MITS5002 Assignment 1 & 2: Security Issues in Cloud Computing
VerifiedAdded on 2023/01/17
|14
|624
|70
Report
AI Summary
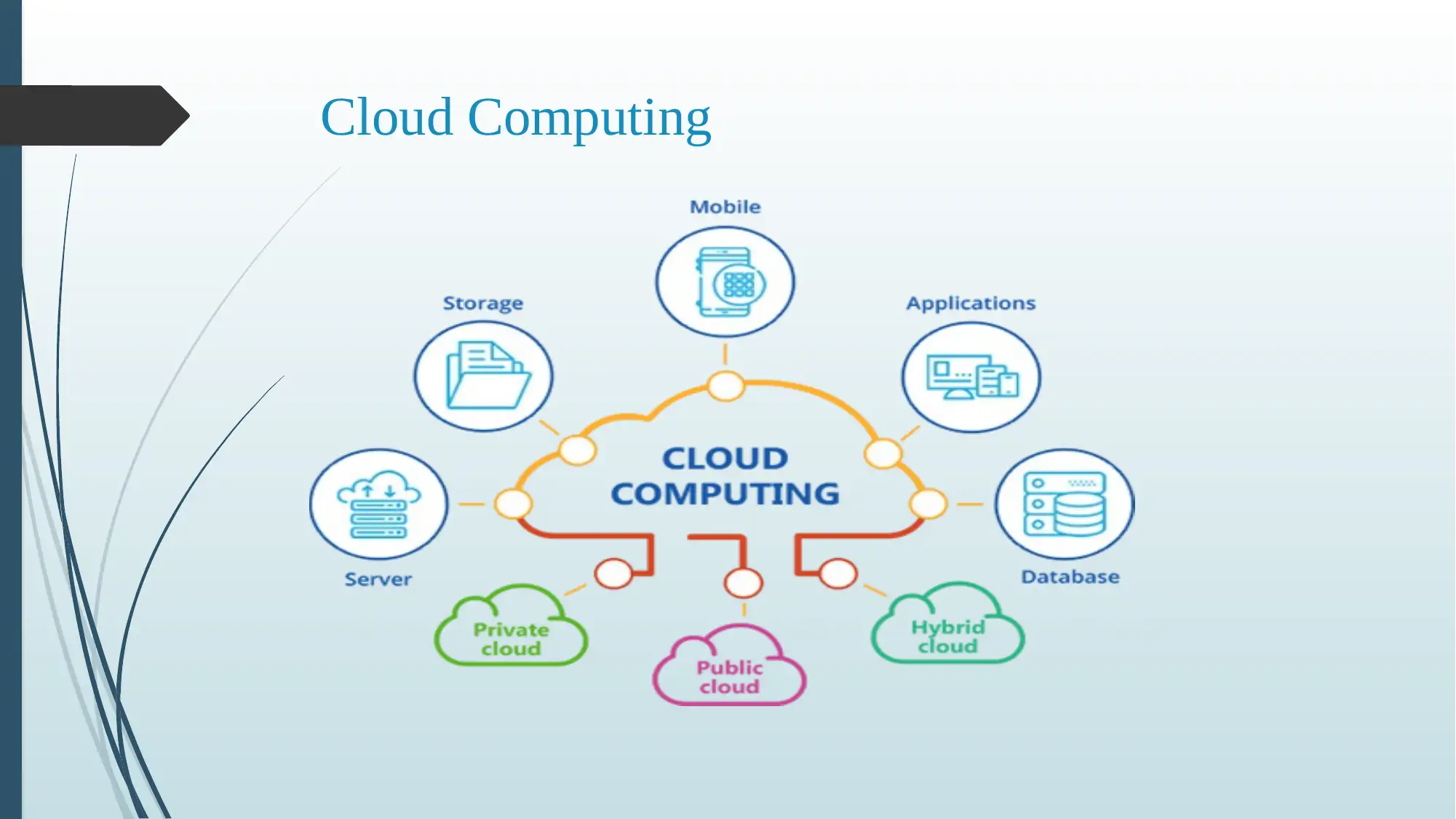
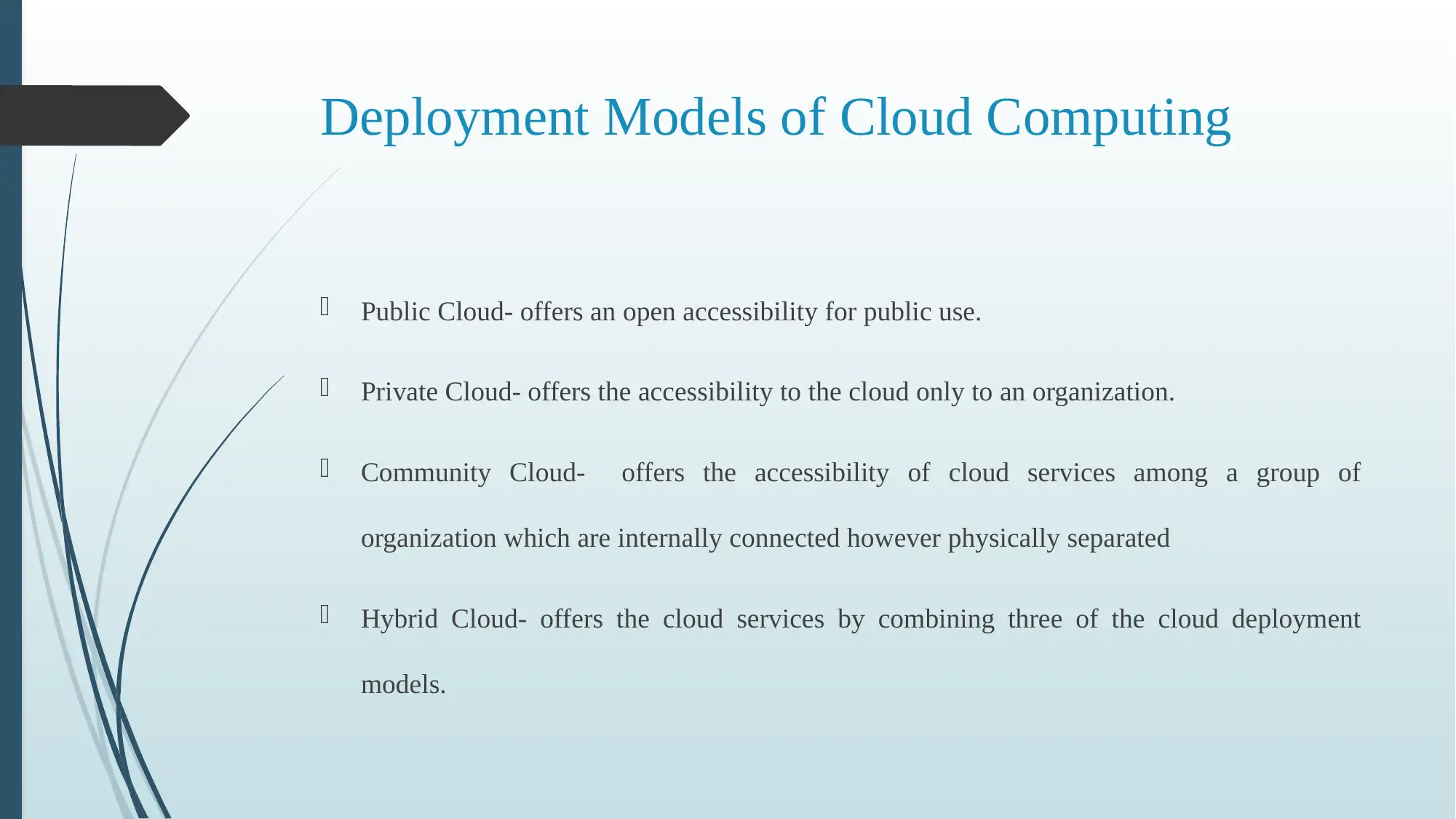
This report delves into the security challenges inherent in cloud computing environments. It highlights key concerns such as data security, the risk of external cyber-attacks leading to data breaches, and the importance of data integrity to prevent unauthorized access or modification. The report also addresses the issue of information availability, emphasizing the potential for server failures and the subsequent impact on data accessibility. Furthermore, it explores data confidentiality issues, including the risks associated with third-party data handlers and data analysis. The report proposes mitigation strategies, such as the incorporation of MAC algorithms for encryption, to enhance cloud computing operations and concludes by emphasizing the importance of addressing these limitations to ensure organizational success. The report is based on the MITS5002 Software Engineering Methodology curriculum, focusing on the critical aspects of cloud computing security.
1 out of 14

















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)