Cyber security Report 2022
Added on 2022-09-17
12 Pages2352 Words20 Views
Cyber Security
CYBERSECURITY 1
Table of Contents
Introduction.....................................................................................................2
Spyware walkthrough.....................................................................................2
What is spyware attack?..............................................................................2
How does spyware attack work?..................................................................4
Real word spyware incident............................................................................6
Conclusion.......................................................................................................8
References.......................................................................................................9
Table of Contents
Introduction.....................................................................................................2
Spyware walkthrough.....................................................................................2
What is spyware attack?..............................................................................2
How does spyware attack work?..................................................................4
Real word spyware incident............................................................................6
Conclusion.......................................................................................................8
References.......................................................................................................9

CYBERSECURITY 2
Introduction
The term spyware is defined as malware attack which infiltrates the
computer device and networks of the consumers. Such kind of malware is
mainly designed and implemented in order to gain access and damage the
computer networks and devices used by the consumers. It is one of the
common security attacks that have the ability to obtain data from
consumers and organizations without taking their permission (Marczak,
Scott-Railton, & McKune, 2015). The key goal of this paper is to explore the
spyware attack and evaluate a real-life example based on the spyware
attack. It is observed that spyware utilizes internet connections in order to
send traffic signals and viruses to the main server and obtain reliable data
of the consumers by blocking communication channels and networks. This
report mainly focuses on the major two sections, for example, spyware
walkthrough and a real-world example of spyware attack.
Spyware walkthrough
What is spyware attack?
Spyware is a kind of malware software which is able to obtain data of
the consumers without their knowledge. It is observed that spyware is
mainly divided into major four parts including adware, tracking cookies,
Trojans and system monitors. Such kind of process is mainly utilized by the
criminals for performing signals and networks to the main servers and
transfers the unwanted signals from one computer to others using internet
connections.
A recent study examined that spyware is a common form of malware
attack that has the potential to gather personal information of the
consumers including, log in details, financial data, profiles and so on
(Abualola, Alhawai, Kadadha, Otrok, & Mourad, 2016). With the spyware
Introduction
The term spyware is defined as malware attack which infiltrates the
computer device and networks of the consumers. Such kind of malware is
mainly designed and implemented in order to gain access and damage the
computer networks and devices used by the consumers. It is one of the
common security attacks that have the ability to obtain data from
consumers and organizations without taking their permission (Marczak,
Scott-Railton, & McKune, 2015). The key goal of this paper is to explore the
spyware attack and evaluate a real-life example based on the spyware
attack. It is observed that spyware utilizes internet connections in order to
send traffic signals and viruses to the main server and obtain reliable data
of the consumers by blocking communication channels and networks. This
report mainly focuses on the major two sections, for example, spyware
walkthrough and a real-world example of spyware attack.
Spyware walkthrough
What is spyware attack?
Spyware is a kind of malware software which is able to obtain data of
the consumers without their knowledge. It is observed that spyware is
mainly divided into major four parts including adware, tracking cookies,
Trojans and system monitors. Such kind of process is mainly utilized by the
criminals for performing signals and networks to the main servers and
transfers the unwanted signals from one computer to others using internet
connections.
A recent study examined that spyware is a common form of malware
attack that has the potential to gather personal information of the
consumers including, log in details, financial data, profiles and so on
(Abualola, Alhawai, Kadadha, Otrok, & Mourad, 2016). With the spyware

CYBERSECURITY 3
signals, the hackers are able to control and handle the computing devices
and systems used by the companies and produce unauthorized changes in
the computing networks. The signs of a spyware attack involve unwanted
behavior and degradation of system effectiveness by which the sensitive
data of consumers can be collected in less time.
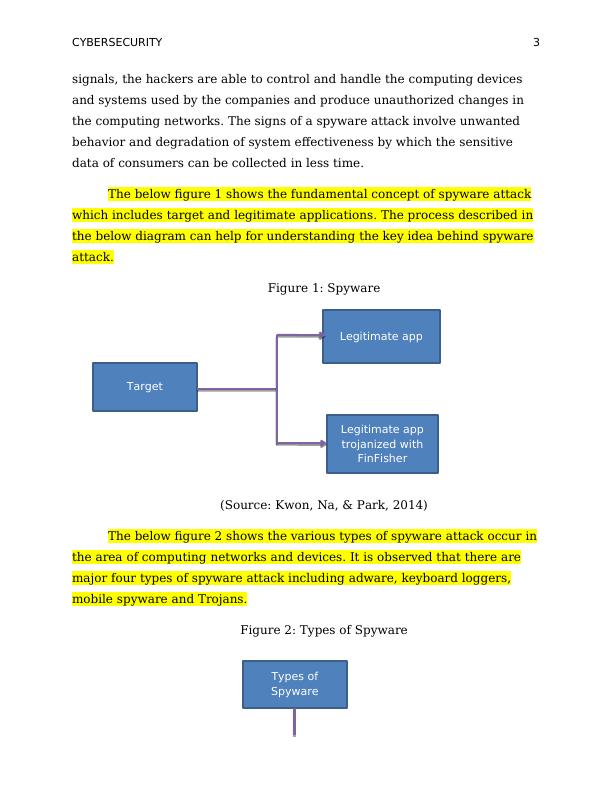
The below figure 1 shows the fundamental concept of spyware attack
which includes target and legitimate applications. The process described in
the below diagram can help for understanding the key idea behind spyware
attack.
Figure 1: Spyware
(Source: Kwon, Na, & Park, 2014)
The below figure 2 shows the various types of spyware attack occur in
the area of computing networks and devices. It is observed that there are
major four types of spyware attack including adware, keyboard loggers,
mobile spyware and Trojans.
Figure 2: Types of Spyware
Legitimate app
Target
Legitimate app
trojanized with
FinFisher
Types of
Spyware
signals, the hackers are able to control and handle the computing devices
and systems used by the companies and produce unauthorized changes in
the computing networks. The signs of a spyware attack involve unwanted
behavior and degradation of system effectiveness by which the sensitive
data of consumers can be collected in less time.
The below figure 1 shows the fundamental concept of spyware attack
which includes target and legitimate applications. The process described in
the below diagram can help for understanding the key idea behind spyware
attack.
Figure 1: Spyware
(Source: Kwon, Na, & Park, 2014)
The below figure 2 shows the various types of spyware attack occur in
the area of computing networks and devices. It is observed that there are
major four types of spyware attack including adware, keyboard loggers,
mobile spyware and Trojans.
Figure 2: Types of Spyware
Legitimate app
Target
Legitimate app
trojanized with
FinFisher
Types of
Spyware
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Ransomware Attack and its Impactlg...
|13
|2416
|74
Malware Attack and Malware Analysis: A Researchlg...
|9
|2293
|146
Malware attack and Malware Analysis: A Researchlg...
|13
|933
|239
Assignment on Risks and Risk Managementlg...
|11
|781
|13
Cyber Security WannCry Attack Case Study 2022lg...
|11
|2314
|16
Ransomware & Malwarelg...
|5
|581
|276