Security Engineering: Cyber Security Threats and Impacts
VerifiedAdded on 2023/03/17
|6
|1416
|53
AI Summary
This document discusses common categories of cyber security threats and their impacts on organizations. It also explores the challenges of mobile and cloud computing in terms of privacy, security, limited energy source, and low bandwidth. The document provides insights into Denial of Service, Man in the Middle Attack, Phishing and Spear Phishing Attacks, Drive By Attack, Password Attack, SQL Injection Attack, Cross Site Scripting Attack, and Eavesdropping Attack.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SECURITY ENGINEERING
SECURITY ENGINEERING
Name of Student
Name of University
Author’s Note
SECURITY ENGINEERING
Name of Student
Name of University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1SECURITY ENGINEERING
Executive summary
Common categories of cyber security threats include Denial of service, Man in the
middle attack, phishing and spear phishing attacks, drive by attack, password attack and many
more. The provided categories of the attacks are categorized on the basis of their impact on
organizations. These attacks are deliberate attempt that is performed by a specific individual,
group of individuals or an organization in order to breach information system of a different
individual or a different organization. This is done in order to seek some benefit from disrupting
the network of a victim. Various cyber security categories have different impacts on an
organization and they are categorized accordingly. The Denial of service attack is considered as
the first priority because it is considered as the most vulnerable one, Man in the middle attack is
the second priority, Phishing attack is third, and drive by attack is fourth. Password attack is
considered as the fifth, SQL injection is sixth, Cross site scripting attack is seventh and
Eavesdropping attack is considered as the last priority. A cyber security category that should be
addressed with the organization includes Denial of service attack. The challenges that mobile as
well as cloud computing needs might bring to the organization include privacy and security,
alteration of network, limited energy source, service availability, low bandwidth and many more.
Among these challenges, low bandwidth is considered as the most vulnerable issue in the cloud
as well as mobile computing within an organization.
Executive summary
Common categories of cyber security threats include Denial of service, Man in the
middle attack, phishing and spear phishing attacks, drive by attack, password attack and many
more. The provided categories of the attacks are categorized on the basis of their impact on
organizations. These attacks are deliberate attempt that is performed by a specific individual,
group of individuals or an organization in order to breach information system of a different
individual or a different organization. This is done in order to seek some benefit from disrupting
the network of a victim. Various cyber security categories have different impacts on an
organization and they are categorized accordingly. The Denial of service attack is considered as
the first priority because it is considered as the most vulnerable one, Man in the middle attack is
the second priority, Phishing attack is third, and drive by attack is fourth. Password attack is
considered as the fifth, SQL injection is sixth, Cross site scripting attack is seventh and
Eavesdropping attack is considered as the last priority. A cyber security category that should be
addressed with the organization includes Denial of service attack. The challenges that mobile as
well as cloud computing needs might bring to the organization include privacy and security,
alteration of network, limited energy source, service availability, low bandwidth and many more.
Among these challenges, low bandwidth is considered as the most vulnerable issue in the cloud
as well as mobile computing within an organization.

2SECURITY ENGINEERING
challenges impact
Denial of service The carrying out of denial of service attack is comparatively
inexpensive, but impacts that it has on the organizations could be
enormous. A medium sized denial of service attack that usually lasts
for around a day could be bought for almost $500 on dark web, this
particular figure pales when compared to the harm that has already
been done to the service operator who would find that the service is
not available for 24 hours (Almorsy, Grundy & Müller, 2016).
Along with direct and financial costs, the unavailability of the
damage that has been occurred to the reputation of the company
might have a severe effect in the long run.
Man in the middle attack The impacts that are posted by Man in the middle attack include
sniffing, malware, binary patching, cookie insertion and many more.
Sniffing is an act that deals with reading traffic as well as collecting
data (Borgohain, Kumar & Sanyal, 2015). Sniffing is usually used
for the purpose of stealing the confidential data that belongs to the
organization. The malware uses misleading advertisements for
tricking a particular user for installing the malware.
phishing and spear
phishing attacks
Phishing and spear phishing attacks cause reputational damage,
intellectual damage and many more. This attack tends to disclose the
embarrassing internal communications that had taken place within an
organization; this creates reputational damage to the organization
(Hossain, Fotouhi & Hasan, 2015). the organization also has chance
to face direct loss, the phishing and spear phishing attacks on various
employees might result in fines levied by various regulatory bodies
in the case of various breached which results in violations in the
challenges impact
Denial of service The carrying out of denial of service attack is comparatively
inexpensive, but impacts that it has on the organizations could be
enormous. A medium sized denial of service attack that usually lasts
for around a day could be bought for almost $500 on dark web, this
particular figure pales when compared to the harm that has already
been done to the service operator who would find that the service is
not available for 24 hours (Almorsy, Grundy & Müller, 2016).
Along with direct and financial costs, the unavailability of the
damage that has been occurred to the reputation of the company
might have a severe effect in the long run.
Man in the middle attack The impacts that are posted by Man in the middle attack include
sniffing, malware, binary patching, cookie insertion and many more.
Sniffing is an act that deals with reading traffic as well as collecting
data (Borgohain, Kumar & Sanyal, 2015). Sniffing is usually used
for the purpose of stealing the confidential data that belongs to the
organization. The malware uses misleading advertisements for
tricking a particular user for installing the malware.
phishing and spear
phishing attacks
Phishing and spear phishing attacks cause reputational damage,
intellectual damage and many more. This attack tends to disclose the
embarrassing internal communications that had taken place within an
organization; this creates reputational damage to the organization
(Hossain, Fotouhi & Hasan, 2015). the organization also has chance
to face direct loss, the phishing and spear phishing attacks on various
employees might result in fines levied by various regulatory bodies
in the case of various breached which results in violations in the

3SECURITY ENGINEERING
HIPAA or the PCI. The overall cost incurred in the process of
protecting identities of customers or employees that have data stolen,
along with theft from the company itself could easily cost around
millions (Jokar, Arianpoo & Leung, 2016).
drive by attack In drive by attacks the cyber criminals concentrate on latching onto
various home networks and not just to access the internet but
especially to find their way badly in secured routers with the help of
working in an effective manner (Lin & Liao, 2017). They aim in
listening to the traffic and hence weaken the actual password as time
passes by. After the password id being compromised, the hacker has
a specific carte blanche in order to access machine along with adding
malware or any sort of key logger software, this enables the hackers
to wait till the users can access their bank (Pathan, 2016).
password attack Password attack can be occurred by various means, these means
include various dictionary attacks, offline detection, rainbow tables,
key logger attacks, spoofs, Trojans, social engineering, and many
more (Yang, Wu & Yin, 2017). Dictionary attacks are known as a
word based brute force attacks, here the hackers gain knowledge
regarding most common passwords that are used by the users; they
guess these passwords and hack the profiles of the users (Almorsy,
Grundy & Müller, 2016). The key logger attacks are occurred for the
same purpose, this malware sits hidden in a particular background
and records keystrokes when the keyboard is pressed, it logs mouse
movements or captures screenshots.
SQL injection attack SQL injection attack allows a particular hacker to view data that is
contained in database and then modify the content in it. It creates
HIPAA or the PCI. The overall cost incurred in the process of
protecting identities of customers or employees that have data stolen,
along with theft from the company itself could easily cost around
millions (Jokar, Arianpoo & Leung, 2016).
drive by attack In drive by attacks the cyber criminals concentrate on latching onto
various home networks and not just to access the internet but
especially to find their way badly in secured routers with the help of
working in an effective manner (Lin & Liao, 2017). They aim in
listening to the traffic and hence weaken the actual password as time
passes by. After the password id being compromised, the hacker has
a specific carte blanche in order to access machine along with adding
malware or any sort of key logger software, this enables the hackers
to wait till the users can access their bank (Pathan, 2016).
password attack Password attack can be occurred by various means, these means
include various dictionary attacks, offline detection, rainbow tables,
key logger attacks, spoofs, Trojans, social engineering, and many
more (Yang, Wu & Yin, 2017). Dictionary attacks are known as a
word based brute force attacks, here the hackers gain knowledge
regarding most common passwords that are used by the users; they
guess these passwords and hack the profiles of the users (Almorsy,
Grundy & Müller, 2016). The key logger attacks are occurred for the
same purpose, this malware sits hidden in a particular background
and records keystrokes when the keyboard is pressed, it logs mouse
movements or captures screenshots.
SQL injection attack SQL injection attack allows a particular hacker to view data that is
contained in database and then modify the content in it. It creates
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
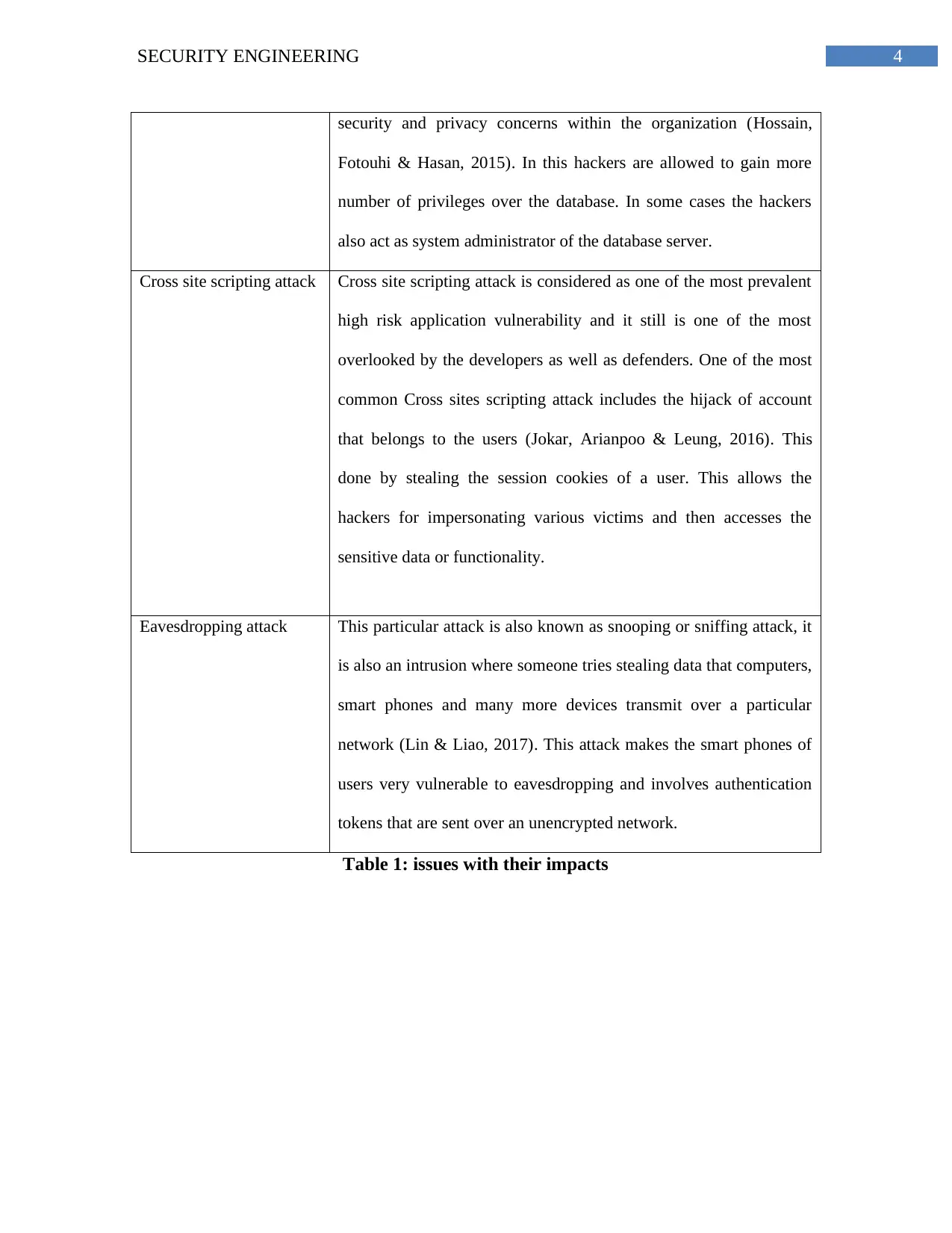
4SECURITY ENGINEERING
security and privacy concerns within the organization (Hossain,
Fotouhi & Hasan, 2015). In this hackers are allowed to gain more
number of privileges over the database. In some cases the hackers
also act as system administrator of the database server.
Cross site scripting attack Cross site scripting attack is considered as one of the most prevalent
high risk application vulnerability and it still is one of the most
overlooked by the developers as well as defenders. One of the most
common Cross sites scripting attack includes the hijack of account
that belongs to the users (Jokar, Arianpoo & Leung, 2016). This
done by stealing the session cookies of a user. This allows the
hackers for impersonating various victims and then accesses the
sensitive data or functionality.
Eavesdropping attack This particular attack is also known as snooping or sniffing attack, it
is also an intrusion where someone tries stealing data that computers,
smart phones and many more devices transmit over a particular
network (Lin & Liao, 2017). This attack makes the smart phones of
users very vulnerable to eavesdropping and involves authentication
tokens that are sent over an unencrypted network.
Table 1: issues with their impacts
security and privacy concerns within the organization (Hossain,
Fotouhi & Hasan, 2015). In this hackers are allowed to gain more
number of privileges over the database. In some cases the hackers
also act as system administrator of the database server.
Cross site scripting attack Cross site scripting attack is considered as one of the most prevalent
high risk application vulnerability and it still is one of the most
overlooked by the developers as well as defenders. One of the most
common Cross sites scripting attack includes the hijack of account
that belongs to the users (Jokar, Arianpoo & Leung, 2016). This
done by stealing the session cookies of a user. This allows the
hackers for impersonating various victims and then accesses the
sensitive data or functionality.
Eavesdropping attack This particular attack is also known as snooping or sniffing attack, it
is also an intrusion where someone tries stealing data that computers,
smart phones and many more devices transmit over a particular
network (Lin & Liao, 2017). This attack makes the smart phones of
users very vulnerable to eavesdropping and involves authentication
tokens that are sent over an unencrypted network.
Table 1: issues with their impacts

5SECURITY ENGINEERING
Bibliography
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of internet
of things. arXiv preprint arXiv:1501.02211.
Hossain, M. M., Fotouhi, M., & Hasan, R. (2015, June). Towards an analysis of security issues,
challenges, and open problems in the internet of things. In 2015 IEEE World Congress on
Services (pp. 21-28). IEEE.
Jokar, P., Arianpoo, N., & Leung, V. C. (2016). A survey on security issues in smart
grids. Security and Communication Networks, 9(3), 262-273.
Lin, I. C., & Liao, T. C. (2017). A Survey of Blockchain Security Issues and Challenges. IJ
Network Security, 19(5), 653-659.
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Yang, Y., Wu, L., Yin, G., Li, L., & Zhao, H. (2017). A survey on security and privacy issues in
Internet-of-Things. IEEE Internet of Things Journal, 4(5), 1250-1258.
Bibliography
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of internet
of things. arXiv preprint arXiv:1501.02211.
Hossain, M. M., Fotouhi, M., & Hasan, R. (2015, June). Towards an analysis of security issues,
challenges, and open problems in the internet of things. In 2015 IEEE World Congress on
Services (pp. 21-28). IEEE.
Jokar, P., Arianpoo, N., & Leung, V. C. (2016). A survey on security issues in smart
grids. Security and Communication Networks, 9(3), 262-273.
Lin, I. C., & Liao, T. C. (2017). A Survey of Blockchain Security Issues and Challenges. IJ
Network Security, 19(5), 653-659.
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Yang, Y., Wu, L., Yin, G., Li, L., & Zhao, H. (2017). A survey on security and privacy issues in
Internet-of-Things. IEEE Internet of Things Journal, 4(5), 1250-1258.
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





