Comparison of Server Availability Monitoring Tools
VerifiedAdded on 2023/02/01
|31
|3202
|26
AI Summary
This report compares different server availability monitoring tools like Nagios Core, Ganglia, Spiceworks, CollectD, Cacti, Icinga, Zabbix, OpenNMS, and WhatsUp Gold. It discusses their features and provides screenshots of disk usage, CPU monitoring, process monitoring, bandwidth monitoring, and resource monitoring.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SYSTEM MANAGEMENT
System Management
Name of the Student
Name of the University
Author Note
System Management
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1SYSTEM MANAGEMENT
Report Layout
Introduction:........................................................................................................................... 2
Comparison:........................................................................................................................... 2
(1) Nagios Core:................................................................................................................. 2
(2) Ganglia:......................................................................................................................... 5
(3) Spiceworks:................................................................................................................... 8
(4) CollectD:...................................................................................................................... 11
(5) Cacti:........................................................................................................................... 13
(6) Icinga:.......................................................................................................................... 16
(7) Zabbix:........................................................................................................................ 21
(8) OpenNMS:................................................................................................................... 24
(9) WhatsUp Gold:............................................................................................................ 26
Evaluation:........................................................................................................................... 29
Identification and Analysis:...................................................................................................29
Propose:............................................................................................................................... 29
Conclusion:.......................................................................................................................... 29
References:.......................................................................................................................... 30
Report Layout
Introduction:........................................................................................................................... 2
Comparison:........................................................................................................................... 2
(1) Nagios Core:................................................................................................................. 2
(2) Ganglia:......................................................................................................................... 5
(3) Spiceworks:................................................................................................................... 8
(4) CollectD:...................................................................................................................... 11
(5) Cacti:........................................................................................................................... 13
(6) Icinga:.......................................................................................................................... 16
(7) Zabbix:........................................................................................................................ 21
(8) OpenNMS:................................................................................................................... 24
(9) WhatsUp Gold:............................................................................................................ 26
Evaluation:........................................................................................................................... 29
Identification and Analysis:...................................................................................................29
Propose:............................................................................................................................... 29
Conclusion:.......................................................................................................................... 29
References:.......................................................................................................................... 30

2SYSTEM MANAGEMENT
Introduction:
Monitoring the availability of the servers is very much important concept for the
organizations as this is one of the core for their day to day operations. Though this is very
much important still the organizations faces various of issues as there is a metrics related
challenges which includes availability of the services, hardware and applications [1]. It is also
very much important for the organization to understand which operations requires which
resources and how much resource is required by those processes.
Thus in this paper various of server availability monitoring tools is leveraged to check
the performance in terms of CPU monitoring, Process Monitoring, Disk Usage, Resource
Monitoring, Bandwidth Monitoring and Overall availability. Also, the server availability
monitoring architecture and solution will be presented to avoid data vulnerability.
Comparison:
In this case nine types of server availability monitoring tools will be discussed which
are the following:
Nagios Core
Ganglia
CollectD
Spiceworks
Cacti
Zabbbix
Icinga
OpenNMS
WhatsUp Gold
(1) Nagios Core:
This is an open serving checking tool. This tool is connected with the entire server for
the monitoring purpose.
Introduction:
Monitoring the availability of the servers is very much important concept for the
organizations as this is one of the core for their day to day operations. Though this is very
much important still the organizations faces various of issues as there is a metrics related
challenges which includes availability of the services, hardware and applications [1]. It is also
very much important for the organization to understand which operations requires which
resources and how much resource is required by those processes.
Thus in this paper various of server availability monitoring tools is leveraged to check
the performance in terms of CPU monitoring, Process Monitoring, Disk Usage, Resource
Monitoring, Bandwidth Monitoring and Overall availability. Also, the server availability
monitoring architecture and solution will be presented to avoid data vulnerability.
Comparison:
In this case nine types of server availability monitoring tools will be discussed which
are the following:
Nagios Core
Ganglia
CollectD
Spiceworks
Cacti
Zabbbix
Icinga
OpenNMS
WhatsUp Gold
(1) Nagios Core:
This is an open serving checking tool. This tool is connected with the entire server for
the monitoring purpose.
3SYSTEM MANAGEMENT
(Figure 1: Disk Usage of Nagios Core)
(Source: Created by the Author)
Disk usage is determined in the above screenshot of Nagios core.
(Figure 2: Bandwidth Monitoring of Nagios Core)
(Source: Created by the Author)
Both the read and write bandwidth has been delivered through the screenshot and
for that Nagios Core has been selected.
(Figure 1: Disk Usage of Nagios Core)
(Source: Created by the Author)
Disk usage is determined in the above screenshot of Nagios core.
(Figure 2: Bandwidth Monitoring of Nagios Core)
(Source: Created by the Author)
Both the read and write bandwidth has been delivered through the screenshot and
for that Nagios Core has been selected.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4SYSTEM MANAGEMENT
(Figure 3: Resource Monitoring of Nagios Core)
(Source: Created by the Author)
On the above screenshot resources of the system has been identified and monitored.
(Figure 4: Process Monitoring of Nagios Core)
(Source: Created by the Author)
(Figure 3: Resource Monitoring of Nagios Core)
(Source: Created by the Author)
On the above screenshot resources of the system has been identified and monitored.
(Figure 4: Process Monitoring of Nagios Core)
(Source: Created by the Author)
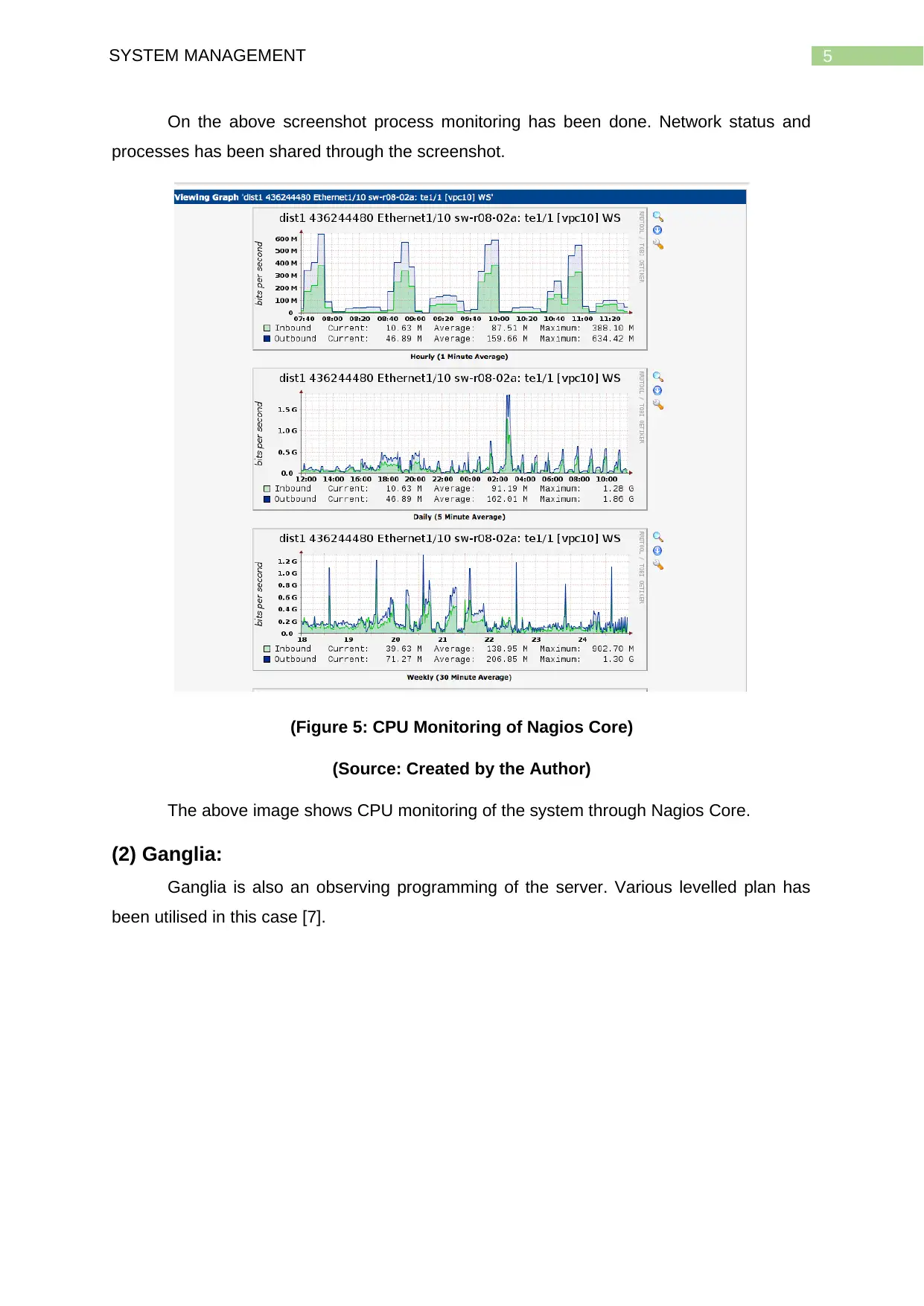
5SYSTEM MANAGEMENT
On the above screenshot process monitoring has been done. Network status and
processes has been shared through the screenshot.
(Figure 5: CPU Monitoring of Nagios Core)
(Source: Created by the Author)
The above image shows CPU monitoring of the system through Nagios Core.
(2) Ganglia:
Ganglia is also an observing programming of the server. Various levelled plan has
been utilised in this case [7].
On the above screenshot process monitoring has been done. Network status and
processes has been shared through the screenshot.
(Figure 5: CPU Monitoring of Nagios Core)
(Source: Created by the Author)
The above image shows CPU monitoring of the system through Nagios Core.
(2) Ganglia:
Ganglia is also an observing programming of the server. Various levelled plan has
been utilised in this case [7].
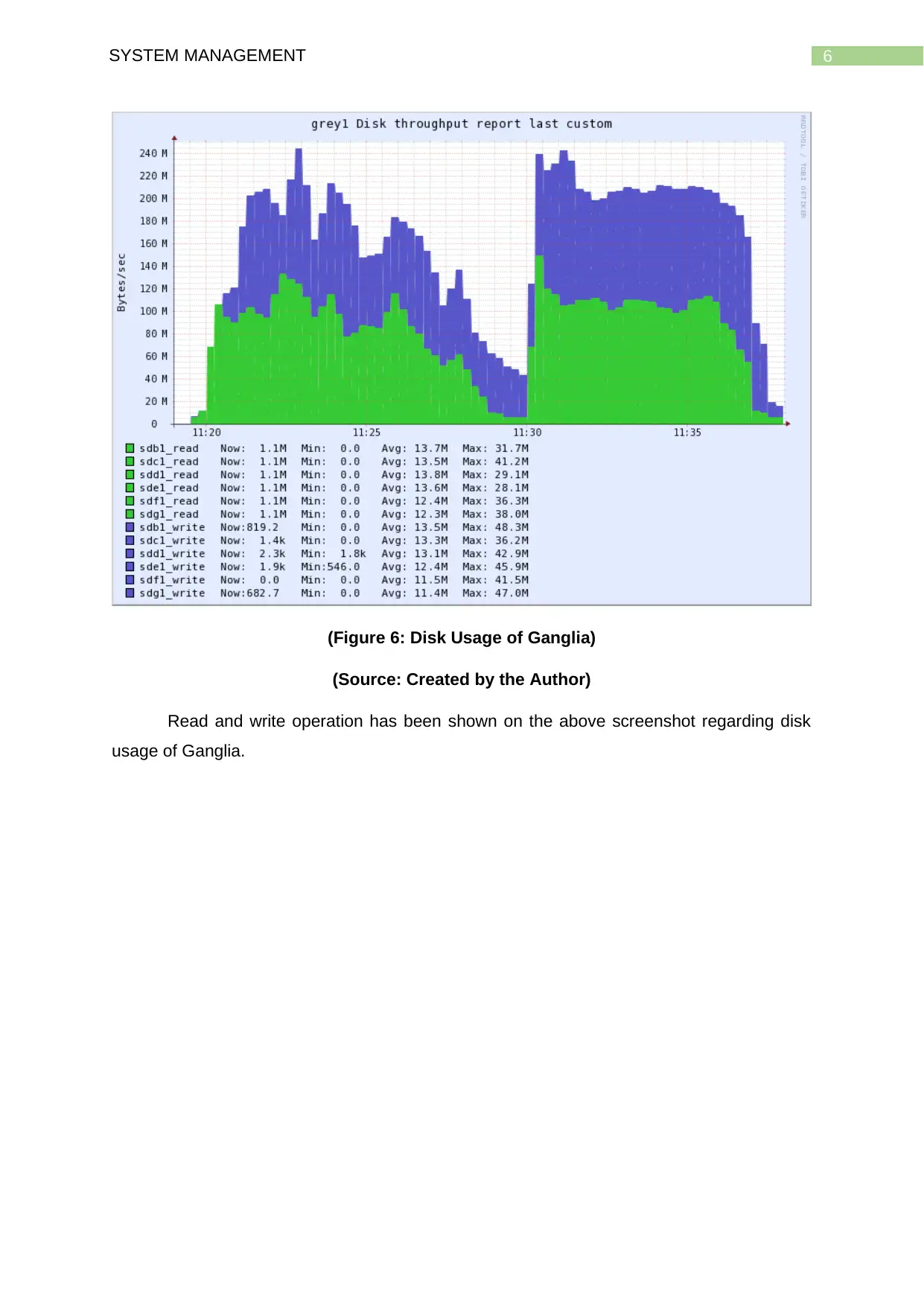
6SYSTEM MANAGEMENT
(Figure 6: Disk Usage of Ganglia)
(Source: Created by the Author)
Read and write operation has been shown on the above screenshot regarding disk
usage of Ganglia.
(Figure 6: Disk Usage of Ganglia)
(Source: Created by the Author)
Read and write operation has been shown on the above screenshot regarding disk
usage of Ganglia.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
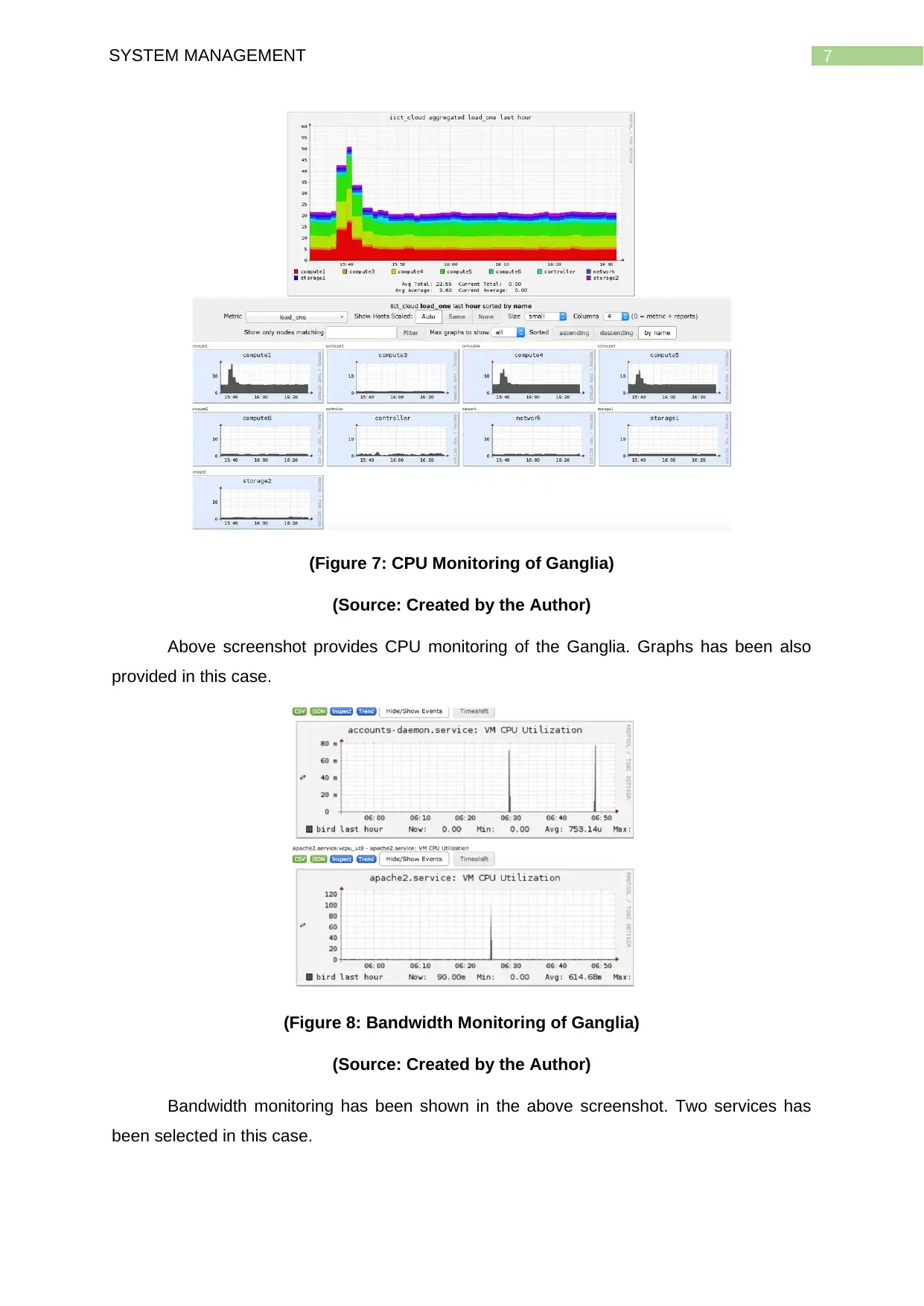
7SYSTEM MANAGEMENT
(Figure 7: CPU Monitoring of Ganglia)
(Source: Created by the Author)
Above screenshot provides CPU monitoring of the Ganglia. Graphs has been also
provided in this case.
(Figure 8: Bandwidth Monitoring of Ganglia)
(Source: Created by the Author)
Bandwidth monitoring has been shown in the above screenshot. Two services has
been selected in this case.
(Figure 7: CPU Monitoring of Ganglia)
(Source: Created by the Author)
Above screenshot provides CPU monitoring of the Ganglia. Graphs has been also
provided in this case.
(Figure 8: Bandwidth Monitoring of Ganglia)
(Source: Created by the Author)
Bandwidth monitoring has been shown in the above screenshot. Two services has
been selected in this case.
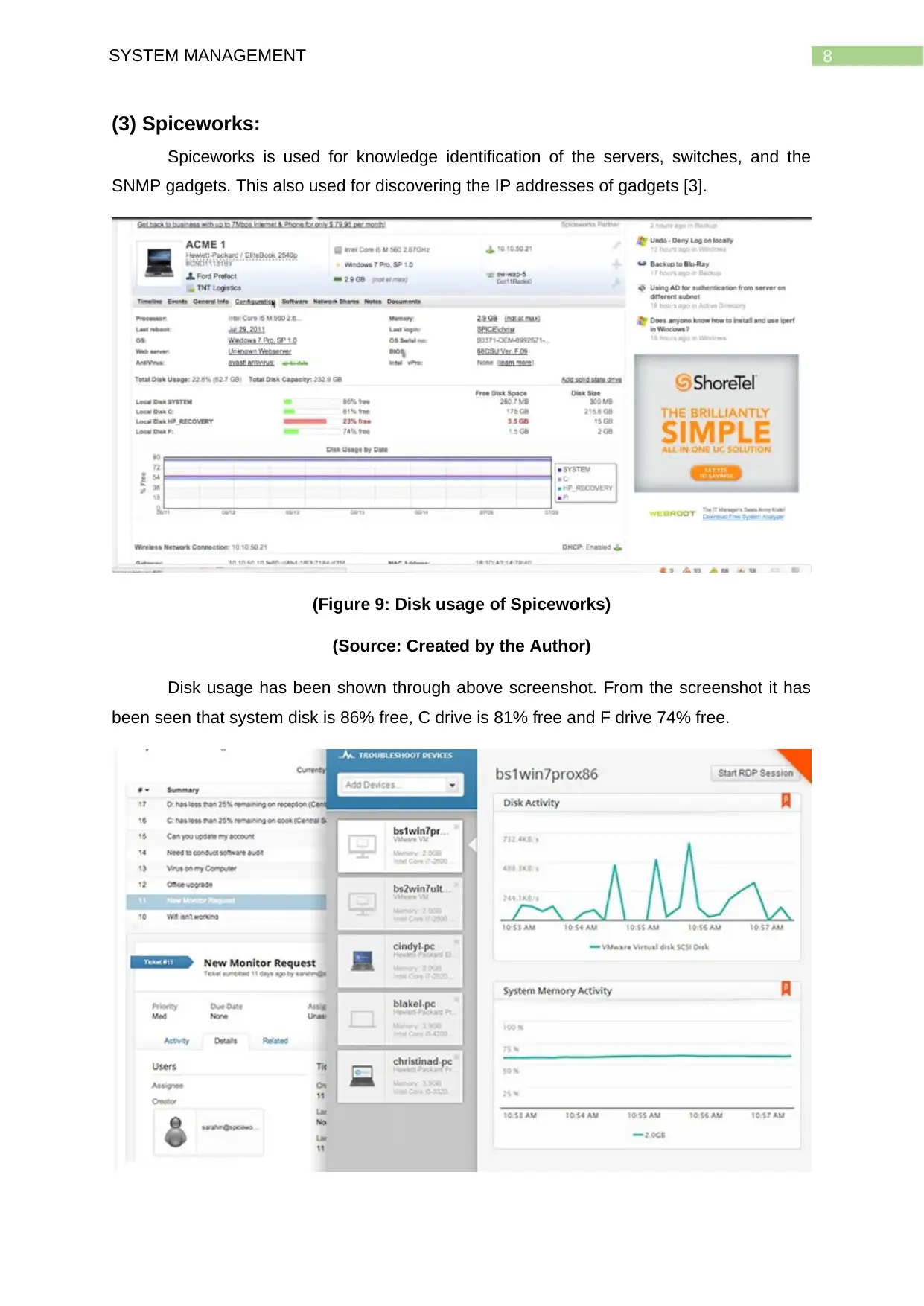
8SYSTEM MANAGEMENT
(3) Spiceworks:
Spiceworks is used for knowledge identification of the servers, switches, and the
SNMP gadgets. This also used for discovering the IP addresses of gadgets [3].
(Figure 9: Disk usage of Spiceworks)
(Source: Created by the Author)
Disk usage has been shown through above screenshot. From the screenshot it has
been seen that system disk is 86% free, C drive is 81% free and F drive 74% free.
(3) Spiceworks:
Spiceworks is used for knowledge identification of the servers, switches, and the
SNMP gadgets. This also used for discovering the IP addresses of gadgets [3].
(Figure 9: Disk usage of Spiceworks)
(Source: Created by the Author)
Disk usage has been shown through above screenshot. From the screenshot it has
been seen that system disk is 86% free, C drive is 81% free and F drive 74% free.
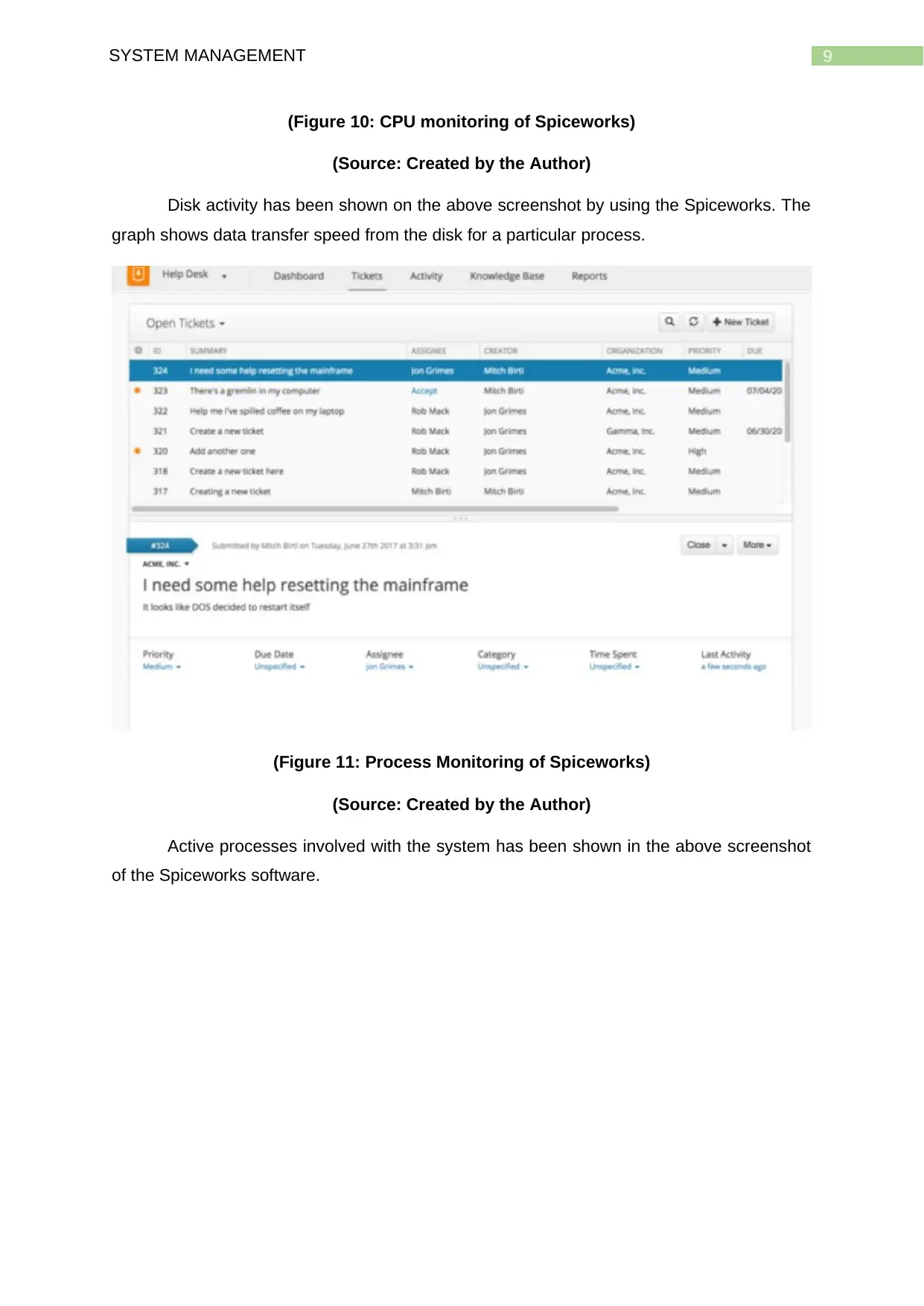
9SYSTEM MANAGEMENT
(Figure 10: CPU monitoring of Spiceworks)
(Source: Created by the Author)
Disk activity has been shown on the above screenshot by using the Spiceworks. The
graph shows data transfer speed from the disk for a particular process.
(Figure 11: Process Monitoring of Spiceworks)
(Source: Created by the Author)
Active processes involved with the system has been shown in the above screenshot
of the Spiceworks software.
(Figure 10: CPU monitoring of Spiceworks)
(Source: Created by the Author)
Disk activity has been shown on the above screenshot by using the Spiceworks. The
graph shows data transfer speed from the disk for a particular process.
(Figure 11: Process Monitoring of Spiceworks)
(Source: Created by the Author)
Active processes involved with the system has been shown in the above screenshot
of the Spiceworks software.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
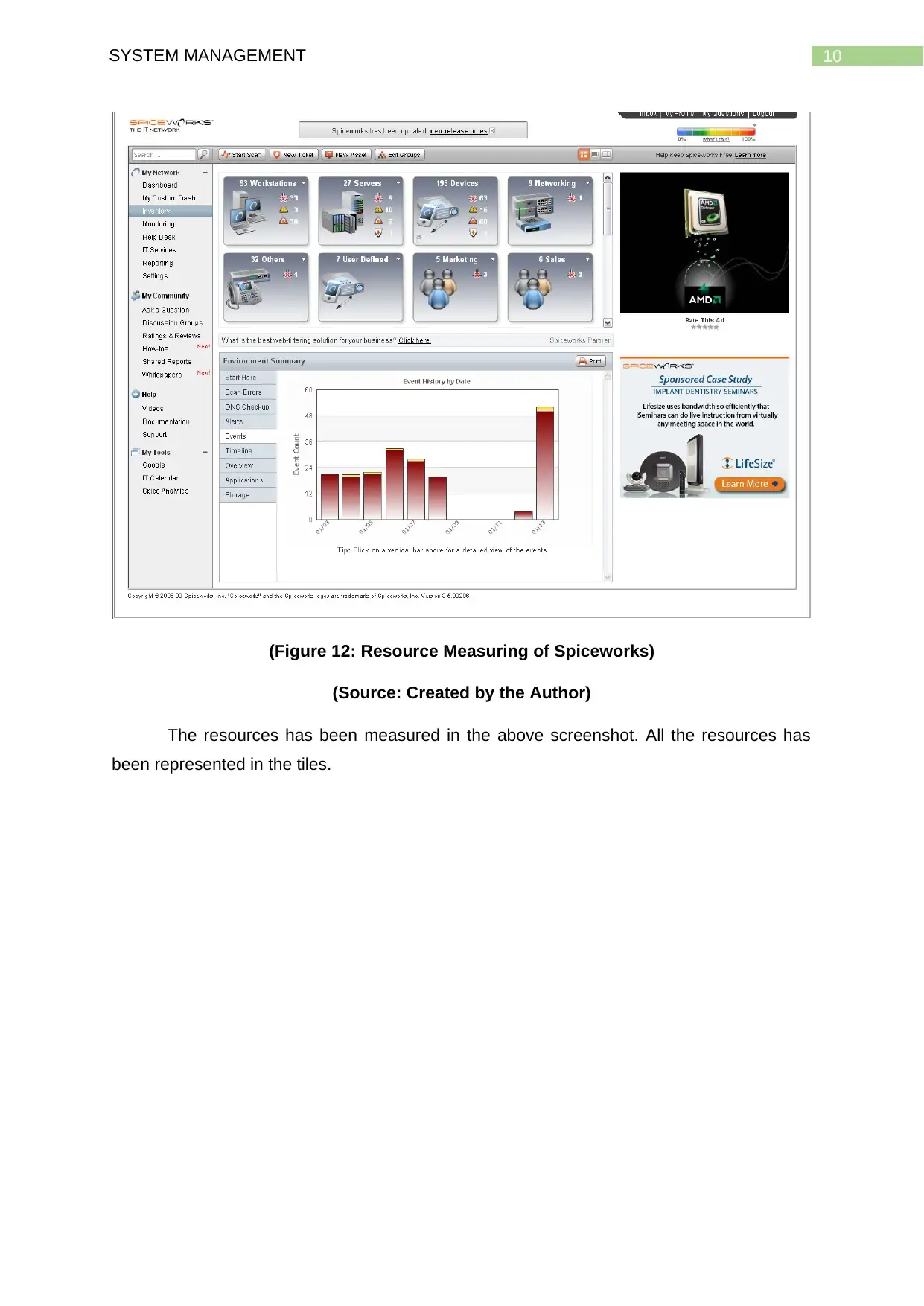
10SYSTEM MANAGEMENT
(Figure 12: Resource Measuring of Spiceworks)
(Source: Created by the Author)
The resources has been measured in the above screenshot. All the resources has
been represented in the tiles.
(Figure 12: Resource Measuring of Spiceworks)
(Source: Created by the Author)
The resources has been measured in the above screenshot. All the resources has
been represented in the tiles.
11SYSTEM MANAGEMENT
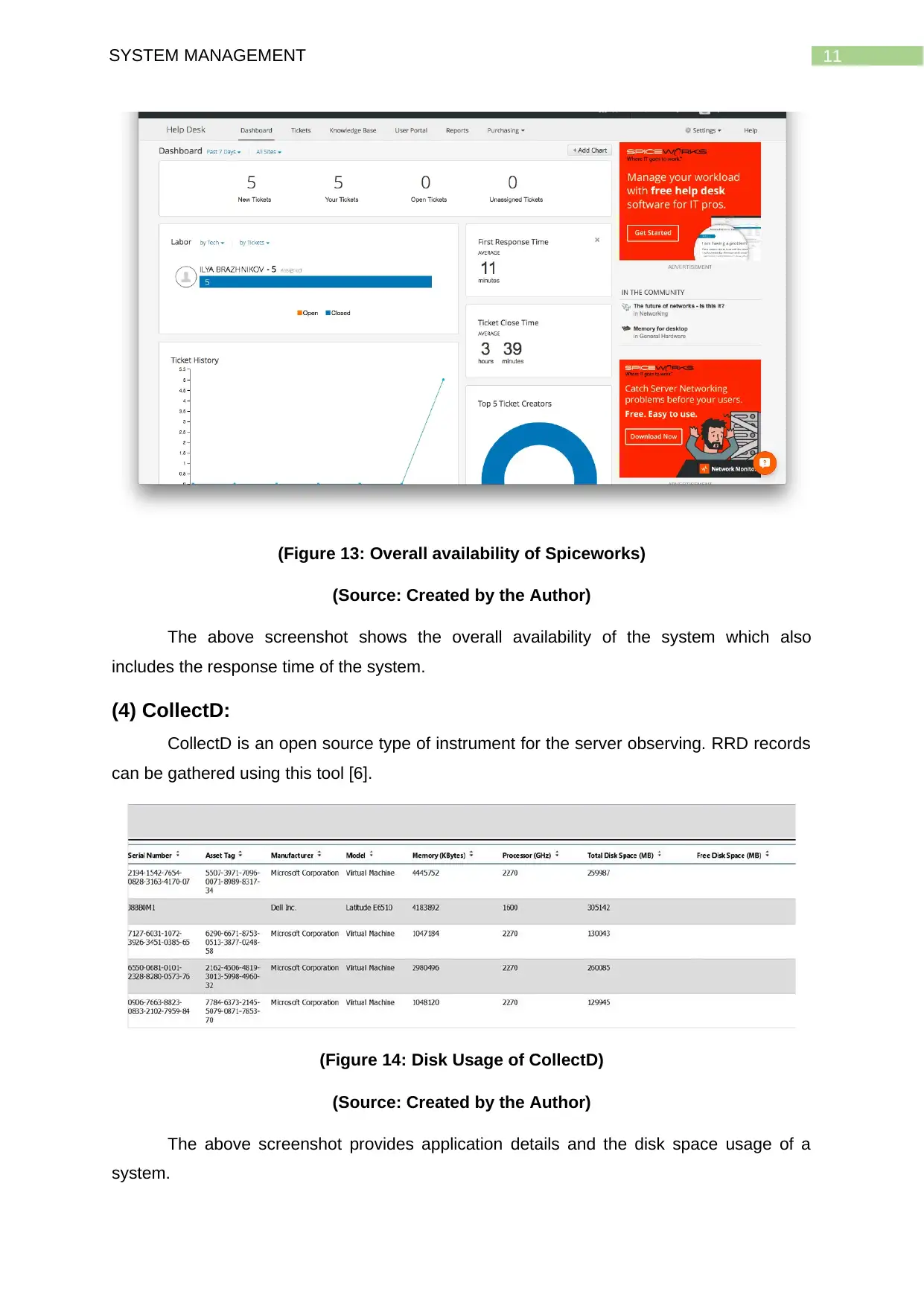
(Figure 13: Overall availability of Spiceworks)
(Source: Created by the Author)
The above screenshot shows the overall availability of the system which also
includes the response time of the system.
(4) CollectD:
CollectD is an open source type of instrument for the server observing. RRD records
can be gathered using this tool [6].
(Figure 14: Disk Usage of CollectD)
(Source: Created by the Author)
The above screenshot provides application details and the disk space usage of a
system.
(Figure 13: Overall availability of Spiceworks)
(Source: Created by the Author)
The above screenshot shows the overall availability of the system which also
includes the response time of the system.
(4) CollectD:
CollectD is an open source type of instrument for the server observing. RRD records
can be gathered using this tool [6].
(Figure 14: Disk Usage of CollectD)
(Source: Created by the Author)
The above screenshot provides application details and the disk space usage of a
system.
12SYSTEM MANAGEMENT
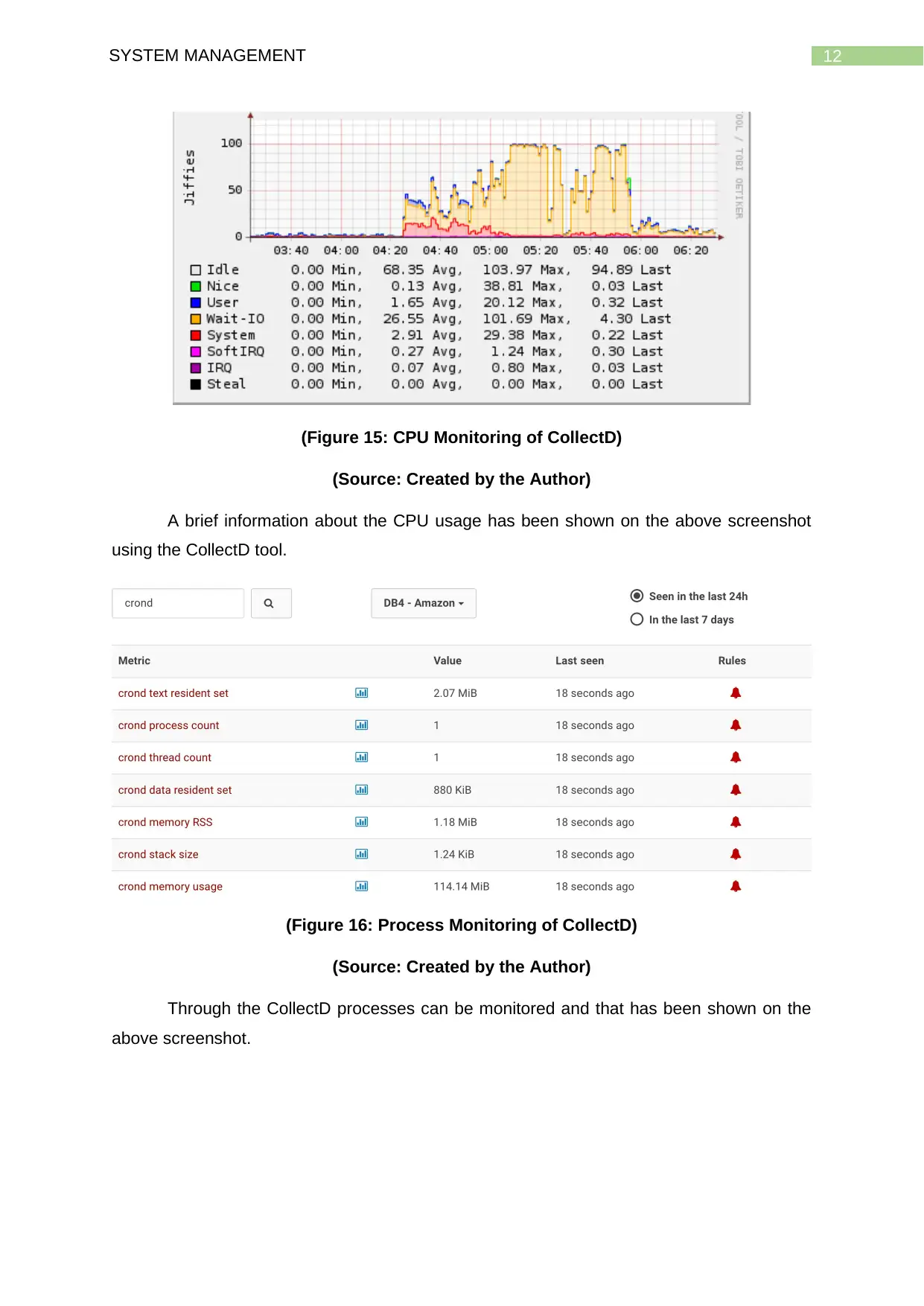
(Figure 15: CPU Monitoring of CollectD)
(Source: Created by the Author)
A brief information about the CPU usage has been shown on the above screenshot
using the CollectD tool.
(Figure 16: Process Monitoring of CollectD)
(Source: Created by the Author)
Through the CollectD processes can be monitored and that has been shown on the
above screenshot.
(Figure 15: CPU Monitoring of CollectD)
(Source: Created by the Author)
A brief information about the CPU usage has been shown on the above screenshot
using the CollectD tool.
(Figure 16: Process Monitoring of CollectD)
(Source: Created by the Author)
Through the CollectD processes can be monitored and that has been shown on the
above screenshot.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13SYSTEM MANAGEMENT
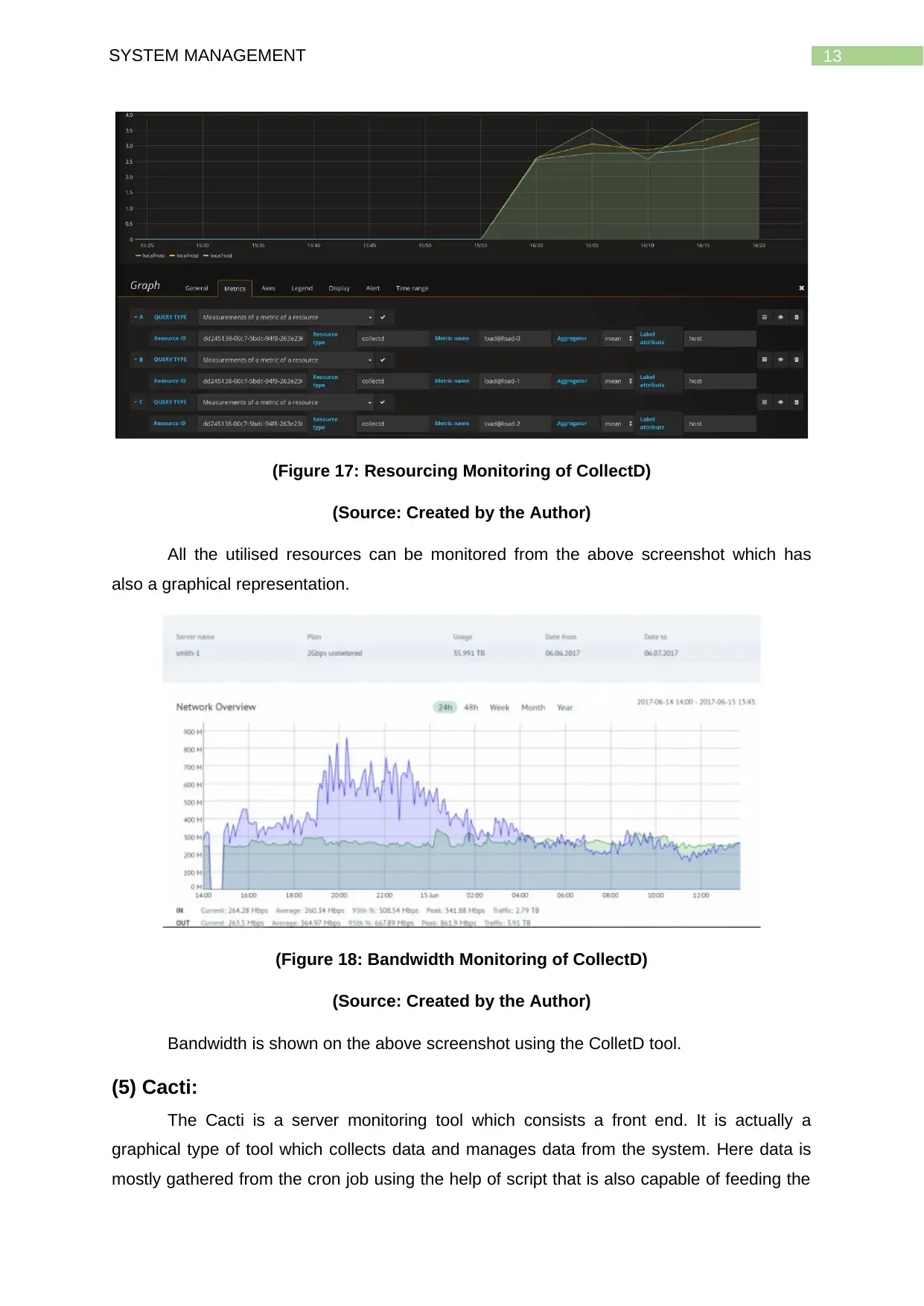
(Figure 17: Resourcing Monitoring of CollectD)
(Source: Created by the Author)
All the utilised resources can be monitored from the above screenshot which has
also a graphical representation.
(Figure 18: Bandwidth Monitoring of CollectD)
(Source: Created by the Author)
Bandwidth is shown on the above screenshot using the ColletD tool.
(5) Cacti:
The Cacti is a server monitoring tool which consists a front end. It is actually a
graphical type of tool which collects data and manages data from the system. Here data is
mostly gathered from the cron job using the help of script that is also capable of feeding the
(Figure 17: Resourcing Monitoring of CollectD)
(Source: Created by the Author)
All the utilised resources can be monitored from the above screenshot which has
also a graphical representation.
(Figure 18: Bandwidth Monitoring of CollectD)
(Source: Created by the Author)
Bandwidth is shown on the above screenshot using the ColletD tool.
(5) Cacti:
The Cacti is a server monitoring tool which consists a front end. It is actually a
graphical type of tool which collects data and manages data from the system. Here data is
mostly gathered from the cron job using the help of script that is also capable of feeding the
14SYSTEM MANAGEMENT
metrics [2]. This tool is capable of generating various of graphs from a particular database.
By using this software graphical results can be generated easily. In the following discussion
Cacti will be elaborated briefly with proper screenshots.
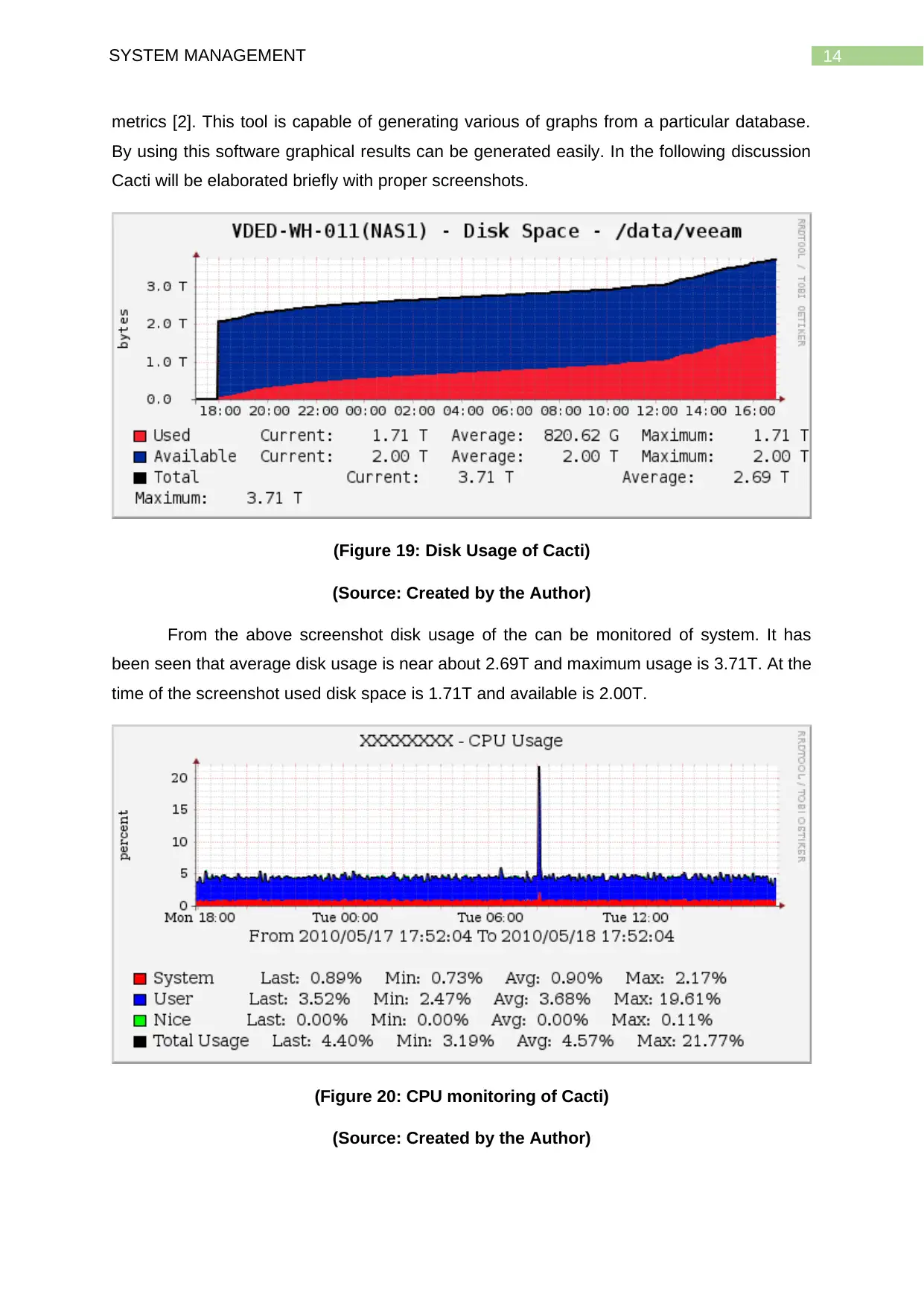
(Figure 19: Disk Usage of Cacti)
(Source: Created by the Author)
From the above screenshot disk usage of the can be monitored of system. It has
been seen that average disk usage is near about 2.69T and maximum usage is 3.71T. At the
time of the screenshot used disk space is 1.71T and available is 2.00T.
(Figure 20: CPU monitoring of Cacti)
(Source: Created by the Author)
metrics [2]. This tool is capable of generating various of graphs from a particular database.
By using this software graphical results can be generated easily. In the following discussion
Cacti will be elaborated briefly with proper screenshots.
(Figure 19: Disk Usage of Cacti)
(Source: Created by the Author)
From the above screenshot disk usage of the can be monitored of system. It has
been seen that average disk usage is near about 2.69T and maximum usage is 3.71T. At the
time of the screenshot used disk space is 1.71T and available is 2.00T.
(Figure 20: CPU monitoring of Cacti)
(Source: Created by the Author)
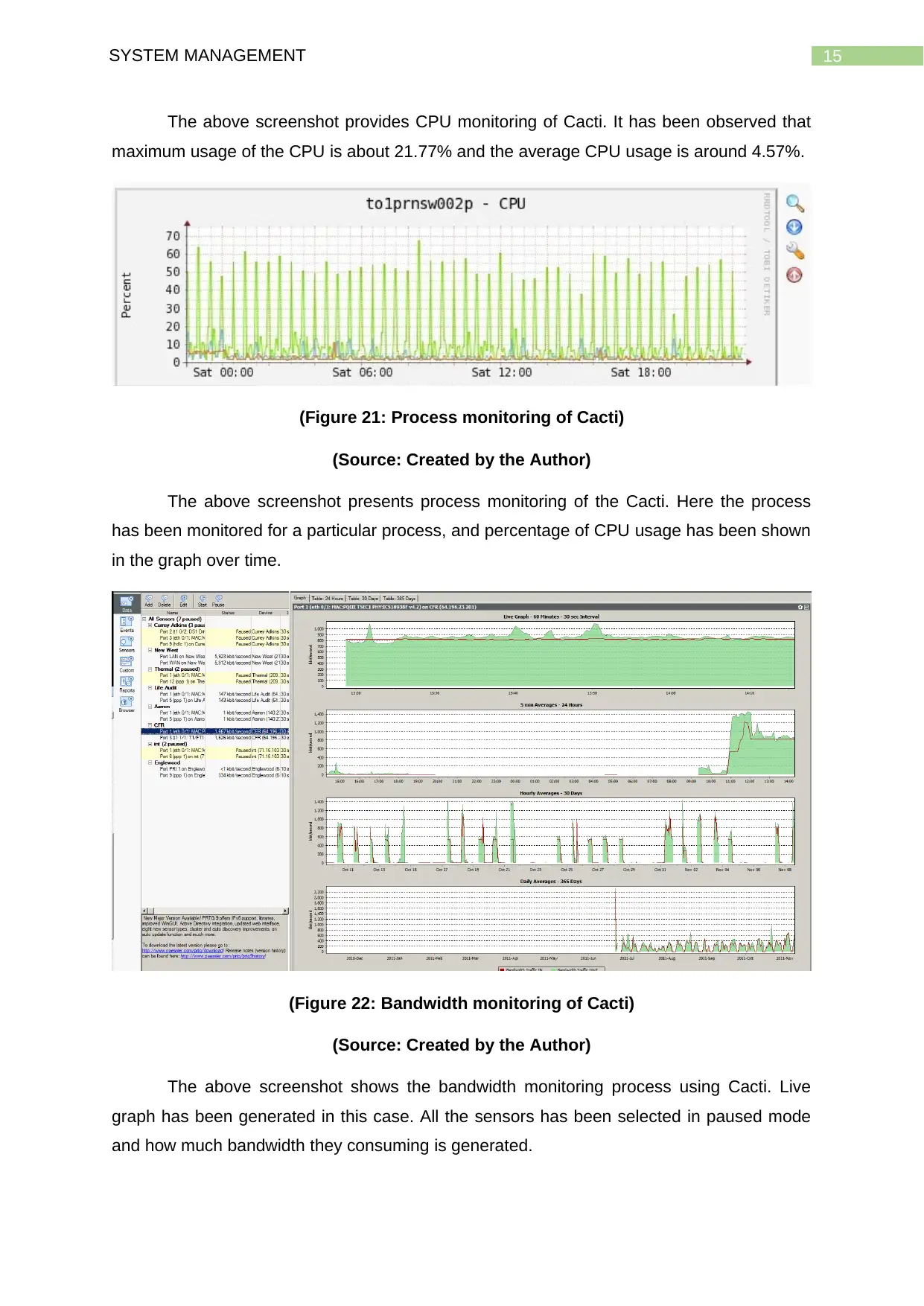
15SYSTEM MANAGEMENT
The above screenshot provides CPU monitoring of Cacti. It has been observed that
maximum usage of the CPU is about 21.77% and the average CPU usage is around 4.57%.
(Figure 21: Process monitoring of Cacti)
(Source: Created by the Author)
The above screenshot presents process monitoring of the Cacti. Here the process
has been monitored for a particular process, and percentage of CPU usage has been shown
in the graph over time.
(Figure 22: Bandwidth monitoring of Cacti)
(Source: Created by the Author)
The above screenshot shows the bandwidth monitoring process using Cacti. Live
graph has been generated in this case. All the sensors has been selected in paused mode
and how much bandwidth they consuming is generated.
The above screenshot provides CPU monitoring of Cacti. It has been observed that
maximum usage of the CPU is about 21.77% and the average CPU usage is around 4.57%.
(Figure 21: Process monitoring of Cacti)
(Source: Created by the Author)
The above screenshot presents process monitoring of the Cacti. Here the process
has been monitored for a particular process, and percentage of CPU usage has been shown
in the graph over time.
(Figure 22: Bandwidth monitoring of Cacti)
(Source: Created by the Author)
The above screenshot shows the bandwidth monitoring process using Cacti. Live
graph has been generated in this case. All the sensors has been selected in paused mode
and how much bandwidth they consuming is generated.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
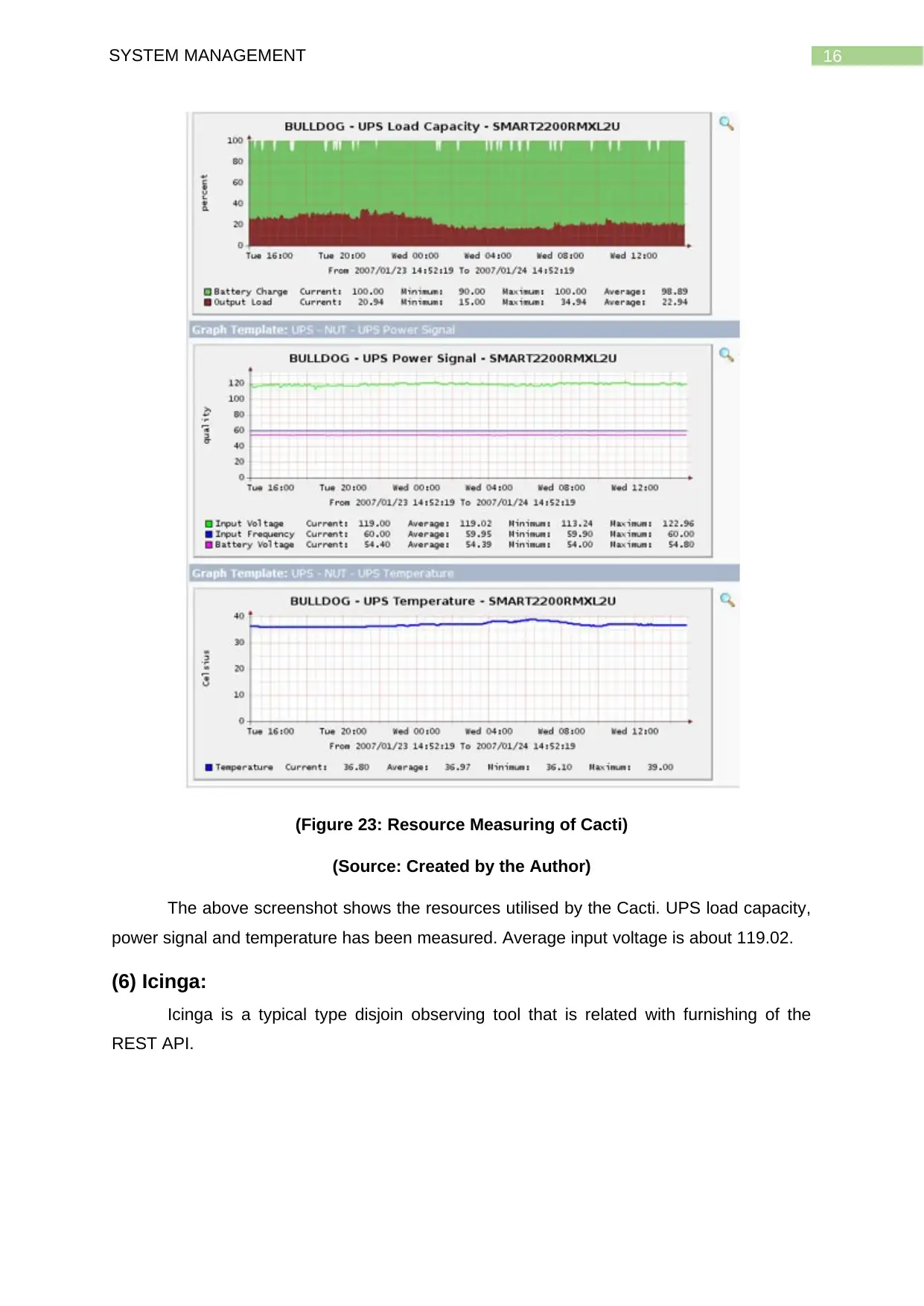
16SYSTEM MANAGEMENT
(Figure 23: Resource Measuring of Cacti)
(Source: Created by the Author)
The above screenshot shows the resources utilised by the Cacti. UPS load capacity,
power signal and temperature has been measured. Average input voltage is about 119.02.
(6) Icinga:
Icinga is a typical type disjoin observing tool that is related with furnishing of the
REST API.
(Figure 23: Resource Measuring of Cacti)
(Source: Created by the Author)
The above screenshot shows the resources utilised by the Cacti. UPS load capacity,
power signal and temperature has been measured. Average input voltage is about 119.02.
(6) Icinga:
Icinga is a typical type disjoin observing tool that is related with furnishing of the
REST API.
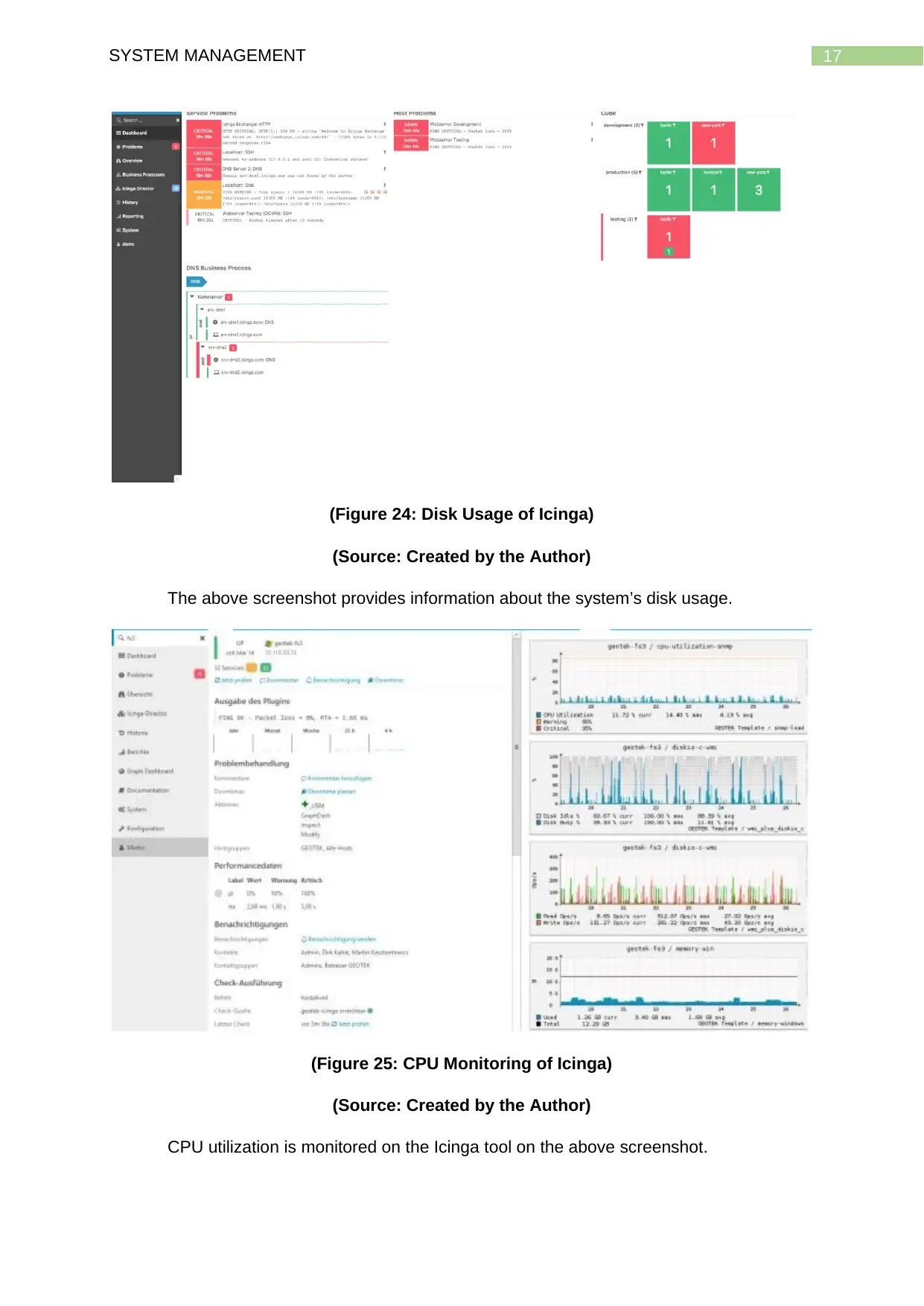
17SYSTEM MANAGEMENT
(Figure 24: Disk Usage of Icinga)
(Source: Created by the Author)
The above screenshot provides information about the system’s disk usage.
(Figure 25: CPU Monitoring of Icinga)
(Source: Created by the Author)
CPU utilization is monitored on the Icinga tool on the above screenshot.
(Figure 24: Disk Usage of Icinga)
(Source: Created by the Author)
The above screenshot provides information about the system’s disk usage.
(Figure 25: CPU Monitoring of Icinga)
(Source: Created by the Author)
CPU utilization is monitored on the Icinga tool on the above screenshot.
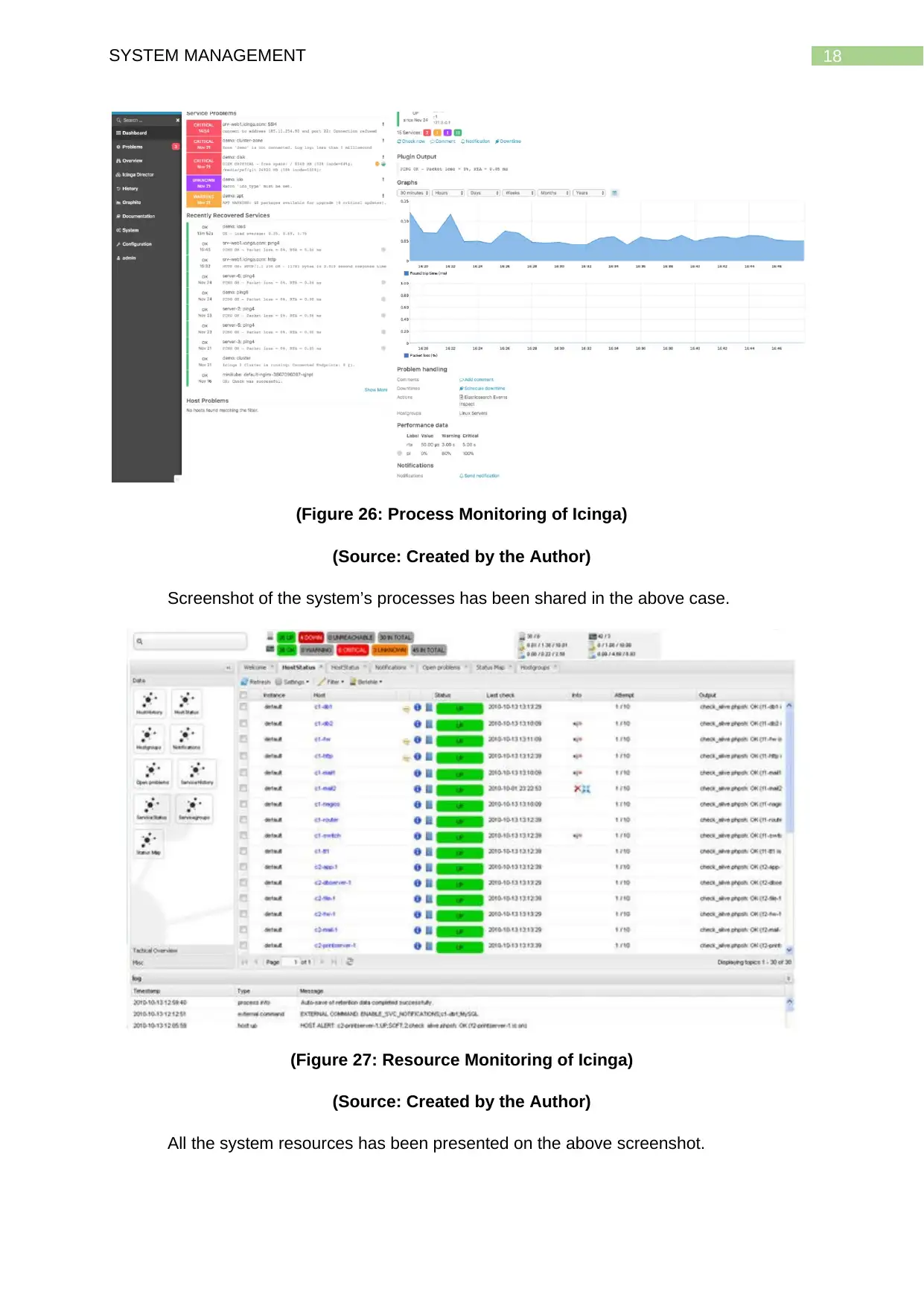
18SYSTEM MANAGEMENT
(Figure 26: Process Monitoring of Icinga)
(Source: Created by the Author)
Screenshot of the system’s processes has been shared in the above case.
(Figure 27: Resource Monitoring of Icinga)
(Source: Created by the Author)
All the system resources has been presented on the above screenshot.
(Figure 26: Process Monitoring of Icinga)
(Source: Created by the Author)
Screenshot of the system’s processes has been shared in the above case.
(Figure 27: Resource Monitoring of Icinga)
(Source: Created by the Author)
All the system resources has been presented on the above screenshot.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
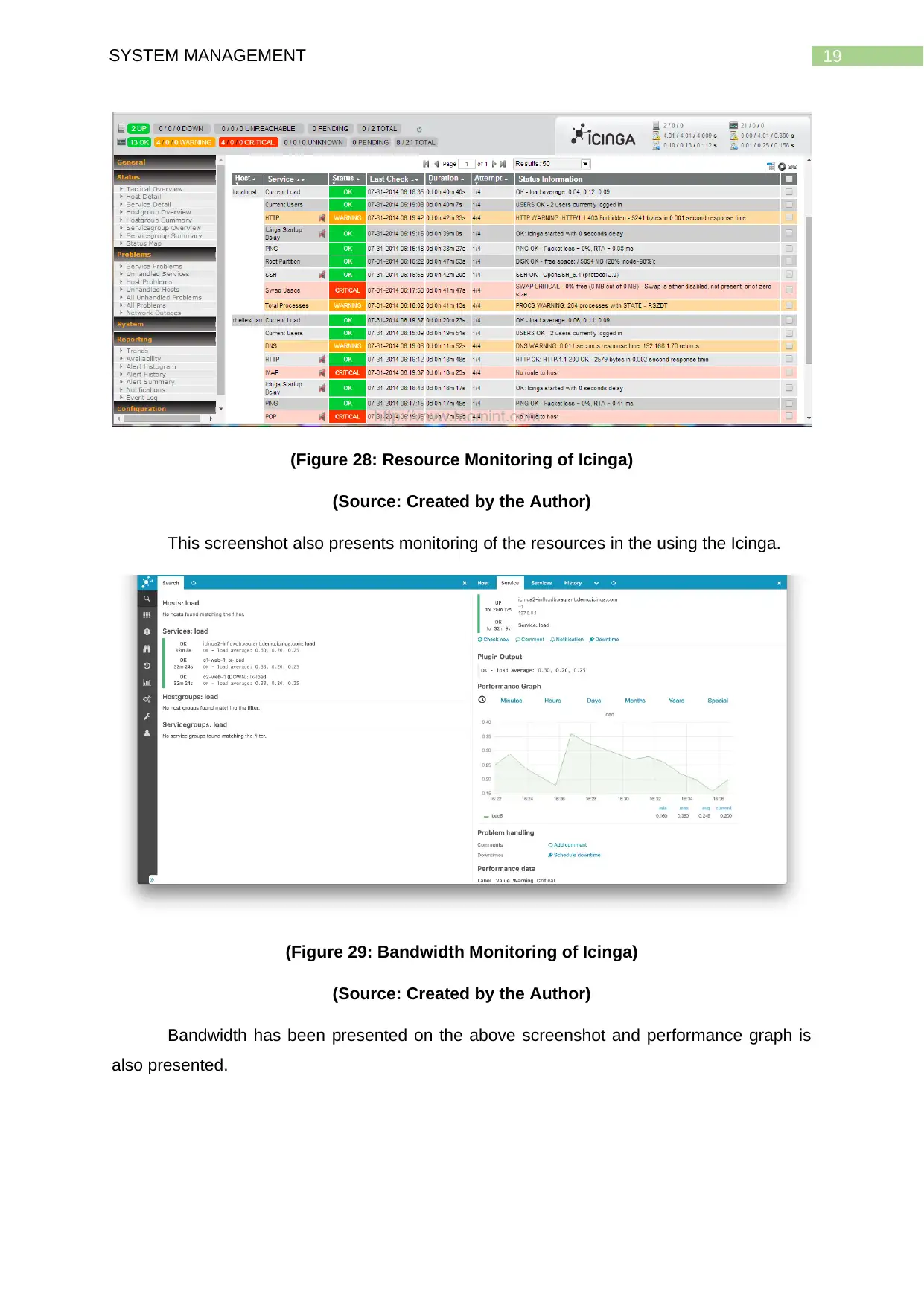
19SYSTEM MANAGEMENT
(Figure 28: Resource Monitoring of Icinga)
(Source: Created by the Author)
This screenshot also presents monitoring of the resources in the using the Icinga.
(Figure 29: Bandwidth Monitoring of Icinga)
(Source: Created by the Author)
Bandwidth has been presented on the above screenshot and performance graph is
also presented.
(Figure 28: Resource Monitoring of Icinga)
(Source: Created by the Author)
This screenshot also presents monitoring of the resources in the using the Icinga.
(Figure 29: Bandwidth Monitoring of Icinga)
(Source: Created by the Author)
Bandwidth has been presented on the above screenshot and performance graph is
also presented.
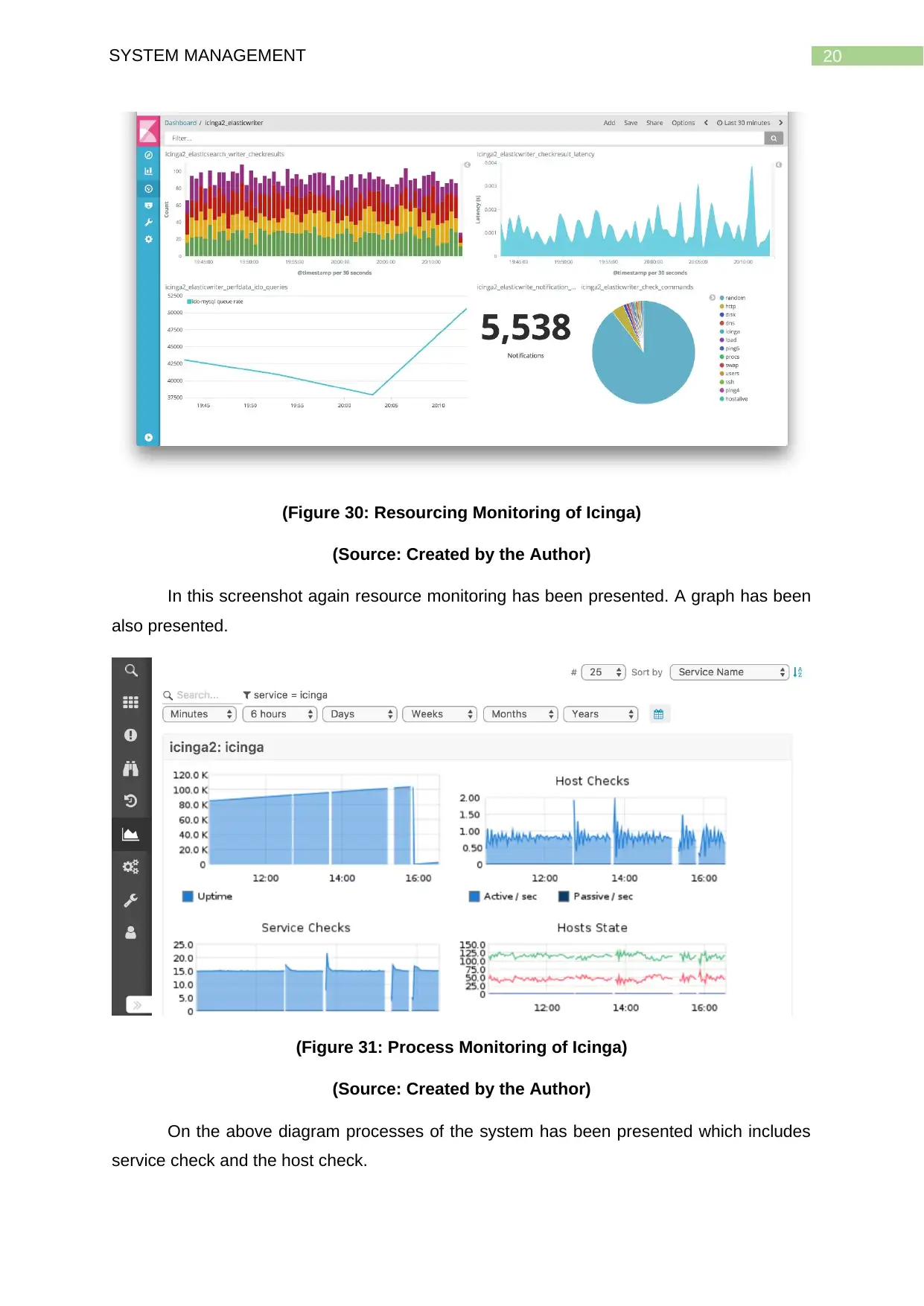
20SYSTEM MANAGEMENT
(Figure 30: Resourcing Monitoring of Icinga)
(Source: Created by the Author)
In this screenshot again resource monitoring has been presented. A graph has been
also presented.
(Figure 31: Process Monitoring of Icinga)
(Source: Created by the Author)
On the above diagram processes of the system has been presented which includes
service check and the host check.
(Figure 30: Resourcing Monitoring of Icinga)
(Source: Created by the Author)
In this screenshot again resource monitoring has been presented. A graph has been
also presented.
(Figure 31: Process Monitoring of Icinga)
(Source: Created by the Author)
On the above diagram processes of the system has been presented which includes
service check and the host check.
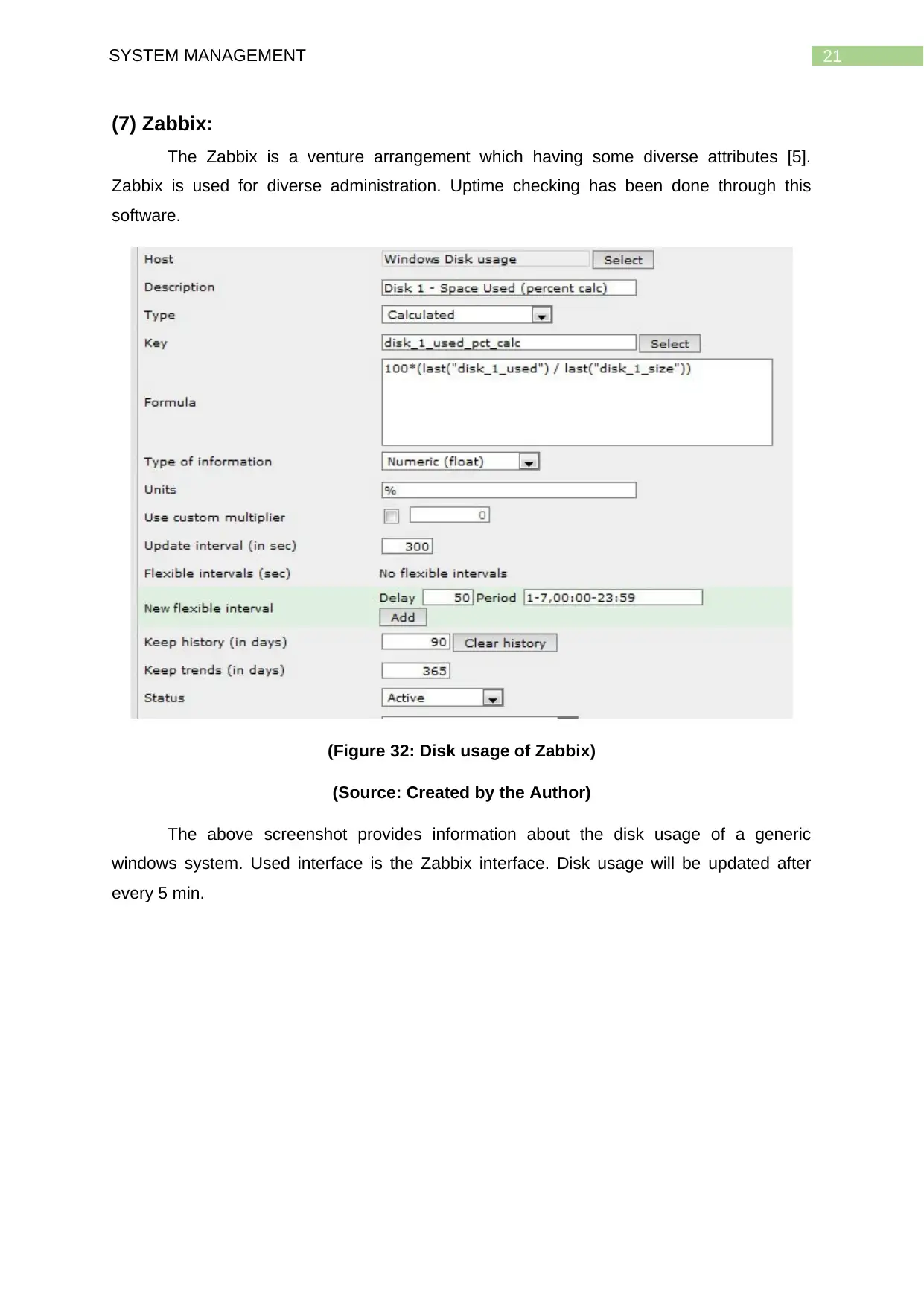
21SYSTEM MANAGEMENT
(7) Zabbix:
The Zabbix is a venture arrangement which having some diverse attributes [5].
Zabbix is used for diverse administration. Uptime checking has been done through this
software.
(Figure 32: Disk usage of Zabbix)
(Source: Created by the Author)
The above screenshot provides information about the disk usage of a generic
windows system. Used interface is the Zabbix interface. Disk usage will be updated after
every 5 min.
(7) Zabbix:
The Zabbix is a venture arrangement which having some diverse attributes [5].
Zabbix is used for diverse administration. Uptime checking has been done through this
software.
(Figure 32: Disk usage of Zabbix)
(Source: Created by the Author)
The above screenshot provides information about the disk usage of a generic
windows system. Used interface is the Zabbix interface. Disk usage will be updated after
every 5 min.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
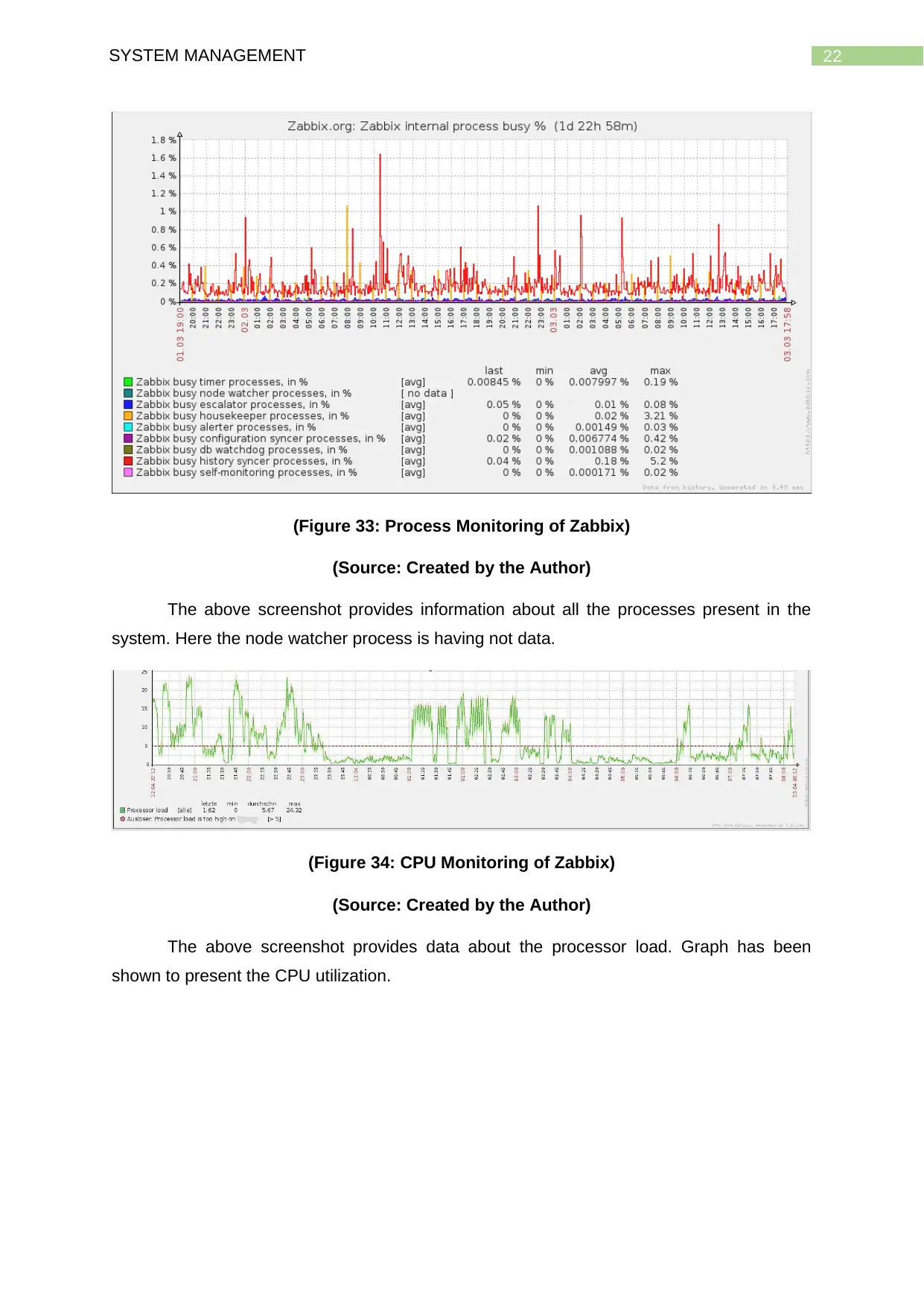
22SYSTEM MANAGEMENT
(Figure 33: Process Monitoring of Zabbix)
(Source: Created by the Author)
The above screenshot provides information about all the processes present in the
system. Here the node watcher process is having not data.
(Figure 34: CPU Monitoring of Zabbix)
(Source: Created by the Author)
The above screenshot provides data about the processor load. Graph has been
shown to present the CPU utilization.
(Figure 33: Process Monitoring of Zabbix)
(Source: Created by the Author)
The above screenshot provides information about all the processes present in the
system. Here the node watcher process is having not data.
(Figure 34: CPU Monitoring of Zabbix)
(Source: Created by the Author)
The above screenshot provides data about the processor load. Graph has been
shown to present the CPU utilization.
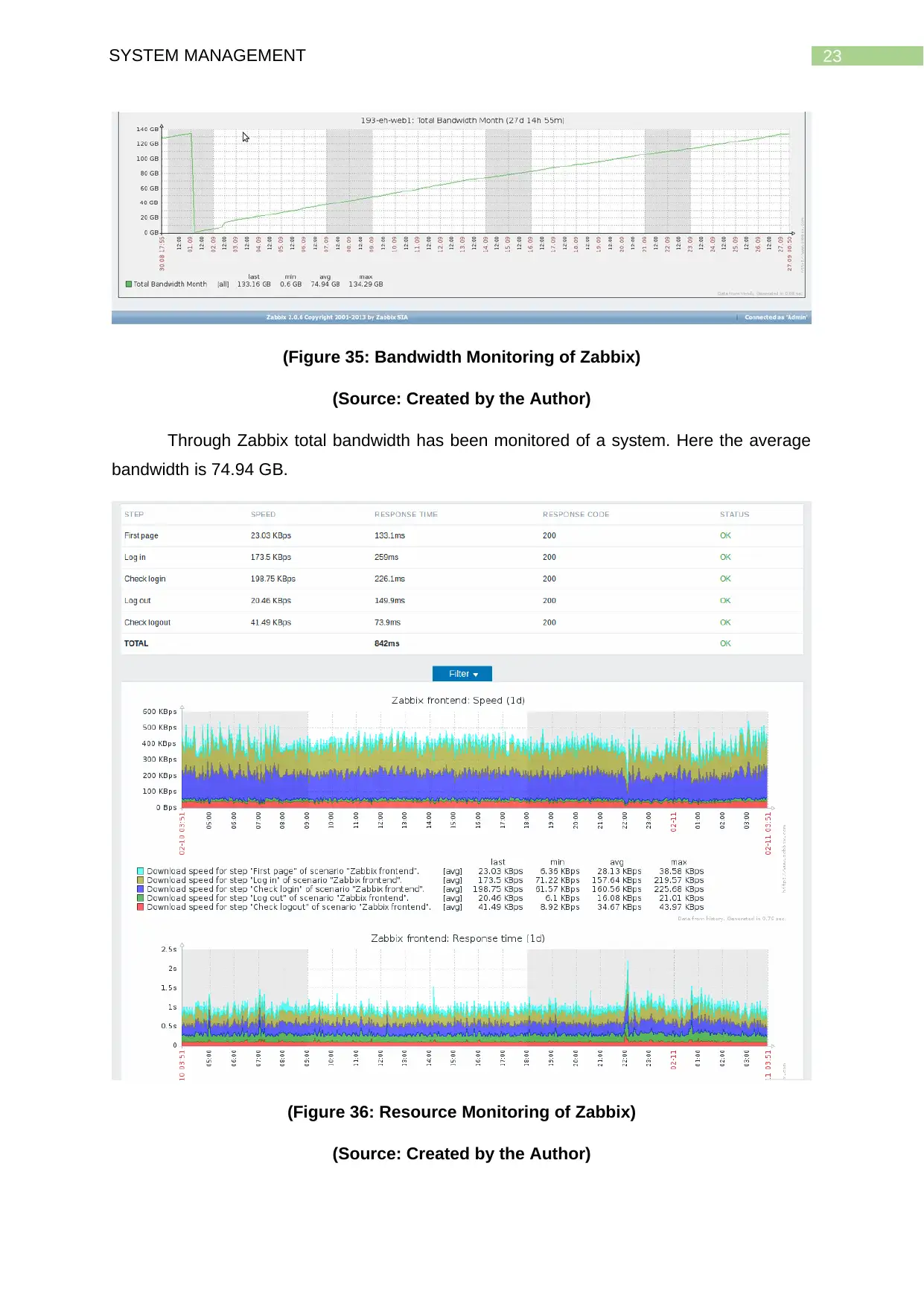
23SYSTEM MANAGEMENT
(Figure 35: Bandwidth Monitoring of Zabbix)
(Source: Created by the Author)
Through Zabbix total bandwidth has been monitored of a system. Here the average
bandwidth is 74.94 GB.
(Figure 36: Resource Monitoring of Zabbix)
(Source: Created by the Author)
(Figure 35: Bandwidth Monitoring of Zabbix)
(Source: Created by the Author)
Through Zabbix total bandwidth has been monitored of a system. Here the average
bandwidth is 74.94 GB.
(Figure 36: Resource Monitoring of Zabbix)
(Source: Created by the Author)
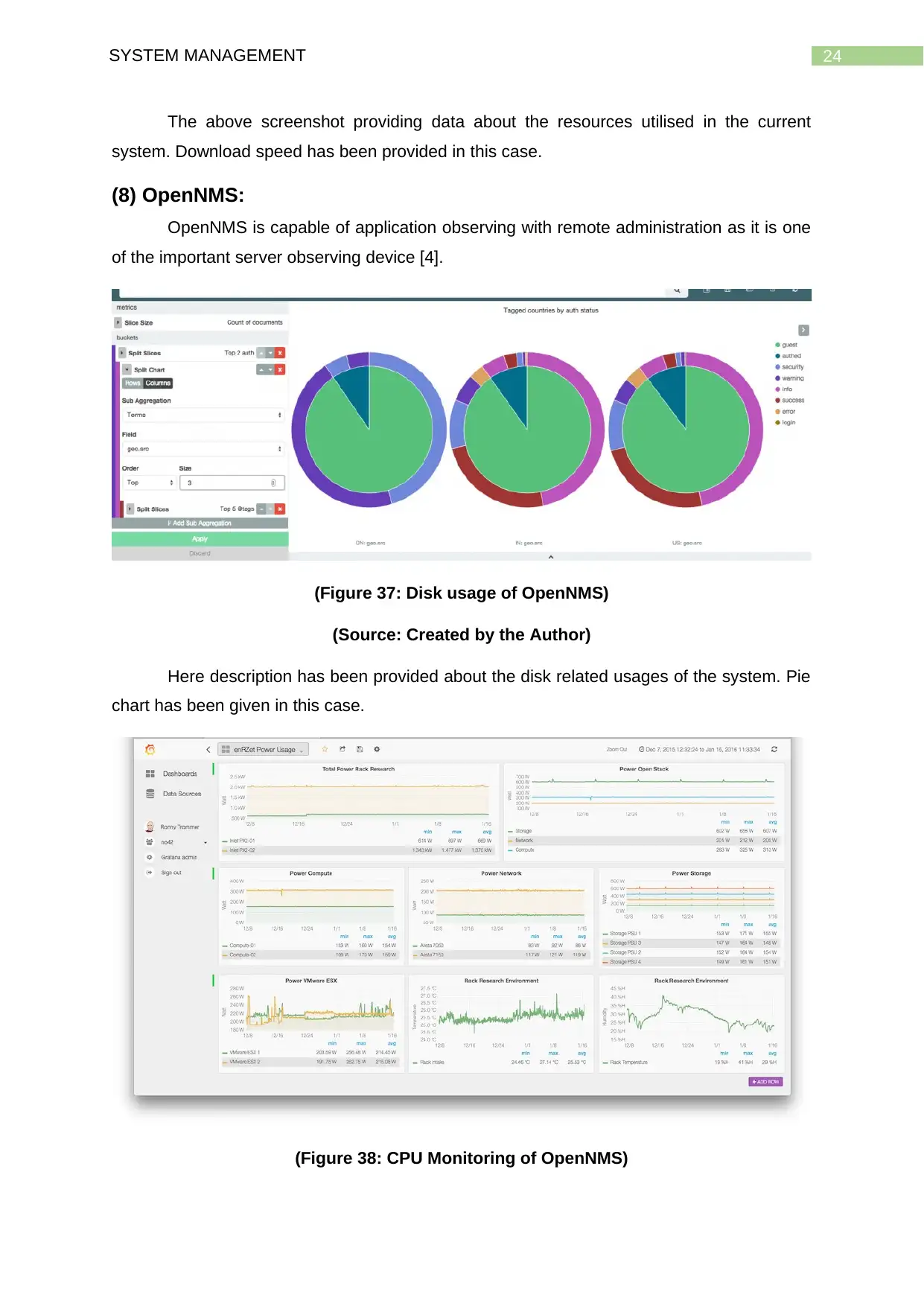
24SYSTEM MANAGEMENT
The above screenshot providing data about the resources utilised in the current
system. Download speed has been provided in this case.
(8) OpenNMS:
OpenNMS is capable of application observing with remote administration as it is one
of the important server observing device [4].
(Figure 37: Disk usage of OpenNMS)
(Source: Created by the Author)
Here description has been provided about the disk related usages of the system. Pie
chart has been given in this case.
(Figure 38: CPU Monitoring of OpenNMS)
The above screenshot providing data about the resources utilised in the current
system. Download speed has been provided in this case.
(8) OpenNMS:
OpenNMS is capable of application observing with remote administration as it is one
of the important server observing device [4].
(Figure 37: Disk usage of OpenNMS)
(Source: Created by the Author)
Here description has been provided about the disk related usages of the system. Pie
chart has been given in this case.
(Figure 38: CPU Monitoring of OpenNMS)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
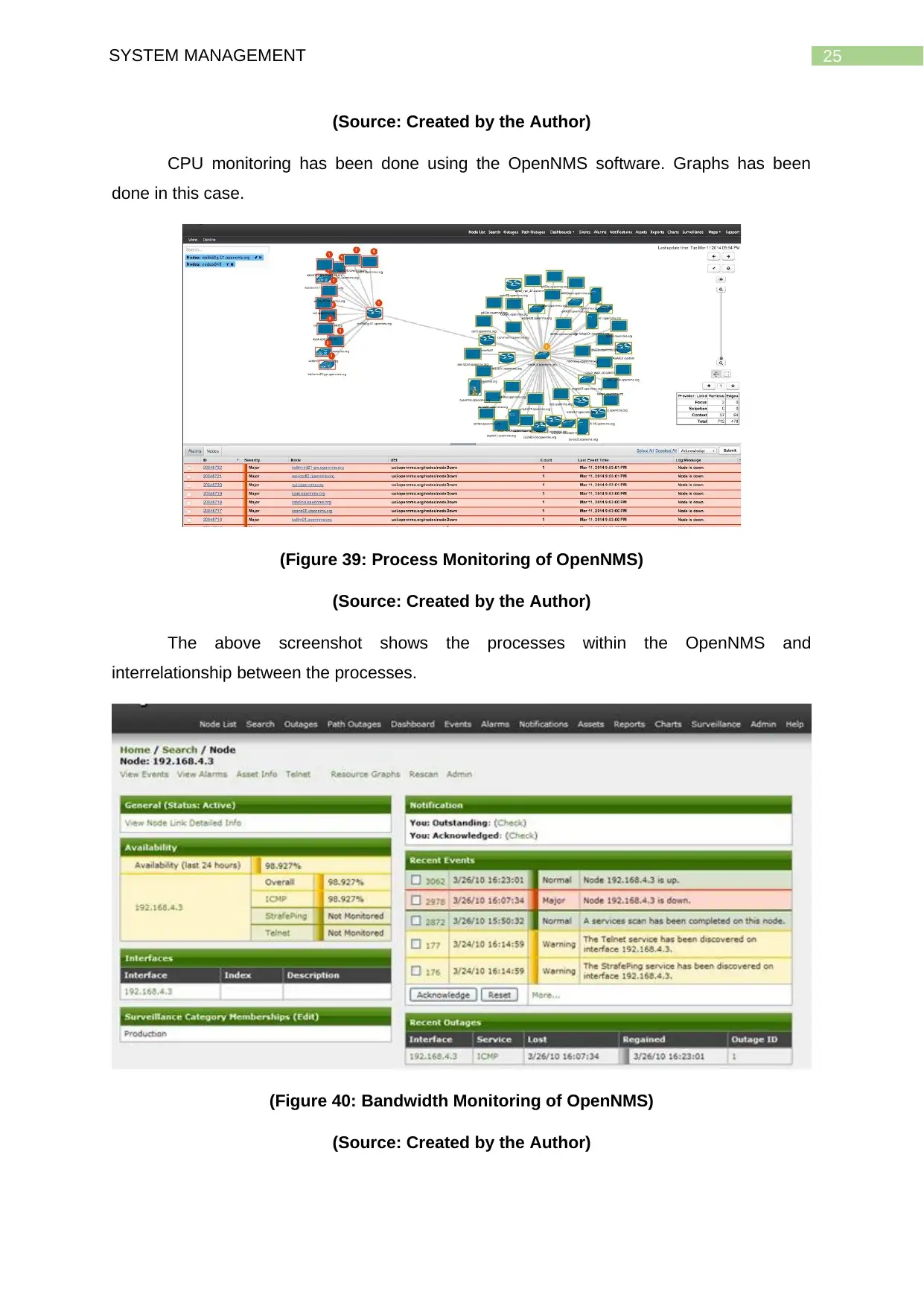
25SYSTEM MANAGEMENT
(Source: Created by the Author)
CPU monitoring has been done using the OpenNMS software. Graphs has been
done in this case.
(Figure 39: Process Monitoring of OpenNMS)
(Source: Created by the Author)
The above screenshot shows the processes within the OpenNMS and
interrelationship between the processes.
(Figure 40: Bandwidth Monitoring of OpenNMS)
(Source: Created by the Author)
(Source: Created by the Author)
CPU monitoring has been done using the OpenNMS software. Graphs has been
done in this case.
(Figure 39: Process Monitoring of OpenNMS)
(Source: Created by the Author)
The above screenshot shows the processes within the OpenNMS and
interrelationship between the processes.
(Figure 40: Bandwidth Monitoring of OpenNMS)
(Source: Created by the Author)
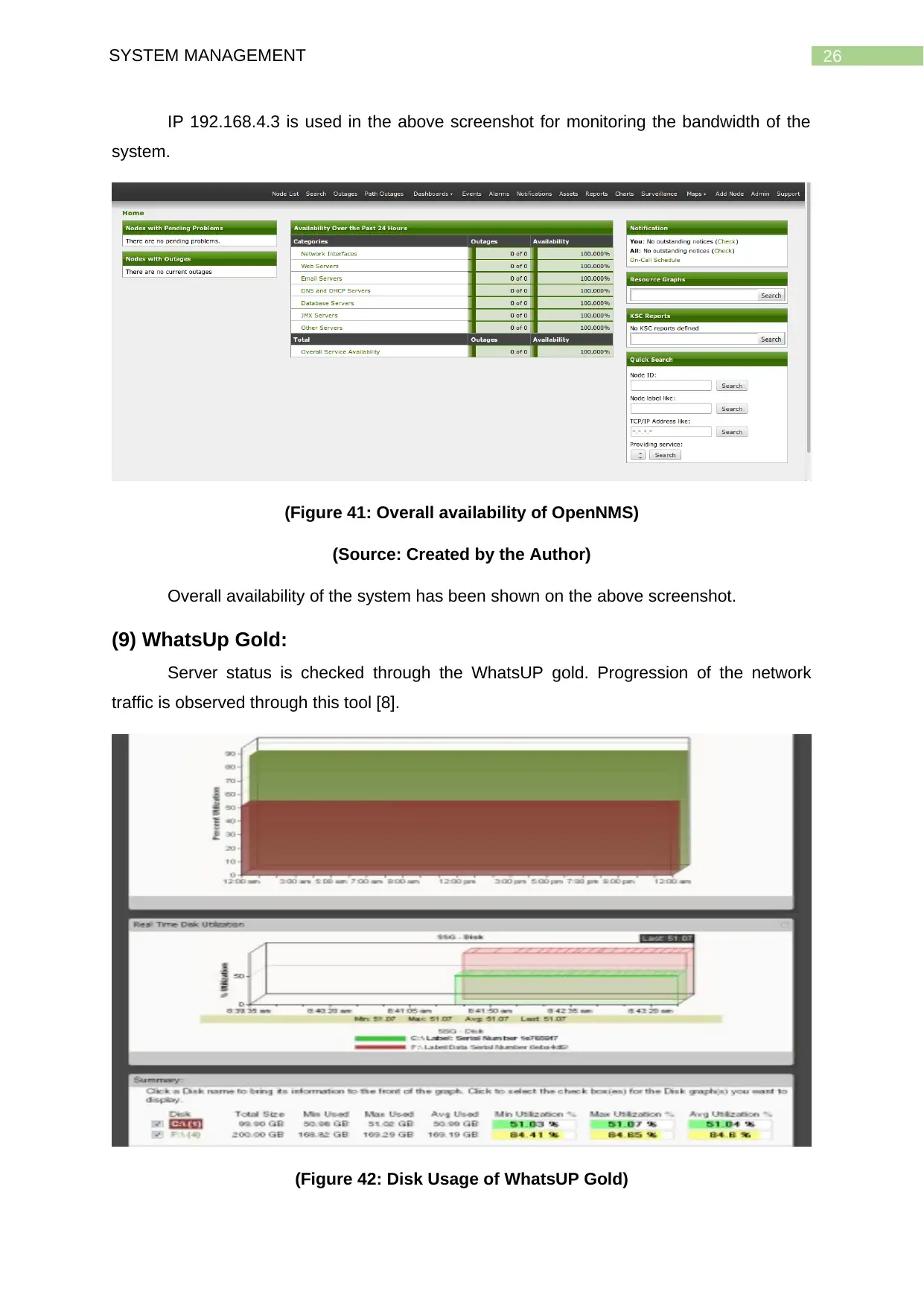
26SYSTEM MANAGEMENT
IP 192.168.4.3 is used in the above screenshot for monitoring the bandwidth of the
system.
(Figure 41: Overall availability of OpenNMS)
(Source: Created by the Author)
Overall availability of the system has been shown on the above screenshot.
(9) WhatsUp Gold:
Server status is checked through the WhatsUP gold. Progression of the network
traffic is observed through this tool [8].
(Figure 42: Disk Usage of WhatsUP Gold)
IP 192.168.4.3 is used in the above screenshot for monitoring the bandwidth of the
system.
(Figure 41: Overall availability of OpenNMS)
(Source: Created by the Author)
Overall availability of the system has been shown on the above screenshot.
(9) WhatsUp Gold:
Server status is checked through the WhatsUP gold. Progression of the network
traffic is observed through this tool [8].
(Figure 42: Disk Usage of WhatsUP Gold)
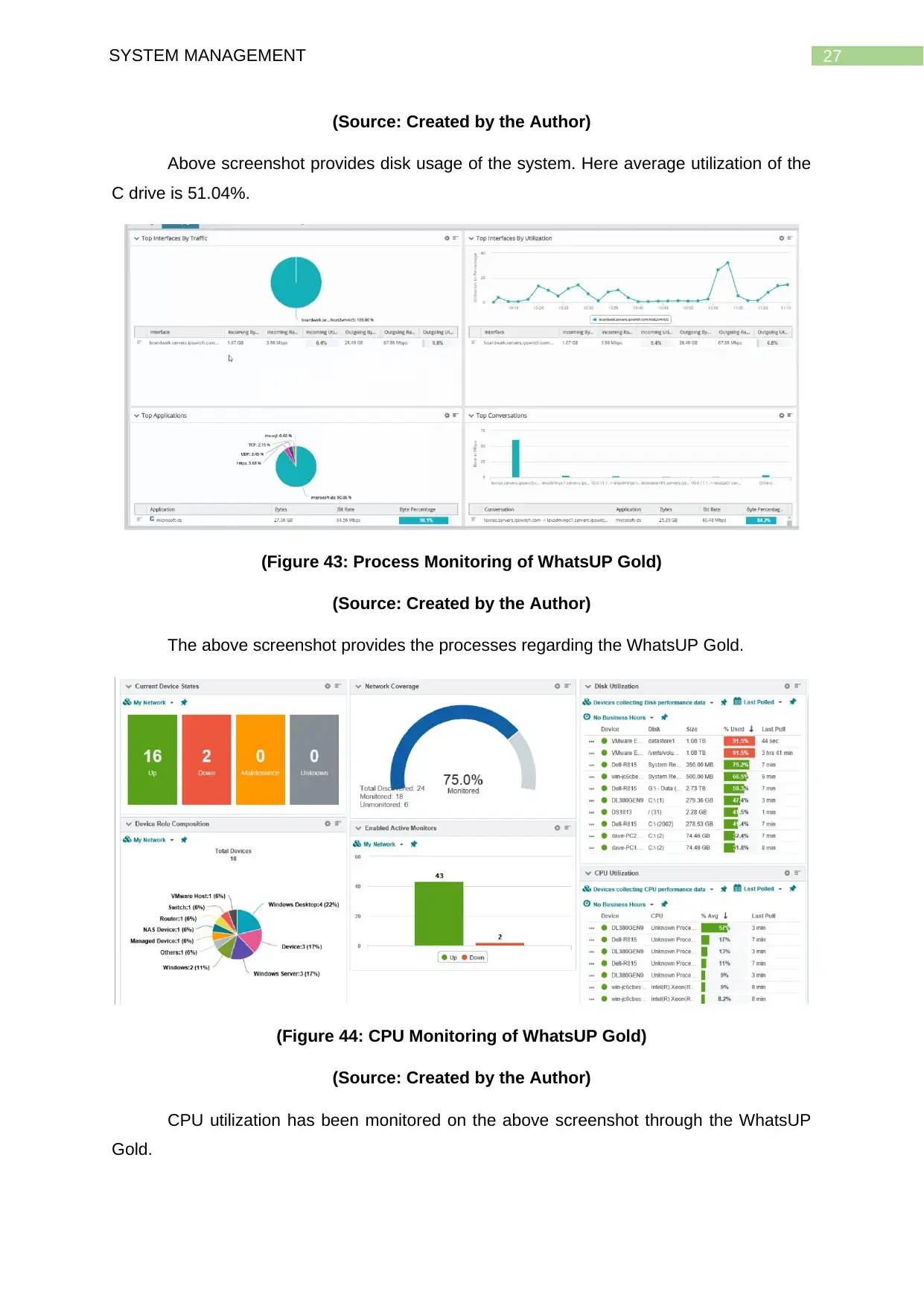
27SYSTEM MANAGEMENT
(Source: Created by the Author)
Above screenshot provides disk usage of the system. Here average utilization of the
C drive is 51.04%.
(Figure 43: Process Monitoring of WhatsUP Gold)
(Source: Created by the Author)
The above screenshot provides the processes regarding the WhatsUP Gold.
(Figure 44: CPU Monitoring of WhatsUP Gold)
(Source: Created by the Author)
CPU utilization has been monitored on the above screenshot through the WhatsUP
Gold.
(Source: Created by the Author)
Above screenshot provides disk usage of the system. Here average utilization of the
C drive is 51.04%.
(Figure 43: Process Monitoring of WhatsUP Gold)
(Source: Created by the Author)
The above screenshot provides the processes regarding the WhatsUP Gold.
(Figure 44: CPU Monitoring of WhatsUP Gold)
(Source: Created by the Author)
CPU utilization has been monitored on the above screenshot through the WhatsUP
Gold.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
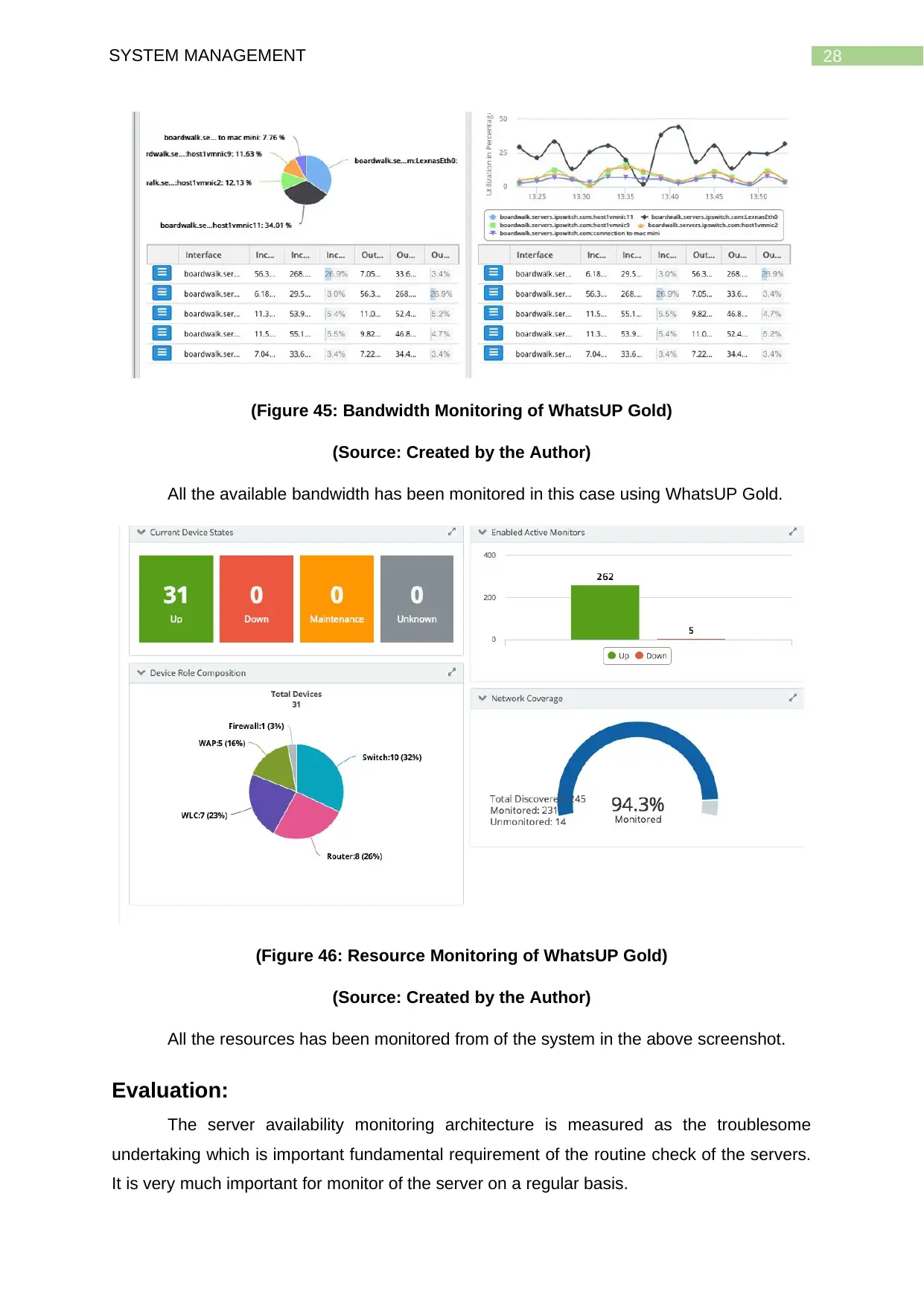
28SYSTEM MANAGEMENT
(Figure 45: Bandwidth Monitoring of WhatsUP Gold)
(Source: Created by the Author)
All the available bandwidth has been monitored in this case using WhatsUP Gold.
(Figure 46: Resource Monitoring of WhatsUP Gold)
(Source: Created by the Author)
All the resources has been monitored from of the system in the above screenshot.
Evaluation:
The server availability monitoring architecture is measured as the troublesome
undertaking which is important fundamental requirement of the routine check of the servers.
It is very much important for monitor of the server on a regular basis.
(Figure 45: Bandwidth Monitoring of WhatsUP Gold)
(Source: Created by the Author)
All the available bandwidth has been monitored in this case using WhatsUP Gold.
(Figure 46: Resource Monitoring of WhatsUP Gold)
(Source: Created by the Author)
All the resources has been monitored from of the system in the above screenshot.
Evaluation:
The server availability monitoring architecture is measured as the troublesome
undertaking which is important fundamental requirement of the routine check of the servers.
It is very much important for monitor of the server on a regular basis.

29SYSTEM MANAGEMENT
Identification and Analysis:
Data can become vulnerable when the server becomes unavailable for many
reasons. Thus some special access is required accessing the servers. Here every of the tool
is important for performing some specific tasks [9]. Extra section of the information is
provided for the information and the vulnerabilities that is identified in this case [7].
Vulnerability exists servers can be experienced by diverse devices.
Propose:
Servers can crash if this tools stops working.
Server can face problem if it fails to detect problem.
System execution regarding the security cannot be resolved.
Conclusion:
The above discussion implies that server monitoring tools are very much important
for monitoring the server so that perfect execution of the server can be achieved. It has been
assessed that observing mechanisms are interrelated with the machine gathering of just as
level of foundation measuring. Here total nine type of server monitoring tool has been
presented and each of them has been assessed in this case. The performance of those tools
has been presented in terms of disk usage, resource measuring, process monitoring,
bandwidth monitoring, overall availability and monitoring of CPU.
Identification and Analysis:
Data can become vulnerable when the server becomes unavailable for many
reasons. Thus some special access is required accessing the servers. Here every of the tool
is important for performing some specific tasks [9]. Extra section of the information is
provided for the information and the vulnerabilities that is identified in this case [7].
Vulnerability exists servers can be experienced by diverse devices.
Propose:
Servers can crash if this tools stops working.
Server can face problem if it fails to detect problem.
System execution regarding the security cannot be resolved.
Conclusion:
The above discussion implies that server monitoring tools are very much important
for monitoring the server so that perfect execution of the server can be achieved. It has been
assessed that observing mechanisms are interrelated with the machine gathering of just as
level of foundation measuring. Here total nine type of server monitoring tool has been
presented and each of them has been assessed in this case. The performance of those tools
has been presented in terms of disk usage, resource measuring, process monitoring,
bandwidth monitoring, overall availability and monitoring of CPU.

30SYSTEM MANAGEMENT
References:
[1] Choi, Jongouk, Chi Shen, Jens Hannemann, and Siddhartha Bhattacharyya. "Real-time
server overloaded monitoring algorithm using back propagation artificial neural network."
In 2017 IEEE 7th Annual Computing and Communication Workshop and Conference
(CCWC), pp. 1-7. IEEE, 2017.
[2] Al Rasyid, M. Udin Harun, Bih-Hwang Lee, and Amang Sudarsono. "Wireless body area
network for monitoring body temperature, heart beat and oxygen in blood." In 2015
International Seminar on Intelligent Technology and Its Applications (ISITIA), pp. 95-98.
IEEE, 2015.
[3] Lombillo, I., H. Blanco, J. Pereda, L. Villegas, C. Carrasco, and J. Balbás. "Structural
health monitoring of a damaged church: design of an integrated platform of electronic
instrumentation, data acquisition and client/server software." Structural Control and Health
Monitoring 23, no. 1 (2016): 69-81.
[4] Chandran, Midhun, and Jayant Walvekar. "Monitoring in a Virtualized
Environment." GSTF Journal on Computing (JoC)1, no. 1 (2018).
[5] Syed, Hassan Jamil, Abdullah Gani, Raja Wasim Ahmad, Muhammad Khurram Khan,
and Abdelmuttlib Ibrahim Abdalla Ahmed. "Cloud monitoring: A review, taxonomy, and open
research issues." Journal of Network and Computer Applications 98 (2017): 11-26.
[6] Flores, Kristoffer O., Isidro M. Butaslac, Jon Enric M. Gonzales, Samuel Matthew G.
Dumlao, and Rosula SJ Reyes. "Precision agriculture monitoring system using wireless
sensor network and Raspberry Pi local server." In 2016 IEEE Region 10 Conference
(TENCON), pp. 3018-3021. IEEE, 2016.
[7] Finn, Robert D., Jody Clements, William Arndt, Benjamin L. Miller, Travis J. Wheeler,
Fabian Schreiber, Alex Bateman, and Sean R. Eddy. "HMMER web server: 2015
update." Nucleic acids research 43, no. W1 (2015): W30-W38.
[8] Van Zundert, G. C. P., J. P. G. L. M. Rodrigues, M. Trellet, C. Schmitz, P. L. Kastritis, E.
Karaca, A. S. J. Melquiond, Marc van Dijk, S. J. De Vries, and A. M. J. J. Bonvin. "The
HADDOCK2. 2 web server: user-friendly integrative modeling of biomolecular
complexes." Journal of molecular biology 428, no. 4 (2016): 720-725.
[9] Richter, Michael, Ramon Rosselló-Móra, Frank Oliver Glöckner, and Jörg Peplies.
"JSpeciesWS: a web server for prokaryotic species circumscription based on pairwise
genome comparison." Bioinformatics 32, no. 6 (2015): 929-931.
References:
[1] Choi, Jongouk, Chi Shen, Jens Hannemann, and Siddhartha Bhattacharyya. "Real-time
server overloaded monitoring algorithm using back propagation artificial neural network."
In 2017 IEEE 7th Annual Computing and Communication Workshop and Conference
(CCWC), pp. 1-7. IEEE, 2017.
[2] Al Rasyid, M. Udin Harun, Bih-Hwang Lee, and Amang Sudarsono. "Wireless body area
network for monitoring body temperature, heart beat and oxygen in blood." In 2015
International Seminar on Intelligent Technology and Its Applications (ISITIA), pp. 95-98.
IEEE, 2015.
[3] Lombillo, I., H. Blanco, J. Pereda, L. Villegas, C. Carrasco, and J. Balbás. "Structural
health monitoring of a damaged church: design of an integrated platform of electronic
instrumentation, data acquisition and client/server software." Structural Control and Health
Monitoring 23, no. 1 (2016): 69-81.
[4] Chandran, Midhun, and Jayant Walvekar. "Monitoring in a Virtualized
Environment." GSTF Journal on Computing (JoC)1, no. 1 (2018).
[5] Syed, Hassan Jamil, Abdullah Gani, Raja Wasim Ahmad, Muhammad Khurram Khan,
and Abdelmuttlib Ibrahim Abdalla Ahmed. "Cloud monitoring: A review, taxonomy, and open
research issues." Journal of Network and Computer Applications 98 (2017): 11-26.
[6] Flores, Kristoffer O., Isidro M. Butaslac, Jon Enric M. Gonzales, Samuel Matthew G.
Dumlao, and Rosula SJ Reyes. "Precision agriculture monitoring system using wireless
sensor network and Raspberry Pi local server." In 2016 IEEE Region 10 Conference
(TENCON), pp. 3018-3021. IEEE, 2016.
[7] Finn, Robert D., Jody Clements, William Arndt, Benjamin L. Miller, Travis J. Wheeler,
Fabian Schreiber, Alex Bateman, and Sean R. Eddy. "HMMER web server: 2015
update." Nucleic acids research 43, no. W1 (2015): W30-W38.
[8] Van Zundert, G. C. P., J. P. G. L. M. Rodrigues, M. Trellet, C. Schmitz, P. L. Kastritis, E.
Karaca, A. S. J. Melquiond, Marc van Dijk, S. J. De Vries, and A. M. J. J. Bonvin. "The
HADDOCK2. 2 web server: user-friendly integrative modeling of biomolecular
complexes." Journal of molecular biology 428, no. 4 (2016): 720-725.
[9] Richter, Michael, Ramon Rosselló-Móra, Frank Oliver Glöckner, and Jörg Peplies.
"JSpeciesWS: a web server for prokaryotic species circumscription based on pairwise
genome comparison." Bioinformatics 32, no. 6 (2015): 929-931.
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





