Web Goat Exploitation and Backtrack Hacking
VerifiedAdded on 2020/04/07
|14
|1488
|304
AI Summary
The assignment delves into the world of web application security by utilizing two powerful tools: the OWASP WebGoat J2EE web application for simulating attacks and BackTrack GNU/Linux for advanced hacking exercises. The document walks through three specific challenges within Web Goat, focusing on authentication bypass, credit card theft, and website defacement. Additionally, it touches upon the use of BackTrack for Facebook hacking. The content explores both offensive and defensive techniques, providing a comprehensive understanding of web security vulnerabilities and mitigation strategies.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

SYSTEM SECURITY
Table of Contents
1. Introduction.......................................................................................................2
Table of Contents
1. Introduction.......................................................................................................2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2. Description of problem:....................................................................................2
3. Techniques used to solve the challenges..........................................................2
4. Screenshots.........................................................................................................3
5. Description of Wireshark.................................................................................9
6. Technique used to attack victim......................................................................9
7. Defense mechanisms........................................................................................12
8. Conclusion........................................................................................................12
References..............................................................................................................12
1
3. Techniques used to solve the challenges..........................................................2
4. Screenshots.........................................................................................................3
5. Description of Wireshark.................................................................................9
6. Technique used to attack victim......................................................................9
7. Defense mechanisms........................................................................................12
8. Conclusion........................................................................................................12
References..............................................................................................................12
1

1. Introduction
The Web Goat J2EE web application (Owasp.org, 2017) (Sinister.ly, 2017) (Udemy, 2017) and
Backtrack GNU/Linux (Dean, 2013) will be installed and configured for performing the security
exploits. The Web Goat application will be used for cracking three challenges. The three
challenges are breaking the authentication, credit card theft and deface the website. The
Backtrack GNU/Linux will be used for face hacking.
Part A
2. Description of problem:
The web goat 5.4 is downloaded to solve this problem. The Web goat challenges are
1. breaking the authorization
2. Credit theft
3. Deface the web page.
3. Techniques used to solve the challenges
1. Download the Web Goat 5.4 by using the gel.com/p/webgoat/
2. Select the Web goat-5.4-OWASP_standard_win#@.zip.
3. Redirect the zip file from the link for downloading.
4. Extract the zip file.
5. Select the bat file in the zip file, to open the web goat with the local host.
6. To start the web goat application, the web browser is accessed.
7. Mozilla fire box is mostly used as web browser to perform the web goat application,
because it runs efficiently.
8. Now the server is initiated. Check whether the server is running or destroyed at the title
bar.
9. To start the access, the selected local host is to be localhost./WebGoat/attack
2
The Web Goat J2EE web application (Owasp.org, 2017) (Sinister.ly, 2017) (Udemy, 2017) and
Backtrack GNU/Linux (Dean, 2013) will be installed and configured for performing the security
exploits. The Web Goat application will be used for cracking three challenges. The three
challenges are breaking the authentication, credit card theft and deface the website. The
Backtrack GNU/Linux will be used for face hacking.
Part A
2. Description of problem:
The web goat 5.4 is downloaded to solve this problem. The Web goat challenges are
1. breaking the authorization
2. Credit theft
3. Deface the web page.
3. Techniques used to solve the challenges
1. Download the Web Goat 5.4 by using the gel.com/p/webgoat/
2. Select the Web goat-5.4-OWASP_standard_win#@.zip.
3. Redirect the zip file from the link for downloading.
4. Extract the zip file.
5. Select the bat file in the zip file, to open the web goat with the local host.
6. To start the web goat application, the web browser is accessed.
7. Mozilla fire box is mostly used as web browser to perform the web goat application,
because it runs efficiently.
8. Now the server is initiated. Check whether the server is running or destroyed at the title
bar.
9. To start the access, the selected local host is to be localhost./WebGoat/attack
2
4. Screenshots
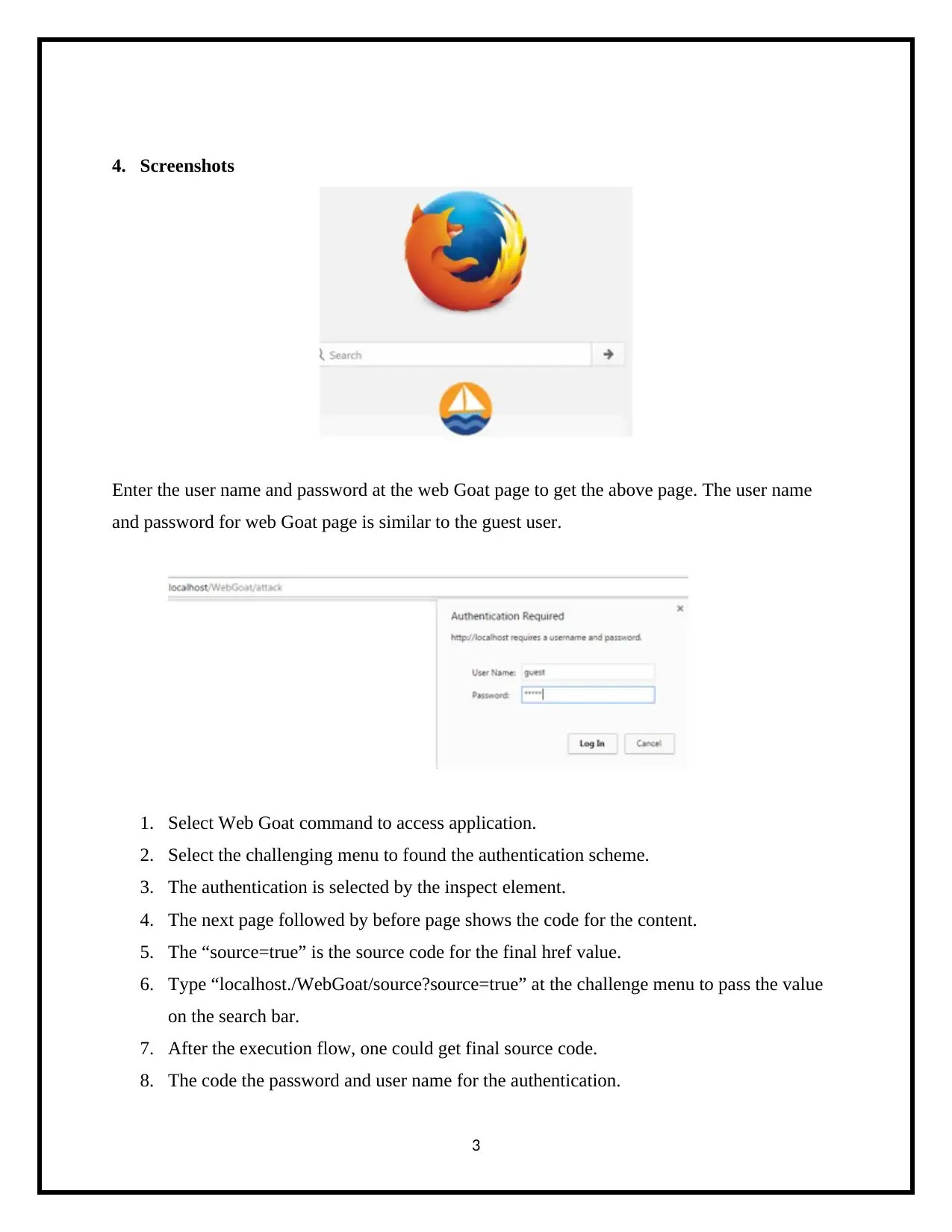
Enter the user name and password at the web Goat page to get the above page. The user name
and password for web Goat page is similar to the guest user.
1. Select Web Goat command to access application.
2. Select the challenging menu to found the authentication scheme.
3. The authentication is selected by the inspect element.
4. The next page followed by before page shows the code for the content.
5. The “source=true” is the source code for the final href value.
6. Type “localhost./WebGoat/source?source=true” at the challenge menu to pass the value
on the search bar.
7. After the execution flow, one could get final source code.
8. The code the password and user name for the authentication.
3
Enter the user name and password at the web Goat page to get the above page. The user name
and password for web Goat page is similar to the guest user.
1. Select Web Goat command to access application.
2. Select the challenging menu to found the authentication scheme.
3. The authentication is selected by the inspect element.
4. The next page followed by before page shows the code for the content.
5. The “source=true” is the source code for the final href value.
6. Type “localhost./WebGoat/source?source=true” at the challenge menu to pass the value
on the search bar.
7. After the execution flow, one could get final source code.
8. The code the password and user name for the authentication.
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
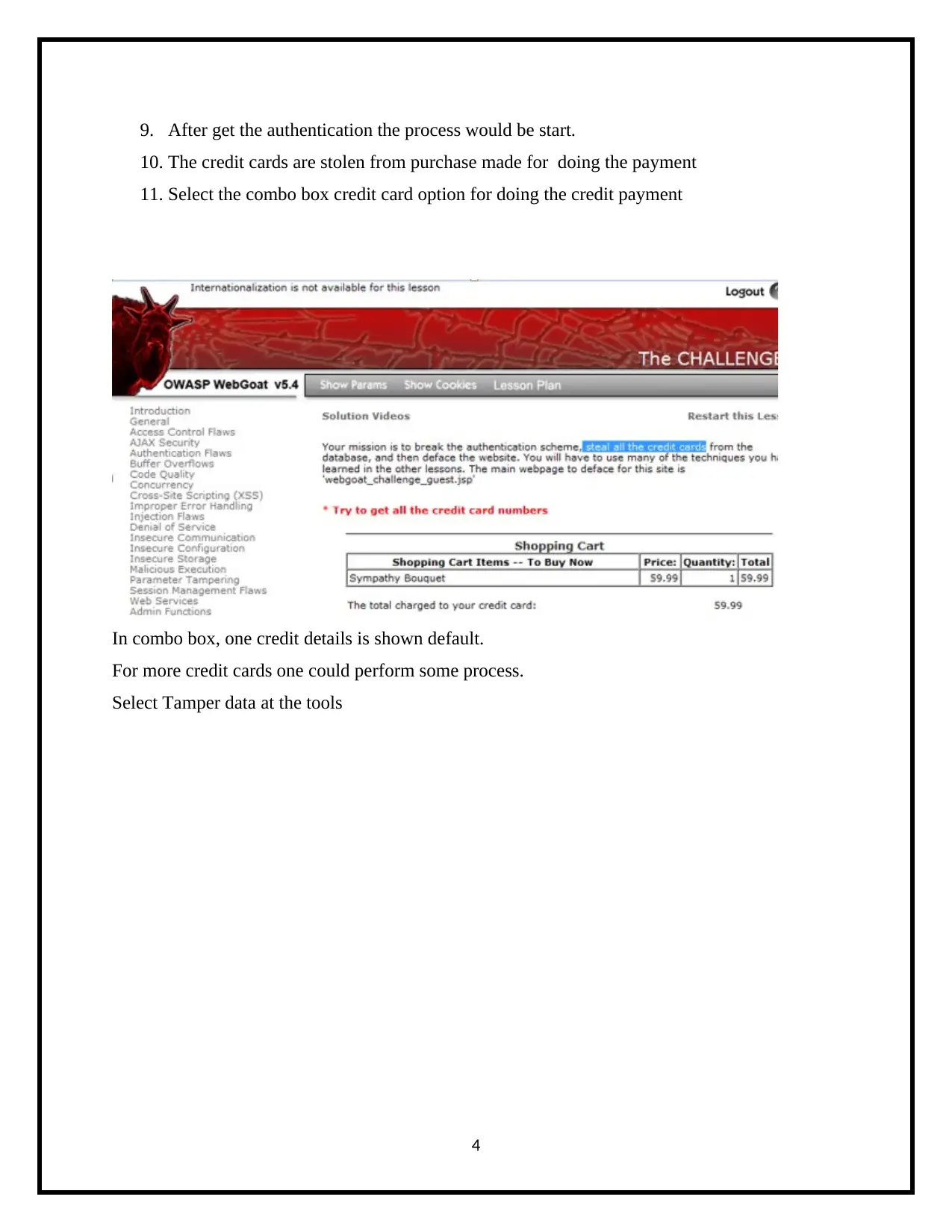
9. After get the authentication the process would be start.
10. The credit cards are stolen from purchase made for doing the payment
11. Select the combo box credit card option for doing the credit payment
In combo box, one credit details is shown default.
For more credit cards one could perform some process.
Select Tamper data at the tools
4
10. The credit cards are stolen from purchase made for doing the payment
11. Select the combo box credit card option for doing the credit payment
In combo box, one credit details is shown default.
For more credit cards one could perform some process.
Select Tamper data at the tools
4
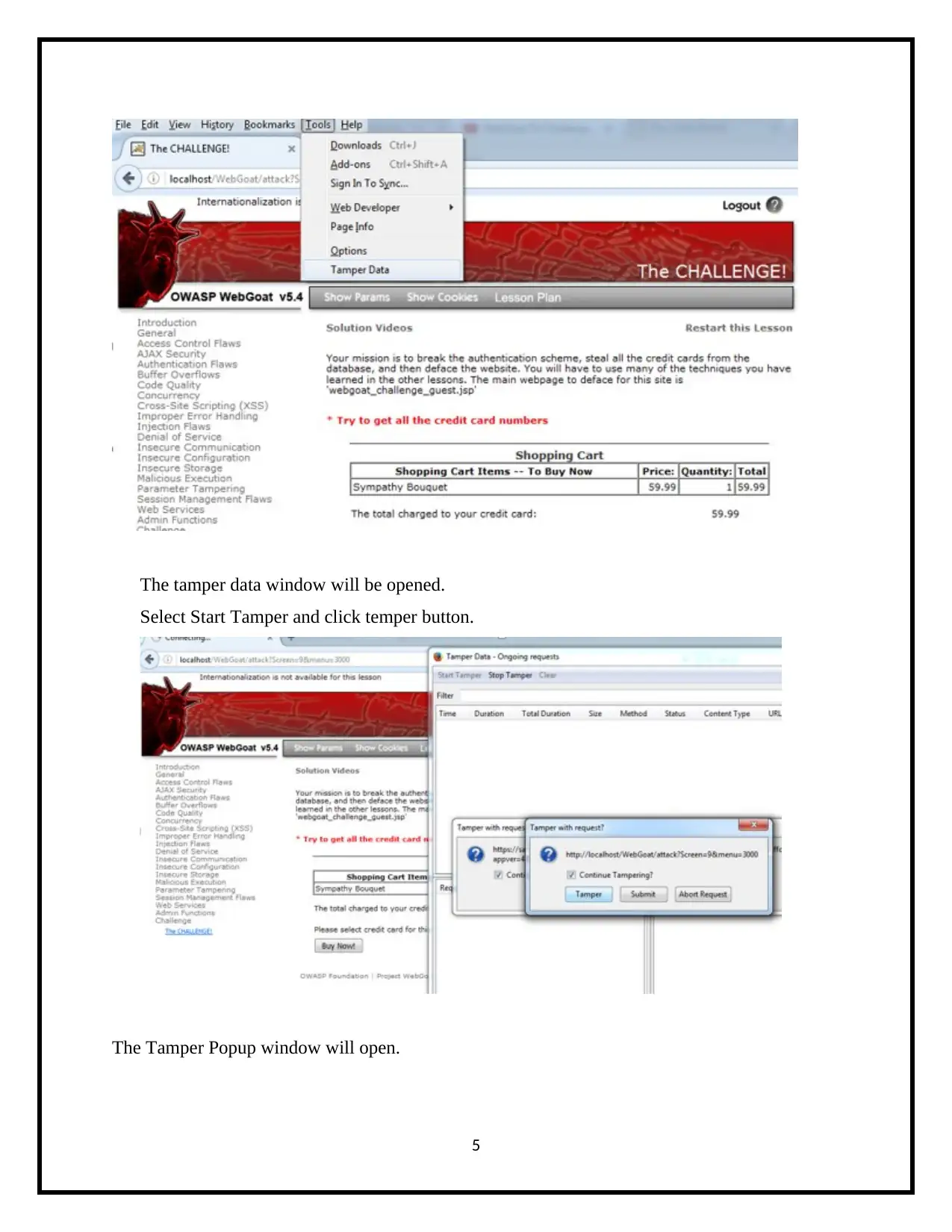
The tamper data window will be opened.
Select Start Tamper and click temper button.
The Tamper Popup window will open.
5
Select Start Tamper and click temper button.
The Tamper Popup window will open.
5
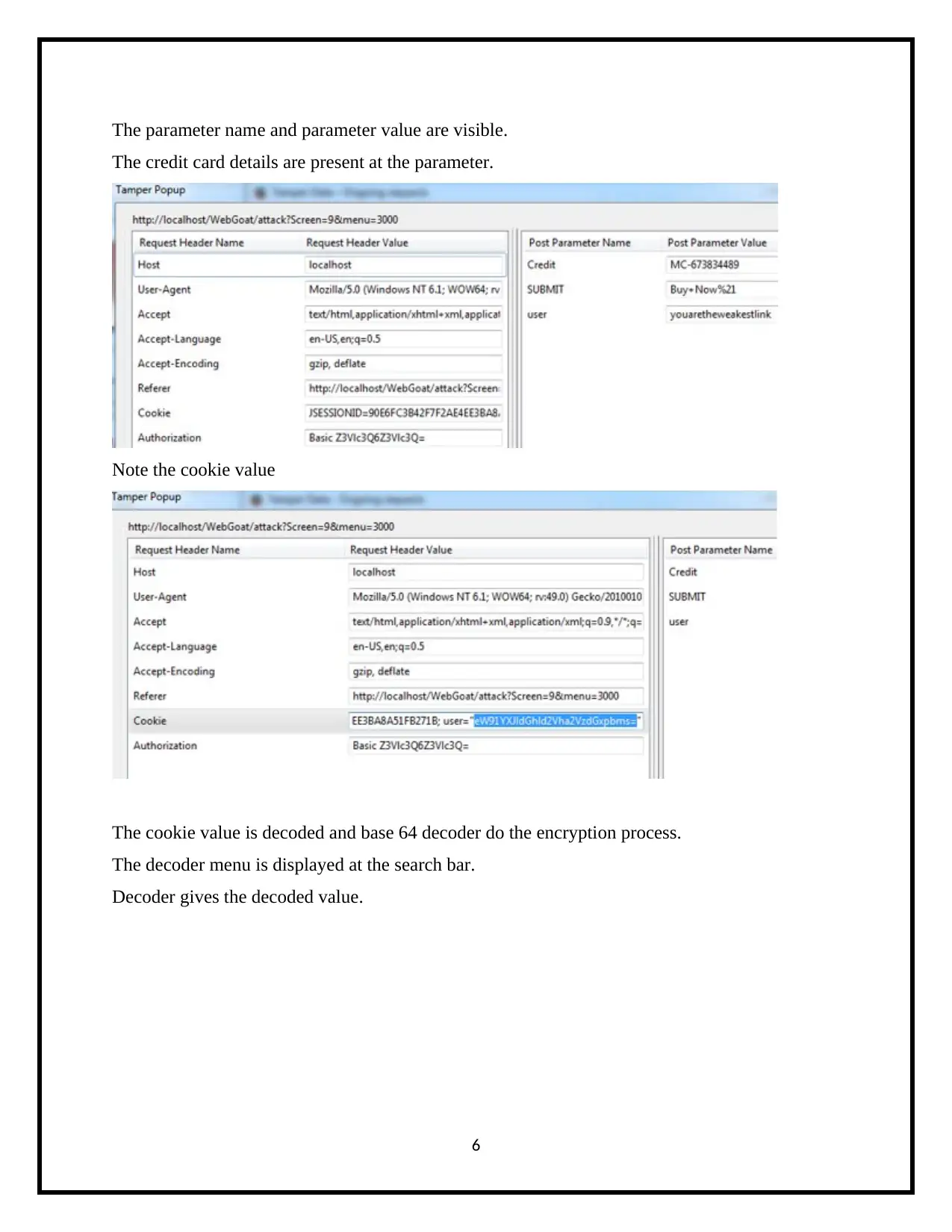
The parameter name and parameter value are visible.
The credit card details are present at the parameter.
Note the cookie value
The cookie value is decoded and base 64 decoder do the encryption process.
The decoder menu is displayed at the search bar.
Decoder gives the decoded value.
6
The credit card details are present at the parameter.
Note the cookie value
The cookie value is decoded and base 64 decoder do the encryption process.
The decoder menu is displayed at the search bar.
Decoder gives the decoded value.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
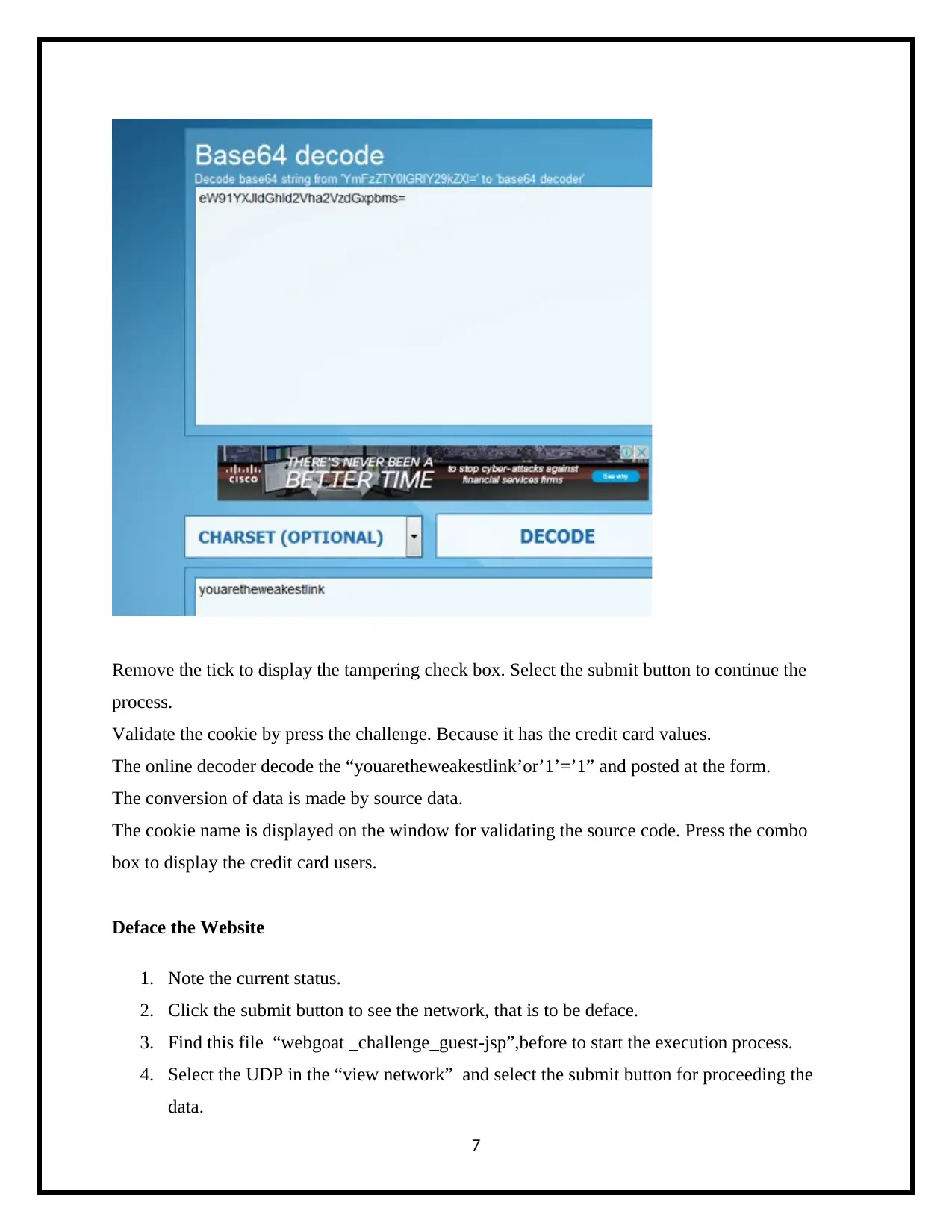
Remove the tick to display the tampering check box. Select the submit button to continue the
process.
Validate the cookie by press the challenge. Because it has the credit card values.
The online decoder decode the “youaretheweakestlink’or’1’=’1” and posted at the form.
The conversion of data is made by source data.
The cookie name is displayed on the window for validating the source code. Press the combo
box to display the credit card users.
Deface the Website
1. Note the current status.
2. Click the submit button to see the network, that is to be deface.
3. Find this file “webgoat _challenge_guest-jsp”,before to start the execution process.
4. Select the UDP in the “view network” and select the submit button for proceeding the
data.
7
process.
Validate the cookie by press the challenge. Because it has the credit card values.
The online decoder decode the “youaretheweakestlink’or’1’=’1” and posted at the form.
The conversion of data is made by source data.
The cookie name is displayed on the window for validating the source code. Press the combo
box to display the credit card users.
Deface the Website
1. Note the current status.
2. Click the submit button to see the network, that is to be deface.
3. Find this file “webgoat _challenge_guest-jsp”,before to start the execution process.
4. Select the UDP in the “view network” and select the submit button for proceeding the
data.
7

5. To change the ping information, select the TCP. To connect the two networks ping
information is used. Press URI component button to get the ping command. Click submit
button to confirm. The ping command and decode value is taken from the TCP .to encode
the file, PHP charset is used. The TCP value is stored with the help of parameter value.
6. This is the path for execution:” c:\Users\hp\Desktop\WebGoat-5.4-
OWASP_Standard_Win32\WebGoat-5.4\tomcat\webapps\WebGoat”.
7. The path for jsp extension is
8. “OWASP_Standard_Win32\WebGoat-5.4\tomcat\webapps\WebGoat\
webgoat_challenge_guest.jsp".”click submit to view the final stage process.
The below measures are the Testing of security attack.
1. Confidentiality
2. Authentication
3. Authorization
4. Non-repudiation
5. Integrity
Methods for testing the attack
1. Testing the cache usage
2. Login credentials check
3. Testing the manipulation of url
4. Checking the execution of SQL injection
Part B:
8
information is used. Press URI component button to get the ping command. Click submit
button to confirm. The ping command and decode value is taken from the TCP .to encode
the file, PHP charset is used. The TCP value is stored with the help of parameter value.
6. This is the path for execution:” c:\Users\hp\Desktop\WebGoat-5.4-
OWASP_Standard_Win32\WebGoat-5.4\tomcat\webapps\WebGoat”.
7. The path for jsp extension is
8. “OWASP_Standard_Win32\WebGoat-5.4\tomcat\webapps\WebGoat\
webgoat_challenge_guest.jsp".”click submit to view the final stage process.
The below measures are the Testing of security attack.
1. Confidentiality
2. Authentication
3. Authorization
4. Non-repudiation
5. Integrity
Methods for testing the attack
1. Testing the cache usage
2. Login credentials check
3. Testing the manipulation of url
4. Checking the execution of SQL injection
Part B:
8
5. Description of Wireshark
It is user for analysing the packets and network traffic.it is one type of open source tool. It is
named as Ethereal. It has three panel to shows the information.
Features
It analyse the data in both data files and wire in the network connection.
It is used for getting the captured data.
It has a data filters.
Wireshark is used for MITM
MITM stands for Man In The Middle attack. It could come in the way of web surfing, social
media and email. It could be happen, when third person intercept the communication between
two users.
6. Technique used to attack victim
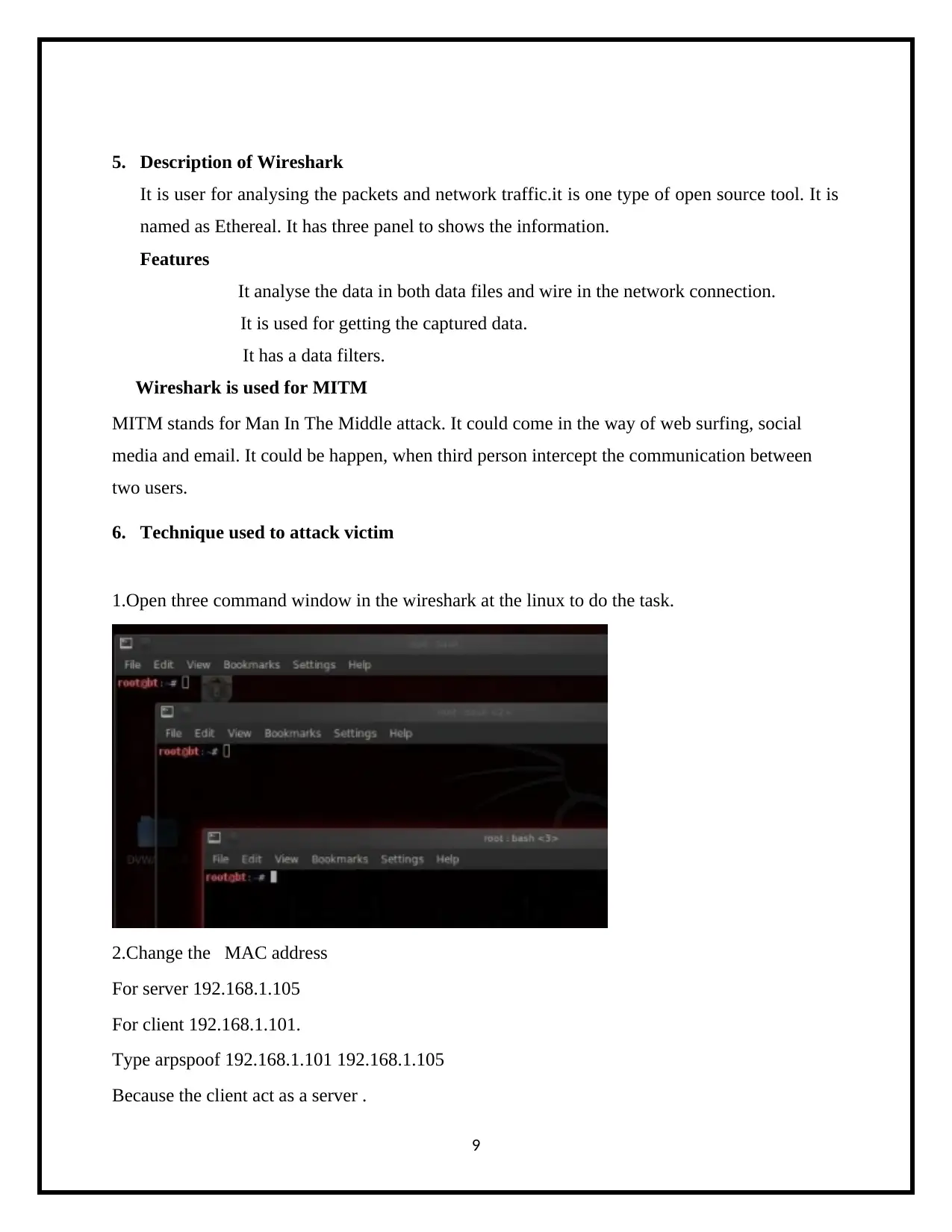
1.Open three command window in the wireshark at the linux to do the task.
2.Change the MAC address
For server 192.168.1.105
For client 192.168.1.101.
Type arpspoof 192.168.1.101 192.168.1.105
Because the client act as a server .
9
It is user for analysing the packets and network traffic.it is one type of open source tool. It is
named as Ethereal. It has three panel to shows the information.
Features
It analyse the data in both data files and wire in the network connection.
It is used for getting the captured data.
It has a data filters.
Wireshark is used for MITM
MITM stands for Man In The Middle attack. It could come in the way of web surfing, social
media and email. It could be happen, when third person intercept the communication between
two users.
6. Technique used to attack victim
1.Open three command window in the wireshark at the linux to do the task.
2.Change the MAC address
For server 192.168.1.105
For client 192.168.1.101.
Type arpspoof 192.168.1.101 192.168.1.105
Because the client act as a server .
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
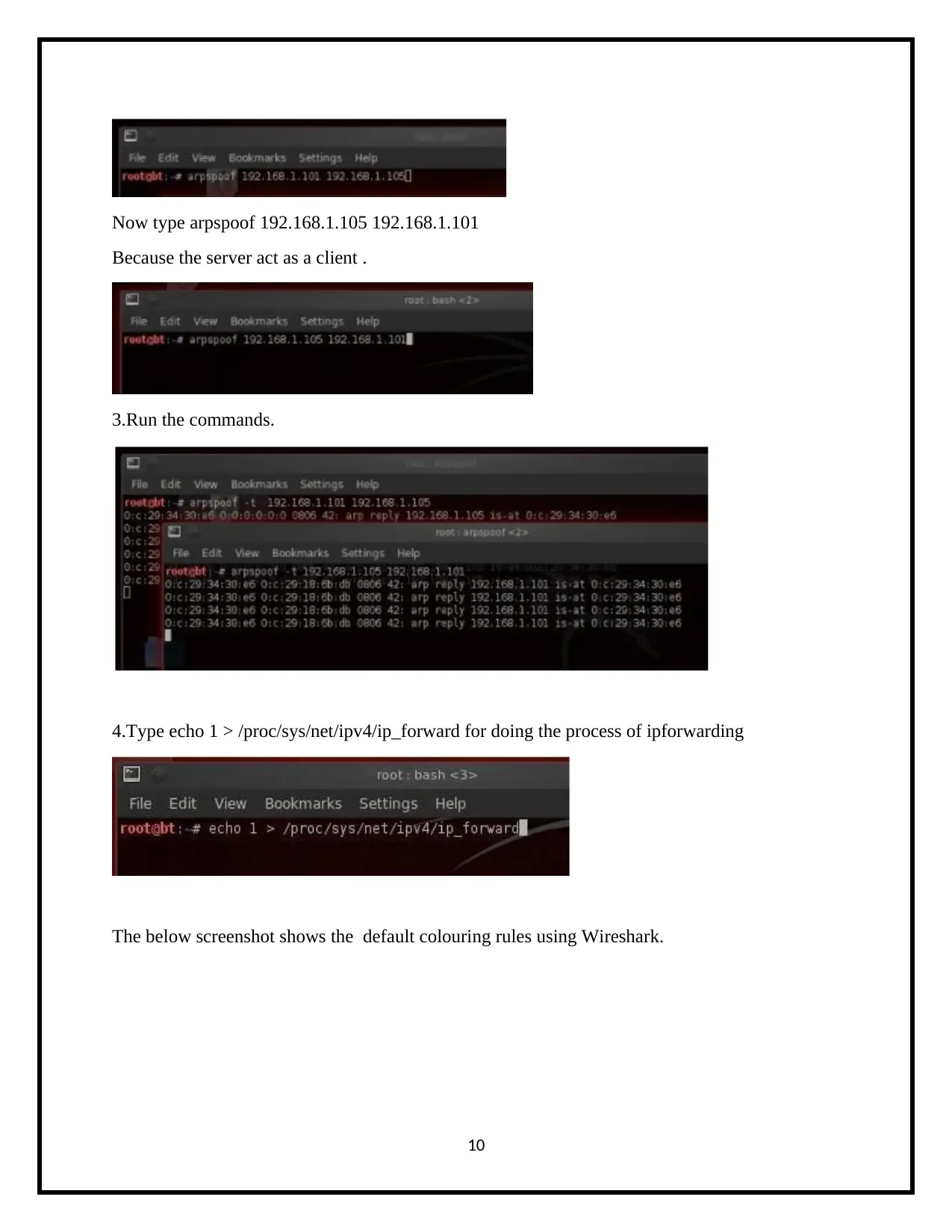
Now type arpspoof 192.168.1.105 192.168.1.101
Because the server act as a client .
3.Run the commands.
4.Type echo 1 > /proc/sys/net/ipv4/ip_forward for doing the process of ipforwarding
The below screenshot shows the default colouring rules using Wireshark.
10
Because the server act as a client .
3.Run the commands.
4.Type echo 1 > /proc/sys/net/ipv4/ip_forward for doing the process of ipforwarding
The below screenshot shows the default colouring rules using Wireshark.
10
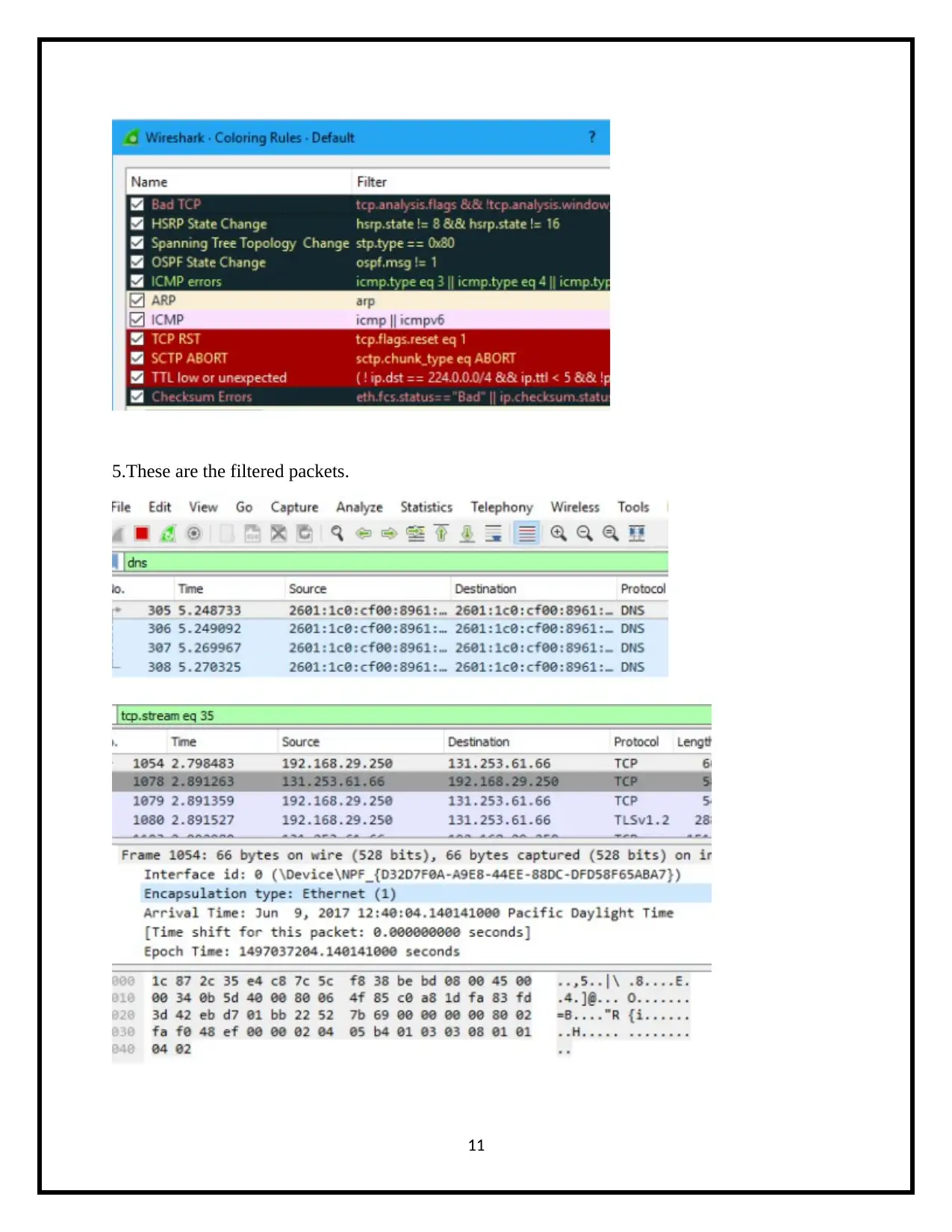
5.These are the filtered packets.
11
11

7. Defense mechanisms
Black-holing or sink holing
Routers and firewalls
Intrusion-detection systems
Servers
DDoS mitigation appliances
Over-provisioning
8. Conclusion
The Web Goat J2EE web application and Backtrack GNU/Linux is installed and configured for
performing the security exploits. The Web Goat application is used for three challenges. The
three challenges are breaking the authentication, credit card theft and deface the website. The
Backtrack GNU/Linux is used for Facebook hacking.
References
Baxter, J. (2014). Wireshark Essentials. Packt Publishing.
Blackstone, W., Lemmings, D. and Prest, W. (n.d.). Commentaries on the laws of England.
Chappell, L. (2012). Wireshark network analysis. San Jose, Calif.: Chappell University.
Dalheimer, M. and Welsh, M. (2009). Running Linux. Sebastopol: O'Reilly Media, Inc.
Darwin, P. and Kozlowski, P. (2013). AngularJS Web Application Development. Birmingham:
Packt Publishing.
Dean, J. (2013). Backtrack. London: Headline.
GNU Octave Beginner's Guide. (2011). Birmingham: Packt Publishing.
Mecklenburg, R. (2009). Managing Projects with GNU Make. Sebastopol: O'Reilly Media, Inc.
Orzach, Y. (2013). Network analysis using Wireshark cookbook. Birmingham: Packt Publishing.
12
Black-holing or sink holing
Routers and firewalls
Intrusion-detection systems
Servers
DDoS mitigation appliances
Over-provisioning
8. Conclusion
The Web Goat J2EE web application and Backtrack GNU/Linux is installed and configured for
performing the security exploits. The Web Goat application is used for three challenges. The
three challenges are breaking the authentication, credit card theft and deface the website. The
Backtrack GNU/Linux is used for Facebook hacking.
References
Baxter, J. (2014). Wireshark Essentials. Packt Publishing.
Blackstone, W., Lemmings, D. and Prest, W. (n.d.). Commentaries on the laws of England.
Chappell, L. (2012). Wireshark network analysis. San Jose, Calif.: Chappell University.
Dalheimer, M. and Welsh, M. (2009). Running Linux. Sebastopol: O'Reilly Media, Inc.
Darwin, P. and Kozlowski, P. (2013). AngularJS Web Application Development. Birmingham:
Packt Publishing.
Dean, J. (2013). Backtrack. London: Headline.
GNU Octave Beginner's Guide. (2011). Birmingham: Packt Publishing.
Mecklenburg, R. (2009). Managing Projects with GNU Make. Sebastopol: O'Reilly Media, Inc.
Orzach, Y. (2013). Network analysis using Wireshark cookbook. Birmingham: Packt Publishing.
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Petersen, R. (2007). Linux. Emeryville, USA: McGraw-Hill Professional Publishing.
Pickrell, L. (2008). Hacking exposed Linux. New York: McGraw-Hill.
Purewal, S. (2014). Learning web application development. Sebastopol, CA: O'Reilly Media.
Shema, M. (2012). Hacking web apps. Amsterdam [u.a.]: Elsevier/Syngress.
Singh, A. (2013). Instant Wireshark starter. Birmingham: Packt Pub. Ltd.
Stuttard, D. and Pinto, M. (2013). The web application hacker's handbook. Hoboken, N.J.:
Wiley.
Sinister.ly. (2017). Question about OWASP WebGoat and challenge sites. [online] Available at:
https://sinister.ly/Thread-Question-about-OWASP-WebGoat-and-challenge-sites [Accessed
28 Sep. 2017].
Udemy. (2017). Learn Hacking using Backtrack 5 - Udemy. [online] Available at:
https://www.udemy.com/learn-hacking-using-backtrack-5/ [Accessed 28 Sep. 2017].
Zeltser.com. (2017). Three Web Attack Vectors Using the Browser. [online] Available at:
https://zeltser.com/web-browser-attack-vectors/ [Accessed 28 Sep. 2017].
13
Pickrell, L. (2008). Hacking exposed Linux. New York: McGraw-Hill.
Purewal, S. (2014). Learning web application development. Sebastopol, CA: O'Reilly Media.
Shema, M. (2012). Hacking web apps. Amsterdam [u.a.]: Elsevier/Syngress.
Singh, A. (2013). Instant Wireshark starter. Birmingham: Packt Pub. Ltd.
Stuttard, D. and Pinto, M. (2013). The web application hacker's handbook. Hoboken, N.J.:
Wiley.
Sinister.ly. (2017). Question about OWASP WebGoat and challenge sites. [online] Available at:
https://sinister.ly/Thread-Question-about-OWASP-WebGoat-and-challenge-sites [Accessed
28 Sep. 2017].
Udemy. (2017). Learn Hacking using Backtrack 5 - Udemy. [online] Available at:
https://www.udemy.com/learn-hacking-using-backtrack-5/ [Accessed 28 Sep. 2017].
Zeltser.com. (2017). Three Web Attack Vectors Using the Browser. [online] Available at:
https://zeltser.com/web-browser-attack-vectors/ [Accessed 28 Sep. 2017].
13
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.

