VLC Media Player: Vulnerabilities, Exploitation, and Countermeasures
VerifiedAdded on 2021/01/01
|13
|3382
|419
Report
AI Summary
This report provides a detailed analysis of software exploitation, focusing on the vulnerabilities and weaknesses of the VLC media player within a Windows system environment. It identifies specific vulnerabilities, such as those related to buffer overflows and flaws in HTTP packet parsing, which can lead to memory corruption and arbitrary code execution. The report explores various exploitation techniques, including arbitrary directory creation, DLL hacking, and network exploitation, including denial-of-service attacks. It also evaluates countermeasures against these exploitation techniques, emphasizing the importance of understanding memory security and implementing defensive measures like static analysis and stack-based buffer flow protection. The report highlights the importance of users installing the latest versions of the application to fix security vulnerabilities and refraining from opening files from untrusted locations.

Software Exploitation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
TASKS.............................................................................................................................................3
The Vulnerabilities and weakness of VLC multiplayer within the system environment..........3
Analyse and evaluate the systems or networks for the exploitation ..........................................6
Understanding the counter measures against the exploitation technique....................................7
Evaluate the secure system design and software protection methods.........................................9
RECOMMENDATION.................................................................................................................10
CONCLUSION..............................................................................................................................11
REFERENCES..............................................................................................................................12
INTRODUCTION...........................................................................................................................3
TASKS.............................................................................................................................................3
The Vulnerabilities and weakness of VLC multiplayer within the system environment..........3
Analyse and evaluate the systems or networks for the exploitation ..........................................6
Understanding the counter measures against the exploitation technique....................................7
Evaluate the secure system design and software protection methods.........................................9
RECOMMENDATION.................................................................................................................10
CONCLUSION..............................................................................................................................11
REFERENCES..............................................................................................................................12

INTRODUCTION
Software exploitation is basically finding the flaws such as overflow of buffer, applicable
the use of free in the software product or exploitation them. The purpose of project to find the
vulnerabilities and weakness of VLC multimedia player within the system environment. VLC
media player is the best example of software exploitation which based on the open source
platform multimedia player and framework that plays important role in terms of optic media and
various type of streaming protocols. This report will describe the Vulnerabilities and weaknesses
which affects VLC multimedia player in the platform such as Windows. Furthermore, this
assignment will discuss about t
TASKS
The Vulnerabilities and weakness of VLC multiplayer within the system environment
VLC is a free and open source cross platform multimedia player or frame work that plays
important role in the multimedia files such as Audio, VCDs, DVD and different type of
streaming protocols.
Vulnerabilities have been discovered in the different version of VLC media player which
may allows corrupting for cyberattacker to easily corrupt the memory. It also executes the
arbitrary code for running the system application in proper manner (Al-Serhani & et.al., 2018).
According to the videosLan project is based on the community of non profit developer those who
will create one of the open source media tools for people. VLC is also the popular and well
known results of project which act as cross platform multimedia player. This framework is
performed different roles in the multimedia files such as VCDs, DVDs, Audio CDs etc.
VLC media player is supports the window's system that can use for all time. It is non
profit organization behind the VLC media players that mange all the desktop operating system.
A vulnerability is the main threat in the VLC media player on windows which is very
critical to handle the system. It has been found the issue in the processing of file and
manipulation within the unknown inputs that lead to corrupt the memory vulnerability. In
videolan.org, it identifying the vulnerability and attack may be initiated remotely. There is not
form of authentication needed for the successful exploitation.
Software exploitation-
Class – Memory corruption
Remote- Yes
Software exploitation is basically finding the flaws such as overflow of buffer, applicable
the use of free in the software product or exploitation them. The purpose of project to find the
vulnerabilities and weakness of VLC multimedia player within the system environment. VLC
media player is the best example of software exploitation which based on the open source
platform multimedia player and framework that plays important role in terms of optic media and
various type of streaming protocols. This report will describe the Vulnerabilities and weaknesses
which affects VLC multimedia player in the platform such as Windows. Furthermore, this
assignment will discuss about t
TASKS
The Vulnerabilities and weakness of VLC multiplayer within the system environment
VLC is a free and open source cross platform multimedia player or frame work that plays
important role in the multimedia files such as Audio, VCDs, DVD and different type of
streaming protocols.
Vulnerabilities have been discovered in the different version of VLC media player which
may allows corrupting for cyberattacker to easily corrupt the memory. It also executes the
arbitrary code for running the system application in proper manner (Al-Serhani & et.al., 2018).
According to the videosLan project is based on the community of non profit developer those who
will create one of the open source media tools for people. VLC is also the popular and well
known results of project which act as cross platform multimedia player. This framework is
performed different roles in the multimedia files such as VCDs, DVDs, Audio CDs etc.
VLC media player is supports the window's system that can use for all time. It is non
profit organization behind the VLC media players that mange all the desktop operating system.
A vulnerability is the main threat in the VLC media player on windows which is very
critical to handle the system. It has been found the issue in the processing of file and
manipulation within the unknown inputs that lead to corrupt the memory vulnerability. In
videolan.org, it identifying the vulnerability and attack may be initiated remotely. There is not
form of authentication needed for the successful exploitation.
Software exploitation-
Class – Memory corruption
Remote- Yes
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Status – Highly functional processing
Local- No
Access- Public
Programming language- C++
Price of exploitation- USD $0-$6k at the moment (calculate the estimations)
This media player is improved the playback for different formats such as apple lossless
audio and MKV files etc.
Codec and other party library can update that help for improve the playback and their
overall quality.
This system is improved the parsing of vimeo playlist and other SRT subtitle or HTML.
There are various type of operating system improvement and also fixes that have made to the
new version of player. There are different platform support this system application such as
windows and Mac OS etc. The users of media player should install the latest version of
application in the operating system which possible to easily fix all the security vulnerabilities.
Vulnerabilities:
It needs for parsing an invalid MKV file but their input validations are insufficient. In this
way, A malicious third party will able to perform execution of arbitrary code.
Illustration 1
Local- No
Access- Public
Programming language- C++
Price of exploitation- USD $0-$6k at the moment (calculate the estimations)
This media player is improved the playback for different formats such as apple lossless
audio and MKV files etc.
Codec and other party library can update that help for improve the playback and their
overall quality.
This system is improved the parsing of vimeo playlist and other SRT subtitle or HTML.
There are various type of operating system improvement and also fixes that have made to the
new version of player. There are different platform support this system application such as
windows and Mac OS etc. The users of media player should install the latest version of
application in the operating system which possible to easily fix all the security vulnerabilities.
Vulnerabilities:
It needs for parsing an invalid MKV file but their input validations are insufficient. In this
way, A malicious third party will able to perform execution of arbitrary code.
Illustration 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

On the other hand, vulnerability is present in the flaw in HTTP packet parsing and their
functionality. It required for analyze the HTTP headers fir tunneling over it. This is also critical
security flaws that control the overall functionality. It found that hackers easily hijack the
computers to the Media player files.
Weakness of VLC media player-
Sometimes, there are some playback problems arises due to malware during the playing
of DVD with VLC. It is needed to upgrade the system application in proper manner.
It can be outdated the interface.
It cannot be downloaded the video music. Playing the video of H.265 encoded videos on the VLC media player get shows the error
related the codec unsupported.
Vulnerabilities and weaknesses that affect VLC on that Windows
Vulnerability is a type of weakness which can easily exploited by the hackers and
attacker. They performed different type of unauthorized action within hardware system. It is
generally refers to the software vulnerabilities in VLC media player.
A vulnerability and weakness is the main spot in the network that might be exploited due
to the security threat. Risk happens in the VLC media player due to the threats and
vulnerabilities. The windows update on the server may cause the vulnerability on the web server
(Fartash & et.al., 2018). This type of risk is associated with the vulnerability such as data loss,
slow down the applications, It is needed for rebuild their server with the help of updation.
A set of high critical vulnerabilities in the terms of cross platform VLC media player that
can put users at risk regarding the remote program executive attacks. As per researcher, it found
that the risk in terms of security. There are another problems generated when the hackers
perform different task to control the compromised device by rigged media files. VideoLan is the
open source that can manage the VLC project in proper manner.
The vulnerability is basically located in the Component of VLC which responsible for
playing the advanced streaming format video files and video LAN etc. There are many users to
refrain from the opening files through untrusted location and also disable the plug in until the
issue is easily patched. Code execution is subtitle vulnerabilities attack on the user of steaming
services and many hacker can access the code or affect the different version of VLC media
player. Hackers are attempts to attack in the check point report where the users can implements
functionality. It required for analyze the HTTP headers fir tunneling over it. This is also critical
security flaws that control the overall functionality. It found that hackers easily hijack the
computers to the Media player files.
Weakness of VLC media player-
Sometimes, there are some playback problems arises due to malware during the playing
of DVD with VLC. It is needed to upgrade the system application in proper manner.
It can be outdated the interface.
It cannot be downloaded the video music. Playing the video of H.265 encoded videos on the VLC media player get shows the error
related the codec unsupported.
Vulnerabilities and weaknesses that affect VLC on that Windows
Vulnerability is a type of weakness which can easily exploited by the hackers and
attacker. They performed different type of unauthorized action within hardware system. It is
generally refers to the software vulnerabilities in VLC media player.
A vulnerability and weakness is the main spot in the network that might be exploited due
to the security threat. Risk happens in the VLC media player due to the threats and
vulnerabilities. The windows update on the server may cause the vulnerability on the web server
(Fartash & et.al., 2018). This type of risk is associated with the vulnerability such as data loss,
slow down the applications, It is needed for rebuild their server with the help of updation.
A set of high critical vulnerabilities in the terms of cross platform VLC media player that
can put users at risk regarding the remote program executive attacks. As per researcher, it found
that the risk in terms of security. There are another problems generated when the hackers
perform different task to control the compromised device by rigged media files. VideoLan is the
open source that can manage the VLC project in proper manner.
The vulnerability is basically located in the Component of VLC which responsible for
playing the advanced streaming format video files and video LAN etc. There are many users to
refrain from the opening files through untrusted location and also disable the plug in until the
issue is easily patched. Code execution is subtitle vulnerabilities attack on the user of steaming
services and many hacker can access the code or affect the different version of VLC media
player. Hackers are attempts to attack in the check point report where the users can implements

the aforementioned streaming services. This type of attack is spreading to the streaming services.
Memory corruption is the affected the VLC Player and this is also another weakness that can be
exploited by the attacker to run the code.
Technical details-
The error is generated in the CUE demuxer that can be exploited which causes of
overflow of stack based buffers. It is specially crafted the image file of CUE.
The error is generated in the real text demuxer that can be exploited which causes the
overflow buffer based on stack.
In windows, VLC media player is based on the hardware decoding which requires 0 copy
of Graphical user interface.
Exploitation is a major issues that required for user to explicitly open the crafted files. As per
media player, it will avoid the standard device for the opening of untrusted parties and
unfaithfully remote sites (Fartash & et.al., 2018). It is the main cause of data loss and affect the
entire application platforms.
Analyse and evaluate the systems or networks for the exploitation
Open source software development is the important paradigms in the terms of
development. It is a key aspect of OSS to determine the success of project and developer can
understand the need or requirement of business process (Loureiro & et.al., 2018). In this way,
there are increasing the risk of exploitation in the system and application because many
vulnerabilities can damage the entire system their processing.
Techniques use the attacker to affect the network system and occurs the exploitation
The technique to exploit the arbitrary directory that creation of vulnerabilities on the
windows to easily access any type of file on the system. Currently, it can be used the spring
creators update that easily track all the files which is based on the long term security benefits. It
also providing the details regarding the vulnerabilities' exploitation.
User can modify the arbitrary file for write the vulnerabilities is where the user can create
and modify the file at different location. Many attackers send the symbolic link to the user
where user can write a link on the particular location. In this way, attacker easily access all the
information related the files. Attacker not only control the local but also written the entire
content of files (Rajasekar & Imafidon, 2018). This is the most common exploitation in the
system that performed by the DLL hacking. The Basic purpose of DLL hacking is to search the
Memory corruption is the affected the VLC Player and this is also another weakness that can be
exploited by the attacker to run the code.
Technical details-
The error is generated in the CUE demuxer that can be exploited which causes of
overflow of stack based buffers. It is specially crafted the image file of CUE.
The error is generated in the real text demuxer that can be exploited which causes the
overflow buffer based on stack.
In windows, VLC media player is based on the hardware decoding which requires 0 copy
of Graphical user interface.
Exploitation is a major issues that required for user to explicitly open the crafted files. As per
media player, it will avoid the standard device for the opening of untrusted parties and
unfaithfully remote sites (Fartash & et.al., 2018). It is the main cause of data loss and affect the
entire application platforms.
Analyse and evaluate the systems or networks for the exploitation
Open source software development is the important paradigms in the terms of
development. It is a key aspect of OSS to determine the success of project and developer can
understand the need or requirement of business process (Loureiro & et.al., 2018). In this way,
there are increasing the risk of exploitation in the system and application because many
vulnerabilities can damage the entire system their processing.
Techniques use the attacker to affect the network system and occurs the exploitation
The technique to exploit the arbitrary directory that creation of vulnerabilities on the
windows to easily access any type of file on the system. Currently, it can be used the spring
creators update that easily track all the files which is based on the long term security benefits. It
also providing the details regarding the vulnerabilities' exploitation.
User can modify the arbitrary file for write the vulnerabilities is where the user can create
and modify the file at different location. Many attackers send the symbolic link to the user
where user can write a link on the particular location. In this way, attacker easily access all the
information related the files. Attacker not only control the local but also written the entire
content of files (Rajasekar & Imafidon, 2018). This is the most common exploitation in the
system that performed by the DLL hacking. The Basic purpose of DLL hacking is to search the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

executable file which run at the high privilege that load from the location where the
vulnerabilities allows writing the content. Attacker easily succeeds if DLL is not ready to find
the location in proper manner.
Network Exploitation-
Network exploitation is mainly delivered to the GCHQ data to the intelligence values by
remotely control the entire network system. It refers to the ability to easily exploit the
information and data which are required to collect or gather information for their own purpose.
The exploitation is explained to identify the target by gleaning the data from them and determine
those surveilled. The attacker is mainly used the system resources which requires for computers.
Denial of service exploitation-
Denial of service is directly attack on the resources that belongs to the enterprises
competitors (Rajasekar & Imafidon, 2018). It can exploit the user of buffer space at the time of
transmission control protocol. Attacker is targeting the system and devices that applicable for
establishing the network connection. This causes the system target at time out while the waiting
response from the devices. Which makes the entire network slow down and become unusable for
users.
Understanding the counter measures against the exploitation technique
There are lack of memory security in the C and C++ often to increase the more chances
of vulnerabilities. VLC media player is also made up with this language so that there are many
risks of slow down the application due to vulnerability. The attacker is mainly used the code
injection affect the overall information flow of applications (Ransome & Misra, 2018). This
attack have played important role in the term of security. The counter measures are different
trade off in the terms of efficiency, performance and compatibility. It makes hard for user to
easily compare and evaluate the counter measure in effective ways.
Counter measures are the techniques to control and manage the exploitation which is
known as vulnerabilities of the specific software components. This method could encompass
both the technical tools and organizational process (Sen, Marijan & Gotlieb, 2018). System and
web application is adopted the counter measure technique to control the exploitation in proper
manner. There are several defensive and preventive countermeasures proposed to mange the
common implementation errors. It includes the appropriate static countermeasure for detecting
the vulnerabilities by using a static analysis.
vulnerabilities allows writing the content. Attacker easily succeeds if DLL is not ready to find
the location in proper manner.
Network Exploitation-
Network exploitation is mainly delivered to the GCHQ data to the intelligence values by
remotely control the entire network system. It refers to the ability to easily exploit the
information and data which are required to collect or gather information for their own purpose.
The exploitation is explained to identify the target by gleaning the data from them and determine
those surveilled. The attacker is mainly used the system resources which requires for computers.
Denial of service exploitation-
Denial of service is directly attack on the resources that belongs to the enterprises
competitors (Rajasekar & Imafidon, 2018). It can exploit the user of buffer space at the time of
transmission control protocol. Attacker is targeting the system and devices that applicable for
establishing the network connection. This causes the system target at time out while the waiting
response from the devices. Which makes the entire network slow down and become unusable for
users.
Understanding the counter measures against the exploitation technique
There are lack of memory security in the C and C++ often to increase the more chances
of vulnerabilities. VLC media player is also made up with this language so that there are many
risks of slow down the application due to vulnerability. The attacker is mainly used the code
injection affect the overall information flow of applications (Ransome & Misra, 2018). This
attack have played important role in the term of security. The counter measures are different
trade off in the terms of efficiency, performance and compatibility. It makes hard for user to
easily compare and evaluate the counter measure in effective ways.
Counter measures are the techniques to control and manage the exploitation which is
known as vulnerabilities of the specific software components. This method could encompass
both the technical tools and organizational process (Sen, Marijan & Gotlieb, 2018). System and
web application is adopted the counter measure technique to control the exploitation in proper
manner. There are several defensive and preventive countermeasures proposed to mange the
common implementation errors. It includes the appropriate static countermeasure for detecting
the vulnerabilities by using a static analysis.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Implementation vulnerabilities and exploitation techniques
It is needed for implementing the techniques against the exploitation which required for
organization to used the method against the attackers that would use to exploit the vulnerability.
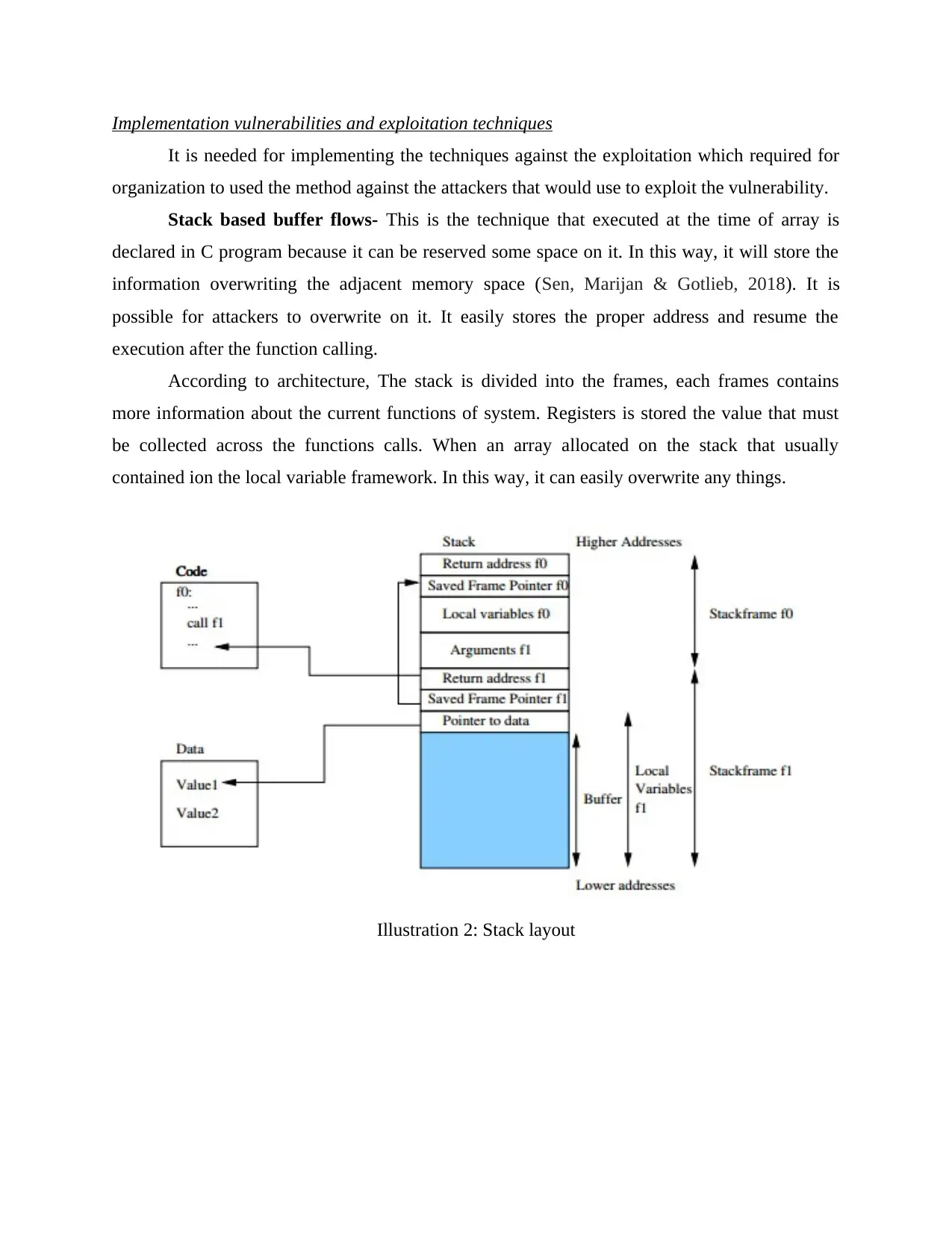
Stack based buffer flows- This is the technique that executed at the time of array is
declared in C program because it can be reserved some space on it. In this way, it will store the
information overwriting the adjacent memory space (Sen, Marijan & Gotlieb, 2018). It is
possible for attackers to overwrite on it. It easily stores the proper address and resume the
execution after the function calling.
According to architecture, The stack is divided into the frames, each frames contains
more information about the current functions of system. Registers is stored the value that must
be collected across the functions calls. When an array allocated on the stack that usually
contained ion the local variable framework. In this way, it can easily overwrite any things.
Illustration 2: Stack layout
It is needed for implementing the techniques against the exploitation which required for
organization to used the method against the attackers that would use to exploit the vulnerability.
Stack based buffer flows- This is the technique that executed at the time of array is
declared in C program because it can be reserved some space on it. In this way, it will store the
information overwriting the adjacent memory space (Sen, Marijan & Gotlieb, 2018). It is
possible for attackers to overwrite on it. It easily stores the proper address and resume the
execution after the function calling.
According to architecture, The stack is divided into the frames, each frames contains
more information about the current functions of system. Registers is stored the value that must
be collected across the functions calls. When an array allocated on the stack that usually
contained ion the local variable framework. In this way, it can easily overwrite any things.
Illustration 2: Stack layout
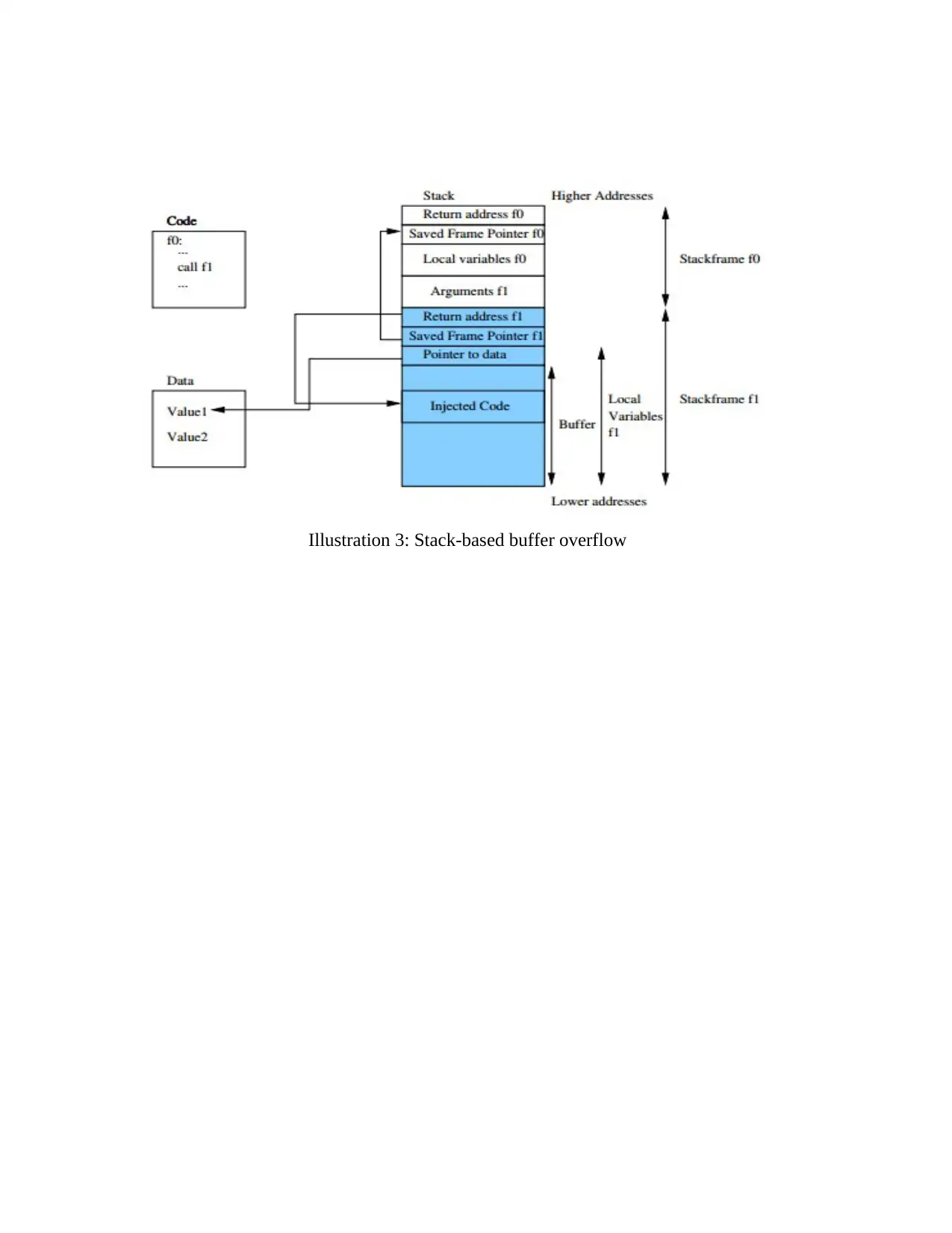
Illustration 3: Stack-based buffer overflow
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Exploitation : if the attackers are capable to make copy all the programs beyond the end of array.
Besides the contents of buffer, the attackers have overwritten the pointer. In this way, it will save
the frame of pointer (Stasinopoulos, Ntantogian & Xenakis, 2019). It could require to continuous
write content into the older frame but in cases, the objective of attackers is to overwrite the return
address, In this way, it will gain the control over the entire program execution process.
Afterwards, Attackers have change the entire return address to pint out the code and they are
copied into the buffer stack.
The particular bug in the VLC media player is copied the documents and automatically
change the entire
Evaluate the secure system design and software protection methods
Secure system design is main concerned about the security and privacy because there are
many attackers affect the entire processing of system. VLC media player is the most common
and flexible player in marketplace. There are large number of people used to support the content
by open source codec files. It is the most appropriate system that can install in the different
platforms such as windows and iOS (Yuce, Schaumon & Witteman, 2018). This player is mainly
supported the media codecs out if box. It is also designed an effective way that support to online
streaming with proper main stream protocols. VLC media player is generally used to view and
listen the audio and video. Media play back can be dedicated the full screen view for people.
Software protection is the important concept in the information technology to protect and
secure system and applications. Nowadays, privacy is the main problem for the system
management because a huge financial loss happen and people suffered by the developers. It
means to safeguard the content of VLC media application program from utilized the use and
control illegal distribution. There are two different type of divided of the software protection
techniques such as hardware based and software based etc.
Software protection is also known as copy protection which necessary for people to
safeguards against to reverse the engineering. It is usually applied the during the time of
installation. Cryptography is a technique to use the cipher information with the help of key. This
type of technique entails to store the software application in the encrypted form on the digital
media (Yuce, Schaumon & Witteman, 2018). In this way, it easily tracks all the activities of
attack. It also addressed the issues and problem related the data security in the terms of integrity.
Besides the contents of buffer, the attackers have overwritten the pointer. In this way, it will save
the frame of pointer (Stasinopoulos, Ntantogian & Xenakis, 2019). It could require to continuous
write content into the older frame but in cases, the objective of attackers is to overwrite the return
address, In this way, it will gain the control over the entire program execution process.
Afterwards, Attackers have change the entire return address to pint out the code and they are
copied into the buffer stack.
The particular bug in the VLC media player is copied the documents and automatically
change the entire
Evaluate the secure system design and software protection methods
Secure system design is main concerned about the security and privacy because there are
many attackers affect the entire processing of system. VLC media player is the most common
and flexible player in marketplace. There are large number of people used to support the content
by open source codec files. It is the most appropriate system that can install in the different
platforms such as windows and iOS (Yuce, Schaumon & Witteman, 2018). This player is mainly
supported the media codecs out if box. It is also designed an effective way that support to online
streaming with proper main stream protocols. VLC media player is generally used to view and
listen the audio and video. Media play back can be dedicated the full screen view for people.
Software protection is the important concept in the information technology to protect and
secure system and applications. Nowadays, privacy is the main problem for the system
management because a huge financial loss happen and people suffered by the developers. It
means to safeguard the content of VLC media application program from utilized the use and
control illegal distribution. There are two different type of divided of the software protection
techniques such as hardware based and software based etc.
Software protection is also known as copy protection which necessary for people to
safeguards against to reverse the engineering. It is usually applied the during the time of
installation. Cryptography is a technique to use the cipher information with the help of key. This
type of technique entails to store the software application in the encrypted form on the digital
media (Yuce, Schaumon & Witteman, 2018). In this way, it easily tracks all the activities of
attack. It also addressed the issues and problem related the data security in the terms of integrity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In this way, it can be stored the confidentiality of information on the business network by using
the encryption algorithm.
Implementation and design errors are generated in the applications so that it leads to
software exploitation. Emulation based software protection method or technique have proposed
in the running application such as VLC media player. This protection method is utilizing the
sandbox that offers to execution of code which protected the sandbox layer in the memory.
Software aging technique is another method for update the software according to their
compatibility. This type of updates help for fixing the bugs and many new features to preserve
the synchronization of software (Yuce, Schaumon & Witteman, 2018). This technique is more
appropriate and beneficial for those applications which are easily immensely the centric
documents.
On the other hand, Modular approach is a type of security design that support through
UML provided in the form of language. In this process, it is required the verification routine to
easily verify the UML model. It is directly integrated with the security that relevant to the
information embedded with the overall system. There are various type of tools available in
market that help for generating code from role based access control. It is modular approach used
to comply with software requirements, authentication, security and integration.
RECOMMENDATION
It will be recommended that Software exploitation is a major causes in the system
application because it affects the entire processing of application. It has been used the different
type of technique to secure the design if VLC media players such as UML design model, aging
technique and emulation based techniques. These are helpful for application to maintain their
performance and efficiency. Software methods has considered the best approaches to handle
complication of their security aspects. For running the application, it is recommended to use the
windows to access any type of application in effective ways. Windows are needed the less
practices in their installation process. It also defaults store the security approach to detect the
unwanted activities of hackers.
the encryption algorithm.
Implementation and design errors are generated in the applications so that it leads to
software exploitation. Emulation based software protection method or technique have proposed
in the running application such as VLC media player. This protection method is utilizing the
sandbox that offers to execution of code which protected the sandbox layer in the memory.
Software aging technique is another method for update the software according to their
compatibility. This type of updates help for fixing the bugs and many new features to preserve
the synchronization of software (Yuce, Schaumon & Witteman, 2018). This technique is more
appropriate and beneficial for those applications which are easily immensely the centric
documents.
On the other hand, Modular approach is a type of security design that support through
UML provided in the form of language. In this process, it is required the verification routine to
easily verify the UML model. It is directly integrated with the security that relevant to the
information embedded with the overall system. There are various type of tools available in
market that help for generating code from role based access control. It is modular approach used
to comply with software requirements, authentication, security and integration.
RECOMMENDATION
It will be recommended that Software exploitation is a major causes in the system
application because it affects the entire processing of application. It has been used the different
type of technique to secure the design if VLC media players such as UML design model, aging
technique and emulation based techniques. These are helpful for application to maintain their
performance and efficiency. Software methods has considered the best approaches to handle
complication of their security aspects. For running the application, it is recommended to use the
windows to access any type of application in effective ways. Windows are needed the less
practices in their installation process. It also defaults store the security approach to detect the
unwanted activities of hackers.

CONCLUSION
As per discussion, it concluded that Software exploitation is process for affecting the
entire information flaws such as overflow of buffer and also applicable the use of free in the
software product or exploitation them. It is summarized that the VLC media player is the best
example of software exploitation which based on the open source platform multimedia player
and framework that plays important role in terms of optic media and various type of streaming
protocols. It also discusses about the software protection technique to control the exploitation in
the application in appropriate manner.
As per discussion, it concluded that Software exploitation is process for affecting the
entire information flaws such as overflow of buffer and also applicable the use of free in the
software product or exploitation them. It is summarized that the VLC media player is the best
example of software exploitation which based on the open source platform multimedia player
and framework that plays important role in terms of optic media and various type of streaming
protocols. It also discusses about the software protection technique to control the exploitation in
the application in appropriate manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

