Security, Audit and Compliance for Marriott International
VerifiedAdded on 2023/04/19
|12
|3474
|52
AI Summary
This report discusses the security handling models and strategies for managing data breaches in companies, with a focus on the case study of Marriott International. The report explains the RSP model of security handling and its stages, and discusses the role of audit and governance in information security. It also highlights the professional roles involved in securing IT systems.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
Security, Audit and Compliance for Marriott International
Matric Number
Module ID
Word Count: 2295
Security, Audit and Compliance for Marriott International
Matric Number
Module ID
Word Count: 2295
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
Executive Summary
This report consists the details of security handling models that are needed for
handling the data breach in companies. The management of security incident mainly
utilizes combination of all the appliances, investigation that are human driven, as well as
software system that are included in a data breach. This process basically starts with
alert which states that the incident has already occurred and there is a need of
engagement of a team who will be capable of handling the incident. There are many
models as well as strategies that are capable of handling all such incidents of data
breach. According to ISO standard there are mainly five steps for managing the security
incident in a company. Those are preparing for handling the incidents, identifying the
potential incidents of security management by monitoring as well as reporting all such
incidents, accessing all the identified incidents for determining the coming steps for
mitigating the risks, and the last step includes about documenting all the discussion
from that particular incident. There are many other models of security handling that
includes SANS, CERT, ISO, and NIST model.
This report has taken the case study of Marriott International a famous company
of U.K. having its properties spread all around the world. Marriott International has faced
a data breach putting the details of their guests at risks. There was no particular amount
about the amount of data breach that had occurred. A particular security model of
incident handling is explained in this report which will help the company to mitigate
further data breach in future.
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
Executive Summary
This report consists the details of security handling models that are needed for
handling the data breach in companies. The management of security incident mainly
utilizes combination of all the appliances, investigation that are human driven, as well as
software system that are included in a data breach. This process basically starts with
alert which states that the incident has already occurred and there is a need of
engagement of a team who will be capable of handling the incident. There are many
models as well as strategies that are capable of handling all such incidents of data
breach. According to ISO standard there are mainly five steps for managing the security
incident in a company. Those are preparing for handling the incidents, identifying the
potential incidents of security management by monitoring as well as reporting all such
incidents, accessing all the identified incidents for determining the coming steps for
mitigating the risks, and the last step includes about documenting all the discussion
from that particular incident. There are many other models of security handling that
includes SANS, CERT, ISO, and NIST model.
This report has taken the case study of Marriott International a famous company
of U.K. having its properties spread all around the world. Marriott International has faced
a data breach putting the details of their guests at risks. There was no particular amount
about the amount of data breach that had occurred. A particular security model of
incident handling is explained in this report which will help the company to mitigate
further data breach in future.

2
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
Table of Contents
1. Introduction.........................................................................................................3
2. Model Selection..................................................................................................3
3. Model Explanation..............................................................................................5
4. Discussion...........................................................................................................7
4.1 Information Security Processes....................................................................7
4.2 Role of Audit based on Information Security................................................7
4.3 Governance Issues Raised and Inclusion of Professional Roles.................8
5. Conclusion..........................................................................................................8
References............................................................................................................10
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
Table of Contents
1. Introduction.........................................................................................................3
2. Model Selection..................................................................................................3
3. Model Explanation..............................................................................................5
4. Discussion...........................................................................................................7
4.1 Information Security Processes....................................................................7
4.2 Role of Audit based on Information Security................................................7
4.3 Governance Issues Raised and Inclusion of Professional Roles.................8
5. Conclusion..........................................................................................................8
References............................................................................................................10

3
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
1. Introduction
Security management is a particular process that helps in identifying, recording,
managing as well as analyzing the security threats or the security incidents in the
present time. Security incident includes active threats as well as attempted intrusion for
data breach (Ruefle et al., 2014). Examples of security incidents involves unauthorized
access of data or policy violations that includes health, social security numbers,
personally identifiable records as well as financial issues. The case study that is taken
for this report is the data breach occurred in Marriott International. Marriott International
is a leading global lodging company having their headquarter in U.K. that has more than
6,700 properties all over the world. This hotel group of Marriott International has
announced that there was a massive data breach that had affected about 500 million
guests. The data breach came from an unauthorized party that has access the
database of Starwood guest authorization (Safa, Von Solms & Furnell, 2016). There
was no specified amount about how much amount of money was beached in that
incident. As a result of the data breach, Marriott International introduced an RSP model
in the company for preventing any further data breach in the organization. This report
addresses the RSP model and a detailed explanation of the model that is selected by
the Marriott International. The reason for selecting the RSP model is addresses with a
diagram that shows the details of the RSP model. Detailed model explanation with a
discussion evaluating relation of the information security processes are explained.
2. Model Selection
The model that is selected for Marriott International is the RSP model. RSP
model states Regions Security Policy (RSP) that is applied to regions of network
security. This model is has a network architecture for network organizations by grouping
the modes in regions that are based on some common purposes. There are many other
models of security handling that includes SANS, CERT, ISO, and NIST model. The
model selected for this organization is mainly based on all the methodologies that are
included in all other security handling models. This particular model includes
combination of all the processes that are in other security models. The aim of RSP
security model is that this provides the organization with a systematic way of detecting
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
1. Introduction
Security management is a particular process that helps in identifying, recording,
managing as well as analyzing the security threats or the security incidents in the
present time. Security incident includes active threats as well as attempted intrusion for
data breach (Ruefle et al., 2014). Examples of security incidents involves unauthorized
access of data or policy violations that includes health, social security numbers,
personally identifiable records as well as financial issues. The case study that is taken
for this report is the data breach occurred in Marriott International. Marriott International
is a leading global lodging company having their headquarter in U.K. that has more than
6,700 properties all over the world. This hotel group of Marriott International has
announced that there was a massive data breach that had affected about 500 million
guests. The data breach came from an unauthorized party that has access the
database of Starwood guest authorization (Safa, Von Solms & Furnell, 2016). There
was no specified amount about how much amount of money was beached in that
incident. As a result of the data breach, Marriott International introduced an RSP model
in the company for preventing any further data breach in the organization. This report
addresses the RSP model and a detailed explanation of the model that is selected by
the Marriott International. The reason for selecting the RSP model is addresses with a
diagram that shows the details of the RSP model. Detailed model explanation with a
discussion evaluating relation of the information security processes are explained.
2. Model Selection
The model that is selected for Marriott International is the RSP model. RSP
model states Regions Security Policy (RSP) that is applied to regions of network
security. This model is has a network architecture for network organizations by grouping
the modes in regions that are based on some common purposes. There are many other
models of security handling that includes SANS, CERT, ISO, and NIST model. The
model selected for this organization is mainly based on all the methodologies that are
included in all other security handling models. This particular model includes
combination of all the processes that are in other security models. The aim of RSP
security model is that this provides the organization with a systematic way of detecting
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
data breach along with coherent approach to detect the processes as well as shows
prompt reaction to the security incidents in the company.
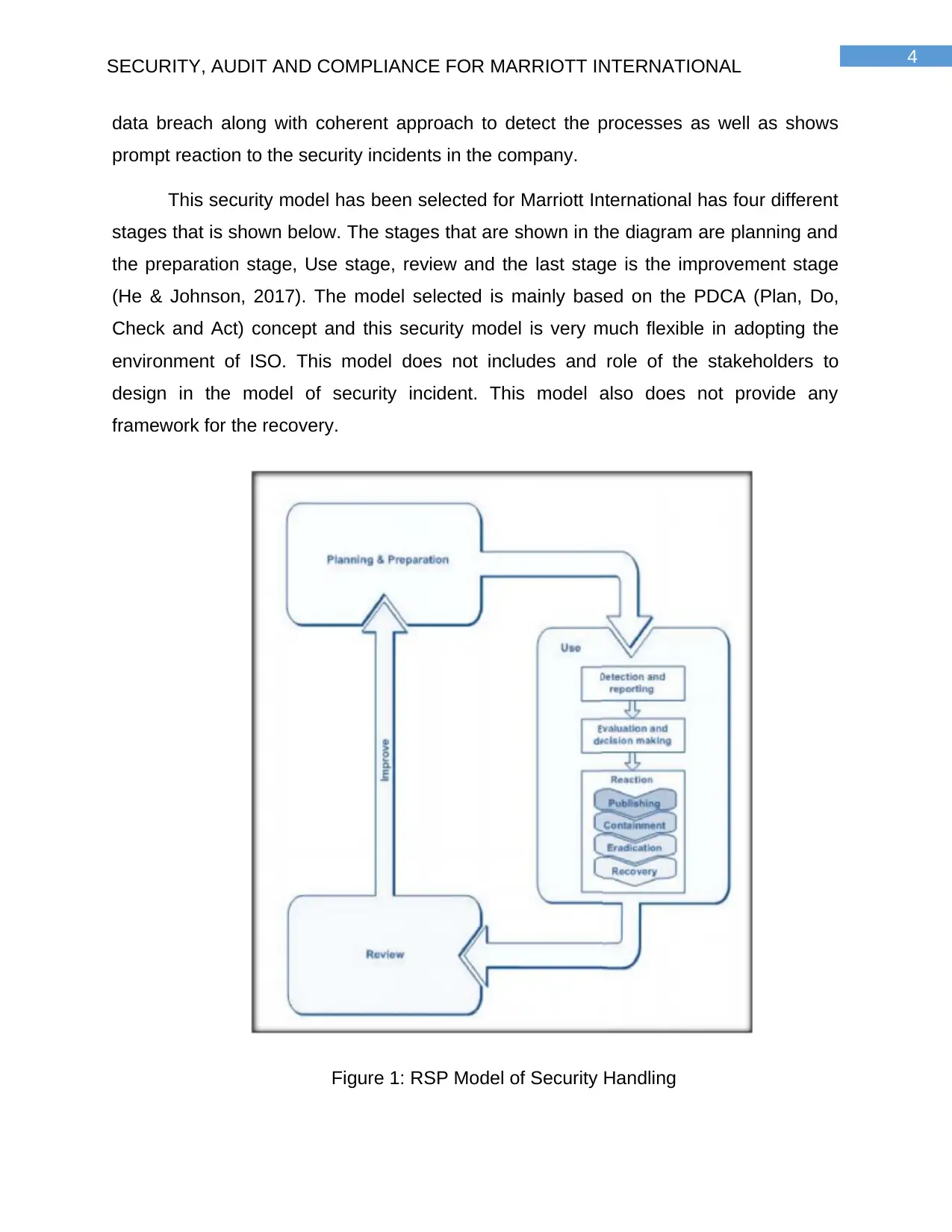
This security model has been selected for Marriott International has four different
stages that is shown below. The stages that are shown in the diagram are planning and
the preparation stage, Use stage, review and the last stage is the improvement stage
(He & Johnson, 2017). The model selected is mainly based on the PDCA (Plan, Do,
Check and Act) concept and this security model is very much flexible in adopting the
environment of ISO. This model does not includes and role of the stakeholders to
design in the model of security incident. This model also does not provide any
framework for the recovery.
Figure 1: RSP Model of Security Handling
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
data breach along with coherent approach to detect the processes as well as shows
prompt reaction to the security incidents in the company.
This security model has been selected for Marriott International has four different
stages that is shown below. The stages that are shown in the diagram are planning and
the preparation stage, Use stage, review and the last stage is the improvement stage
(He & Johnson, 2017). The model selected is mainly based on the PDCA (Plan, Do,
Check and Act) concept and this security model is very much flexible in adopting the
environment of ISO. This model does not includes and role of the stakeholders to
design in the model of security incident. This model also does not provide any
framework for the recovery.
Figure 1: RSP Model of Security Handling

5
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
(Source: Rahman & Choo, 2015)
As the steps are divided in four different stages, it is very easy to keep a track on
the data involved in the organization. The planning and preparation stage helps in
preparing a detailed planning for detecting as well as how to reacting for the security
breach. The use stage can help Marriott International to detect and report the breach
and evaluate them accordingly (Rahman, Cahyani & Choo, 2107). There is also a
review stage and improvement stage that helps to improve the security in Marriott
International. Review helps the analyst of Marriott International to review all the steps
that are taken for analyzing and evaluating the data breach and further improvements
includes in further improvement that can be made in future. A detailed explanation of
the RSP model of security handling is explained in the section below.
3. Model Explanation
This report based on the information security handling model based on the report
of Marriott International. This report has focused on the impacts of Regions Security
Policy (RSP) Model, which would be helpful for handling the information security
systems and technology within the hotel business (Cheng et al., 2013). The report is
based on the revealing of massive form of data breach in Marriott International that
would have affected around 500 million guests. These guests have submitted their
credentials to the hotel reception during their stay at the hotel. These credentials
included name, addresses, passport number and other information, which could have
been stolen by hackers for their personal use.
Based on the incident of data breach, there could be a suggestion of using of a
information security model that could be proposed for the organisation in order to
prevent such kind of incidents in the future (Duffield, 2014). The RSP model could be
defined to provide a new kind of look at the network architecture of the organisation.
This model is primarily based on the methodologies that would be proposed by NIST,
SANS, ISO and CERT model. The primary objective of the model is based on providing
a coherent and systematic approach based on the process of detecting and reacting to
several incidents of security. This model would comprise of four stages, which could be
discussed as:
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
(Source: Rahman & Choo, 2015)
As the steps are divided in four different stages, it is very easy to keep a track on
the data involved in the organization. The planning and preparation stage helps in
preparing a detailed planning for detecting as well as how to reacting for the security
breach. The use stage can help Marriott International to detect and report the breach
and evaluate them accordingly (Rahman, Cahyani & Choo, 2107). There is also a
review stage and improvement stage that helps to improve the security in Marriott
International. Review helps the analyst of Marriott International to review all the steps
that are taken for analyzing and evaluating the data breach and further improvements
includes in further improvement that can be made in future. A detailed explanation of
the RSP model of security handling is explained in the section below.
3. Model Explanation
This report based on the information security handling model based on the report
of Marriott International. This report has focused on the impacts of Regions Security
Policy (RSP) Model, which would be helpful for handling the information security
systems and technology within the hotel business (Cheng et al., 2013). The report is
based on the revealing of massive form of data breach in Marriott International that
would have affected around 500 million guests. These guests have submitted their
credentials to the hotel reception during their stay at the hotel. These credentials
included name, addresses, passport number and other information, which could have
been stolen by hackers for their personal use.
Based on the incident of data breach, there could be a suggestion of using of a
information security model that could be proposed for the organisation in order to
prevent such kind of incidents in the future (Duffield, 2014). The RSP model could be
defined to provide a new kind of look at the network architecture of the organisation.
This model is primarily based on the methodologies that would be proposed by NIST,
SANS, ISO and CERT model. The primary objective of the model is based on providing
a coherent and systematic approach based on the process of detecting and reacting to
several incidents of security. This model would comprise of four stages, which could be
discussed as:

6
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
1. Planning and Preparation – This stage is considered as the primary stage
based on providing a definition for the detection and reacting to different forms of abuse
on the IT systems (Nelson & Staggers, 2016). The different kinds of actions would be
mainly based on developing of a proper organisational structure. This could be achieved
based on three layers: Process Layer, Organisation Layer and Technology Layer.
2. Use Stage – This is considered as the secondary stage. This stage would be
able to constitute the primary part based on the presented process of detecting and
reacting to several IT systems (Crossler et al., 2013). There are some of the steps that
have been defined within the use stages. These include:
Detection and Reporting – This phase would be able to focus on the collection
of events that would be entirely connected based on IT security. This would be
able to report to the concerned people within the proper time interval.
Evaluation and Making of Decisions – In this phase, the classification of abuse
would be conducted along with the proper form of assessment based on the
impact of IT environment (Skopik, Settanni & Fiedler, 2016). During this phase,
the different forms of vital decisions that would be concerned on the seizure of
evidences and their analysis would be made.
Reaction – There are some kinds of actions, which would be taken based on the
classification of data based on abuse within the stages:
i. Publishing – Different kinds of contacts within the environment based
on purpose of acquiring or passing of information would be detected.
ii. Containment – All kinds of actions would be undertaken for the
purpose of minimizing the negative kinds of influences within the IT environment
of the concerned organisation.
iii. Eradication – Different suitable measures would be connected based
on the elimination of several kinds of factors that would make the abuse to be
possible (Pearson, 2013).
iv. Recovery – Various kinds of activities would be carried out based on
restoring of normal kind of operational status within the IT system.
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
1. Planning and Preparation – This stage is considered as the primary stage
based on providing a definition for the detection and reacting to different forms of abuse
on the IT systems (Nelson & Staggers, 2016). The different kinds of actions would be
mainly based on developing of a proper organisational structure. This could be achieved
based on three layers: Process Layer, Organisation Layer and Technology Layer.
2. Use Stage – This is considered as the secondary stage. This stage would be
able to constitute the primary part based on the presented process of detecting and
reacting to several IT systems (Crossler et al., 2013). There are some of the steps that
have been defined within the use stages. These include:
Detection and Reporting – This phase would be able to focus on the collection
of events that would be entirely connected based on IT security. This would be
able to report to the concerned people within the proper time interval.
Evaluation and Making of Decisions – In this phase, the classification of abuse
would be conducted along with the proper form of assessment based on the
impact of IT environment (Skopik, Settanni & Fiedler, 2016). During this phase,
the different forms of vital decisions that would be concerned on the seizure of
evidences and their analysis would be made.
Reaction – There are some kinds of actions, which would be taken based on the
classification of data based on abuse within the stages:
i. Publishing – Different kinds of contacts within the environment based
on purpose of acquiring or passing of information would be detected.
ii. Containment – All kinds of actions would be undertaken for the
purpose of minimizing the negative kinds of influences within the IT environment
of the concerned organisation.
iii. Eradication – Different suitable measures would be connected based
on the elimination of several kinds of factors that would make the abuse to be
possible (Pearson, 2013).
iv. Recovery – Various kinds of activities would be carried out based on
restoring of normal kind of operational status within the IT system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
3. Review – Some of the following steps that would be conducted within
the Review phase include:
Analysis of different materials of evidences that would be located outside of the
IT system based on the relation of abuse (Almorsy, Grundy & Müller, 2016).
Preparing of various enhancements based within the IT environment that would
be connected within the identified abuse (Soomro, Shah & Ahmed, 2016).
Preparing of potential improvements based within the process of detection and
reaction based on situations of abuse whenever different deficiencies would be
discovered.
Preparing of final report.
4. Improvements – This stage would mainly put focus on the implementation
of processes such as prevention, correction and detection of mechanisms within the
IT environment (Kshetri, 2013). This stage would also concentrate on the
implementation of several enhancements within the processes of reaction and
detection of IT systems within every layer.
4. Discussion
4.1 Information Security Processes
Risk Management processes within Information Security could be defined as the
processes of management of risks that would be associated within the use of IT
systems within any concerned organisation. It would involve the certain processes such
as identification, assessment and treating of risks. The final aim of the process is based
on treating of risks based on according of the overall risks of the organisation
(Baskerville, Spagnoletti & Kim, 2014). Different businesses should not eliminate the
need of risk assessment. They should be able to seek the identification and
achievement of an acceptable form of risk levels based within the organisation.
4.2 Role of Audit based on Information Security
An Information Technology (IT) audit could be defined as the examination of the
controls of management within an IT infrastructure. Different kinds of IT audits should
be able to determine whether the IT controls would be able to protect the assets of the
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
3. Review – Some of the following steps that would be conducted within
the Review phase include:
Analysis of different materials of evidences that would be located outside of the
IT system based on the relation of abuse (Almorsy, Grundy & Müller, 2016).
Preparing of various enhancements based within the IT environment that would
be connected within the identified abuse (Soomro, Shah & Ahmed, 2016).
Preparing of potential improvements based within the process of detection and
reaction based on situations of abuse whenever different deficiencies would be
discovered.
Preparing of final report.
4. Improvements – This stage would mainly put focus on the implementation
of processes such as prevention, correction and detection of mechanisms within the
IT environment (Kshetri, 2013). This stage would also concentrate on the
implementation of several enhancements within the processes of reaction and
detection of IT systems within every layer.
4. Discussion
4.1 Information Security Processes
Risk Management processes within Information Security could be defined as the
processes of management of risks that would be associated within the use of IT
systems within any concerned organisation. It would involve the certain processes such
as identification, assessment and treating of risks. The final aim of the process is based
on treating of risks based on according of the overall risks of the organisation
(Baskerville, Spagnoletti & Kim, 2014). Different businesses should not eliminate the
need of risk assessment. They should be able to seek the identification and
achievement of an acceptable form of risk levels based within the organisation.
4.2 Role of Audit based on Information Security
An Information Technology (IT) audit could be defined as the examination of the
controls of management within an IT infrastructure. Different kinds of IT audits should
be able to determine whether the IT controls would be able to protect the assets of the

8
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
company, ensure the integrity of data that would be aligned within the goals of the
organisation (Rodrigues et al., 2013). The impact of audit within the Marriott
International would be able to prevent such kind of systems from further kinds of IT data
breaches.
4.3 Governance Issues Raised and Inclusion of Professional Roles
IT Security governance could be defined as the systems in which an organisation
would be able to direct and control the IT security. Governance would be able to specify
the framework of accountability (Flores, Antonsen & Ekstedt, 2014). This would be able
to provide insight on ensuring of risks that the management would be able to ensure the
risks and would be adequately mitigated.
Based on the consideration of the data breach incident at Marriott International, it
could be considered that various professionals within an IT industry would be able to
take responsibility of the protection of networks, computer systems and network
architecture. The different roles of the people who would be able to handle the security
of the systems include IT security engineers, Chief Information Officer (CIO), Chief
Security Officer (CSO), Chief Technology Officer (CTO), Information Assurance
Manager (IAM) and other computer operators (Hu, West & Smarandescu, 2015). These
job of the IT professionals would mainly revolve around the protection of IT systems.
These would include the infrastructure, network and every other areas of IT. Securing
the information assets, data of customers, financial information would be very much
essential for securing the primary information of customers within the hotel business.
5. Conclusion
From the discussion above, it can be summarized that security handling is an
important part of an organization. There are many other models that handles the
security incidents that occurs in a company. Marriott International that has been
discussed in this report had faced a data breach which is explained in this report. As
discussed above, Security management provides robust as well as comprehensive view
related to any security issue within the company. Security incident includes active
threats as well as attempted intrusion for data breach. Security management helps in
identifying, recording, managing as well as analyzing the security threats or the security
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
company, ensure the integrity of data that would be aligned within the goals of the
organisation (Rodrigues et al., 2013). The impact of audit within the Marriott
International would be able to prevent such kind of systems from further kinds of IT data
breaches.
4.3 Governance Issues Raised and Inclusion of Professional Roles
IT Security governance could be defined as the systems in which an organisation
would be able to direct and control the IT security. Governance would be able to specify
the framework of accountability (Flores, Antonsen & Ekstedt, 2014). This would be able
to provide insight on ensuring of risks that the management would be able to ensure the
risks and would be adequately mitigated.
Based on the consideration of the data breach incident at Marriott International, it
could be considered that various professionals within an IT industry would be able to
take responsibility of the protection of networks, computer systems and network
architecture. The different roles of the people who would be able to handle the security
of the systems include IT security engineers, Chief Information Officer (CIO), Chief
Security Officer (CSO), Chief Technology Officer (CTO), Information Assurance
Manager (IAM) and other computer operators (Hu, West & Smarandescu, 2015). These
job of the IT professionals would mainly revolve around the protection of IT systems.
These would include the infrastructure, network and every other areas of IT. Securing
the information assets, data of customers, financial information would be very much
essential for securing the primary information of customers within the hotel business.
5. Conclusion
From the discussion above, it can be summarized that security handling is an
important part of an organization. There are many other models that handles the
security incidents that occurs in a company. Marriott International that has been
discussed in this report had faced a data breach which is explained in this report. As
discussed above, Security management provides robust as well as comprehensive view
related to any security issue within the company. Security incident includes active
threats as well as attempted intrusion for data breach. Security management helps in
identifying, recording, managing as well as analyzing the security threats or the security

9
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
incidents in the present time. The management of security incident mainly utilizes
combination of all the appliances, investigation that are human driven, as well as
software system that are included in a data breach. This process basically starts with
alert which states that the incident has already occurred and there is a need of
engagement of a team who will be capable of handling the incident. There always
remains a need of involving security handling incident model in a company and such a
model is selected in this report for handling further data breach in Marriott International.
This report explained the RSP model and a detailed explanation of the model
that is selected by the Marriott International. The reason for selecting the RSP model is
addresses with a diagram that shows the details of the RSP model. Detailed model
explanation with a discussion evaluating relation of the information security processes
are explained.
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
incidents in the present time. The management of security incident mainly utilizes
combination of all the appliances, investigation that are human driven, as well as
software system that are included in a data breach. This process basically starts with
alert which states that the incident has already occurred and there is a need of
engagement of a team who will be capable of handling the incident. There always
remains a need of involving security handling incident model in a company and such a
model is selected in this report for handling further data breach in Marriott International.
This report explained the RSP model and a detailed explanation of the model
that is selected by the Marriott International. The reason for selecting the RSP model is
addresses with a diagram that shows the details of the RSP model. Detailed model
explanation with a discussion evaluating relation of the information security processes
are explained.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
References
Ab Rahman, N. H., & Choo, K. K. R. (2015). A survey of information security incident
handling in the cloud. computers & security, 49, 45-69.
Ab Rahman, N. H., Cahyani, N. D. W., & Choo, K. K. R. (2017). Cloud incident handling
and forensic‐by‐design: cloud storage as a case study. Concurrency and
Computation: Practice and Experience, 29(14), e3868.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
management, 51(1), 138-151.
Cheng, L., Li, Y., Li, W., Holm, E., & Zhai, Q. (2013). Understanding the violation of IS
security policy in organizations: An integrated model based on social control and
deterrence theory. Computers & Security, 39, 447-459.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R.
(2013). Future directions for behavioral information security research. computers
& security, 32, 90-101.
Duffield, M. (2014). Global governance and the new wars: the merging of development
and security. Zed Books Ltd..
Flores, W. R., Antonsen, E., & Ekstedt, M. (2014). Information security knowledge
sharing in organizations: Investigating the effect of behavioral information
security governance and national culture. Computers & Security, 43, 90-110.
He, Y., & Johnson, C. (2017). Challenges of information security incident learning: An
industrial case study in a Chinese healthcare organization. Informatics for Health
and Social Care, 42(4), 393-408.
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
References
Ab Rahman, N. H., & Choo, K. K. R. (2015). A survey of information security incident
handling in the cloud. computers & security, 49, 45-69.
Ab Rahman, N. H., Cahyani, N. D. W., & Choo, K. K. R. (2017). Cloud incident handling
and forensic‐by‐design: cloud storage as a case study. Concurrency and
Computation: Practice and Experience, 29(14), e3868.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
management, 51(1), 138-151.
Cheng, L., Li, Y., Li, W., Holm, E., & Zhai, Q. (2013). Understanding the violation of IS
security policy in organizations: An integrated model based on social control and
deterrence theory. Computers & Security, 39, 447-459.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R.
(2013). Future directions for behavioral information security research. computers
& security, 32, 90-101.
Duffield, M. (2014). Global governance and the new wars: the merging of development
and security. Zed Books Ltd..
Flores, W. R., Antonsen, E., & Ekstedt, M. (2014). Information security knowledge
sharing in organizations: Investigating the effect of behavioral information
security governance and national culture. Computers & Security, 43, 90-110.
He, Y., & Johnson, C. (2017). Challenges of information security incident learning: An
industrial case study in a Chinese healthcare organization. Informatics for Health
and Social Care, 42(4), 393-408.

11
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
Hu, Q., West, R., & Smarandescu, L. (2015). The role of self-control in information
security violations: Insights from a cognitive neuroscience perspective. Journal of
Management Information Systems, 31(4), 6-48.
Kshetri, N. (2013). Privacy and security issues in cloud computing: The role of
institutions and institutional evolution. Telecommunications Policy, 37(4-5), 372-
386.
Nelson, R., & Staggers, N. (2016). Health Informatics-E-Book: An Interprofessional
Approach. Elsevier Health Sciences.
Pearson, S. (2013). Privacy, security and trust in cloud computing. In Privacy and
Security for Cloud Computing (pp. 3-42). Springer, London.
Rodrigues, J. J., De La Torre, I., Fernández, G., & López-Coronado, M. (2013). Analysis
of the security and privacy requirements of cloud-based electronic health records
systems. Journal of medical Internet research, 15(8).
Ruefle, R., Dorofee, A., Mundie, D., Householder, A. D., Murray, M., & Perl, S. J.
(2014). Computer security incident response team development and
evolution. IEEE Security & Privacy, 12(5), 16-26.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. Computers & Security, 56, 70-82.
Skopik, F., Settanni, G., & Fiedler, R. (2016). A problem shared is a problem halved: A
survey on the dimensions of collective cyber defense through security
information sharing. Computers & Security, 60, 154-176.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management
needs more holistic approach: A literature review. International Journal of
Information Management, 36(2), 215-225.
SECURITY, AUDIT AND COMPLIANCE FOR MARRIOTT INTERNATIONAL
Hu, Q., West, R., & Smarandescu, L. (2015). The role of self-control in information
security violations: Insights from a cognitive neuroscience perspective. Journal of
Management Information Systems, 31(4), 6-48.
Kshetri, N. (2013). Privacy and security issues in cloud computing: The role of
institutions and institutional evolution. Telecommunications Policy, 37(4-5), 372-
386.
Nelson, R., & Staggers, N. (2016). Health Informatics-E-Book: An Interprofessional
Approach. Elsevier Health Sciences.
Pearson, S. (2013). Privacy, security and trust in cloud computing. In Privacy and
Security for Cloud Computing (pp. 3-42). Springer, London.
Rodrigues, J. J., De La Torre, I., Fernández, G., & López-Coronado, M. (2013). Analysis
of the security and privacy requirements of cloud-based electronic health records
systems. Journal of medical Internet research, 15(8).
Ruefle, R., Dorofee, A., Mundie, D., Householder, A. D., Murray, M., & Perl, S. J.
(2014). Computer security incident response team development and
evolution. IEEE Security & Privacy, 12(5), 16-26.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. Computers & Security, 56, 70-82.
Skopik, F., Settanni, G., & Fiedler, R. (2016). A problem shared is a problem halved: A
survey on the dimensions of collective cyber defense through security
information sharing. Computers & Security, 60, 154-176.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management
needs more holistic approach: A literature review. International Journal of
Information Management, 36(2), 215-225.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





