by the patients. The subscription requests of the patients can
be managed in an organized manner as a result of the security and privacy issues of the pervasive
systems.
Evidence and examples
It can be also said that the service provided by the hospital staff to the patients in terms of
the IT innovations like temperature sensor, voice recognition security systems, artificial
intelligence based devices and wireless computing are all vulnerable to the privacy and security
issues of the mobile and pervasive systems. The computing activities of the healthcare
organization can get disrupted due to the security and privacy issues of the mobile and pervasive
systems (Omoogun et al., 2017). The system vulnerabilities can get enhanced due to the security
and vulnerabilities of the pervasive systems used in the healthcare organization. The
computations capability of the systems which are used in the hospital premises is also decreased
due to the security and privacy issues of the pervasive system.
Synthesis of the case study
Based on the above diagram it can be said that the security and the privacy issues of the
pervasive system used in a healthcare organization cab have a significant impact to each of the
stakeholders (Ren et al., 2015). The different types of stakeholders of the healthcare organization
which are affected due to the security and the privacy issues are patients, Hospital staff, family of
the patients, care-centre and IT administrators.

6SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
Recommendations
The following recommendations will be very much important for the stakeholders to
address security issues.
Transparency and unobtrusiveness: The focal point of the pervasive computing helps
in transforming the users into first-class entities. The entire computer-based machinery of
the healthcare organization must be frequently examined.
Different level of security services: The security protocols of each of the stakeholder are
different from each other, thus different levels of security services should be deployed for
each of the stakeholders of the healthcare organization.
Flexibility and customizability: The subsystems associated with the IT infrastructure of
the healthcare organization must be very much flexible in nature. The adaptability and
customizability of the subsystems should be understood in the first place in order to
mitigate security and privacy issues.
Extended boundaries: Concepts from the physical world must be incorporated in order
to deal with the existing security and privacy issues faced by the organization due to the
use of pervasive systems.
Conclusions
The paper was very much important to understand the privacy and the security issues of
the mobile and pervasive systems which are used in a health care organizations which are an IoT
enabled environment as it uses a huge number of IoT based systems and devices in their working
environment such as the temperature sensors. The opinion of the researchers discussing
numerous aspects of security and privacy issues associated with the use of the pervasive systems
can be also determined from the paper as well. Critical analysis of the case study can be also
concluded from this paper, along with that the paper also includes a recommendations unit
stating the probable recommendations which can be used by business organizations in order to
address the privacy and security issues of the pervasive systems. The research questions of the
paper such as the privacy issues of the pervasive systems along with the mitigation plan are
successfully addressed throughout the discussion part of the paper. Thus, it can be also said that
SYSTEMS
Recommendations
The following recommendations will be very much important for the stakeholders to
address security issues.
Transparency and unobtrusiveness: The focal point of the pervasive computing helps
in transforming the users into first-class entities. The entire computer-based machinery of
the healthcare organization must be frequently examined.
Different level of security services: The security protocols of each of the stakeholder are
different from each other, thus different levels of security services should be deployed for
each of the stakeholders of the healthcare organization.
Flexibility and customizability: The subsystems associated with the IT infrastructure of
the healthcare organization must be very much flexible in nature. The adaptability and
customizability of the subsystems should be understood in the first place in order to
mitigate security and privacy issues.
Extended boundaries: Concepts from the physical world must be incorporated in order
to deal with the existing security and privacy issues faced by the organization due to the
use of pervasive systems.
Conclusions
The paper was very much important to understand the privacy and the security issues of
the mobile and pervasive systems which are used in a health care organizations which are an IoT
enabled environment as it uses a huge number of IoT based systems and devices in their working
environment such as the temperature sensors. The opinion of the researchers discussing
numerous aspects of security and privacy issues associated with the use of the pervasive systems
can be also determined from the paper as well. Critical analysis of the case study can be also
concluded from this paper, along with that the paper also includes a recommendations unit
stating the probable recommendations which can be used by business organizations in order to
address the privacy and security issues of the pervasive systems. The research questions of the
paper such as the privacy issues of the pervasive systems along with the mitigation plan are
successfully addressed throughout the discussion part of the paper. Thus, it can be also said that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
this paper can be very much useful for the future researches which aims in studying the recent
computing attacks which are conducted due to privacy and security issues of pervasive systems.
SYSTEMS
this paper can be very much useful for the future researches which aims in studying the recent
computing attacks which are conducted due to privacy and security issues of pervasive systems.

8SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
References
Abawajy, J. H., & Hassan, M. M. (2017). Federated internet of things and cloud computing
pervasive patient health monitoring system. IEEE Communications Magazine, 55(1), 48-
53.
Arapinis, M., Mancini, L. I., Ritter, E., & Ryan, M. D. (2017). Analysis of privacy in mobile
telephony systems. International Journal of Information Security, 16(5), 491-523.
Baig, M. M., GholamHosseini, H., & Connolly, M. J. (2015). Mobile healthcare applications:
system design review, critical issues and challenges. Australasian physical &
engineering sciences in medicine, 38(1), 23-38.
Bettini, C., & Riboni, D. (2015). Privacy protection in pervasive systems: State of the art and
technical challenges. Pervasive and Mobile Computing, 17, 159-174.
Davies, N., Friday, A., Clinch, S., Sas, C., Langheinrich, M., Ward, G., & Schmidt, A. (2015).
Security and privacy implications of pervasive memory augmentation. IEEE Pervasive
Computing, 14(1), 44-53.
Gisdakis, S., Giannetsos, T., & Papadimitratos, P. (2016). Security, privacy, and incentive
provision for mobile crowd sensing systems. IEEE Internet of Things Journal, 3(5), 839-
853.
Kotz, D., Gunter, C. A., Kumar, S., & Weiner, J. P. (2016). Privacy and security in mobile
health: a research agenda. Computer, 49(6), 22-30.
Kumar, A., & Xie, B. (Eds.). (2016). Handbook of Mobile Systems Applications and Services.
CRC Press.
Mollah, M. B., Azad, M. A. K., & Vasilakos, A. (2017). Security and privacy challenges in
mobile cloud computing: Survey and way ahead. Journal of Network and Computer
Applications, 84, 38-54.
Omoogun, M., Seeam, P., Ramsurrun, V., Bellekens, X., & Seeam, A. (2017, June). When
eHealth meets the internet of things: Pervasive security and privacy challenges. In 2017
SYSTEMS
References
Abawajy, J. H., & Hassan, M. M. (2017). Federated internet of things and cloud computing
pervasive patient health monitoring system. IEEE Communications Magazine, 55(1), 48-
53.
Arapinis, M., Mancini, L. I., Ritter, E., & Ryan, M. D. (2017). Analysis of privacy in mobile
telephony systems. International Journal of Information Security, 16(5), 491-523.
Baig, M. M., GholamHosseini, H., & Connolly, M. J. (2015). Mobile healthcare applications:
system design review, critical issues and challenges. Australasian physical &
engineering sciences in medicine, 38(1), 23-38.
Bettini, C., & Riboni, D. (2015). Privacy protection in pervasive systems: State of the art and
technical challenges. Pervasive and Mobile Computing, 17, 159-174.
Davies, N., Friday, A., Clinch, S., Sas, C., Langheinrich, M., Ward, G., & Schmidt, A. (2015).
Security and privacy implications of pervasive memory augmentation. IEEE Pervasive
Computing, 14(1), 44-53.
Gisdakis, S., Giannetsos, T., & Papadimitratos, P. (2016). Security, privacy, and incentive
provision for mobile crowd sensing systems. IEEE Internet of Things Journal, 3(5), 839-
853.
Kotz, D., Gunter, C. A., Kumar, S., & Weiner, J. P. (2016). Privacy and security in mobile
health: a research agenda. Computer, 49(6), 22-30.
Kumar, A., & Xie, B. (Eds.). (2016). Handbook of Mobile Systems Applications and Services.
CRC Press.
Mollah, M. B., Azad, M. A. K., & Vasilakos, A. (2017). Security and privacy challenges in
mobile cloud computing: Survey and way ahead. Journal of Network and Computer
Applications, 84, 38-54.
Omoogun, M., Seeam, P., Ramsurrun, V., Bellekens, X., & Seeam, A. (2017, June). When
eHealth meets the internet of things: Pervasive security and privacy challenges. In 2017

9SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
International Conference on Cyber Security And Protection Of Digital Services (Cyber
Security) (pp. 1-7). IEEE.
Ren, J., Zhang, Y., Zhang, K., & Shen, X. (2015). Exploiting mobile crowdsourcing for
pervasive cloud services: challenges and solutions. IEEE Communications Magazine,
53(3), 98-105.
Zhang, J., Xue, N., & Huang, X. (2016). A secure system for pervasive social network-based
healthcare. IEEE Access, 4, 9239-9250.
SYSTEMS
International Conference on Cyber Security And Protection Of Digital Services (Cyber
Security) (pp. 1-7). IEEE.
Ren, J., Zhang, Y., Zhang, K., & Shen, X. (2015). Exploiting mobile crowdsourcing for
pervasive cloud services: challenges and solutions. IEEE Communications Magazine,
53(3), 98-105.
Zhang, J., Xue, N., & Huang, X. (2016). A secure system for pervasive social network-based
healthcare. IEEE Access, 4, 9239-9250.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
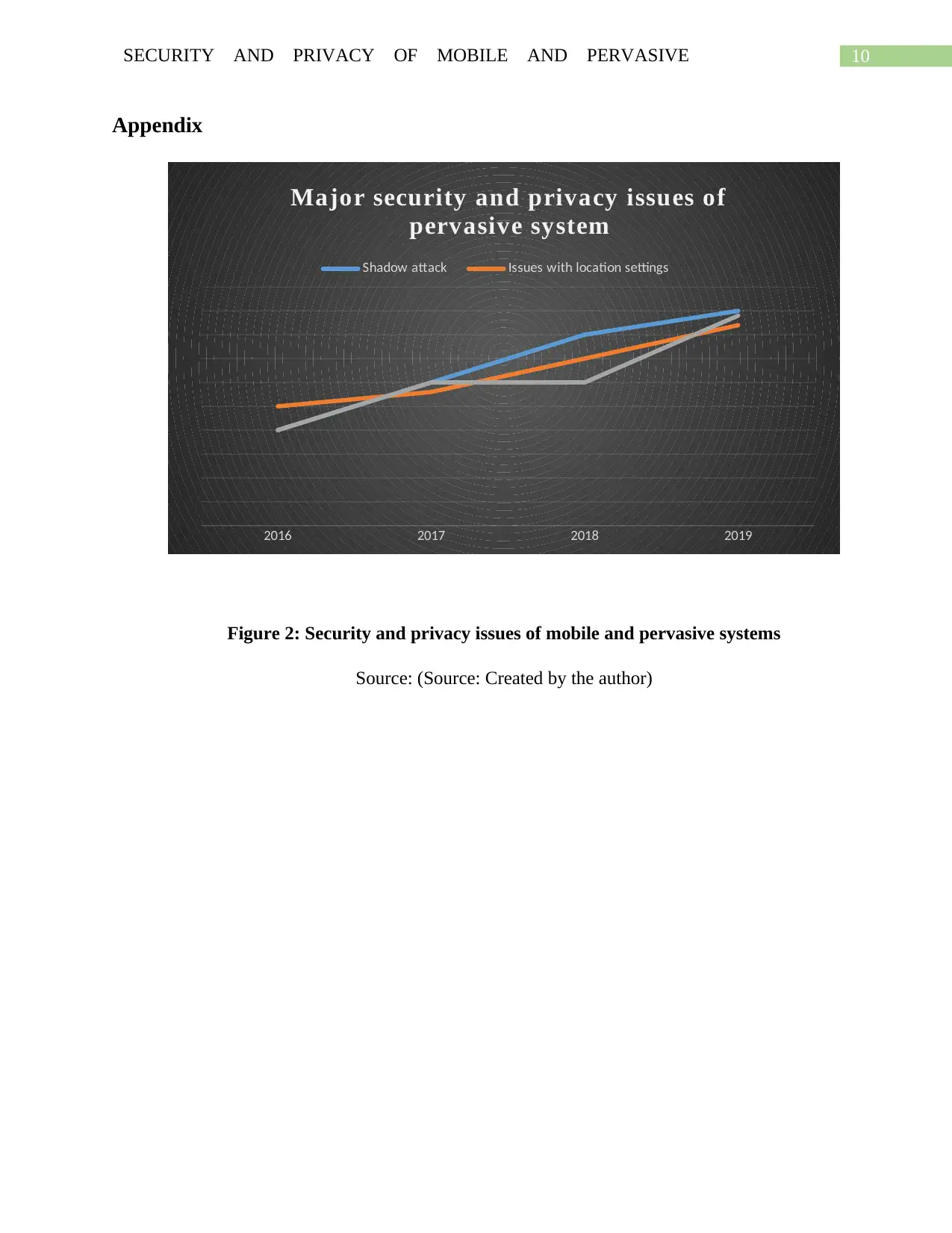
10SECURITY AND PRIVACY OF MOBILE AND PERVASIVE
SYSTEMS
Appendix
2016 2017 2018 2019
Major security and privacy issues of
pervasive system
Shadow attack Issues with location settings
Figure 2: Security and privacy issues of mobile and pervasive systems
Source: (Source: Created by the author)
SYSTEMS
Appendix
2016 2017 2018 2019
Major security and privacy issues of
pervasive system
Shadow attack Issues with location settings
Figure 2: Security and privacy issues of mobile and pervasive systems
Source: (Source: Created by the author)
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




