Environmental Security Objectives for Mysql Database Management System
VerifiedAdded on 2019/09/20
|11
|2532
|595
Report
AI Summary
The Mysql database management system has several environmental security objectives, including access control, auditing and authentication, and encryption to maintain secure data. The functional requirements for the Mysql database include classes such as privacy, families like pseudonymity, components like alias pseudonymity, and elements like signature events. Assurance requirements include classes like development, security target evaluation, and tests, families like security problem definition, extended component definition, and conformance claims, components like developer providing security objectives, and elements like measurable and objective performance metrics. The target of evaluation summary describes the implementation of the target of evaluation with security functions and assurance security specifications. Finally, the assurance evaluation evaluates the developer process to achieve security for Mysql database management system in areas such as identification and authentication, database resource quotes, access control, privileges and roles, and auditing.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Security Target Document for MySQL
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Title: Security target document for Mysql
Student Name:
Student Id:
Subject:
Student Name:
Student Id:
Subject:

Table of Contents:
1. Introduction
2. Target of Evaluation
2.1 Overview
2.2 Description
2.3 Mysql Database security Management
2.4 Mysql database Auditing
3. Security Problems
3.1 Threats about TOE
3.2 Assumptions about TOE
3.3 Organization Security Polices
4. Security Objectives
4.1 Target of Evaluation security objectives
4.2 Environmental Security objectives for mysql
5. Security Requirements
5.1 Functional Requirements
5.2 Assurance Requirements
6. Target of Evaluation Summary
6.1 Security Functionality
6.2 Assurance evaluation
7. References
1. Introduction
2. Target of Evaluation
2.1 Overview
2.2 Description
2.3 Mysql Database security Management
2.4 Mysql database Auditing
3. Security Problems
3.1 Threats about TOE
3.2 Assumptions about TOE
3.3 Organization Security Polices
4. Security Objectives
4.1 Target of Evaluation security objectives
4.2 Environmental Security objectives for mysql
5. Security Requirements
5.1 Functional Requirements
5.2 Assurance Requirements
6. Target of Evaluation Summary
6.1 Security Functionality
6.2 Assurance evaluation
7. References

1. Introduction:
This report is based on the Mysql database management system in context of CybSec
organization. There are provided security target document for Mysql database management
system which will be used for a company CybSec which is planning to request common criteria
certification for its web-based system. The entire security target document is based on the
Mysql database management system and there are also included further terms with respect to
the Mysql database such as Target of evaluation for document which includes the overview of
the system, description, and Mysql database security management. Moreover, the security
target document includes many related topics such as security objectives (Target of evolution
security objectives, Environmental security objectives), security requirements (Functional
Security requirements and assurance security requirements) and Target of evaluation summary
with appropriate references. Thus all these things are described as follows in the report with a
proper security target document for Mysql database management system.
2. Target of Evaluation:
The target of evaluation process includes the details of any particular product testing
with respect to its security properties. There are described multiple things in this
phase of the document such as overview, description, Mysql database security
Management, and MySql database Auditing. These terms are described with respect
to the target of security evolution for Mysql database management system. Thus this
target of evolution is described as follows in detail.
2.1 Overview:
MySQL is the most popular open source database. It enables the cost effective
delivery of reliable and high-performance web-based and embedded database
applications. Implementation of MySQL database for any organization is very easy
but it is very important to consider security issues while installation of MySQL
database and working on it. While considering database security implementation of
database vault became considerable. Vault comes with a variety of integrations to
different systems. Vaults are integrated with MySQL as secret backend. A secret
backend can provide secrets. It means that Vault can create and revoke users for
databases on demand.
2.2Description:
Organizations of all sizes commonly adopting MySQL database because it empower
them to build applications which are faster and handle highly diverse types of data.
To enhance security to access database and management database credentials and
roles Vaults are implements to enhance and ensure security audits. It is encrypted
file in the MySQL workbench data directory. The Vault provides a convenient secure
This report is based on the Mysql database management system in context of CybSec
organization. There are provided security target document for Mysql database management
system which will be used for a company CybSec which is planning to request common criteria
certification for its web-based system. The entire security target document is based on the
Mysql database management system and there are also included further terms with respect to
the Mysql database such as Target of evaluation for document which includes the overview of
the system, description, and Mysql database security management. Moreover, the security
target document includes many related topics such as security objectives (Target of evolution
security objectives, Environmental security objectives), security requirements (Functional
Security requirements and assurance security requirements) and Target of evaluation summary
with appropriate references. Thus all these things are described as follows in the report with a
proper security target document for Mysql database management system.
2. Target of Evaluation:
The target of evaluation process includes the details of any particular product testing
with respect to its security properties. There are described multiple things in this
phase of the document such as overview, description, Mysql database security
Management, and MySql database Auditing. These terms are described with respect
to the target of security evolution for Mysql database management system. Thus this
target of evolution is described as follows in detail.
2.1 Overview:
MySQL is the most popular open source database. It enables the cost effective
delivery of reliable and high-performance web-based and embedded database
applications. Implementation of MySQL database for any organization is very easy
but it is very important to consider security issues while installation of MySQL
database and working on it. While considering database security implementation of
database vault became considerable. Vault comes with a variety of integrations to
different systems. Vaults are integrated with MySQL as secret backend. A secret
backend can provide secrets. It means that Vault can create and revoke users for
databases on demand.
2.2Description:
Organizations of all sizes commonly adopting MySQL database because it empower
them to build applications which are faster and handle highly diverse types of data.
To enhance security to access database and management database credentials and
roles Vaults are implements to enhance and ensure security audits. It is encrypted
file in the MySQL workbench data directory. The Vault provides a convenient secure
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

storage for password used to access MySQL server. The Metadata of MySQL
database includes the roles introduced by the database vaults.
MySQL Database Vaults provides.
Access control functionality that allows to group database schema, roles and
objects, define common rules that controls and allow user to how users can
execute database SQL queries.
Define and use factors that can be evaluate as part of the rules.
Audit capabilities related to management activities of MySQL database
Vaults.
To create database credentials, role should be setup first. Roles control the permission
context for database credentials generation. A role defines the permissions and max lease
time for the credentials. The lease is in Vault-speak the duration the credentials are valid.
Vaults revoke credentials from database system once they are expired. In addition it extends
the auditing functionality with specific auditing and specific audit functions related to the
additional access control functionality. There are further additions to the management
functionality with new roles defined by database Vault and management functionality for
managing the additional access control and audit functions.
2.3 MySQL Database Security Management:
In account of security with in MySQL database installation and managing credentials
with respect to roles and vaults the wide range of topics comes in consideration and
how they affect the security of your MySQL server.
Access control and security within the database system. It includes the users
and databases granted with access to the databases, stored programs and
views.
Features offered by security related plugins. Plugins for authenticating clients
to connect to MySQL database. Password validation plugin for implementing
password strength policies. MySQL Enterprise Audit, Implemented using a
server plugin, uses the open MySQL Audit API to enable standard.
General factors that affect security. These include choosing good passwords
and generating unnecessary privileges to users.
Network security of MySQL and system. It states that the security of
database
2.4 MySQL Database Auditing
MySQL Enterprise Audit provides policy-based auditing solution that provides
satisfyregulatory compliances and strong security controls. As secured data is
collected,stored and used online, it becomes strong and essential component of any
securitystrategy. To defense against the misuse of information, Sarbanes-Oxley
database includes the roles introduced by the database vaults.
MySQL Database Vaults provides.
Access control functionality that allows to group database schema, roles and
objects, define common rules that controls and allow user to how users can
execute database SQL queries.
Define and use factors that can be evaluate as part of the rules.
Audit capabilities related to management activities of MySQL database
Vaults.
To create database credentials, role should be setup first. Roles control the permission
context for database credentials generation. A role defines the permissions and max lease
time for the credentials. The lease is in Vault-speak the duration the credentials are valid.
Vaults revoke credentials from database system once they are expired. In addition it extends
the auditing functionality with specific auditing and specific audit functions related to the
additional access control functionality. There are further additions to the management
functionality with new roles defined by database Vault and management functionality for
managing the additional access control and audit functions.
2.3 MySQL Database Security Management:
In account of security with in MySQL database installation and managing credentials
with respect to roles and vaults the wide range of topics comes in consideration and
how they affect the security of your MySQL server.
Access control and security within the database system. It includes the users
and databases granted with access to the databases, stored programs and
views.
Features offered by security related plugins. Plugins for authenticating clients
to connect to MySQL database. Password validation plugin for implementing
password strength policies. MySQL Enterprise Audit, Implemented using a
server plugin, uses the open MySQL Audit API to enable standard.
General factors that affect security. These include choosing good passwords
and generating unnecessary privileges to users.
Network security of MySQL and system. It states that the security of
database
2.4 MySQL Database Auditing
MySQL Enterprise Audit provides policy-based auditing solution that provides
satisfyregulatory compliances and strong security controls. As secured data is
collected,stored and used online, it becomes strong and essential component of any
securitystrategy. To defense against the misuse of information, Sarbanes-Oxley
popularcompliance regulations including HIPAA and the PCI Data Security Standard
requireorganization to attack access to information.MySQL Audit provided DBAs
tools to add to their new and existing application byenabling following these:
Audit files are encrypted using AES encryption and can also share and
Decrypt using encryption key.
Perform forensic analysis and data’s validity to confirm data integrity.
Select option between JSOM or XML
Files can be zipped and reduce the size up to 10 times which can save
thedisk space and performance.
3. Security problems
This phase in the security target documents for Mysql database management system
deals with the major problems came across the Mysql database. There are described
the major security problems in terms of threats, assumptions and organization
security policies. Thus all these are described as follows in details.
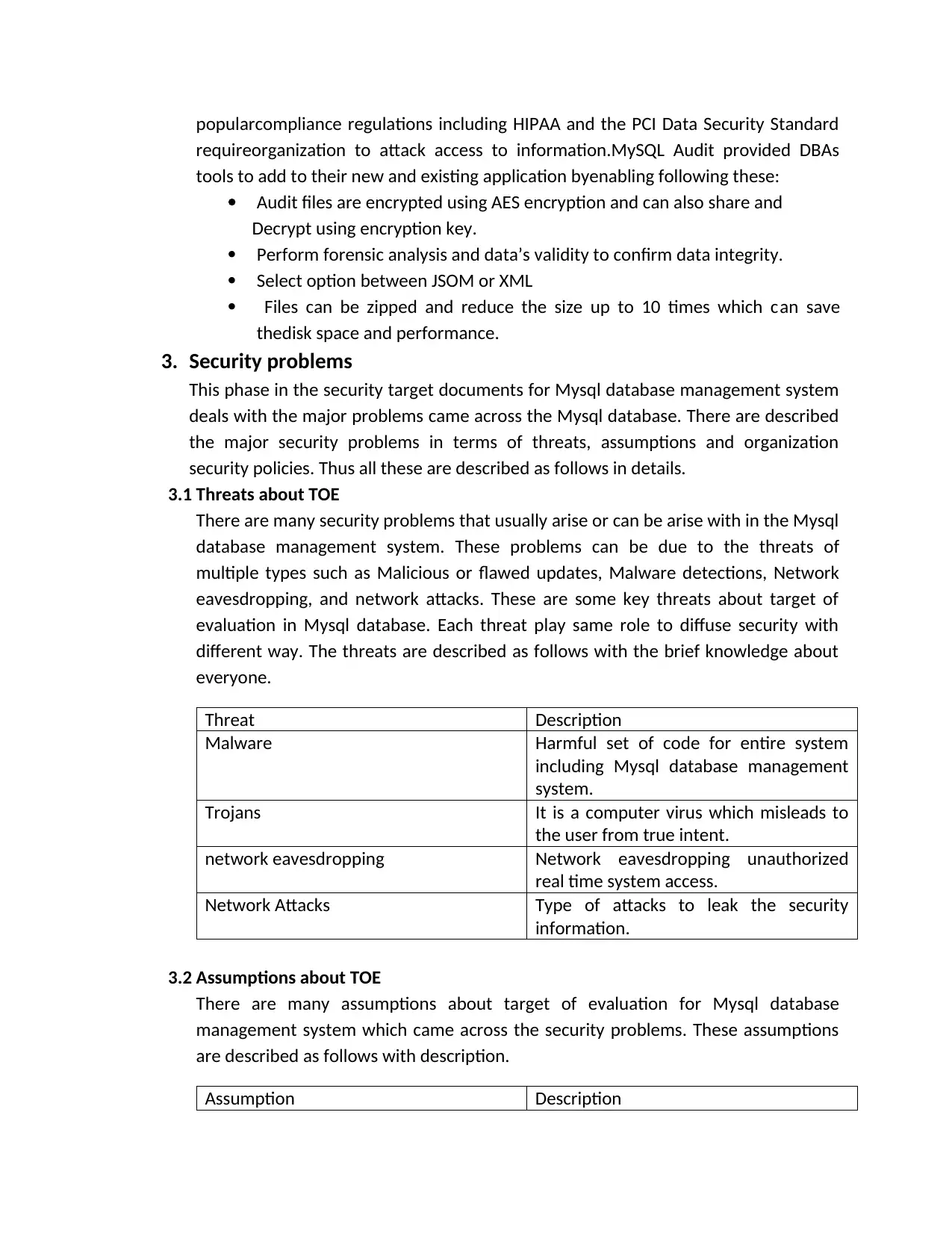
3.1 Threats about TOE
There are many security problems that usually arise or can be arise with in the Mysql
database management system. These problems can be due to the threats of
multiple types such as Malicious or flawed updates, Malware detections, Network
eavesdropping, and network attacks. These are some key threats about target of
evaluation in Mysql database. Each threat play same role to diffuse security with
different way. The threats are described as follows with the brief knowledge about
everyone.
Threat Description
Malware Harmful set of code for entire system
including Mysql database management
system.
Trojans It is a computer virus which misleads to
the user from true intent.
network eavesdropping Network eavesdropping unauthorized
real time system access.
Network Attacks Type of attacks to leak the security
information.
3.2 Assumptions about TOE
There are many assumptions about target of evaluation for Mysql database
management system which came across the security problems. These assumptions
are described as follows with description.
Assumption Description
requireorganization to attack access to information.MySQL Audit provided DBAs
tools to add to their new and existing application byenabling following these:
Audit files are encrypted using AES encryption and can also share and
Decrypt using encryption key.
Perform forensic analysis and data’s validity to confirm data integrity.
Select option between JSOM or XML
Files can be zipped and reduce the size up to 10 times which can save
thedisk space and performance.
3. Security problems
This phase in the security target documents for Mysql database management system
deals with the major problems came across the Mysql database. There are described
the major security problems in terms of threats, assumptions and organization
security policies. Thus all these are described as follows in details.
3.1 Threats about TOE
There are many security problems that usually arise or can be arise with in the Mysql
database management system. These problems can be due to the threats of
multiple types such as Malicious or flawed updates, Malware detections, Network
eavesdropping, and network attacks. These are some key threats about target of
evaluation in Mysql database. Each threat play same role to diffuse security with
different way. The threats are described as follows with the brief knowledge about
everyone.
Threat Description
Malware Harmful set of code for entire system
including Mysql database management
system.
Trojans It is a computer virus which misleads to
the user from true intent.
network eavesdropping Network eavesdropping unauthorized
real time system access.
Network Attacks Type of attacks to leak the security
information.
3.2 Assumptions about TOE
There are many assumptions about target of evaluation for Mysql database
management system which came across the security problems. These assumptions
are described as follows with description.
Assumption Description
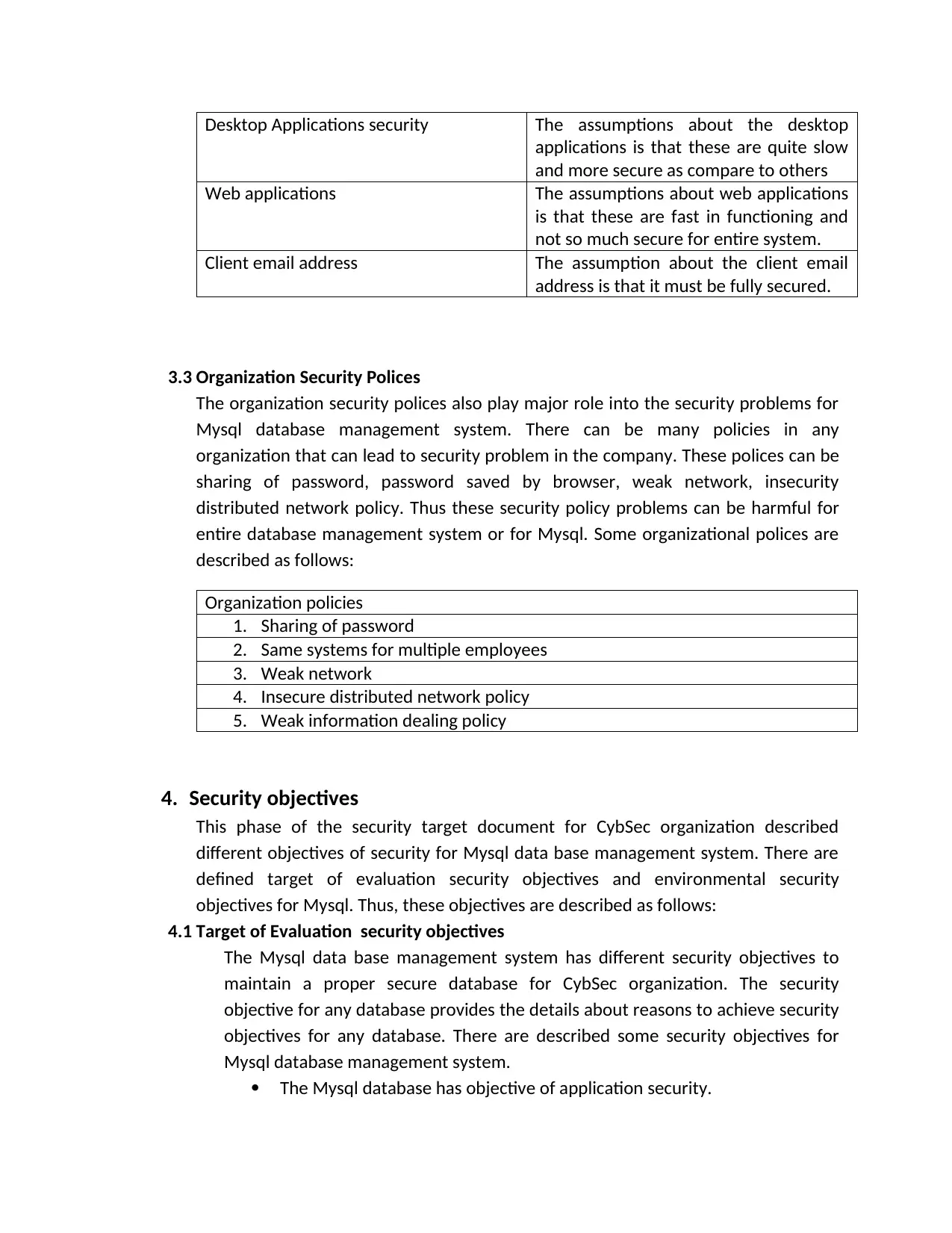
Desktop Applications security The assumptions about the desktop
applications is that these are quite slow
and more secure as compare to others
Web applications The assumptions about web applications
is that these are fast in functioning and
not so much secure for entire system.
Client email address The assumption about the client email
address is that it must be fully secured.
3.3 Organization Security Polices
The organization security polices also play major role into the security problems for
Mysql database management system. There can be many policies in any
organization that can lead to security problem in the company. These polices can be
sharing of password, password saved by browser, weak network, insecurity
distributed network policy. Thus these security policy problems can be harmful for
entire database management system or for Mysql. Some organizational polices are
described as follows:
Organization policies
1. Sharing of password
2. Same systems for multiple employees
3. Weak network
4. Insecure distributed network policy
5. Weak information dealing policy
4. Security objectives
This phase of the security target document for CybSec organization described
different objectives of security for Mysql data base management system. There are
defined target of evaluation security objectives and environmental security
objectives for Mysql. Thus, these objectives are described as follows:
4.1 Target of Evaluation security objectives
The Mysql data base management system has different security objectives to
maintain a proper secure database for CybSec organization. The security
objective for any database provides the details about reasons to achieve security
objectives for any database. There are described some security objectives for
Mysql database management system.
The Mysql database has objective of application security.
applications is that these are quite slow
and more secure as compare to others
Web applications The assumptions about web applications
is that these are fast in functioning and
not so much secure for entire system.
Client email address The assumption about the client email
address is that it must be fully secured.
3.3 Organization Security Polices
The organization security polices also play major role into the security problems for
Mysql database management system. There can be many policies in any
organization that can lead to security problem in the company. These polices can be
sharing of password, password saved by browser, weak network, insecurity
distributed network policy. Thus these security policy problems can be harmful for
entire database management system or for Mysql. Some organizational polices are
described as follows:
Organization policies
1. Sharing of password
2. Same systems for multiple employees
3. Weak network
4. Insecure distributed network policy
5. Weak information dealing policy
4. Security objectives
This phase of the security target document for CybSec organization described
different objectives of security for Mysql data base management system. There are
defined target of evaluation security objectives and environmental security
objectives for Mysql. Thus, these objectives are described as follows:
4.1 Target of Evaluation security objectives
The Mysql data base management system has different security objectives to
maintain a proper secure database for CybSec organization. The security
objective for any database provides the details about reasons to achieve security
objectives for any database. There are described some security objectives for
Mysql database management system.
The Mysql database has objective of application security.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The main objective of security can be backup of important previous data
from database.
The integrity controls also a security objective of Mysql database
management system.
To provide atomicity for database can be a security objective for Mysql
database management system.
Thus these are the target of evolution security objective for Mysql
database.
4.2 Environmental Security objectives for Mysql
The Mysql database also has many environmental security objectives which are
related to the external environment of database management system. Some of
the environmental security objectives for Mysql database management system
are described as follows:
The access control of database management system is one of the major
objectives of Environmental security objective of Mysql.
Auditing and authentication are also other environmental security
objectives for Mysql database management system.
The encryption to maintain the secure data by changing its form is also
one of the good environmental security objectives of Mysql database
management system.
Thus these are some of the environmental security objectives for Mysql
database management system.
5. Security Requirements
This phase of the security target document contains details about the security
requirements for Mysql database. This also includes the functional and assurance
security requirements for Mysql database in context of CybSec Company. Thus the
main ideas regarding this security are described as follows:
5.1 Functional Requirements
The Mysql database has a lot of functional security requirements which are
described as follows to implement properly secure database management
system for CybSec organization. Thus the security functional requirements in
terms of classes, families, component and elements are described as follows:
Classes
The organizational groups whose members share the common intent but
may provide the different coverage of security objectives. The Security
requirement class is privacy.
Families
from database.
The integrity controls also a security objective of Mysql database
management system.
To provide atomicity for database can be a security objective for Mysql
database management system.
Thus these are the target of evolution security objective for Mysql
database.
4.2 Environmental Security objectives for Mysql
The Mysql database also has many environmental security objectives which are
related to the external environment of database management system. Some of
the environmental security objectives for Mysql database management system
are described as follows:
The access control of database management system is one of the major
objectives of Environmental security objective of Mysql.
Auditing and authentication are also other environmental security
objectives for Mysql database management system.
The encryption to maintain the secure data by changing its form is also
one of the good environmental security objectives of Mysql database
management system.
Thus these are some of the environmental security objectives for Mysql
database management system.
5. Security Requirements
This phase of the security target document contains details about the security
requirements for Mysql database. This also includes the functional and assurance
security requirements for Mysql database in context of CybSec Company. Thus the
main ideas regarding this security are described as follows:
5.1 Functional Requirements
The Mysql database has a lot of functional security requirements which are
described as follows to implement properly secure database management
system for CybSec organization. Thus the security functional requirements in
terms of classes, families, component and elements are described as follows:
Classes
The organizational groups whose members share the common intent but
may provide the different coverage of security objectives. The Security
requirement class is privacy.
Families

The organizational groups whose comes under family are shares the
common security objectives but with different emphasis. The family
comes under the privacy class is Pseudonymity.
Component
The component contains actual smallest sets of security functional
requirements of Pseudonymity family which are given as follows:
1. The pseudonymity need a set of users that are not able to determine
the user’s identity to bound user to a subject or operation but the
user will be still accountable for all of its actions.
2. The Alias pseudonymity, needs TSF to follow the particular
construction rules for the alias to the users identity.
Elements
This contains the members of components which cannot be selected
individually that are described as follows:
1. The elements can be signature event or event sequence that indicates
the potential violation of enforcement of security functional
requirements.
5.2 Assurance Requirements
The assurance security requirements in the complete security target of Mysql
database management system plays a major role in to achieve proper security by
tool. The Mysql database must have a proper server managing the security for
entire company. The assurance requirements in terms of classes, families,
component and elements are described as follows:
Classes
The assurance requirement classes are given as follows:
Development, security target evaluation and tests.
Families
The families for assurance security requirements are described as
follows:
1. The security problem definition for entire system.
2. The extended component definition for entire system.
3. Conformance claims for the system
Components
The components are the smallest set of assurance requirements such as
the developer shall provide the security objectives and employees gives
common security objectives but with different emphasis. The family
comes under the privacy class is Pseudonymity.
Component
The component contains actual smallest sets of security functional
requirements of Pseudonymity family which are given as follows:
1. The pseudonymity need a set of users that are not able to determine
the user’s identity to bound user to a subject or operation but the
user will be still accountable for all of its actions.
2. The Alias pseudonymity, needs TSF to follow the particular
construction rules for the alias to the users identity.
Elements
This contains the members of components which cannot be selected
individually that are described as follows:
1. The elements can be signature event or event sequence that indicates
the potential violation of enforcement of security functional
requirements.
5.2 Assurance Requirements
The assurance security requirements in the complete security target of Mysql
database management system plays a major role in to achieve proper security by
tool. The Mysql database must have a proper server managing the security for
entire company. The assurance requirements in terms of classes, families,
component and elements are described as follows:
Classes
The assurance requirement classes are given as follows:
Development, security target evaluation and tests.
Families
The families for assurance security requirements are described as
follows:
1. The security problem definition for entire system.
2. The extended component definition for entire system.
3. Conformance claims for the system
Components
The components are the smallest set of assurance requirements such as
the developer shall provide the security objectives and employees gives

the best performance in the development and testing of the entire
system.
Elements
The elements are used to identify the individual requirements for the
system as per the classes, families and component. The elements of
development family are described as follows:
1. The developer will be able to provide the security objective for entire
system.
2. In case of content requirements, the extended components for
system must be consist of measurable and objective elements.
6. Target of Evaluation Summary
This phase of the document is used to provide the general overall idea about the
target of evaluation summary. This used to describe the general understanding about
the development of target of evaluation. There are described the implementation of
target of evaluation with the help of security functions and assurance security
specifications which are also described as follows in a details view.
6.1 Security Functionality
The target of evaluation summary specification is described the details here that
how target of evaluation is connected with the Mysql database management
system. The Mysql database is meeting with the evolution of target with respect to
the society because it contains proper secure server with the better operating
system and other functional and assurance requirements.
6.2 Assurance evaluation
This phase of the document is used to provide a high-level description about the
developer process to achieve the security for Mysql database management system.
The target of security is evaluated for Mysql database management system in
different areas such as identification and authentication, database resource quotes,
access control, privileges and roles and about the auditing of the database
management system.
Thus this is the complete summary about the target of evaluation for database
management system in terms of security functionality and assurance evaluation .
7. References
Common criteria Reforms: “Better Security Products Through Increased Cooperation
with industry”.
Beznosov, Konstantin and Kruchten, Philippe, Towards Agile Security Assurance,
system.
Elements
The elements are used to identify the individual requirements for the
system as per the classes, families and component. The elements of
development family are described as follows:
1. The developer will be able to provide the security objective for entire
system.
2. In case of content requirements, the extended components for
system must be consist of measurable and objective elements.
6. Target of Evaluation Summary
This phase of the document is used to provide the general overall idea about the
target of evaluation summary. This used to describe the general understanding about
the development of target of evaluation. There are described the implementation of
target of evaluation with the help of security functions and assurance security
specifications which are also described as follows in a details view.
6.1 Security Functionality
The target of evaluation summary specification is described the details here that
how target of evaluation is connected with the Mysql database management
system. The Mysql database is meeting with the evolution of target with respect to
the society because it contains proper secure server with the better operating
system and other functional and assurance requirements.
6.2 Assurance evaluation
This phase of the document is used to provide a high-level description about the
developer process to achieve the security for Mysql database management system.
The target of security is evaluated for Mysql database management system in
different areas such as identification and authentication, database resource quotes,
access control, privileges and roles and about the auditing of the database
management system.
Thus this is the complete summary about the target of evaluation for database
management system in terms of security functionality and assurance evaluation .
7. References
Common criteria Reforms: “Better Security Products Through Increased Cooperation
with industry”.
Beznosov, Konstantin and Kruchten, Philippe, Towards Agile Security Assurance,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Wayrynen, J. Boden, M. and Bostrom, Security Engineering and eXtreme
programming.
Common criteria for information Technology Security evaluation, Part 1: Introduction
and general model, Sep 2012, CCMB-2012-09-002.
Common criteria for information Technology Security evaluation, Part 3: Scurity
assurance criteria for information technology evaluation CCMB-2012-09-003.
http://www.mysql.com/
Common criteria evaluation and validation scheme, validation report, Red hat
enterprise Linux, version 5.
Common criteria for information technology security evaluation version- 3.1
Urlocker, M. Zack 2005, Google runs MySQL.
Calbum, Thomas 2007, “Google Releases Improved MySql”
Callaghan, Mark, 2010, “Master-slave replication”
Sobel, Jason 2007, “database blog” Retrieved 2017
Steven J. Vaughan-Nichols 2013, “WebScale SQL: MySQL”
programming.
Common criteria for information Technology Security evaluation, Part 1: Introduction
and general model, Sep 2012, CCMB-2012-09-002.
Common criteria for information Technology Security evaluation, Part 3: Scurity
assurance criteria for information technology evaluation CCMB-2012-09-003.
http://www.mysql.com/
Common criteria evaluation and validation scheme, validation report, Red hat
enterprise Linux, version 5.
Common criteria for information technology security evaluation version- 3.1
Urlocker, M. Zack 2005, Google runs MySQL.
Calbum, Thomas 2007, “Google Releases Improved MySql”
Callaghan, Mark, 2010, “Master-slave replication”
Sobel, Jason 2007, “database blog” Retrieved 2017
Steven J. Vaughan-Nichols 2013, “WebScale SQL: MySQL”
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





