University Security in Computing and Information Technology Assignment
VerifiedAdded on 2022/10/01
|9
|1672
|462
Homework Assignment
AI Summary
This document presents a comprehensive solution to a security in computing and information technology assignment, covering various cryptographic techniques. The assignment includes cryptanalysis of simple substitution ciphers, double transposition ciphers, and complex substitution ciphers. It also addresses the application of hash algorithms, specifically SHA-256, in a sealed bid auction scenario. Furthermore, the solution demonstrates the encryption and decryption steps using the Paillier encryption algorithm. The solution provides step-by-step explanations and calculations for each problem, offering a detailed understanding of the concepts and practical applications of these security measures. The assignment covers topics from lectures 1-4 on security in computing and information technology, including symmetric and asymmetric key cryptography.

Running head: Security in computing and information technology
Security in computing and information technology
Name of the Student
Name of the University
Author Note
Security in computing and information technology
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security in computing and information technology 1
Q1 Cryptanalysis
a)
[Cryptanalysis on Simple Substituion Cipher] (Marks 1)
Show step-by-step process to find the plaintext and the key for the following ciphertext
using the concept of simple substitution cipher ‘shift by n’ as discussed in Lecture-1:
Ciphertext: NZXMTYLETZYD. Find the plaintext using shift by n as discussed in
Lecture-1 and tutorial-1.
Simple substitution cipher is a figure that has been used for a huge number of years. It
fundamentally comprises of substituting each plaintext character for an alternate cipher text
character. It varies from the Caesar cipher in that the figure letters in order isn't just the letter
set moved, it is totally confused.
For example
The algorithm for finding the cipher text is a shown below. The 26 letters of alphabet
are used as plain text and the cipher text is the inversion of the letters of alphabet.
Plain alphabet: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher alphabet: DEFGHIJKLMNOPQRSTUVWXYZABC
So, from the above cryptanalysis formula, the cipher text was given as NZXMTYLETZYD.
In this case we have to look at the alternate letters in the position of the plain alphabet letters
Therefore, the correct plain text for the cipher text NZXMTYLETZYD
The key that is used for decoding the cipher text is FTHESANDSTAR.
a b c d e f g h i j k l m n o p q r s t u v w x y z
y s f e m n r x I b j v w l k u a d t z o g p c h q
Q1 Cryptanalysis
a)
[Cryptanalysis on Simple Substituion Cipher] (Marks 1)
Show step-by-step process to find the plaintext and the key for the following ciphertext
using the concept of simple substitution cipher ‘shift by n’ as discussed in Lecture-1:
Ciphertext: NZXMTYLETZYD. Find the plaintext using shift by n as discussed in
Lecture-1 and tutorial-1.
Simple substitution cipher is a figure that has been used for a huge number of years. It
fundamentally comprises of substituting each plaintext character for an alternate cipher text
character. It varies from the Caesar cipher in that the figure letters in order isn't just the letter
set moved, it is totally confused.
For example
The algorithm for finding the cipher text is a shown below. The 26 letters of alphabet
are used as plain text and the cipher text is the inversion of the letters of alphabet.
Plain alphabet: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher alphabet: DEFGHIJKLMNOPQRSTUVWXYZABC
So, from the above cryptanalysis formula, the cipher text was given as NZXMTYLETZYD.
In this case we have to look at the alternate letters in the position of the plain alphabet letters
Therefore, the correct plain text for the cipher text NZXMTYLETZYD
The key that is used for decoding the cipher text is FTHESANDSTAR.
a b c d e f g h i j k l m n o p q r s t u v w x y z
y s f e m n r x I b j v w l k u a d t z o g p c h q
2Security in computing and information technology
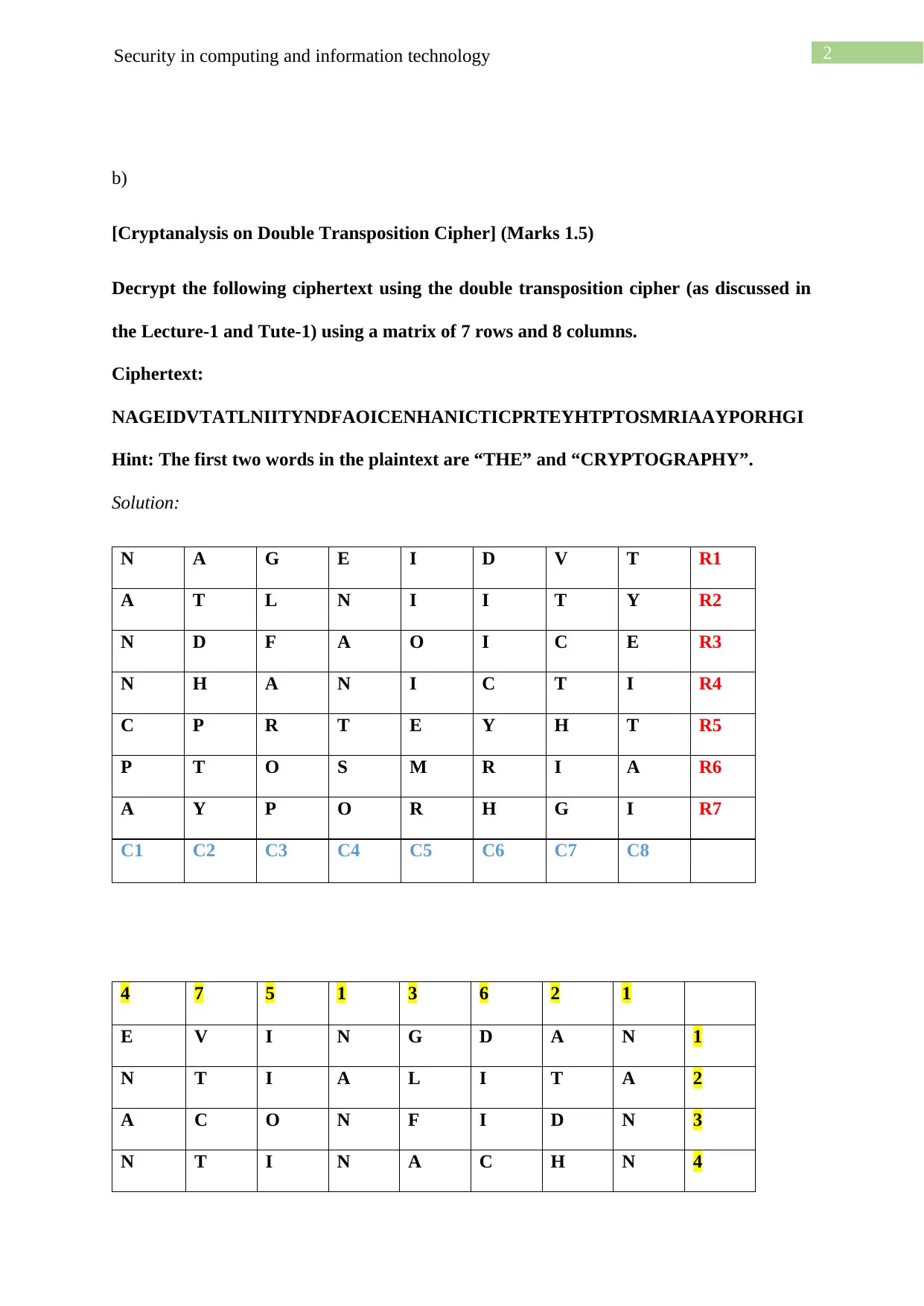
b)
[Cryptanalysis on Double Transposition Cipher] (Marks 1.5)
Decrypt the following ciphertext using the double transposition cipher (as discussed in
the Lecture-1 and Tute-1) using a matrix of 7 rows and 8 columns.
Ciphertext:
NAGEIDVTATLNIITYNDFAOICENHANICTICPRTEYHTPTOSMRIAAYPORHGI
Hint: The first two words in the plaintext are “THE” and “CRYPTOGRAPHY”.
Solution:
N A G E I D V T R1
A T L N I I T Y R2
N D F A O I C E R3
N H A N I C T I R4
C P R T E Y H T R5
P T O S M R I A R6
A Y P O R H G I R7
C1 C2 C3 C4 C5 C6 C7 C8
4 7 5 1 3 6 2 1
E V I N G D A N 1
N T I A L I T A 2
A C O N F I D N 3
N T I N A C H N 4
b)
[Cryptanalysis on Double Transposition Cipher] (Marks 1.5)
Decrypt the following ciphertext using the double transposition cipher (as discussed in
the Lecture-1 and Tute-1) using a matrix of 7 rows and 8 columns.
Ciphertext:
NAGEIDVTATLNIITYNDFAOICENHANICTICPRTEYHTPTOSMRIAAYPORHGI
Hint: The first two words in the plaintext are “THE” and “CRYPTOGRAPHY”.
Solution:
N A G E I D V T R1
A T L N I I T Y R2
N D F A O I C E R3
N H A N I C T I R4
C P R T E Y H T R5
P T O S M R I A R6
A Y P O R H G I R7
C1 C2 C3 C4 C5 C6 C7 C8
4 7 5 1 3 6 2 1
E V I N G D A N 1
N T I A L I T A 2
A C O N F I D N 3
N T I N A C H N 4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
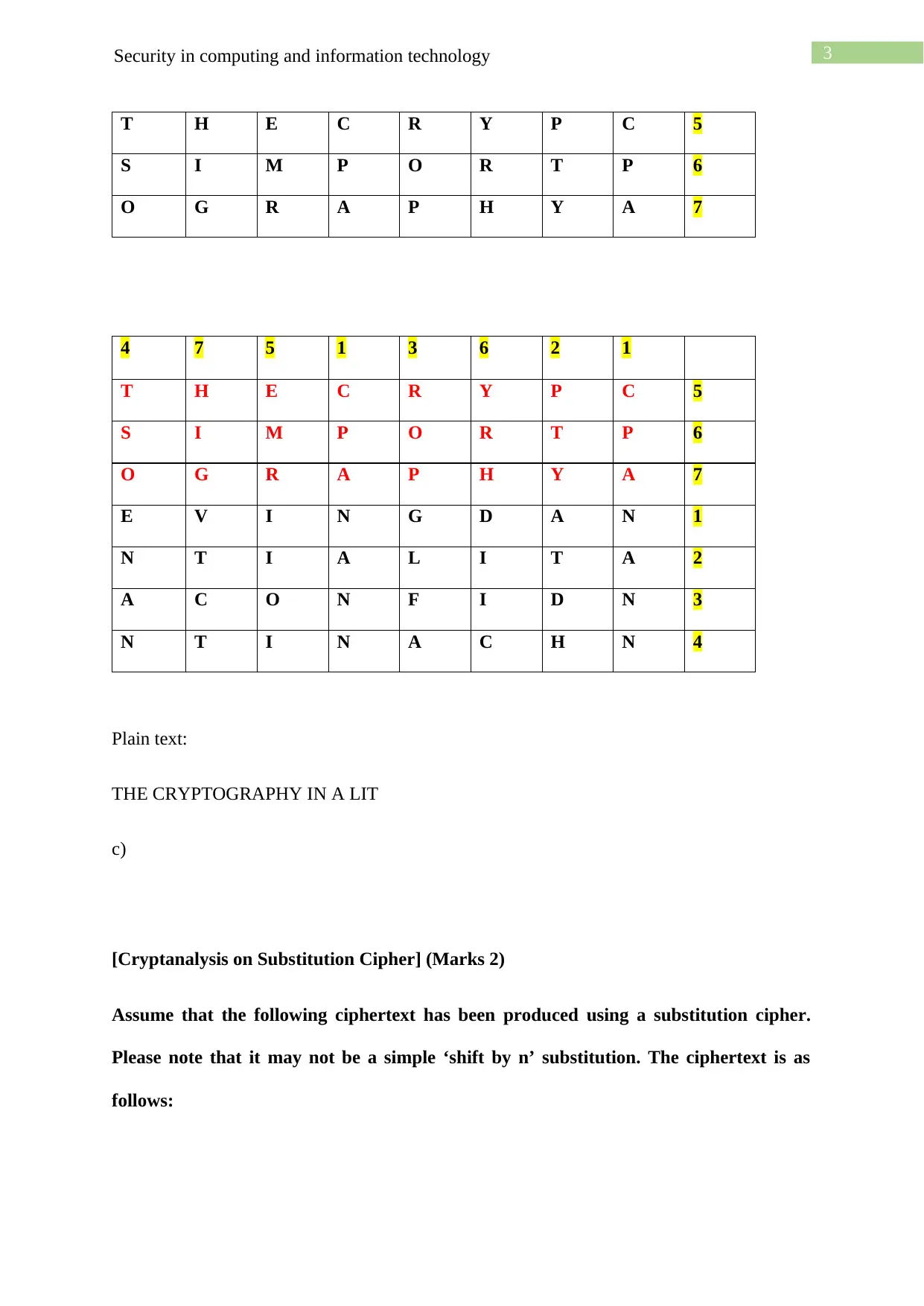
3Security in computing and information technology
T H E C R Y P C 5
S I M P O R T P 6
O G R A P H Y A 7
4 7 5 1 3 6 2 1
T H E C R Y P C 5
S I M P O R T P 6
O G R A P H Y A 7
E V I N G D A N 1
N T I A L I T A 2
A C O N F I D N 3
N T I N A C H N 4
Plain text:
THE CRYPTOGRAPHY IN A LIT
c)
[Cryptanalysis on Substitution Cipher] (Marks 2)
Assume that the following ciphertext has been produced using a substitution cipher.
Please note that it may not be a simple ‘shift by n’ substitution. The ciphertext is as
follows:
T H E C R Y P C 5
S I M P O R T P 6
O G R A P H Y A 7
4 7 5 1 3 6 2 1
T H E C R Y P C 5
S I M P O R T P 6
O G R A P H Y A 7
E V I N G D A N 1
N T I A L I T A 2
A C O N F I D N 3
N T I N A C H N 4
Plain text:
THE CRYPTOGRAPHY IN A LIT
c)
[Cryptanalysis on Substitution Cipher] (Marks 2)
Assume that the following ciphertext has been produced using a substitution cipher.
Please note that it may not be a simple ‘shift by n’ substitution. The ciphertext is as
follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4Security in computing and information technology
MDUNPWV UF IYR PEUQUIV BK PT UTLUNULSPQ BD JDBSM IB FRWQSLR
IYRZFRQNRF, BD UTKBDZPIUBT PEBSI IYRZFRQNRF, PTL IYRDREV
RHMDRFF IYRZFRQNRF FRQRWIUNRQV. IYR EBSTLPDURF PTL WBTIRTI
BK AYPI UF WBTFULRDRL MDUNPIR LUKKRD PZBTJ WSQISDRF PTL
UTLUNULSPQF. AYRT FBZRIYUTJ UF MDUNPIR IB P MRDFBT, UI SFSPQQV
ZRPTF IYPI FBZRIYUTJ UF UTYRDRTIQV FMRWUPQ BD FRTFUIUNR IB
IYRZ. IYR LBZPUT BK MDUNPWV MPDIUPQQV BNRDQPMF AUIY
FRWSDUIV, AYUWY WPT UTWQSLR IYR WBTWRMIF BK PMMDBMDUPIR
SFR, PF ARQQ PF MDBIRWIUBT BK UTKBDZPIUBT. MDUNPWV ZPV PQFB
IPCR IYR KBDZ BK EBLUQV UTIRJDUIV. IYR DUJYI TBI IB ER FSEXRWIRL
IB STFPTWIUBTRL UTNPFUBTF BK MDUNPWV EV IYR JBNRDTZRTI,
WBDMBDPIUBTF BD UTLUNULSPQF UF MPDI BK ZPTV WBSTIDURF'
MDUNPWV QPAF, PTL UT FBZR WPFRF, WBTFIUISIUBTF.
Solution:
Cipher text:
MDUNPWV UF IYR PEUQUIV BK PT UTLUNULSPQ BD JDBSM IB FRWQSLR
IYRZFRQNRF, BD UTKBDZPIUBT PEBSI IYRZFRQNRF, PTL IYRDREV RHMDRFF
IYRZFRQNRF FRQRWIUNRQV. IYR EBSTLPDURF PTL WBTIRTI BK AYPI UF
WBTFULRDRL MDUNPIR LUKKRD PZBTJ WSQISDRF PTL UTLUNULSPQF. AYRT
FBZRIYUTJ UF MDUNPIR IB P MRDFBT, UI SFSPQQV ZRPTF IYPI FBZRIYUTJ UF
UTYRDRTIQV FMRWUPQ BD FRTFUIUNR IB IYRZ. IYR LBZPUT BK MDUNPWV
MPDIUPQQV BNRDQPMF AUIY FRWSDUIV, AYUWY WPT UTWQSLR IYR
WBTWRMIF BK PMMDBMDUPIR SFR, PF ARQQ PF MDBIRWIUBT BK
UTKBDZPIUBT. MDUNPWV ZPV PQFB IPCR IYR KBDZ BK EBLUQV UTIRJDUIV.
MDUNPWV UF IYR PEUQUIV BK PT UTLUNULSPQ BD JDBSM IB FRWQSLR
IYRZFRQNRF, BD UTKBDZPIUBT PEBSI IYRZFRQNRF, PTL IYRDREV
RHMDRFF IYRZFRQNRF FRQRWIUNRQV. IYR EBSTLPDURF PTL WBTIRTI
BK AYPI UF WBTFULRDRL MDUNPIR LUKKRD PZBTJ WSQISDRF PTL
UTLUNULSPQF. AYRT FBZRIYUTJ UF MDUNPIR IB P MRDFBT, UI SFSPQQV
ZRPTF IYPI FBZRIYUTJ UF UTYRDRTIQV FMRWUPQ BD FRTFUIUNR IB
IYRZ. IYR LBZPUT BK MDUNPWV MPDIUPQQV BNRDQPMF AUIY
FRWSDUIV, AYUWY WPT UTWQSLR IYR WBTWRMIF BK PMMDBMDUPIR
SFR, PF ARQQ PF MDBIRWIUBT BK UTKBDZPIUBT. MDUNPWV ZPV PQFB
IPCR IYR KBDZ BK EBLUQV UTIRJDUIV. IYR DUJYI TBI IB ER FSEXRWIRL
IB STFPTWIUBTRL UTNPFUBTF BK MDUNPWV EV IYR JBNRDTZRTI,
WBDMBDPIUBTF BD UTLUNULSPQF UF MPDI BK ZPTV WBSTIDURF'
MDUNPWV QPAF, PTL UT FBZR WPFRF, WBTFIUISIUBTF.
Solution:
Cipher text:
MDUNPWV UF IYR PEUQUIV BK PT UTLUNULSPQ BD JDBSM IB FRWQSLR
IYRZFRQNRF, BD UTKBDZPIUBT PEBSI IYRZFRQNRF, PTL IYRDREV RHMDRFF
IYRZFRQNRF FRQRWIUNRQV. IYR EBSTLPDURF PTL WBTIRTI BK AYPI UF
WBTFULRDRL MDUNPIR LUKKRD PZBTJ WSQISDRF PTL UTLUNULSPQF. AYRT
FBZRIYUTJ UF MDUNPIR IB P MRDFBT, UI SFSPQQV ZRPTF IYPI FBZRIYUTJ UF
UTYRDRTIQV FMRWUPQ BD FRTFUIUNR IB IYRZ. IYR LBZPUT BK MDUNPWV
MPDIUPQQV BNRDQPMF AUIY FRWSDUIV, AYUWY WPT UTWQSLR IYR
WBTWRMIF BK PMMDBMDUPIR SFR, PF ARQQ PF MDBIRWIUBT BK
UTKBDZPIUBT. MDUNPWV ZPV PQFB IPCR IYR KBDZ BK EBLUQV UTIRJDUIV.

5Security in computing and information technology
IYR DUJYI TBI IB ER FSEXRWIRL IB STFPTWIUBTRL UTNPFUBTF BK MDUNPWV
EV IYR JBNRDTZRTI, WBDMBDPIUBTF BD UTLUNULSPQF UF MPDI BK ZPTV
WBSTIDURF' MDUNPWV QPAF, PTL UT FBZR WPFRF, WBTFIUISIUBTF
Key:
abcdefghijklmnopqrstuvwxyz
pewlrkjyuxcqztbmgdfisnahvo
PRIVACY IS THE ABILITY OF AN INDIVIDUAL OR GROUP TO SECLUDE
THEMSELVES, OR INFORMATION ABOUT THEMSELVES, AND THEREBY
EXPRESS THEMSELVES SELECTIVELY. THE BOUNDARIES AND CONTENT OF
WHAT IS CONSIDERED PRIVATE DIFFER AMONG CULTURES AND
INDIVIDUALS. WHEN SOMETHING IS PRIVATE TO A PERSON, IT USUALLY
MEANS THAT SOMETHING IS INHERENTLY SPECIAL OR SENSITIVE TO THEM.
THE DOMAIN OF PRIVACY PARTIALLY OVERLAPS WITH SECURITY, WHICH
CAN INCLUDE THE CONCEPTS OF APPROPRIATE USE, AS WELL AS
PROTECTION OF INFORMATION. PRIVACY MAY ALSO TAKE THE FORM OF
BODILY INTEGRITY. THE RIGHT NOT TO BE SUBJECTED TO UNSANCTIONED
INVASIONS OF PRIVACY BY THE GOVERNMENT, CORPORATIONS OR
INDIVIDUALS IS PART OF MANY COUNTRIES' PRIVACY LAWS, AND IN SOME
CASES, CONSTITUTIONS.
Question 2:
Application of Hash Algorithm (Marks: 2)
IYR DUJYI TBI IB ER FSEXRWIRL IB STFPTWIUBTRL UTNPFUBTF BK MDUNPWV
EV IYR JBNRDTZRTI, WBDMBDPIUBTF BD UTLUNULSPQF UF MPDI BK ZPTV
WBSTIDURF' MDUNPWV QPAF, PTL UT FBZR WPFRF, WBTFIUISIUBTF
Key:
abcdefghijklmnopqrstuvwxyz
pewlrkjyuxcqztbmgdfisnahvo
PRIVACY IS THE ABILITY OF AN INDIVIDUAL OR GROUP TO SECLUDE
THEMSELVES, OR INFORMATION ABOUT THEMSELVES, AND THEREBY
EXPRESS THEMSELVES SELECTIVELY. THE BOUNDARIES AND CONTENT OF
WHAT IS CONSIDERED PRIVATE DIFFER AMONG CULTURES AND
INDIVIDUALS. WHEN SOMETHING IS PRIVATE TO A PERSON, IT USUALLY
MEANS THAT SOMETHING IS INHERENTLY SPECIAL OR SENSITIVE TO THEM.
THE DOMAIN OF PRIVACY PARTIALLY OVERLAPS WITH SECURITY, WHICH
CAN INCLUDE THE CONCEPTS OF APPROPRIATE USE, AS WELL AS
PROTECTION OF INFORMATION. PRIVACY MAY ALSO TAKE THE FORM OF
BODILY INTEGRITY. THE RIGHT NOT TO BE SUBJECTED TO UNSANCTIONED
INVASIONS OF PRIVACY BY THE GOVERNMENT, CORPORATIONS OR
INDIVIDUALS IS PART OF MANY COUNTRIES' PRIVACY LAWS, AND IN SOME
CASES, CONSTITUTIONS.
Question 2:
Application of Hash Algorithm (Marks: 2)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6Security in computing and information technology
Assume that Alice, Bob and Trudy want to participate in an online auction to purchase
an item. The idea here is that these are supposed to be sealed bids, i.e. each bidder gets
one chance to submit a secret bid. In order to submit a secret bid, a bidder generates
hash value of their bid amount using SHA-256 hash algorithm and sends the hash value
as their bid to the auctioneer. All of the bids are revealed when all of the participants
send their secret bid to the auctioneer. Trudy is a smart person who is certain that Alice
and Bob will both place their bids between $351 and $365. Trudy
captures the following hash values of Alice and bob:
Hash value of Alice:
73DAA9289DDD08A53BA86F065DDB07BF915ABA208BEC652E999613D2A8444228
Hash value of Bob:
9197E4844ABED2FEA3569A2ACF7B0D584C979C333AB7AE10BA6C3398987765A
Solution:
Suppose Alice, Bob and Trudy are bidders
They will send each a secret bids
But Trudy is a nice guy and understands that Alice and Bob has places a bid between $351
and $365
Alice will submit bids A, Bob B and Trudy C each will create an Algorithm h(A), h(B) and
h(C) respectively
For example
Alice submit bid
h(351)=73DAA9289DD08A53BA86F065DDB07BF915ABA208BEC652E999613D2A8444
228
Bob
Assume that Alice, Bob and Trudy want to participate in an online auction to purchase
an item. The idea here is that these are supposed to be sealed bids, i.e. each bidder gets
one chance to submit a secret bid. In order to submit a secret bid, a bidder generates
hash value of their bid amount using SHA-256 hash algorithm and sends the hash value
as their bid to the auctioneer. All of the bids are revealed when all of the participants
send their secret bid to the auctioneer. Trudy is a smart person who is certain that Alice
and Bob will both place their bids between $351 and $365. Trudy
captures the following hash values of Alice and bob:
Hash value of Alice:
73DAA9289DDD08A53BA86F065DDB07BF915ABA208BEC652E999613D2A8444228
Hash value of Bob:
9197E4844ABED2FEA3569A2ACF7B0D584C979C333AB7AE10BA6C3398987765A
Solution:
Suppose Alice, Bob and Trudy are bidders
They will send each a secret bids
But Trudy is a nice guy and understands that Alice and Bob has places a bid between $351
and $365
Alice will submit bids A, Bob B and Trudy C each will create an Algorithm h(A), h(B) and
h(C) respectively
For example
Alice submit bid
h(351)=73DAA9289DD08A53BA86F065DDB07BF915ABA208BEC652E999613D2A8444
228
Bob
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7Security in computing and information technology
h(365)=9197E4844ABED2FEA3569A2ACF7B0D584C979C333AB7AE10BA6C33989877
6F5A
From this Trudy could learn that he must submit h(366) for him to win the bid. So, he will
generate h (366) algorithm and submit.
Question 6
Paillier Encryption algorithm (Marks: 2.5)
Now, Alice and Bob decide to use Paillier encryption algorithm for their new
communication. Alice has a message M=4567 to send to Bob securely using Paillier
encryption algorithm. Bob chooses p=137, q=83, and selects an integer g =173. Alice
selects a random number r=73. Show the encryption and decryption steps
Solution:
Sender Alice: M= 4567, r =73
Receiver Bob: p=137, q =83, g =173
The algorithm is as follows:
Select two of the large primes, p and q.
Calculate the product n=p x q, gcd(n,Φ(n)) = 1, where Φ(n) is Euler Function.
Choose a random number g, gcd(L(gλ mod n2 ) n) = 1 where L(t)= (t 1) / n and
λ(n)=lcm(p 1 q 1) yp p g gcd(L(g mod n ), n) = 1, where L(t)= (t-1) / n and
λ(n)=lcm(p-1,q-1).
The public key is composed of (g, n), while the private key is composed of (p,q,λ).
The Encryption of a message m < n is given by:
c=gmr n mod n2
The Decryption of ciphertext c is given by: The Decryption of ciphertext c is given
by:
m=(L(gλ mod n2 )/L(gλ mod n2 ) )mod n
h(365)=9197E4844ABED2FEA3569A2ACF7B0D584C979C333AB7AE10BA6C33989877
6F5A
From this Trudy could learn that he must submit h(366) for him to win the bid. So, he will
generate h (366) algorithm and submit.
Question 6
Paillier Encryption algorithm (Marks: 2.5)
Now, Alice and Bob decide to use Paillier encryption algorithm for their new
communication. Alice has a message M=4567 to send to Bob securely using Paillier
encryption algorithm. Bob chooses p=137, q=83, and selects an integer g =173. Alice
selects a random number r=73. Show the encryption and decryption steps
Solution:
Sender Alice: M= 4567, r =73
Receiver Bob: p=137, q =83, g =173
The algorithm is as follows:
Select two of the large primes, p and q.
Calculate the product n=p x q, gcd(n,Φ(n)) = 1, where Φ(n) is Euler Function.
Choose a random number g, gcd(L(gλ mod n2 ) n) = 1 where L(t)= (t 1) / n and
λ(n)=lcm(p 1 q 1) yp p g gcd(L(g mod n ), n) = 1, where L(t)= (t-1) / n and
λ(n)=lcm(p-1,q-1).
The public key is composed of (g, n), while the private key is composed of (p,q,λ).
The Encryption of a message m < n is given by:
c=gmr n mod n2
The Decryption of ciphertext c is given by: The Decryption of ciphertext c is given
by:
m=(L(gλ mod n2 )/L(gλ mod n2 ) )mod n

8Security in computing and information technology
Encryption:
gcd(pq)(p-1)(q-1)= 1
Decryption:
gcd (11371,11152) =1
Receiver computes:
n= 11371
g =173
Receiver sends (n, g) = (11371, 173)
Private Key parameter is calculated
Parameter y = lcm(p-1)*(q-1)
Hence k= L(u)
Encryption:
gcd(pq)(p-1)(q-1)= 1
Decryption:
gcd (11371,11152) =1
Receiver computes:
n= 11371
g =173
Receiver sends (n, g) = (11371, 173)
Private Key parameter is calculated
Parameter y = lcm(p-1)*(q-1)
Hence k= L(u)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





