Mitigation Strategies for Distributed Denial of Service (DDoS) Attack
Added on 2023-06-08
7 Pages1857 Words53 Views
INFORMATION SECURITY

1
Contents
INTRODUCTION.................................................................................................................................2
Q1..........................................................................................................................................................2
Name of the threat.............................................................................................................................2
System it attacks................................................................................................................................3
Performing attacks.............................................................................................................................3
Mitigation strategies..........................................................................................................................3
Potential exploiters............................................................................................................................4
Reflection..........................................................................................................................................5
CONCLUSION.....................................................................................................................................5
REFERENCES......................................................................................................................................6
Contents
INTRODUCTION.................................................................................................................................2
Q1..........................................................................................................................................................2
Name of the threat.............................................................................................................................2
System it attacks................................................................................................................................3
Performing attacks.............................................................................................................................3
Mitigation strategies..........................................................................................................................3
Potential exploiters............................................................................................................................4
Reflection..........................................................................................................................................5
CONCLUSION.....................................................................................................................................5
REFERENCES......................................................................................................................................6

2
INTRODUCTION
Cyber Security has become a very big challenge for the modern day IT users whether they are
individuals or the overall organisation. With the increase in the number of hacking activities,
organisations need to be ready with their mitigations strategies so as to confront these threats.
There are various types of threats emerging in cyber security (Von Solms and Van Niekerk,
2013). These threats can be extremely dangerous in the modern day competitive environment.
This report identifies the threats and provides mitigation strategies for it. It also evaluates the
type of systems that is attacked by this threat and also gives details about the ways in which
attacks are conducted.
Q1
Name of the threat
Distributed Denial of Service (DDoS) is an attack which is considered to be as the subclass of
Denial of Service (DoS) attack. It is an attack that includes multiple connected online devices
and is used for sending a target website with fake traffic. This is not conducted to breach the
security of the infrastructure rather they are done so that target website gets unavailable to
users that are legitimate (Yan, et. al. 2012). It is dangerous as it acts as a legitimate screen
behind which other attacks could be possible.
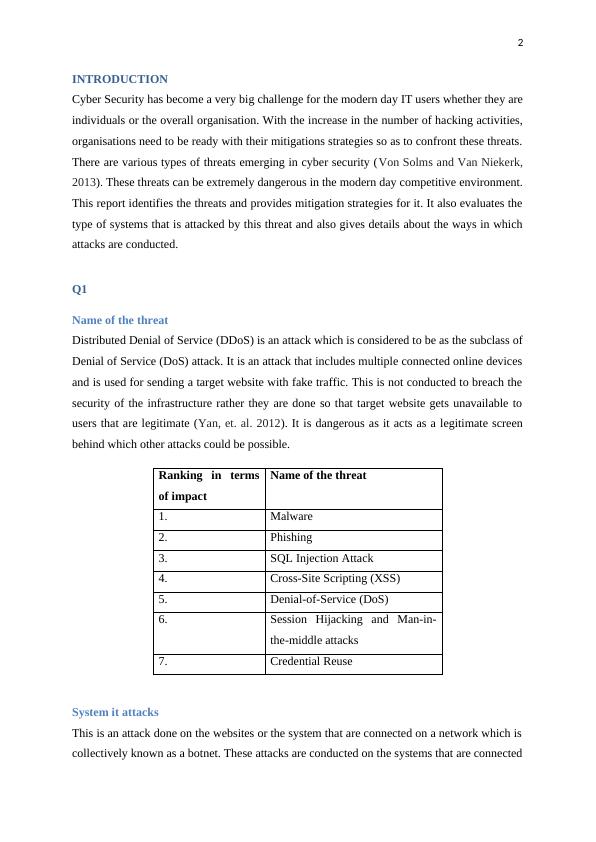
Ranking in terms
of impact
Name of the threat
1. Malware
2. Phishing
3. SQL Injection Attack
4. Cross-Site Scripting (XSS)
5. Denial-of-Service (DoS)
6. Session Hijacking and Man-in-
the-middle attacks
7. Credential Reuse
System it attacks
This is an attack done on the websites or the system that are connected on a network which is
collectively known as a botnet. These attacks are conducted on the systems that are connected
INTRODUCTION
Cyber Security has become a very big challenge for the modern day IT users whether they are
individuals or the overall organisation. With the increase in the number of hacking activities,
organisations need to be ready with their mitigations strategies so as to confront these threats.
There are various types of threats emerging in cyber security (Von Solms and Van Niekerk,
2013). These threats can be extremely dangerous in the modern day competitive environment.
This report identifies the threats and provides mitigation strategies for it. It also evaluates the
type of systems that is attacked by this threat and also gives details about the ways in which
attacks are conducted.
Q1
Name of the threat
Distributed Denial of Service (DDoS) is an attack which is considered to be as the subclass of
Denial of Service (DoS) attack. It is an attack that includes multiple connected online devices
and is used for sending a target website with fake traffic. This is not conducted to breach the
security of the infrastructure rather they are done so that target website gets unavailable to
users that are legitimate (Yan, et. al. 2012). It is dangerous as it acts as a legitimate screen
behind which other attacks could be possible.
Ranking in terms
of impact
Name of the threat
1. Malware
2. Phishing
3. SQL Injection Attack
4. Cross-Site Scripting (XSS)
5. Denial-of-Service (DoS)
6. Session Hijacking and Man-in-
the-middle attacks
7. Credential Reuse
System it attacks
This is an attack done on the websites or the system that are connected on a network which is
collectively known as a botnet. These attacks are conducted on the systems that are connected
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
DDOS attacklg...
|5
|1194
|491
Computer Security: DDoS Attackslg...
|11
|2444
|233
Article Review of Denial of Service Attack Assignmentlg...
|4
|688
|137
The Assignment on Information Securitylg...
|12
|832
|36
DDoS Attack at GitHub: Details, Outcome, Impact, and Mitigationlg...
|13
|2099
|392
Cyber Securitylg...
|1
|274
|55
