Security and Risk Management: Proposal for MYOB, Australia
VerifiedAdded on 2020/03/16
|15
|3258
|295
Report
AI Summary
This report presents a comprehensive security and risk management proposal for MYOB Australia. It begins with an introduction to the organization and the shift to cloud-based operations, highlighting the associated security risks. The investigation section details the tools and techniques used to analyze MYOB's current situation, including documentation review, Delphi technique, interviews, and SWOT analysis. A risk analysis matrix identifies and assesses various risks, such as system integration vulnerabilities, technical setup limitations, internal sabotage, poor auditing, and cyber security threats. The report then outlines a disaster recovery plan addressing these risks, emphasizing the need for preventative measures, strict policies, robust firewalls, and technical upgrades. Finally, it proposes a contingency plan and business continuity plan (BCP) to ensure business resilience. The report offers strategies to mitigate risks and maintain operational continuity in the face of potential disruptions, offering valuable insights into proactive risk management for organizations like MYOB.

Running Head: SECURITY AND RISK MANAGEMENT
Security and Risk Management: Proposal for MYOB, Australia
Name of the Student
Name of the University
Security and Risk Management: Proposal for MYOB, Australia
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY AND RISK MANAGEMENT
Table of Contents
1.0 Introduction................................................................................................................................2
2.0 Investigation..............................................................................................................................3
3.0 Risk Analysis Matrix.................................................................................................................4
4.0 Disaster Recovery (DR) Plan.....................................................................................................8
5.0 Proposal for Contingency Plan and Business Continuity Plan (BCP).....................................10
6.0 Analysis and Report on Controls.............................................................................................11
7.0 Logical Map of Organizational Structure................................................................................12
8.0 Conclusion...............................................................................................................................13
References......................................................................................................................................14
Table of Contents
1.0 Introduction................................................................................................................................2
2.0 Investigation..............................................................................................................................3
3.0 Risk Analysis Matrix.................................................................................................................4
4.0 Disaster Recovery (DR) Plan.....................................................................................................8
5.0 Proposal for Contingency Plan and Business Continuity Plan (BCP).....................................10
6.0 Analysis and Report on Controls.............................................................................................11
7.0 Logical Map of Organizational Structure................................................................................12
8.0 Conclusion...............................................................................................................................13
References......................................................................................................................................14

2SECURITY AND RISK MANAGEMENT
1.0 Introduction
The chosen organization for the investigation of various risks and preparation of risk
management plan is MYOB (Mind Your Own Business), Australia. MYOB is an Australian
based organization that develops tax and accounting softwares for helping small and medium
sized business organizations. Since the advent of cloud computing services, MYOB has hosted
its entire operations online in the cloud interface (Lim et al., 2013). Instead of physical storage
and manual handling of the operations, the cloud based system is much more efficient and does
not require additional physical storage space. However, due to hosting the entire operations, the
company faces some serious security risks. The main risks will be discussed later in this report.
Due to the chances of occurrence of the risks, some disaster may occur during anytime that will
not only disrupt in the business operations but will also incur serious long term consequences in
the business of MYOB. Hence, it is important to prepare a contingency plan in order to recover
the system from the possible attacks and security issues. However, contingency planning is only
a short term plan for system recovery. It is more important to develop a risk management plan in
order to ensure that the chances of the risks are minimized to as low as possible. Moreover,
business continuity planning is required in order to maintain business continuity in spite of
occurrence of the risks.
In this report, the current situation at MYOB has been analyzed with the help of some
risk analysis tools and techniques. Moreover, the main risks have been identified and a
contingency plan has been prepared. Finally, a proposal has been prepared for the business
continuity planning of the organization.
1.0 Introduction
The chosen organization for the investigation of various risks and preparation of risk
management plan is MYOB (Mind Your Own Business), Australia. MYOB is an Australian
based organization that develops tax and accounting softwares for helping small and medium
sized business organizations. Since the advent of cloud computing services, MYOB has hosted
its entire operations online in the cloud interface (Lim et al., 2013). Instead of physical storage
and manual handling of the operations, the cloud based system is much more efficient and does
not require additional physical storage space. However, due to hosting the entire operations, the
company faces some serious security risks. The main risks will be discussed later in this report.
Due to the chances of occurrence of the risks, some disaster may occur during anytime that will
not only disrupt in the business operations but will also incur serious long term consequences in
the business of MYOB. Hence, it is important to prepare a contingency plan in order to recover
the system from the possible attacks and security issues. However, contingency planning is only
a short term plan for system recovery. It is more important to develop a risk management plan in
order to ensure that the chances of the risks are minimized to as low as possible. Moreover,
business continuity planning is required in order to maintain business continuity in spite of
occurrence of the risks.
In this report, the current situation at MYOB has been analyzed with the help of some
risk analysis tools and techniques. Moreover, the main risks have been identified and a
contingency plan has been prepared. Finally, a proposal has been prepared for the business
continuity planning of the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY AND RISK MANAGEMENT
2.0 Investigation
In order to investigate the existing situation at MYOB and identify the risks associated
with it, a number of tools and techniques have been used. These tools and techniques are
described as follows.
Documentation Review – Documentation review is a basic risk assessment technique that
is used to analyze the existing situation in an organization. Analysis and review of the existing
situation helps to identify the gaps that may result in the security risks and issues. For this
project, a documentation review was conducted where the documents of MYOB were reviewed
for analyzing the current situation of the company.
Delphi Technique – In Delphi technique, a team of experts are contracted anonymously
and some information is sent to them for analysis and review. The whole process is kept
anonymous in order to avoid biasing. After the information is sent, the experts analyze it and
reach suitable conclusions (Sadgrove et al., 2016). These conclusions are listed, documentation
and sent back. This Delphi technique is an effective analysis tool as a team of experts conduct
the entire analysis process.
Interview – Personal or questionnaire interview is one of the most effective tools for risk
analysis in an organization. In addition to understanding the existing situation at the
organization, several diverse ideas can be generated in the interview that helps to analyze various
aspects of the organization instead of focusing on just one. In this particular project, a
questionnaire based interview has been conducted on the current employees of MYOB. The main
aim of this interview was to identify the gaps that may cause risks in the company’s existing
business system. Instead of conducting overall overview, the employees’ opinions were collected
2.0 Investigation
In order to investigate the existing situation at MYOB and identify the risks associated
with it, a number of tools and techniques have been used. These tools and techniques are
described as follows.
Documentation Review – Documentation review is a basic risk assessment technique that
is used to analyze the existing situation in an organization. Analysis and review of the existing
situation helps to identify the gaps that may result in the security risks and issues. For this
project, a documentation review was conducted where the documents of MYOB were reviewed
for analyzing the current situation of the company.
Delphi Technique – In Delphi technique, a team of experts are contracted anonymously
and some information is sent to them for analysis and review. The whole process is kept
anonymous in order to avoid biasing. After the information is sent, the experts analyze it and
reach suitable conclusions (Sadgrove et al., 2016). These conclusions are listed, documentation
and sent back. This Delphi technique is an effective analysis tool as a team of experts conduct
the entire analysis process.
Interview – Personal or questionnaire interview is one of the most effective tools for risk
analysis in an organization. In addition to understanding the existing situation at the
organization, several diverse ideas can be generated in the interview that helps to analyze various
aspects of the organization instead of focusing on just one. In this particular project, a
questionnaire based interview has been conducted on the current employees of MYOB. The main
aim of this interview was to identify the gaps that may cause risks in the company’s existing
business system. Instead of conducting overall overview, the employees’ opinions were collected
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SECURITY AND RISK MANAGEMENT
(Suter II, 2016). The advantage of this approach was that different employees opined about
various gaps that the existing situation of MYOB currently has.
SWOT Analysis – SWOT analysis is also an effective tool that can be used to identify
four main aspects of an organization – Strength, Weakness, Opportunity and Threat. However,
SWOT analysis is only based on overall rough analysis and cannot be considered as 100%
accurate. Still, SWOT analysis has been used to identify the overall situation at the organization
including its strengths and opportunities.
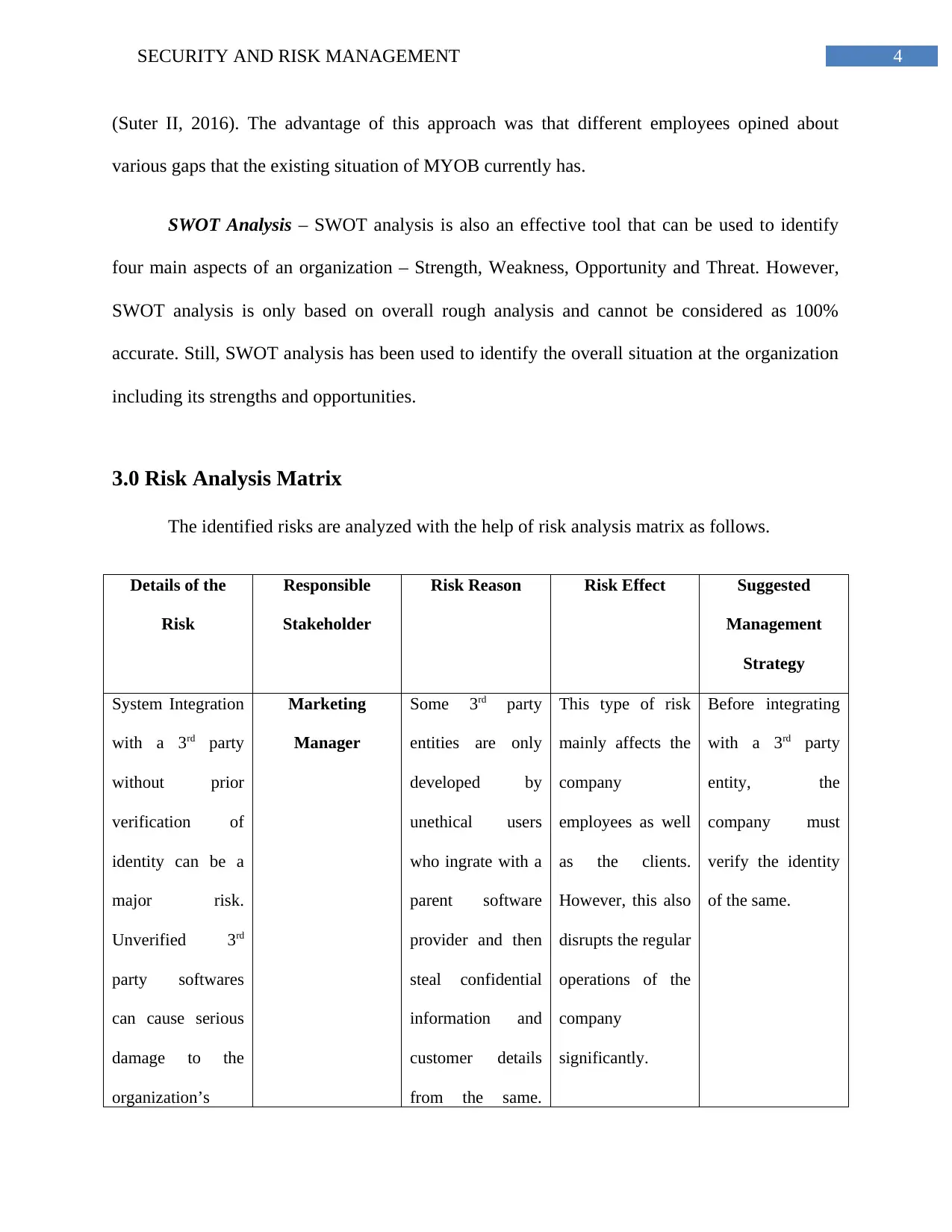
3.0 Risk Analysis Matrix
The identified risks are analyzed with the help of risk analysis matrix as follows.
Details of the
Risk
Responsible
Stakeholder
Risk Reason Risk Effect Suggested
Management
Strategy
System Integration
with a 3rd party
without prior
verification of
identity can be a
major risk.
Unverified 3rd
party softwares
can cause serious
damage to the
organization’s
Marketing
Manager
Some 3rd party
entities are only
developed by
unethical users
who ingrate with a
parent software
provider and then
steal confidential
information and
customer details
from the same.
This type of risk
mainly affects the
company
employees as well
as the clients.
However, this also
disrupts the regular
operations of the
company
significantly.
Before integrating
with a 3rd party
entity, the
company must
verify the identity
of the same.
(Suter II, 2016). The advantage of this approach was that different employees opined about
various gaps that the existing situation of MYOB currently has.
SWOT Analysis – SWOT analysis is also an effective tool that can be used to identify
four main aspects of an organization – Strength, Weakness, Opportunity and Threat. However,
SWOT analysis is only based on overall rough analysis and cannot be considered as 100%
accurate. Still, SWOT analysis has been used to identify the overall situation at the organization
including its strengths and opportunities.
3.0 Risk Analysis Matrix
The identified risks are analyzed with the help of risk analysis matrix as follows.
Details of the
Risk
Responsible
Stakeholder
Risk Reason Risk Effect Suggested
Management
Strategy
System Integration
with a 3rd party
without prior
verification of
identity can be a
major risk.
Unverified 3rd
party softwares
can cause serious
damage to the
organization’s
Marketing
Manager
Some 3rd party
entities are only
developed by
unethical users
who ingrate with a
parent software
provider and then
steal confidential
information and
customer details
from the same.
This type of risk
mainly affects the
company
employees as well
as the clients.
However, this also
disrupts the regular
operations of the
company
significantly.
Before integrating
with a 3rd party
entity, the
company must
verify the identity
of the same.
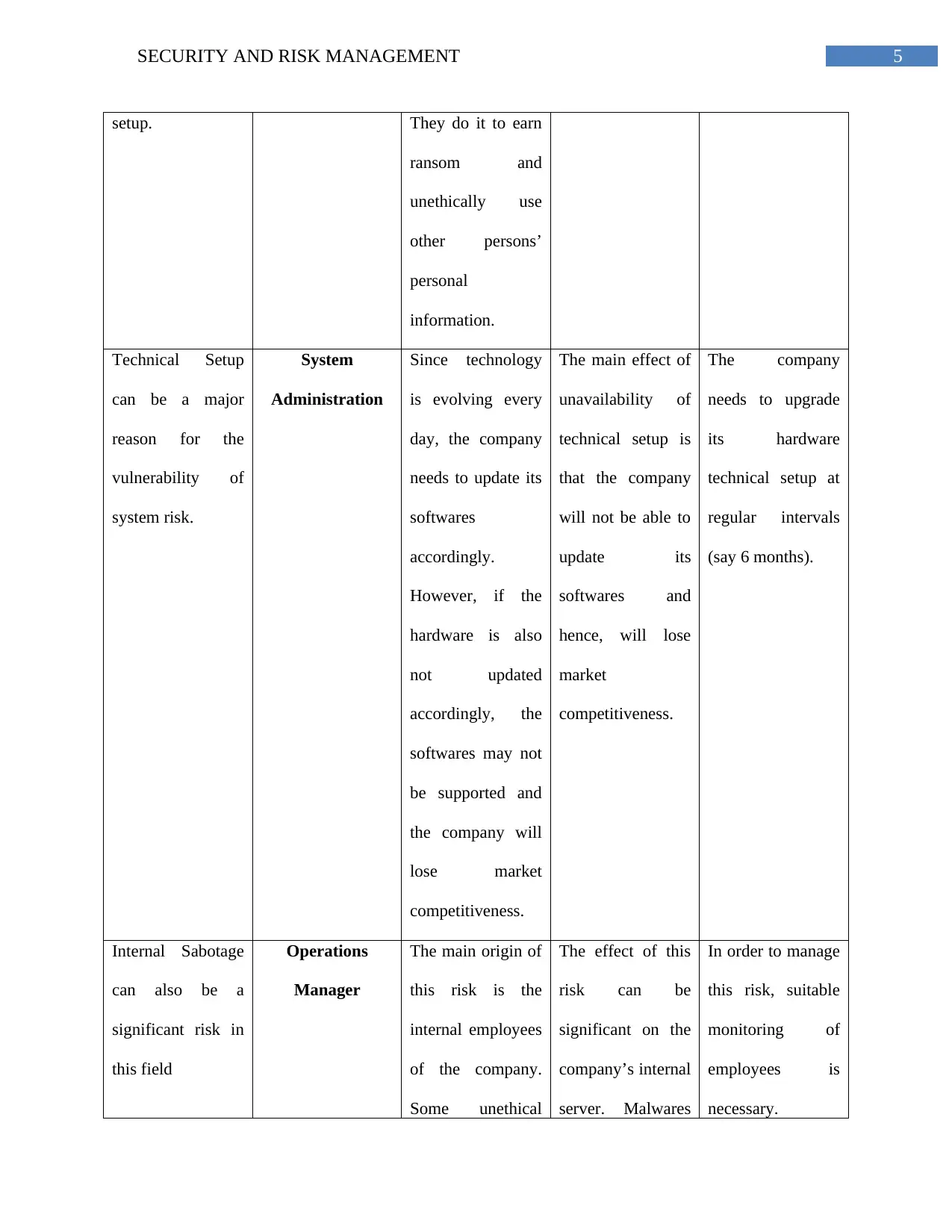
5SECURITY AND RISK MANAGEMENT
setup. They do it to earn
ransom and
unethically use
other persons’
personal
information.
Technical Setup
can be a major
reason for the
vulnerability of
system risk.
System
Administration
Since technology
is evolving every
day, the company
needs to update its
softwares
accordingly.
However, if the
hardware is also
not updated
accordingly, the
softwares may not
be supported and
the company will
lose market
competitiveness.
The main effect of
unavailability of
technical setup is
that the company
will not be able to
update its
softwares and
hence, will lose
market
competitiveness.
The company
needs to upgrade
its hardware
technical setup at
regular intervals
(say 6 months).
Internal Sabotage
can also be a
significant risk in
this field
Operations
Manager
The main origin of
this risk is the
internal employees
of the company.
Some unethical
The effect of this
risk can be
significant on the
company’s internal
server. Malwares
In order to manage
this risk, suitable
monitoring of
employees is
necessary.
setup. They do it to earn
ransom and
unethically use
other persons’
personal
information.
Technical Setup
can be a major
reason for the
vulnerability of
system risk.
System
Administration
Since technology
is evolving every
day, the company
needs to update its
softwares
accordingly.
However, if the
hardware is also
not updated
accordingly, the
softwares may not
be supported and
the company will
lose market
competitiveness.
The main effect of
unavailability of
technical setup is
that the company
will not be able to
update its
softwares and
hence, will lose
market
competitiveness.
The company
needs to upgrade
its hardware
technical setup at
regular intervals
(say 6 months).
Internal Sabotage
can also be a
significant risk in
this field
Operations
Manager
The main origin of
this risk is the
internal employees
of the company.
Some unethical
The effect of this
risk can be
significant on the
company’s internal
server. Malwares
In order to manage
this risk, suitable
monitoring of
employees is
necessary.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
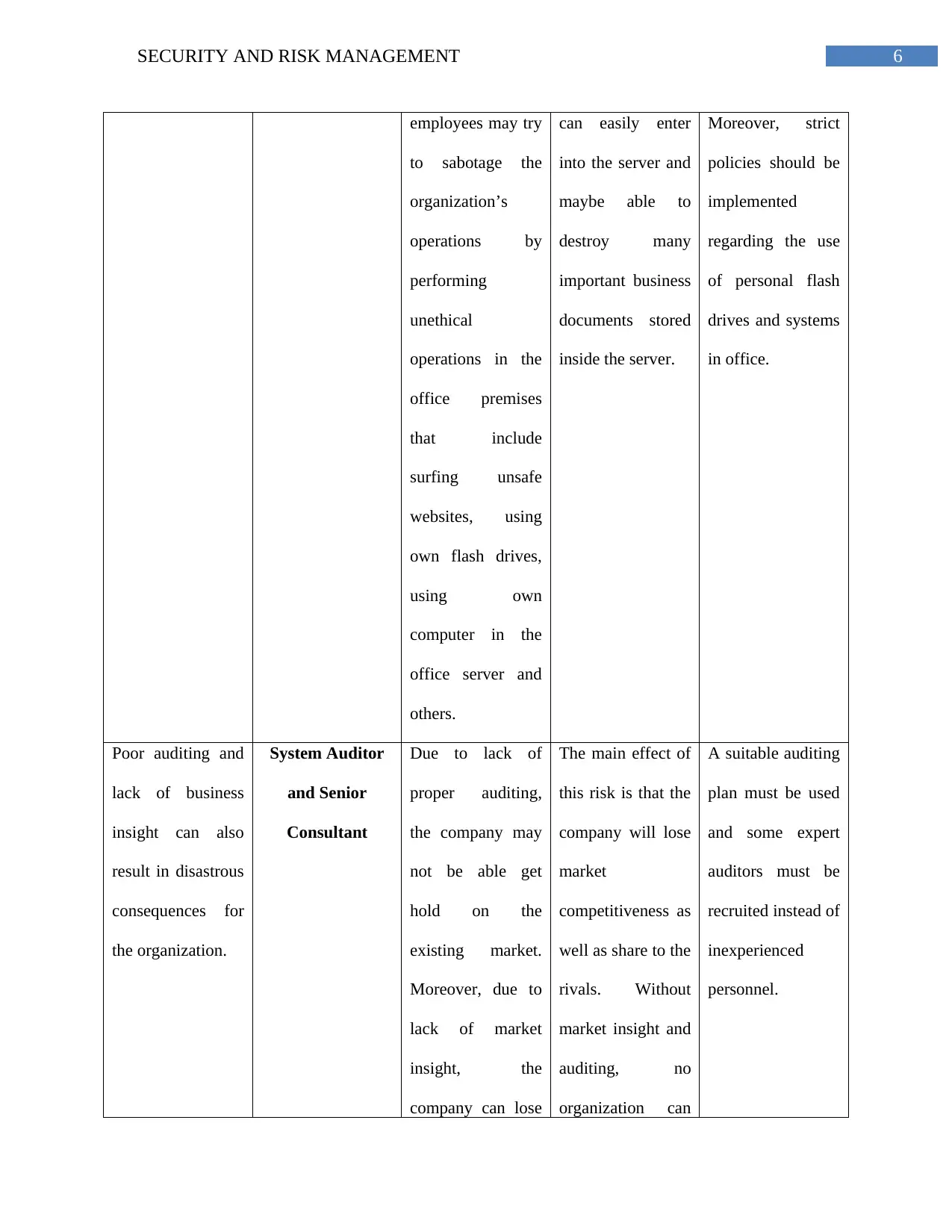
6SECURITY AND RISK MANAGEMENT
employees may try
to sabotage the
organization’s
operations by
performing
unethical
operations in the
office premises
that include
surfing unsafe
websites, using
own flash drives,
using own
computer in the
office server and
others.
can easily enter
into the server and
maybe able to
destroy many
important business
documents stored
inside the server.
Moreover, strict
policies should be
implemented
regarding the use
of personal flash
drives and systems
in office.
Poor auditing and
lack of business
insight can also
result in disastrous
consequences for
the organization.
System Auditor
and Senior
Consultant
Due to lack of
proper auditing,
the company may
not be able get
hold on the
existing market.
Moreover, due to
lack of market
insight, the
company can lose
The main effect of
this risk is that the
company will lose
market
competitiveness as
well as share to the
rivals. Without
market insight and
auditing, no
organization can
A suitable auditing
plan must be used
and some expert
auditors must be
recruited instead of
inexperienced
personnel.
employees may try
to sabotage the
organization’s
operations by
performing
unethical
operations in the
office premises
that include
surfing unsafe
websites, using
own flash drives,
using own
computer in the
office server and
others.
can easily enter
into the server and
maybe able to
destroy many
important business
documents stored
inside the server.
Moreover, strict
policies should be
implemented
regarding the use
of personal flash
drives and systems
in office.
Poor auditing and
lack of business
insight can also
result in disastrous
consequences for
the organization.
System Auditor
and Senior
Consultant
Due to lack of
proper auditing,
the company may
not be able get
hold on the
existing market.
Moreover, due to
lack of market
insight, the
company can lose
The main effect of
this risk is that the
company will lose
market
competitiveness as
well as share to the
rivals. Without
market insight and
auditing, no
organization can
A suitable auditing
plan must be used
and some expert
auditors must be
recruited instead of
inexperienced
personnel.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
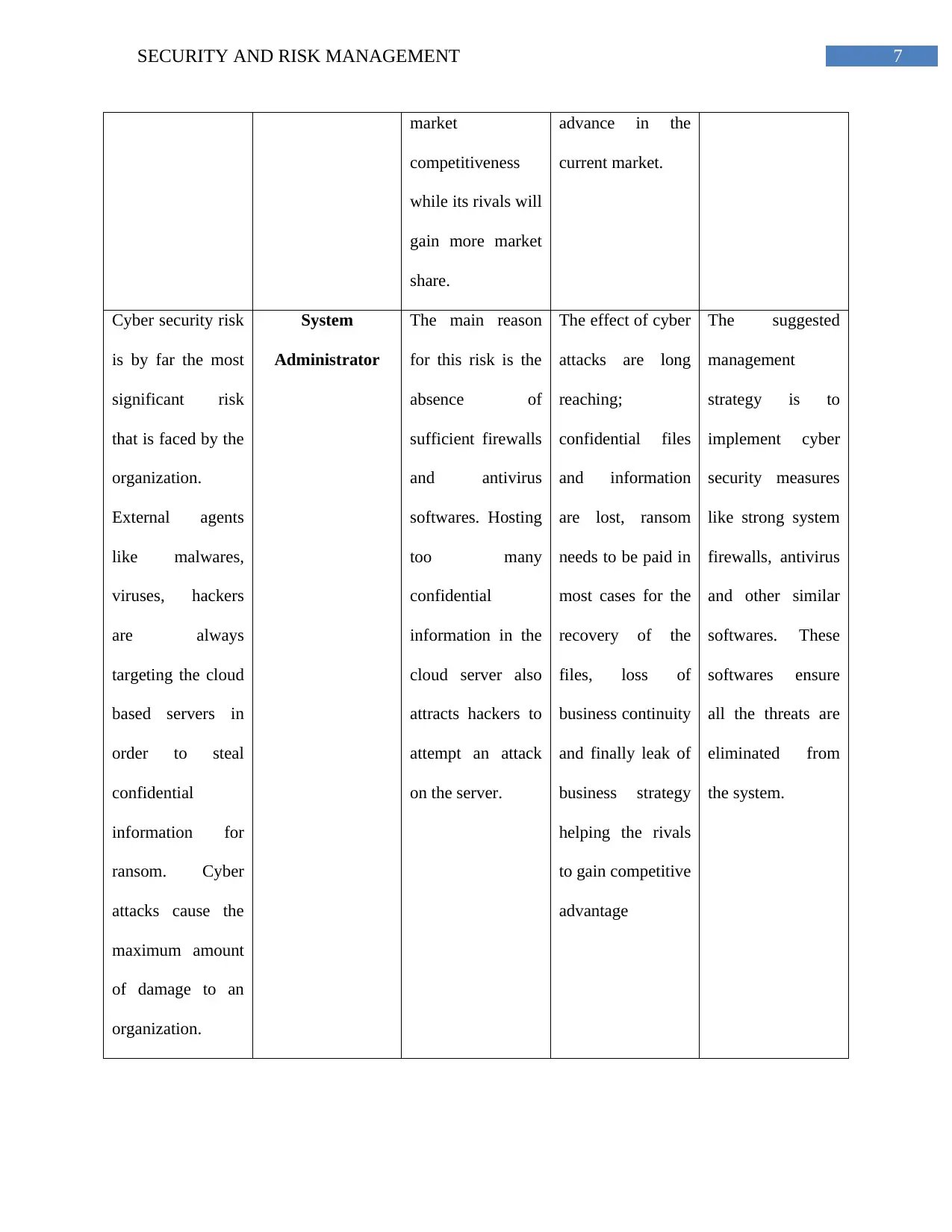
7SECURITY AND RISK MANAGEMENT
market
competitiveness
while its rivals will
gain more market
share.
advance in the
current market.
Cyber security risk
is by far the most
significant risk
that is faced by the
organization.
External agents
like malwares,
viruses, hackers
are always
targeting the cloud
based servers in
order to steal
confidential
information for
ransom. Cyber
attacks cause the
maximum amount
of damage to an
organization.
System
Administrator
The main reason
for this risk is the
absence of
sufficient firewalls
and antivirus
softwares. Hosting
too many
confidential
information in the
cloud server also
attracts hackers to
attempt an attack
on the server.
The effect of cyber
attacks are long
reaching;
confidential files
and information
are lost, ransom
needs to be paid in
most cases for the
recovery of the
files, loss of
business continuity
and finally leak of
business strategy
helping the rivals
to gain competitive
advantage
The suggested
management
strategy is to
implement cyber
security measures
like strong system
firewalls, antivirus
and other similar
softwares. These
softwares ensure
all the threats are
eliminated from
the system.
market
competitiveness
while its rivals will
gain more market
share.
advance in the
current market.
Cyber security risk
is by far the most
significant risk
that is faced by the
organization.
External agents
like malwares,
viruses, hackers
are always
targeting the cloud
based servers in
order to steal
confidential
information for
ransom. Cyber
attacks cause the
maximum amount
of damage to an
organization.
System
Administrator
The main reason
for this risk is the
absence of
sufficient firewalls
and antivirus
softwares. Hosting
too many
confidential
information in the
cloud server also
attracts hackers to
attempt an attack
on the server.
The effect of cyber
attacks are long
reaching;
confidential files
and information
are lost, ransom
needs to be paid in
most cases for the
recovery of the
files, loss of
business continuity
and finally leak of
business strategy
helping the rivals
to gain competitive
advantage
The suggested
management
strategy is to
implement cyber
security measures
like strong system
firewalls, antivirus
and other similar
softwares. These
softwares ensure
all the threats are
eliminated from
the system.

8SECURITY AND RISK MANAGEMENT
4.0 Disaster Recovery (DR) Plan
In order to prepare the disaster recovery plan, the identified risks are to be analyzed in
detail. The identified risks are as follows.
Integration with 3rd Party Entity – As discussed in the risk analysis matrix, integration
with 3rd party entity without verifying its identity or origin can be a reason for serious
vulnerability or risk of the organization. During the course of the business operations, the
company may need to integrate with some 3rd party softwares and systems in order to enhance
the business system (Mason, 2014). The duty of these 3rd party softwares is to enhance the
existing software operations including quality, performance and additional features. However,
there are some fraud 3rd party softwares that appear to provide services and after integration, they
just use the business link to break into the central server for stealing data and information. Since
MYOB uses cloud server for hosting all the data, it is even more easier to break into it and steal
information.
Lack of Technical Setup – During the analysis, it has been found that there is a lack of
sufficient technical setup at MYOB. Initially, the technical setup was developed of the highest
configuration for the system that was available then (Thakor, 2016). However, MYOB needed to
upgrade the system frequently in order to accommodate new software versions. On the other
hand, there have been no recent records of technical upgrade at MYOB whereas many new
versions of accounting softwares have been released since. As a result, the existing technical
setup does not support the latest software versions that in turn leads to the loss of market
competitiveness of the company.
4.0 Disaster Recovery (DR) Plan
In order to prepare the disaster recovery plan, the identified risks are to be analyzed in
detail. The identified risks are as follows.
Integration with 3rd Party Entity – As discussed in the risk analysis matrix, integration
with 3rd party entity without verifying its identity or origin can be a reason for serious
vulnerability or risk of the organization. During the course of the business operations, the
company may need to integrate with some 3rd party softwares and systems in order to enhance
the business system (Mason, 2014). The duty of these 3rd party softwares is to enhance the
existing software operations including quality, performance and additional features. However,
there are some fraud 3rd party softwares that appear to provide services and after integration, they
just use the business link to break into the central server for stealing data and information. Since
MYOB uses cloud server for hosting all the data, it is even more easier to break into it and steal
information.
Lack of Technical Setup – During the analysis, it has been found that there is a lack of
sufficient technical setup at MYOB. Initially, the technical setup was developed of the highest
configuration for the system that was available then (Thakor, 2016). However, MYOB needed to
upgrade the system frequently in order to accommodate new software versions. On the other
hand, there have been no recent records of technical upgrade at MYOB whereas many new
versions of accounting softwares have been released since. As a result, the existing technical
setup does not support the latest software versions that in turn leads to the loss of market
competitiveness of the company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SECURITY AND RISK MANAGEMENT
Internal Sabotage – There have been a number of records of internal sabotage inside
MYOB. There are records of some employees who unethically used external flash drives inside
the computer system. Due to this, many malwares entered the server and resulted in server
disruptions (Eriksson et al., 2014). Moreover, the company once allowed BYOD (Bring Your
Own Device) for the employees. However, after finding that many malwares were entering from
the external devices, the company stopped this policy and provided systems for employees to
work.
Poor Auditing – Poor auditing was once a serious issue in the organizational operations at
MYOB. Due to recruitment of inexperienced and incompetent auditors, the company underwent
a phase of business downfall. Moreover, there was a lack of market insight of the company’s
Senior Consultant that resulted in loss of market competitiveness of the company.
Cyber Security – Cyber security is a common risk for all business organizations that use
cloud computing servers for data storage and management. MYOB is a company that uses cloud
server to store all business and client data to save physical storage spaces as well as avoid
manual data handling (Li, 2014). Hence, there is a significant threat related to the security of the
data stored in the cloud server.
Disaster Recovery (DR) Plan – From the list of all the risks and threats, it is evident that
without any disaster recovery plan, the company will not be able to recover easily if any of the
significant risks actually occur. Firstly, the company needs to minimize the chances of
occurrence of such a risk at all cost. In order to do that, the company needs to prepare plans in
advance and take suitable measures accordingly. Secondly, the company needs to implement
strict policies regarding the use of devices inside office premises violation of which will lead to
Internal Sabotage – There have been a number of records of internal sabotage inside
MYOB. There are records of some employees who unethically used external flash drives inside
the computer system. Due to this, many malwares entered the server and resulted in server
disruptions (Eriksson et al., 2014). Moreover, the company once allowed BYOD (Bring Your
Own Device) for the employees. However, after finding that many malwares were entering from
the external devices, the company stopped this policy and provided systems for employees to
work.
Poor Auditing – Poor auditing was once a serious issue in the organizational operations at
MYOB. Due to recruitment of inexperienced and incompetent auditors, the company underwent
a phase of business downfall. Moreover, there was a lack of market insight of the company’s
Senior Consultant that resulted in loss of market competitiveness of the company.
Cyber Security – Cyber security is a common risk for all business organizations that use
cloud computing servers for data storage and management. MYOB is a company that uses cloud
server to store all business and client data to save physical storage spaces as well as avoid
manual data handling (Li, 2014). Hence, there is a significant threat related to the security of the
data stored in the cloud server.
Disaster Recovery (DR) Plan – From the list of all the risks and threats, it is evident that
without any disaster recovery plan, the company will not be able to recover easily if any of the
significant risks actually occur. Firstly, the company needs to minimize the chances of
occurrence of such a risk at all cost. In order to do that, the company needs to prepare plans in
advance and take suitable measures accordingly. Secondly, the company needs to implement
strict policies regarding the use of devices inside office premises violation of which will lead to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SECURITY AND RISK MANAGEMENT
serious consequences (Brindley, 2017). Thirdly, the company will need to implement strong
firewalls and antivirus softwares in the existing server. Finally, the company must upgrade the
existing technical setup in order to support more advanced versions of various softwares.
5.0 Proposal for Contingency Plan and Business Continuity Plan (BCP)
In order to prepare a contingency plan for maintaining business continuity, the company
needs to ensure some sequential steps are followed. This is explained as follows.
Contingency planning for business continuity mainly contains four main steps – Identify,
Analyze, Create and Measure.
Identify – This step mainly involves identification and assessment of any risk that may
occur / have occurred during the course of business operations. Identification of the risk is
required in order to find and apply suitable solution.
Business
Continuity
Planning
Step 1:
Identify
Step 2:
Analyze
Step 3:
Create
Step 4:
Measure
serious consequences (Brindley, 2017). Thirdly, the company will need to implement strong
firewalls and antivirus softwares in the existing server. Finally, the company must upgrade the
existing technical setup in order to support more advanced versions of various softwares.
5.0 Proposal for Contingency Plan and Business Continuity Plan (BCP)
In order to prepare a contingency plan for maintaining business continuity, the company
needs to ensure some sequential steps are followed. This is explained as follows.
Contingency planning for business continuity mainly contains four main steps – Identify,
Analyze, Create and Measure.
Identify – This step mainly involves identification and assessment of any risk that may
occur / have occurred during the course of business operations. Identification of the risk is
required in order to find and apply suitable solution.
Business
Continuity
Planning
Step 1:
Identify
Step 2:
Analyze
Step 3:
Create
Step 4:
Measure

11SECURITY AND RISK MANAGEMENT
Analyze – This step includes the impact of the risk on the daily business operations. If it
has minor impact, it can be addressed in due course. However, if it has massive impact on the
business, it must be addressed immediately at all costs (Schwing & Albers, 2013). For this,
analysis of the risk is necessary to understand its extent of power for affecting the business.
Create – In this step, a risk management plan is created in order to address the identified
risk. The plan should be created such that the risk is mitigated and long term strategy is
developed so that the risk does not occur anytime in the future.
Measure – This is the final step where the entire system is measured after the application
of the risk management plan. The system is tested in order to ensure the chance of occurrence of
the risk is minimized and a maintenance plan is developed. The aim of this plan is to ensure
maintenance of the system is done properly in order to avoid occurrence of any risks in future.
6.0 Analysis and Report on Controls
In order to control the risk aspect, MYOB needs to use the risk management tools
effectively. Moreover, simple application of the tools is not sufficient; it is important to apply
risk management tools in all seven OSI model layers (Boritz, Carnaghan & Alencar, 2014). This
is to ensure the stored data is protected in every phase – storage, presentation, transport, etc.
Special encryption techniques can be used to encrypt the data while it is being stored in the cloud
interface or transmitted to another system. If all the seven OSI model layers are protected and
encrypted, it is highly unlikely to be affected by any security risks.
7.0 Logical Map of Organizational Structure
The logical map of organizational structure is shown in the following diagram.
Analyze – This step includes the impact of the risk on the daily business operations. If it
has minor impact, it can be addressed in due course. However, if it has massive impact on the
business, it must be addressed immediately at all costs (Schwing & Albers, 2013). For this,
analysis of the risk is necessary to understand its extent of power for affecting the business.
Create – In this step, a risk management plan is created in order to address the identified
risk. The plan should be created such that the risk is mitigated and long term strategy is
developed so that the risk does not occur anytime in the future.
Measure – This is the final step where the entire system is measured after the application
of the risk management plan. The system is tested in order to ensure the chance of occurrence of
the risk is minimized and a maintenance plan is developed. The aim of this plan is to ensure
maintenance of the system is done properly in order to avoid occurrence of any risks in future.
6.0 Analysis and Report on Controls
In order to control the risk aspect, MYOB needs to use the risk management tools
effectively. Moreover, simple application of the tools is not sufficient; it is important to apply
risk management tools in all seven OSI model layers (Boritz, Carnaghan & Alencar, 2014). This
is to ensure the stored data is protected in every phase – storage, presentation, transport, etc.
Special encryption techniques can be used to encrypt the data while it is being stored in the cloud
interface or transmitted to another system. If all the seven OSI model layers are protected and
encrypted, it is highly unlikely to be affected by any security risks.
7.0 Logical Map of Organizational Structure
The logical map of organizational structure is shown in the following diagram.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




