VPN Setup in Campus Environment
VerifiedAdded on 2019/10/08
|11
|2179
|191
Report
AI Summary
This research report investigates the setup of a Virtual Private Network (VPN) within a university campus utilizing the existing wireless network infrastructure. The report begins with an introduction defining VPNs and their benefits in providing secure access to campus resources for students, even remotely. The research questions focus on the practical aspects of VPN implementation, including required hardware and software, and the overall advantages for both students and the university. A literature review examines existing research on VPN technologies, security protocols (IPsec, L2TP, PPTP, SSL), and authentication methods. The methodology section outlines a deductive approach using qualitative data from secondary sources like journals and research papers. The report details the expected outcomes, including a comprehensive explanation of the VPN setup process, identification of necessary tools, and an assessment of the benefits. A timeline for the research is provided, followed by a critical evaluation of the process and potential limitations. Finally, a list of references cites relevant research papers and patents.

Setting up a Virtual Private Network in Campus Environment using University Wireless Network
Research Proposal
ABC
[Pick the date]
Research Proposal
ABC
[Pick the date]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction.................................................................................................................................................2
Literature review.........................................................................................................................................3
Research methodology................................................................................................................................6
Critical evaluation and reflection of the outcome and process...................................................................6
Timeline.......................................................................................................................................................7
References...................................................................................................................................................9
Introduction.................................................................................................................................................2
Literature review.........................................................................................................................................3
Research methodology................................................................................................................................6
Critical evaluation and reflection of the outcome and process...................................................................6
Timeline.......................................................................................................................................................7
References...................................................................................................................................................9

Introduction
Virtual private network is the one that offers a secure network connection which is layered on the
top of a public network like Internet (Eisendrath, 2002). The infrastructure of the internet is used
to move the secured data within the network of campuses. It can help the students of the campus
to access the online resources even when they are absent from the campus and the resources
provided by the university can also be accesses as per the comfort level of students and as per
their convenience. For this, the campus’s wireless network will be used so that the e-services of
the campus and other computing facilities can be accessed.
Research Questions
The research aims to answer the following questions:
1. How can a VPN be set up in the campus environment using the university’s wireless
network?
2. What are the hardware and software tools which are required to set up the VPN in
campus?
3. How can the students and University be benefited if a VPN is set up in the campus
environment?
Objectives of the research
The research will try to fulfill the following objectives:
1. To understand the process of setting up the VPN in the campus environment using the
university’s wireless network.
Virtual private network is the one that offers a secure network connection which is layered on the
top of a public network like Internet (Eisendrath, 2002). The infrastructure of the internet is used
to move the secured data within the network of campuses. It can help the students of the campus
to access the online resources even when they are absent from the campus and the resources
provided by the university can also be accesses as per the comfort level of students and as per
their convenience. For this, the campus’s wireless network will be used so that the e-services of
the campus and other computing facilities can be accessed.
Research Questions
The research aims to answer the following questions:
1. How can a VPN be set up in the campus environment using the university’s wireless
network?
2. What are the hardware and software tools which are required to set up the VPN in
campus?
3. How can the students and University be benefited if a VPN is set up in the campus
environment?
Objectives of the research
The research will try to fulfill the following objectives:
1. To understand the process of setting up the VPN in the campus environment using the
university’s wireless network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. To identify the hardware and software tools which are required to set up the VPN in
campus.
3. To determine the benefits of VPN to students and university.
Literature review
It has been suggested by (Papp, 2014) that the technology of VPN transmits the data between
devices in a secured manner. The successful implementation of VPN has been observed by
(Suzuki, 2001) in wireless networks while using the internet as a medium. After observing the
success of the use of VPN in Networks which are wired, and after understanding the implications
of insecurity pointed towards networks which are wireless, it has engaged administrators and
developers to utilize it in the case of networks which are wireless (Appavoo, et al., 2008).
In one of the paper by (Kim, 2006), it is properly taken care of whether the Passwords and
Username or a certificate can take the form of Security Credentials. Instead, the VPN client gets
equipped with an awareness of the restricted Information related to the Credentials. Secondly, it
was clearly defined by (Walter, 2016) that the security which ensures authorization allows the
client of VPN to draw a connection with VPN and a set of constraints by the connection are also
provided like idle timeout, the maximum time of connection, required a method of
authentication, etc. The data is sent to VPN server and VPN client by encrypting the data using
the algorithm encryption and by using the key which is confidential and known only to the server
and client of VPN. This was also observed in (Asati et al., 2014) that how a private intranet and
the server gets exposed to the attack. The internet based attacker floods the server of VPN with
many packets, and they access the intranet as a router by using the intranet. To deal with these
types of attacks, the VPN server's interface of the internet is dealt with a number of IP packet
filters that allows only VPN traffic. This may also ensure that rejection of Service attacks and
campus.
3. To determine the benefits of VPN to students and university.
Literature review
It has been suggested by (Papp, 2014) that the technology of VPN transmits the data between
devices in a secured manner. The successful implementation of VPN has been observed by
(Suzuki, 2001) in wireless networks while using the internet as a medium. After observing the
success of the use of VPN in Networks which are wired, and after understanding the implications
of insecurity pointed towards networks which are wireless, it has engaged administrators and
developers to utilize it in the case of networks which are wireless (Appavoo, et al., 2008).
In one of the paper by (Kim, 2006), it is properly taken care of whether the Passwords and
Username or a certificate can take the form of Security Credentials. Instead, the VPN client gets
equipped with an awareness of the restricted Information related to the Credentials. Secondly, it
was clearly defined by (Walter, 2016) that the security which ensures authorization allows the
client of VPN to draw a connection with VPN and a set of constraints by the connection are also
provided like idle timeout, the maximum time of connection, required a method of
authentication, etc. The data is sent to VPN server and VPN client by encrypting the data using
the algorithm encryption and by using the key which is confidential and known only to the server
and client of VPN. This was also observed in (Asati et al., 2014) that how a private intranet and
the server gets exposed to the attack. The internet based attacker floods the server of VPN with
many packets, and they access the intranet as a router by using the intranet. To deal with these
types of attacks, the VPN server's interface of the internet is dealt with a number of IP packet
filters that allows only VPN traffic. This may also ensure that rejection of Service attacks and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

hacking of internet does not touch the normal course of operations. In the research that was
conducted in 2010, it was justified that in order to allow a connection to be accepted, the attempt
should be authorized and authenticated by use of credentials which are valid (Border et al.,
2015).
It has been identified by (Husain, 2016) that to communicate inside the campus, the internet has
become the most commonly used channel. Therefore in order to provide the efficient and secured
delivery of data, the infrastructure of IT has accepted the challenge to provide for the same. A
Virtual Private Network (VPN) is a Network which is privately held to transfer the data and uses
the publicly held infrastructure of telecommunication. It sustains confidentiality by using
security procedure and a tunneling protocol. The main intention to use VPN is to provide a
connection between the university and the students that are well secured and encrypted. A VPN
operates by transmitting data to the internet via “Tunnels” which are encrypted and secured. The
different kinds of protocols which are used by VPN for tunneling are (Mullick et al., 2013):
Internet Protocol Security (IPSEC): IPsec authenticates users, data integrity and encryption
of data during the transmission of data between receivers and senders. Three protocols which
are primary in nature are used: Internet Key Exchange (IKE), Encapsulated Security Payload
(ESP), and Authentication Header. These are used to transmit data and establish a connection
in a secured way.
Layer2 Tunneling Protocol (L2TP): L2TP tunneling is achieved through encapsulating at
multiple levels. An L2TP header and a PPP header get encapsulated with PPP data. A UDP
header encapsulates an L2TP.
conducted in 2010, it was justified that in order to allow a connection to be accepted, the attempt
should be authorized and authenticated by use of credentials which are valid (Border et al.,
2015).
It has been identified by (Husain, 2016) that to communicate inside the campus, the internet has
become the most commonly used channel. Therefore in order to provide the efficient and secured
delivery of data, the infrastructure of IT has accepted the challenge to provide for the same. A
Virtual Private Network (VPN) is a Network which is privately held to transfer the data and uses
the publicly held infrastructure of telecommunication. It sustains confidentiality by using
security procedure and a tunneling protocol. The main intention to use VPN is to provide a
connection between the university and the students that are well secured and encrypted. A VPN
operates by transmitting data to the internet via “Tunnels” which are encrypted and secured. The
different kinds of protocols which are used by VPN for tunneling are (Mullick et al., 2013):
Internet Protocol Security (IPSEC): IPsec authenticates users, data integrity and encryption
of data during the transmission of data between receivers and senders. Three protocols which
are primary in nature are used: Internet Key Exchange (IKE), Encapsulated Security Payload
(ESP), and Authentication Header. These are used to transmit data and establish a connection
in a secured way.
Layer2 Tunneling Protocol (L2TP): L2TP tunneling is achieved through encapsulating at
multiple levels. An L2TP header and a PPP header get encapsulated with PPP data. A UDP
header encapsulates an L2TP.

Point to point tunneling Protocol (PPTP): PPTP is an OSI Layer2 protocol which is an
extension of point-to-point protocol (PPP). An IP datagram is created by it which contains
PPP packets being encrypted and transported via the tunnel.
Secure Sockets Layer (SSL): A seamless connections is committed and given to users with
web browsers while using SSL. The data is protected by getting encrypted and using the hash
to ensure integrity.
The process of setting up the VPN can be traced from the paper of ( Shokhor, S.,
and Shigapov, A., F5 Networks, Inc., 2013). To use VPN technology, one can use the
tunnel or end to end connection, in place of putting in use the WEP key to
encrypt the data.
A tunnel is created on top to make the VPN work. The security levels that are provided by VPN
includes (Papp, 2014):
User-Based Authentication:
Every logged on user at a station which is particularly wireless should be authorized by a VPN
Server who are getting connected to WLAN using the client of VPN.
Encryption:
At the top of every unsecured medium, a VPN provides a secured tunnel. In order to provide
double security and confidentiality to the data transmitted, the data which is passing through the
tunnel also gets encrypted. Now, Even if a hacker manages to get access to the tunnel
information, it has to decode it to understand the data.
Data Authentication:
extension of point-to-point protocol (PPP). An IP datagram is created by it which contains
PPP packets being encrypted and transported via the tunnel.
Secure Sockets Layer (SSL): A seamless connections is committed and given to users with
web browsers while using SSL. The data is protected by getting encrypted and using the hash
to ensure integrity.
The process of setting up the VPN can be traced from the paper of ( Shokhor, S.,
and Shigapov, A., F5 Networks, Inc., 2013). To use VPN technology, one can use the
tunnel or end to end connection, in place of putting in use the WEP key to
encrypt the data.
A tunnel is created on top to make the VPN work. The security levels that are provided by VPN
includes (Papp, 2014):
User-Based Authentication:
Every logged on user at a station which is particularly wireless should be authorized by a VPN
Server who are getting connected to WLAN using the client of VPN.
Encryption:
At the top of every unsecured medium, a VPN provides a secured tunnel. In order to provide
double security and confidentiality to the data transmitted, the data which is passing through the
tunnel also gets encrypted. Now, Even if a hacker manages to get access to the tunnel
information, it has to decode it to understand the data.
Data Authentication:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This feature confirms that all the data that is coming from any point is authenticated and thus
conforms the authentication of the point of origin.
Research methodology
This research is deductive approach because there is no generation of a new theory from the data.
Instead, just the existing theory is being tested and implemented for setting up a VPN in the
campus. Since the research questions are theoretical and they do not need the quantitative results,
the nature of data that will be collected for this study will be qualitative. Only the secondary
sources will be used to collect the dat. The data will be collected using the journals, research
papers, case studies, and articles.
The source of data will be secondary because secondary sources will be able to justify the
descriptive research design. The secondary data will be collected from the journals, articles;
newspapers etc. which will form a base for the study, help in identifying the processes and will
also help in fulfilling the objectives in the study. The data will be analyzed carefully from the
secondary sources and by comparing the work of various researchers and authors.
Critical evaluation and reflection of the outcome and process
The outcomes expected from this research are that the research will explain in detail about the
process of setting up a VPN be in the campus environment using the university’s wireless
network. Also, the research will help in identifying the hardware and software tools which are
required to set up the VPN in campus so that the arrangements can be made in the university
conforms the authentication of the point of origin.
Research methodology
This research is deductive approach because there is no generation of a new theory from the data.
Instead, just the existing theory is being tested and implemented for setting up a VPN in the
campus. Since the research questions are theoretical and they do not need the quantitative results,
the nature of data that will be collected for this study will be qualitative. Only the secondary
sources will be used to collect the dat. The data will be collected using the journals, research
papers, case studies, and articles.
The source of data will be secondary because secondary sources will be able to justify the
descriptive research design. The secondary data will be collected from the journals, articles;
newspapers etc. which will form a base for the study, help in identifying the processes and will
also help in fulfilling the objectives in the study. The data will be analyzed carefully from the
secondary sources and by comparing the work of various researchers and authors.
Critical evaluation and reflection of the outcome and process
The outcomes expected from this research are that the research will explain in detail about the
process of setting up a VPN be in the campus environment using the university’s wireless
network. Also, the research will help in identifying the hardware and software tools which are
required to set up the VPN in campus so that the arrangements can be made in the university
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

campus. Then, the research will help in giving the result of this by describing the benefits that
the students and University will get after VPN is set up in the campus environment.
The results of the study will get communicated to the large audience in the form of the report and
the research paper that will be submitted and published in the journals, and the websites. This
research is intended for a larger audience and all the members of the educational community.
Thus, the universities can enable and equip their students with accessing the online resources
even when they are absent from the campus and the resources provided by the university can also
be accessed as per the comfort level of students.
It will form a base for the further research when the other researchers will identify the lacking
area in the research and they will set up their new objectives accordingly.
The possible limitations of the findings may be that the process that is applicable to one
university may not able applicable other because the requirements may be different. Also, the
benefits that this system will give to the campus may be different from the other campuses.
Timeline
Introduction 3 days
Literature review 10 days
the students and University will get after VPN is set up in the campus environment.
The results of the study will get communicated to the large audience in the form of the report and
the research paper that will be submitted and published in the journals, and the websites. This
research is intended for a larger audience and all the members of the educational community.
Thus, the universities can enable and equip their students with accessing the online resources
even when they are absent from the campus and the resources provided by the university can also
be accessed as per the comfort level of students.
It will form a base for the further research when the other researchers will identify the lacking
area in the research and they will set up their new objectives accordingly.
The possible limitations of the findings may be that the process that is applicable to one
university may not able applicable other because the requirements may be different. Also, the
benefits that this system will give to the campus may be different from the other campuses.
Timeline
Introduction 3 days
Literature review 10 days
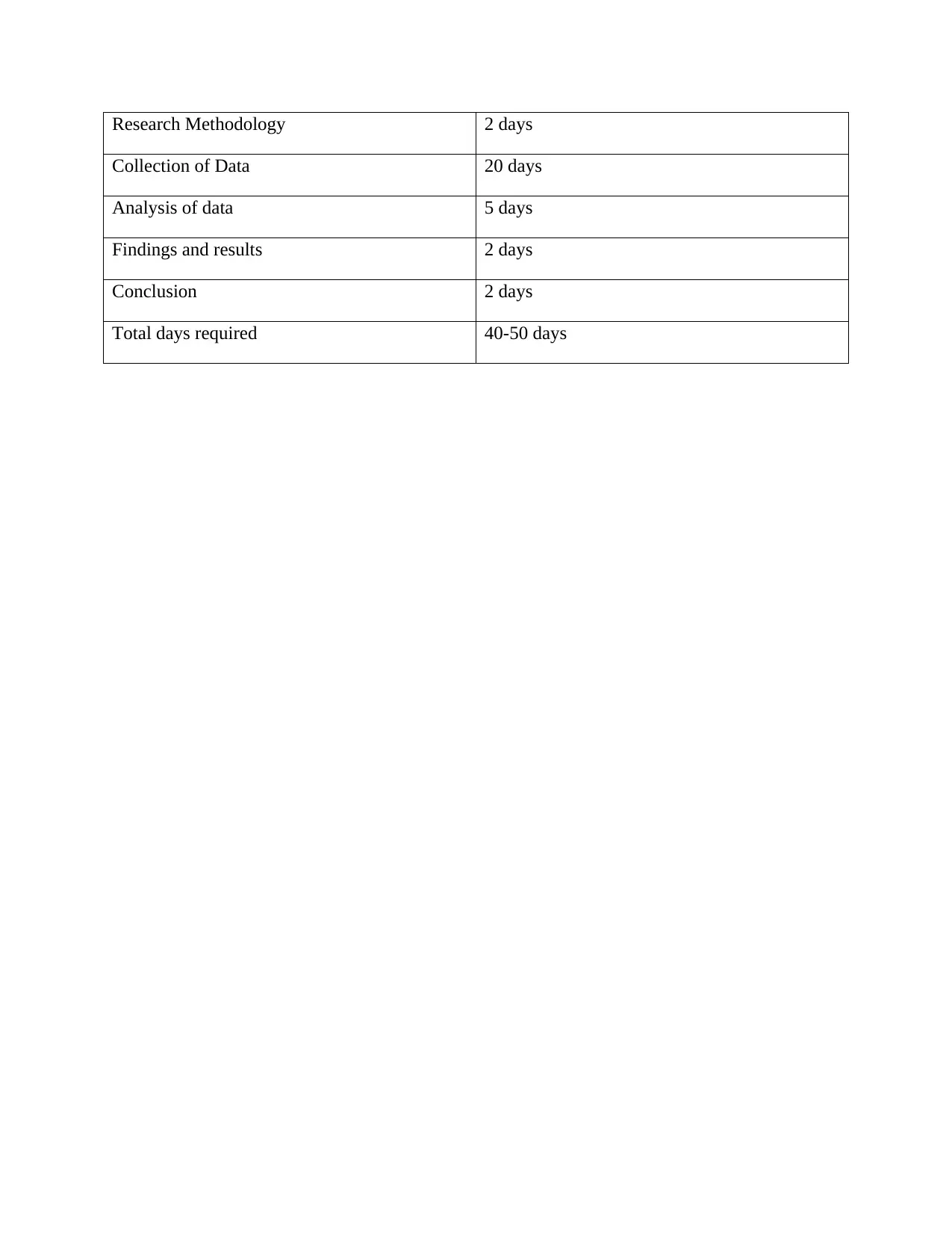
Research Methodology 2 days
Collection of Data 20 days
Analysis of data 5 days
Findings and results 2 days
Conclusion 2 days
Total days required 40-50 days
Collection of Data 20 days
Analysis of data 5 days
Findings and results 2 days
Conclusion 2 days
Total days required 40-50 days
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Appavoo, J., Uhlig, V. and Waterland, A., 2008. Project Kittyhawk: building a global-scale
computer: Blue Gene/P as a generic computing platform. ACM SIGOPS Operating Systems
Review, 42(1), pp.77-84.
Asati, R., Khalid, M., Cherukuri, S., Durazzo, K.A. and Murthy, S., Cisco Technology, Inc.,
2014. Integrating service insertion architecture and virtual private network. U.S. Patent
8,650,618.
Border, J., Dillon, D. and Pardee, P., Hughes Network Systems, Llc, 2015. Method and system
for communicating over a segmented virtual private network (VPN). U.S. Patent 8,976,798.
Eisendrath, E., Rosenfield, A.M., Ohmaye, E. and Keating, P., Unext. Com Llc, 2002. Online
virtual campus. U.S. Patent 6,347,333.
Husain, S.M.A., Printz, R.P. and Mellacheruvu, R.K., Clearcube Technology, Inc., 2016. Zero
client device with integrated virtual private network capability. U.S. Patent 9,389,825.
Kim, S.H., Mims, C. and Holmes, K.P., 2006. An introduction to current trends and benefits of
mobile wireless technology use in higher education. AACE journal, 14(1), pp.77-100.
Mullick, A., Nanjundaswamy, S. and Soni, A., Citrix Systems, Inc., 2013. Method and appliance
for authenticating, by an appliance, a client to access a virtual private network connection,
based on an attribute of a client-side certificate. U.S. Patent 8,413,229.
Papp, O., Mihaly, A., Csàszàr, A. and Westberg, L., Telefonaktiebolaget LM Ericsson (Publ),
2014. Setting up a virtual private network. U.S. Patent 8,761,043.
Appavoo, J., Uhlig, V. and Waterland, A., 2008. Project Kittyhawk: building a global-scale
computer: Blue Gene/P as a generic computing platform. ACM SIGOPS Operating Systems
Review, 42(1), pp.77-84.
Asati, R., Khalid, M., Cherukuri, S., Durazzo, K.A. and Murthy, S., Cisco Technology, Inc.,
2014. Integrating service insertion architecture and virtual private network. U.S. Patent
8,650,618.
Border, J., Dillon, D. and Pardee, P., Hughes Network Systems, Llc, 2015. Method and system
for communicating over a segmented virtual private network (VPN). U.S. Patent 8,976,798.
Eisendrath, E., Rosenfield, A.M., Ohmaye, E. and Keating, P., Unext. Com Llc, 2002. Online
virtual campus. U.S. Patent 6,347,333.
Husain, S.M.A., Printz, R.P. and Mellacheruvu, R.K., Clearcube Technology, Inc., 2016. Zero
client device with integrated virtual private network capability. U.S. Patent 9,389,825.
Kim, S.H., Mims, C. and Holmes, K.P., 2006. An introduction to current trends and benefits of
mobile wireless technology use in higher education. AACE journal, 14(1), pp.77-100.
Mullick, A., Nanjundaswamy, S. and Soni, A., Citrix Systems, Inc., 2013. Method and appliance
for authenticating, by an appliance, a client to access a virtual private network connection,
based on an attribute of a client-side certificate. U.S. Patent 8,413,229.
Papp, O., Mihaly, A., Csàszàr, A. and Westberg, L., Telefonaktiebolaget LM Ericsson (Publ),
2014. Setting up a virtual private network. U.S. Patent 8,761,043.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Shokhor, S., and Shigapov, A., F5 Networks, Inc., 2013. System and method for dynamic policy
based access over a virtual private network. U.S. Patent 8,560,709.
Suzuki, H., 2001. System providing a virtual private network service. U.S. Patent Application
09/998,550.
Walter, M., Campagna, N., Chen, Y.Z. and Gill, M.S., Palo Alto Networks, Inc.,
2016. Credentials management in large scale virtual private network deployment. U.S. Patent
9,306,911.
based access over a virtual private network. U.S. Patent 8,560,709.
Suzuki, H., 2001. System providing a virtual private network service. U.S. Patent Application
09/998,550.
Walter, M., Campagna, N., Chen, Y.Z. and Gill, M.S., Palo Alto Networks, Inc.,
2016. Credentials management in large scale virtual private network deployment. U.S. Patent
9,306,911.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





