Network Design for Enhanced Data Security
VerifiedAdded on 2020/04/01
|17
|2371
|296
AI Summary
This assignment delves into the intricacies of network design with a primary focus on bolstering data security. It emphasizes the importance of restricting data access to trusted clients only and outlines the need for robust protocols to govern data transmission and connection establishment within home and neighbor networks. The document also highlights the significance of maintaining data logs to track data flow and identify potential security breaches.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
NABIN PANTHA MIT173044
DILAN PERERA
DILAN PERERA
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Executive summary
ABC is an IT company, located in Melbourne. They are involved in giving it support and services to their
clients. They are into server connection, server set up, website development, website designing,
software development, mobile application development, graphics designing and content writing. They
are into winning the trust of our customers since inception. They are going to set up a centralized user
authentication for server.
ABC is an IT company, located in Melbourne. They are involved in giving it support and services to their
clients. They are into server connection, server set up, website development, website designing,
software development, mobile application development, graphics designing and content writing. They
are into winning the trust of our customers since inception. They are going to set up a centralized user
authentication for server.

Contents
Introduction.................................................................................................................................................4
Network requirements and design model...................................................................................................4
Design of Network diagram using Netsim...................................................................................................5
Network Diagram....................................................................................................................................5
Demonstration............................................................................................................................................8
Configuration of the whole project set up a DNS (domain name server)................................................8
Step 1: Centralized user authentication..............................................................................................9
Step 2: Set up a DNS (Domain name server)........................................................................................9
Step 3: Set up a DHCP server to acquire IP address...........................................................................10
Step 4: Create a mirror server for the backup purpose in case of failure..........................................11
Proper labeled Screenshots from implementation....................................................................................13
Active Directory Replication on Windows Server 2012 R2....................................................................13
Installing a window server 2012 by opening the Active directory administration.....................................15
Network performance Result................................................................................................................16
Step 5: Network Implementation and Network testing.....................................................................16
Conclusion.................................................................................................................................................17
Reference..................................................................................................................................................19
Introduction.................................................................................................................................................4
Network requirements and design model...................................................................................................4
Design of Network diagram using Netsim...................................................................................................5
Network Diagram....................................................................................................................................5
Demonstration............................................................................................................................................8
Configuration of the whole project set up a DNS (domain name server)................................................8
Step 1: Centralized user authentication..............................................................................................9
Step 2: Set up a DNS (Domain name server)........................................................................................9
Step 3: Set up a DHCP server to acquire IP address...........................................................................10
Step 4: Create a mirror server for the backup purpose in case of failure..........................................11
Proper labeled Screenshots from implementation....................................................................................13
Active Directory Replication on Windows Server 2012 R2....................................................................13
Installing a window server 2012 by opening the Active directory administration.....................................15
Network performance Result................................................................................................................16
Step 5: Network Implementation and Network testing.....................................................................16
Conclusion.................................................................................................................................................17
Reference..................................................................................................................................................19
Introduction
ABC is an IT company which is based on Melbourne. The company has three departments in the field of
Sales, Finance and HR. In each of these departments there are 15 people working. Back up of important
resources in the form of data is the main concern for the company. Now the company has a system
administrator to look after the data recovery in case of any system failure. It is the responsibility of the
system administrator to replicate the active directory of the company and move the database from one
site to another for future. A copy of the master domain controller i.e. DC1 is created to make sure for
future availability.
Network requirements and design model
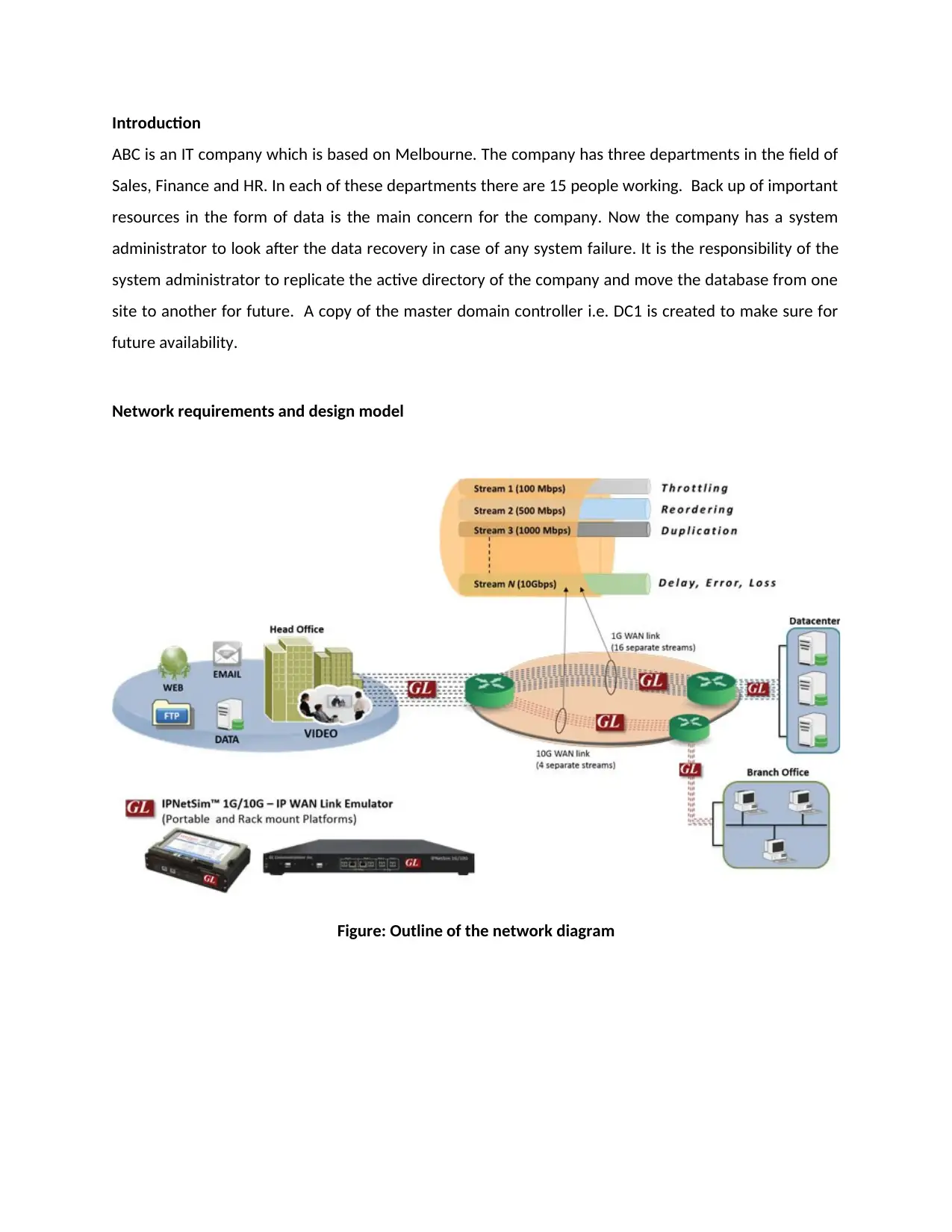
Figure: Outline of the network diagram
ABC is an IT company which is based on Melbourne. The company has three departments in the field of
Sales, Finance and HR. In each of these departments there are 15 people working. Back up of important
resources in the form of data is the main concern for the company. Now the company has a system
administrator to look after the data recovery in case of any system failure. It is the responsibility of the
system administrator to replicate the active directory of the company and move the database from one
site to another for future. A copy of the master domain controller i.e. DC1 is created to make sure for
future availability.
Network requirements and design model
Figure: Outline of the network diagram
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Design of Network diagram using Netsim
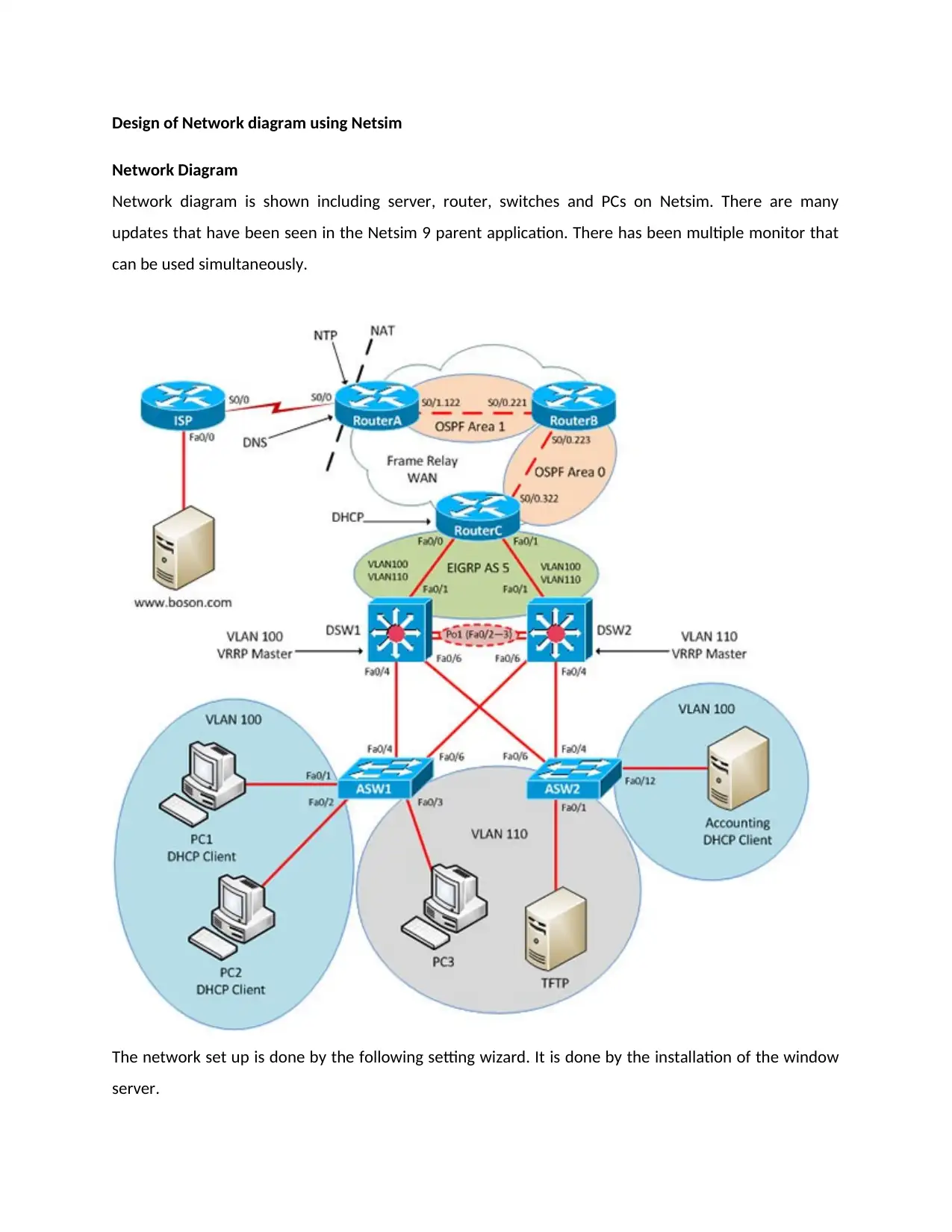
Network Diagram
Network diagram is shown including server, router, switches and PCs on Netsim. There are many
updates that have been seen in the Netsim 9 parent application. There has been multiple monitor that
can be used simultaneously.
The network set up is done by the following setting wizard. It is done by the installation of the window
server.
Network Diagram
Network diagram is shown including server, router, switches and PCs on Netsim. There are many
updates that have been seen in the Netsim 9 parent application. There has been multiple monitor that
can be used simultaneously.
The network set up is done by the following setting wizard. It is done by the installation of the window
server.
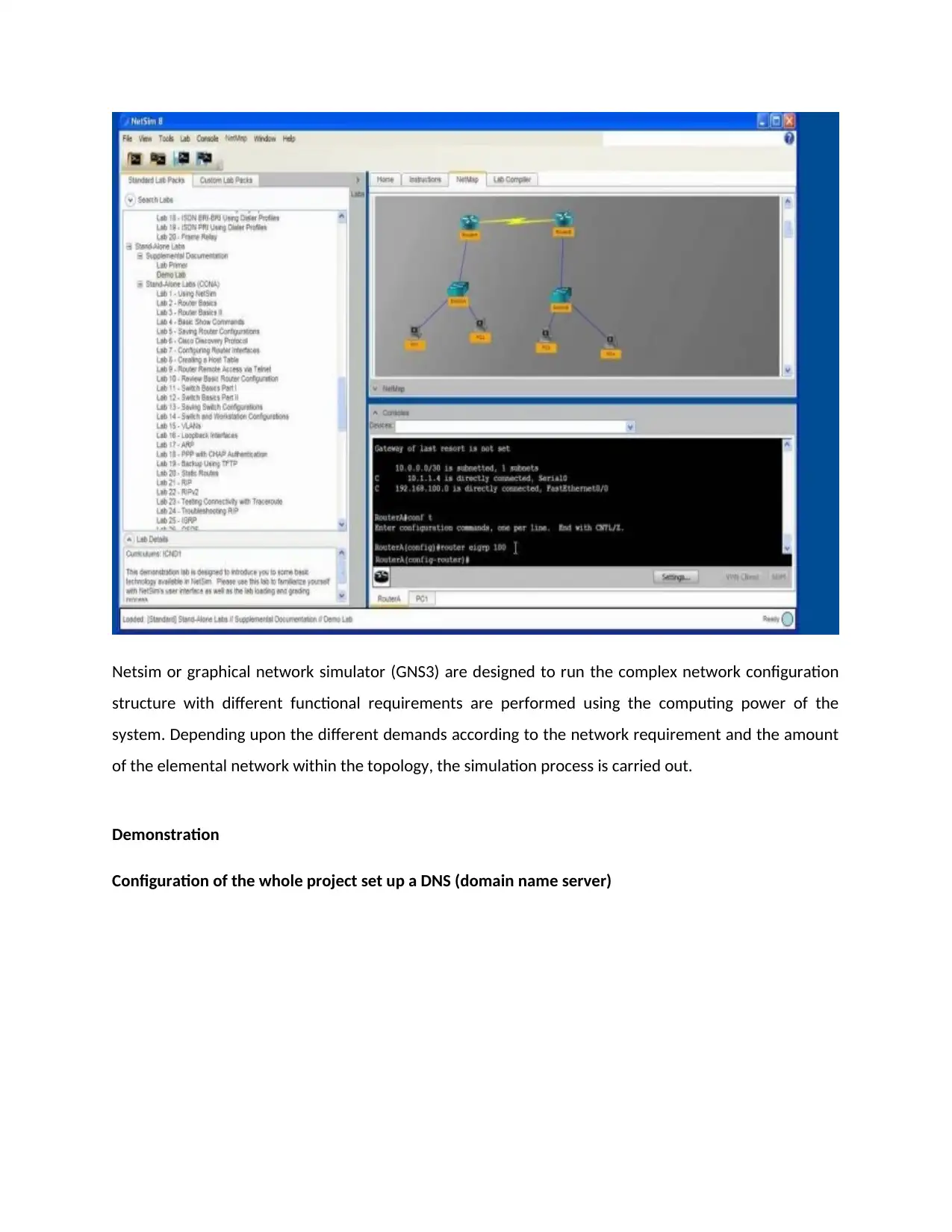
Netsim or graphical network simulator (GNS3) are designed to run the complex network configuration
structure with different functional requirements are performed using the computing power of the
system. Depending upon the different demands according to the network requirement and the amount
of the elemental network within the topology, the simulation process is carried out.
Demonstration
Configuration of the whole project set up a DNS (domain name server)
structure with different functional requirements are performed using the computing power of the
system. Depending upon the different demands according to the network requirement and the amount
of the elemental network within the topology, the simulation process is carried out.
Demonstration
Configuration of the whole project set up a DNS (domain name server)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Step 1: Centralized user authentication
The network servers are centralized computer system within an office, lab or an institute. In the network
servers the programs, data, algorithms and many data files are stored. These files are accessed by the all
computers in the place which are under the main server. The users in the network will share all kinds of
data from the server. The security of the servers is so high that they are protected from all kinds of
threats and faults. The network servers need the hard drives of vey high capacity in the order of 100 GB
and above. As the data shared by the users, this storage capacity of the server must be very high. This
drive size must be too high for the video storage. In the server model one must always prefer the wired
connection of the computer rather than the wireless as the data rates of the wired connections are far
ahead then the wireless connection [1].
Step 2: Set up a DNS (Domain name server)
DNS is abbreviated as the domain name server. This is very similar to the phone call or the truck call. The
internet access has a special type of data establishment. In this the source person will request for the
data access or the data connection establishment. In which the destination must accept or respond. or
else the data may not be obtained or accessed completed. One must know the connection
The network servers are centralized computer system within an office, lab or an institute. In the network
servers the programs, data, algorithms and many data files are stored. These files are accessed by the all
computers in the place which are under the main server. The users in the network will share all kinds of
data from the server. The security of the servers is so high that they are protected from all kinds of
threats and faults. The network servers need the hard drives of vey high capacity in the order of 100 GB
and above. As the data shared by the users, this storage capacity of the server must be very high. This
drive size must be too high for the video storage. In the server model one must always prefer the wired
connection of the computer rather than the wireless as the data rates of the wired connections are far
ahead then the wireless connection [1].
Step 2: Set up a DNS (Domain name server)
DNS is abbreviated as the domain name server. This is very similar to the phone call or the truck call. The
internet access has a special type of data establishment. In this the source person will request for the
data access or the data connection establishment. In which the destination must accept or respond. or
else the data may not be obtained or accessed completed. One must know the connection

establishment between the systems. Here in the network server management we must connect the
servers [5]. First there must be request from the home server to the destination, and then the
destination must accept the request. Then only the next process is started. Then the destination must
send you the acknowledgement. After receiving the acknowledgement the source will now ask the data
whatever they need. Then the source request for data access will be accepted by the destination server
for the data. After reading the data request from the source the destination will ready the data for the
source. After receiving the request the source will accept the data from the destination. Once the data is
transferred continuously from the destination then at one point they will end the data transfer. In this
time source will send a stop request for the server. Hence the data transfer will be stopped. This process
will take place with the help of DNS servers with the requests through the network servers [6]. The DNS
servers will communicate with the other DNS servers and the client pc also. In some environment the
DNS servers will not communicate with the clients but only communicate with the DNS servers only. The
IP address is always necessary for the communication of the data in any DNS server based
communication.
Step 3: Set up a DHCP server to acquire IP address
DHCP is abbreviated as dynamic host configuration protocol. TheDHCP is a type of network protocol
which will allows the servers to automatically assign the IP of the clients, source, destination or any IP
address which is required for some work action. TheIP address will be in the form of number and will
have to follow some rules for the establishment of connection. These IP address will vary from time to
time and from the system to system, network to network. Hence the obtaining of the IP address
automatically is very crucial. The manual process of obtaining such IP address is not possible in all cases.
It will be tedious process.
servers [5]. First there must be request from the home server to the destination, and then the
destination must accept the request. Then only the next process is started. Then the destination must
send you the acknowledgement. After receiving the acknowledgement the source will now ask the data
whatever they need. Then the source request for data access will be accepted by the destination server
for the data. After reading the data request from the source the destination will ready the data for the
source. After receiving the request the source will accept the data from the destination. Once the data is
transferred continuously from the destination then at one point they will end the data transfer. In this
time source will send a stop request for the server. Hence the data transfer will be stopped. This process
will take place with the help of DNS servers with the requests through the network servers [6]. The DNS
servers will communicate with the other DNS servers and the client pc also. In some environment the
DNS servers will not communicate with the clients but only communicate with the DNS servers only. The
IP address is always necessary for the communication of the data in any DNS server based
communication.
Step 3: Set up a DHCP server to acquire IP address
DHCP is abbreviated as dynamic host configuration protocol. TheDHCP is a type of network protocol
which will allows the servers to automatically assign the IP of the clients, source, destination or any IP
address which is required for some work action. TheIP address will be in the form of number and will
have to follow some rules for the establishment of connection. These IP address will vary from time to
time and from the system to system, network to network. Hence the obtaining of the IP address
automatically is very crucial. The manual process of obtaining such IP address is not possible in all cases.
It will be tedious process.

The DHCP client will initial ask for the IP lease request for the DHCP servers. Then the DHCP servers must
offer the lease. If they are not offering the lease it is not possible for the data to establish. Then after the
IP lease offer the next process is associated with the IP lease selection. The IP lease selection will be
initiated with the DHCP client. Then after DHCP client request the DHCP server must receive the IP lease
selection request. Once the DHCP server got the request from the DHCP client it will give the IP lease
acknowledgement to the DHCP client. The DHCP client will receive the IP lease acknowledgement. The IP
process must be very quick and automatic or else the data will flow very slowly. There are three types of
allocation. The first one is the dynamic allocation, the second one is the automatic allocation and the
third and final one is the manual allocation. The dynamic allocation of IP address is varied according to
the situation. In this it may done automatically or by manually. In the automatic process the IP address is
allocated automatically [4]. The least preferred is manual process of establishing the IP address. These
are the important IP allocations in the DHCP.
Step 4: Create a mirror server for the backup purpose in case of failure.
The mirror servers are one of the backup kinds of servers always necessary for the data storage. The
accessing data from the servers have to be back up or stored for various uses like reference or proof. If
the server suddenly fails to work or crash the data then entire process will be affected. The data must be
stored in the alternate servers for the safety. The alternate servers are known as the mirror servers, the
mirror servers are very essential in the data safety. The data in the main server and the mirror servers
are stored simultaneously. There should not be much time delay in the storage. The mirror server must
have the same configuration of the main server as the data is replicated. Mirror server is also known as
slave servers. There are some types of mirror server software which will tell the identical nature of the
master server and the mirror servers.
offer the lease. If they are not offering the lease it is not possible for the data to establish. Then after the
IP lease offer the next process is associated with the IP lease selection. The IP lease selection will be
initiated with the DHCP client. Then after DHCP client request the DHCP server must receive the IP lease
selection request. Once the DHCP server got the request from the DHCP client it will give the IP lease
acknowledgement to the DHCP client. The DHCP client will receive the IP lease acknowledgement. The IP
process must be very quick and automatic or else the data will flow very slowly. There are three types of
allocation. The first one is the dynamic allocation, the second one is the automatic allocation and the
third and final one is the manual allocation. The dynamic allocation of IP address is varied according to
the situation. In this it may done automatically or by manually. In the automatic process the IP address is
allocated automatically [4]. The least preferred is manual process of establishing the IP address. These
are the important IP allocations in the DHCP.
Step 4: Create a mirror server for the backup purpose in case of failure.
The mirror servers are one of the backup kinds of servers always necessary for the data storage. The
accessing data from the servers have to be back up or stored for various uses like reference or proof. If
the server suddenly fails to work or crash the data then entire process will be affected. The data must be
stored in the alternate servers for the safety. The alternate servers are known as the mirror servers, the
mirror servers are very essential in the data safety. The data in the main server and the mirror servers
are stored simultaneously. There should not be much time delay in the storage. The mirror server must
have the same configuration of the main server as the data is replicated. Mirror server is also known as
slave servers. There are some types of mirror server software which will tell the identical nature of the
master server and the mirror servers.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Running Performance test on the server
Proper labeled Screenshots from implementation
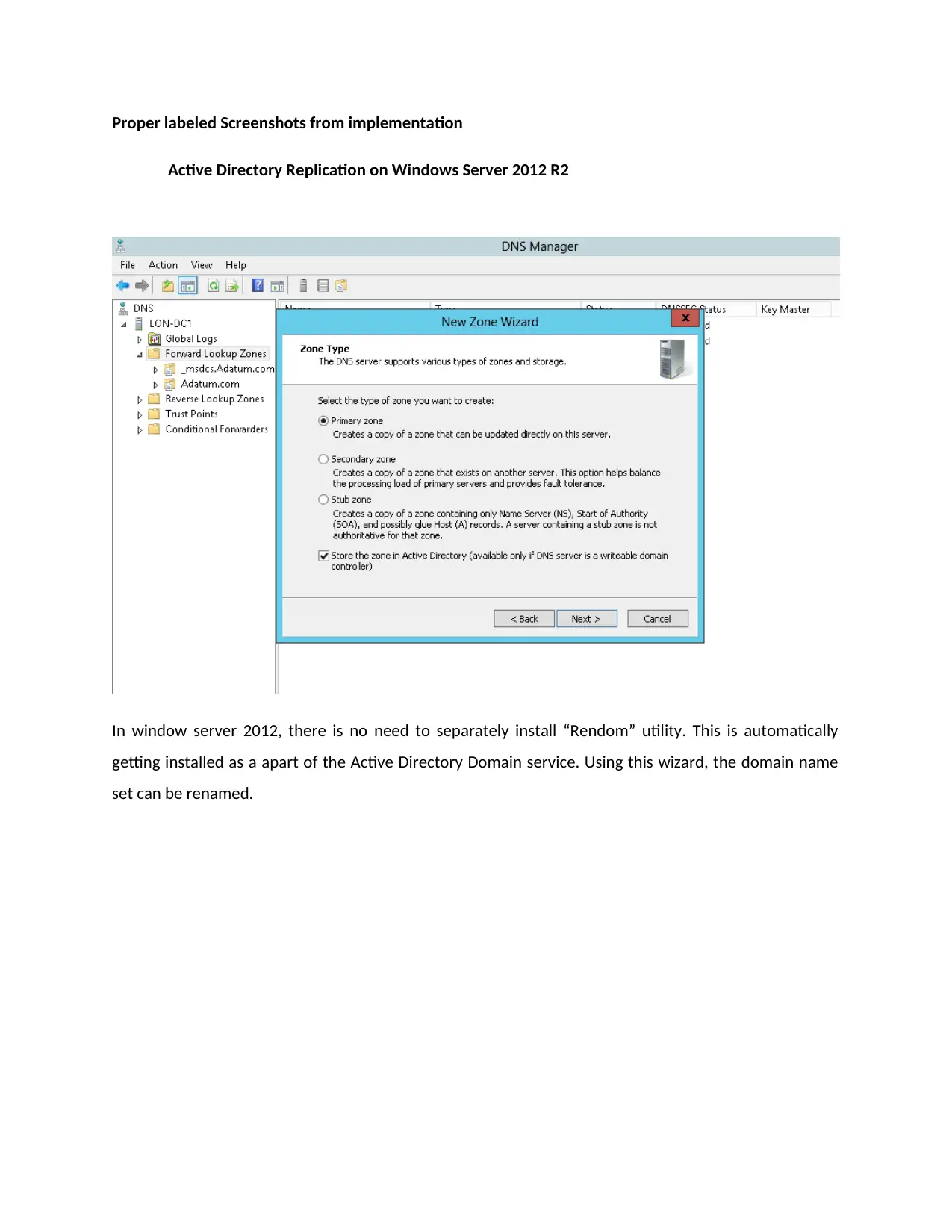
Active Directory Replication on Windows Server 2012 R2
In window server 2012, there is no need to separately install “Rendom” utility. This is automatically
getting installed as a apart of the Active Directory Domain service. Using this wizard, the domain name
set can be renamed.
Active Directory Replication on Windows Server 2012 R2
In window server 2012, there is no need to separately install “Rendom” utility. This is automatically
getting installed as a apart of the Active Directory Domain service. Using this wizard, the domain name
set can be renamed.
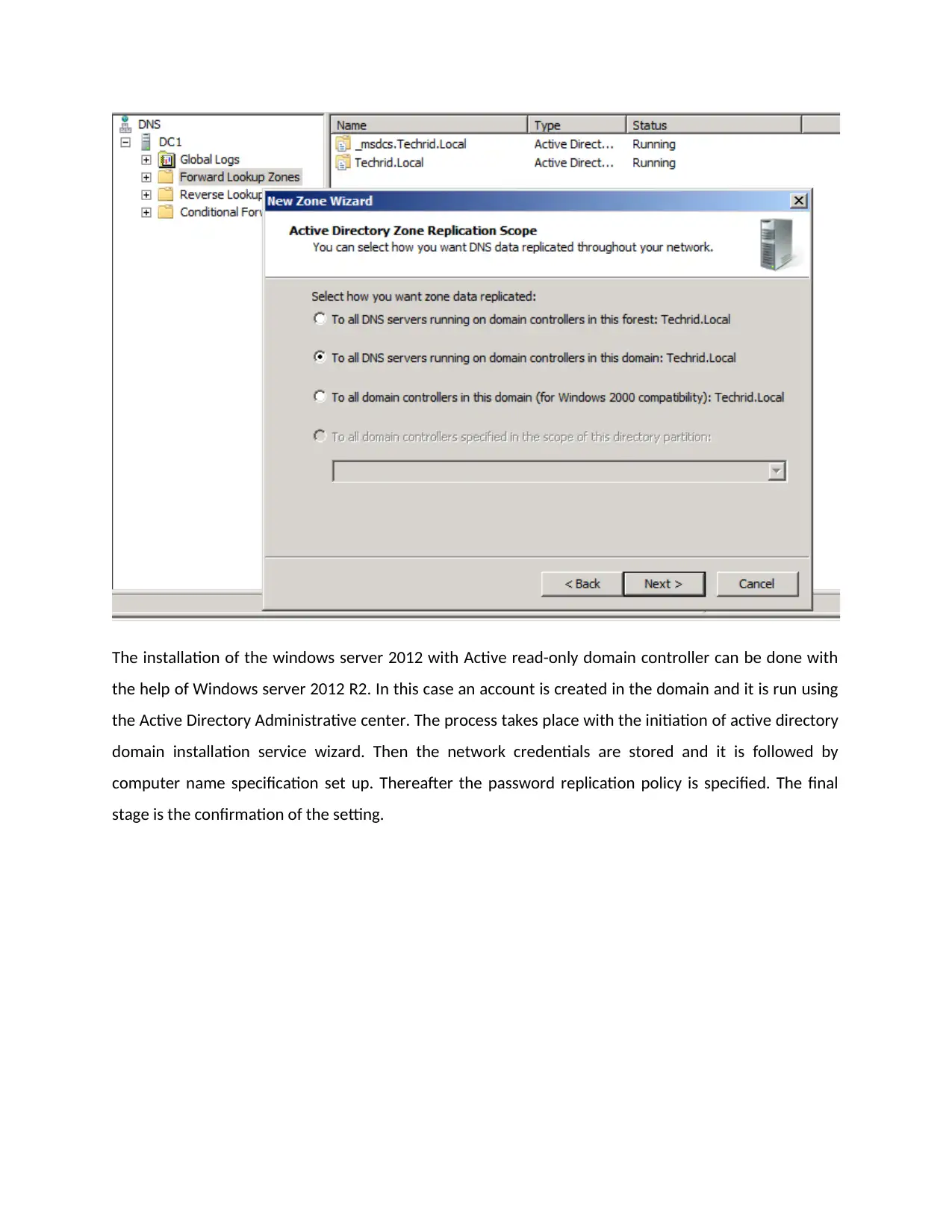
The installation of the windows server 2012 with Active read-only domain controller can be done with
the help of Windows server 2012 R2. In this case an account is created in the domain and it is run using
the Active Directory Administrative center. The process takes place with the initiation of active directory
domain installation service wizard. Then the network credentials are stored and it is followed by
computer name specification set up. Thereafter the password replication policy is specified. The final
stage is the confirmation of the setting.
the help of Windows server 2012 R2. In this case an account is created in the domain and it is run using
the Active Directory Administrative center. The process takes place with the initiation of active directory
domain installation service wizard. Then the network credentials are stored and it is followed by
computer name specification set up. Thereafter the password replication policy is specified. The final
stage is the confirmation of the setting.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
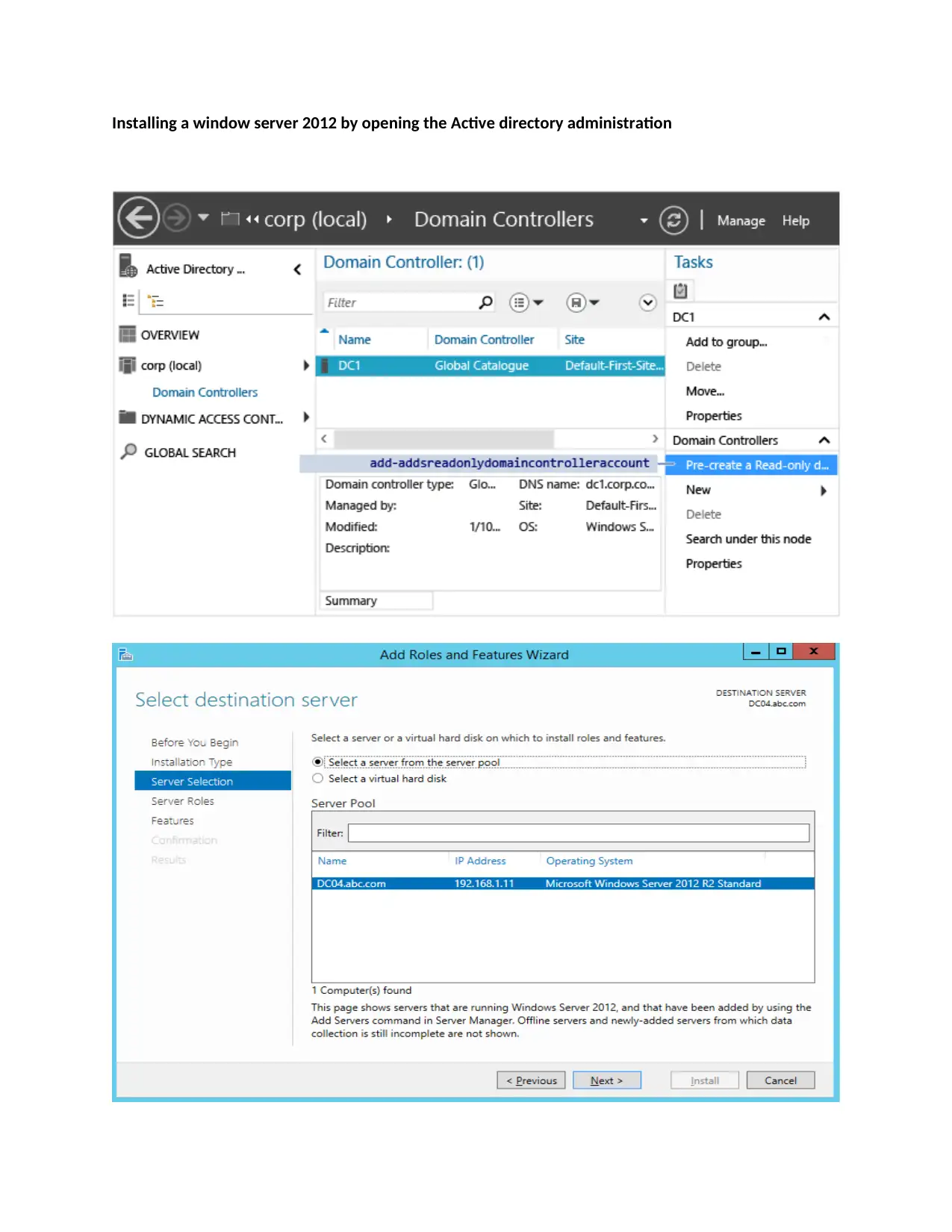
Installing a window server 2012 by opening the Active directory administration
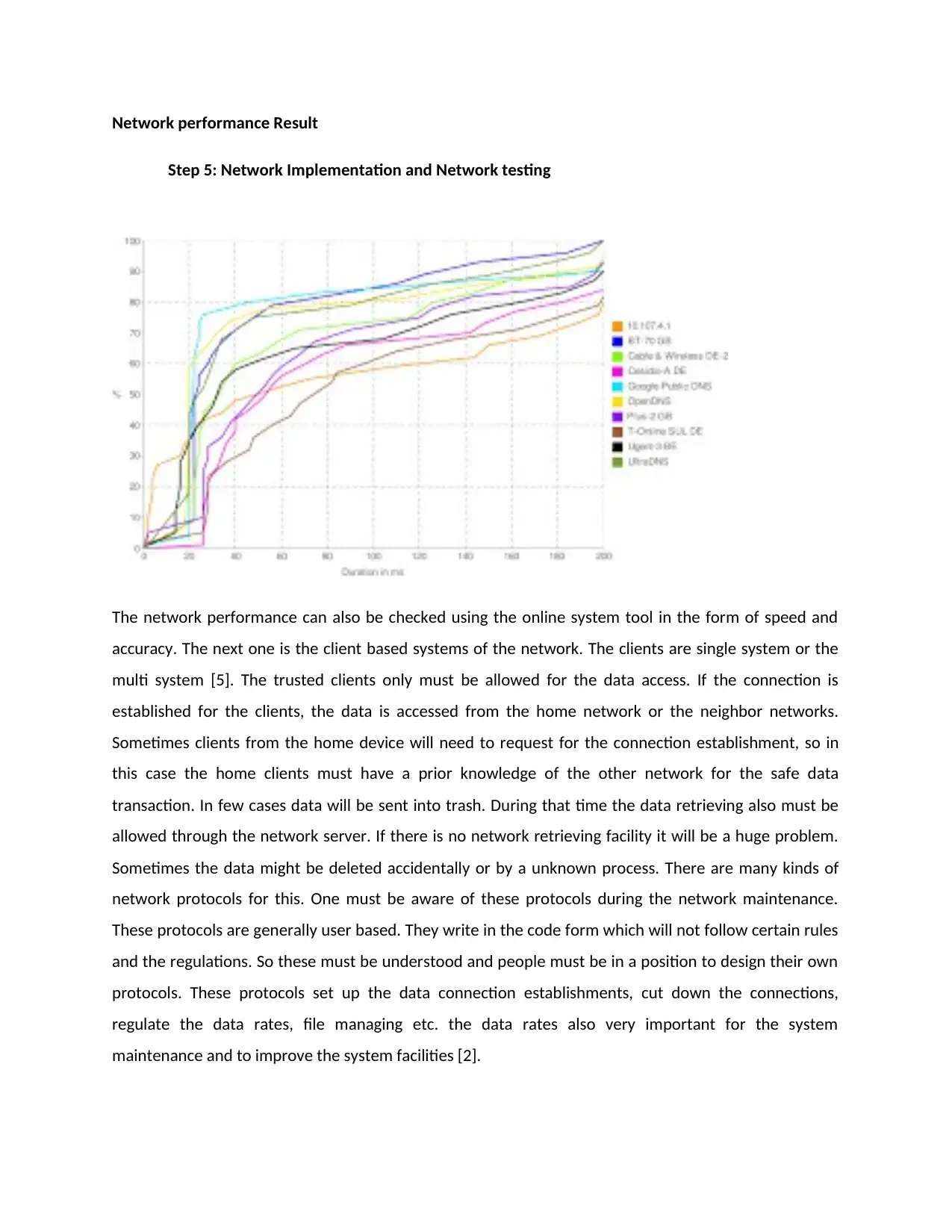
Network performance Result
Step 5: Network Implementation and Network testing
The network performance can also be checked using the online system tool in the form of speed and
accuracy. The next one is the client based systems of the network. The clients are single system or the
multi system [5]. The trusted clients only must be allowed for the data access. If the connection is
established for the clients, the data is accessed from the home network or the neighbor networks.
Sometimes clients from the home device will need to request for the connection establishment, so in
this case the home clients must have a prior knowledge of the other network for the safe data
transaction. In few cases data will be sent into trash. During that time the data retrieving also must be
allowed through the network server. If there is no network retrieving facility it will be a huge problem.
Sometimes the data might be deleted accidentally or by a unknown process. There are many kinds of
network protocols for this. One must be aware of these protocols during the network maintenance.
These protocols are generally user based. They write in the code form which will not follow certain rules
and the regulations. So these must be understood and people must be in a position to design their own
protocols. These protocols set up the data connection establishments, cut down the connections,
regulate the data rates, file managing etc. the data rates also very important for the system
maintenance and to improve the system facilities [2].
Step 5: Network Implementation and Network testing
The network performance can also be checked using the online system tool in the form of speed and
accuracy. The next one is the client based systems of the network. The clients are single system or the
multi system [5]. The trusted clients only must be allowed for the data access. If the connection is
established for the clients, the data is accessed from the home network or the neighbor networks.
Sometimes clients from the home device will need to request for the connection establishment, so in
this case the home clients must have a prior knowledge of the other network for the safe data
transaction. In few cases data will be sent into trash. During that time the data retrieving also must be
allowed through the network server. If there is no network retrieving facility it will be a huge problem.
Sometimes the data might be deleted accidentally or by a unknown process. There are many kinds of
network protocols for this. One must be aware of these protocols during the network maintenance.
These protocols are generally user based. They write in the code form which will not follow certain rules
and the regulations. So these must be understood and people must be in a position to design their own
protocols. These protocols set up the data connection establishments, cut down the connections,
regulate the data rates, file managing etc. the data rates also very important for the system
maintenance and to improve the system facilities [2].

Conclusion
The network design is done by keeping the above factors to improve the functionality of the network
server. The data in the home network is accessed by the external servers or the computers inside the
home network [3]. One has to maintain the data log or the data access by the systems. This will help us
to where the data is distributed and is the data is moving the right direction or not. The destination
address also can be noted in the server because of its log register in the server. If the destination is came
to know as an untrusted one then the problems will arise. So the connection between the untrusted
systems will be cut down. The above process will generally take place in the online environment.
The network design is done by keeping the above factors to improve the functionality of the network
server. The data in the home network is accessed by the external servers or the computers inside the
home network [3]. One has to maintain the data log or the data access by the systems. This will help us
to where the data is distributed and is the data is moving the right direction or not. The destination
address also can be noted in the server because of its log register in the server. If the destination is came
to know as an untrusted one then the problems will arise. So the connection between the untrusted
systems will be cut down. The above process will generally take place in the online environment.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Reference
[1] S.Alabady, “Design and implementation of a network security model for cooperative network.”
In international Arab journal of e-technology, 2009.
[2] Q. Ali and S. Alabady, “Design and implementation of a secured remotely administrated
network.” In proceedings international ARAB conference on information technology, ACIT, 2007.
[3] S.bukhari, S. rehmani and S. Siraj, ieeexplore. IEEE, (2015, 30 november) [online]. available:
http://ieeexplore.ieee.org.mit.idm.oclc.org/xpl/articledetails.jsp?
arnumber=7339651&querytext=wireless%20networks&newsearch=true. [accessed 2015].
[4] R.C. Meurant, “Providing every student with an ipad as a means of helping develop Koreanelf
digital literacy.” Sixth international conference on networked computing and advanced
information management (ncm), pp.242- 247, 2010.
[5] C, Teng and R. helps, “Mobile application development: essential new directions for it.”
Seventhinternational conference on information technology, pp.471.475, 2010.
[6] W. Yeh, “A marketing research of new digital readers and ipad in comprehensive aspect.”
International conference on computer application and system modeling (ICC SAM 2010), pp.320-
323, 2010.
[1] S.Alabady, “Design and implementation of a network security model for cooperative network.”
In international Arab journal of e-technology, 2009.
[2] Q. Ali and S. Alabady, “Design and implementation of a secured remotely administrated
network.” In proceedings international ARAB conference on information technology, ACIT, 2007.
[3] S.bukhari, S. rehmani and S. Siraj, ieeexplore. IEEE, (2015, 30 november) [online]. available:
http://ieeexplore.ieee.org.mit.idm.oclc.org/xpl/articledetails.jsp?
arnumber=7339651&querytext=wireless%20networks&newsearch=true. [accessed 2015].
[4] R.C. Meurant, “Providing every student with an ipad as a means of helping develop Koreanelf
digital literacy.” Sixth international conference on networked computing and advanced
information management (ncm), pp.242- 247, 2010.
[5] C, Teng and R. helps, “Mobile application development: essential new directions for it.”
Seventhinternational conference on information technology, pp.471.475, 2010.
[6] W. Yeh, “A marketing research of new digital readers and ipad in comprehensive aspect.”
International conference on computer application and system modeling (ICC SAM 2010), pp.320-
323, 2010.
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





